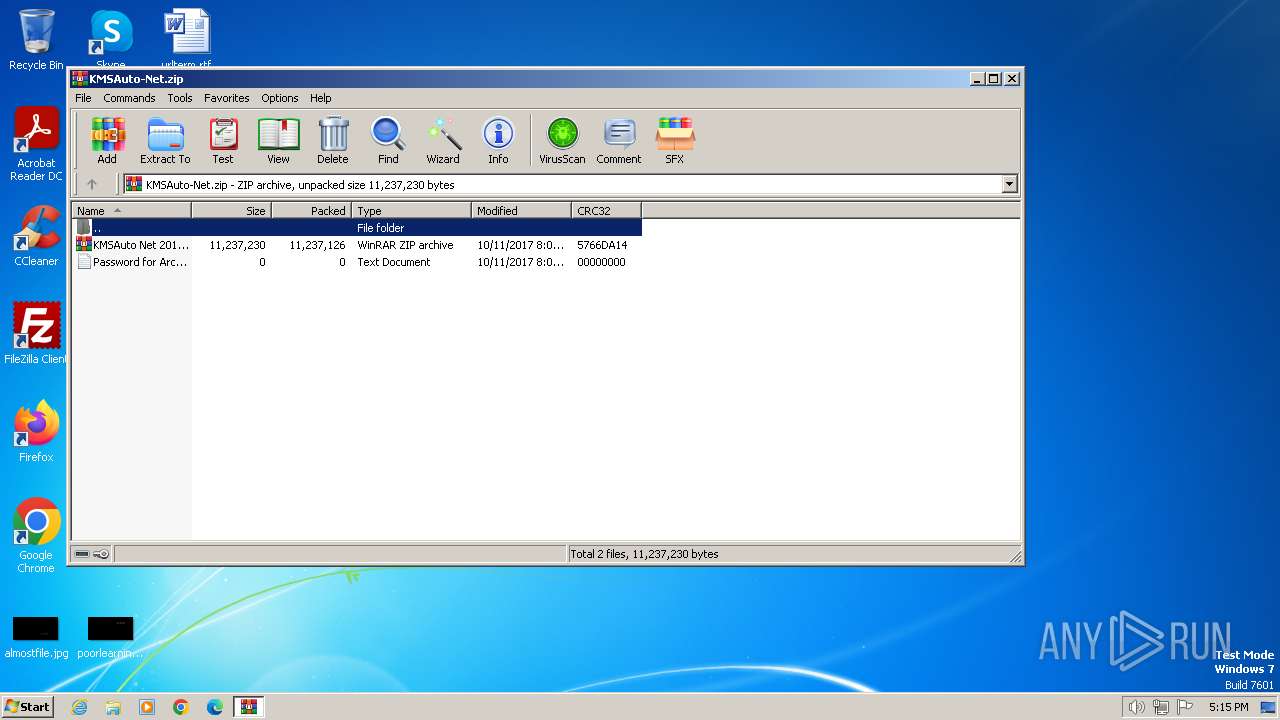
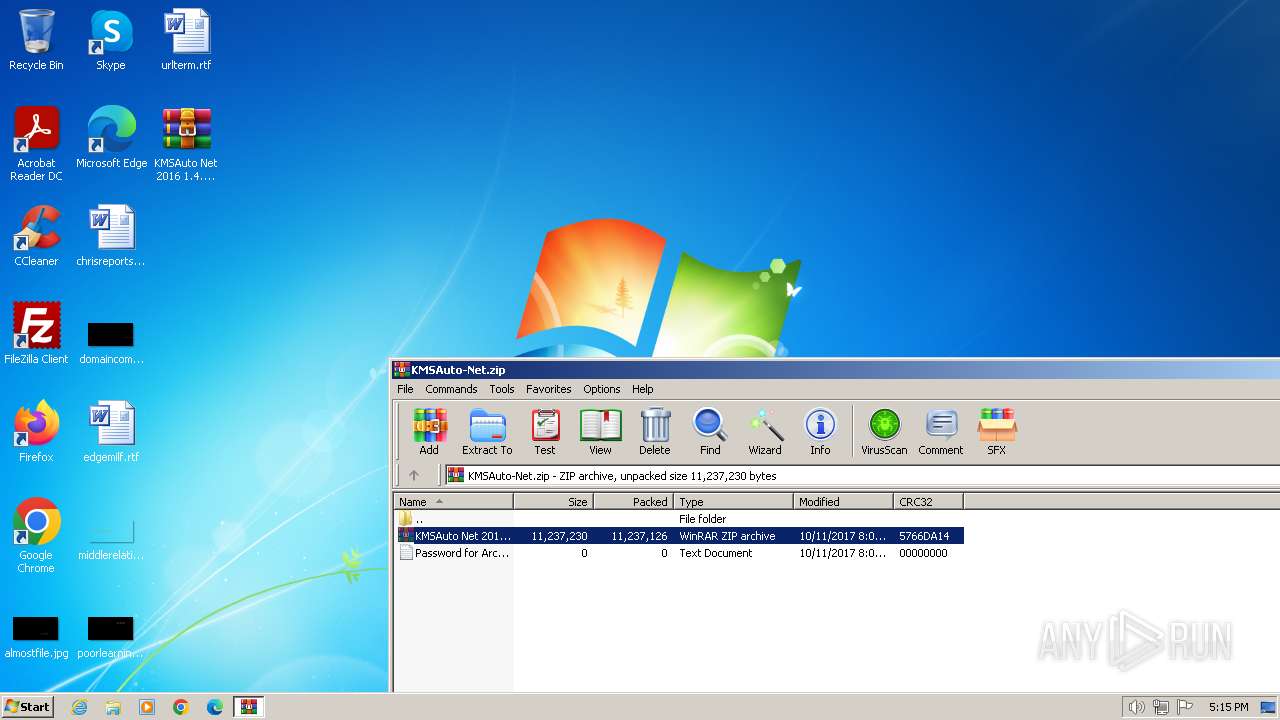
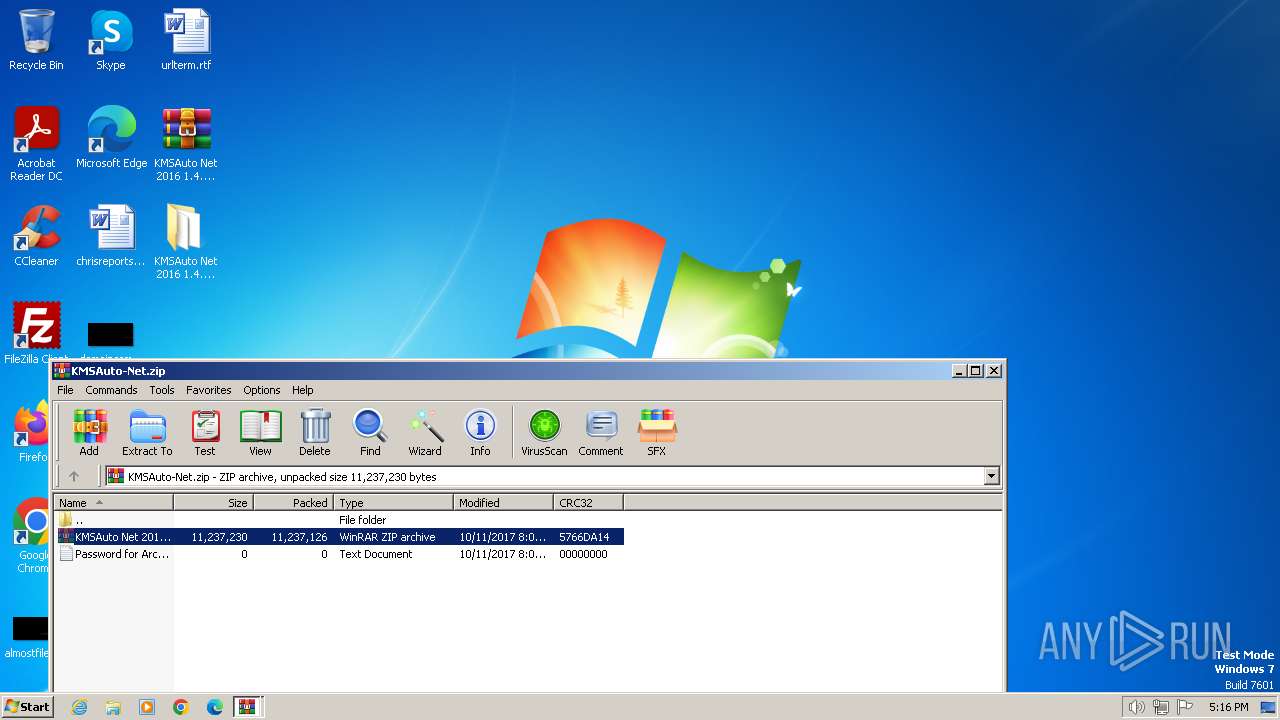
| File name: | KMSAuto-Net.zip |
| Full analysis: | https://app.any.run/tasks/68d4dfac-e3e3-4fe8-b4a7-d0750e9a5c6e |
| Verdict: | Malicious activity |
| Analysis date: | March 18, 2024, 17:14:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 386CB87E6430D914820D793DB19D7D33 |
| SHA1: | 160A3788D24787FBF1C7579AC2A5DA2D0AE8E25B |
| SHA256: | D4230CAE5C3E1B11FCA61A711E7F3886088F6728858108A6811670AA3616A57B |
| SSDEEP: | 196608:qpAtZ+U7OeubvGx9Y9oFMmtcdV0wvnZDsuKYqCVtIlehIuoOCYgM2cXNAOQ8JWcC:qpesfvuw2FMmKwanBsuYLu8Yg/Pl8JWJ |
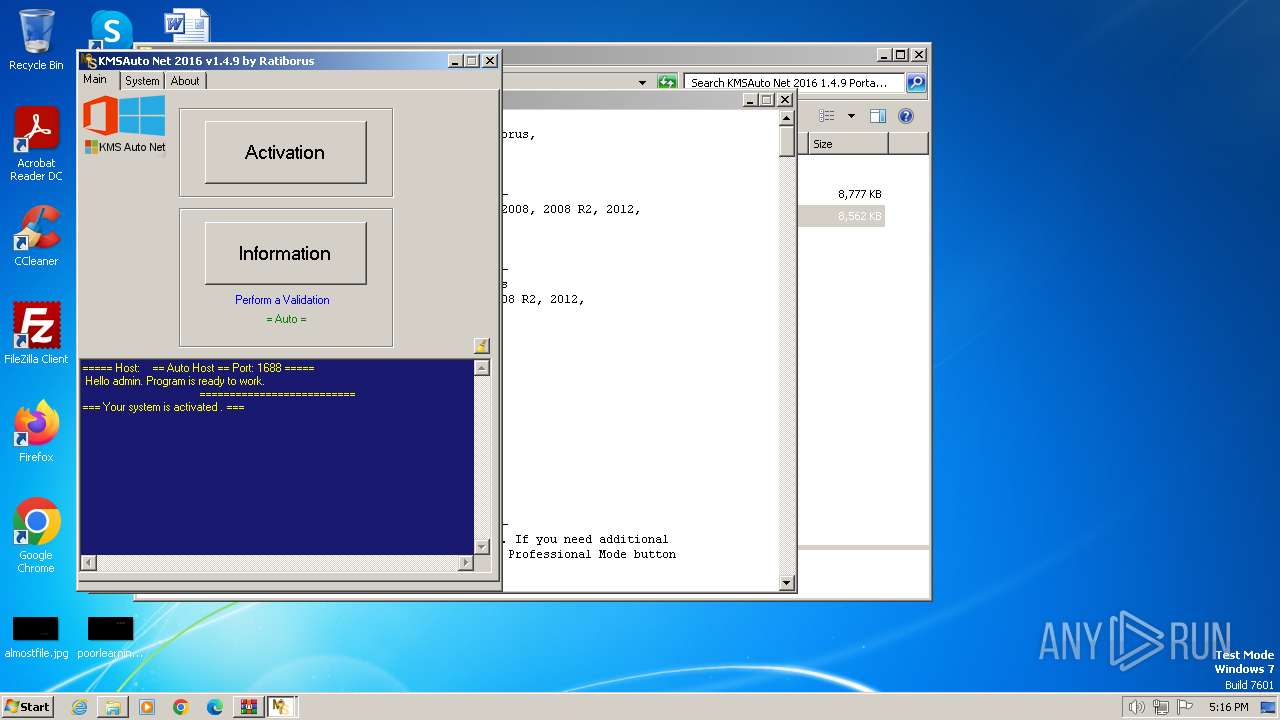
MALICIOUS
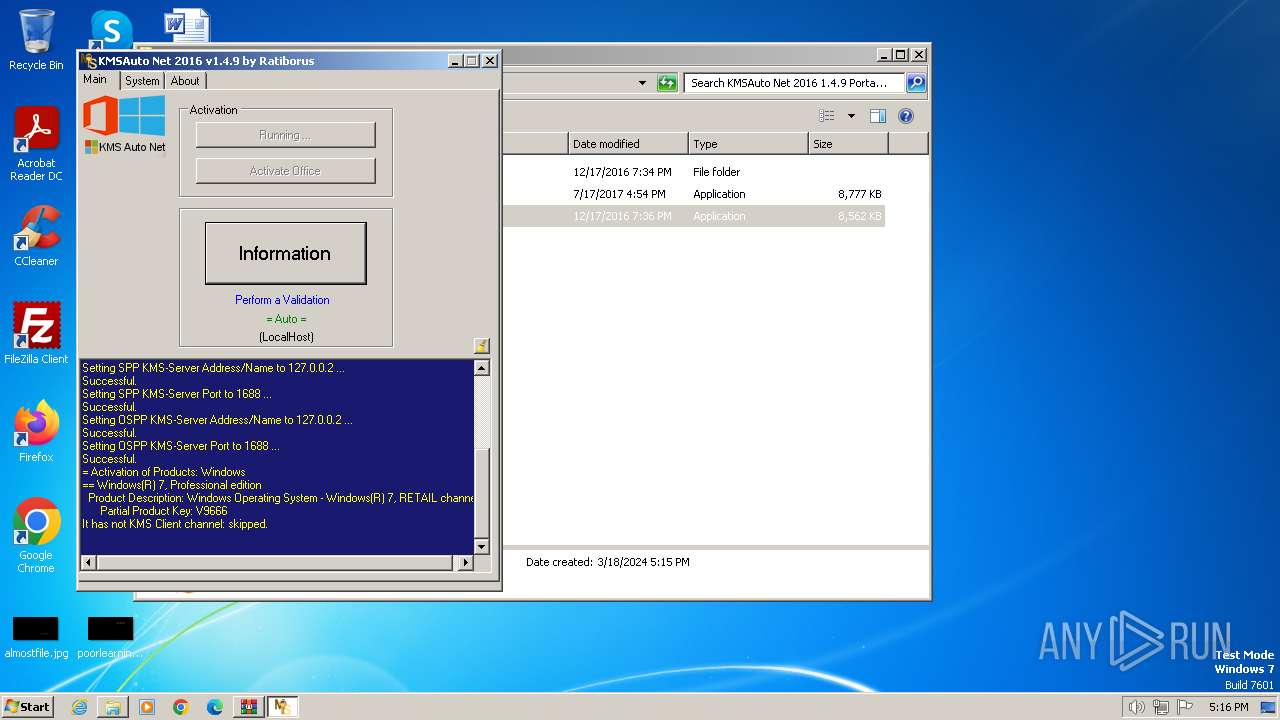
Drops the executable file immediately after the start
- KMSAuto Net.exe (PID: 2560)
- AESDecoder.exe (PID: 3592)
- bin.dat (PID: 884)
- bin_x86.dat (PID: 3860)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 3936)
- cmd.exe (PID: 3708)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3936)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 2560)
- cmd.exe (PID: 3708)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 2560)
Starts application with an unusual extension
- cmd.exe (PID: 2556)
- cmd.exe (PID: 3568)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 2560)
Executable content was dropped or overwritten
- KMSAuto Net.exe (PID: 2560)
- bin.dat (PID: 884)
- AESDecoder.exe (PID: 3592)
- bin_x86.dat (PID: 3860)
Drops a system driver (possible attempt to evade defenses)
- bin_x86.dat (PID: 3860)
Process drops legitimate windows executable
- bin_x86.dat (PID: 3860)
Executes as Windows Service
- KMSSS.exe (PID: 3704)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 2560)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 2560)
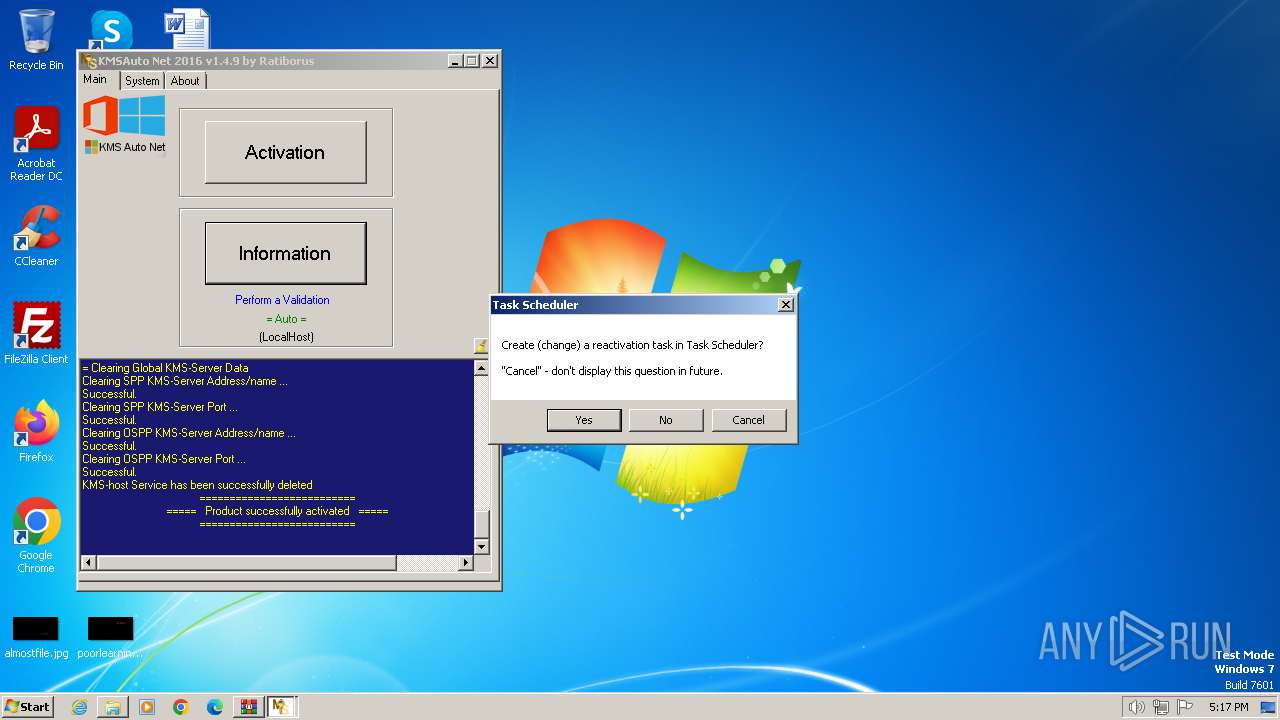
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 2560)
Starts SC.EXE for service management
- KMSAuto Net.exe (PID: 2560)
Reads the date of Windows installation
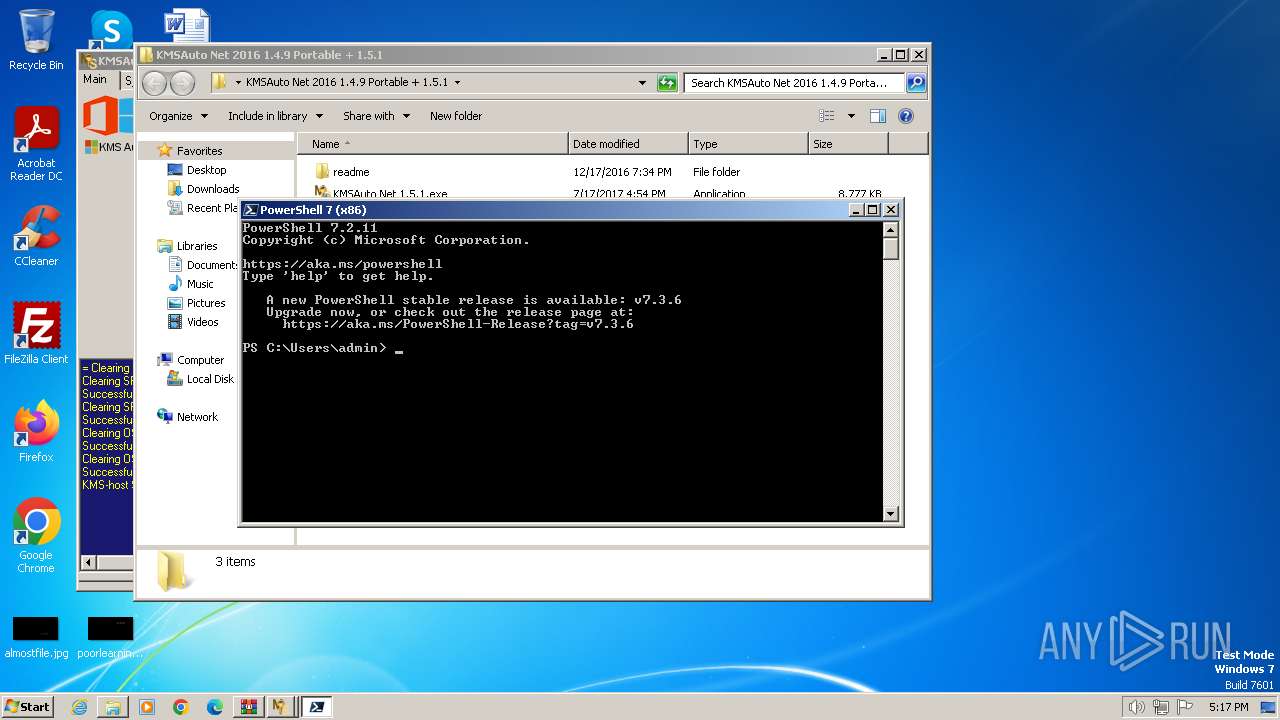
- pwsh.exe (PID: 3676)
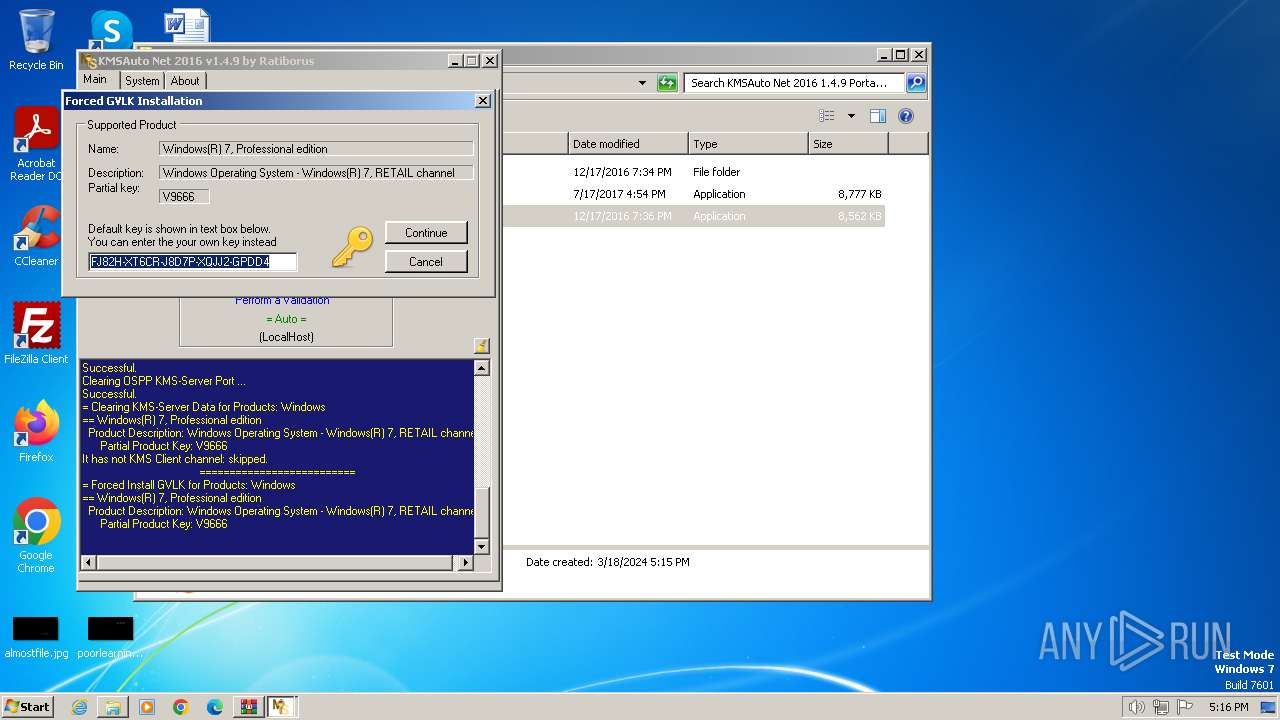
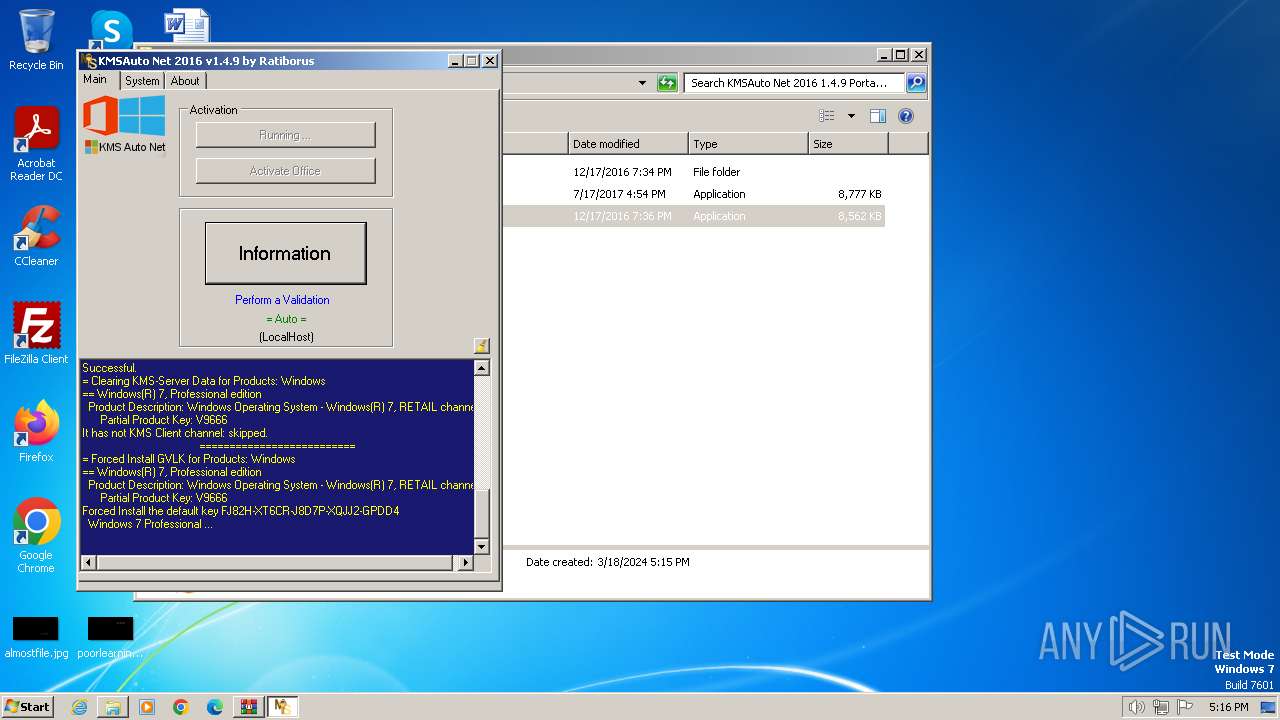
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 952)
- KMSAuto Net.exe (PID: 2560)
INFO
Checks supported languages
- KMSAuto Net 1.5.1.exe (PID: 1336)
- KMSAuto Net 1.5.1.exe (PID: 2632)
- KMSAuto Net.exe (PID: 2560)
- AESDecoder.exe (PID: 3592)
- bin_x86.dat (PID: 3860)
- bin.dat (PID: 884)
- KMSSS.exe (PID: 3704)
- pwsh.exe (PID: 3676)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2208)
Reads the machine GUID from the registry
- KMSAuto Net 1.5.1.exe (PID: 1336)
- KMSAuto Net 1.5.1.exe (PID: 2632)
- KMSAuto Net.exe (PID: 2560)
- KMSSS.exe (PID: 3704)
Reads the computer name
- KMSAuto Net 1.5.1.exe (PID: 1336)
- KMSAuto Net 1.5.1.exe (PID: 2632)
- KMSAuto Net.exe (PID: 2560)
- KMSSS.exe (PID: 3704)
- pwsh.exe (PID: 3676)
Manual execution by a user
- KMSAuto Net 1.5.1.exe (PID: 2632)
- KMSAuto Net 1.5.1.exe (PID: 3404)
- KMSAuto Net 1.5.1.exe (PID: 1336)
- KMSAuto Net 1.5.1.exe (PID: 2596)
- KMSAuto Net.exe (PID: 1232)
- KMSAuto Net.exe (PID: 2560)
- pwsh.exe (PID: 3676)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2208)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 2560)
Reads Environment values
- KMSAuto Net.exe (PID: 2560)
Reads product name
- KMSAuto Net.exe (PID: 2560)
Creates files in the program directory
- cmd.exe (PID: 2868)
- KMSAuto Net.exe (PID: 2560)
- AESDecoder.exe (PID: 3592)
- bin.dat (PID: 884)
- bin_x86.dat (PID: 3860)
- KMSSS.exe (PID: 3704)
Reads Microsoft Office registry keys
- KMSAuto Net.exe (PID: 2560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2017:10:11 22:06:02 |
| ZipCRC: | 0x5766da14 |
| ZipCompressedSize: | 11237126 |
| ZipUncompressedSize: | 11237230 |
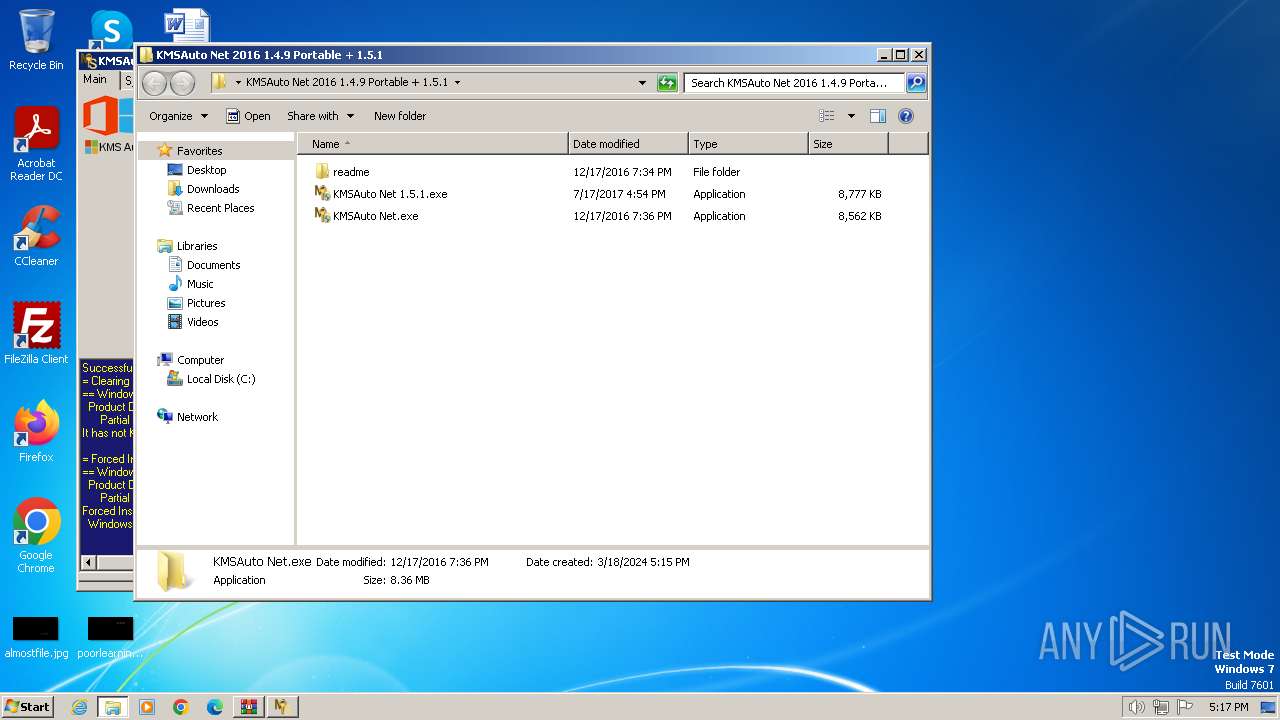
| ZipFileName: | KMSAuto Net 2016 1.4.9 Portable + 1.5.1.zip |
Total processes
135
Monitored processes
49
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | C:\Windows\system32\cmd.exe /c netstat -ano | find ":1688 " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 840 | "sc.exe" stop KMSEmulator | C:\Windows\System32\sc.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 884 | bin.dat -y -pkmsauto | C:\ProgramData\KMSAuto\bin.dat | cmd.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: HIGH Description: 7z Console SFX Exit code: 0 Version: 15.14 Modules
| |||||||||||||||
| 952 | C:\Windows\System32\cmd.exe /D /c reg.exe DELETE HKLM\SYSTEM\CurrentControlSet\Services\KMSEmulator /f | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 984 | cmd /c md "C:\Users\admin\AppData\Local\MSfree Inc" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | "C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\KMSAuto Net.exe" | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\KMSAuto Net.exe | — | explorer.exe | |||||||||||
User: admin Company: MSFree Inc. Integrity Level: MEDIUM Description: KMSAuto Net Exit code: 3221226540 Version: 1.4.9 Modules
| |||||||||||||||
| 1288 | C:\Windows\System32\cmd.exe /D /c AESDecoder.exe | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1308 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55C92734-D682-4D71-983E-D6EC3F16059F" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\KMSAuto Net 1.5.1.exe" | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\KMSAuto Net 1.5.1.exe | explorer.exe | ||||||||||||
User: admin Company: MSFree Inc. Integrity Level: HIGH Description: KMSAuto Net Exit code: 0 Version: 1.5.1 Modules
| |||||||||||||||
| 1728 | C:\Windows\System32\reg delete "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform\0FF1CE15-A989-479D-AF46-F275C6370663" /f | C:\Windows\System32\reg.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
16 764
Read events
16 475
Write events
281
Delete events
8
Modification events
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto-Net.zip | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
17
Suspicious files
10
Text files
16
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3936 | WinRAR.exe | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1.zip | compressed | |
MD5:146C2759347E0D52625CCB4076E97EBB | SHA256:322E6E04DB88AADBA5EF0C92CA471F2A11046C1884DDE3D3FA05C35F3418EF36 | |||
| 2208 | WinRAR.exe | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\readme\readme_bg.txt | text | |
MD5:D6761E218D57B85236345F74EA44A684 | SHA256:E03107D2DEC7EB59033B4D0CACF9DD320C3BE1D9389295F87F069E667F138201 | |||
| 3936 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3936.11990\KMSAuto Net 2016 1.4.9 Portable + 1.5.1.zip | compressed | |
MD5:146C2759347E0D52625CCB4076E97EBB | SHA256:322E6E04DB88AADBA5EF0C92CA471F2A11046C1884DDE3D3FA05C35F3418EF36 | |||
| 2584 | cmd.exe | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 2560 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\bin.dat | executable | |
MD5:2A96E417738225FA806A6EF275443BC8 | SHA256:839D31305D8FA842C832E8EC0F61D6BC575734449EB774B7C8DD79669594E25B | |||
| 884 | bin.dat | C:\ProgramData\KMSAuto\bin\AESDecoder.exe | executable | |
MD5:B90ED3E4DBB23A464723706F12C86065 | SHA256:8391D5B724D235BA52531D9A6D85E466382CE15CBD6BA97C4AD1278ED1F03BD7 | |||
| 884 | bin.dat | C:\ProgramData\KMSAuto\bin\TunMirror.exe.aes | binary | |
MD5:6D6E295744D3750355227EFD55824BE1 | SHA256:F67F0232100F7CC7E469DC14079EDF7D72EC25E48CA3B5AC9B40ED025F1BA0EF | |||
| 2208 | WinRAR.exe | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\readme\readme_fr.txt | text | |
MD5:474FB9BCC634EA9BC1F2B77382A0D03B | SHA256:D0B8BBE89016B3E05FF1C376C9A3CCE7CA2E4070BFFC11BFD9A91808B6DC060C | |||
| 2208 | WinRAR.exe | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\readme\readme_cn.txt | text | |
MD5:67FA7B665E63269A86043ABA1C462EFA | SHA256:752D7FF42C648AFAC4D40A418512DB6E49896FA24BB1949442DDF50FF64B01AA | |||
| 2208 | WinRAR.exe | C:\Users\admin\Desktop\KMSAuto Net 2016 1.4.9 Portable + 1.5.1\KMSAuto Net 1.5.1.exe | executable | |
MD5:93A3A8CE440197D31168FAC569082937 | SHA256:22EF521964080E77D7006F9341D720683FA98409361C62A7BC4FE81EC474B1B2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
3676 | pwsh.exe | 23.34.234.76:443 | aka.ms | Bezeq International | US | unknown |
3676 | pwsh.exe | 52.239.160.36:443 | pscoretestdata.blob.core.windows.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
Threats
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 3676. Message ID: [0x2509].
|