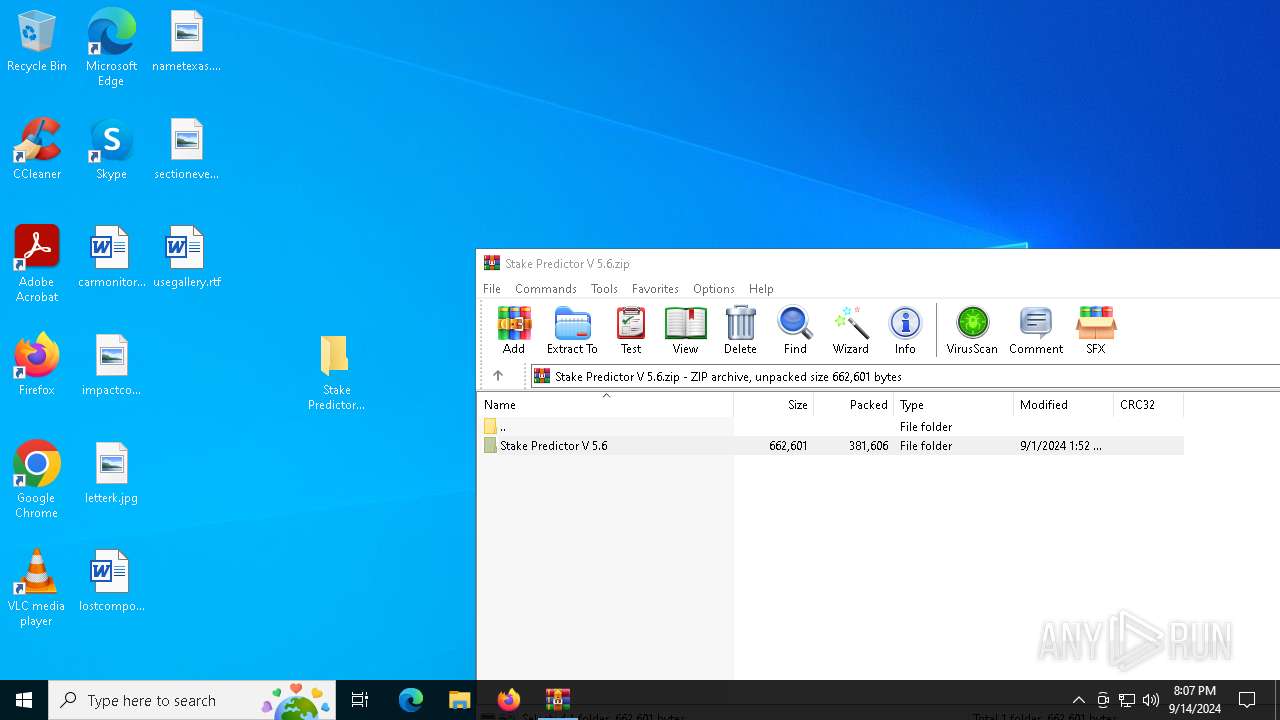
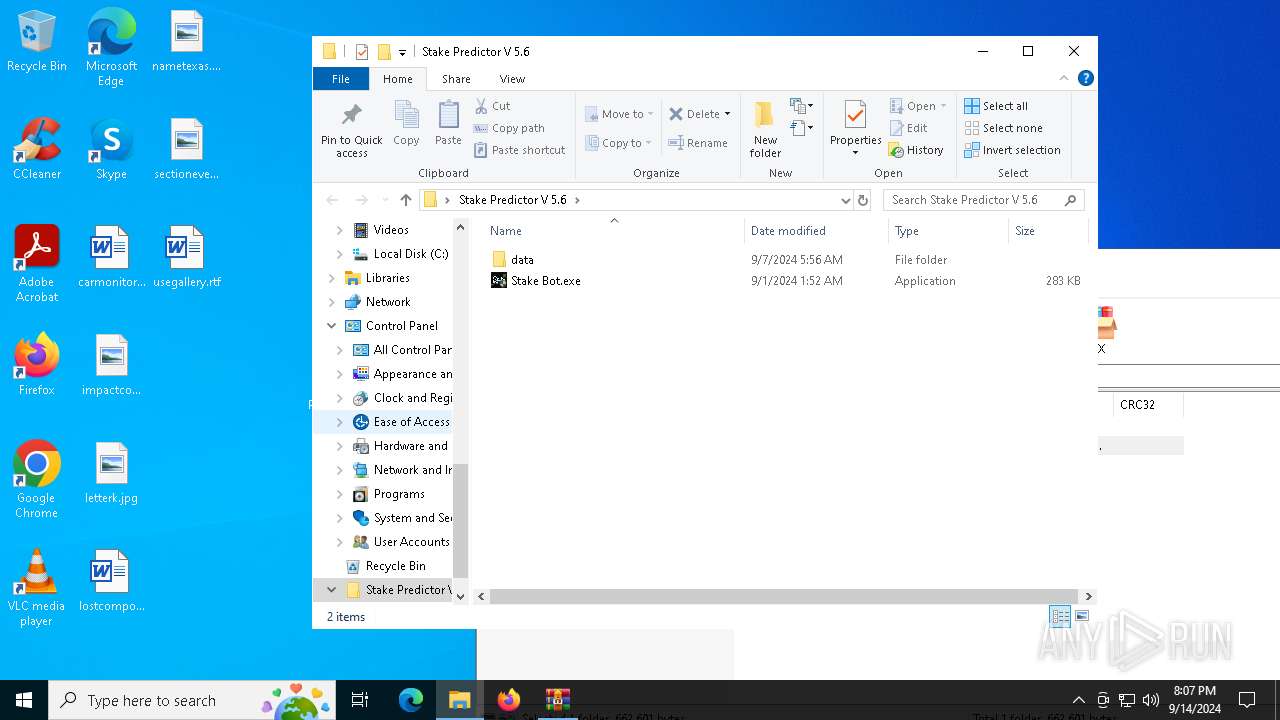
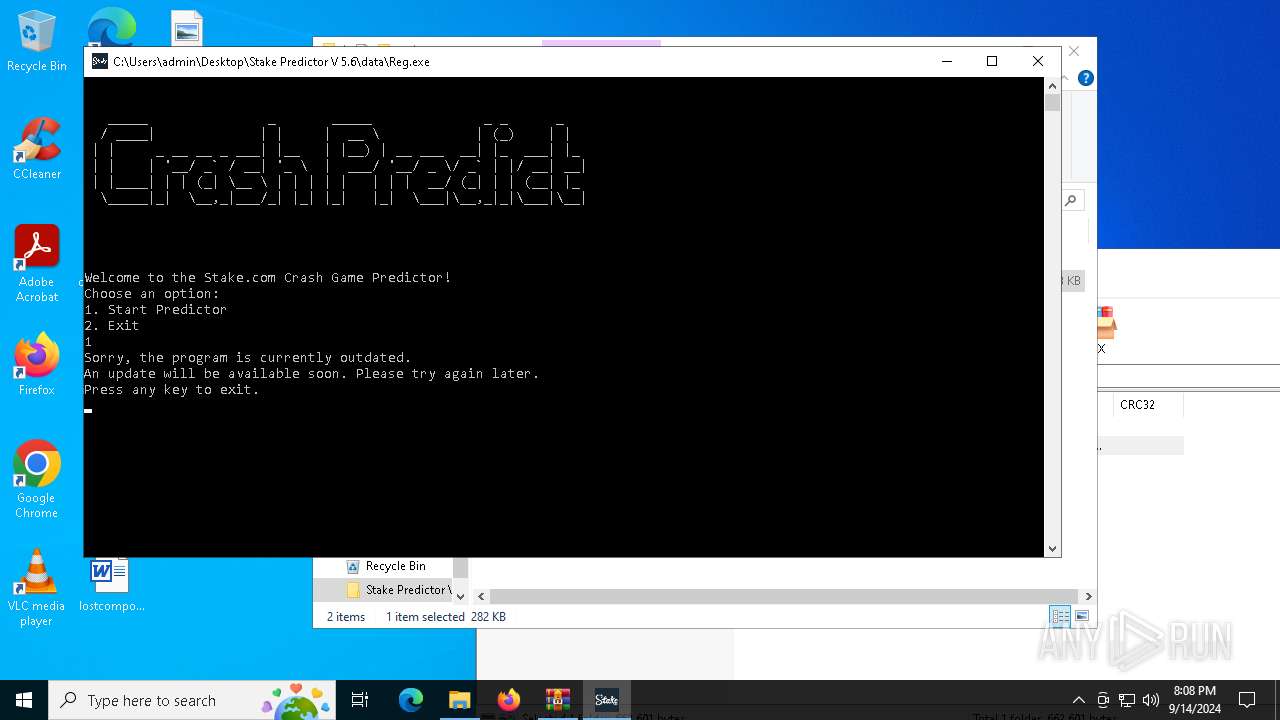
| File name: | Stake Predictor V 5.6.zip |
| Full analysis: | https://app.any.run/tasks/07911fe4-b3fb-41ed-a4bb-3850d9aee5eb |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | September 14, 2024, 20:07:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 0D4ABD4F4BF5B0FF9FC791D3B3D10CC6 |
| SHA1: | 5E1816A6C1B73B325467D56C08815D006A4899D1 |
| SHA256: | D4283E57BB3334829406B1B5D9BA80687DB1473D8CDFD2D48378B32184AC5529 |
| SSDEEP: | 6144:oLH0JfRZZf6ROTm6HUzG2V9yUrFAYh0qiXkGQBs1/voOvAo3GL+vfqbhHnNfJgTg:G0yRcHUSyyUZA0/6ZJ/QOvFjq91JnHN |
MALICIOUS
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 876)
Application was injected by another process
- svchost.exe (PID: 4324)
- svchost.exe (PID: 2160)
- svchost.exe (PID: 4332)
- explorer.exe (PID: 4552)
- svchost.exe (PID: 2496)
- svchost.exe (PID: 3340)
- svchost.exe (PID: 1364)
- svchost.exe (PID: 1508)
- svchost.exe (PID: 5092)
- svchost.exe (PID: 1128)
- svchost.exe (PID: 2000)
- svchost.exe (PID: 6492)
- svchost.exe (PID: 3084)
- svchost.exe (PID: 3496)
- svchost.exe (PID: 4300)
- svchost.exe (PID: 3888)
- svchost.exe (PID: 2304)
- svchost.exe (PID: 1316)
- svchost.exe (PID: 2692)
- svchost.exe (PID: 1404)
- svchost.exe (PID: 5036)
- svchost.exe (PID: 5256)
- svchost.exe (PID: 2664)
- svchost.exe (PID: 2344)
- svchost.exe (PID: 5236)
- svchost.exe (PID: 896)
- svchost.exe (PID: 1272)
- svchost.exe (PID: 2256)
- svchost.exe (PID: 1872)
- svchost.exe (PID: 5416)
- svchost.exe (PID: 1864)
- svchost.exe (PID: 1472)
- svchost.exe (PID: 3260)
- svchost.exe (PID: 476)
- svchost.exe (PID: 4808)
- svchost.exe (PID: 3408)
- svchost.exe (PID: 6976)
- svchost.exe (PID: 4000)
- svchost.exe (PID: 3020)
- svchost.exe (PID: 3220)
- svchost.exe (PID: 3012)
- svchost.exe (PID: 3056)
- svchost.exe (PID: 2072)
- svchost.exe (PID: 2996)
- svchost.exe (PID: 1816)
- svchost.exe (PID: 2412)
- svchost.exe (PID: 1620)
- svchost.exe (PID: 1628)
- svchost.exe (PID: 1036)
- svchost.exe (PID: 1796)
- svchost.exe (PID: 1012)
- svchost.exe (PID: 3200)
- svchost.exe (PID: 2184)
- svchost.exe (PID: 1200)
- svchost.exe (PID: 2788)
- svchost.exe (PID: 1824)
- svchost.exe (PID: 1408)
- svchost.exe (PID: 4184)
- svchost.exe (PID: 1208)
- svchost.exe (PID: 1600)
- svchost.exe (PID: 2312)
- svchost.exe (PID: 2968)
- svchost.exe (PID: 1192)
- svchost.exe (PID: 3548)
- svchost.exe (PID: 4140)
- svchost.exe (PID: 7100)
- svchost.exe (PID: 1588)
- svchost.exe (PID: 3272)
- svchost.exe (PID: 4532)
Adds path to the Windows Defender exclusion list
- powershell.exe (PID: 876)
Uses AES cipher (POWERSHELL)
- powershell.exe (PID: 876)
Gets or sets the symmetric key that is used for encryption and decryption (POWERSHELL)
- powershell.exe (PID: 876)
Gets or sets the initialization vector for the symmetric algorithm (POWERSHELL)
- powershell.exe (PID: 876)
Runs injected code in another process
- powershell.exe (PID: 876)
Connects to the CnC server
- powershell.exe (PID: 876)
XWORM has been detected (SURICATA)
- powershell.exe (PID: 876)
XWORM has been detected (YARA)
- powershell.exe (PID: 876)
SUSPICIOUS
The process checks if it is being run in the virtual environment
- explorer.exe (PID: 4552)
- Stake Bot.exe (PID: 6016)
Checks Windows Trust Settings
- Stake Bot.exe (PID: 6016)
Reads security settings of Internet Explorer
- Stake Bot.exe (PID: 6016)
Adds/modifies Windows certificates
- Stake Bot.exe (PID: 6016)
Executable content was dropped or overwritten
- Stake Bot.exe (PID: 6016)
Executing commands from a ".bat" file
- Stake Bot.exe (PID: 6016)
- cmd.exe (PID: 3972)
Reads the date of Windows installation
- Stake Bot.exe (PID: 6016)
Starts CMD.EXE for commands execution
- Stake Bot.exe (PID: 6016)
- cmd.exe (PID: 3972)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 876)
Application launched itself
- cmd.exe (PID: 3972)
- powershell.exe (PID: 876)
Cryptography encrypted command line is found
- cmd.exe (PID: 6008)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3972)
- powershell.exe (PID: 876)
Process checks specific path in scheduled tasks
- powershell.exe (PID: 5708)
Probably obfuscated PowerShell command line is found
- powershell.exe (PID: 876)
Script adds exclusion path to Windows Defender
- powershell.exe (PID: 876)
Contacting a server suspected of hosting an CnC
- powershell.exe (PID: 876)
Connects to unusual port
- powershell.exe (PID: 876)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4692)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
Manual execution by a user
- Stake Bot.exe (PID: 5880)
- Stake Bot.exe (PID: 6016)
The process uses the downloaded file
- WinRAR.exe (PID: 4692)
- explorer.exe (PID: 4552)
- Stake Bot.exe (PID: 6016)
- powershell.exe (PID: 876)
Checks supported languages
- Stake Bot.exe (PID: 6016)
- Reg.exe (PID: 2264)
Reads the computer name
- Stake Bot.exe (PID: 6016)
- Reg.exe (PID: 2264)
Reads the machine GUID from the registry
- Stake Bot.exe (PID: 6016)
Reads Environment values
- Stake Bot.exe (PID: 6016)
Create files in a temporary directory
- Stake Bot.exe (PID: 6016)
Reads the software policy settings
- Stake Bot.exe (PID: 6016)
Checks proxy server information
- Stake Bot.exe (PID: 6016)
Creates files or folders in the user directory
- Stake Bot.exe (PID: 6016)
Checks if a key exists in the options dictionary (POWERSHELL)
- Stake Bot.exe (PID: 6016)
- powershell.exe (PID: 5708)
- powershell.exe (PID: 2268)
- powershell.exe (PID: 3244)
Process checks computer location settings
- Stake Bot.exe (PID: 6016)
Checks current location (POWERSHELL)
- powershell.exe (PID: 876)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 876)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 876)
Gets data length (POWERSHELL)
- powershell.exe (PID: 876)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 3244)
Reads the time zone
- svchost.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
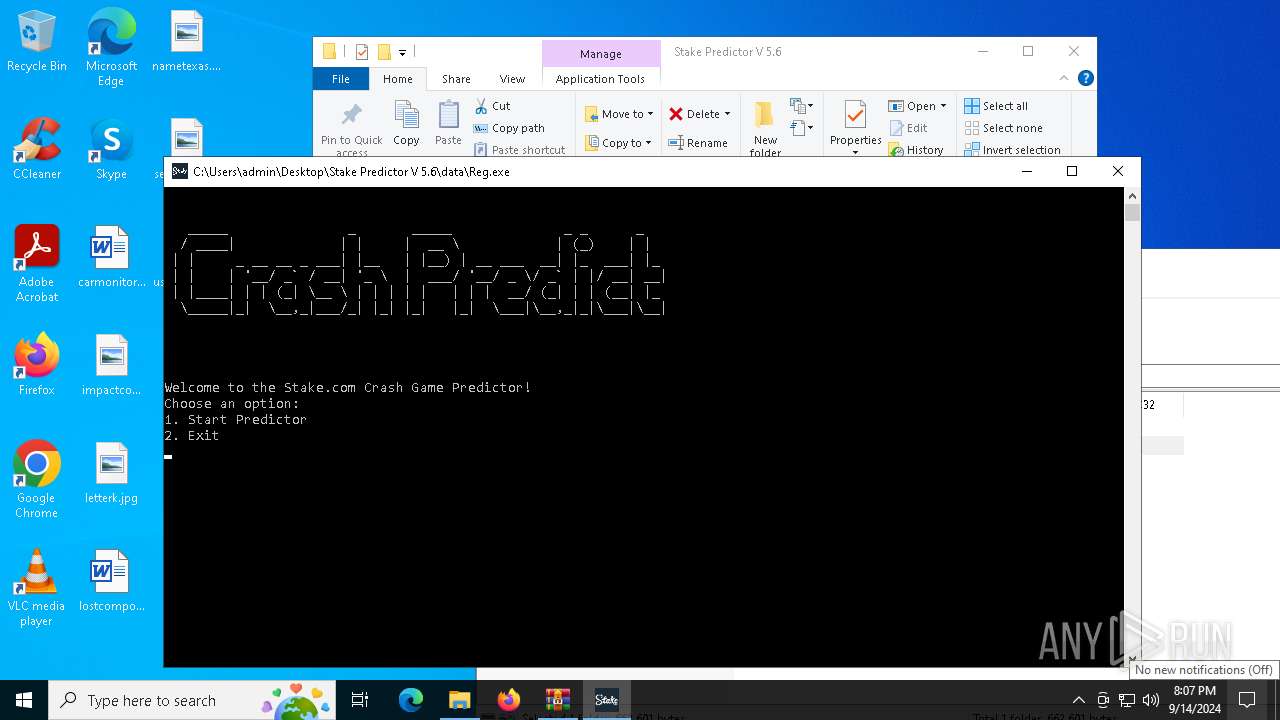
XWorm
(PID) Process(876) powershell.exe
C2elaablibeh.ddnsgeek.com:777
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop name0SOURCE0
MutexEy1WKEpbD0m3kx4K
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:01 02:52:12 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Stake Predictor V 5.6/ |
Total processes
147
Monitored processes
85
Malicious processes
4
Suspicious processes
68
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 476 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p -s LSM | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
XWorm(PID) Process(876) powershell.exe C2elaablibeh.ddnsgeek.com:777 Keys AES<123456789> Options Splitter<Xwormmm> Sleep time3 USB drop name0SOURCE0 MutexEy1WKEpbD0m3kx4K | |||||||||||||||
| 896 | C:\WINDOWS\system32\svchost.exe -k DcomLaunch -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | C:\WINDOWS\system32\svchost.exe -k RPCSS -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s gpsvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\System32\svchost.exe -k netsvcs -p -s Browser | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1192 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNoNetwork -p | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s NcbService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s TimeBrokerSvc | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 231
Read events
66 569
Write events
364
Delete events
298
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000702E8 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Stake Predictor V 5.6.zip | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4692) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1316) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{C2AF3602-9179-4BAE-85B3-74A4EF5CF51F} |
| Operation: | write | Name: | DynamicInfo |
Value: 03000000BDCB09F80A59DA0133966BBDE106DB0100000000000000007CBD9FC0E106DB01 | |||
| (PID) Process: | (1316) svchost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Schedule\TaskCache\Tasks\{F93AD50A-2FB2-4A34-88EF-786903C710ED} |
| Operation: | write | Name: | DynamicInfo |
Value: 03000000C09775A51C59DA0133966BBDE106DB0100000000054000809ED900C2E106DB01 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C00000012000000000000006300610072006D006F006E00690074006F0072002E007200740066003E00200020000000190000000000000069006D00700061006300740063006F006D006D0075006E00690074006900650073002E006A00700067003E002000200000000F000000000000006C00650074007400650072006B002E006A00700067003E0020002000000016000000000000006C006F007300740063006F006D0070006F006E0065006E00740073002E007200740066003E0020002000000011000000000000006E0061006D006500740065007800610073002E006A00700067003E002000200000001300000000000000730065006300740069006F006E006500760065006E002E0070006E0067003E002000200000001200000000000000750073006500670061006C006C006500720079002E007200740066003E0020002000000019000000000000005300740061006B006500200050007200650064006900630074006F00720020005600200035002E0036003E005C0020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001000000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000008040000040400F00 | |||
Executable files
3
Suspicious files
29
Text files
21
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1620 | svchost.exe | C:\Windows\Prefetch\TASKHOSTW.EXE-3E0B74C8.pf | binary | |
MD5:347FAB08B29482090116C62F19C4CAF0 | SHA256:F3D7F2D1BE439C17082276C5704DEA719357A28DC5D59267C6D16F8348510A32 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4692.27643\Stake Predictor V 5.6\data\Reg.dll | text | |
MD5:CFDC06989DB1E858A3A48DE991424B8A | SHA256:DF2F7A635EBE6A7D38290C0307046D201C1AE102F26BBB7C1456849F246FD1E8 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\HOST.EXE-F5D74C61.pf | binary | |
MD5:05127B9A37F0F9590E948FD32CA2F273 | SHA256:E0DE7E84D7A09133299E0EF9030E42531DDAC3999EA5CCDDDEF173C90D6E89F8 | |||
| 6016 | Stake Bot.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_k0okb4vi.hlb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-AD0331FB.pf | binary | |
MD5:0D77360E116459254093E855D07C2BF3 | SHA256:FAECE57D9356BA371F30EF8ADAD6F3964CE0F342FFCC1646E225B40C46FF3DDF | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4692.27643\Stake Predictor V 5.6\Stake Bot.exe | executable | |
MD5:0EBEB0FF3A23DD295F906DD41AC9B39A | SHA256:FFC4FA30E484C0C9276D9C238D73AABA1F54FE42FE9E14719F89FD51FD54C4F3 | |||
| 4692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4692.27643\Stake Predictor V 5.6\data\Reg.data | executable | |
MD5:F64CA5AE585DD9430B129D86C26CC43C | SHA256:B115F53262A07B5860E49ED0F729828DDA650B1E612C4DC03413F21BF4B9EE3B | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\WINRAR.EXE-94E7D80C.pf | binary | |
MD5:BC3CE9F716E9352C9D43D979B76F9CC4 | SHA256:C28AFAF7995BAE85A8AAC8132846463A136200CC0E1E099213CA7C62EB13972A | |||
| 1620 | svchost.exe | C:\Windows\Prefetch\SVCHOST.EXE-6C525542.pf | binary | |
MD5:F88EC1433358458C3C6A9F816334B2AA | SHA256:689EC6CB933D05E7BC4B49AE9163A47294A25E85231B2C2E76F77C8CF18C2D52 | |||
| 4552 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:59CA8FB18C99B00BA424D9D698F9EC6A | SHA256:6153A553D824B1C8CA0623EC469F7968FA1091905911FBE6B3D8FCE18811DB9F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
35
DNS requests
16
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7128 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6016 | Stake Bot.exe | GET | 200 | 52.6.97.148:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQg3SSkKA74hABkhmlBtJTz8w3hlAQU%2BWC71OPVNPa49QaAJadz20ZpqJ4CEEJLalPOx2YUHCpjsaUcQQQ%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.6.97.148:80 | http://ocsps.ssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSoEwb5tith0jIBy9frSyNGB1lsAAQUNr1J%2FzEs669qQP6ZwBbtuvxI3V8CEC5PS6JcFeO7CIfoudHuK%2F8%3D | unknown | — | — | whitelisted |
1404 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4252 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4252 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7128 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6192 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7128 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
7128 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 20.7.2.167:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6016 | Stake Bot.exe | 52.6.97.148:80 | ocsps.ssl.com | AMAZON-AES | US | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsps.ssl.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
elaablibeh.ddnsgeek.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.ddnsgeek .com Domain |
13 ETPRO signatures available at the full report