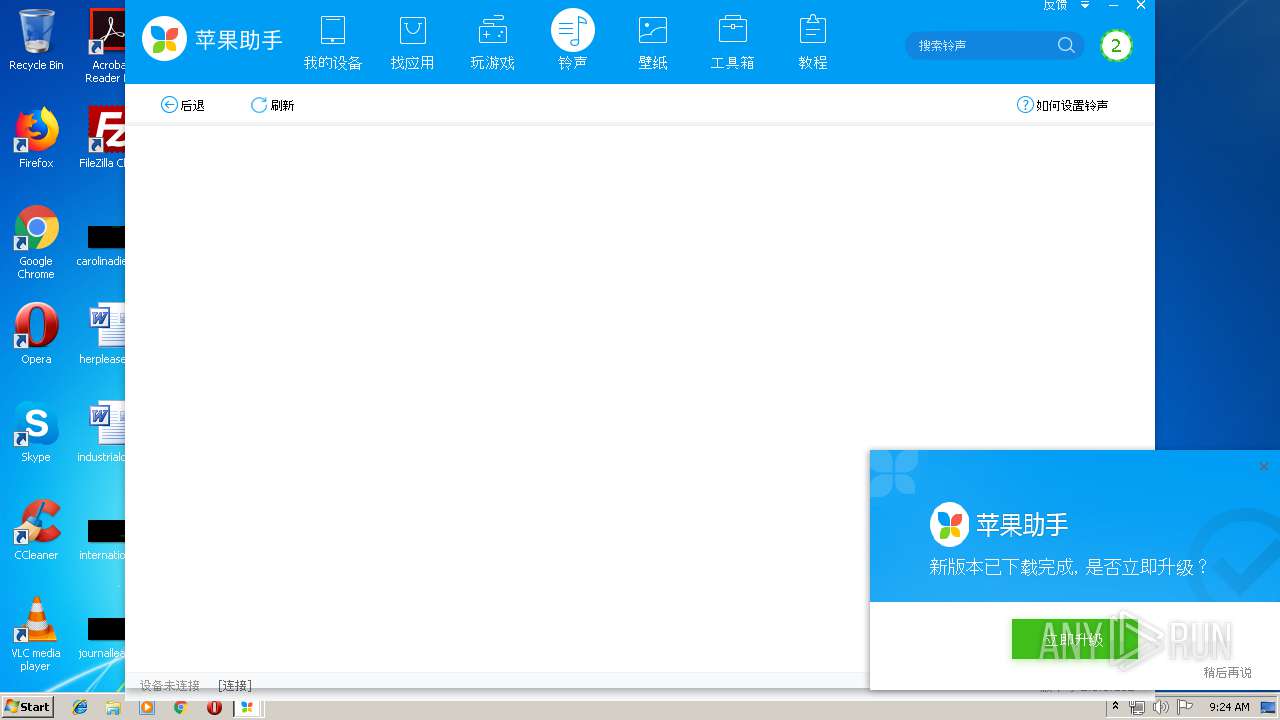
| download: | pgzs_pc_11_0612.exe |
| Full analysis: | https://app.any.run/tasks/5f697f29-3223-4f17-9448-ba73b376853e |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2019, 08:20:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D20EA130B454771F8D4EE700630076BE |
| SHA1: | BAC08138C90FE6EC3625C604A6671674AF9499C7 |
| SHA256: | D45FC0597EC77A1EC5454B1BE41974D7FD588DEDBAB371C6EA5374A11A572CA2 |
| SSDEEP: | 393216:jCeiJJXVwurDwAPWRc2nzr3gL89xWIRA3MKNhddVRXxR+2cm4KD5ewwZff:+roab2nHgL8FRjKNHRXxo2cSkwSf |
MALICIOUS
Application was dropped or rewritten from another process
- SetupFsdu.exe (PID: 2392)
- SetupFsdu.exe (PID: 1140)
- SetupFsdu.exe (PID: 252)
- SetupFsdu.exe (PID: 2100)
- nsA175.tmp (PID: 1696)
- nsA5CD.tmp (PID: 3468)
- nsA406.tmp (PID: 620)
- SetupFsdu.exe (PID: 1704)
- nsA7F0.tmp (PID: 2152)
- nsAA14.tmp (PID: 2092)
- nsAC38.tmp (PID: 3100)
- SetupFsdu.exe (PID: 636)
- AppleAssistDeviceService.exe (PID: 1652)
- AppleAssistDeviceService.exe (PID: 3204)
- UACHelper.exe (PID: 2872)
- AppleAssist.exe (PID: 3284)
- update.exe (PID: 2500)
- AppleAssistProxy.exe (PID: 2280)
- AppleAssist.exe (PID: 2952)
- ServerStatistics.exe (PID: 3680)
Loads dropped or rewritten executable
- SetupFsdu.exe (PID: 2392)
- SetupFsdu.exe (PID: 1140)
- pgzs_pc_11_0612.exe (PID: 2568)
- SetupFsdu.exe (PID: 2100)
- SetupFsdu.exe (PID: 252)
- SetupFsdu.exe (PID: 636)
- SetupFsdu.exe (PID: 1704)
- AppleAssistDeviceService.exe (PID: 1652)
- AppleAssistDeviceService.exe (PID: 3204)
- AppleAssist.exe (PID: 3284)
- UACHelper.exe (PID: 2872)
- update.exe (PID: 2500)
- AppleAssist.exe (PID: 2952)
- ServerStatistics.exe (PID: 3680)
Changes the autorun value in the registry
- pgzs_pc_11_0612.exe (PID: 2568)
Adds new firewall rule via NETSH.EXE
- nsA175.tmp (PID: 1696)
- nsA406.tmp (PID: 620)
- nsA5CD.tmp (PID: 3468)
- nsA7F0.tmp (PID: 2152)
SUSPICIOUS
Changes IE settings (feature browser emulation)
- pgzs_pc_11_0612.exe (PID: 2568)
Creates a software uninstall entry
- pgzs_pc_11_0612.exe (PID: 2568)
Starts application with an unusual extension
- pgzs_pc_11_0612.exe (PID: 2568)
Uses NETSH.EXE for network configuration
- nsA175.tmp (PID: 1696)
- nsA406.tmp (PID: 620)
- nsAC38.tmp (PID: 3100)
- nsA5CD.tmp (PID: 3468)
- nsA7F0.tmp (PID: 2152)
- nsAA14.tmp (PID: 2092)
Modifies the open verb of a shell class
- pgzs_pc_11_0612.exe (PID: 2568)
- UACHelper.exe (PID: 2872)
- AppleAssist.exe (PID: 3284)
Executable content was dropped or overwritten
- pgzs_pc_11_0612.exe (PID: 2568)
- AppleAssistDeviceService.exe (PID: 1652)
Creates files in the user directory
- pgzs_pc_11_0612.exe (PID: 2568)
Executed as Windows Service
- AppleAssistDeviceService.exe (PID: 3204)
Creates files in the program directory
- pgzs_pc_11_0612.exe (PID: 2568)
Starts CMD.EXE for commands execution
- pgzs_pc_11_0612.exe (PID: 2568)
Creates files in the Windows directory
- AppleAssistDeviceService.exe (PID: 3204)
- AppleAssistDeviceService.exe (PID: 1652)
Creates files in the driver directory
- AppleAssistDeviceService.exe (PID: 1652)
Searches for installed software
- AppleAssistProxy.exe (PID: 2280)
- UACHelper.exe (PID: 2872)
Reads internet explorer settings
- AppleAssist.exe (PID: 3284)
INFO
Dropped object may contain Bitcoin addresses
- pgzs_pc_11_0612.exe (PID: 2568)
Manual execution by user
- AppleAssist.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 20:19:54+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 28160 |
| InitializedDataSize: | 445952 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x3883 |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.3.162 |
| ProductVersionNumber: | 2.0.3.162 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | 苹果助手 |
| FileDescription: | 苹果助手安装包 |
| FileVersion: | 2.0.3.162 |
| InternalName: | AppleAssist.exe |
| LegalCopyright: | 苹果助手 Copyright(c)2017 |
| ProductName: | 苹果助手 |
| ProductVersion: | 2.0.3.162 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 24-Feb-2012 19:19:54 |
| Detected languages: |
|
| CompanyName: | 苹果助手 |
| FileDescription: | 苹果助手安装包 |
| FileVersion: | 2.0.3.162 |
| InternalName: | AppleAssist.exe |
| LegalCopyright: | 苹果助手 Copyright(c)2017 |
| ProductName: | 苹果助手 |
| ProductVersion: | 2.0.3.162 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 24-Feb-2012 19:19:54 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006DAE | 0x00006E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.50853 |
.rdata | 0x00008000 | 0x00002A62 | 0x00002C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.39054 |
.data | 0x0000B000 | 0x00067EBC | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 1.43086 |
.ndata | 0x00073000 | 0x000D5000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00148000 | 0x000050D0 | 0x00005200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.55883 |
.reloc | 0x0014E000 | 0x00000F32 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.38873 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21712 | 968 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 4.67942 | 4264 | UNKNOWN | English - United States | RT_ICON |
3 | 4.5697 | 2440 | UNKNOWN | English - United States | RT_ICON |
4 | 5.05529 | 1128 | UNKNOWN | English - United States | RT_ICON |
103 | 2.62308 | 62 | UNKNOWN | English - United States | RT_GROUP_ICON |
105 | 2.68733 | 494 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.86626 | 228 | UNKNOWN | English - United States | RT_DIALOG |
111 | 2.9304 | 218 | UNKNOWN | English - United States | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
VERSION.dll |
ole32.dll |
Total processes
72
Monitored processes
29
Malicious processes
10
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe" -protocol=1 -category=安装流程 -action=开始普通安装 -label=自定义安装,点击下一步 -ver=2.0.3.162 -channelid=5f9or9MZAosCu0YX5qu2qQ== | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe | pgzs_pc_11_0612.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: HIGH Description: TODO: <文件说明> Exit code: 0 Version: 1.0.0.5 Modules
| |||||||||||||||
| 392 | netsh advfirewall firewall add rule name="苹果助手" dir=in program="C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\AppleAssist.exe" action=allow | C:\Windows\system32\netsh.exe | — | nsA175.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | "C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\nsA406.tmp" netsh advfirewall firewall add rule name="苹果助手代理程序" dir=in program="C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\AppleAssistProxy.exe" action=allow | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\nsA406.tmp | — | pgzs_pc_11_0612.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 636 | "C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe" -type=2 -ver=2.0.3.162 -channelid=5f9or9MZAosCu0YX5qu2qQ== | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe | pgzs_pc_11_0612.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: HIGH Description: TODO: <文件说明> Exit code: 0 Version: 1.0.0.5 Modules
| |||||||||||||||
| 712 | netsh advfirewall firewall add rule name="苹果助手代理程序" dir=in program="C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\AppleAssistProxy.exe" action=allow | C:\Windows\system32\netsh.exe | — | nsA406.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe" -type=1 -ver=2.0.3.162 -channelid=5f9or9MZAosCu0YX5qu2qQ== | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe | pgzs_pc_11_0612.exe | ||||||||||||
User: admin Company: TODO: <公司名> Integrity Level: HIGH Description: TODO: <文件说明> Exit code: 0 Version: 1.0.0.5 Modules
| |||||||||||||||
| 1360 | netsh advfirewall firewall add rule name="苹果助手连接" protocol=TCP dir=in localport=5037 action=allow | C:\Windows\system32\netsh.exe | — | nsAA14.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1388 | netsh advfirewall firewall add rule name="苹果助手IDCM32" dir=in program="C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\IDCM32.exe" action=allow | C:\Windows\system32\netsh.exe | — | nsA5CD.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1652 | "C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\AppleAssistDeviceService.exe" -r | C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\AppleAssistDeviceService.exe | pgzs_pc_11_0612.exe | ||||||||||||
User: admin Company: 福建智度科技有限公司 Integrity Level: HIGH Description: 苹果助手设备服务程序 Exit code: 0 Version: 1, 3, 2, 9 Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\nsA175.tmp" netsh advfirewall firewall add rule name="苹果助手" dir=in program="C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\AppleAssist.exe" action=allow | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\nsA175.tmp | — | pgzs_pc_11_0612.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 427
Read events
718
Write events
709
Delete events
0
Modification events
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2392) SetupFsdu.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SetupFsdu_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
124
Suspicious files
62
Text files
124
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2568 | pgzs_pc_11_0612.exe | C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\app.7z | — | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\Tqwavlib.dll | text | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\logo.ico | image | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\logo.ico | image | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\SetupFsdu.exe | executable | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\Tqwavlib.dll | text | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\System.dll | executable | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\skin.zip | compressed | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Users\admin\AppData\Local\Temp\nsf70FE.tmp\BgWorker.dll | executable | |
MD5:— | SHA256:— | |||
| 2568 | pgzs_pc_11_0612.exe | C:\Program Files\91 Wireless\AppleAssist\2.0.3.162\config.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
124
TCP/UDP connections
65
DNS requests
19
Threats
107
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | AppleAssistDeviceService.exe | GET | — | 45.126.120.235:80 | http://nav.sj.soupingguo.com/controller.ashx?action=gettutorial&brand=ddm_error_log&model=default&fwversion=default&project=0 | CN | — | — | malicious |
2500 | update.exe | GET | 200 | 45.126.120.235:80 | http://sjupdate.sj.soupingguo.com/checkupdate.ashx?mt=255&softid=227&fwv=all&version=2.0.3.162&branch=0&format=xml&lan=0&isbeta=0&ismanual=0&md5=972c8a2b7660de27625cd7843be9b922 | CN | text | 801 b | malicious |
636 | SetupFsdu.exe | POST | 200 | 45.126.120.235:80 | http://tj.service.soupingguo.com/stats/ | CN | abr | 26 b | malicious |
3284 | AppleAssist.exe | POST | 200 | 45.126.120.235:80 | http://appuse.sj.soupingguo.com/api2.ashx | CN | abr | 79 b | malicious |
1140 | SetupFsdu.exe | POST | 200 | 45.126.120.235:80 | http://tj.service.soupingguo.com/stats/ | CN | abr | 26 b | malicious |
2568 | pgzs_pc_11_0612.exe | POST | 200 | 45.126.120.235:80 | http://pc5.sj.soupingguo.com/V6/config | CN | binary | 24 b | malicious |
3284 | AppleAssist.exe | POST | 200 | 45.126.120.235:80 | http://pc5.sj.soupingguo.com/V6/config | CN | pi2 | 8.50 Kb | malicious |
3284 | AppleAssist.exe | GET | 200 | 45.126.120.235:80 | http://pc5.sj.soupingguo.com/controller.ashx?act=getsoftidfinstallanduninstall&version=0&platform=Android&fw=&isipad=0&jailbreak=false&protocolVer=2.0&user=6&clientver=2%2E0%2E3%2E162 | CN | text | 450 b | malicious |
3284 | AppleAssist.exe | GET | 200 | 45.126.120.235:80 | http://nav.sj.soupingguo.com/controller.ashx?action=gettutorial&brand=ddm_error_log&model=default&fwversion=default&project=0 | CN | text | 95 b | malicious |
3284 | AppleAssist.exe | POST | 200 | 45.126.120.235:80 | http://appuse.sj.soupingguo.com/api2.ashx | CN | binary | 79 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2500 | update.exe | 45.126.120.235:80 | pc5.sj.soupingguo.com | Fuzhou | CN | malicious |
3284 | AppleAssist.exe | 172.217.22.78:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
3284 | AppleAssist.exe | 103.8.32.227:80 | kyyapp.kuyinxiu.com | No.31,Jin-rong Street | CN | unknown |
3204 | AppleAssistDeviceService.exe | 103.254.191.59:80 | bos.pgzs.com | IDC, China Telecommunications Corporation | CN | malicious |
3284 | AppleAssist.exe | 2.16.186.35:80 | is2.mzstatic.com | Akamai International B.V. | — | whitelisted |
2500 | update.exe | 103.254.191.59:80 | bos.pgzs.com | IDC, China Telecommunications Corporation | CN | malicious |
2392 | SetupFsdu.exe | 172.217.22.78:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
— | — | 172.217.21.206:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
252 | SetupFsdu.exe | 172.217.22.78:80 | www.google-analytics.com | Google Inc. | US | whitelisted |
1140 | SetupFsdu.exe | 45.126.120.235:80 | pc5.sj.soupingguo.com | Fuzhou | CN | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google-analytics.com |
| whitelisted |
pc5.sj.soupingguo.com |
| malicious |
tj.service.soupingguo.com |
| malicious |
device.sj.soupingguo.com |
| malicious |
nav.sj.soupingguo.com |
| malicious |
sjupdate.sj.soupingguo.com |
| malicious |
appuse.sj.soupingguo.com |
| malicious |
itunesapp2.sj.soupingguo.com |
| malicious |
bos.pgzs.com |
| malicious |
cfg.service.soupingguo.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2100 | SetupFsdu.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
2392 | SetupFsdu.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
252 | SetupFsdu.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
1140 | SetupFsdu.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
2568 | pgzs_pc_11_0612.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
1704 | SetupFsdu.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
2568 | pgzs_pc_11_0612.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
2500 | update.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
3204 | AppleAssistDeviceService.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
3284 | AppleAssist.exe | A Network Trojan was detected | ET MALWARE User-Agent (User-Agent Mozilla/4.0 (compatible )) |
Process | Message |
|---|---|
pgzs_pc_11_0612.exe | ????GA:UA-82224620-6-????-??[????]- |
AppleAssist.exe | 91Assist=>???? |
AppleAssist.exe | 91Assist=>????:??????????,?? |
AppleAssist.exe | 91Assist=>????:?????MUTEX?? |
AppleAssist.exe | 91Assist=>CheckIntegrity start |
AppleAssist.exe | 91Assist=>CheckIntegrity end |
AppleAssist.exe | 91Assist=>Main::StartApp |
AppleAssist.exe | CFileOperation::CreateEmptyFile failed with error 5 : Access is denied.
|
UACHelper.exe | uachelper main |
UACHelper.exe | uachelper SetUnhandleException begin |