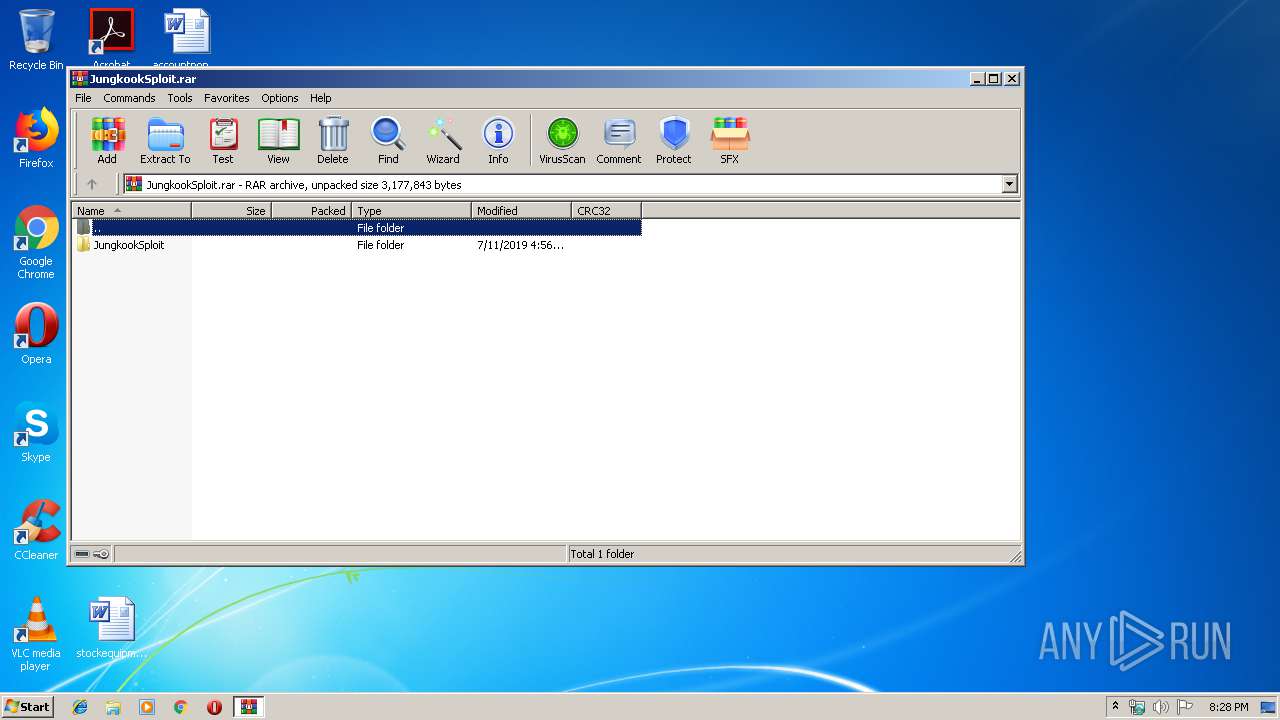
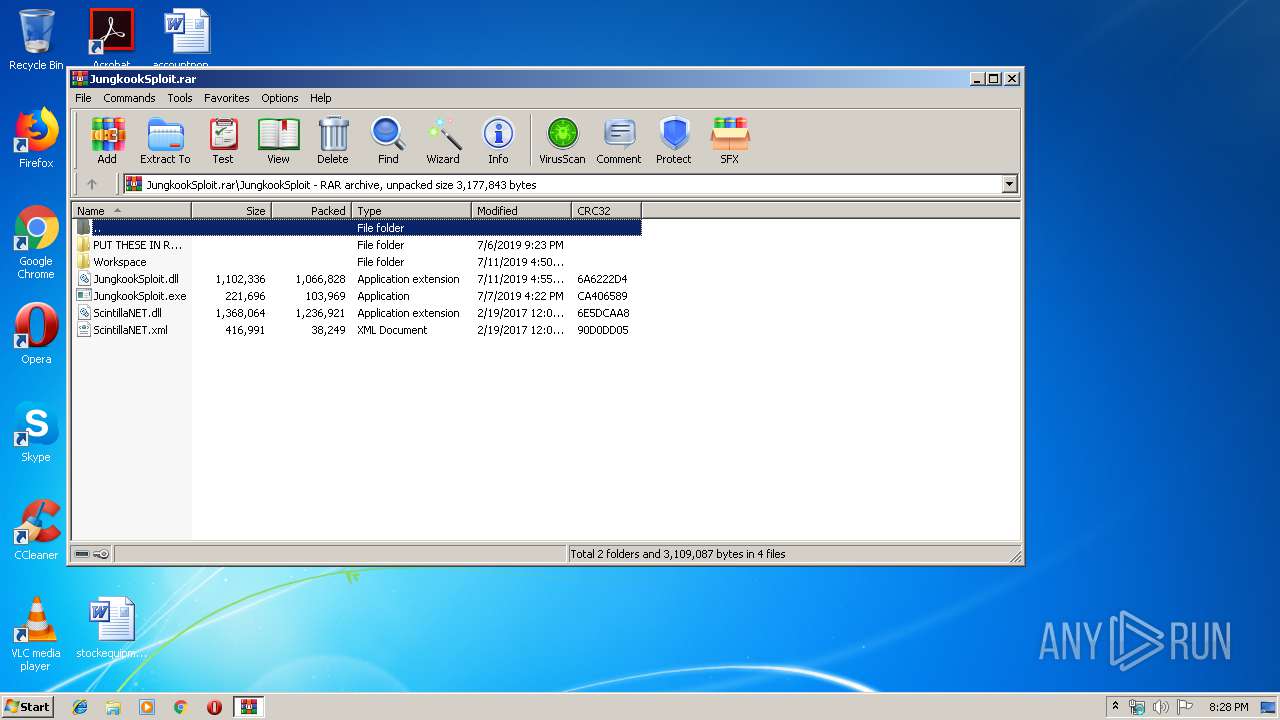
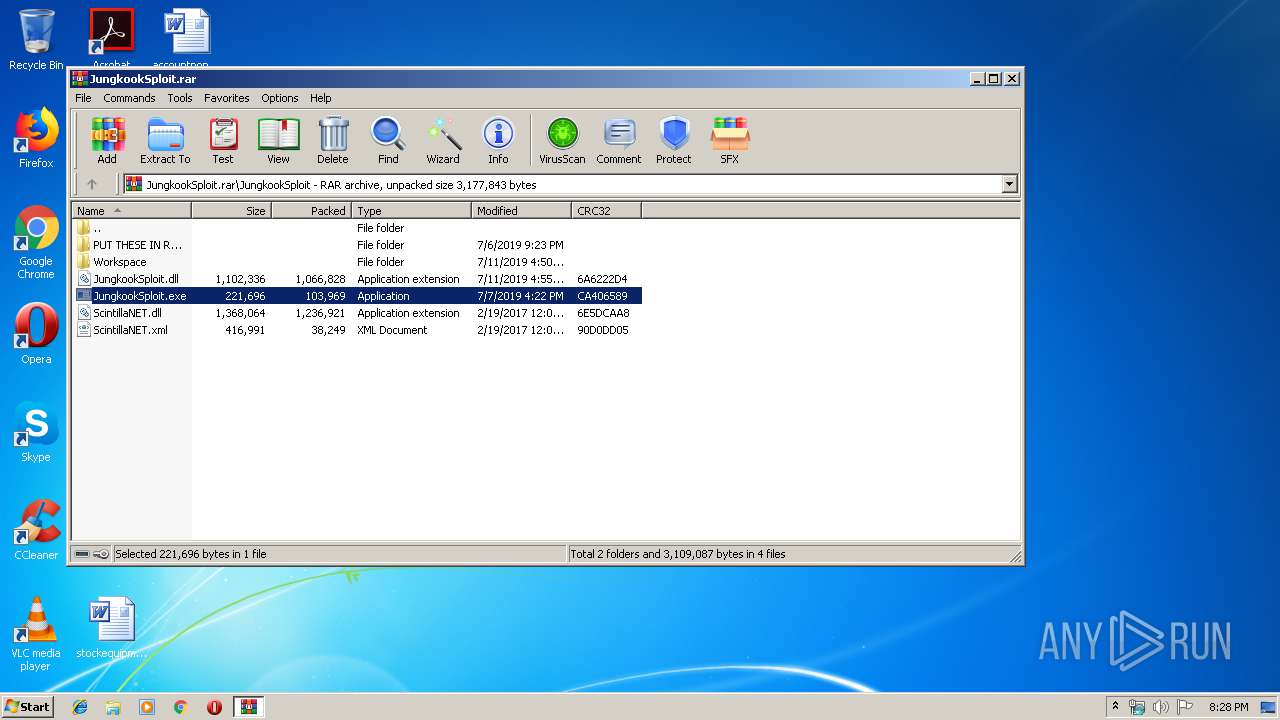
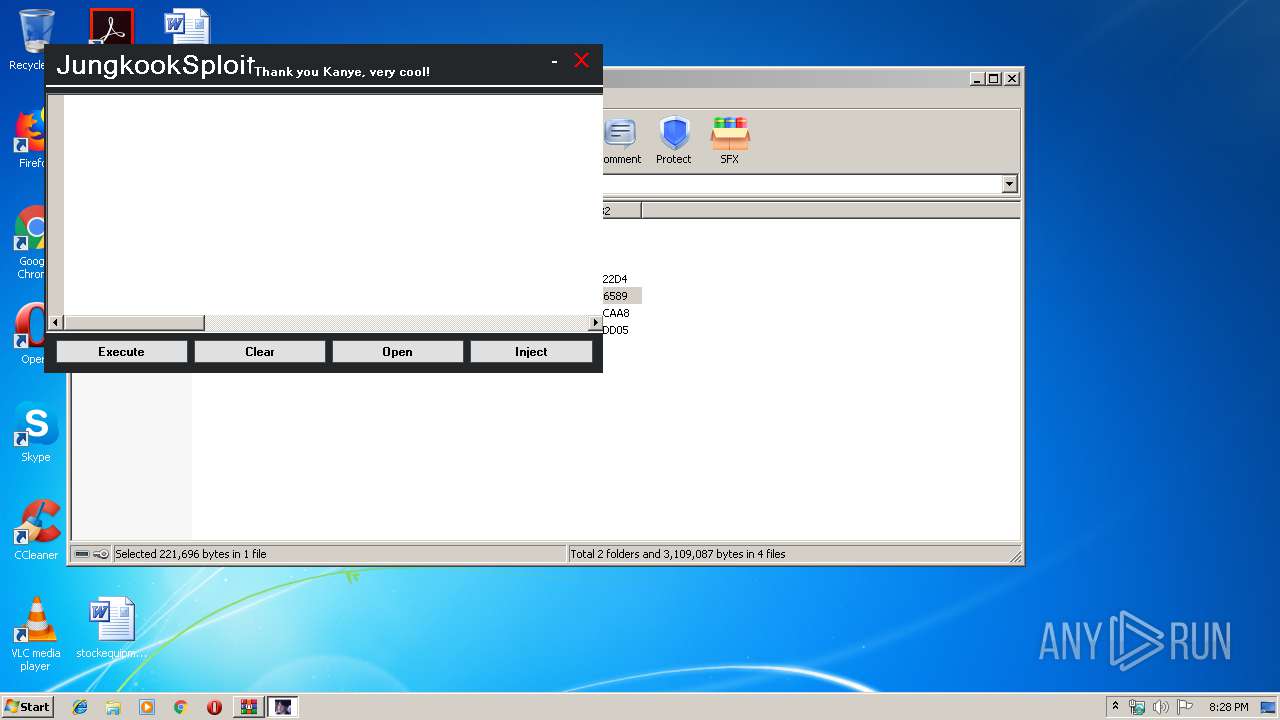
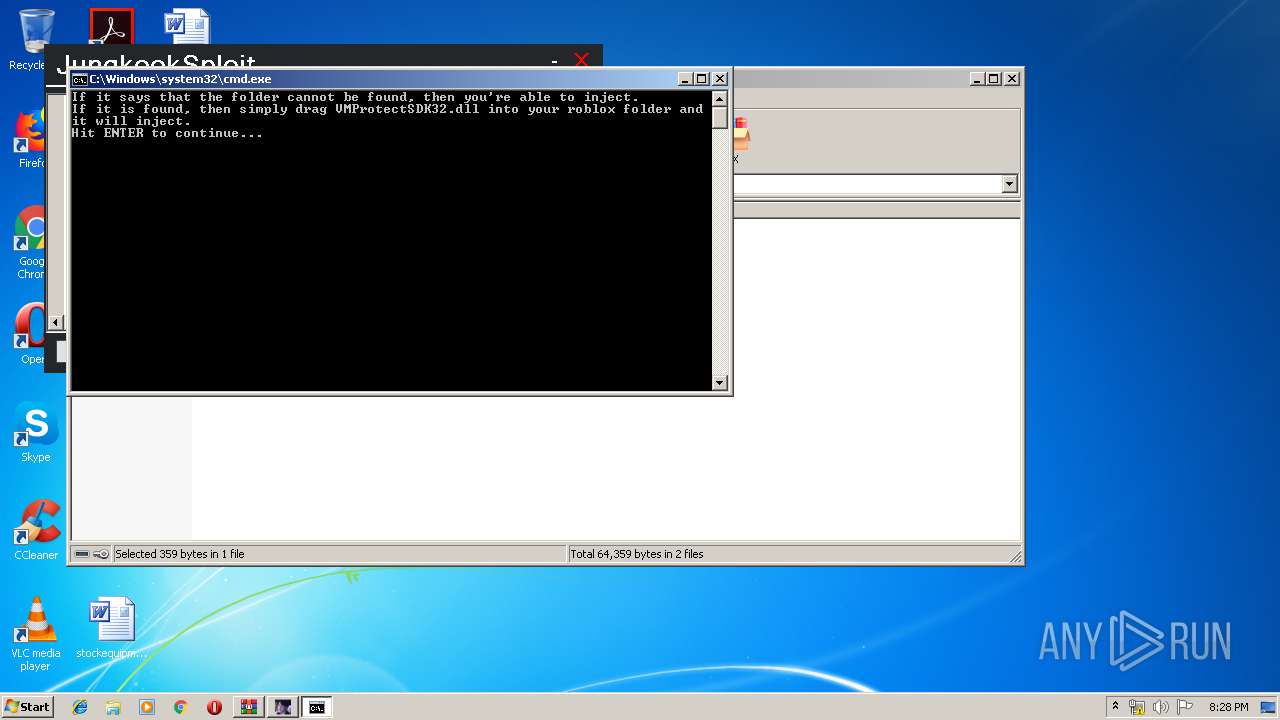
| File name: | JungkookSploit.rar |
| Full analysis: | https://app.any.run/tasks/235ccf4b-b046-459a-a67f-a4aa89f6b4f7 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 19:27:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 0B7318106D3663809140E8139AC8A8C6 |
| SHA1: | 08A7518BC23BEAFBAD67B522D7EC6C566245EEFF |
| SHA256: | D4A7017B105791A9C0D52A684F9FCB0FD21C4750B689F9D6B072182DE1058EDB |
| SSDEEP: | 49152:A50qg9p8lzK9Du2NplBaA2HBsw+e1FX9ZbX29JU+SDj756HNU5j9:AzgsFK9a2H3aA2HBsw+erXa9JU+SbCWZ |
MALICIOUS
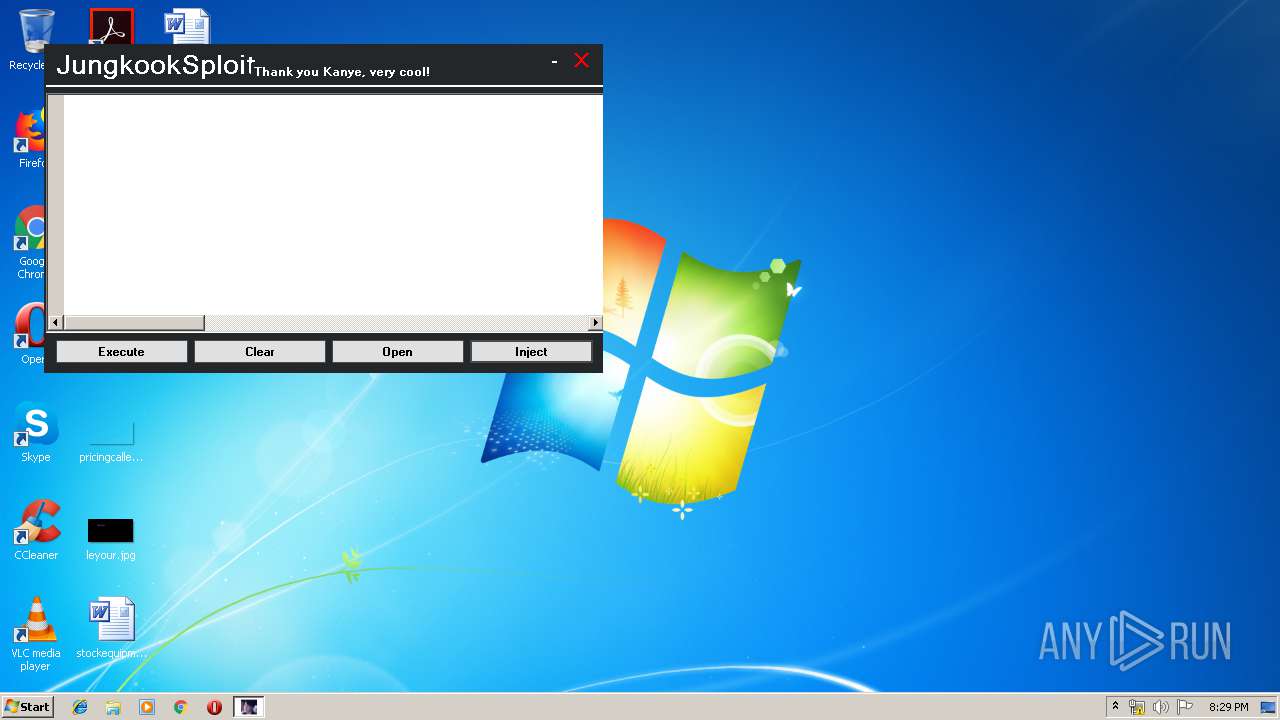
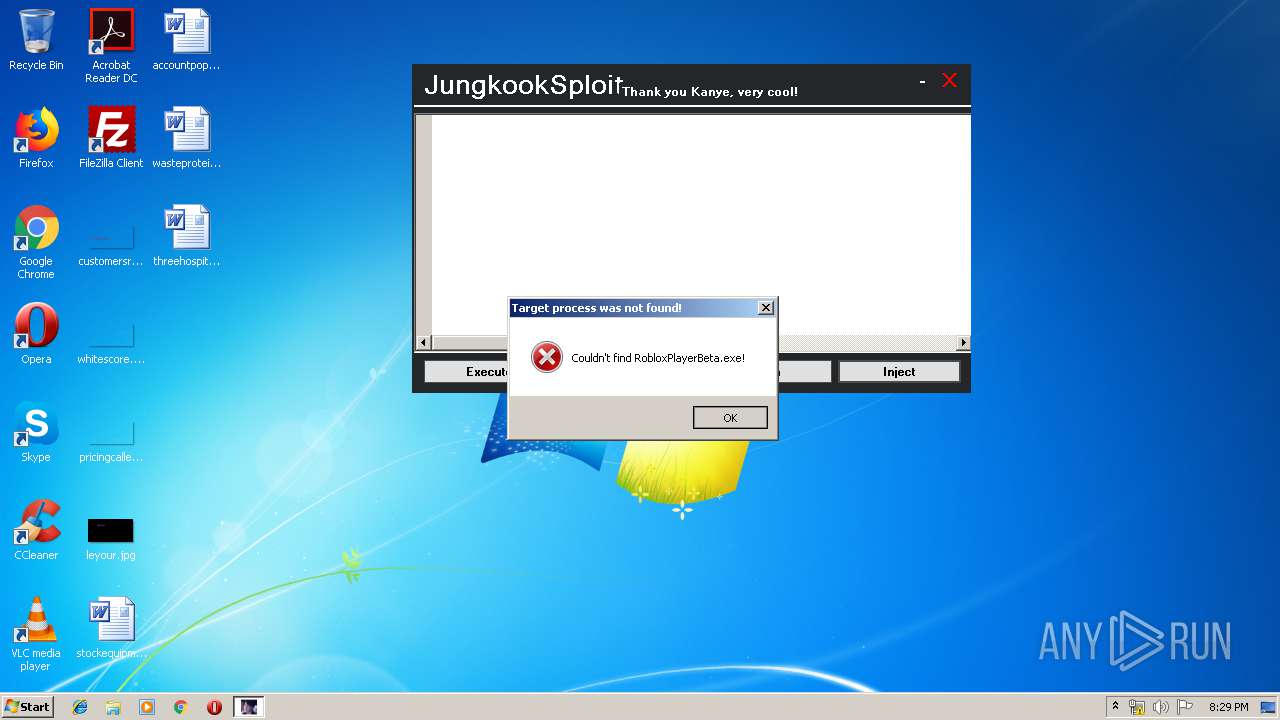
Application was dropped or rewritten from another process
- JungkookSploit.exe (PID: 1640)
Loads dropped or rewritten executable
- JungkookSploit.exe (PID: 1640)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3040)
- JungkookSploit.exe (PID: 1640)
Executed via COM
- explorer.exe (PID: 2660)
- explorer.exe (PID: 3600)
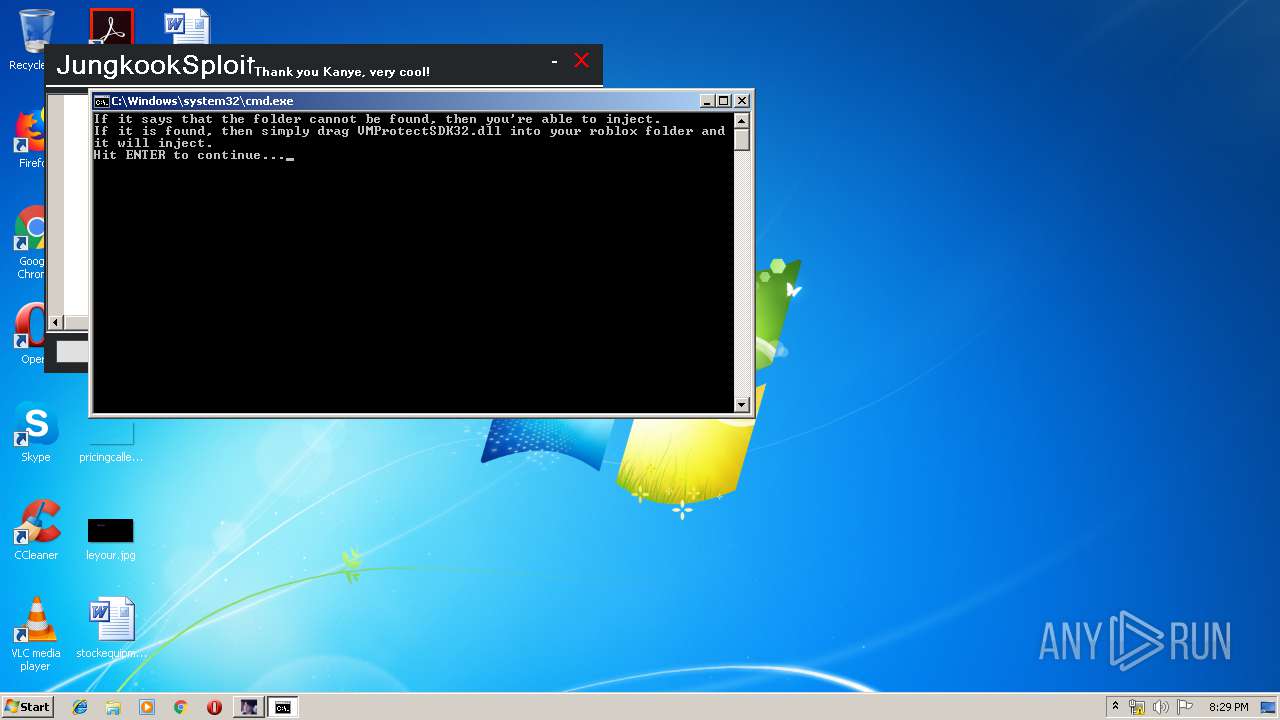
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3040)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
41
Monitored processes
8
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1640 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\JungkookSploit.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\JungkookSploit.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AxonSimpleUI Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2660 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
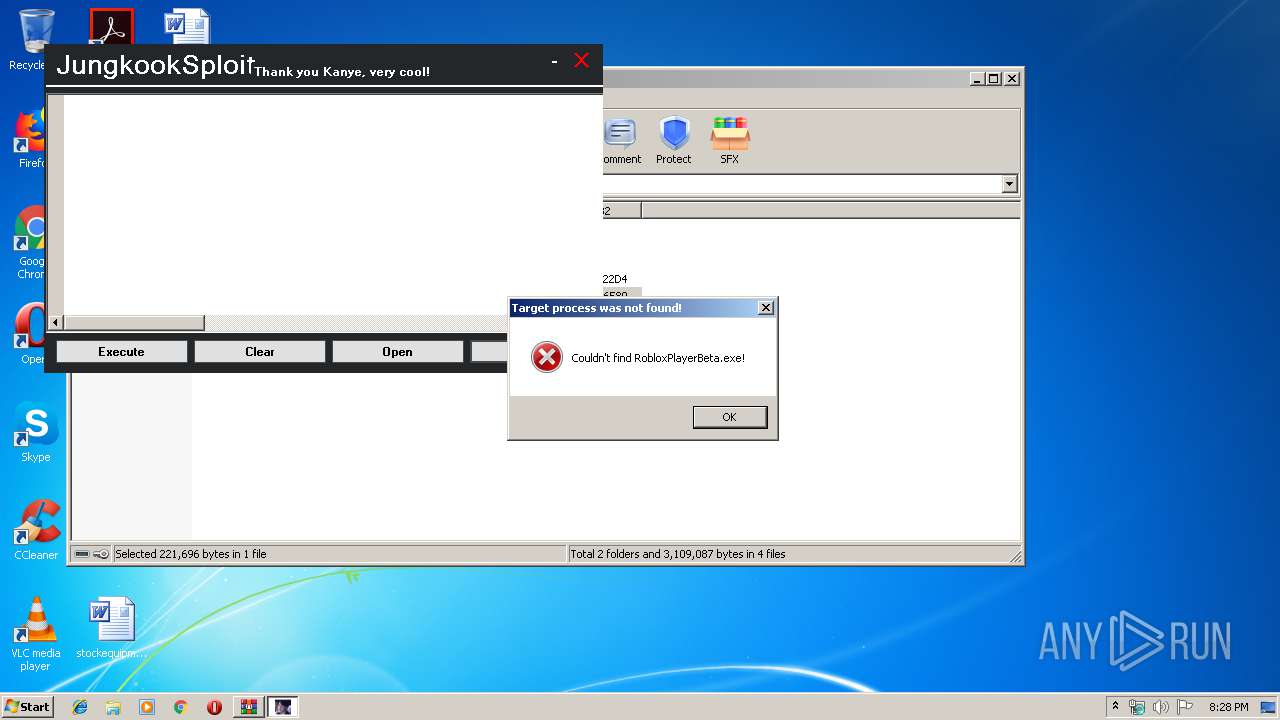
| 2812 | explorer C:\Users\admin\AppData\Local\Roblox\Versions\version-8ea9490e0ca04991 | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3040 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\JungkookSploit.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3088 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3040.31693\open roblox folder - u dont need to add this.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3600 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3804 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DIa3040.33979\open roblox folder - u dont need to add this.bat" " | C:\Windows\system32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3880 | explorer C:\Users\admin\AppData\Local\Roblox\Versions\version-8ea9490e0ca04991 | C:\Windows\explorer.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 738
Read events
1 591
Write events
147
Delete events
0
Modification events
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\JungkookSploit.rar | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
5
Suspicious files
0
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\Workspace\autoexe\init.lua | text | |
MD5:— | SHA256:— | |||
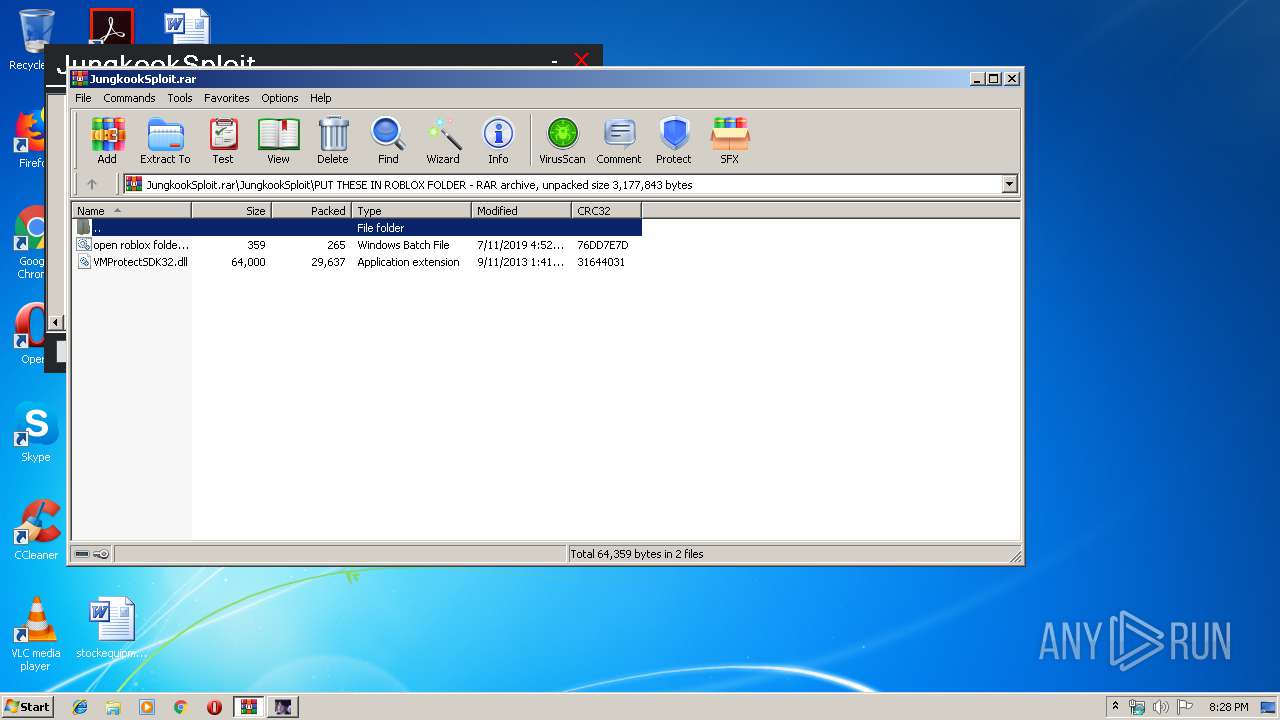
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3040.33979\open roblox folder - u dont need to add this.bat | text | |
MD5:— | SHA256:— | |||
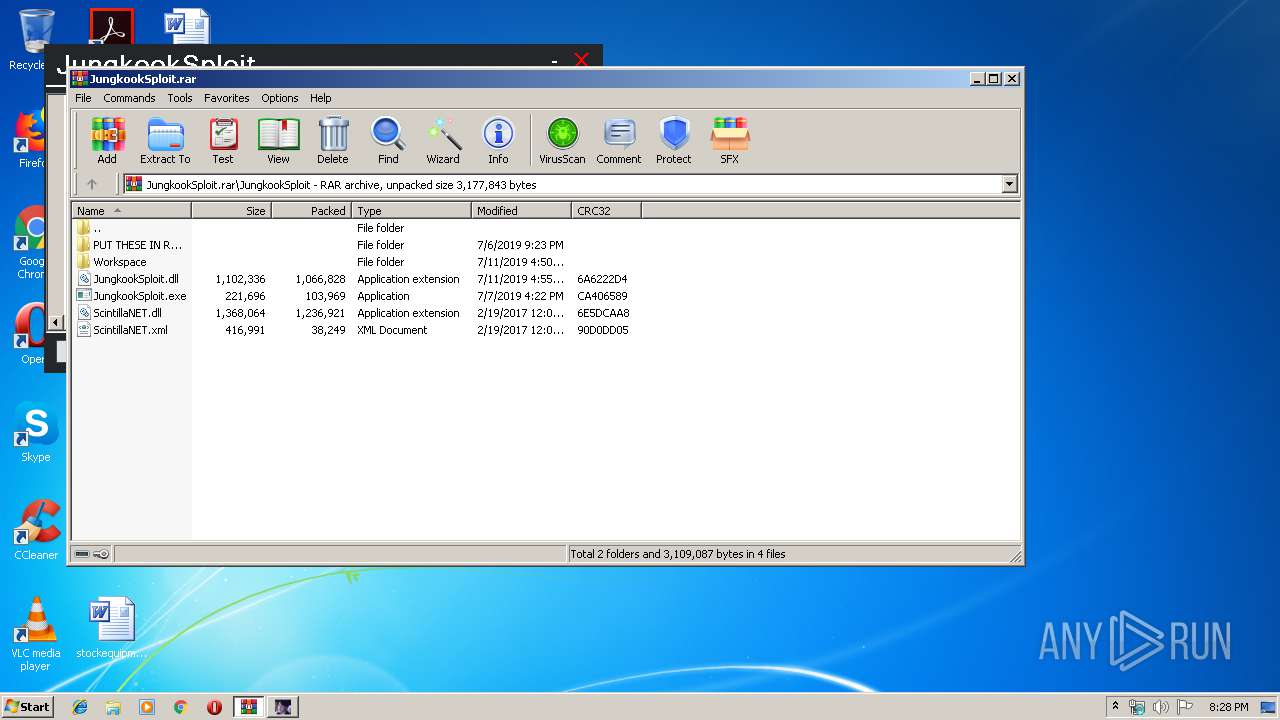
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\JungkookSploit.exe | executable | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\JungkookSploit.dll | executable | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\ScintillaNET.dll | executable | |
MD5:9166536C31F4E725E6BEFE85E2889A4B | SHA256:AD0CC5A4D4A6AAE06EE360339C851892B74B8A275CE89C1B48185672179F3163 | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\PUT THESE IN ROBLOX FOLDER\open roblox folder - u dont need to add this.bat | text | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3040.31693\open roblox folder - u dont need to add this.bat | text | |
MD5:— | SHA256:— | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\PUT THESE IN ROBLOX FOLDER\VMProtectSDK32.dll | executable | |
MD5:1E6FDCD6D847BBF9CD3A37BA72CDA3F7 | SHA256:06754CB39C2E814577AC287B7DD0083F59933C867038407CDDFB22EBC6C0F193 | |||
| 3040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3040.30471\JungkookSploit\ScintillaNET.xml | xml | |
MD5:E200C312A4C43F78021A9CFD75B0B9D2 | SHA256:D40A05B1D45B13C7AD7395024743E68667A340D488CD9ACD71BC4824D6944538 | |||
| 1640 | JungkookSploit.exe | C:\Users\admin\AppData\Local\Temp\ScintillaNET\3.6.3\x86\SciLexer.dll | executable | |
MD5:2FF7ACFA80647EE46CC3C0E446327108 | SHA256:08F0CBBC5162F236C37166772BE2C9B8FFD465D32DF17EA9D45626C4ED2C911D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report