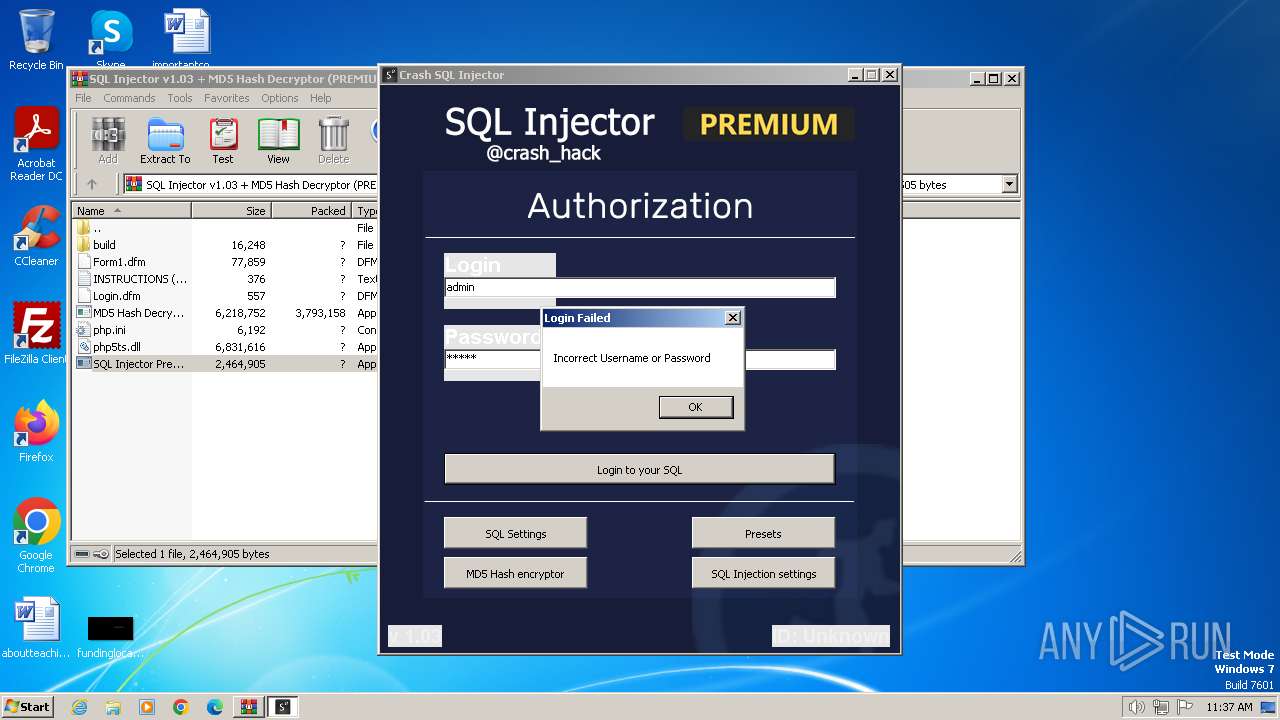
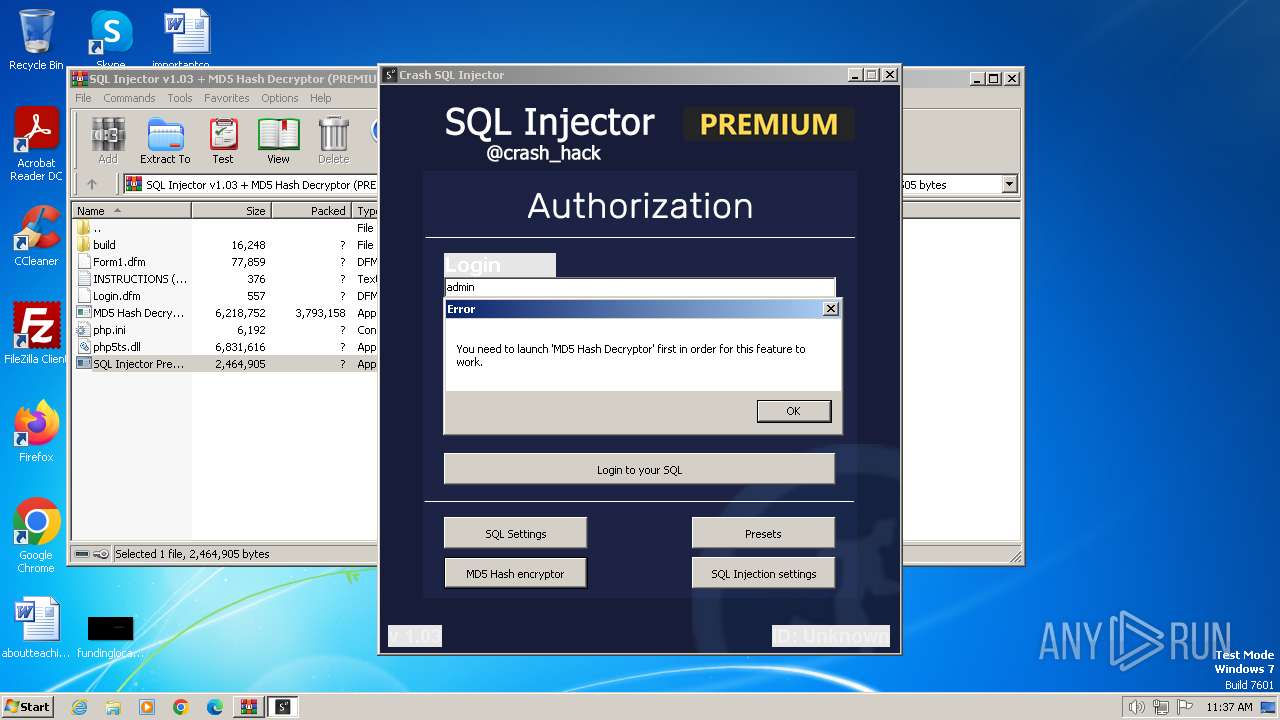
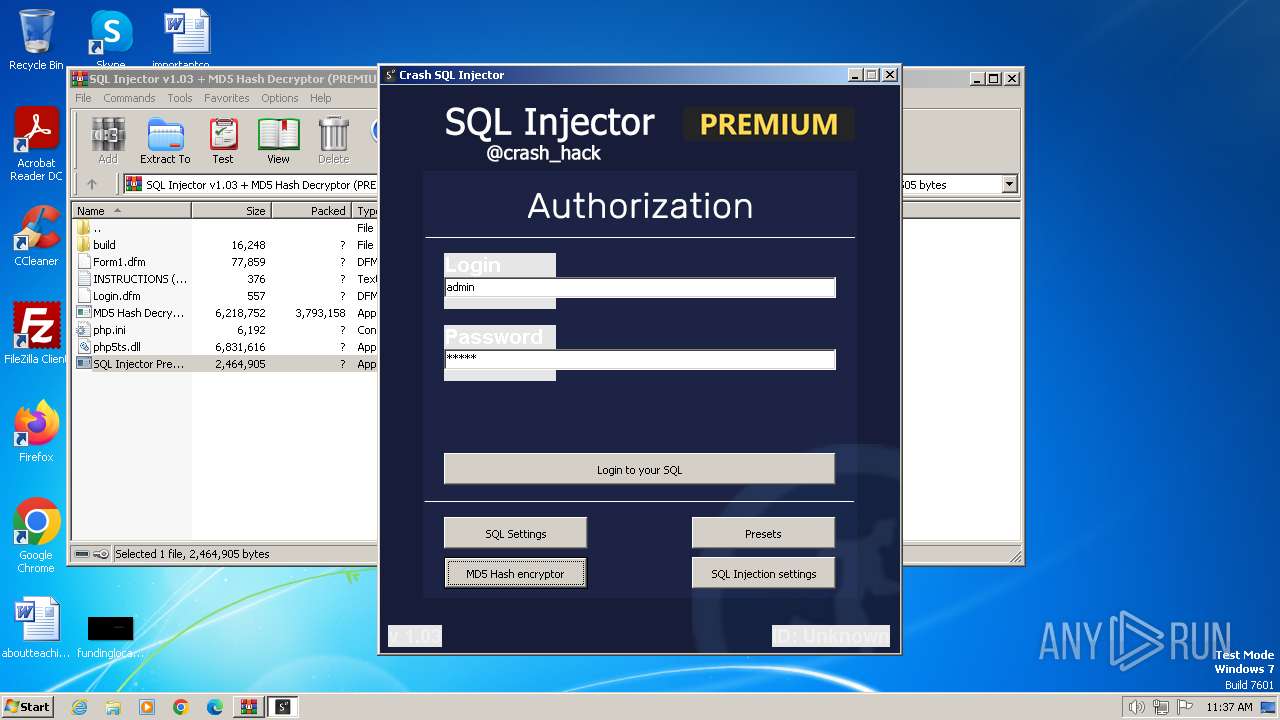
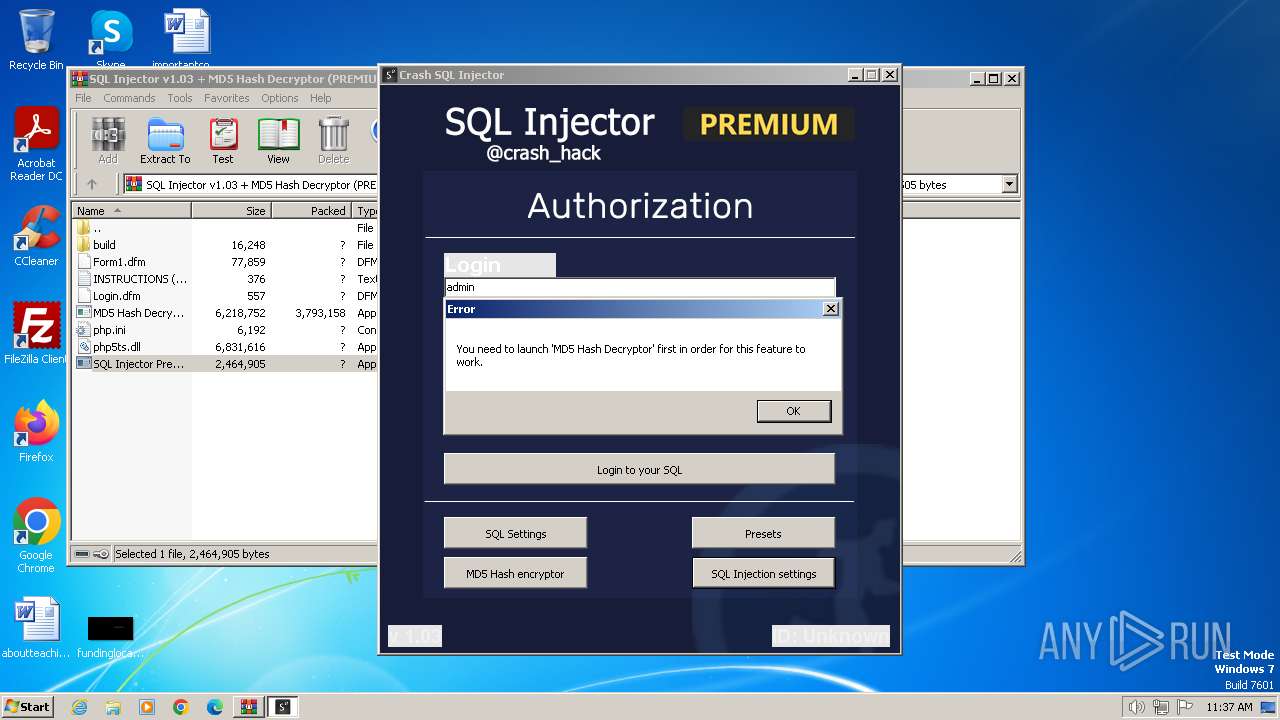
| File name: | SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM).7z |
| Full analysis: | https://app.any.run/tasks/ad117eef-cd5d-410b-9f5b-7719994cdf98 |
| Verdict: | Malicious activity |
| Analysis date: | March 30, 2024, 11:37:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 60492AD4233F7F1FFE92D84F8FB7F42B |
| SHA1: | 13F66996505062FC343D21843FC2A382728D8365 |
| SHA256: | D46CA596437C9D1378EE83E00C8E923591AA03CD611CB6150B07B08413570607 |
| SSDEEP: | 98304:rBbJqZjoY0tv3EuKORyduS5fqJPfMZomIXaaKg0CviM:rBlq8F3/KAydVjZUXa5gF/ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2120)
- MD5 Hash Decryptor.exe (PID: 2960)
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Adds path to the Windows Defender exclusion list
- MD5 Hash Decryptor.exe (PID: 2960)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2120)
- MD5 Hash Decryptor.exe (PID: 2960)
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Starts CMD.EXE for commands execution
- MD5 Hash Decryptor.exe (PID: 2960)
- w36y2M0QX7.exe (PID: 748)
Reads the Internet Settings
- MD5 Hash Decryptor.exe (PID: 2960)
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Executed via WMI
- schtasks.exe (PID: 2724)
- schtasks.exe (PID: 2744)
- schtasks.exe (PID: 1308)
- schtasks.exe (PID: 1844)
- schtasks.exe (PID: 2788)
- schtasks.exe (PID: 3324)
- schtasks.exe (PID: 2240)
- schtasks.exe (PID: 1848)
- schtasks.exe (PID: 880)
- schtasks.exe (PID: 680)
- schtasks.exe (PID: 1772)
- schtasks.exe (PID: 568)
- schtasks.exe (PID: 3556)
- schtasks.exe (PID: 2568)
- schtasks.exe (PID: 1404)
- schtasks.exe (PID: 316)
- schtasks.exe (PID: 2020)
- schtasks.exe (PID: 2348)
- schtasks.exe (PID: 2588)
- schtasks.exe (PID: 2640)
- schtasks.exe (PID: 984)
- schtasks.exe (PID: 552)
- schtasks.exe (PID: 1780)
- schtasks.exe (PID: 3520)
- schtasks.exe (PID: 1216)
- schtasks.exe (PID: 1592)
- schtasks.exe (PID: 3172)
- schtasks.exe (PID: 2584)
- schtasks.exe (PID: 1036)
- schtasks.exe (PID: 3260)
Probably delay the execution using 'w32tm.exe'
- cmd.exe (PID: 3028)
The executable file from the user directory is run by the CMD process
- w36y2M0QX7.exe (PID: 1792)
The process creates files with name similar to system file names
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
Executing commands from a ".bat" file
- w36y2M0QX7.exe (PID: 748)
Starts itself from another location
- w36y2M0QX7.exe (PID: 1792)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1172)
- wscript.exe (PID: 4092)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 1172)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 4092)
The process executes VB scripts
- cmd.exe (PID: 2984)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 4092)
INFO
Checks supported languages
- SQL Injector Premium v1.03.exe (PID: 3092)
- MD5 Hash Decryptor.exe (PID: 2960)
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Reads the computer name
- SQL Injector Premium v1.03.exe (PID: 3092)
- MD5 Hash Decryptor.exe (PID: 2960)
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Create files in a temporary directory
- SQL Injector Premium v1.03.exe (PID: 3092)
- w36y2M0QX7.exe (PID: 748)
- cmd.exe (PID: 2984)
Creates files or folders in the user directory
- MD5 Hash Decryptor.exe (PID: 2960)
Reads the machine GUID from the registry
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Reads Environment values
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Reads product name
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
- cmd.exe (PID: 2984)
Creates files in the program directory
- w36y2M0QX7.exe (PID: 748)
- w36y2M0QX7.exe (PID: 1792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
85
Monitored processes
43
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 316 | schtasks.exe /create /tn "winlogonw" /sc MINUTE /mo 11 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\winlogon.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | schtasks.exe /create /tn "msiexecm" /sc MINUTE /mo 5 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\msiexec.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 568 | schtasks.exe /create /tn "System" /sc ONLOGON /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\System.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 680 | schtasks.exe /create /tn "taskengt" /sc MINUTE /mo 13 /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\taskeng.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | "C:\Users\admin\AppData\Roaming\w36y2M0QX7.exe" | C:\Users\admin\AppData\Roaming\w36y2M0QX7.exe | — | MD5 Hash Decryptor.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Version: 1.1.1o Modules
| |||||||||||||||
| 880 | schtasks.exe /create /tn "taskeng" /sc ONLOGON /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\taskeng.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 984 | schtasks.exe /create /tn "msiexec" /sc ONLOGON /tr "'C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\msiexec.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | schtasks.exe /create /tn "cmdc" /sc MINUTE /mo 5 /tr "'C:\Program Files\Microsoft Visual Studio 8\VSTA\Bin\cmd.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1172 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\5376564a-736e-44c8-87b5-44b8826fe073.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1216 | schtasks.exe /create /tn "cmd" /sc ONLOGON /tr "'C:\Program Files\Microsoft Visual Studio 8\VSTA\Bin\cmd.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 282
Read events
16 200
Write events
82
Delete events
0
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM).7z | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
21
Suspicious files
0
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\build\build.cfg | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\build\form1.button1.OnMouseDown.php | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\build\form1.button3.OnClick.php | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\build\form1.timer1.OnTimer.php | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\build\icon.ico | image | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\build\sql.button1.OnClick.php | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\Form1.dfm | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\INSTRUCTIONS (HOW TO LAUNCH).txt | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\Login.dfm | text | |
MD5:— | SHA256:— | |||
| 2120 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2120.13974\SQL Injector v1.03 + MD5 Hash Decryptor (PREMIUM)\php.ini | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |