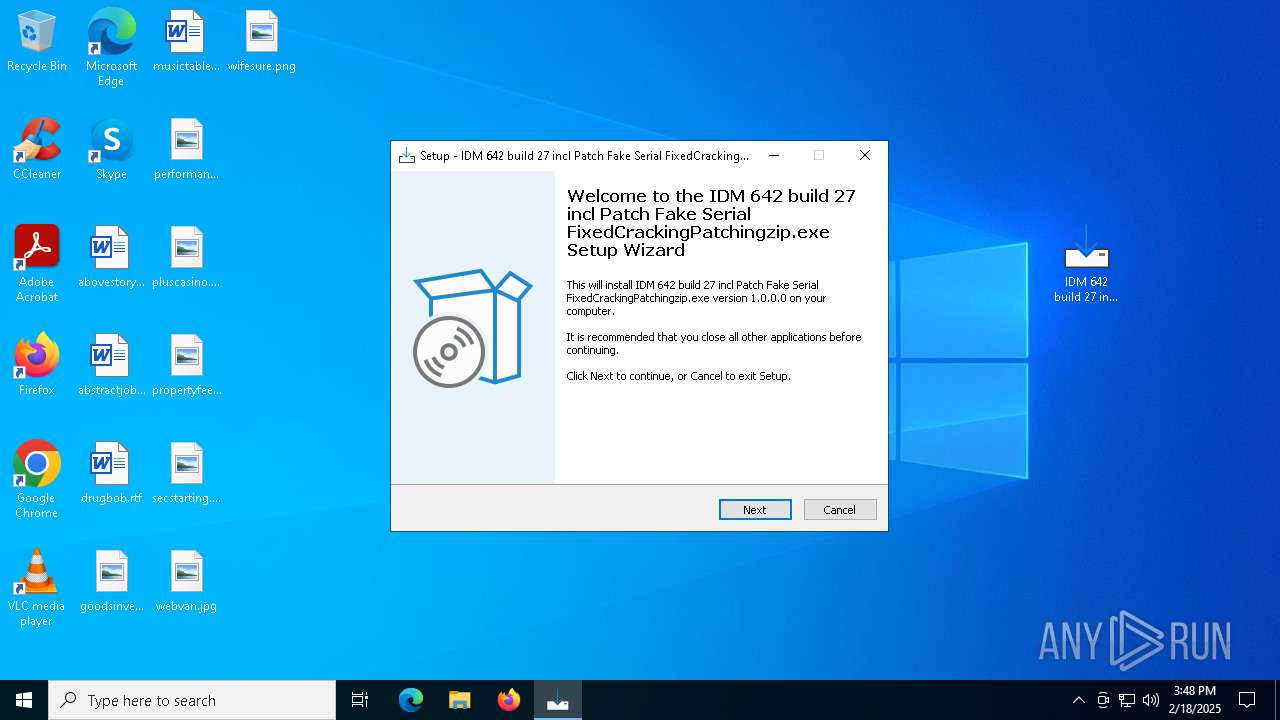
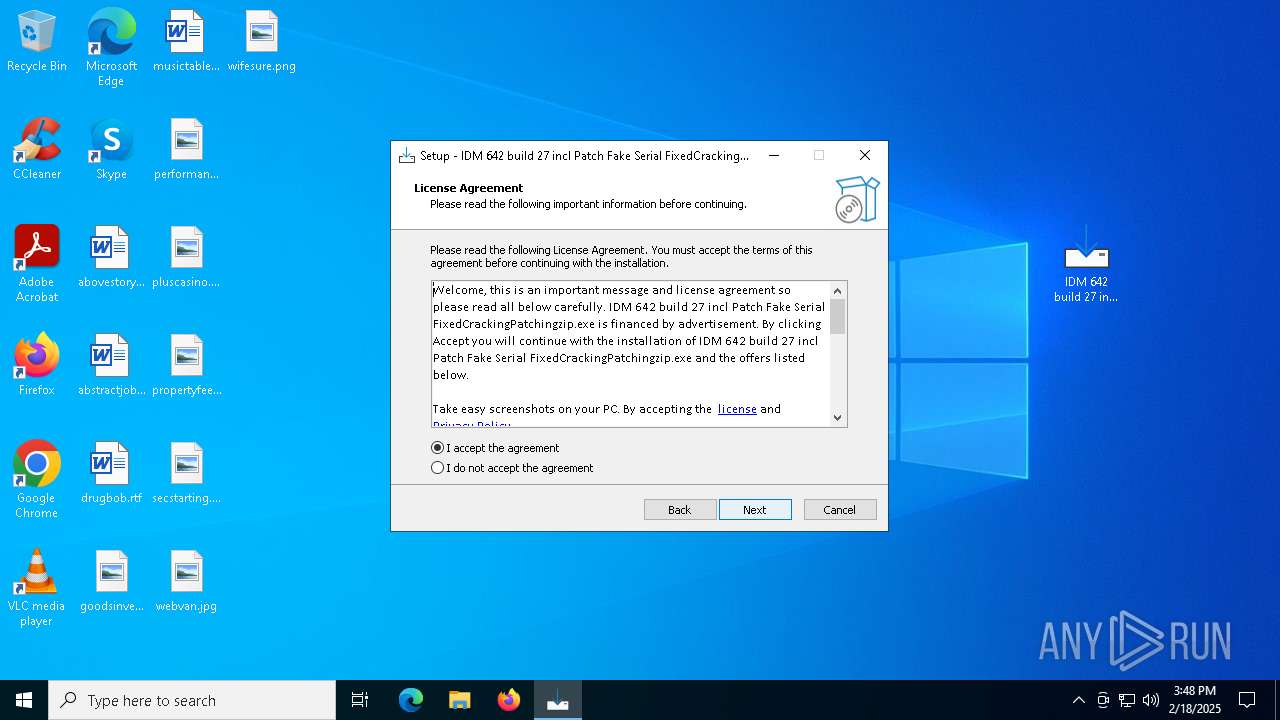
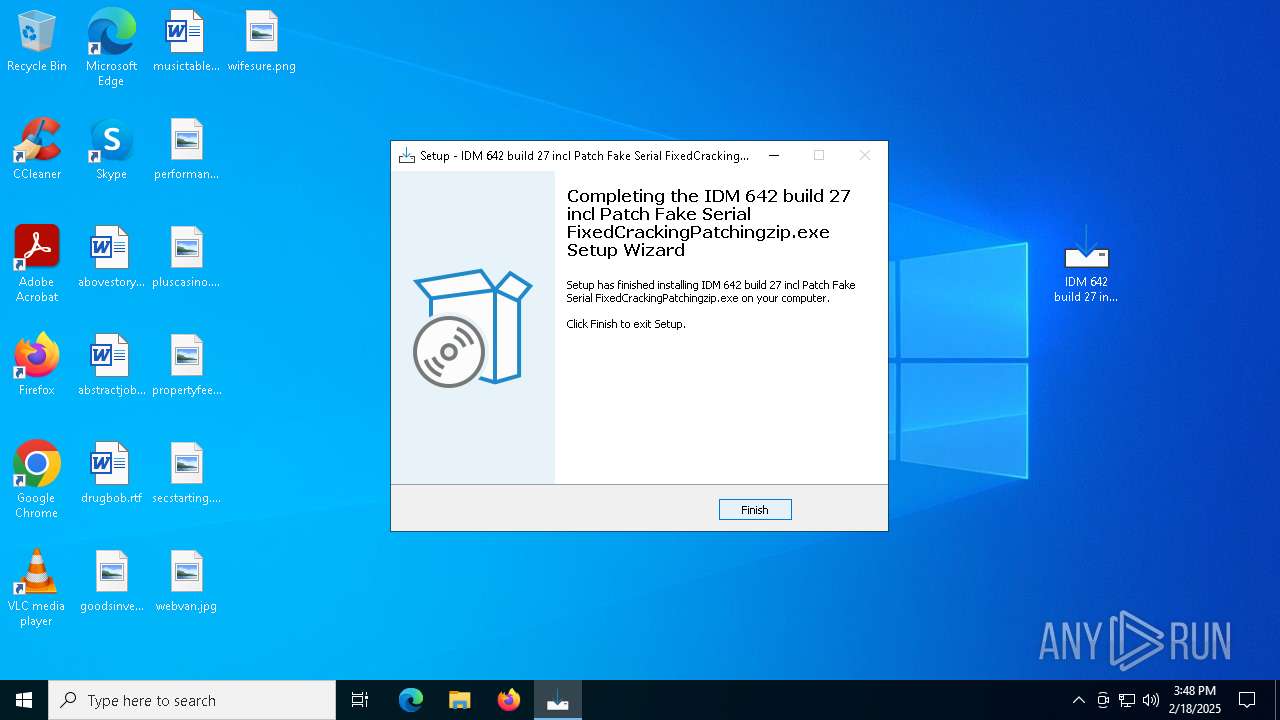
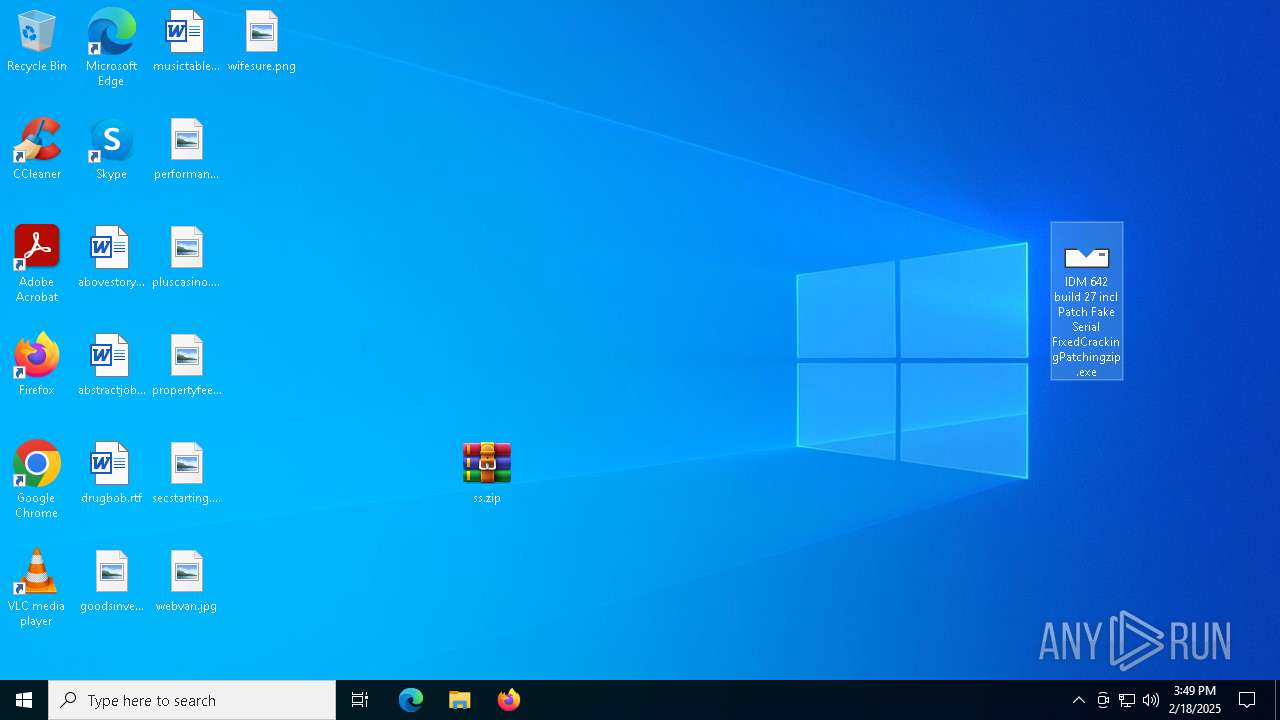
| File name: | 21421149483.zip |
| Full analysis: | https://app.any.run/tasks/b54031e1-1f34-4f06-8f64-fc5d92e4e040 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2025, 15:47:30 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | ADDB6A1FB08822FE243DEE51C3C5D5BD |
| SHA1: | 3A48E85676755CD35E62475D6123084BDABCF991 |
| SHA256: | D44912A878E6F69564A69A3DBE54FD8A6762375F6CA4A59A0BD758C6BDB96D25 |
| SSDEEP: | 49152:oRlf1PKN86USZiBe0O7xFbWsipAlU3fPFg9IPjAjCwi19HHU0+4wK/Ti2eGUpImR:Ol9iqPCiBDO7TippPFhuCwa9HHU0+1K8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
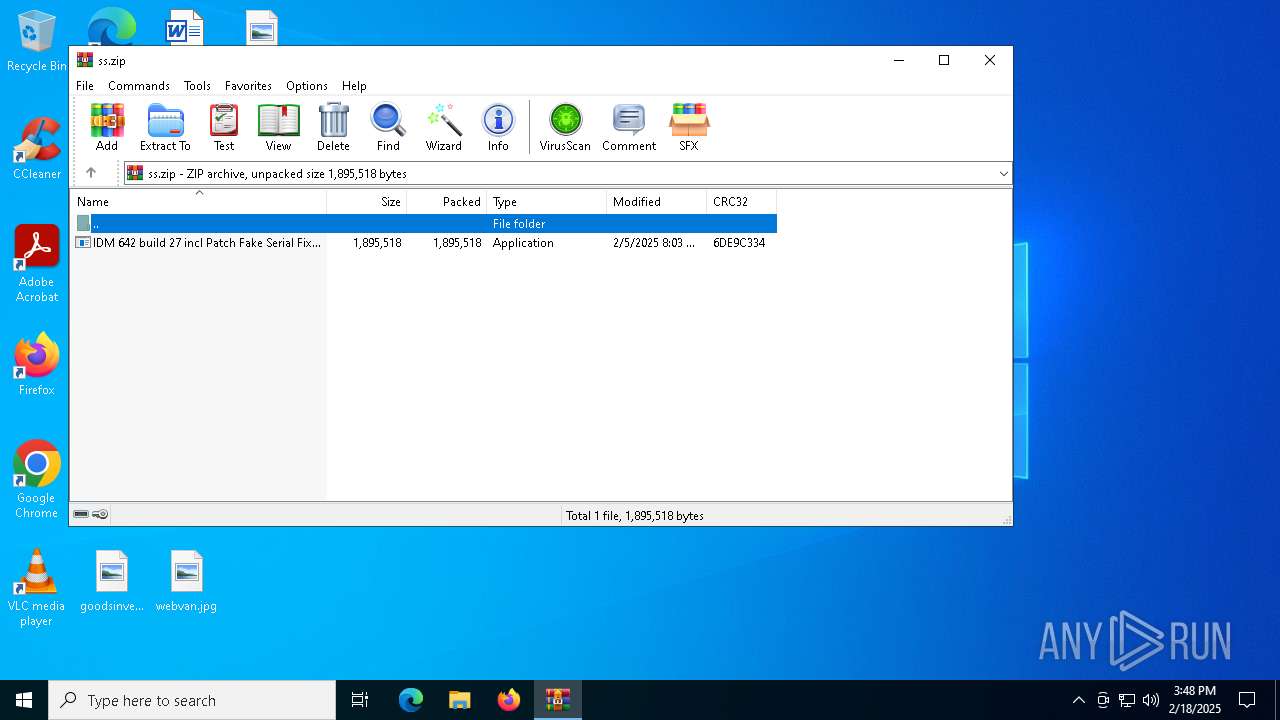
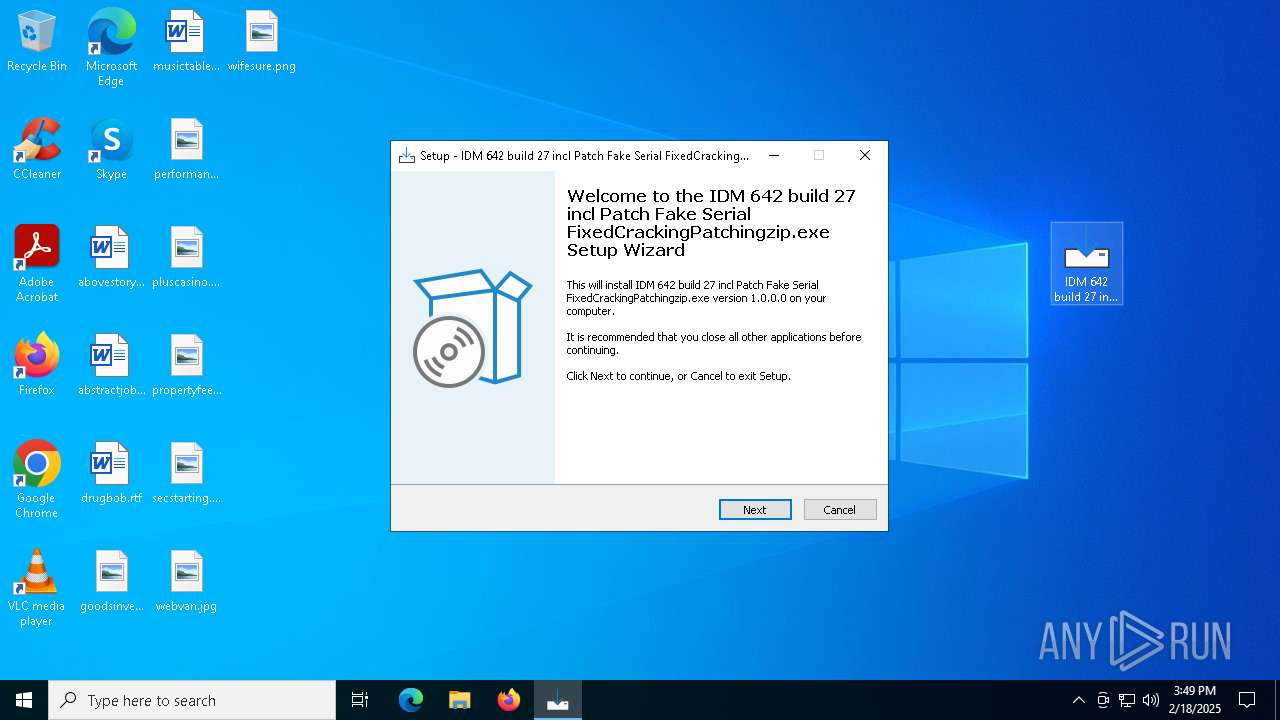
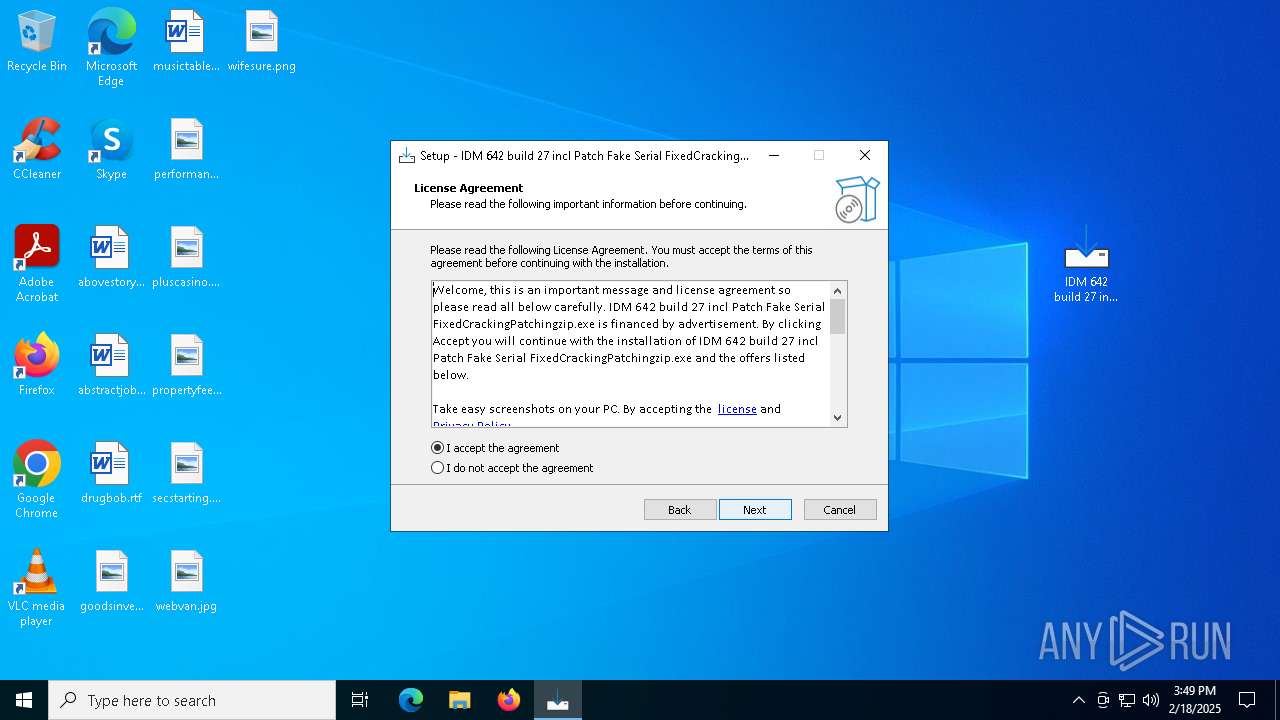
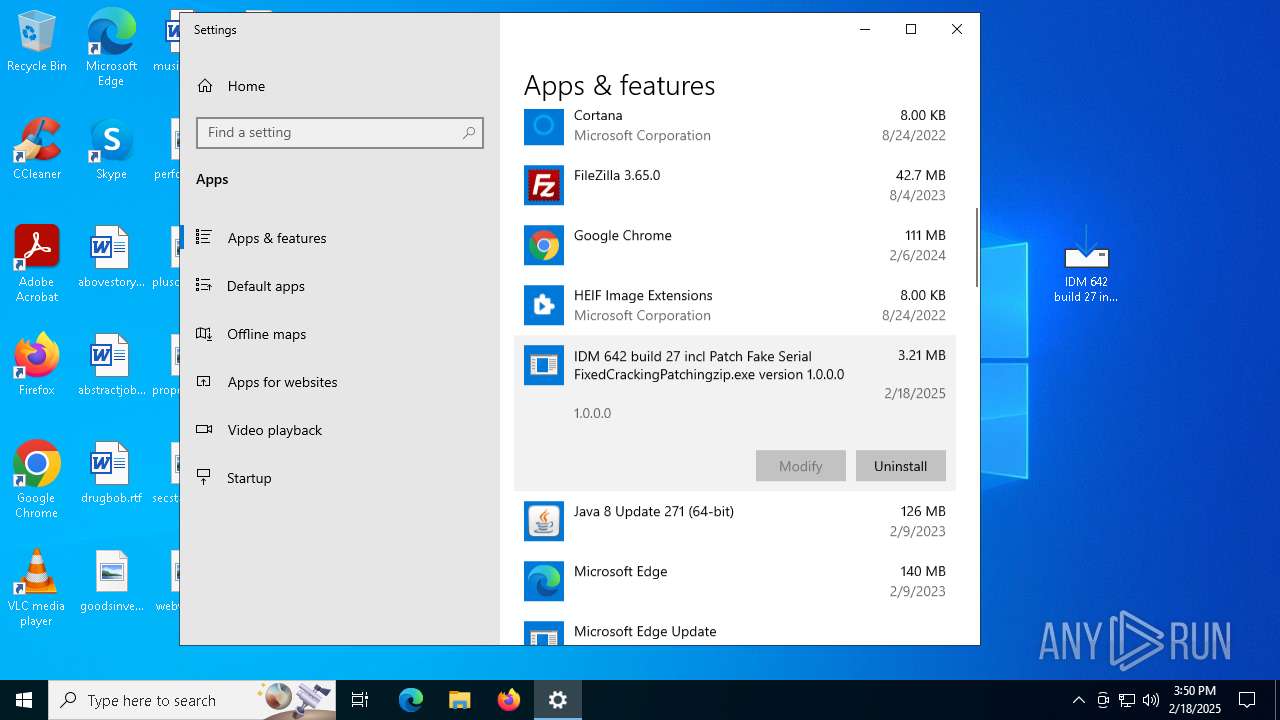
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 3724)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 5032)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 4592)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 6244)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 6240)
Reads the Windows owner or organization settings
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
Reads security settings of Internet Explorer
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 6240)
There is functionality for taking screenshot (YARA)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
INFO
Process checks computer location settings
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1580)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1744)
Manual execution by a user
- notepad++.exe (PID: 7164)
- WinRAR.exe (PID: 7096)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 3724)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 4592)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7096)
Create files in a temporary directory
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 3724)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 5032)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 4592)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 6244)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 6240)
Checks supported languages
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 3724)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1580)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 5032)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1744)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 6244)
Creates files in the program directory
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 6240)
Detects InnoSetup installer (YARA)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 3724)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 5032)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1580)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 4592)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1744)
Compiled with Borland Delphi (YARA)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 3724)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1580)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 5032)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 4592)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1744)
Checks proxy server information
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 6240)
Creates a software uninstall entry
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1064)
Reads the computer name
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp (PID: 1744)
- IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe (PID: 6244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
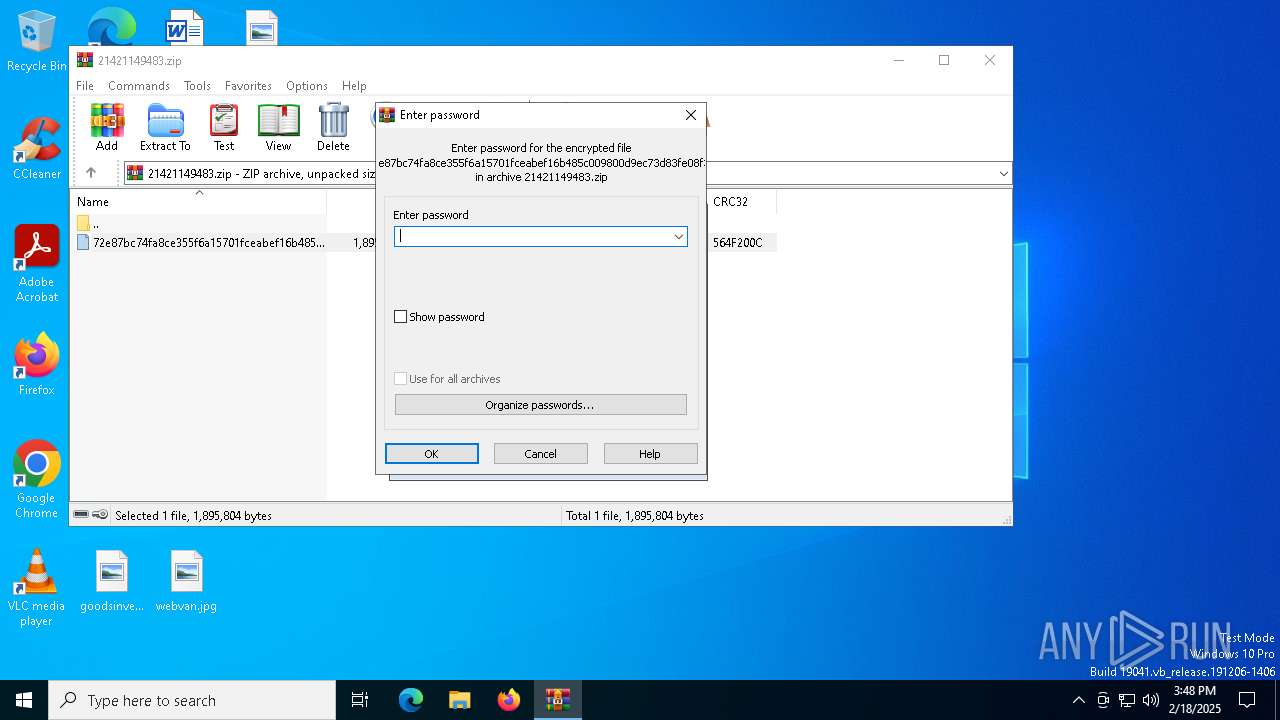
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x564f200c |
| ZipCompressedSize: | 1371880 |
| ZipUncompressedSize: | 1895804 |
| ZipFileName: | 72e87bc74fa8ce355f6a15701fceabef16b485c009800d9ec73d83fe08f32c35 |
Total processes
148
Monitored processes
12
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1064 | "C:\Users\admin\AppData\Local\Temp\is-OBNDN.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp" /SL5="$D02AE,935482,845824,C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" /SPAWNWND=$D02B0 /NOTIFYWND=$D030A | C:\Users\admin\AppData\Local\Temp\is-OBNDN.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1580 | "C:\Users\admin\AppData\Local\Temp\is-0A8IS.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp" /SL5="$D030A,935482,845824,C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" | C:\Users\admin\AppData\Local\Temp\is-0A8IS.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | — | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1744 | "C:\Users\admin\AppData\Local\Temp\is-H3QD7.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp" /SL5="$D023A,935482,845824,C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" | C:\Users\admin\AppData\Local\Temp\is-H3QD7.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | — | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | |||||||||||
User: admin Company: Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3724 | "C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" | C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchin Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4592 | "C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" | C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | explorer.exe | ||||||||||||
User: admin Company: Integrity Level: MEDIUM Description: IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchin Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5000 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\21421149483.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5032 | "C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" /SPAWNWND=$D02B0 /NOTIFYWND=$D030A | C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchin Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6240 | "C:\Users\admin\AppData\Local\Temp\is-9B49E.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp" /SL5="$C02AA,935482,845824,C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" /SPAWNWND=$E02AE /NOTIFYWND=$D023A | C:\Users\admin\AppData\Local\Temp\is-9B49E.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6244 | "C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe" /SPAWNWND=$E02AE /NOTIFYWND=$D023A | C:\Users\admin\Desktop\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | ||||||||||||
User: admin Company: Integrity Level: HIGH Description: IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchin Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 501
Read events
4 427
Write events
73
Delete events
1
Modification events
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\21421149483.zip | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5000) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
13
Suspicious files
2
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7164 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 7164 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\langs.xml | xml | |
MD5:FE22EC5755BC98988F9656F73B2E6FB8 | SHA256:F972C425CE176E960F6347F1CA2F64A8CE2B95A375C33A03E57538052BA0624D | |||
| 6240 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | C:\Users\admin\AppData\Local\Temp\is-98JIO.tmp\idp.dll | executable | |
MD5:55C310C0319260D798757557AB3BF636 | SHA256:54E7E0AD32A22B775131A6288F083ED3286A9A436941377FC20F85DD9AD983ED | |||
| 1064 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | C:\Program Files (x86)\Setup\unins000.exe | executable | |
MD5:E92B89FE33CC8EAA15E087C53E8A7E27 | SHA256:A142181BA7A0CE3F9D35349E984E514107A2C8F6908465EE916BE02819617B90 | |||
| 7164 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 6244 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | C:\Users\admin\AppData\Local\Temp\is-9B49E.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | executable | |
MD5:FE0A3C4AB8D241C553DDCB7249D6C4AC | SHA256:F1B1AC7E98B7A7119D89C402C35016E25670197ADC739F3E9459C904C77E9D89 | |||
| 6240 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | C:\Users\admin\AppData\Local\Temp\is-98JIO.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 4592 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.exe | C:\Users\admin\AppData\Local\Temp\is-H3QD7.tmp\IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | executable | |
MD5:FE0A3C4AB8D241C553DDCB7249D6C4AC | SHA256:F1B1AC7E98B7A7119D89C402C35016E25670197ADC739F3E9459C904C77E9D89 | |||
| 6240 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | C:\Program Files (x86)\Setup\is-HJQ20.tmp | executable | |
MD5:E92B89FE33CC8EAA15E087C53E8A7E27 | SHA256:A142181BA7A0CE3F9D35349E984E514107A2C8F6908465EE916BE02819617B90 | |||
| 1064 | IDM 642 build 27 incl Patch Fake Serial FixedCrackingPatchingzip.tmp | C:\Users\admin\AppData\Local\Temp\is-325SQ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
46
DNS requests
31
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
440 | svchost.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
440 | svchost.exe | GET | 200 | 23.209.214.100:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6844 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6844 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6368 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6100 | SystemSettings.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5064 | SearchApp.exe | 92.123.104.52:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1228 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
440 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
440 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
440 | svchost.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
440 | svchost.exe | 23.209.214.100:80 | www.microsoft.com | PT. Telekomunikasi Selular | ID | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 92.123.104.44:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|