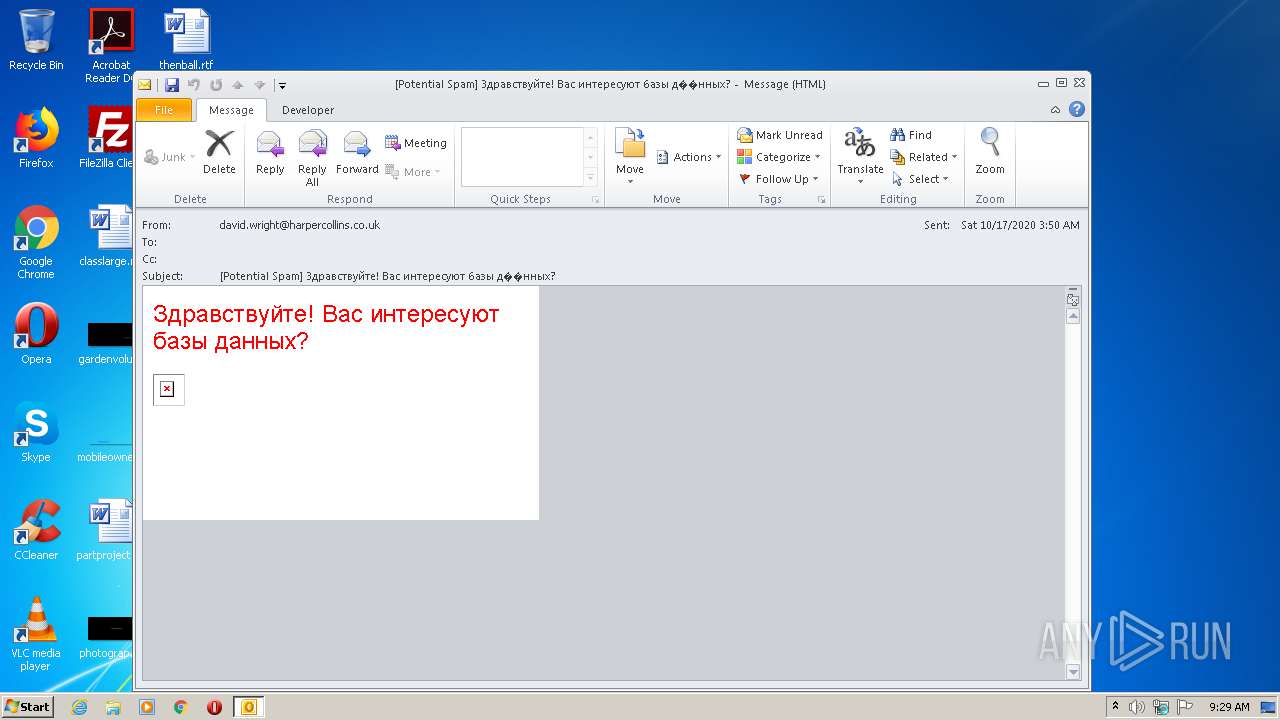
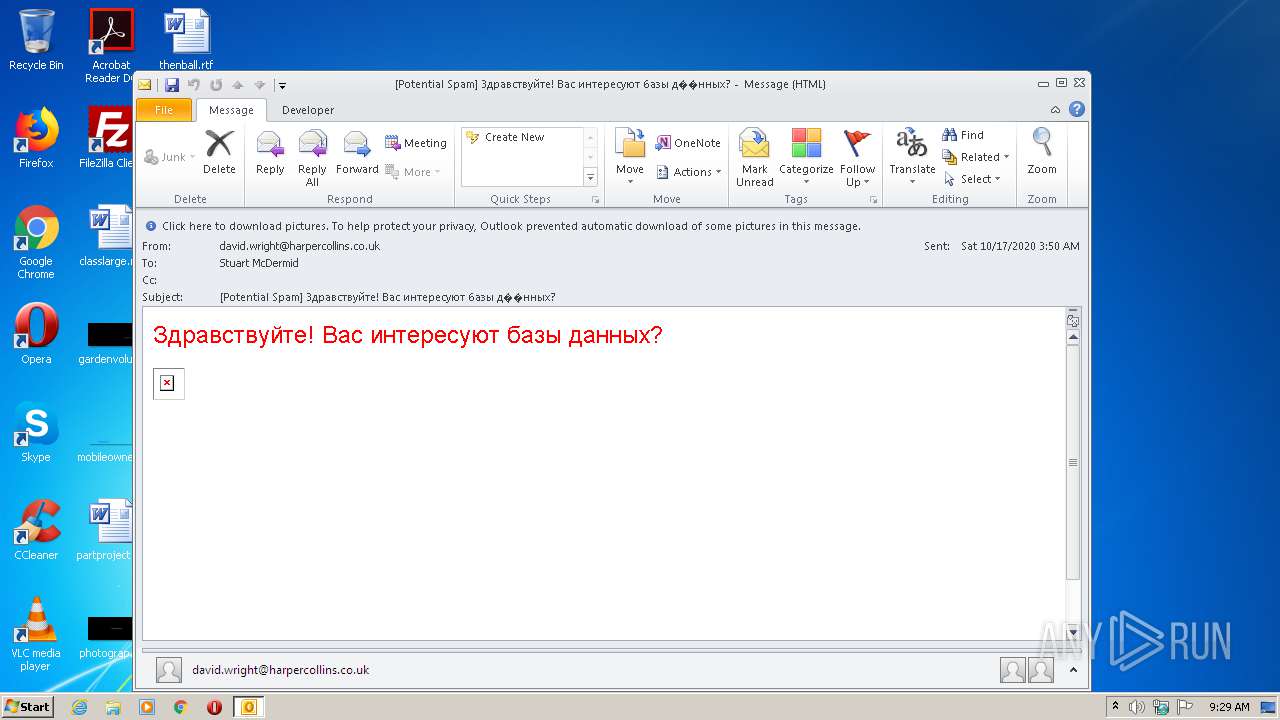
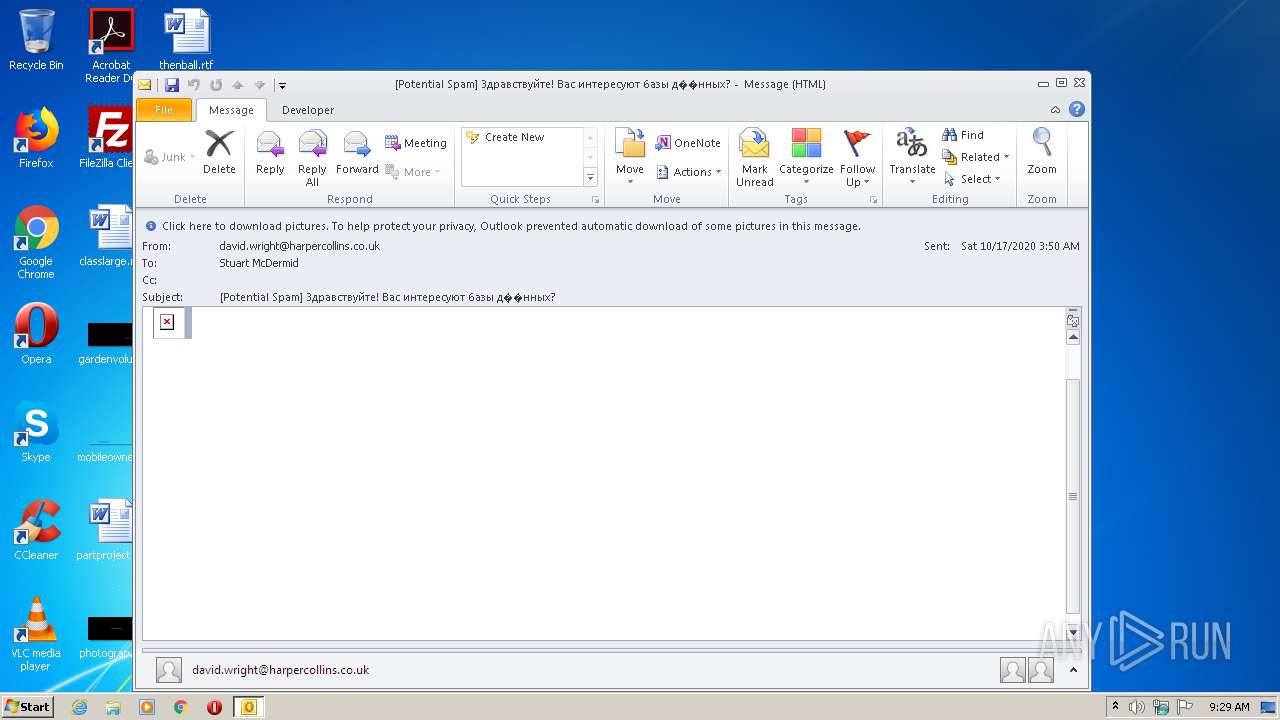
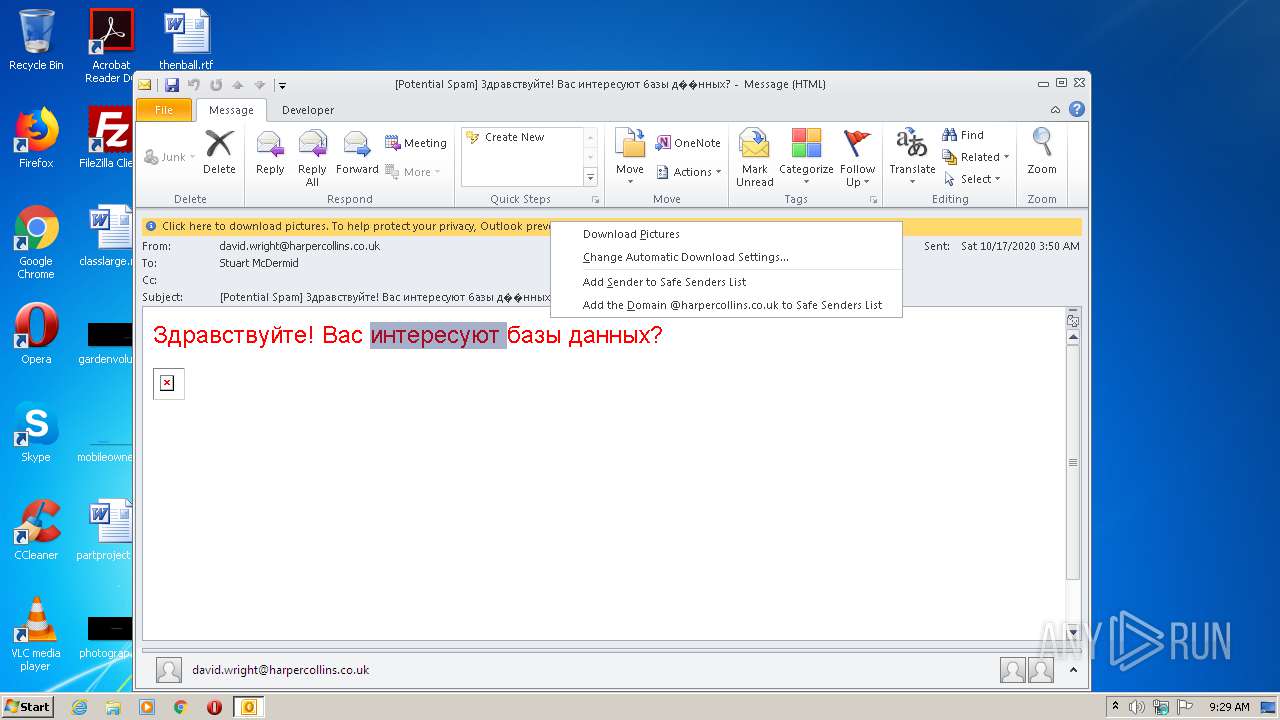
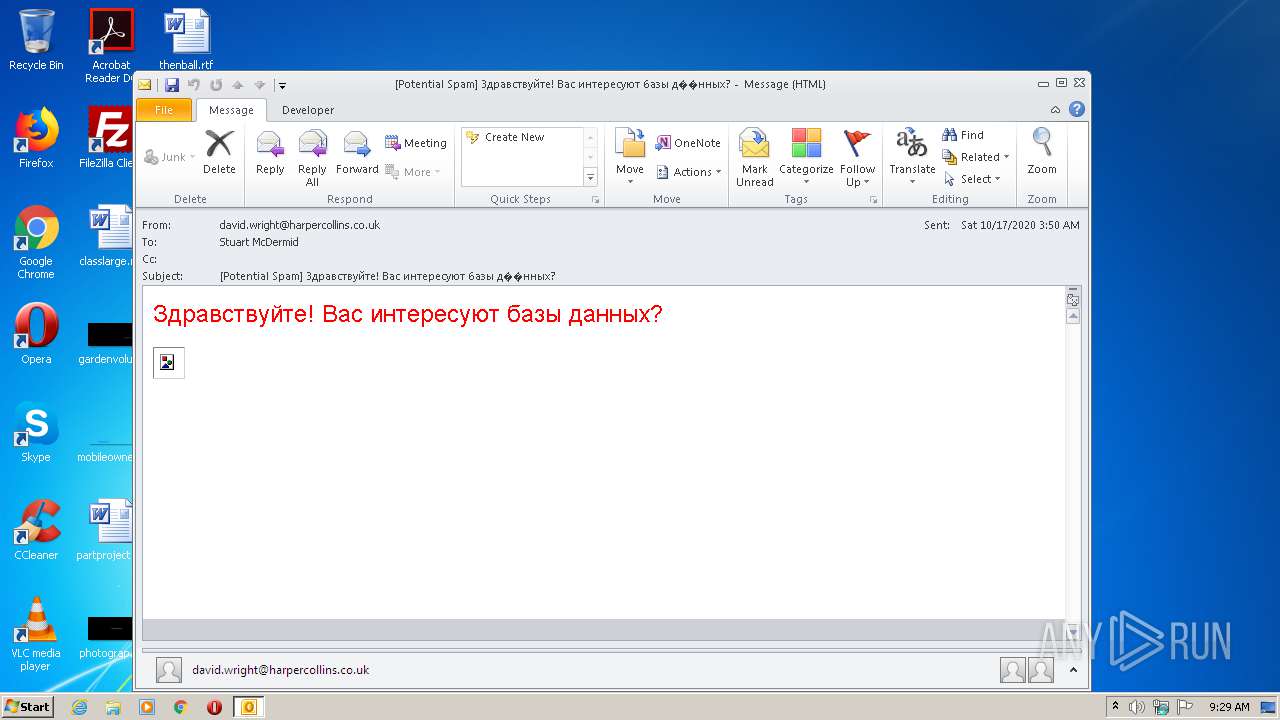
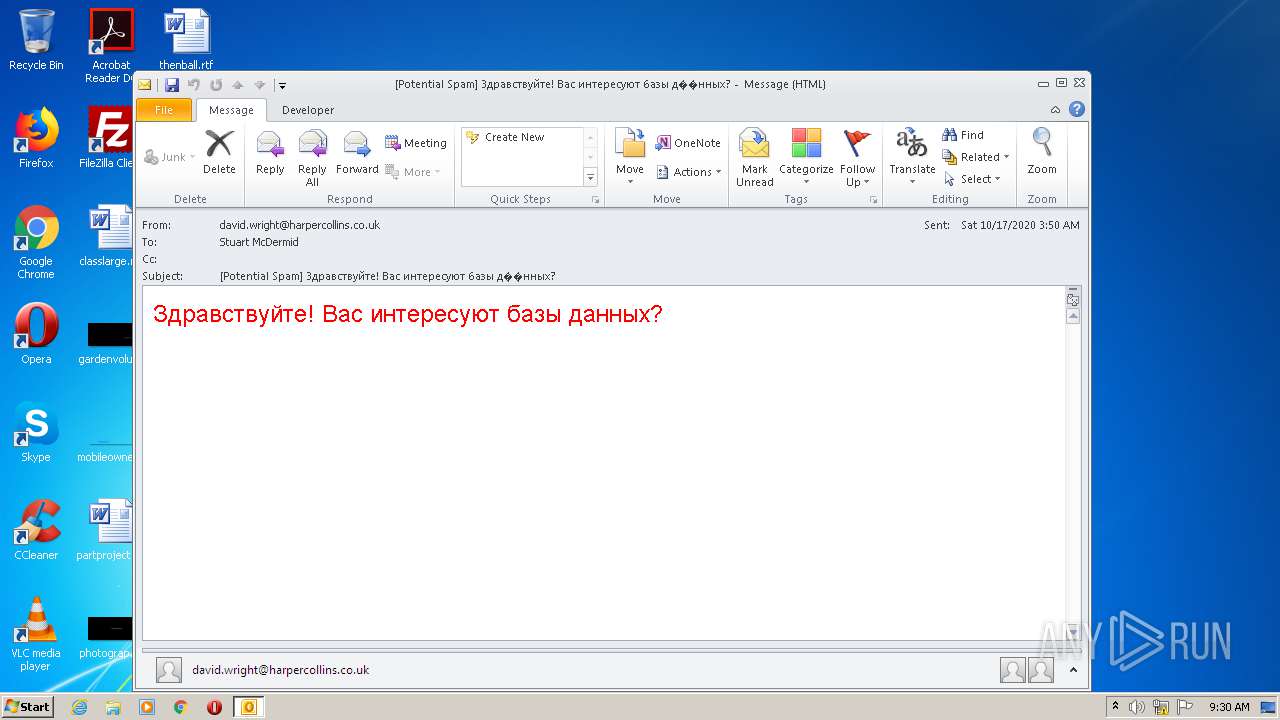
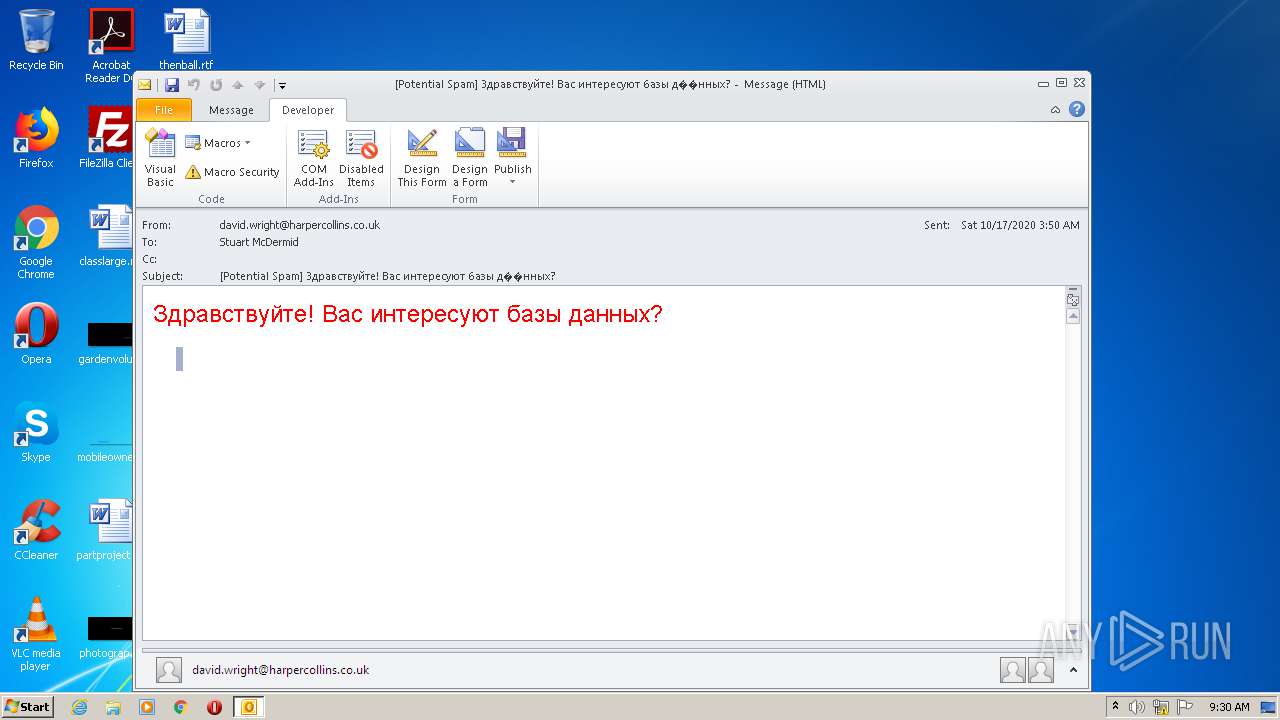
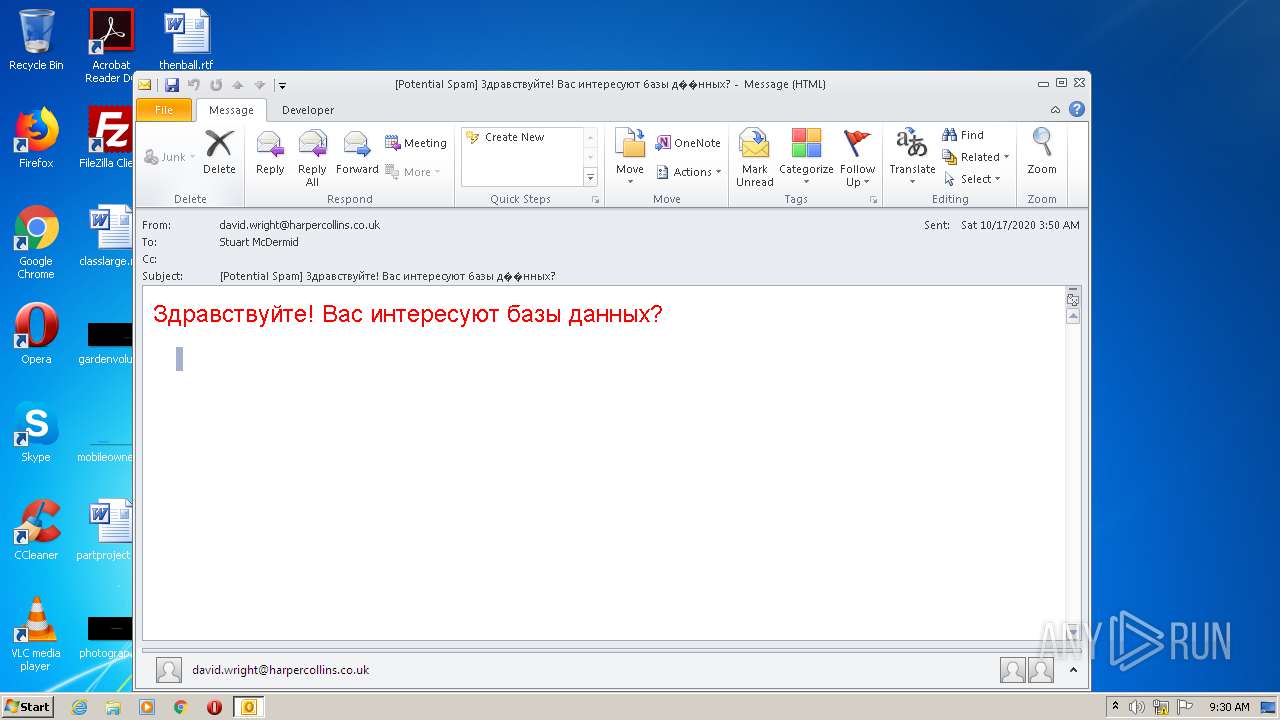
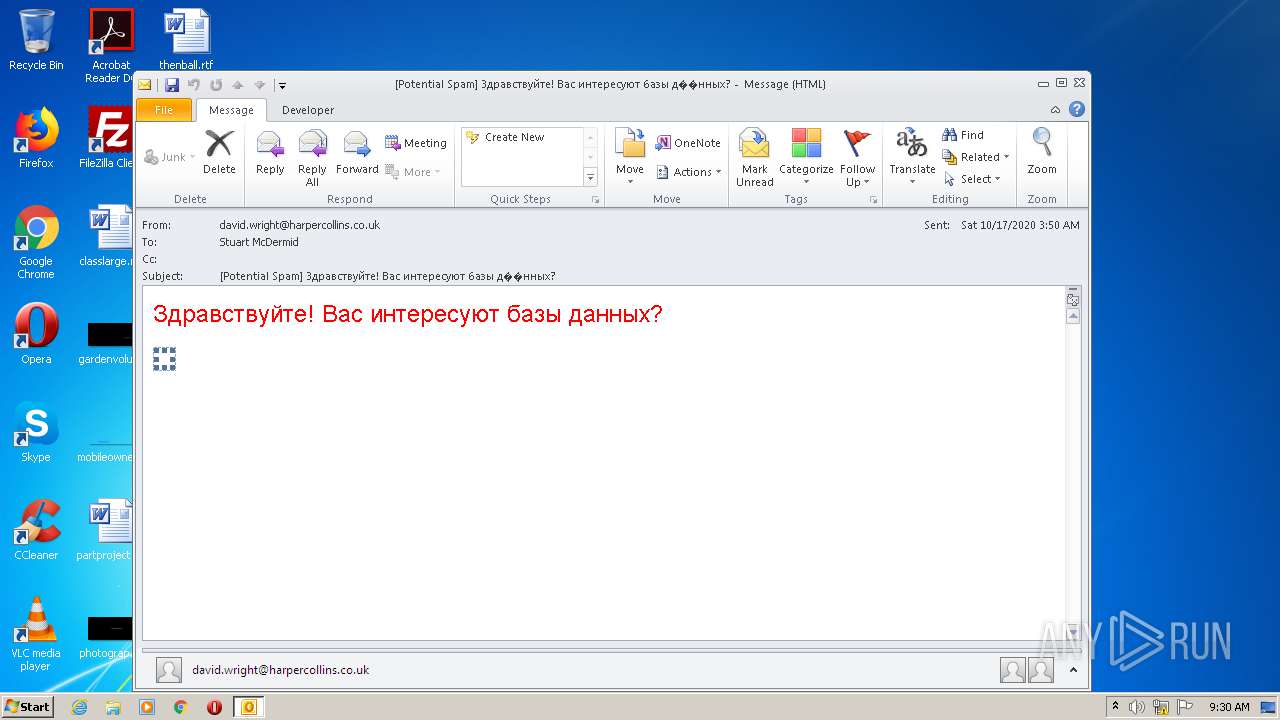
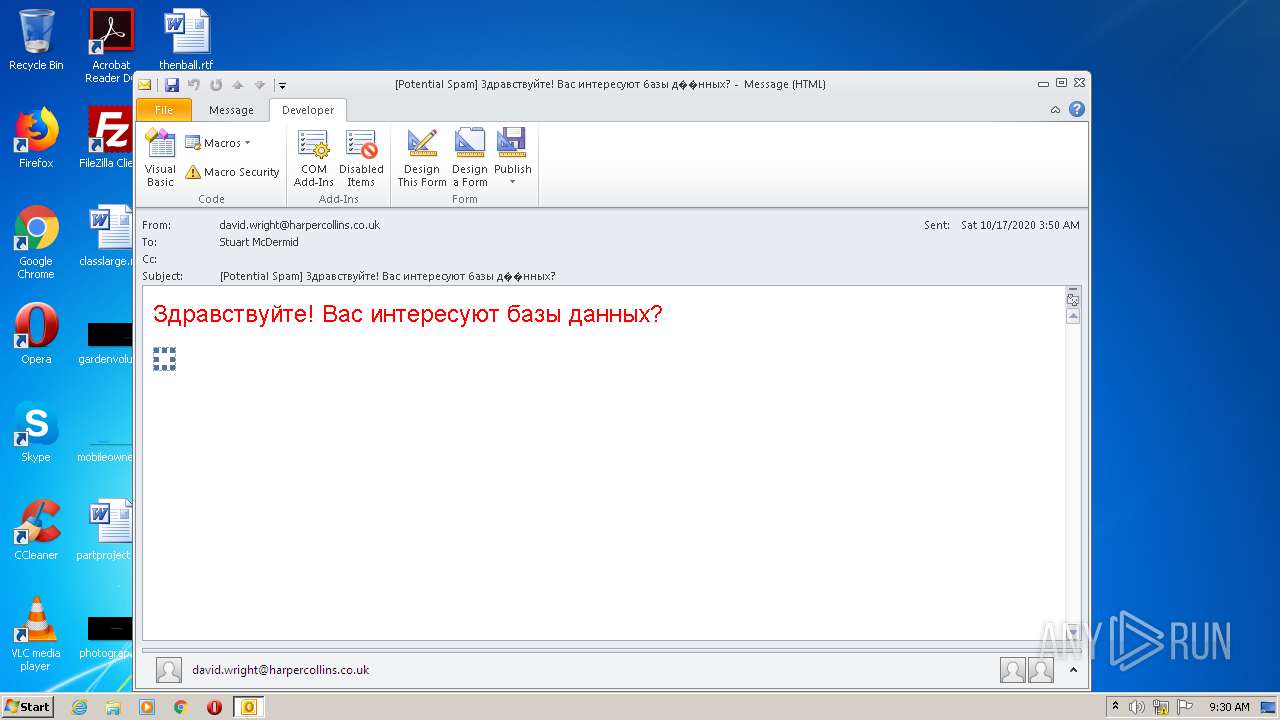
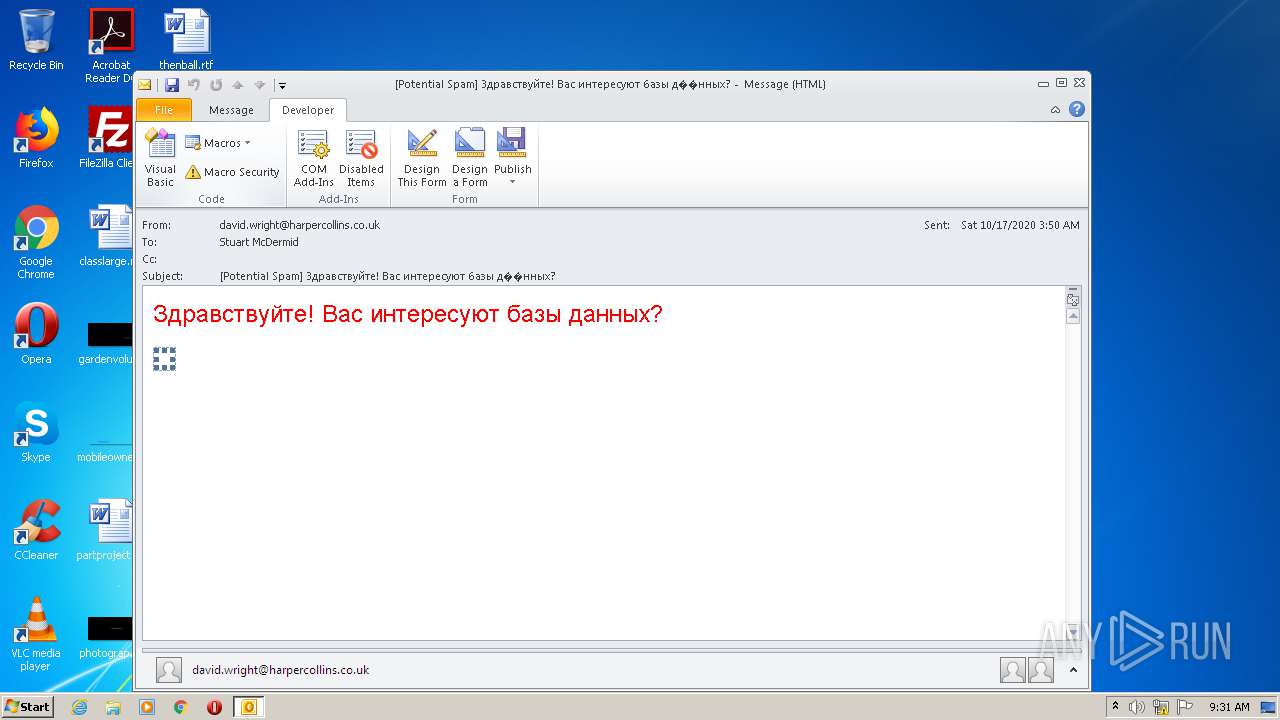
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/c1b77e8e-830c-4085-acdd-8aa7d4d5b11e |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 08:28:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | FE62AED890808C0C2280FA4B616BDDD8 |
| SHA1: | 12033015B1AAE568B214AFC646A99DB95739D631 |
| SHA256: | D3CEEC14C27367B27E1570EE450CE11DFB0586076353E04CF88C605DDAC23455 |
| SSDEEP: | 96:0iRD8+CRwojLUcoo7YVRX2WsMwrVaAjL5jUIQihYTYIPYIF7+dTRLlYFO+FA5LiD:yYWYrIlQRCLCT9FA52L2gx |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3120)
Reads internet explorer settings
- OUTLOOK.EXE (PID: 3120)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3120)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3120)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
37
Monitored processes
1
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3120 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\phish_alert_sp2_2.0.0.0.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
17 906
Read events
7 673
Write events
10 212
Delete events
21
Modification events
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3120) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
7
Text files
35
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR4FBB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\Cab1ABC.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\Tar1ABD.tmp | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\N0E2PI0U.txt | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\T3L2OX6A.txt | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\BK4H5LX5.txt | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\9FF67FB3141440EED32363089565AE60_E4CAD512174D24D3415321B7394484B9 | der | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\config14[1].xml | — | |
MD5:— | SHA256:— | |||
| 3120 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
7
DNS requests
6
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3120 | OUTLOOK.EXE | GET | 200 | 104.27.187.111:80 | http://ipic.su/img/img7/fs/belyj.1602843672.png | US | image | 148 b | whitelisted |
3120 | OUTLOOK.EXE | GET | 304 | 104.27.187.111:80 | http://ipic.su/img/img7/fs/belyj.1602843672.png | US | image | 148 b | whitelisted |
3120 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAtqs7A%2Bsan2xGCSaqjN%2FrM%3D | US | der | 1.47 Kb | whitelisted |
3120 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3120 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3120 | OUTLOOK.EXE | GET | 200 | 52.109.88.8:80 | http://office14client.microsoft.com/config14?UILCID=1033&CLCID=1033&ILCID=1033&HelpLCID=1033&App={CFF13DD8-6EF2-49EB-B265-E3BFC6501C1D}&build=14.0.6023 | NL | xml | 1.99 Kb | whitelisted |
3120 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA%2BUTTAX%2Fq1pMJ1jNafwO%2F0%3D | US | der | 278 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3120 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3120 | OUTLOOK.EXE | 104.27.168.227:443 | goo.su | Cloudflare Inc | US | shared |
3120 | OUTLOOK.EXE | 104.27.187.111:80 | ipic.su | Cloudflare Inc | US | shared |
3120 | OUTLOOK.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3120 | OUTLOOK.EXE | 52.109.88.8:80 | office14client.microsoft.com | Microsoft Corporation | NL | whitelisted |
3120 | OUTLOOK.EXE | 52.109.8.27:443 | rr.office.microsoft.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
goo.su |
| suspicious |
ocsp.digicert.com |
| whitelisted |
ipic.su |
| whitelisted |
office14client.microsoft.com |
| whitelisted |
rr.office.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1048 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
3120 | OUTLOOK.EXE | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3120 | OUTLOOK.EXE | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |