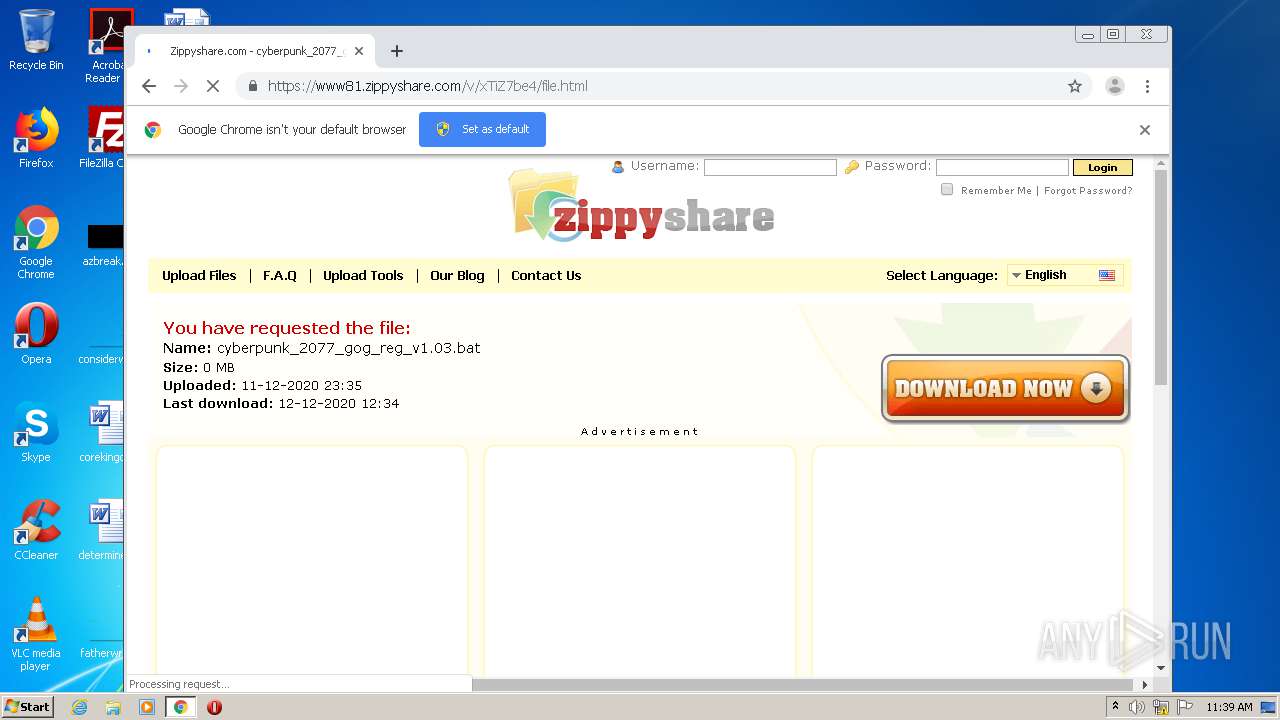
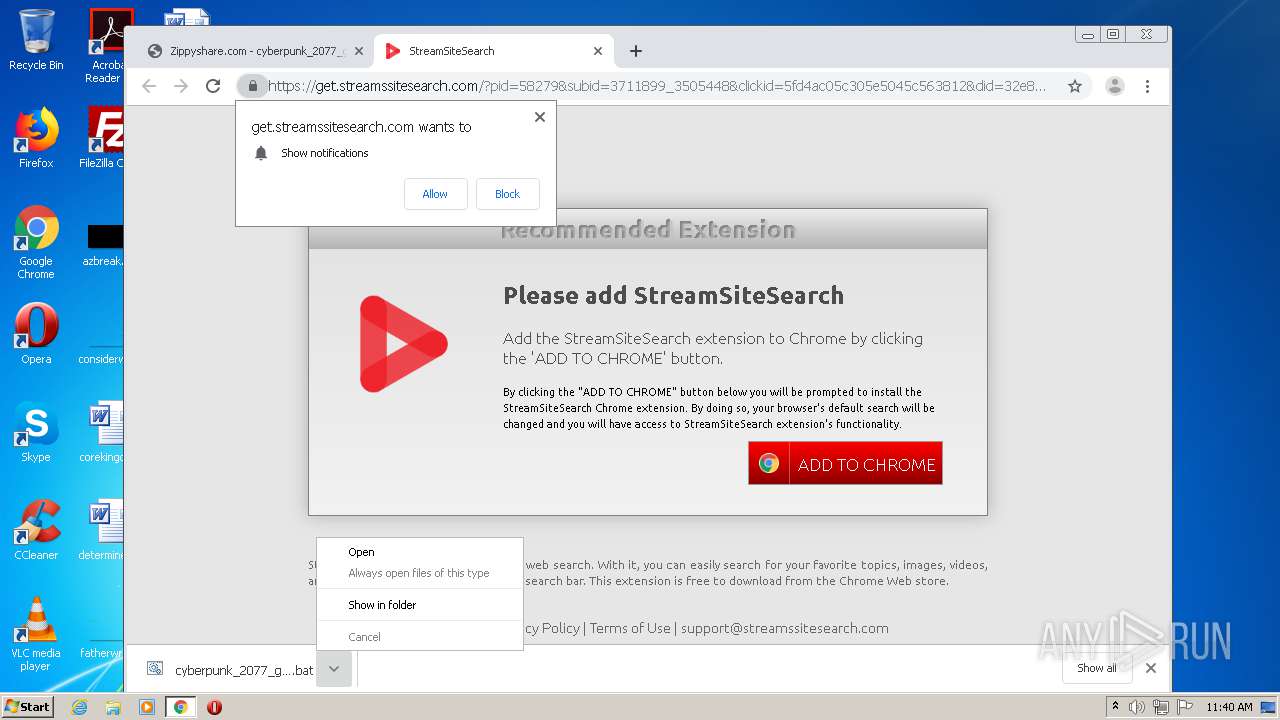
| URL: | https://www81.zippyshare.com/v/xTiZ7be4/file.html |
| Full analysis: | https://app.any.run/tasks/1b385bd4-bb4b-431b-84b0-7a90c1ae0777 |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2020, 11:39:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A6600310A693489B7B79104910369E16 |
| SHA1: | 2C26B87653F18B173840143CAB5FEC69C6B44D70 |
| SHA256: | D3CF5F0334DBF49F469B3C8D8CB439CD1B11D44392A21BA6021A7E1729E87A7A |
| SSDEEP: | 3:N8DSdSc3GKjKztgmwJ:2OdSc3GjzKmwJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executed via COM
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2472)
Modifies files in Chrome extension folder
- chrome.exe (PID: 272)
INFO
Application launched itself
- iexplore.exe (PID: 2596)
- chrome.exe (PID: 272)
Changes internet zones settings
- iexplore.exe (PID: 2596)
Reads settings of System Certificates
- iexplore.exe (PID: 2332)
- iexplore.exe (PID: 2596)
Creates files in the user directory
- iexplore.exe (PID: 2332)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2472)
Reads internet explorer settings
- iexplore.exe (PID: 2332)
Manual execution by user
- chrome.exe (PID: 272)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 960)
Reads the hosts file
- chrome.exe (PID: 272)
- chrome.exe (PID: 1868)
Changes settings of System certificates
- iexplore.exe (PID: 2596)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
46
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,6954797307039841593,17095056644310079681,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1228420546018346941 --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4720 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,6954797307039841593,17095056644310079681,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15026997118733583445 --mojo-platform-channel-handle=3780 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 620 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,6954797307039841593,17095056644310079681,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18211169127575013790 --mojo-platform-channel-handle=3524 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 688 | net session | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 756 | C:\Windows\system32\net1 session | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1576 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
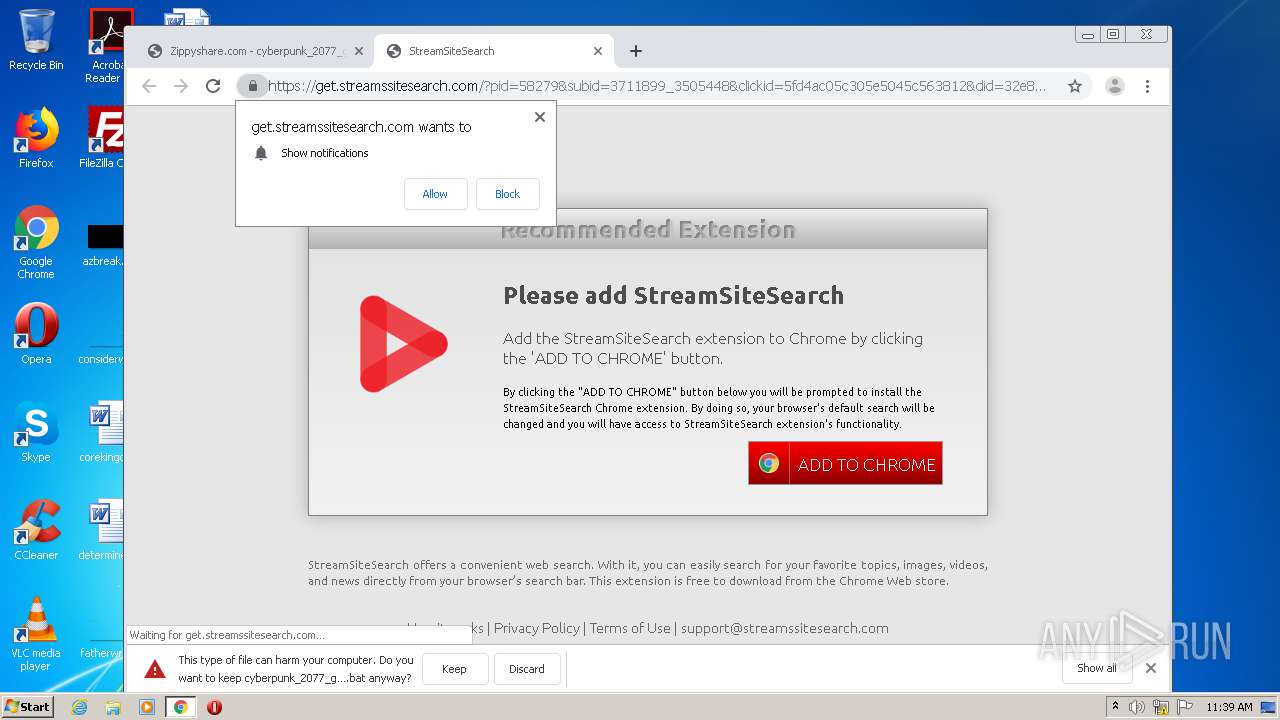
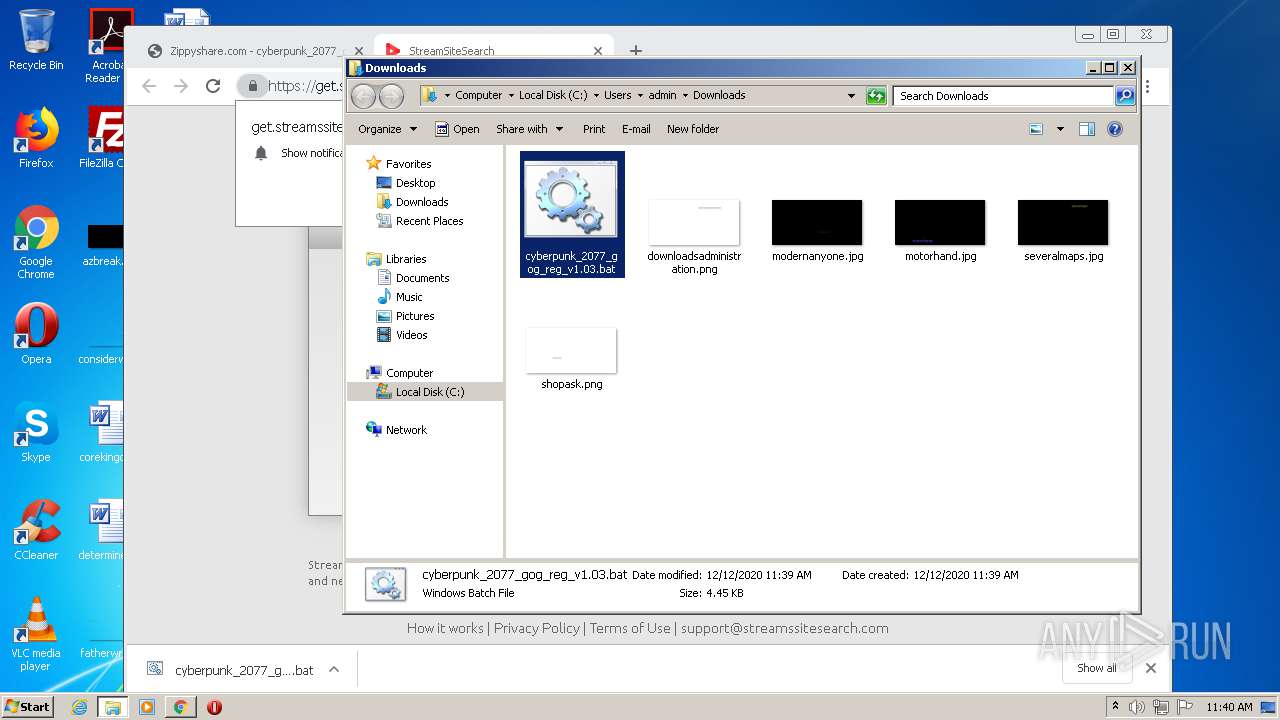
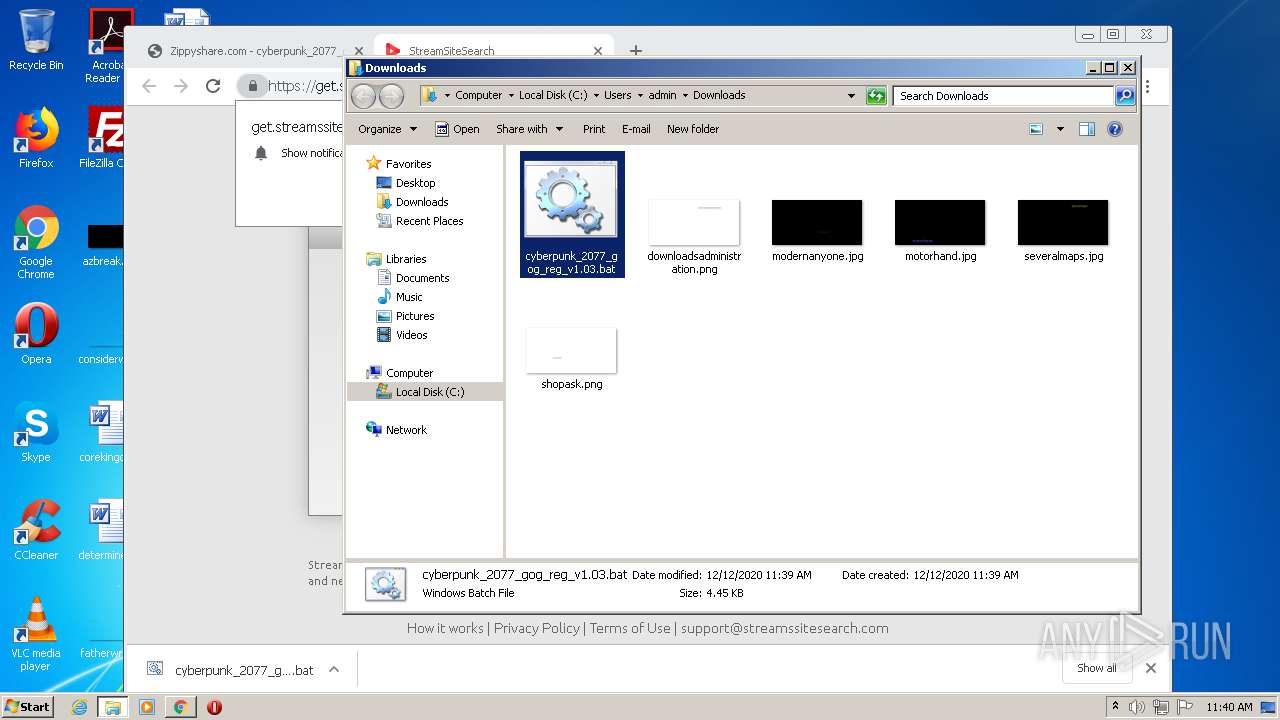
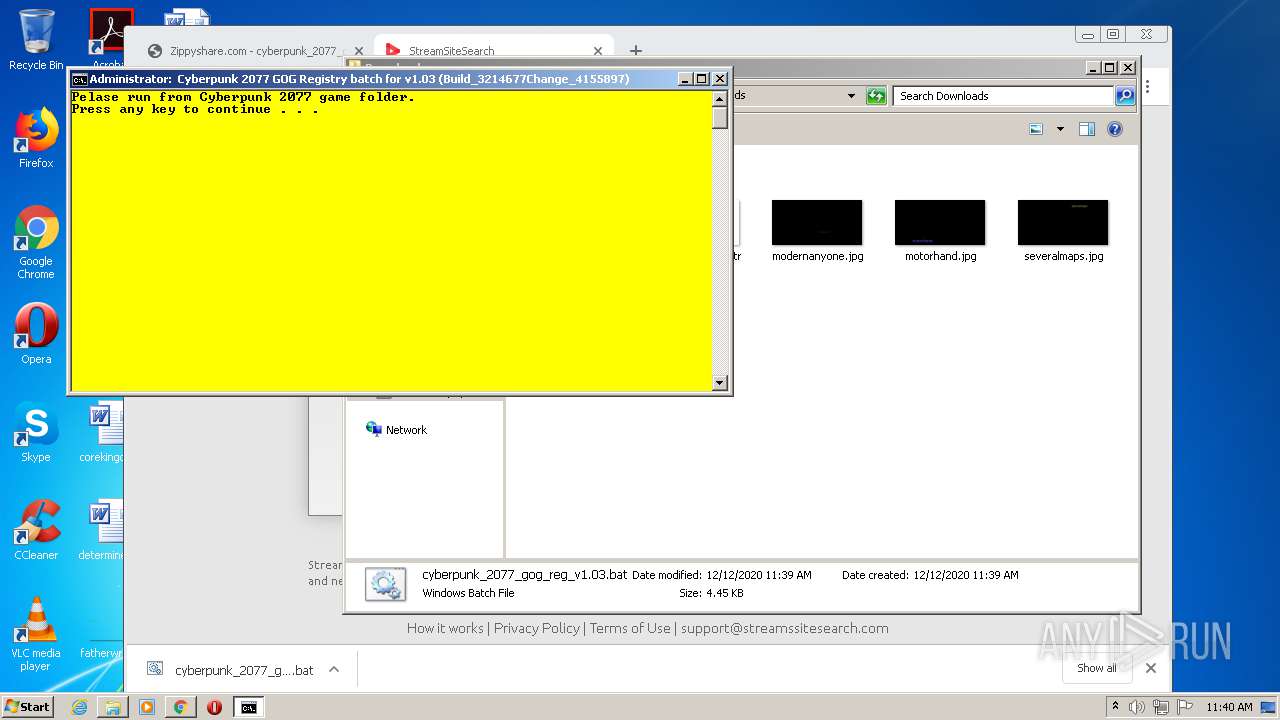
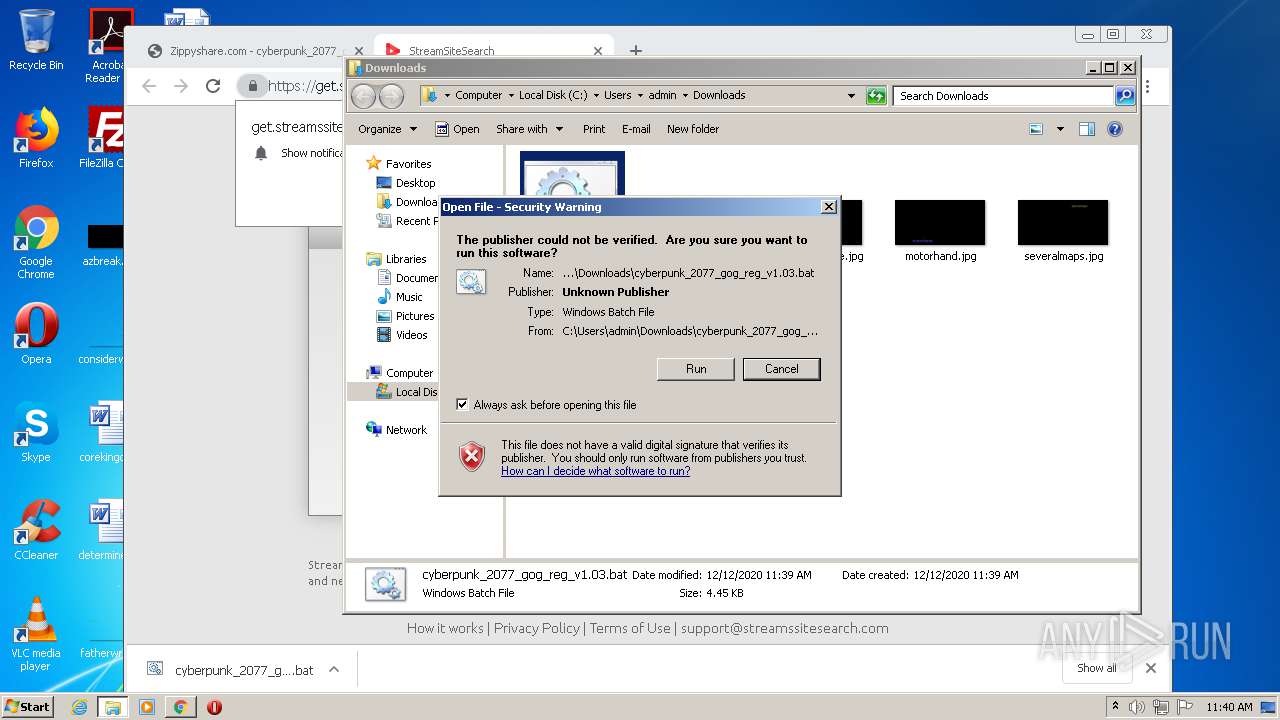
| 960 | cmd /c ""C:\Users\admin\Downloads\cyberpunk_2077_gog_reg_v1.03.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,6954797307039841593,17095056644310079681,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=7455484301062382422 --mojo-platform-channel-handle=3672 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1236 | net session | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 963
Read events
1 717
Write events
238
Delete events
8
Modification events
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2146694364 | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30855291 | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2596) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
190
Text files
286
Unknown types
83
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabCDC6.tmp | — | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarCDC7.tmp | — | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\ACF244F1A10D4DBED0D88EBA0C43A9B5_BA1AB6C2BDFDF57799E8116E4002D001 | der | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\viewjs-5c4b087e763baf82dfed5e75dc71d50f709ecb00[1].js | text | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BC570EC0DE58335AFAF92FDC8E3AA330_D21CA3FA19E2494154CA1B3726B54309 | der | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\file[1].htm | html | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\viewjs-9c29d4e653e865831dc028fdac7e7dfff3be049e[1].css | text | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\ads[1].js | text | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8828F39C7C0CE9A14B25C7EB321181BA_BD8B98368542C3BBAE3413A0EF3BB623 | binary | |
MD5:— | SHA256:— | |||
| 2332 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\sw[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
56
TCP/UDP connections
174
DNS requests
105
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2332 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2332 | iexplore.exe | GET | 200 | 23.37.43.27:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS56bKHAoUD%2BOyl%2B0LhPg9JxyQm4gQUf9Nlp8Ld7LvwMAnzQzn6Aq8zMTMCEGMYDTj7gJd4qdA1oxYY%2BEA%3D | NL | der | 1.71 Kb | shared |
2332 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/gsalphasha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSE1Wv4CYvTB7dm2OHrrWWWqmtnYQQU9c3VPAhQ%2BWpPOreX2laD5mnSaPcCDAQ2J002vedADHR8qQ%3D%3D | US | der | 1.49 Kb | whitelisted |
2332 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp2.globalsign.com/gsalphasha2g2/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSE1Wv4CYvTB7dm2OHrrWWWqmtnYQQU9c3VPAhQ%2BWpPOreX2laD5mnSaPcCDAQ2J002vedADHR8qQ%3D%3D | US | der | 1.49 Kb | whitelisted |
2332 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgP2A5SWAiYn9Ga%2Bug%2FFNbJMWw%3D%3D | unknown | der | 527 b | whitelisted |
2332 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
2332 | iexplore.exe | GET | 200 | 2.16.186.11:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgP2A5SWAiYn9Ga%2Bug%2FFNbJMWw%3D%3D | unknown | der | 527 b | whitelisted |
2332 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | der | 727 b | whitelisted |
2332 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAyO4MkNaokViAQGHuJB%2Ba8%3D | US | der | 471 b | whitelisted |
2332 | iexplore.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/rootr1/MEwwSjBIMEYwRDAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCCwQAAAAAAURO8DYx | US | der | 1.49 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2332 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
2332 | iexplore.exe | 23.37.43.27:80 | s.symcd.com | Akamai Technologies, Inc. | NL | whitelisted |
2332 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2332 | iexplore.exe | 216.58.210.8:443 | ssl.google-analytics.com | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 216.58.207.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2332 | iexplore.exe | 46.166.139.215:443 | www81.zippyshare.com | NForce Entertainment B.V. | NL | unknown |
2332 | iexplore.exe | 104.18.20.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
2332 | iexplore.exe | 104.18.21.226:80 | ocsp.globalsign.com | Cloudflare Inc | US | shared |
2332 | iexplore.exe | 65.9.70.55:443 | ds88pc0kw6cvc.cloudfront.net | AT&T Services, Inc. | US | malicious |
2332 | iexplore.exe | 65.9.70.24:443 | d10lumateci472.cloudfront.net | AT&T Services, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www81.zippyshare.com |
| unknown |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
d10lumateci472.cloudfront.net |
| whitelisted |
ds88pc0kw6cvc.cloudfront.net |
| whitelisted |
s7.addthis.com |
| whitelisted |
p232207.clksite.com |
| whitelisted |
www.maxonclick.com |
| whitelisted |
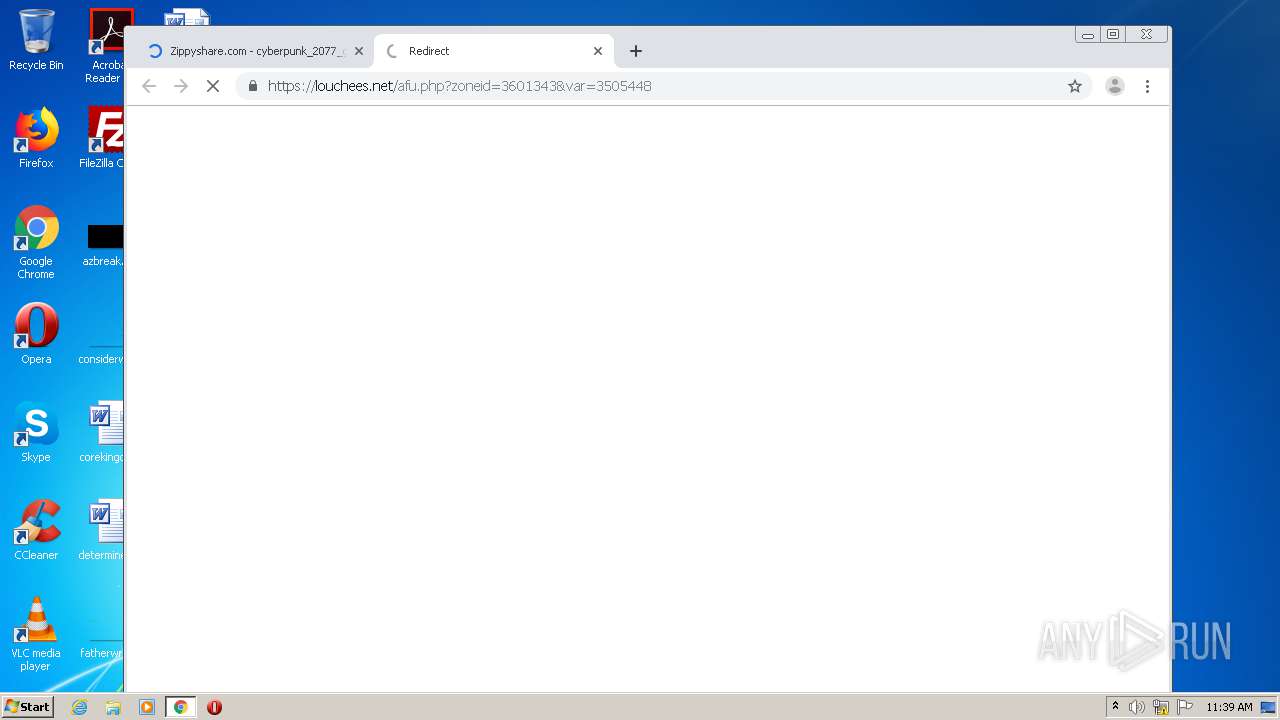
louchees.net |
| malicious |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1056 | svchost.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |