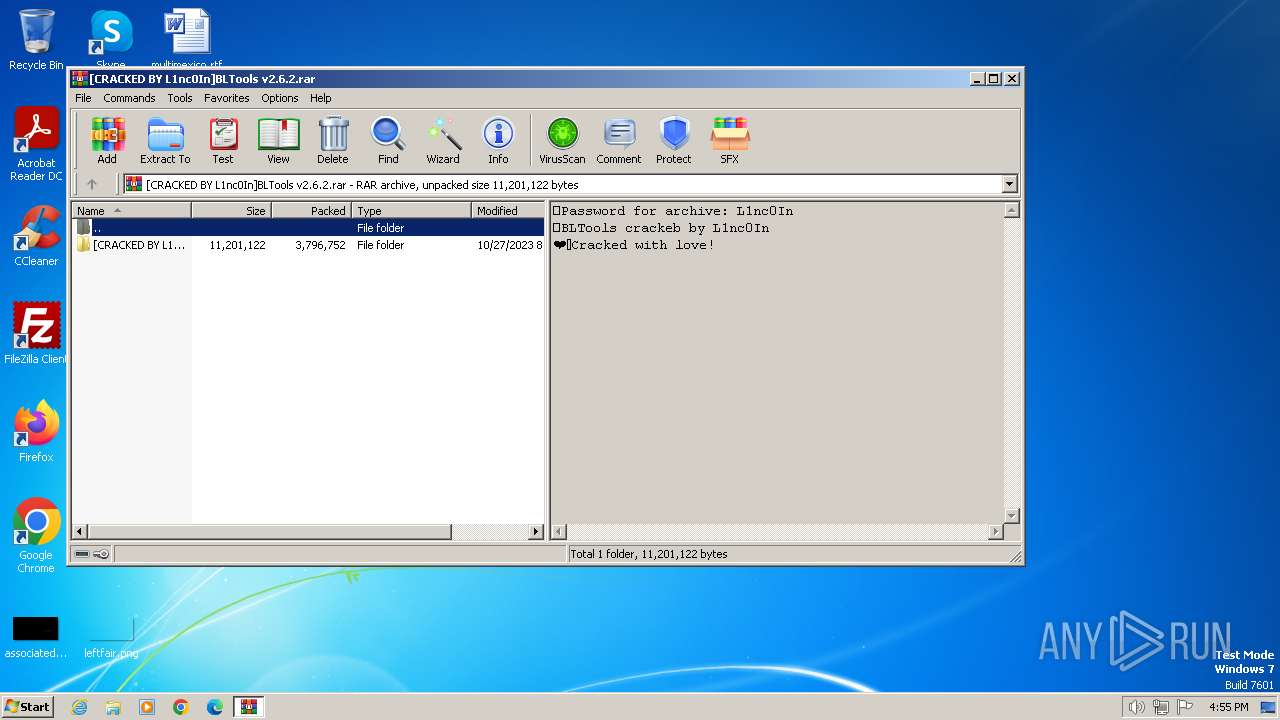
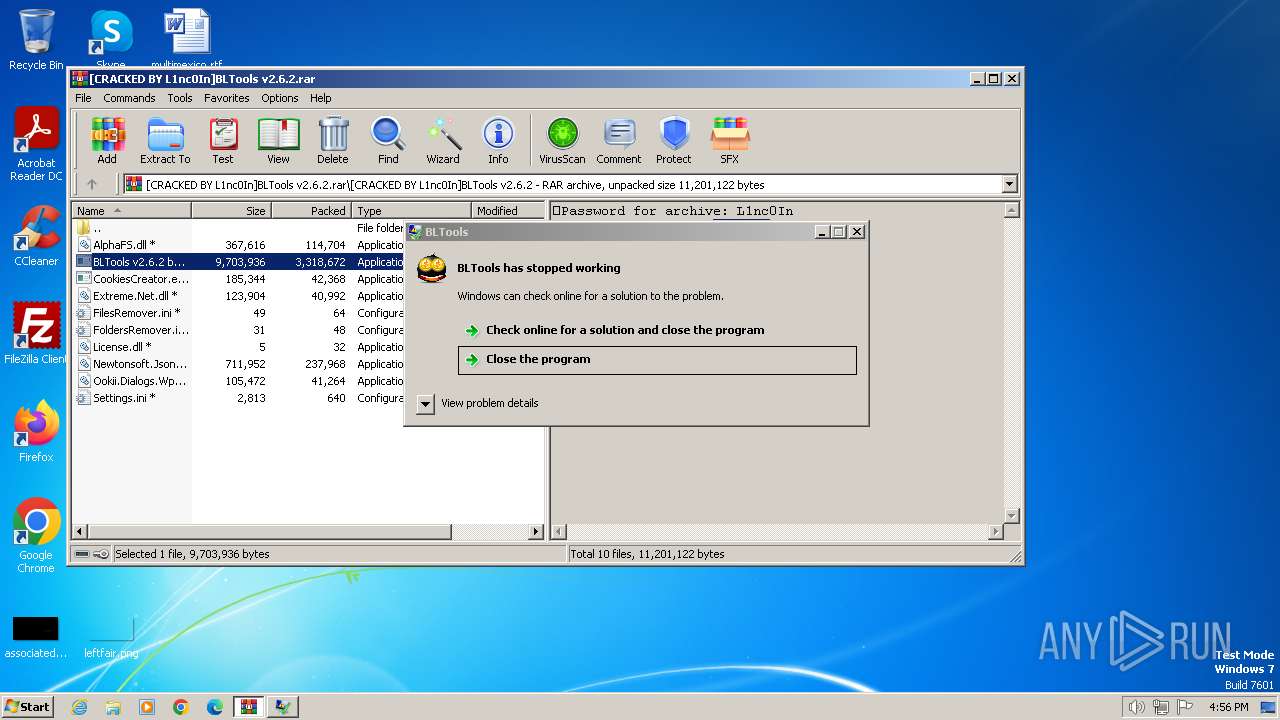
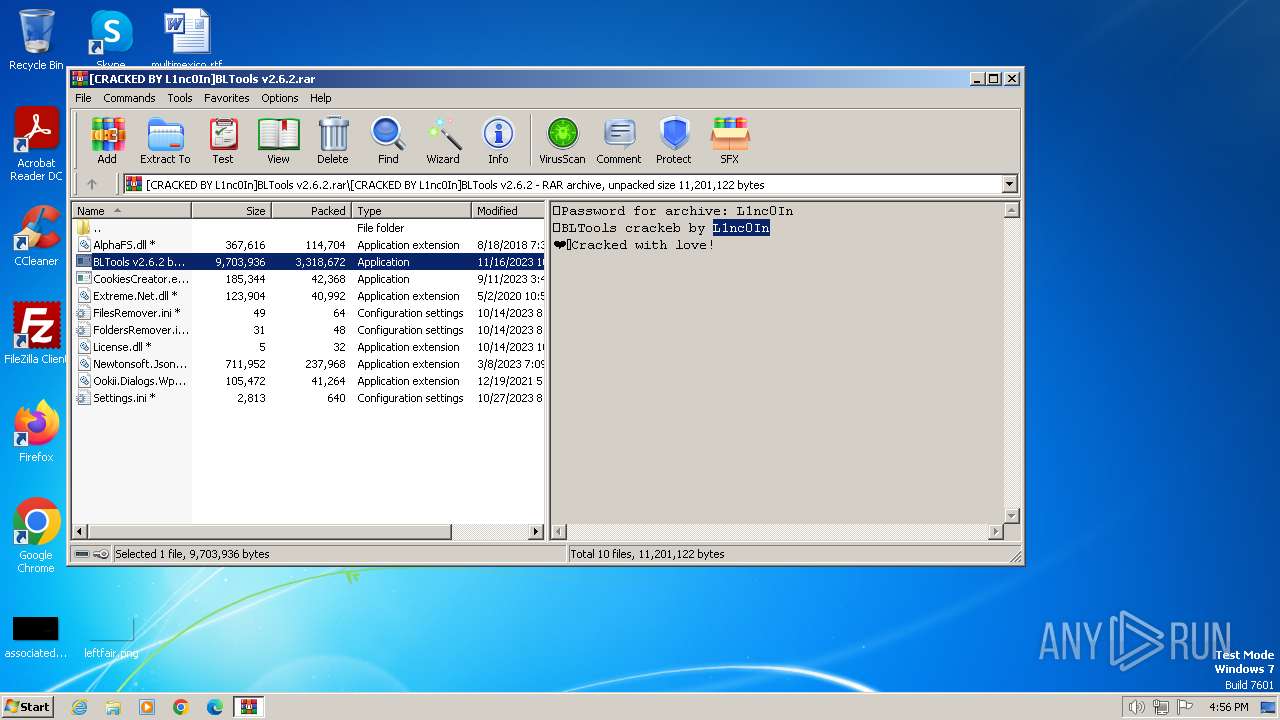
| File name: | [CRACKED BY L1nc0In]BLTools v2.6.2.rar |
| Full analysis: | https://app.any.run/tasks/1365b040-e260-450d-b556-ccc5d089a5a9 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | April 07, 2024, 15:55:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 36990D5928E917D875C9FF63C6704836 |
| SHA1: | CA0DD62162273BA109040AD4B32E34ED8F6E94DC |
| SHA256: | D4979FB42C5CEDD4E6787166510BE44ADE799FBADAE1805C9520B70821A677D9 |
| SSDEEP: | 98304:1CAN25uP+N6tQQ+wMVOqiCH6K8Cp5v0GyYPCYHKSed/6qZ+JBLogG5jZkN8W5Ho/:XTmuQAg6 |
MALICIOUS
Drops the executable file immediately after the start
- DCRatBuild.exe (PID: 2184)
- BLTools v2.6.2 by L1nc0In.exe (PID: 3964)
- Websaves.exe (PID: 1576)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 3068)
UAC/LUA settings modification
- Websaves.exe (PID: 1576)
Adds path to the Windows Defender exclusion list
- Websaves.exe (PID: 1576)
DCRAT has been detected (YARA)
- Websaves.exe (PID: 1576)
SUSPICIOUS
Reads security settings of Internet Explorer
- DCRatBuild.exe (PID: 2184)
- BLTools v2.6.2 by L1nc0In.exe (PID: 3964)
- WinRAR.exe (PID: 4008)
- Websaves.exe (PID: 1576)
Reads the Internet Settings
- DCRatBuild.exe (PID: 2184)
- BLTools v2.6.2 by L1nc0In.exe (PID: 3964)
- wscript.exe (PID: 3068)
- powershell.exe (PID: 4072)
- powershell.exe (PID: 4084)
- Websaves.exe (PID: 1576)
- powershell.exe (PID: 572)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 3792)
- powershell.exe (PID: 1820)
- powershell.exe (PID: 1504)
- powershell.exe (PID: 1172)
- powershell.exe (PID: 584)
- powershell.exe (PID: 1424)
- powershell.exe (PID: 3492)
- powershell.exe (PID: 1604)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 3068)
- Websaves.exe (PID: 1576)
Executing commands from a ".bat" file
- wscript.exe (PID: 3068)
- Websaves.exe (PID: 1576)
Executed via WMI
- schtasks.exe (PID: 3544)
- schtasks.exe (PID: 3404)
- schtasks.exe (PID: 2336)
- schtasks.exe (PID: 3224)
- schtasks.exe (PID: 3496)
- schtasks.exe (PID: 3616)
- schtasks.exe (PID: 2468)
- schtasks.exe (PID: 1484)
- schtasks.exe (PID: 3444)
- schtasks.exe (PID: 1780)
- schtasks.exe (PID: 1608)
- schtasks.exe (PID: 2112)
- schtasks.exe (PID: 3980)
- schtasks.exe (PID: 2096)
- schtasks.exe (PID: 712)
- schtasks.exe (PID: 3984)
- schtasks.exe (PID: 3088)
- schtasks.exe (PID: 316)
- schtasks.exe (PID: 3036)
- schtasks.exe (PID: 2480)
- schtasks.exe (PID: 1020)
- schtasks.exe (PID: 2584)
- schtasks.exe (PID: 2308)
- schtasks.exe (PID: 2344)
- schtasks.exe (PID: 3172)
- schtasks.exe (PID: 3232)
- schtasks.exe (PID: 3336)
- schtasks.exe (PID: 2984)
- schtasks.exe (PID: 3100)
- schtasks.exe (PID: 3352)
- schtasks.exe (PID: 2024)
- schtasks.exe (PID: 3620)
- schtasks.exe (PID: 1796)
- schtasks.exe (PID: 1936)
- schtasks.exe (PID: 2808)
- schtasks.exe (PID: 984)
The process creates files with name similar to system file names
- Websaves.exe (PID: 1576)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3068)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 2764)
Using PowerShell to operate with local accounts
- powershell.exe (PID: 572)
- powershell.exe (PID: 4072)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 1172)
- powershell.exe (PID: 3792)
- powershell.exe (PID: 1820)
- powershell.exe (PID: 1504)
- powershell.exe (PID: 584)
- powershell.exe (PID: 1424)
- powershell.exe (PID: 3492)
- powershell.exe (PID: 1604)
Script adds exclusion path to Windows Defender
- Websaves.exe (PID: 1576)
Starts POWERSHELL.EXE for commands execution
- Websaves.exe (PID: 1576)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4008)
Checks supported languages
- BLTools v2.6.2 by L1nc0In.exe (PID: 1928)
- BLTools v2.6.2 by L1nc0In.exe (PID: 3964)
- DCRatBuild.exe (PID: 2184)
- Websaves.exe (PID: 1576)
- SearchProtocolHost.exe (PID: 1380)
Reads the computer name
- BLTools v2.6.2 by L1nc0In.exe (PID: 1928)
- BLTools v2.6.2 by L1nc0In.exe (PID: 3964)
- DCRatBuild.exe (PID: 2184)
- Websaves.exe (PID: 1576)
- SearchProtocolHost.exe (PID: 1380)
Create files in a temporary directory
- BLTools v2.6.2 by L1nc0In.exe (PID: 3964)
- Websaves.exe (PID: 1576)
Reads the machine GUID from the registry
- BLTools v2.6.2 by L1nc0In.exe (PID: 1928)
- Websaves.exe (PID: 1576)
- SearchProtocolHost.exe (PID: 1380)
Reads Environment values
- Websaves.exe (PID: 1576)
- SearchProtocolHost.exe (PID: 1380)
Reads product name
- Websaves.exe (PID: 1576)
- SearchProtocolHost.exe (PID: 1380)
Process checks whether UAC notifications are on
- Websaves.exe (PID: 1576)
Creates files in the program directory
- Websaves.exe (PID: 1576)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4084)
- powershell.exe (PID: 1820)
- powershell.exe (PID: 572)
- powershell.exe (PID: 1504)
- powershell.exe (PID: 1172)
- powershell.exe (PID: 4072)
- powershell.exe (PID: 2492)
- powershell.exe (PID: 3792)
- powershell.exe (PID: 584)
- powershell.exe (PID: 1424)
- powershell.exe (PID: 3492)
- powershell.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
115
Monitored processes
60
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\BLTools v2.6.2 by L1nc0In.exe" | C:\Users\admin\AppData\Local\Temp\BLTools v2.6.2 by L1nc0In.exe | — | BLTools v2.6.2 by L1nc0In.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: BLTools Exit code: 3221226540 Version: 2.6.2.0 Modules
| |||||||||||||||
| 316 | schtasks.exe /create /tn "SearchProtocolHostS" /sc MINUTE /mo 7 /tr "'C:\ComagentServerCommon\SearchProtocolHost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 572 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/MSOCache/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Websaves.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 584 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/Program Files/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Websaves.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 712 | schtasks.exe /create /tn "taskhost" /sc ONLOGON /tr "'C:\ComagentServerCommon\taskhost.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | "C:\Users\admin\AppData\Local\Temp\DCRatBuild.exe" | C:\Users\admin\AppData\Local\Temp\DCRatBuild.exe | — | BLTools v2.6.2 by L1nc0In.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 984 | schtasks.exe /create /tn "dwmd" /sc MINUTE /mo 11 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\dwm.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | schtasks.exe /create /tn "msiexecm" /sc MINUTE /mo 12 /tr "'C:\Program Files\Opera\msiexec.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1172 | "powershell" -Command Add-MpPreference -ExclusionPath 'C:/ProgramData/' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | Websaves.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1380 | "C:\ComagentServerCommon\SearchProtocolHost.exe" | C:\ComagentServerCommon\SearchProtocolHost.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 5.15.2.0 Modules
| |||||||||||||||
Total events
35 958
Read events
35 805
Write events
153
Delete events
0
Modification events
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[CRACKED BY L1nc0In]BLTools v2.6.2.rar | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4008) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
21
Suspicious files
2
Text files
19
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
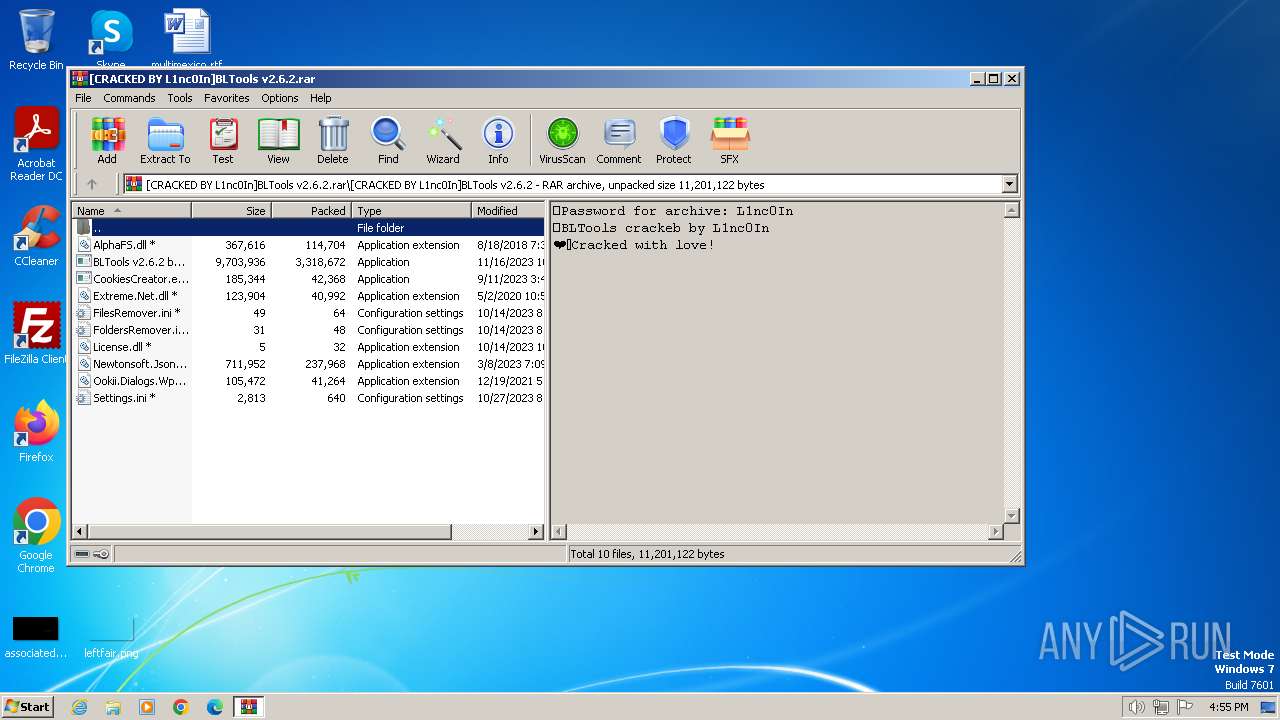
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\AlphaFS.dll | executable | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\BLTools v2.6.2 by L1nc0In.exe | executable | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\CookiesCreator.exe | executable | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\Extreme.Net.dll | executable | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\FilesRemover.ini | text | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\FoldersRemover.ini | text | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\License.dll | text | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\Newtonsoft.Json.dll | executable | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\Ookii.Dialogs.Wpf.dll | executable | |
MD5:— | SHA256:— | |||
| 4008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb4008.34025\[CRACKED BY L1nc0In]BLTools v2.6.2\Settings.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |