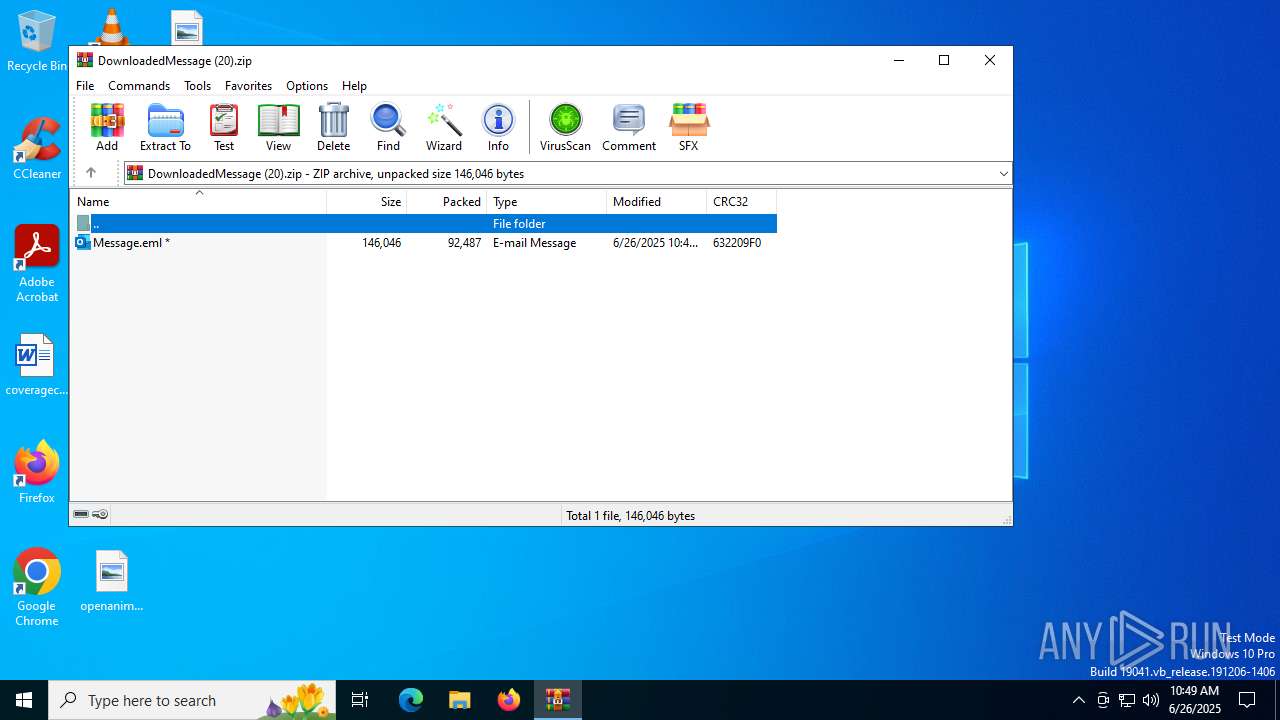
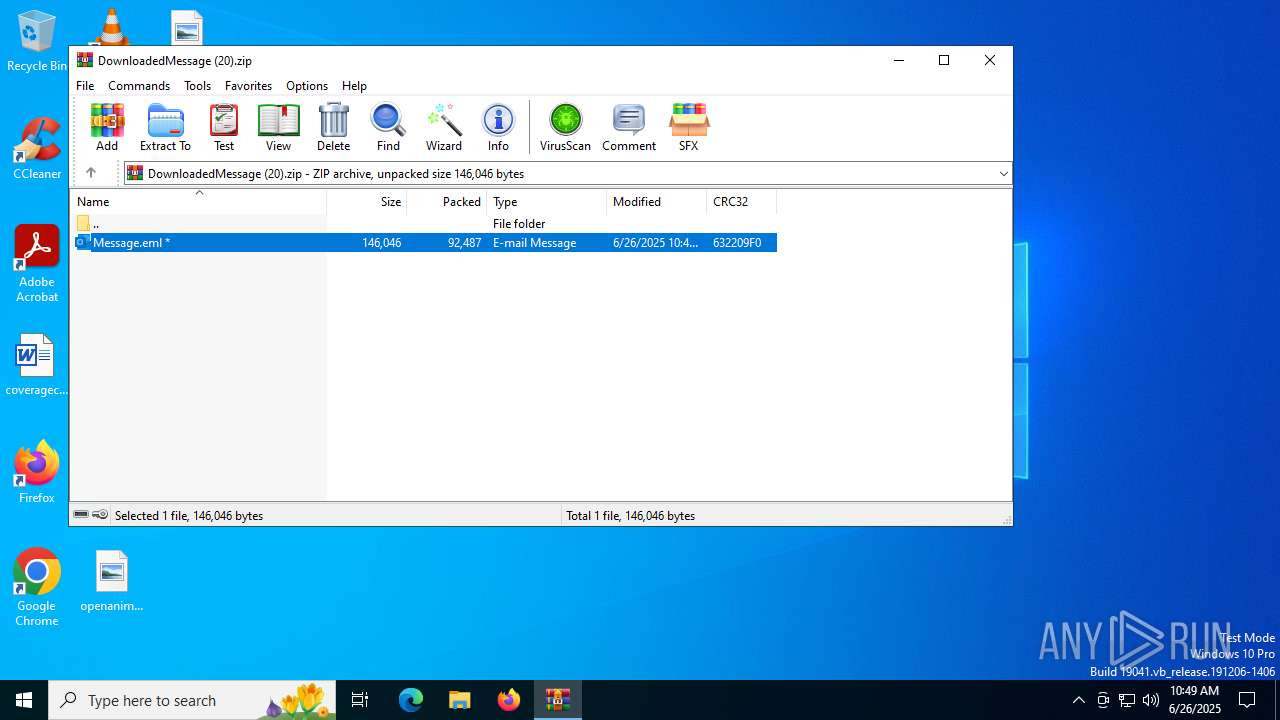
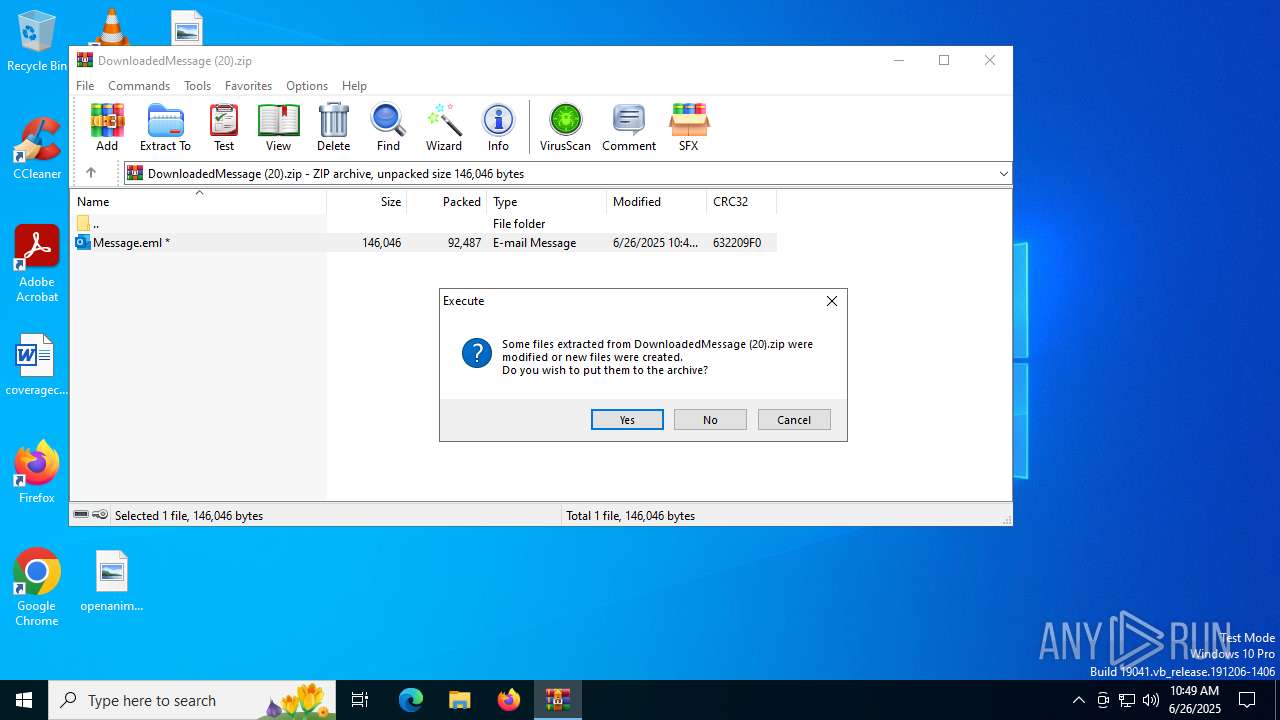
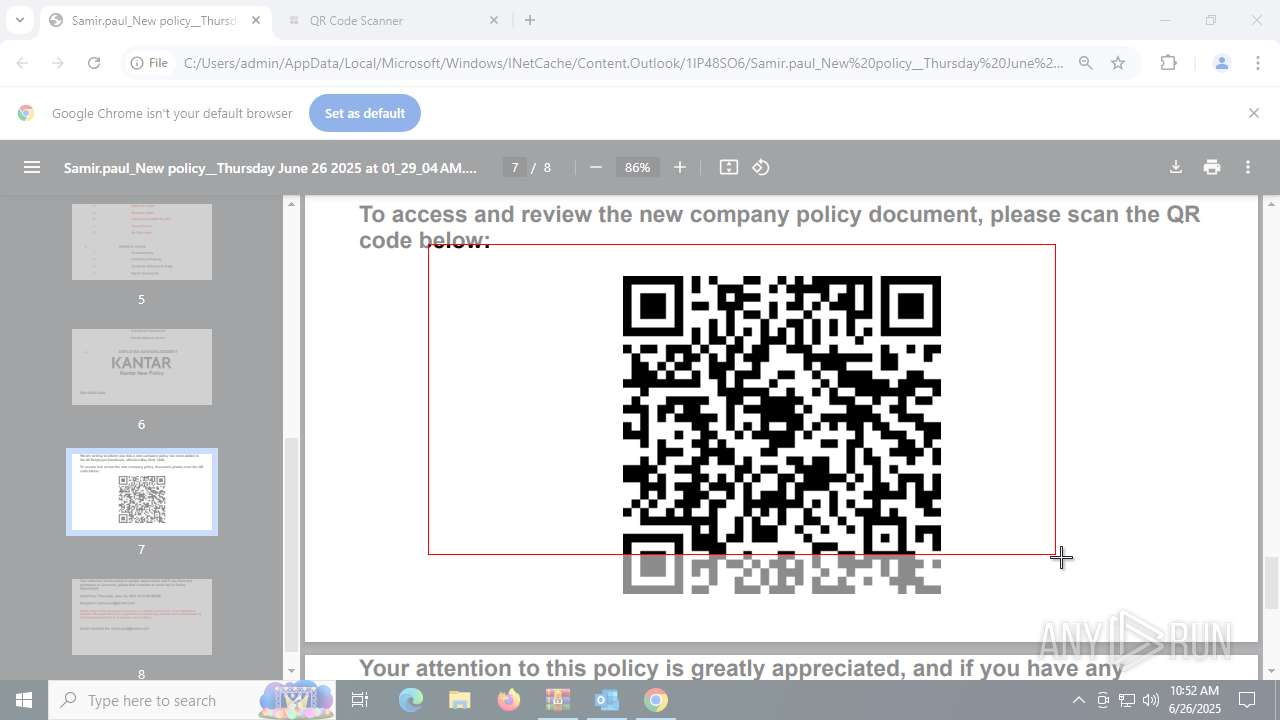
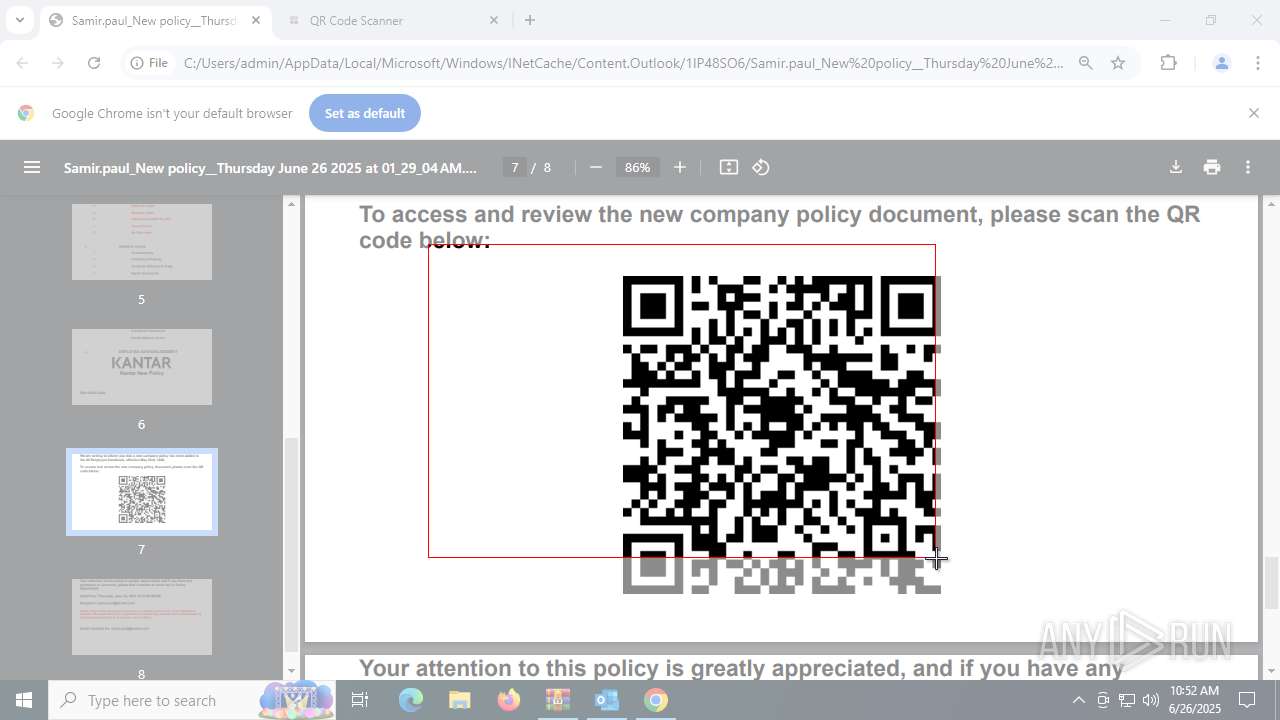
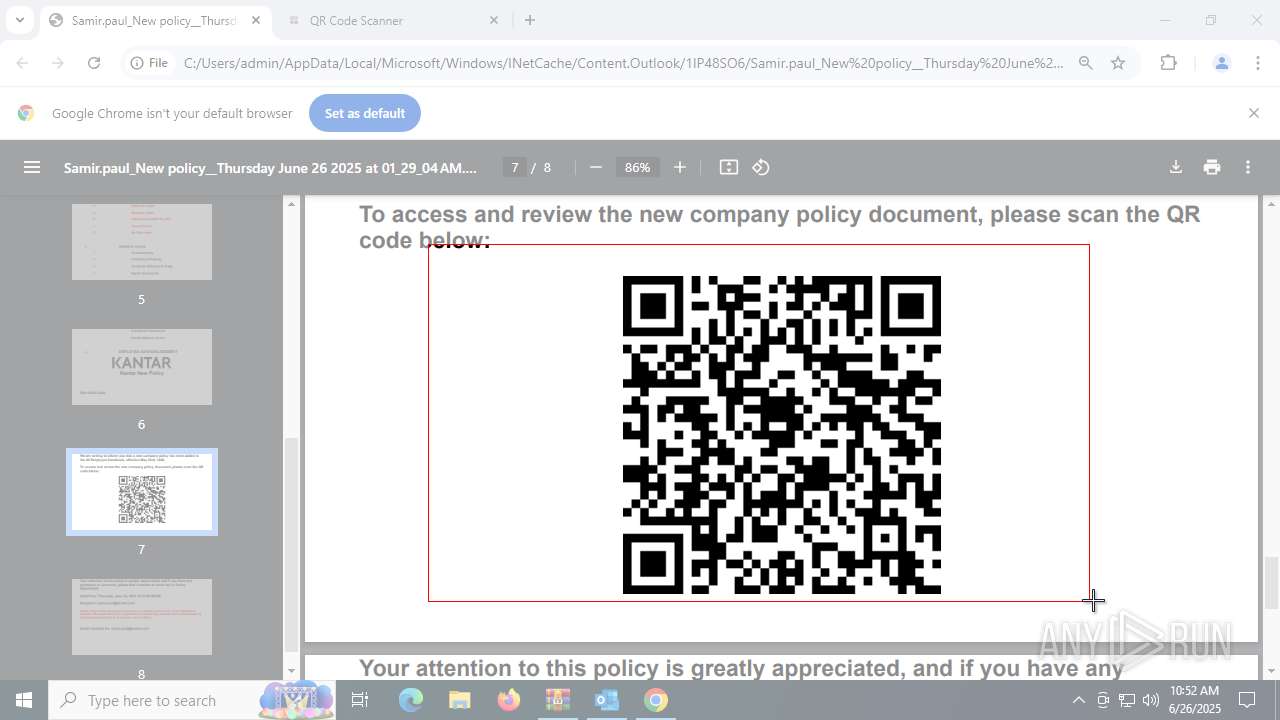
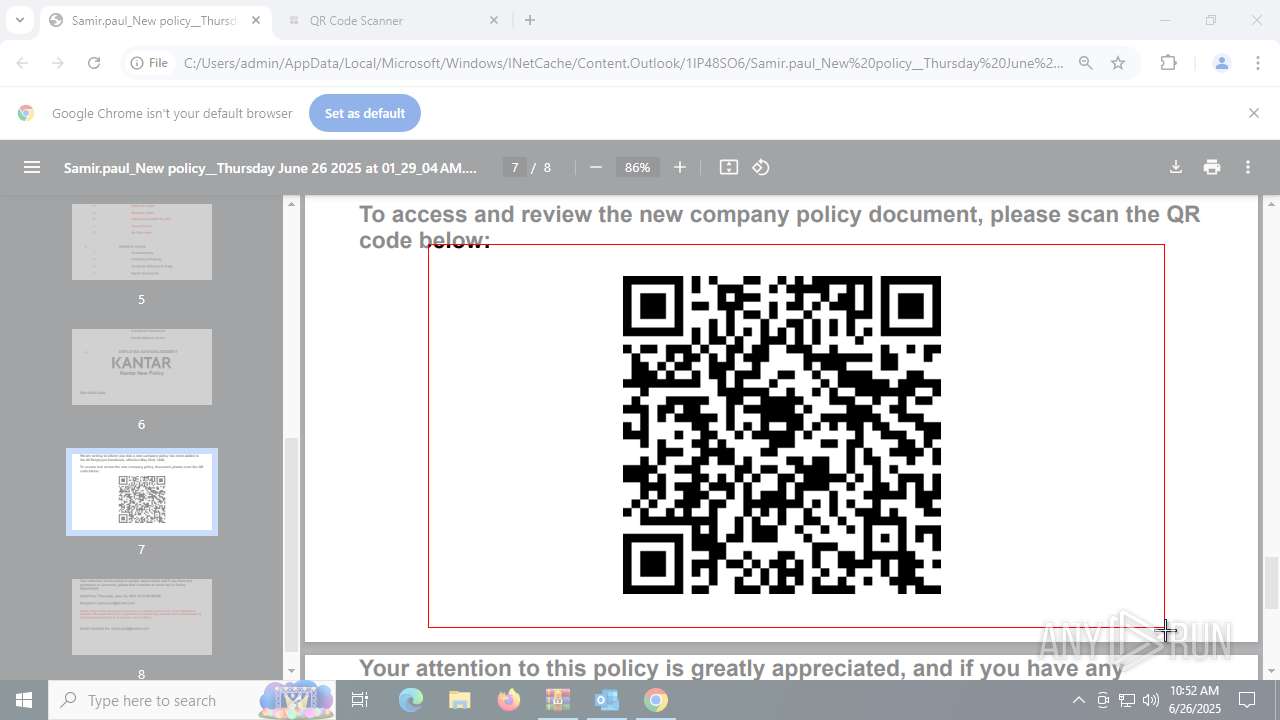
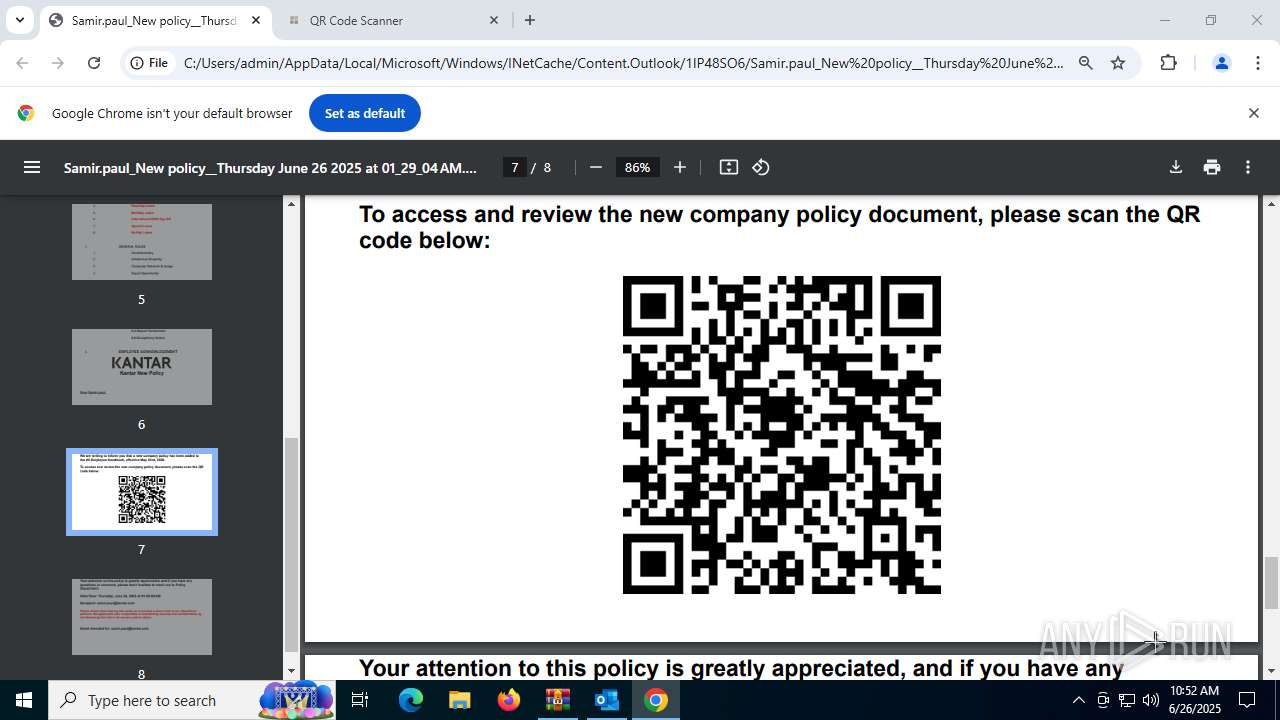
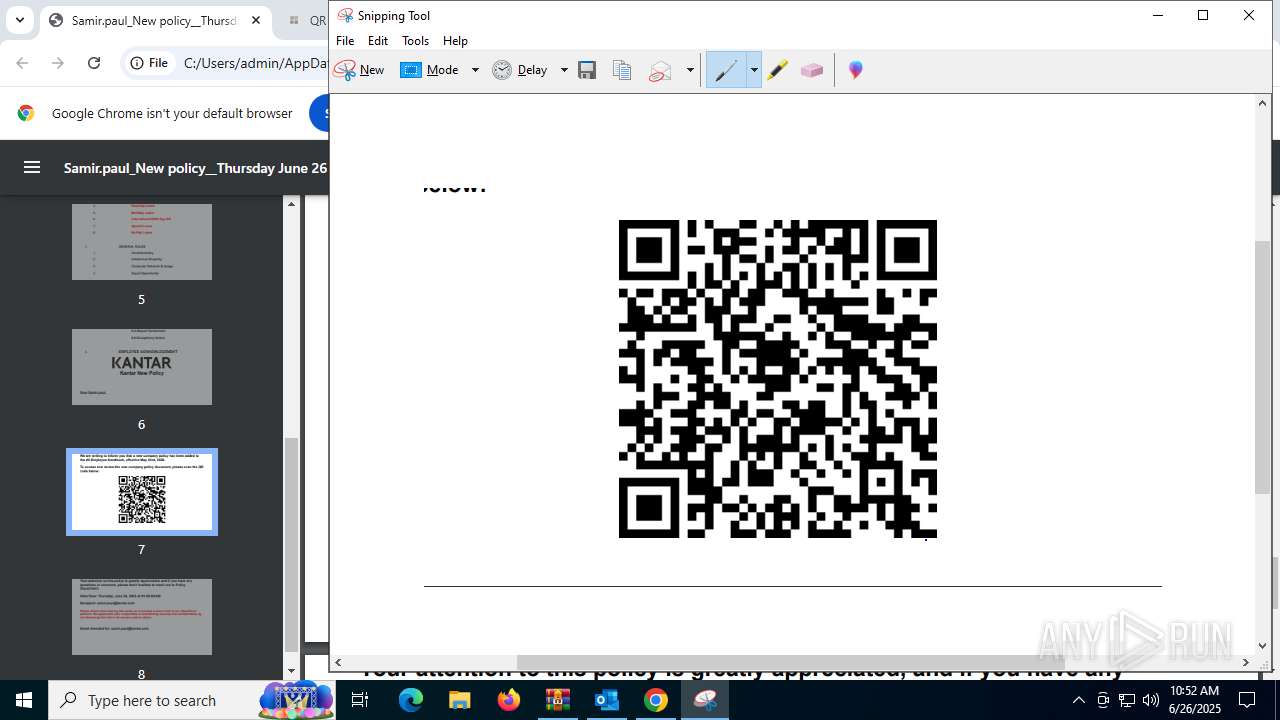
| File name: | DownloadedMessage (20).zip |
| Full analysis: | https://app.any.run/tasks/e48f8825-69ae-442e-aa68-5f8325f010b6 |
| Verdict: | Malicious activity |
| Analysis date: | June 26, 2025, 10:49:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 75983BE4F556F2326B9306C1179ACBF8 |
| SHA1: | BBA3E874F877C5F63973A97F7EC594B4D8E3D5F3 |
| SHA256: | D4094BECCCACCF0CEBE0A3B55BB6BC8D5DB74EB693ACF8AD8B4EA65151076D33 |
| SSDEEP: | 1536:8Ak0ejep5KFukHE2RpZJ115Xldk6o1QBnkX7xIb5jIiVJG/YjI3hOe:tajcKVFZ5pldk6o1QxkNIDXcYYhZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 3100)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3100)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3100)
- OpenWith.exe (PID: 4040)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4040)
Application launched itself
- chrome.exe (PID: 3788)
Checks proxy server information
- slui.exe (PID: 1984)
Reads the software policy settings
- slui.exe (PID: 1984)
Manual execution by a user
- SnippingTool.exe (PID: 7416)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:26 10:48:36 |
| ZipCRC: | 0x632209f0 |
| ZipCompressedSize: | 92487 |
| ZipUncompressedSize: | 146046 |
| ZipFileName: | Message.eml |
Total processes
197
Monitored processes
53
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=5760,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5792 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 640 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=3172,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=3184 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1100 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=6252,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6340 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1160 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5792,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=5720 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=43 --field-trial-handle=7264,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=7480 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --field-trial-handle=5832,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6048 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --string-annotations --enable-dinosaur-easter-egg-alt-images --disable-gpu-compositing --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=30 --field-trial-handle=6608,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6332 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
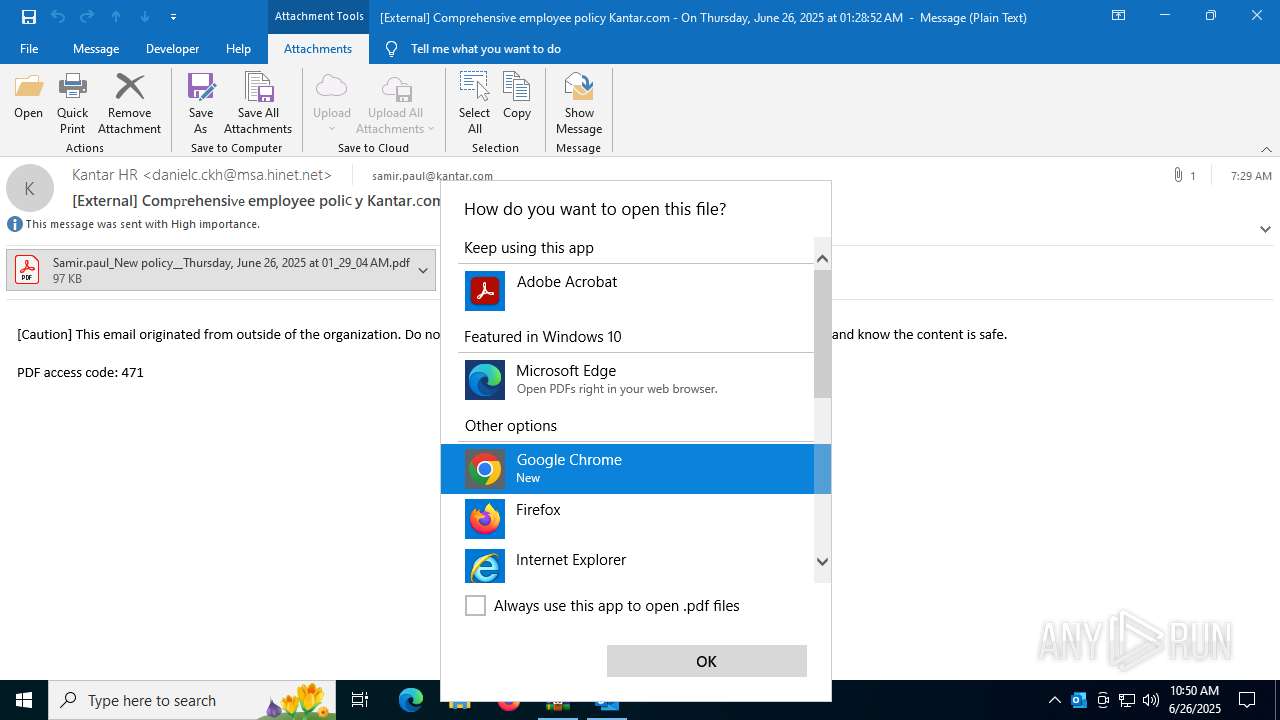
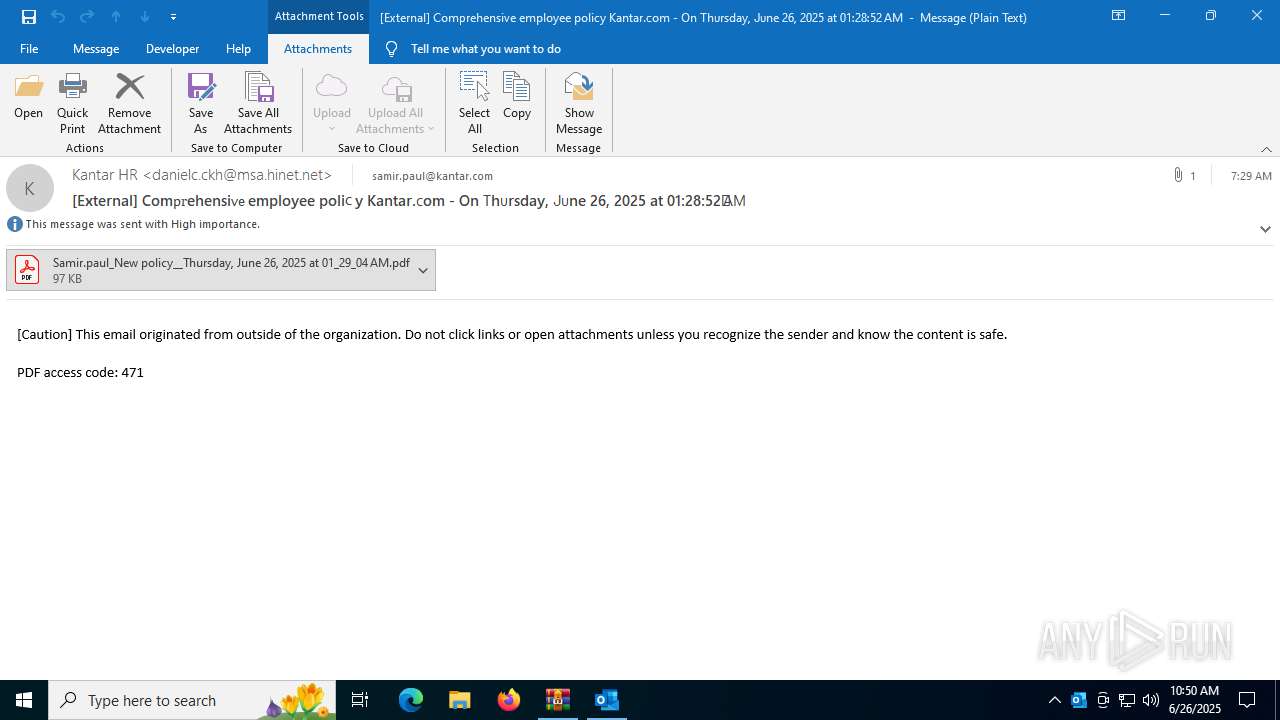
| 1520 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\Rar$DIb3100.29146\Message.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1700 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --field-trial-handle=2024,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=2004 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Version: 133.0.6943.127 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --field-trial-handle=6492,i,1287249428834423732,10158372099437124967,262144 --variations-seed-version=20250221-144540.991000 --mojo-platform-channel-handle=6392 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 133.0.6943.127 Modules
| |||||||||||||||
Total events
30 724
Read events
29 482
Write events
1 096
Delete events
146
Modification events
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DownloadedMessage (20).zip | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.eml\OpenWithProgids |
| Operation: | write | Name: | Outlook.File.eml.15 |
Value: | |||
| (PID) Process: | (3100) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {5FA29220-36A1-40F9-89C6-F4B384B7642E} {886D8EEB-8CF2-4446-8D02-CDBA1DBDCF99} 0xFFFF |
Value: 010000000000000054D6580C88E6DB01 | |||
Executable files
0
Suspicious files
325
Text files
56
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1520 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:FA1083F92A4B7F1B7E652439787A5308 | SHA256:E11A9C469386745D11D9AF0044C2CDAF96699F207FBEFD1DBF480C3B449A8122 | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:880C2CA90C4B9082ECF290CE3472B5E3 | SHA256:12DECABEEA60ED5F3E45203251E603EDFA65ADB606752C6CDA6840BE5625D5CF | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_BEAAAC48C329B34AABDAC5ADBCB7BD5D.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
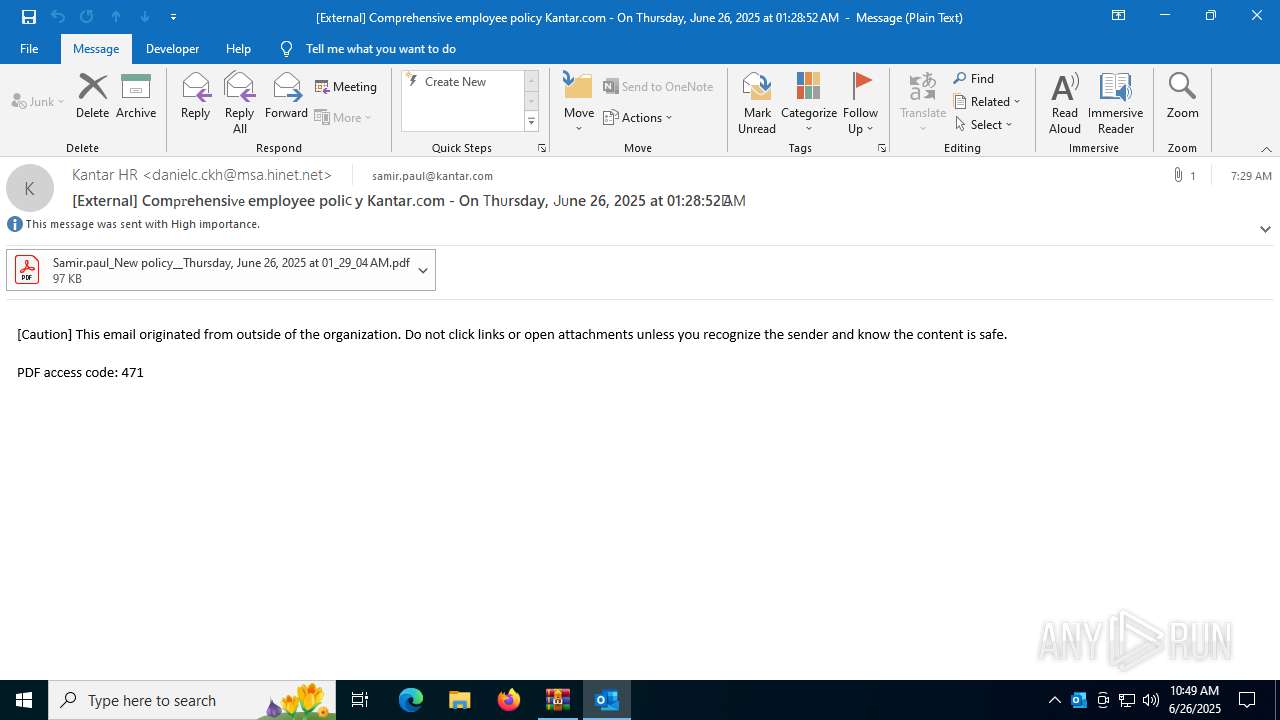
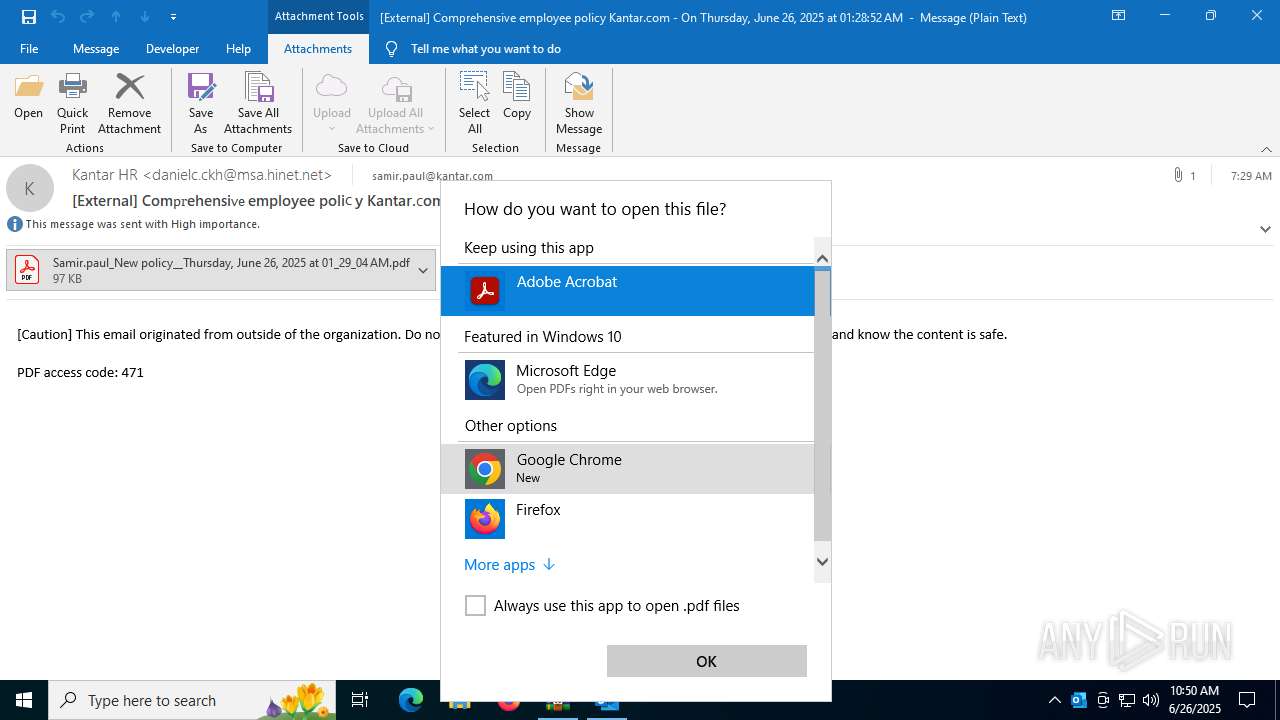
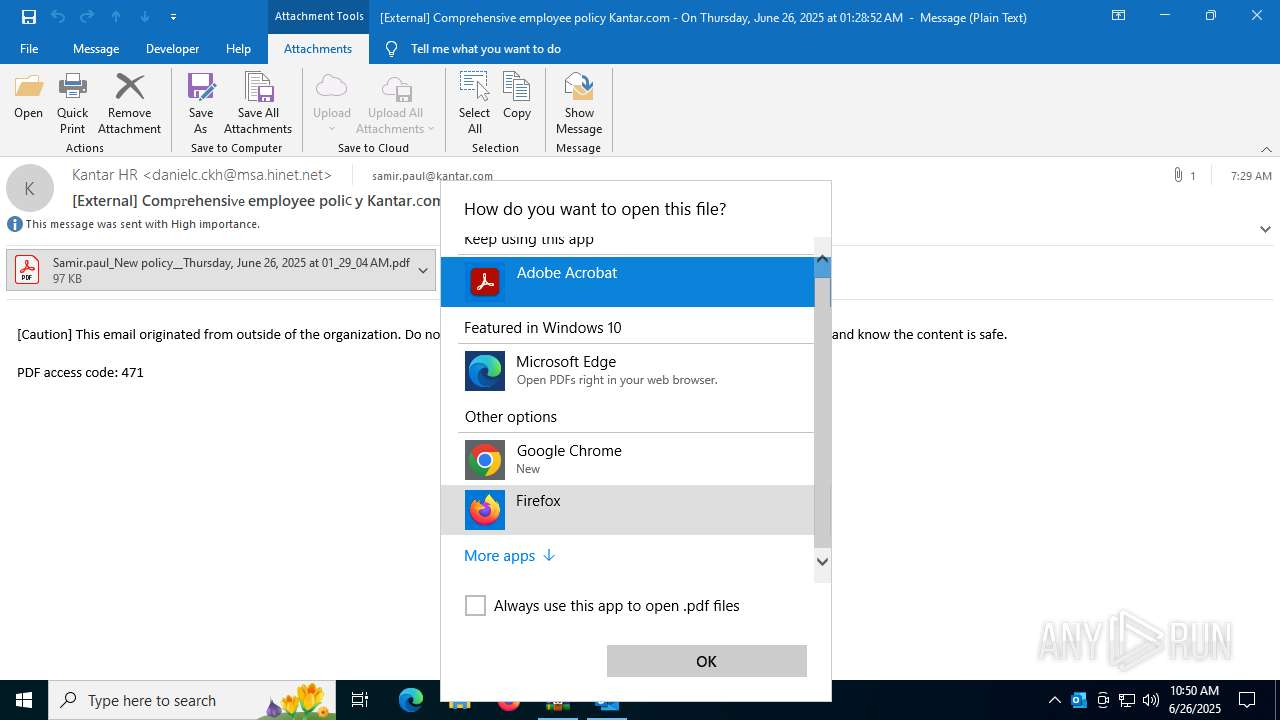
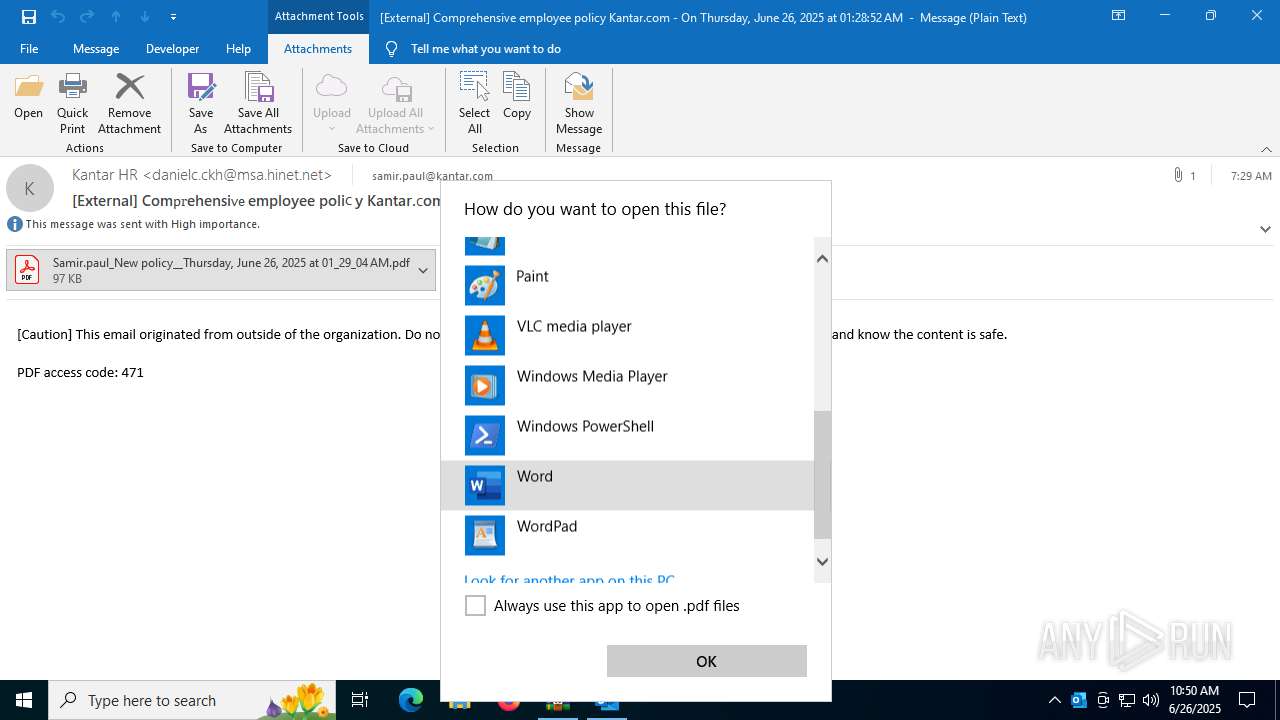
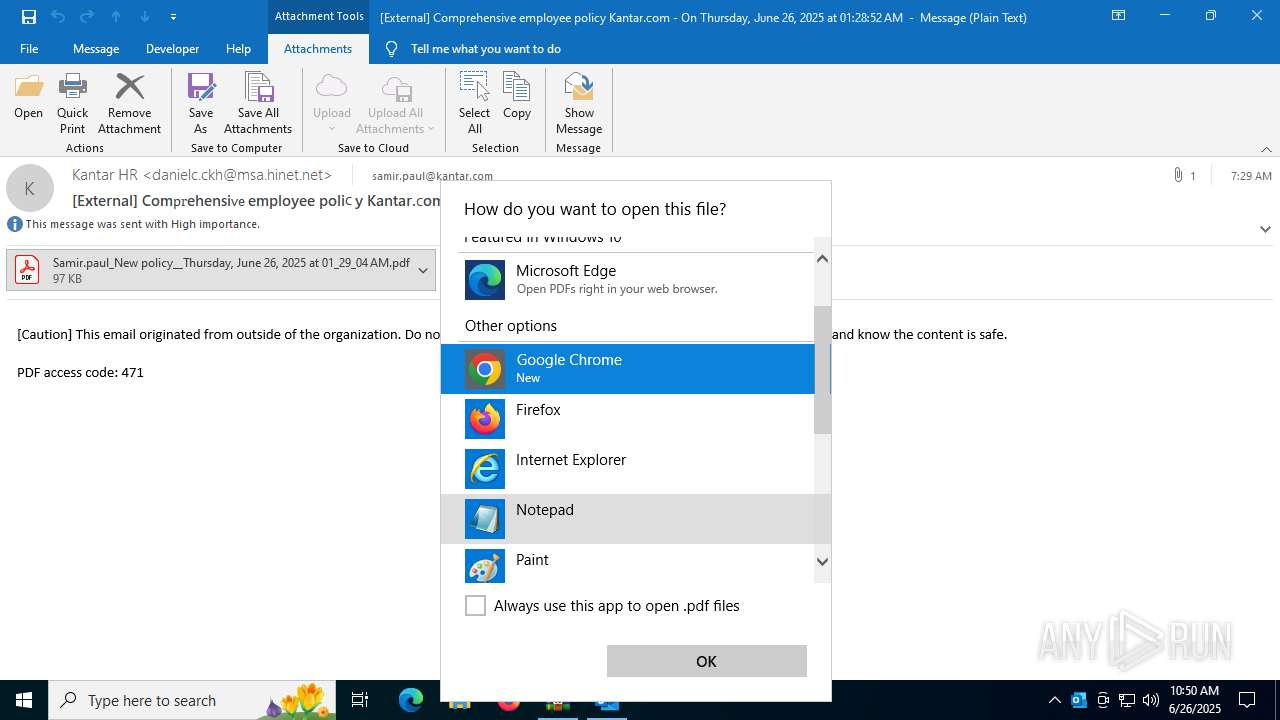
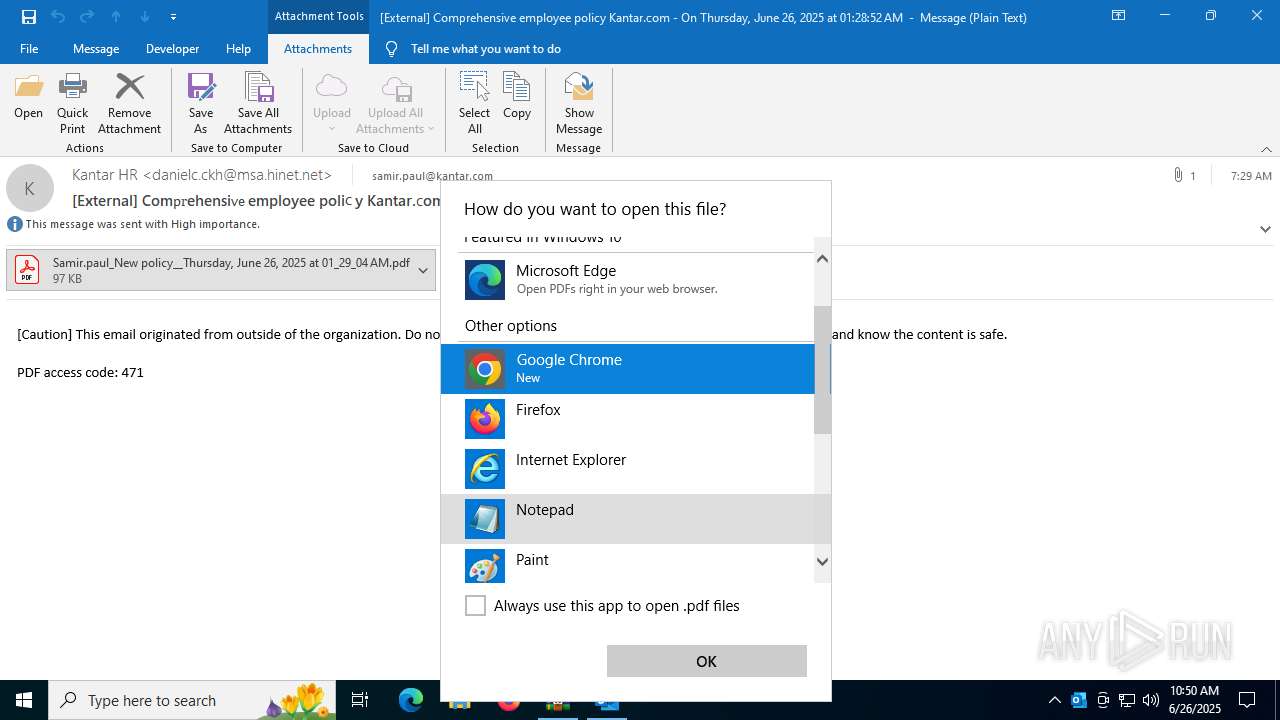
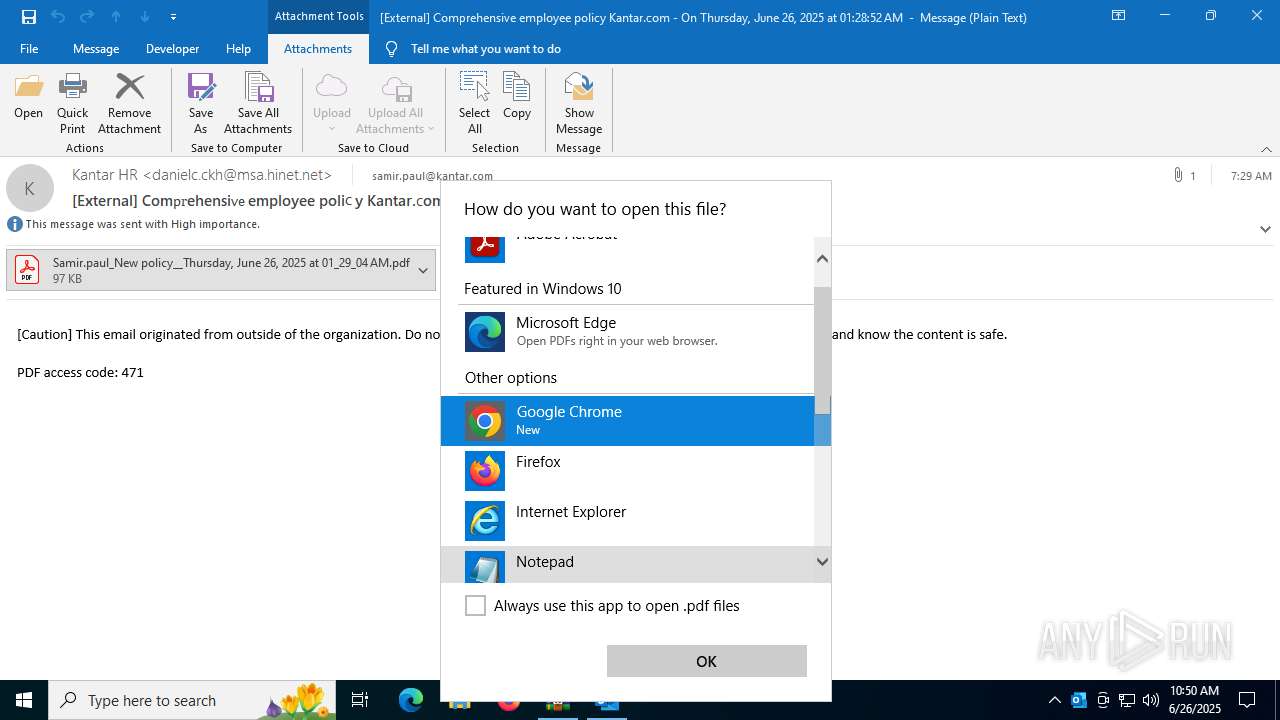
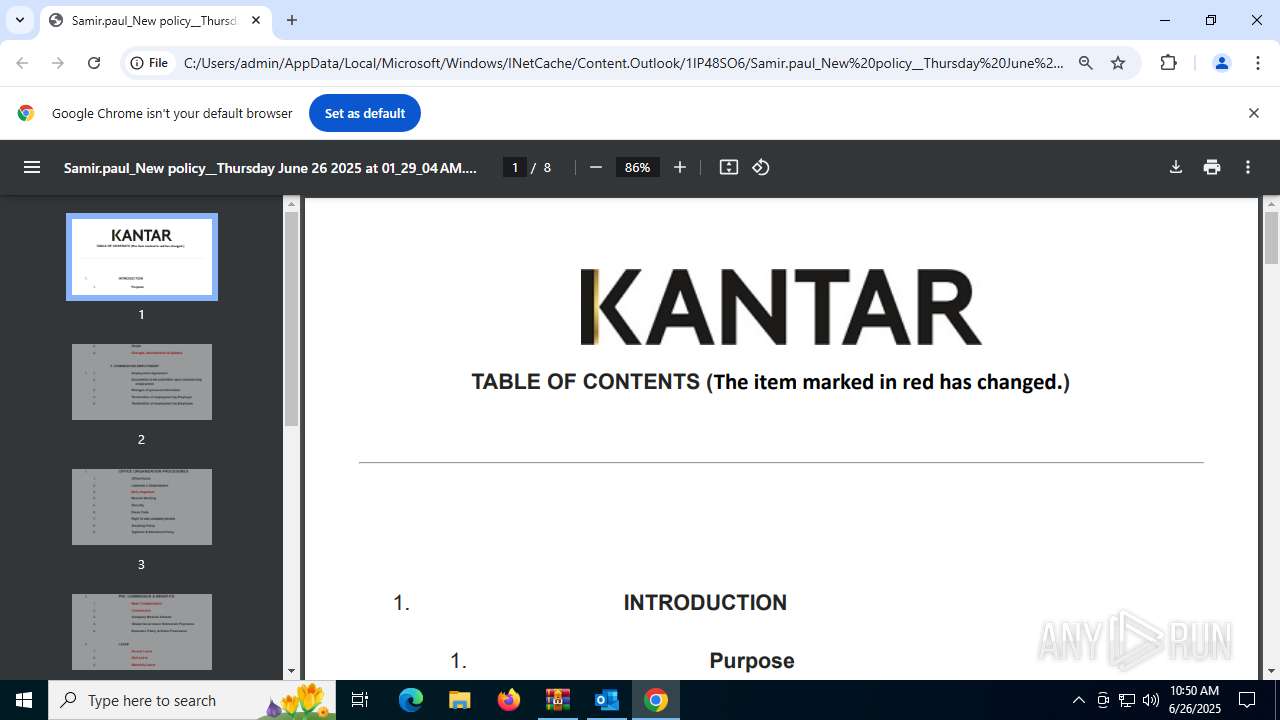
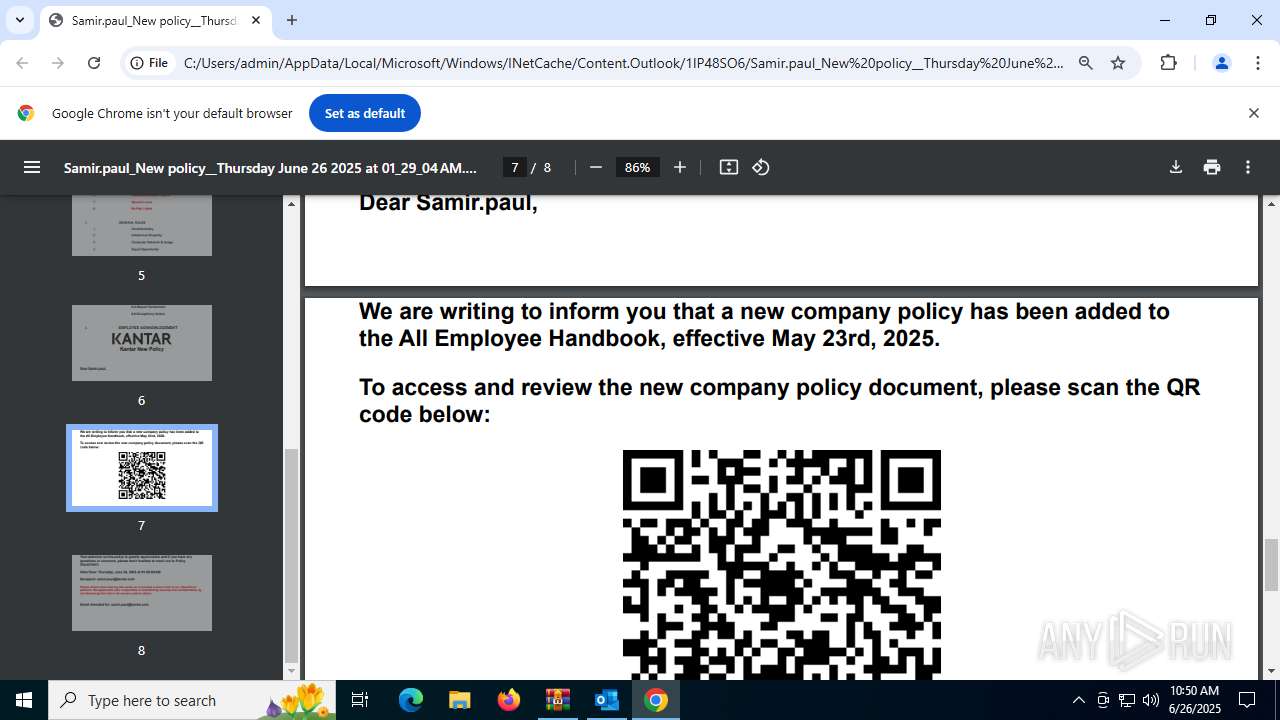
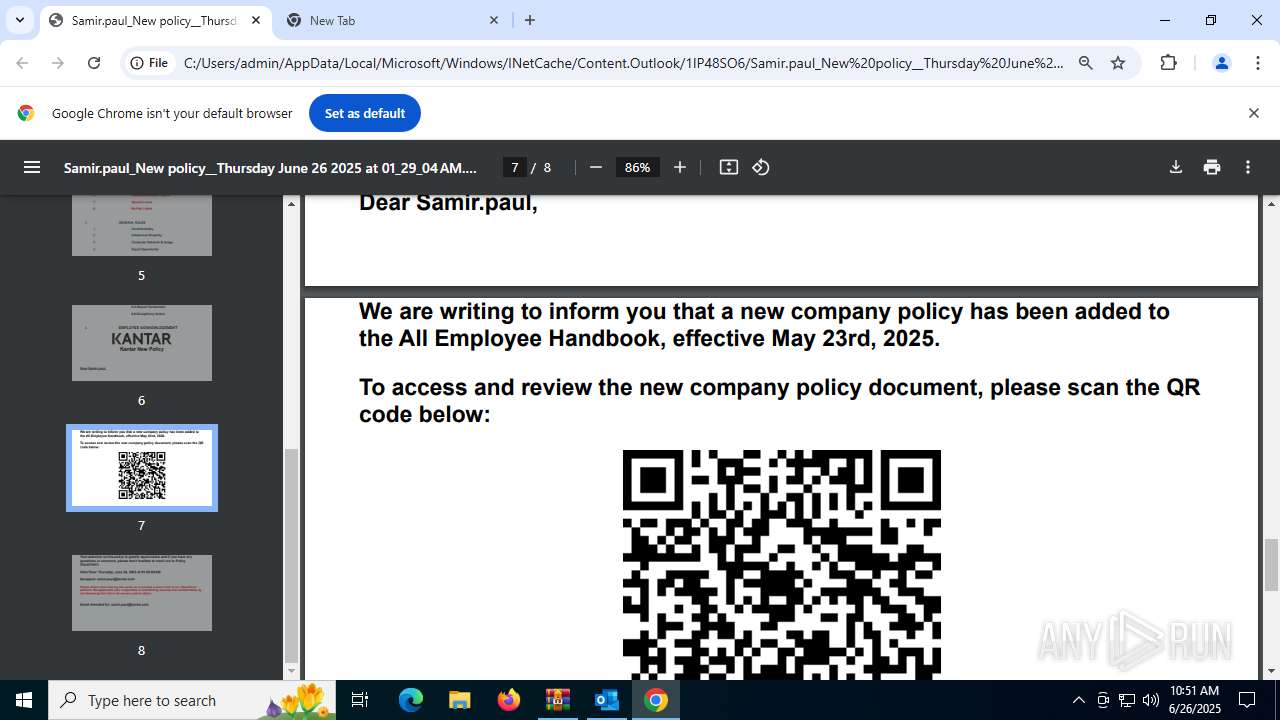
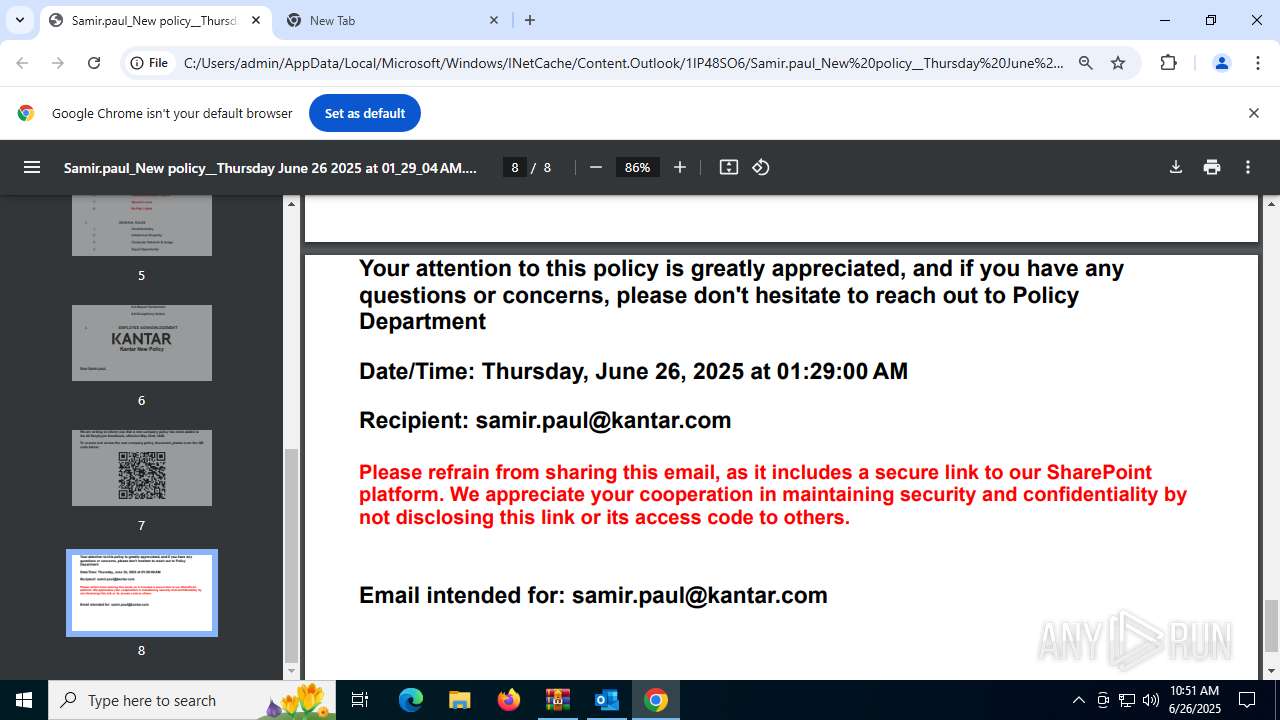
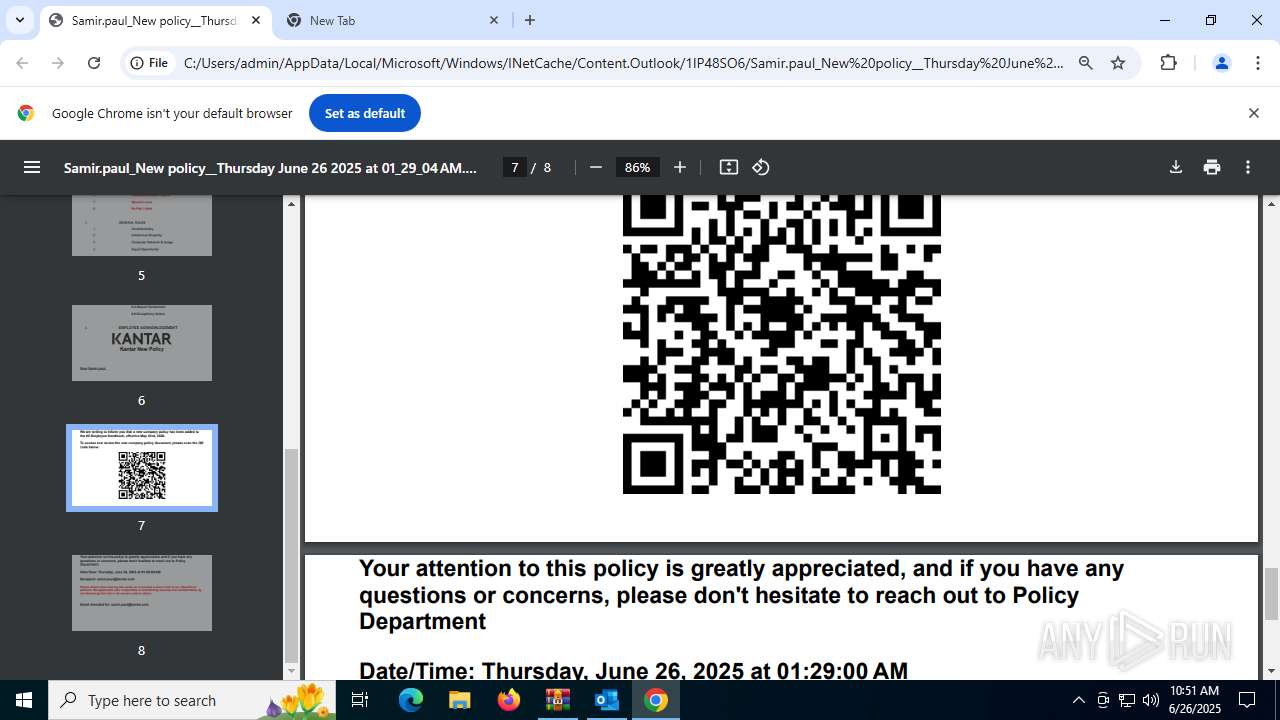
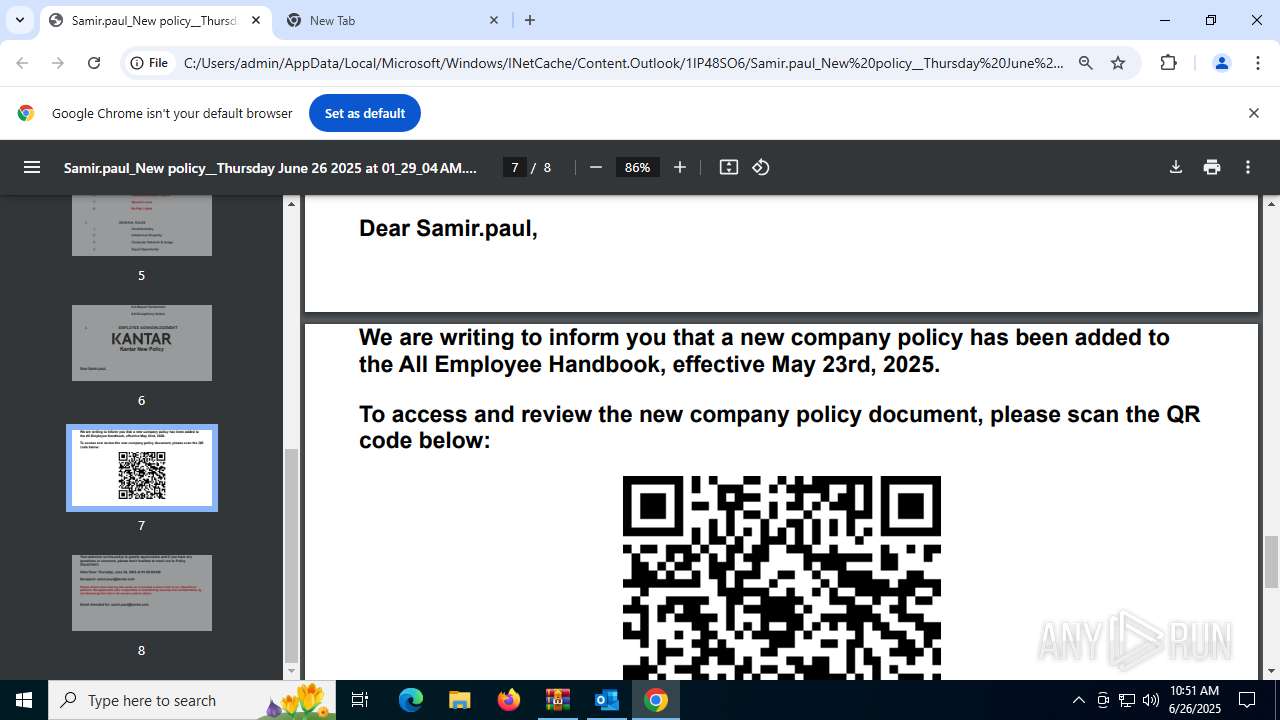
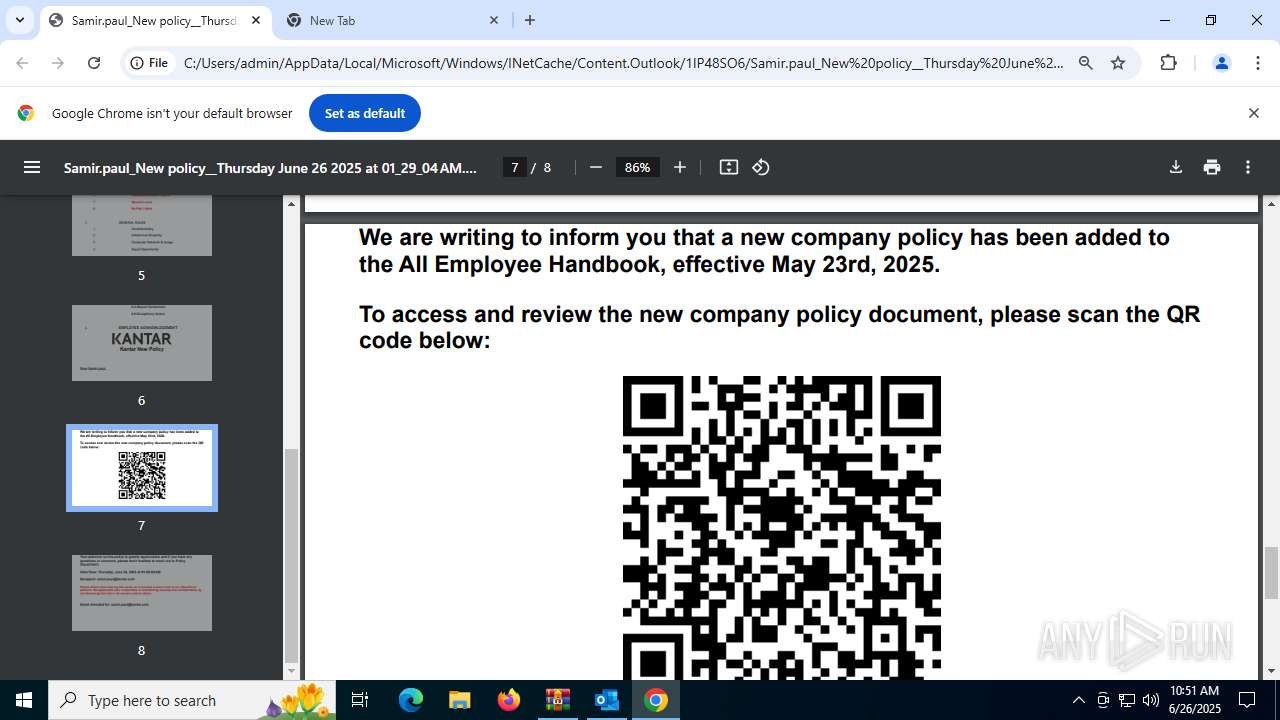
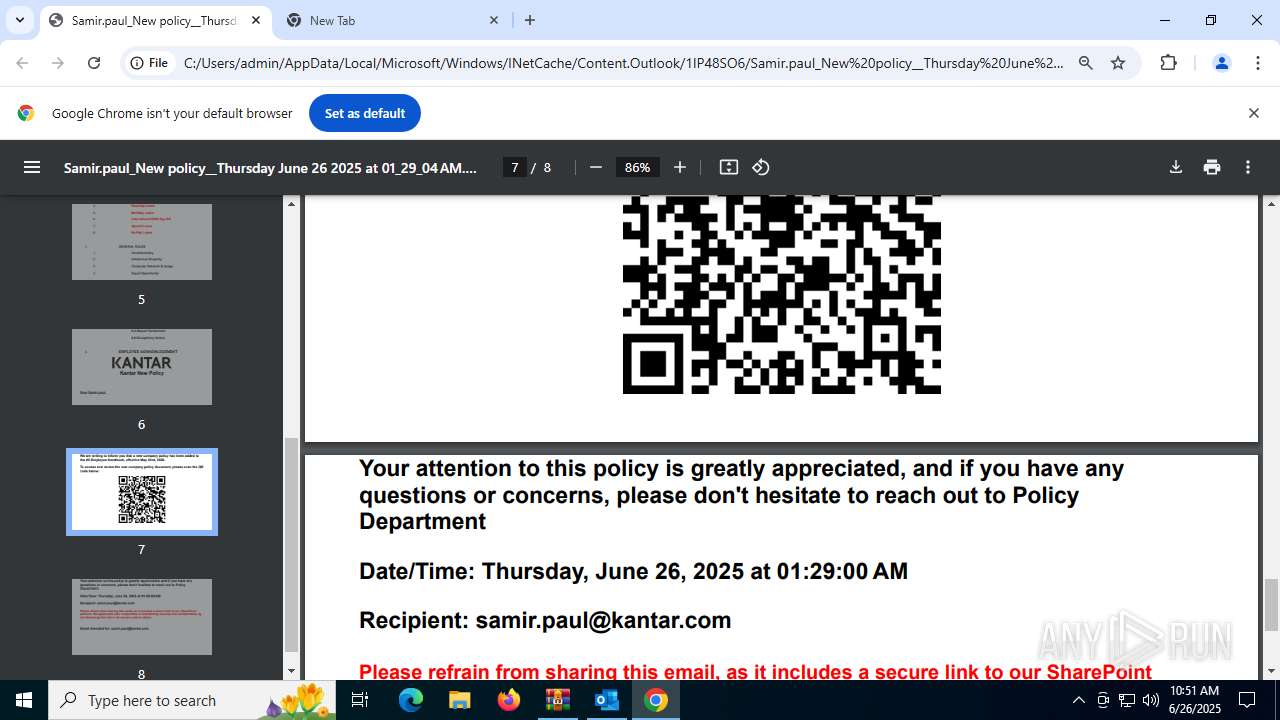
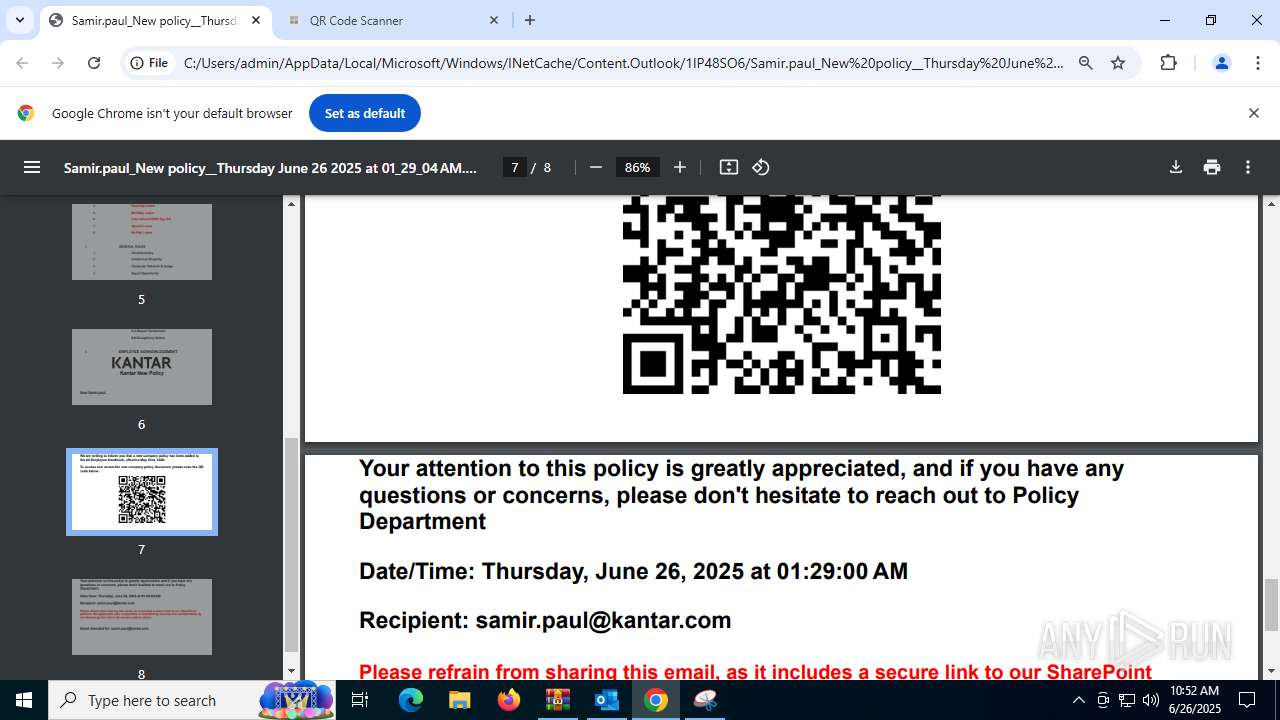
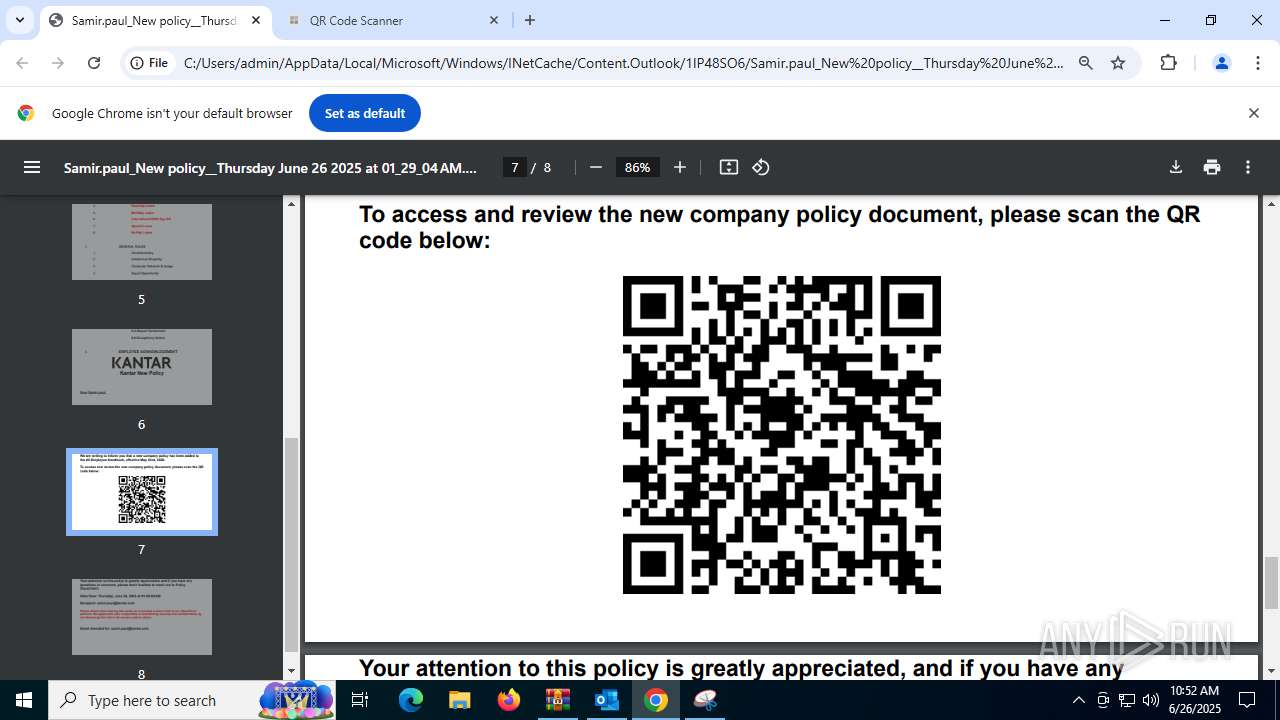
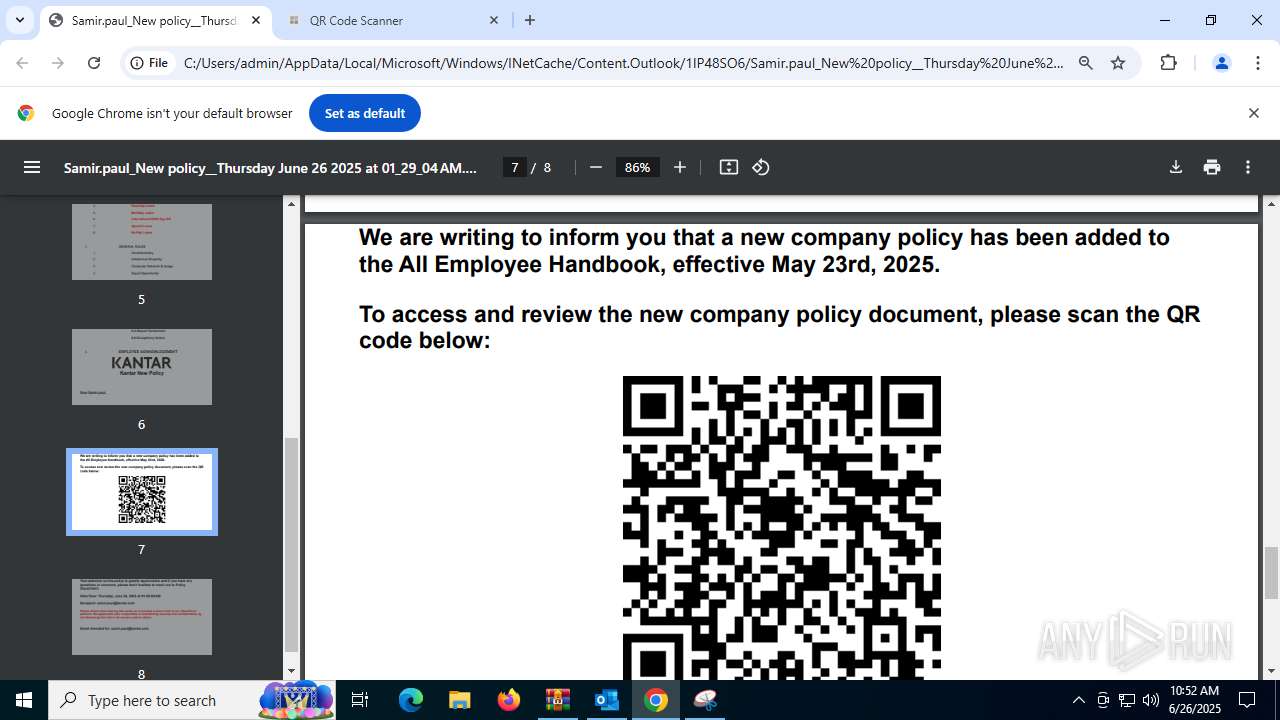
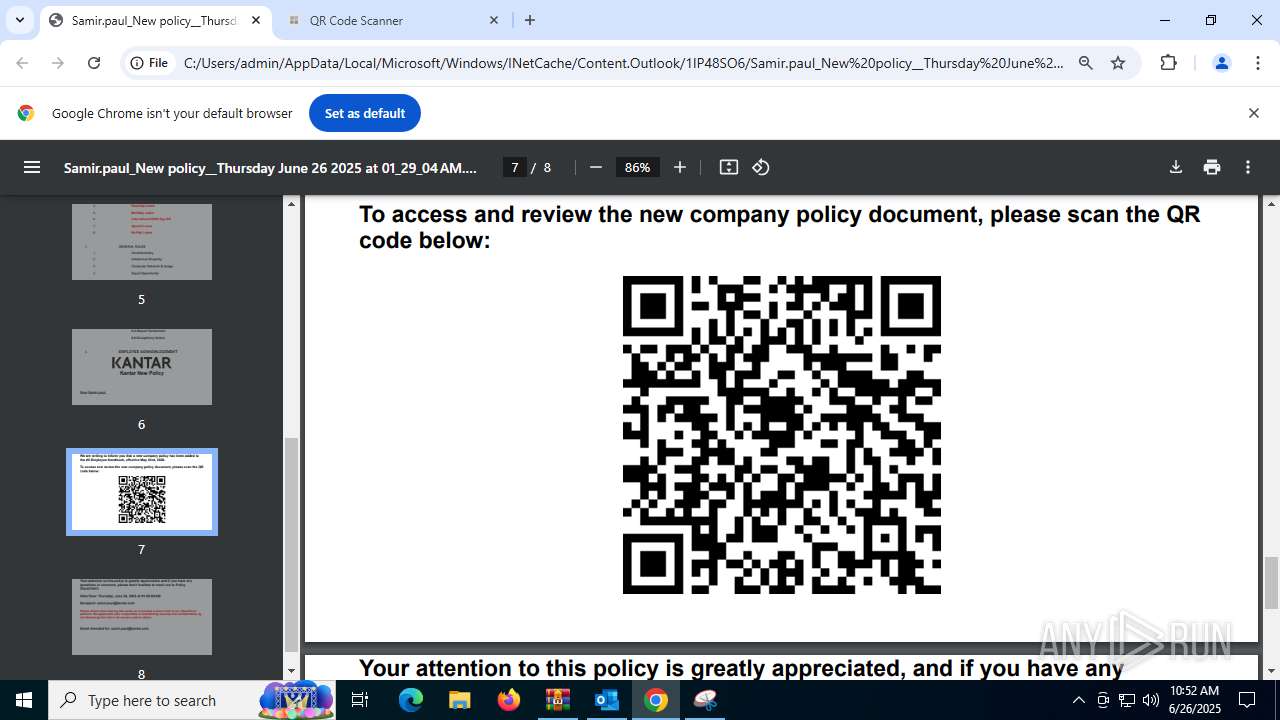
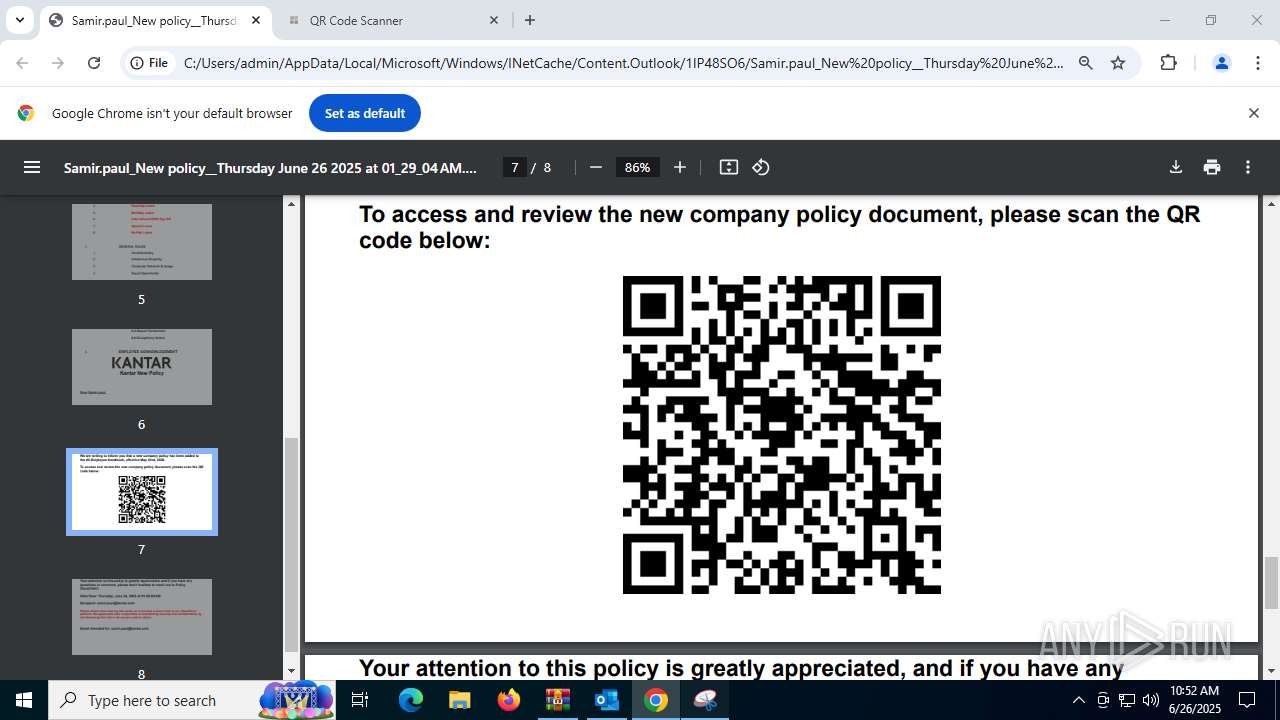
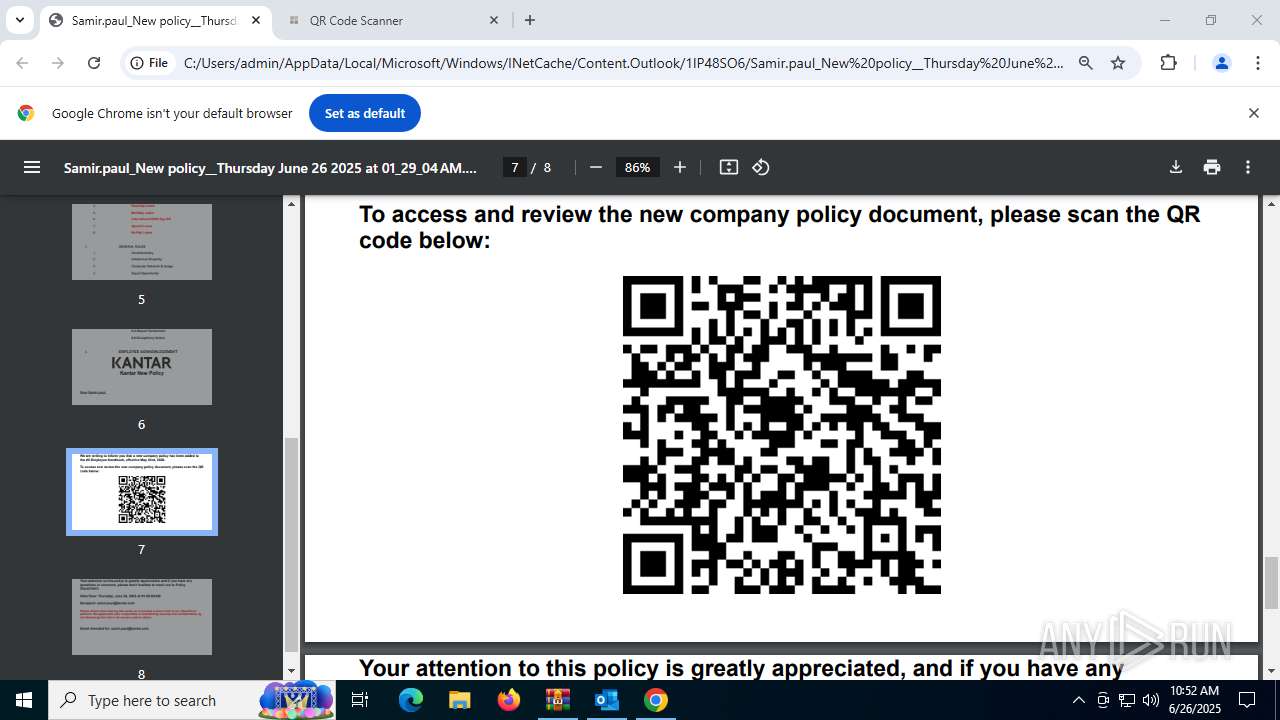
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\1IP48SO6\Samir.paul_New policy__Thursday June 26 2025 at 01_29_04 AM.pdf | ||
MD5:F2070615F33C8B78FF63EF6EF055E83F | SHA256:0F8E8A27158E071E592B35D7A9E1438D6BAA388056481BEEB6D94DBEA2E2054F | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:5580B76FACBFC2A85FF454206B0D48A8 | SHA256:5E60BF1671FD9D40EEFB5C9B94E247BB1E2ABAE4B04559E74A775EE8EDD64BF5 | |||
| 1520 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\1IP48SO6\Samir.paul_New policy__Thursday June 26 2025 at 01_29_04 AM (002).pdf:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3788 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF185261.TMP | — | |
MD5:— | SHA256:— | |||
| 3788 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3788 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\ClientCertificates\LOG.old~RF185261.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
161
DNS requests
190
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3944 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4100 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1520 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4100 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1520 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3964 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acpeapixpwuzscfa5h5j5m7c4xaa_2025.6.16.0/niikhdgajlphfehepabhhblakbdgeefj_2025.06.16.00_all_acgsomx5qtwgffxcrxwhoksfom7q.crx3 | unknown | — | — | whitelisted |
3780 | chrome.exe | GET | 200 | 172.217.16.142:80 | http://clients2.google.com/time/1/current?cup2key=8:84FMnkTHU635XxTN6CFfGcwhrJouSdLG5ZpayT8TCJI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1740 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3944 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3944 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1520 | OUTLOOK.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |
3780 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |