| File name: | VBS.LoveLetter.txt.vbs |
| Full analysis: | https://app.any.run/tasks/078990a4-08a7-4c0a-bf3c-96f131d34adc |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 22:34:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-c |
| File info: | C source, Non-ISO extended-ASCII text |
| MD5: | 836A5ABD025D60A7AA8550679DD556C9 |
| SHA1: | A71042308730A358ACB9BCB03A7412B1859320D7 |
| SHA256: | D3F6956E01E2A4BCDBDCE1B41D0F31E546A102DC384FC9E81B9F1D912E099A13 |
| SSDEEP: | 192:1p9Tx0wI1TzMjMJDMxMWMDMrMvGMDMRMVM3MeMkl7iI243aNKss5xEDHoZ:1pxiwI1TzcoD+dqE1qyq47Mk9kD0 |
MALICIOUS
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 3384)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 3384)
Deletes a file (SCRIPT)
- wscript.exe (PID: 3384)
SUSPICIOUS
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 3384)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 3384)
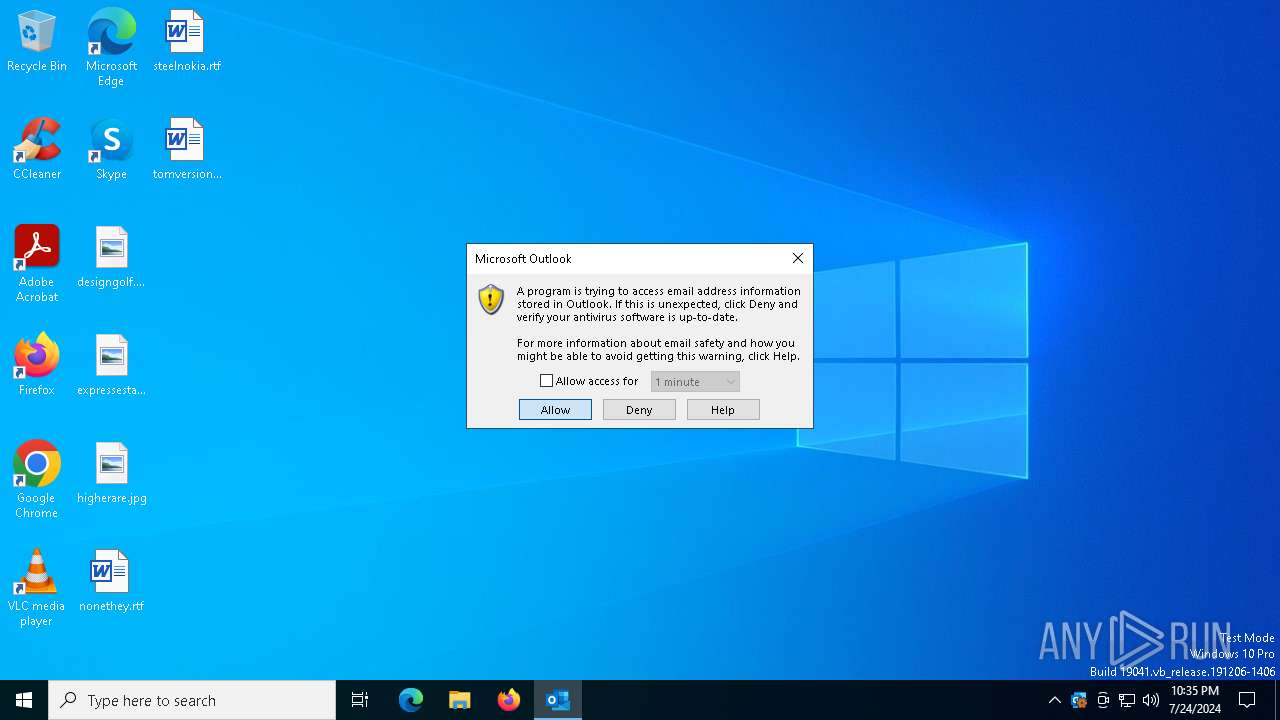
Changes the title of the Internet Explorer window
- wscript.exe (PID: 3384)
Runs shell command (SCRIPT)
- wscript.exe (PID: 3384)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 3384)
Changes the Home page of Internet Explorer
- wscript.exe (PID: 3384)
Gets the drive type (SCRIPT)
- wscript.exe (PID: 3384)
Executes application which crashes
- wscript.exe (PID: 3384)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 3384)
INFO
Checks proxy server information
- slui.exe (PID: 6696)
Reads the software policy settings
- slui.exe (PID: 6696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
142
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3384 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\AppData\Local\Temp\VBS.LoveLetter.txt.vbs | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 3221225477 Version: 5.812.10240.16384 Modules
| |||||||||||||||
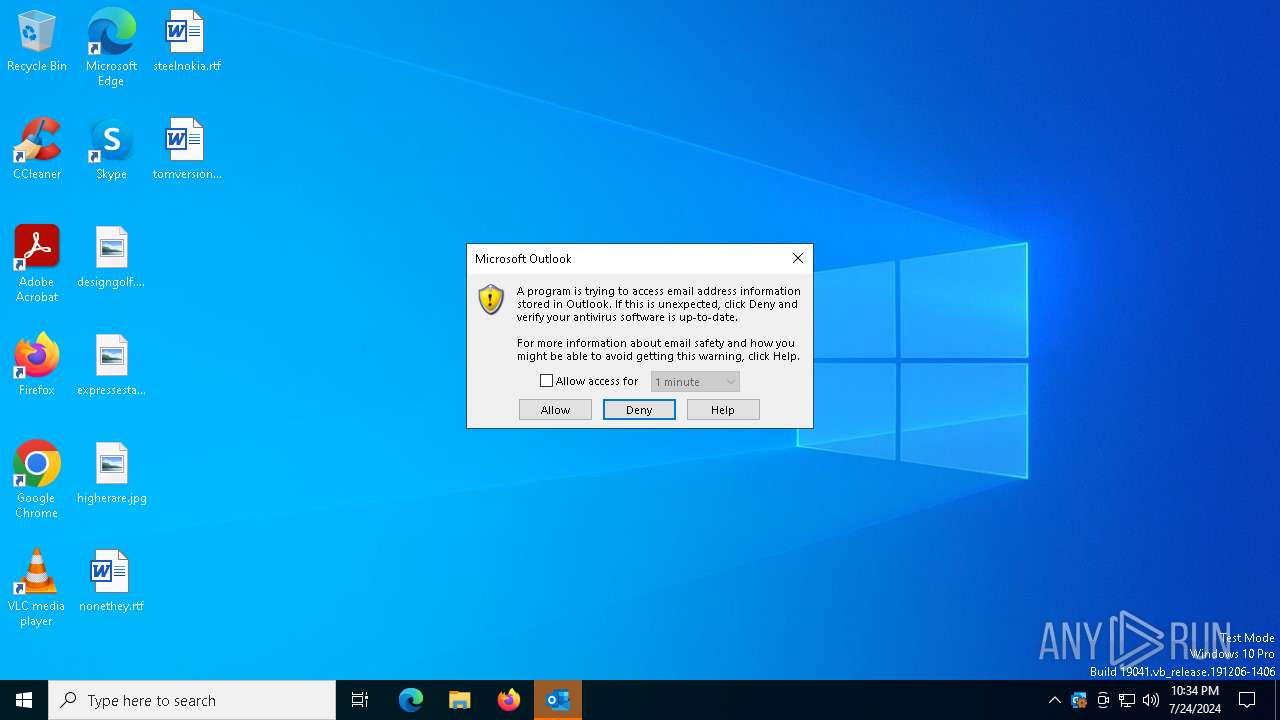
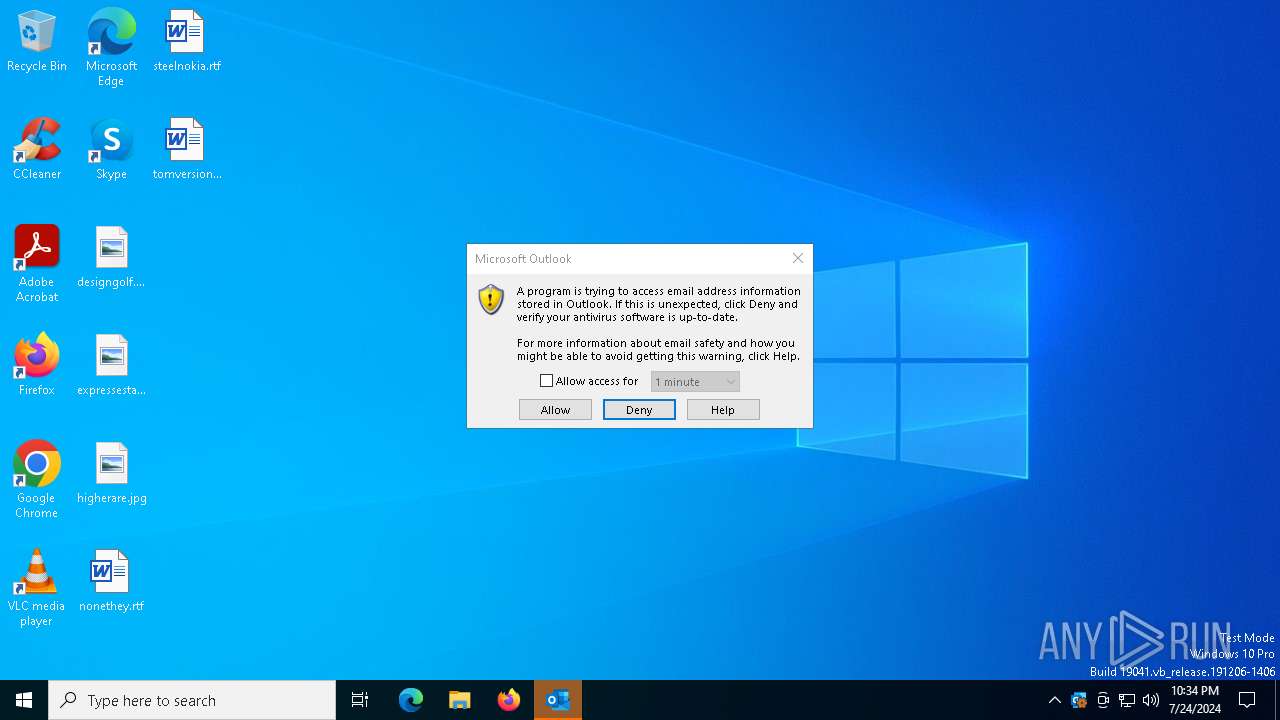
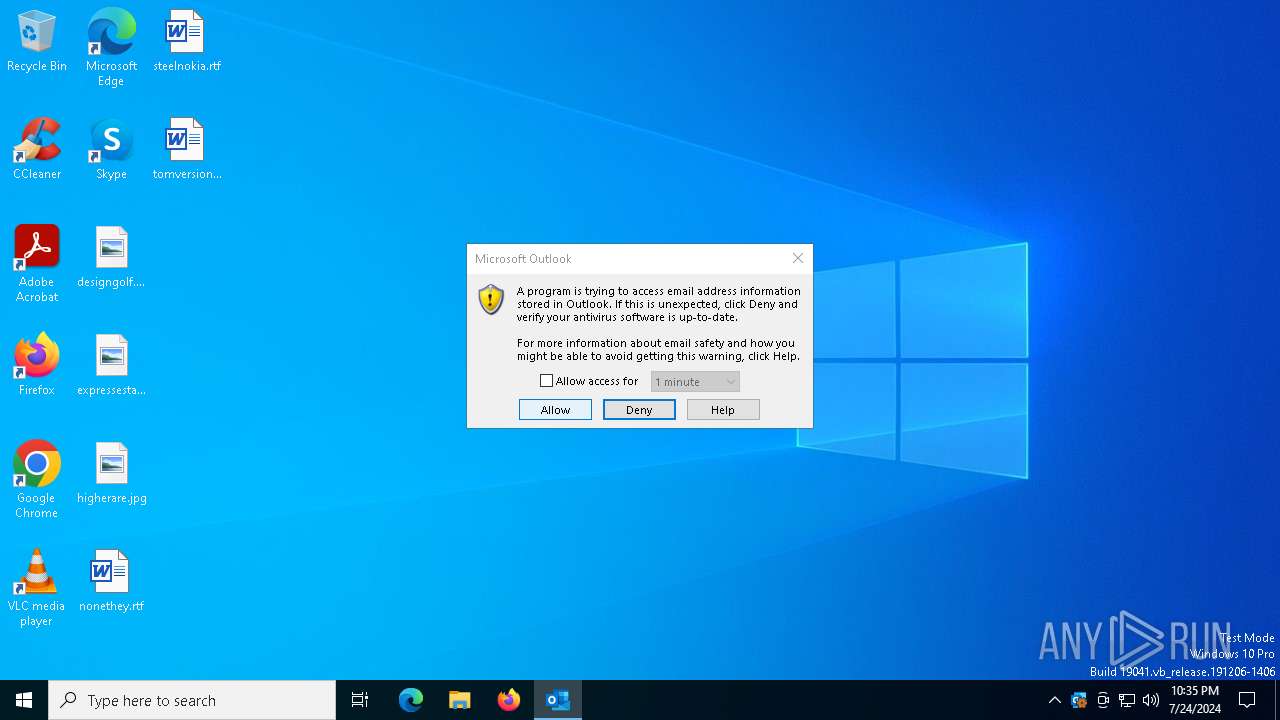
| 4188 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6696 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7160 | C:\WINDOWS\system32\WerFault.exe -u -p 3384 -s 980 | C:\Windows\System32\WerFault.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
7 619
Read events
7 302
Write events
288
Delete events
29
Modification events
| (PID) Process: | (3384) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | Start Page |
Value: www.o2.pl | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E05000000000000000500000000000000 | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\4188 |
| Operation: | write | Name: | 0 |
Value: 0B0E10321BF4BF971187469081212A66965F22230046B7F887AA9BC3B7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511DC20D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshotLanguages |
Value: de-de;en-us;es-es;fr-fr;it-it;ja-jp;ko-kr;pt-br;ru-ru;tr-tr | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 1 | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 1 | |||
| (PID) Process: | (4188) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 1 | |||
Executable files
0
Suspicious files
14
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4188 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7160 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_WScript.exe_a4b8af2d183afea7fd6e13de5b147874c8d2939_debcac4a_ac930c47-e819-4b1e-8b9b-9cfc5cd91f61\Report.wer | — | |
MD5:— | SHA256:— | |||
| 4188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4188 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:ADB529A70DB60590DF365249FBCA0C13 | SHA256:8E18A95DBA344A7162496711FC0DFC93218544308A31B8674637079287189CD6 | |||
| 4188 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\~Outlook1.pst.tmp | binary | |
MD5:EBB2432BEFFC7C19010009FE2AD36B83 | SHA256:D40653854A695CE7A7A1199BA4EE675E0C3AB41E6AE4253A114FB45555AD82AE | |||
| 7160 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:82C30E45BF5F93A5DB1D5E47F913053B | SHA256:2C6BBFF9207065E8800C4AF0CB2748818ABB3CFFC0D6D518FE17F76A232F8967 | |||
| 7160 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERBE99.tmp.WERInternalMetadata.xml | xml | |
MD5:ECA8E33F904ACB1B96FCB1B898D272AF | SHA256:102EB9E28073883BA23F1EC31C3209D69239202ACEA62448CCF9830B11AEB127 | |||
| 4188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:6F93EDE360B0D6810B4E3E04D34C4915 | SHA256:CD63D02281264B640AEC1751A23096F5BD77C0AD9531F084CAEF28CA786F76BF | |||
| 4188 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:386DF96199D0DED2E6C7D41486BB1B74 | SHA256:C21C1AE33C7302C121114132F0977EB35352905E686B4FAA5766A37DFAABC208 | |||
| 4188 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240724T2234550755-4188.etl | binary | |
MD5:53AF91EDB9C1EFFA747E66D6E61B06E6 | SHA256:579FEE0EF6289B5486EE85BB6A80C84011A96497E0CCA3FCE5D3F2D51B03BB90 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
51
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1324 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4188 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4188 | OUTLOOK.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3212 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3076 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 4.209.33.156:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4512 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6696 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4188 | OUTLOOK.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4188 | OUTLOOK.EXE | 23.48.23.18:443 | omex.cdn.office.net | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |