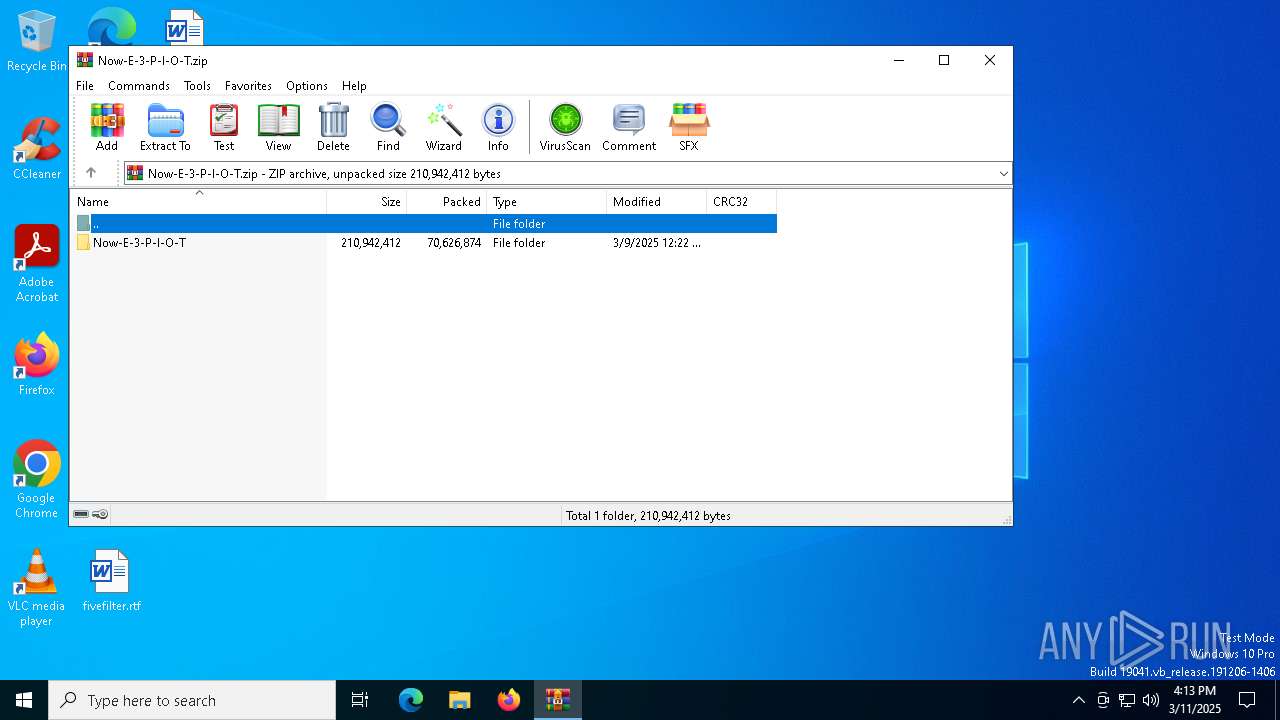
| File name: | Now-E-3-P-I-O-T.zip |
| Full analysis: | https://app.any.run/tasks/3b7e8148-d67d-495b-b250-9ee55bd9d88b |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2025, 16:13:17 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | C431D2C0B13B2D104ED9A9B040D8BAB6 |
| SHA1: | C7A54E17213C8FE7D9271074838156E17AC57A4A |
| SHA256: | D43AE989CCB100CC431FFFE775068FD2514A51683FE94355837314B9D276885B |
| SSDEEP: | 786432:iRmPIjwGBQT/Q6djNP7pByIvEphPRQrbp:bPIjHBQrQ6djN7Py9ip |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7780)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7780)
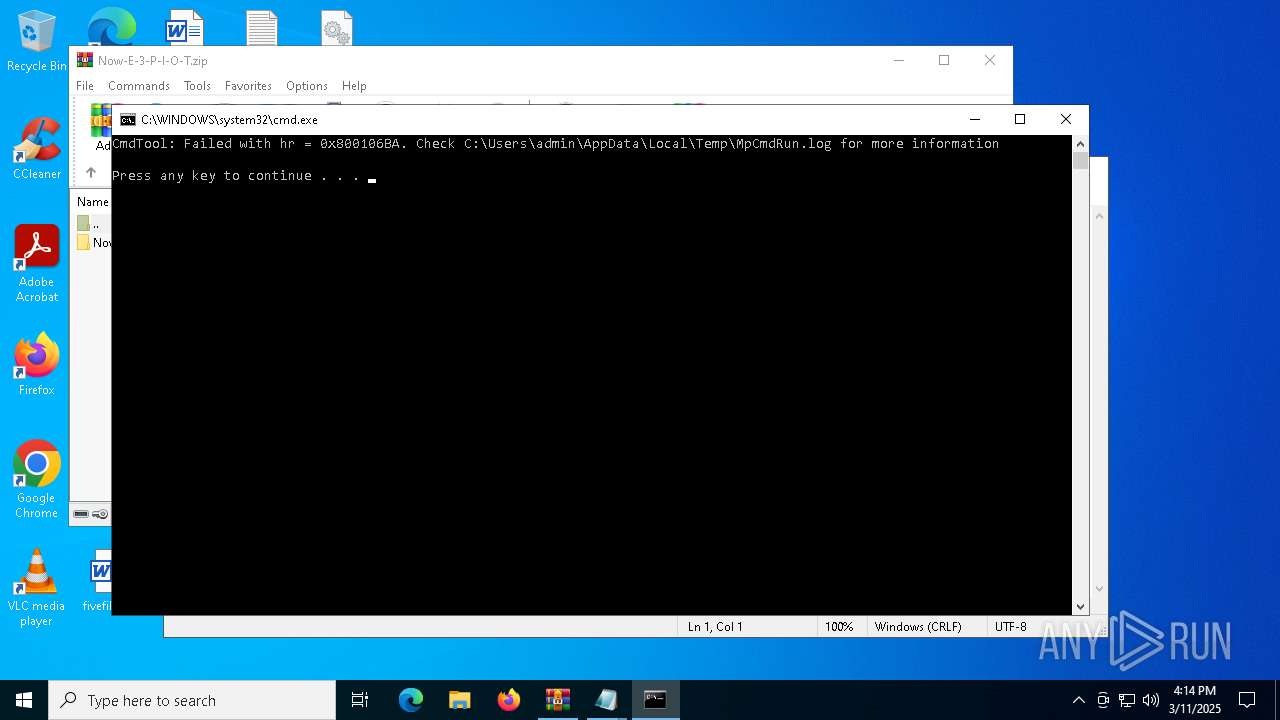
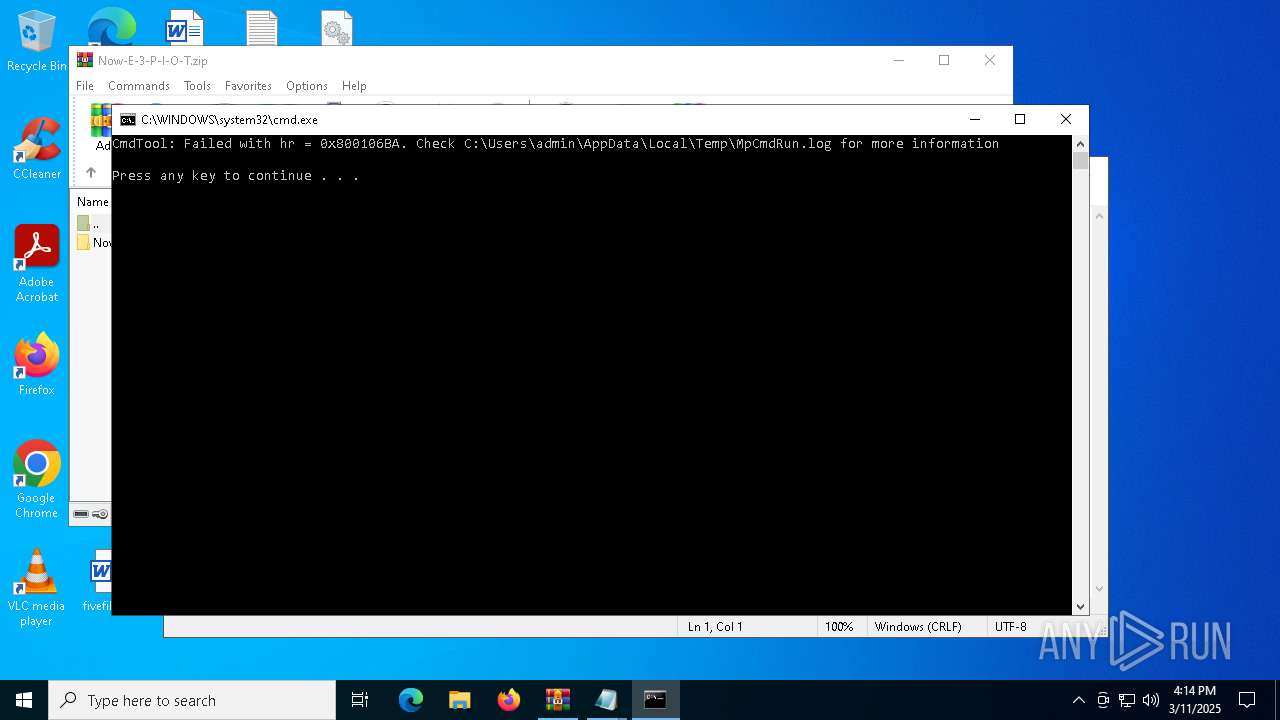
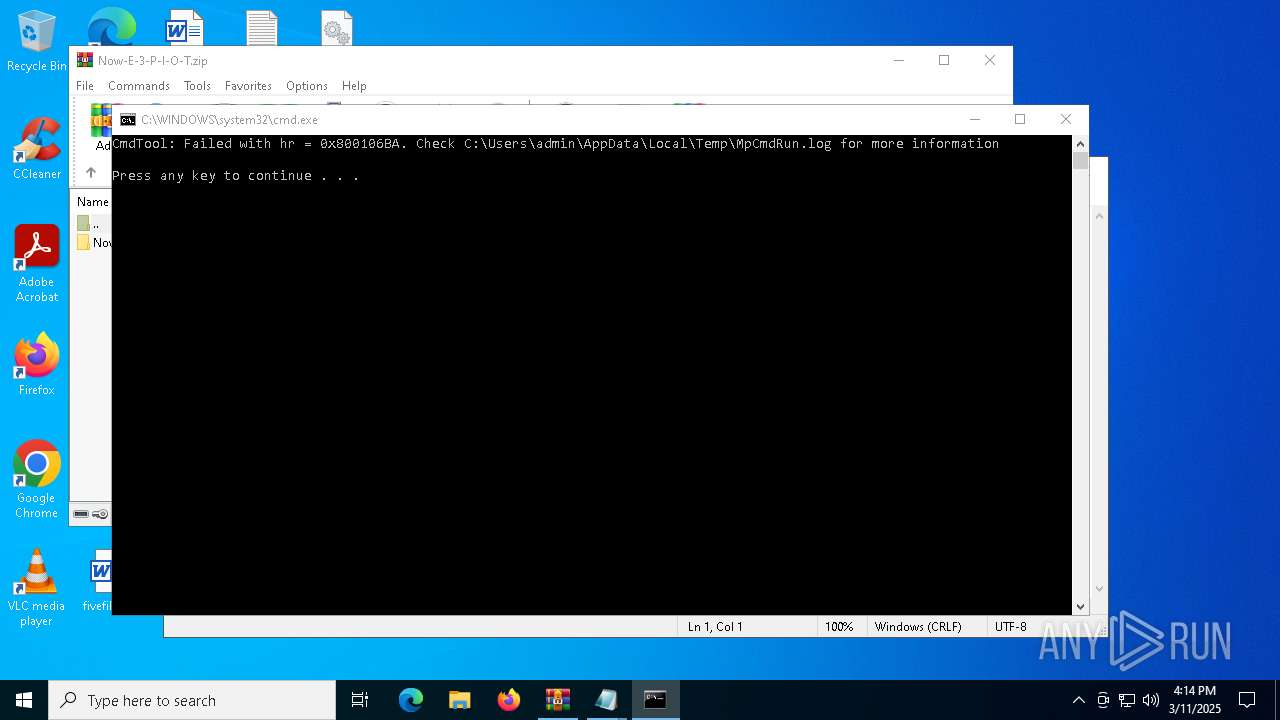
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7780)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7780)
INFO
Manual execution by a user
- notepad.exe (PID: 8012)
- notepad.exe (PID: 8136)
- notepad.exe (PID: 8092)
- notepad.exe (PID: 8180)
- notepad.exe (PID: 7268)
- OpenWith.exe (PID: 7236)
- OpenWith.exe (PID: 7336)
- notepad.exe (PID: 8052)
The sample compiled with english language support
- WinRAR.exe (PID: 7780)
Reads security settings of Internet Explorer
- notepad.exe (PID: 8012)
- notepad.exe (PID: 8052)
- notepad.exe (PID: 8180)
- notepad.exe (PID: 7268)
- notepad.exe (PID: 8092)
- notepad.exe (PID: 8136)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7236)
- OpenWith.exe (PID: 7336)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7780)
Create files in a temporary directory
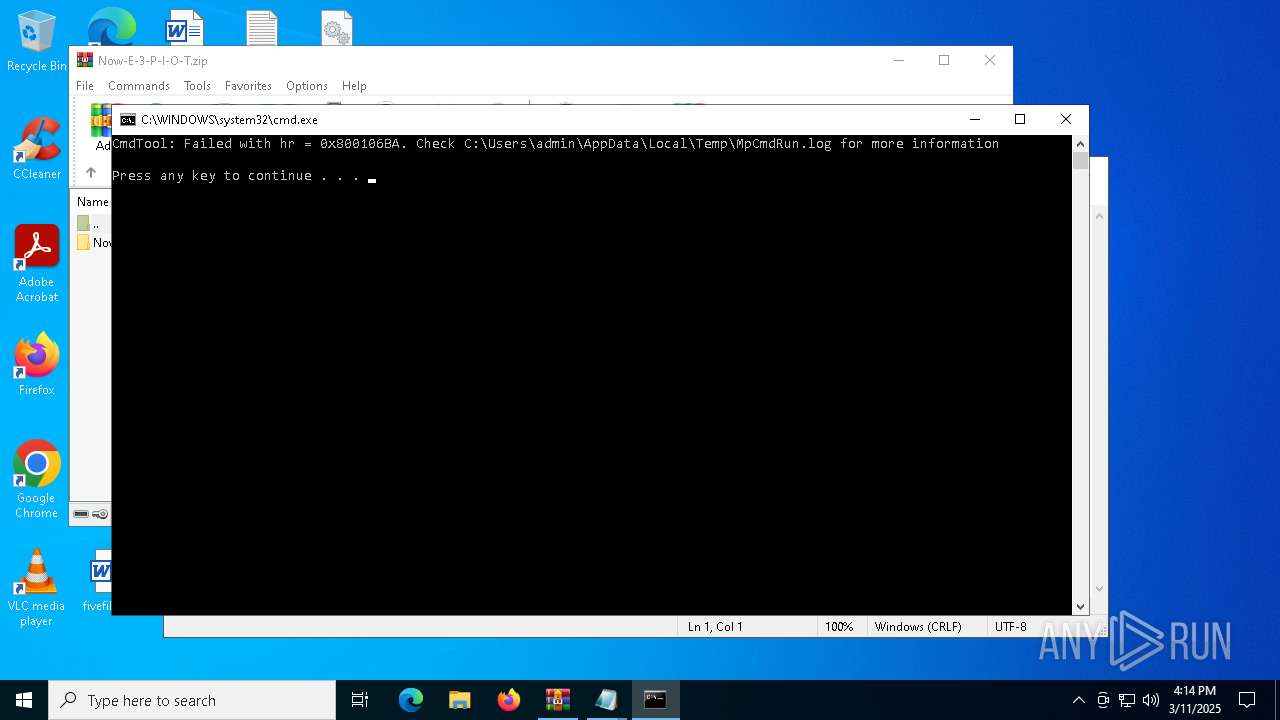
- MpCmdRun.exe (PID: 2236)
Checks supported languages
- MpCmdRun.exe (PID: 2236)
Checks proxy server information
- slui.exe (PID: 7196)
Reads the computer name
- MpCmdRun.exe (PID: 2236)
Reads the software policy settings
- slui.exe (PID: 7196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (66.6) |
|---|---|---|
| .zip | | | ZIP compressed archive (33.3) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:08 16:22:46 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Now-E-3-P-I-O-T/ |
Total processes
130
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2236 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Rar$Scan55519.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7196 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
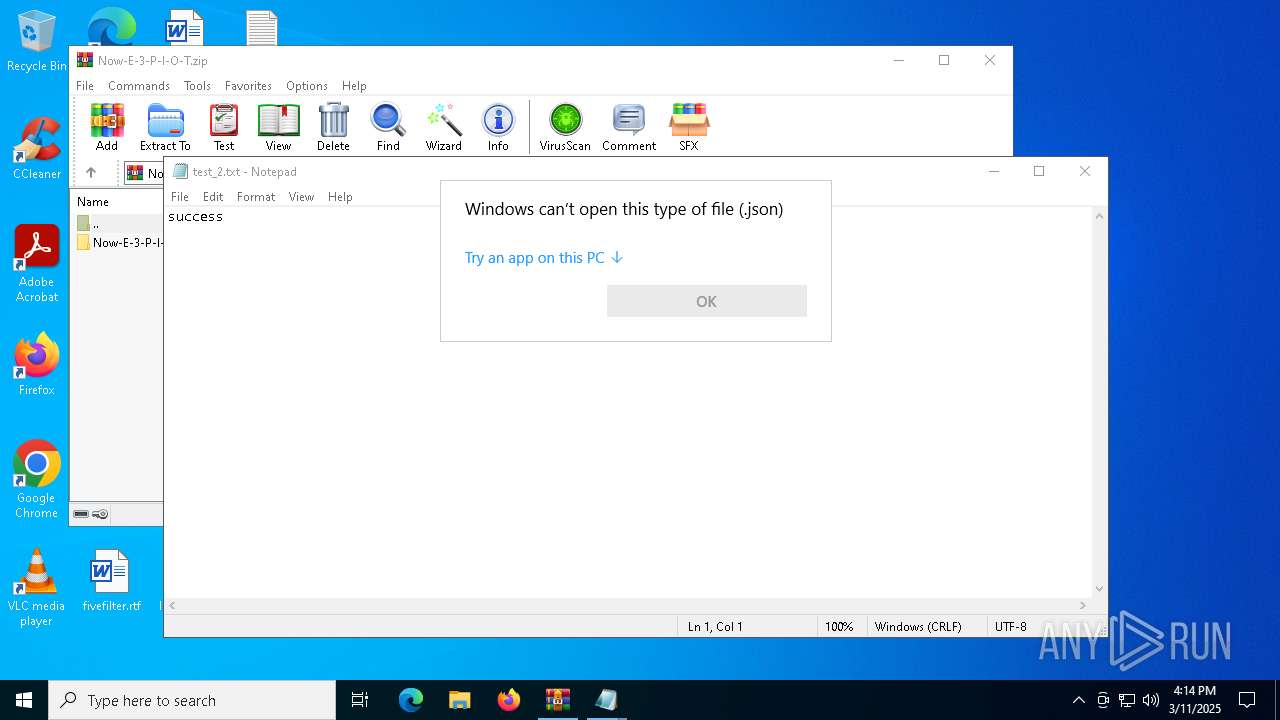
| 7236 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\vk_swiftshader_icd.json | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7268 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\test_2.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7336 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\ProtectionManagement.mfl | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7780 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Now-E-3-P-I-O-T.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 8012 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\LICENSE.electron.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
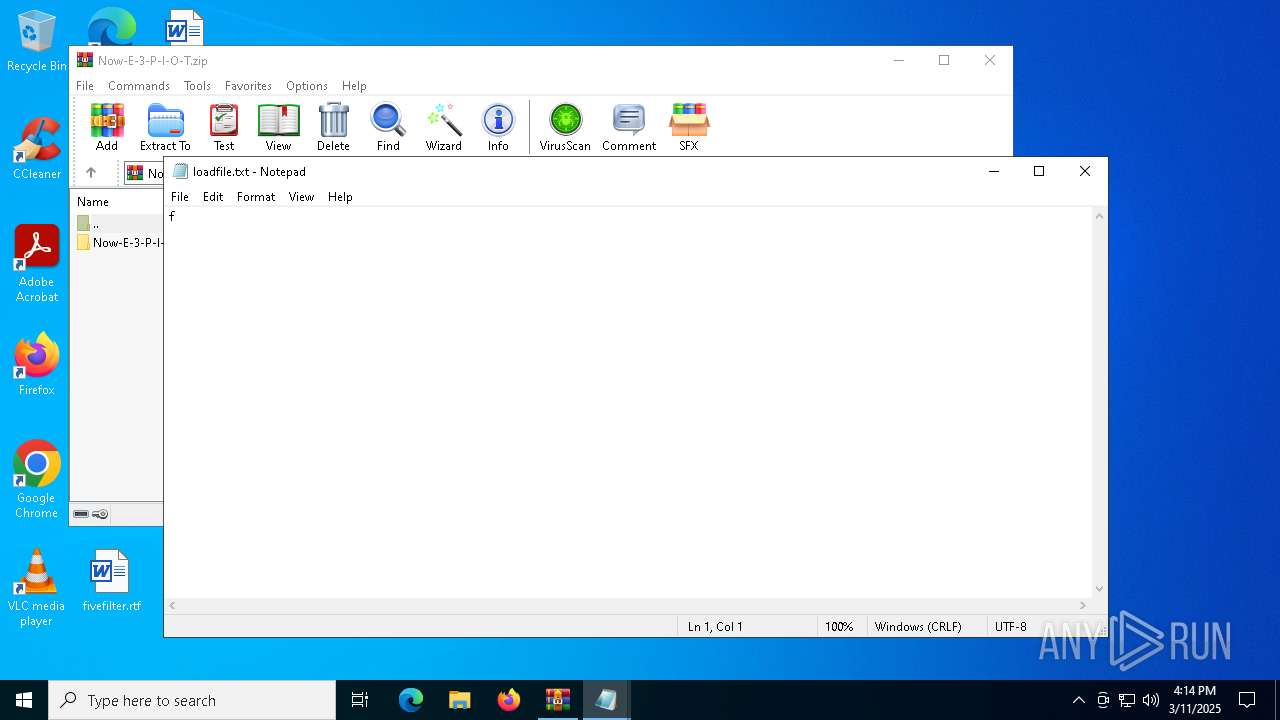
| 8052 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\loadfile.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 018
Read events
7 008
Write events
10
Delete events
0
Modification events
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Now-E-3-P-I-O-T.zip | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
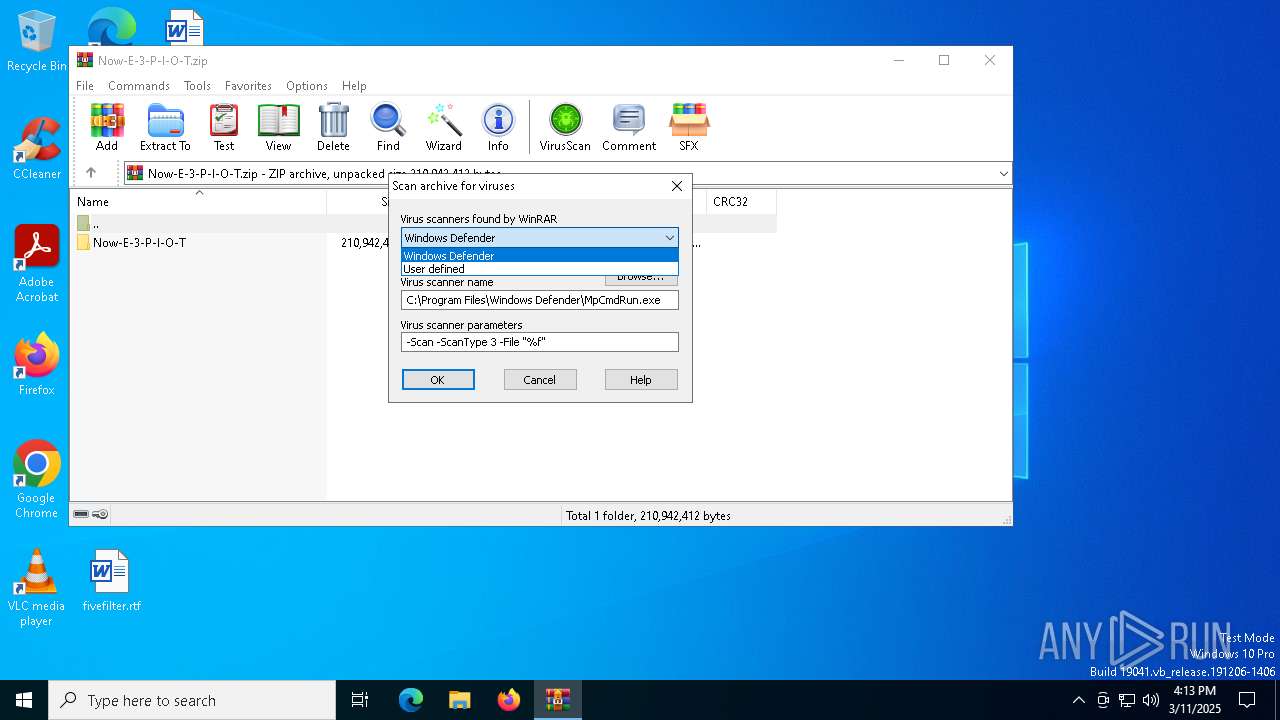
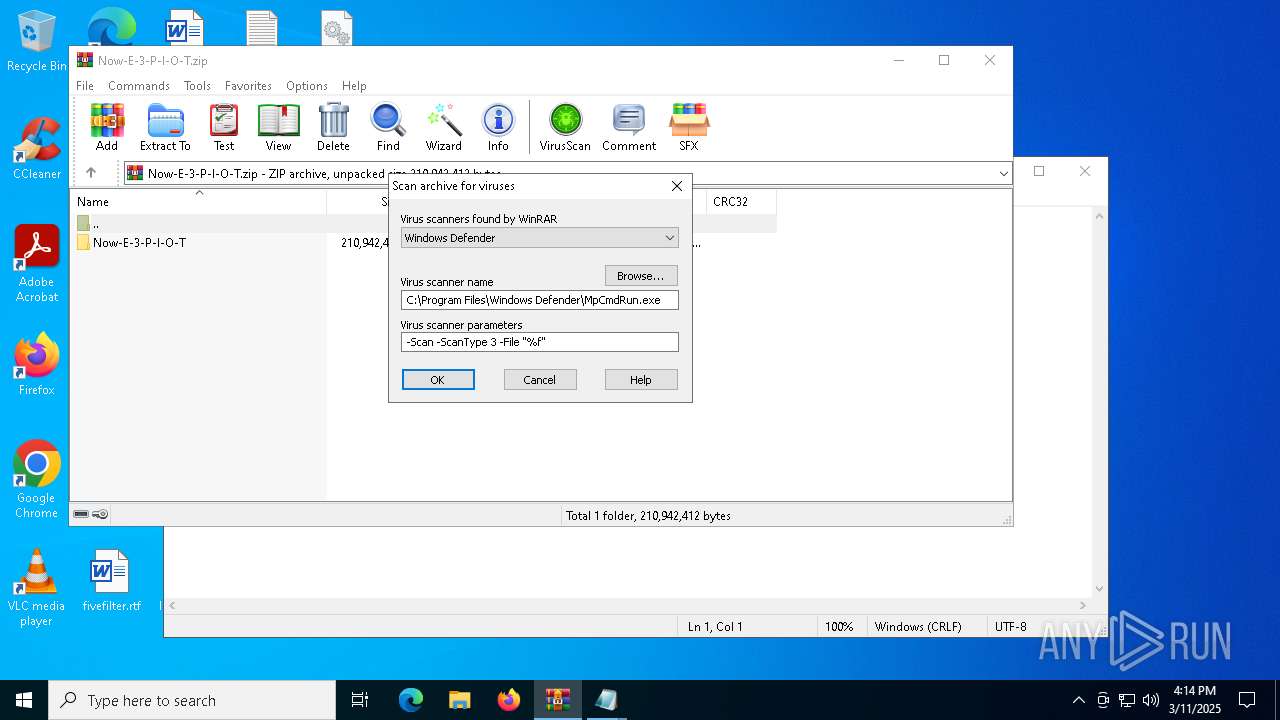
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
| (PID) Process: | (7780) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
Executable files
33
Suspicious files
192
Text files
19
Unknown types
0
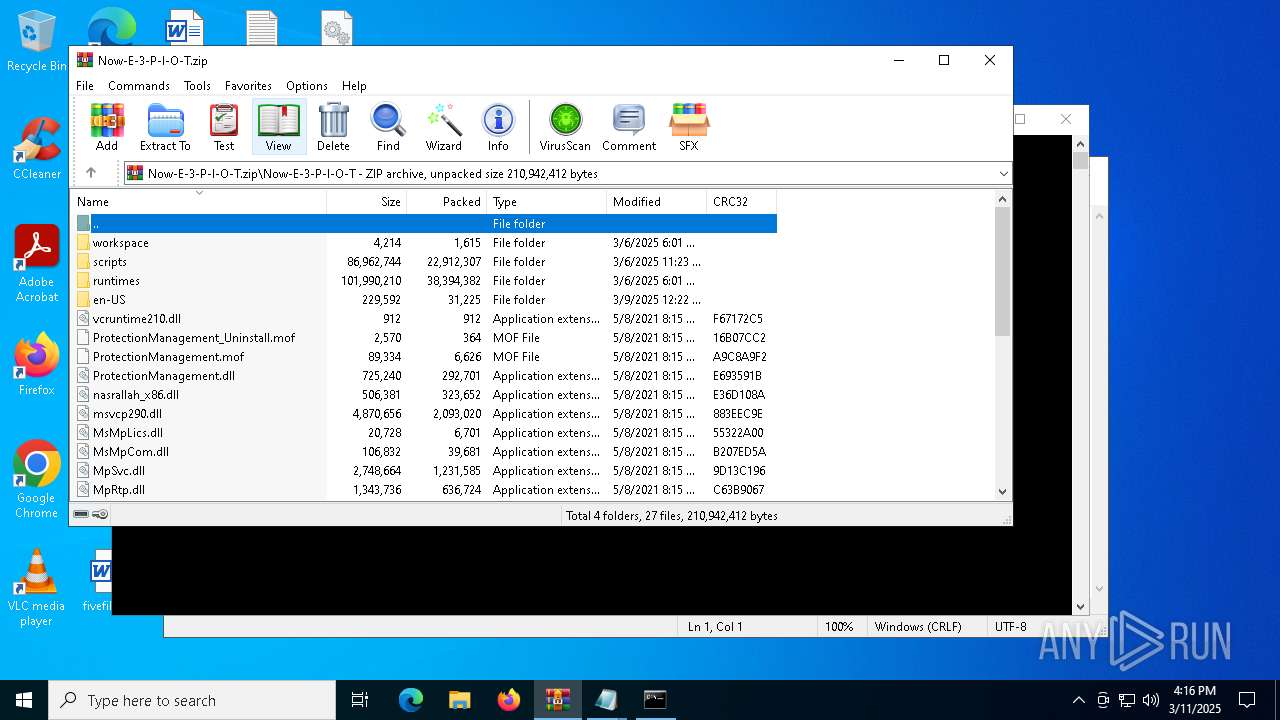
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\AMMonitoringProvider.dll | executable | |
MD5:F2AE2445AC7ECA1EE8480321B03241FA | SHA256:8DA3D256EF7DF249138D8E934FBD74FDA8F31C5B5758F26A757F2C686E1DEBDF | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\AmStatusInstall.mof | text | |
MD5:EAA6FC46125F59D04BCBB6122817B41E | SHA256:67191020D74AE8400F875238E494AAF5D28EEFEC7EFE1D1D20D2DB068D5E35D6 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\en-US\EppManifest.dll.mui | executable | |
MD5:1F9E87B6393FAD0794FF9CA470A5FC54 | SHA256:AF826EA80A404AA017E2C2FA91076D962B40E4D0D2A27D292EDB8BF7ADC19AE4 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\en-US\MpEvMsg.dll.mui | executable | |
MD5:0F7456FBB76D25BB366A6FA9A9D4D7CE | SHA256:3C18C85F5C5C96DB16A83FEB576F41857B664B9FEB026E6E7859AAB428FBF9D4 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\Bootstrapper-uip-WEB.exe | executable | |
MD5:72256F138063B9EEAC72EE741737B8E3 | SHA256:1CD644B750884906B707419C8F40598C04F1402E4E93CBF4A33F3254846DC870 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\en-US\ProtectionManagement_Uninstall.mfl | text | |
MD5:AFE6664D26D5D05B4568E329BE37D7DE | SHA256:B6BAC201F1586B4C357521C46421086557A0DF86A022B120B723EB047E450D43 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\en-US\ProtectionManagement.dll.mui | executable | |
MD5:752AD6B6FFA3A5CC25E1EF6CFAC6E826 | SHA256:115C3FDD3374332BB063793ACF7D0F4DF94E9F4B5A25D4E28D6A783AE0275234 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\FepUnregister.mof | text | |
MD5:CCE6F066104177A368EE528EBF94A170 | SHA256:58996425ADD2DFC63157CBD618ABB81C722FADCF5E2133D2488DB2840DBF47D5 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\mpclient.dll | executable | |
MD5:03050ADA90924BAFE40913078068CFEA | SHA256:06BA7ACD7617CEAEE3F57922DC00F5D4093110797C1C32F0EF9BB9D985F60811 | |||
| 7780 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7780.49172\Now-E-3-P-I-O-T.zip\Now-E-3-P-I-O-T\endpointdlp.dll | executable | |
MD5:4433F83C04F409EAEA6E9D8E36708684 | SHA256:4804AE834CA909178F3E9D6876209AA10851A36BC4EDAFD75A571E980013DA1D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
21
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 20.83.72.98:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
7412 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7196 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
activation-v2.sls.microsoft.com |
| whitelisted |