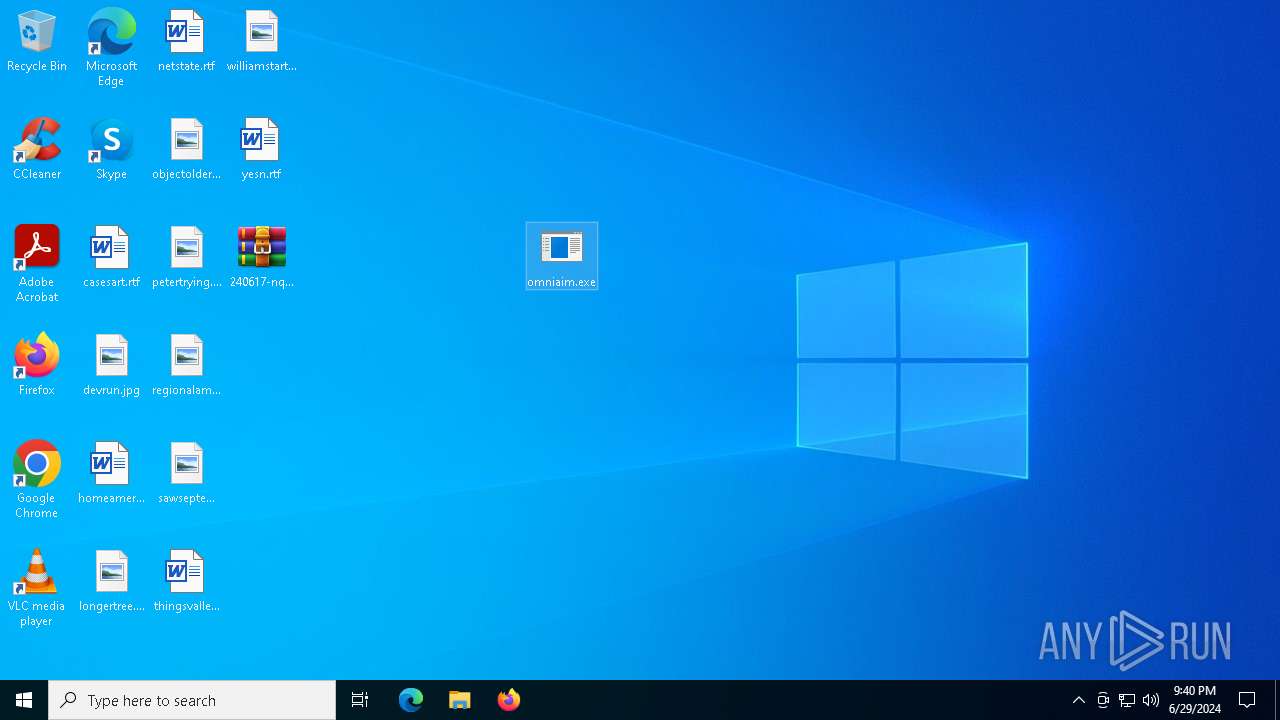
| File name: | 240617-nq98hayfja_pw_infected.zip |
| Full analysis: | https://app.any.run/tasks/22bd8abf-6c13-464e-9270-3b6afb74df07 |
| Verdict: | Malicious activity |
| Analysis date: | June 29, 2024, 21:39:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
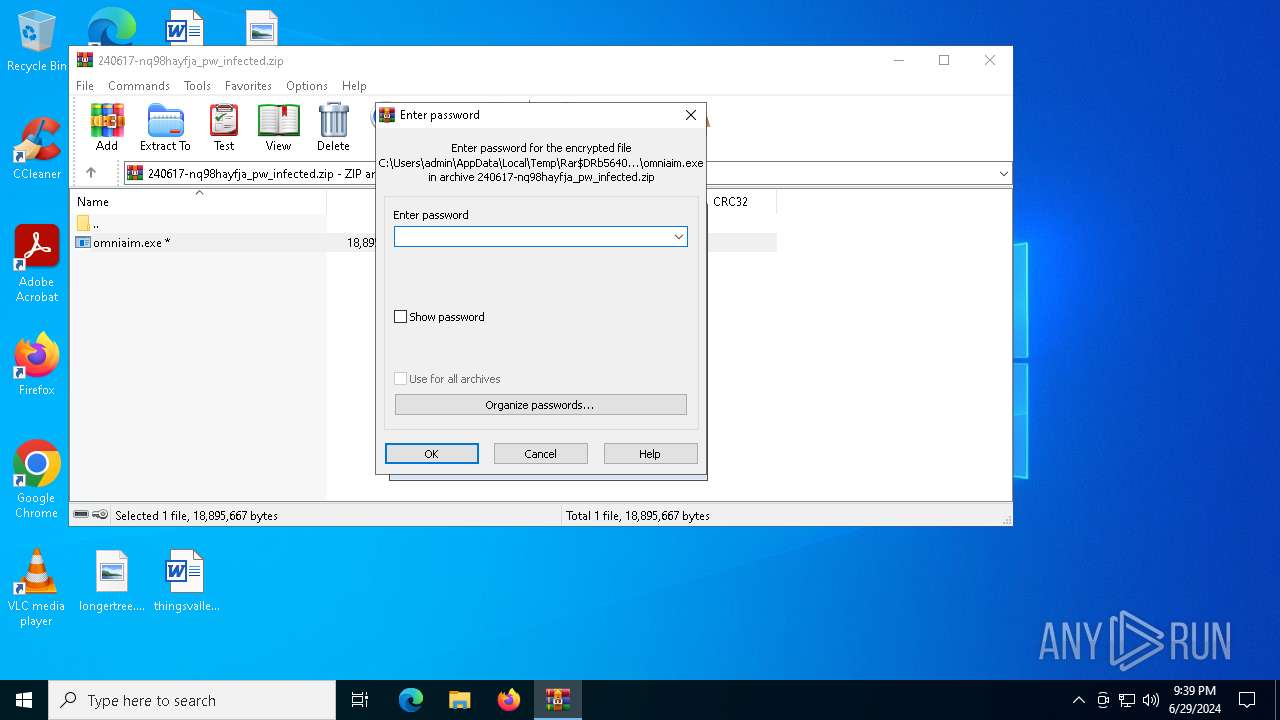
| File info: | Zip archive data, at least v2.0 to extract, compression method=AES Encrypted |
| MD5: | BC12A6054F9A16E5C00BF60B8B616E22 |
| SHA1: | C83F2BC681D37726BD7BE90E1A7317C60407E4D2 |
| SHA256: | D40F0BD161D0A280EE2595D7BE3949EF6636D52BE1AA1ABF8647EC53D365C8BC |
| SSDEEP: | 98304:bRCnBcUzbvULJOZga0EfGXMHRFkktlyOU9Doo7/XMLhAMZcxjE1wUm4fDwrBxCjw:muTDem20atN+DysdpRPeh+bcbIYE |
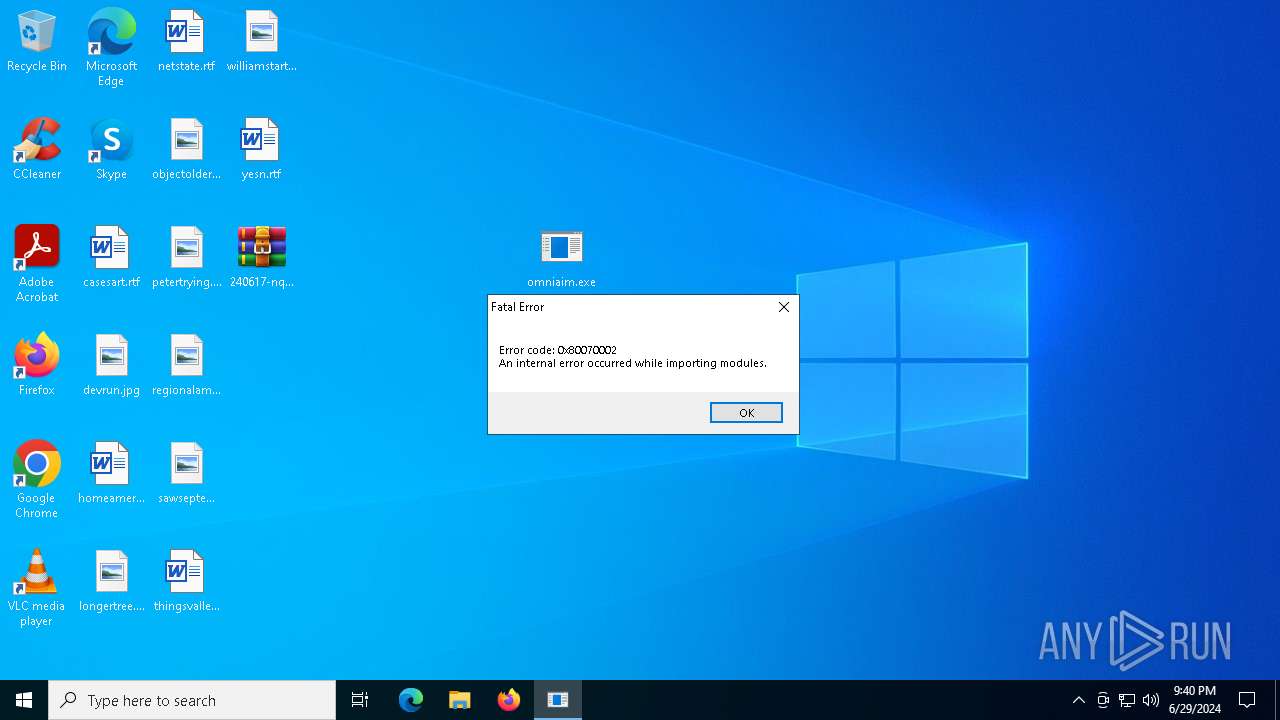
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 5640)
- omniaim.exe (PID: 3976)
Actions looks like stealing of personal data
- omniaim.exe (PID: 7072)
SUSPICIOUS
Process drops python dynamic module
- omniaim.exe (PID: 3976)
The process drops C-runtime libraries
- omniaim.exe (PID: 3976)
Process drops legitimate windows executable
- omniaim.exe (PID: 3976)
Application launched itself
- omniaim.exe (PID: 3976)
Accesses product unique identifier via WMI (SCRIPT)
- WMIC.exe (PID: 7012)
- WMIC.exe (PID: 6324)
Loads Python modules
- omniaim.exe (PID: 7072)
Starts CMD.EXE for commands execution
- omniaim.exe (PID: 7072)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 5480)
- cmd.exe (PID: 3940)
Uses NETSH.EXE to obtain data on the network
- cmd.exe (PID: 6176)
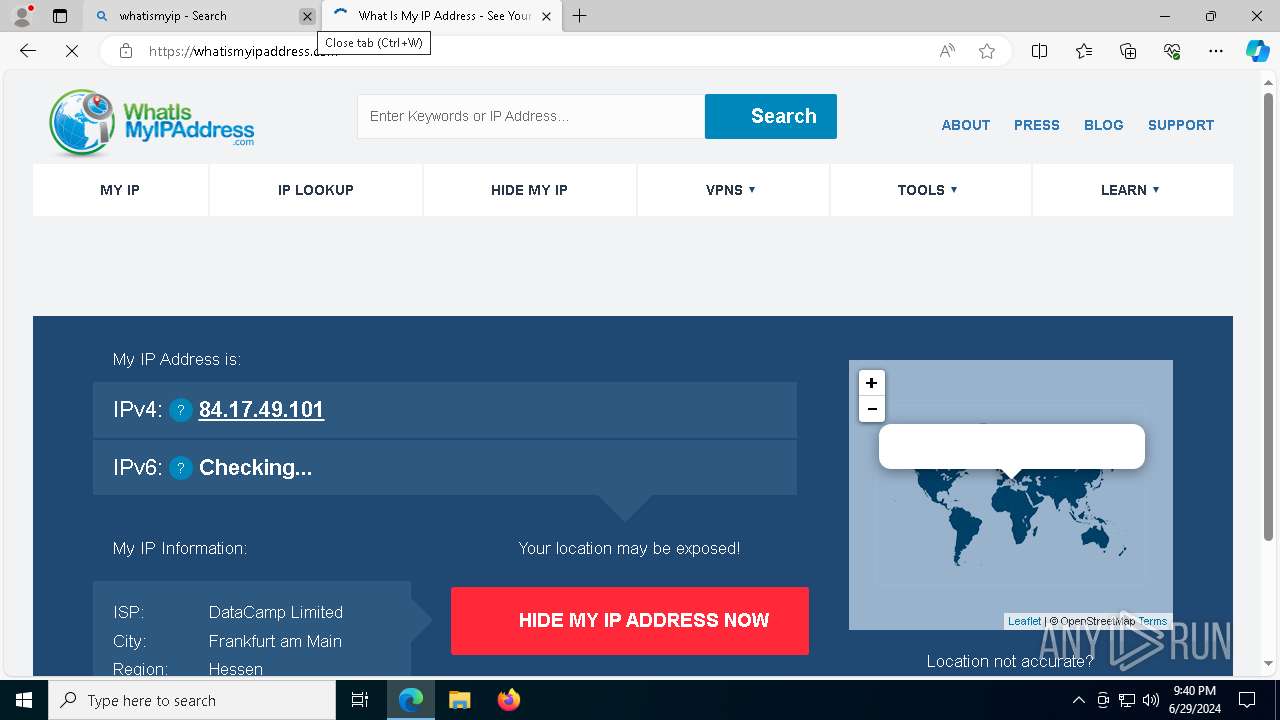
Checks for external IP
- omniaim.exe (PID: 7072)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 6468)
Accesses operating system name via WMI (SCRIPT)
- WMIC.exe (PID: 6796)
Uses WMIC.EXE to obtain CPU information
- omniaim.exe (PID: 7072)
Uses WMIC.EXE to obtain a list of video controllers
- cmd.exe (PID: 1848)
Accesses video controller name via WMI (SCRIPT)
- WMIC.exe (PID: 1204)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6864)
Executable content was dropped or overwritten
- omniaim.exe (PID: 3976)
INFO
Reads the computer name
- TextInputHost.exe (PID: 6596)
- identity_helper.exe (PID: 6152)
- omniaim.exe (PID: 3976)
- omniaim.exe (PID: 7072)
Manual execution by a user
- msedge.exe (PID: 5480)
- omniaim.exe (PID: 3976)
Checks supported languages
- TextInputHost.exe (PID: 6596)
- identity_helper.exe (PID: 6152)
- omniaim.exe (PID: 3976)
- omniaim.exe (PID: 7072)
Reads Microsoft Office registry keys
- msedge.exe (PID: 5480)
- msedge.exe (PID: 3868)
Application launched itself
- msedge.exe (PID: 3868)
- msedge.exe (PID: 5480)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5640)
Checks operating system version
- omniaim.exe (PID: 7072)
Reads the machine GUID from the registry
- omniaim.exe (PID: 7072)
Checks proxy server information
- omniaim.exe (PID: 7072)
Creates files or folders in the user directory
- omniaim.exe (PID: 7072)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7012)
- WMIC.exe (PID: 6796)
- WMIC.exe (PID: 6948)
- WMIC.exe (PID: 1204)
- WMIC.exe (PID: 700)
- WMIC.exe (PID: 6324)
Create files in a temporary directory
- omniaim.exe (PID: 7072)
- omniaim.exe (PID: 3976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 13509193 |
| ZipUncompressedSize: | 18895667 |
| ZipFileName: | omniaim.exe |
Total processes
199
Monitored processes
64
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 700 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=6128 --field-trial-handle=2380,i,1536282692021903086,10425209583387413003,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 700 | wmic computersystem get totalphysicalmemory | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | wmic path win32_VideoController get name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1848 | C:\WINDOWS\system32\cmd.exe /c "wmic path win32_VideoController get name" | C:\Windows\System32\cmd.exe | — | omniaim.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2012 | netsh wlan show profiles | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5868 --field-trial-handle=2380,i,1536282692021903086,10425209583387413003,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4900 --field-trial-handle=2480,i,10244165502292110235,6047067323583613327,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3628 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3680 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4680 --field-trial-handle=2480,i,10244165502292110235,6047067323583613327,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 15 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
19 129
Read events
19 053
Write events
74
Delete events
2
Modification events
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\240617-nq98hayfja_pw_infected.zip | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (5640) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
99
Suspicious files
531
Text files
147
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1b0cbe.TMP | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1b0cbe.TMP | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1b0cbe.TMP | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF1b0cbe.TMP | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1b0cce.TMP | — | |
MD5:— | SHA256:— | |||
| 5480 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
163
DNS requests
180
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1544 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
3672 | svchost.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3672 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6156 | msedge.exe | GET | 304 | 184.24.77.47:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
6156 | msedge.exe | GET | 304 | 69.192.161.44:80 | http://x1.i.lencr.org/ | unknown | — | — | unknown |
6156 | msedge.exe | GET | 304 | 69.192.161.44:80 | http://r3.i.lencr.org/ | unknown | — | — | unknown |
2392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2392 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
4756 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3672 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3652 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1320 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
1544 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
4656 | SearchApp.exe | 2.23.209.165:443 | th.bing.com | Akamai International B.V. | GB | unknown |
1060 | svchost.exe | 2.19.246.123:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6156 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6156 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
2168 | svchost.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |
6156 | msedge.exe | Device Retrieving External IP Address Detected | ET INFO External IP Lookup Domain in DNS Lookup (whatismyipaddress .com) |