| File name: | d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe |
| Full analysis: | https://app.any.run/tasks/c87dfa68-1729-4497-958f-1a06af27e69a |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2024, 09:27:11 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | AB7F39826E8FA9EFD5E429BF45DF882E |
| SHA1: | 6DF2FDF734A59B35326A2E882E1E8F25A4FD499B |
| SHA256: | D3CD75E8FE17280F8813F00C2E18E4999787E2C6CCF43E20A450D018999E8F0B |
| SSDEEP: | 98304:dh7Jc09d/1Xn0R7PRD+9KWFn1O6Al0QFUv6Azk7prpSPynGRter9t2oEhaI0vZRW:6tS |
MALICIOUS
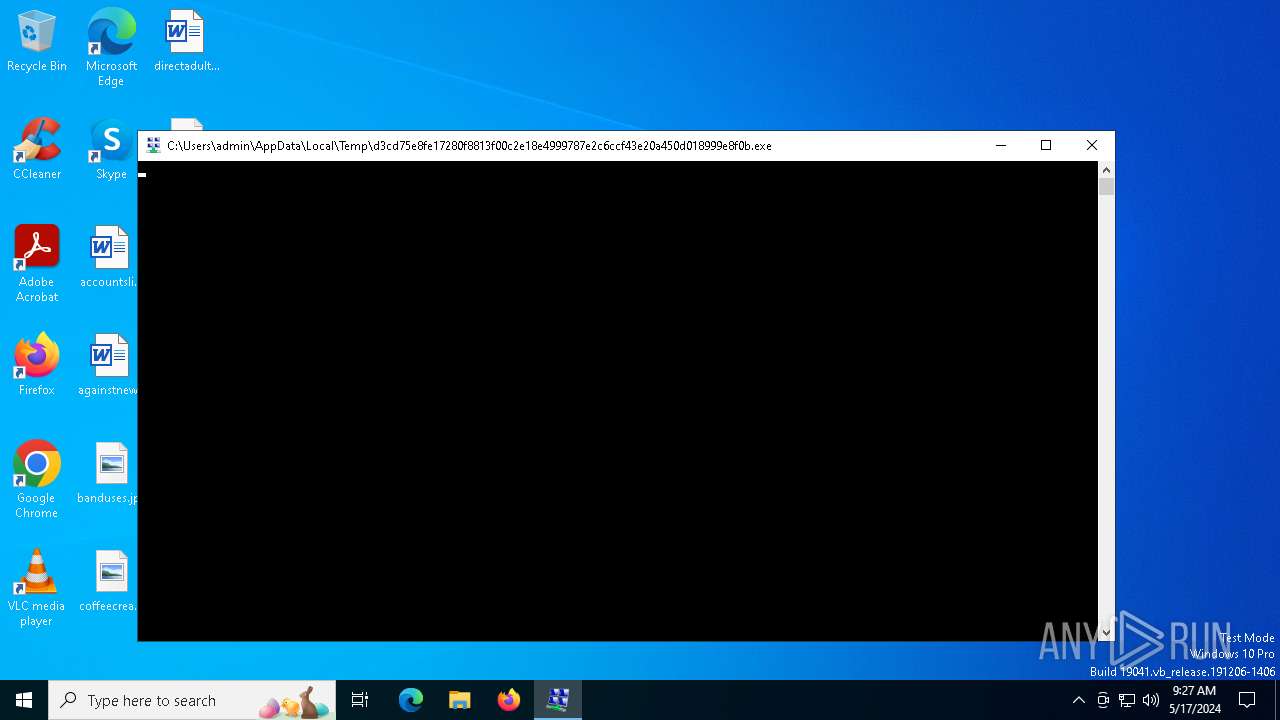
Drops the executable file immediately after the start
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
Creates a writable file in the system directory
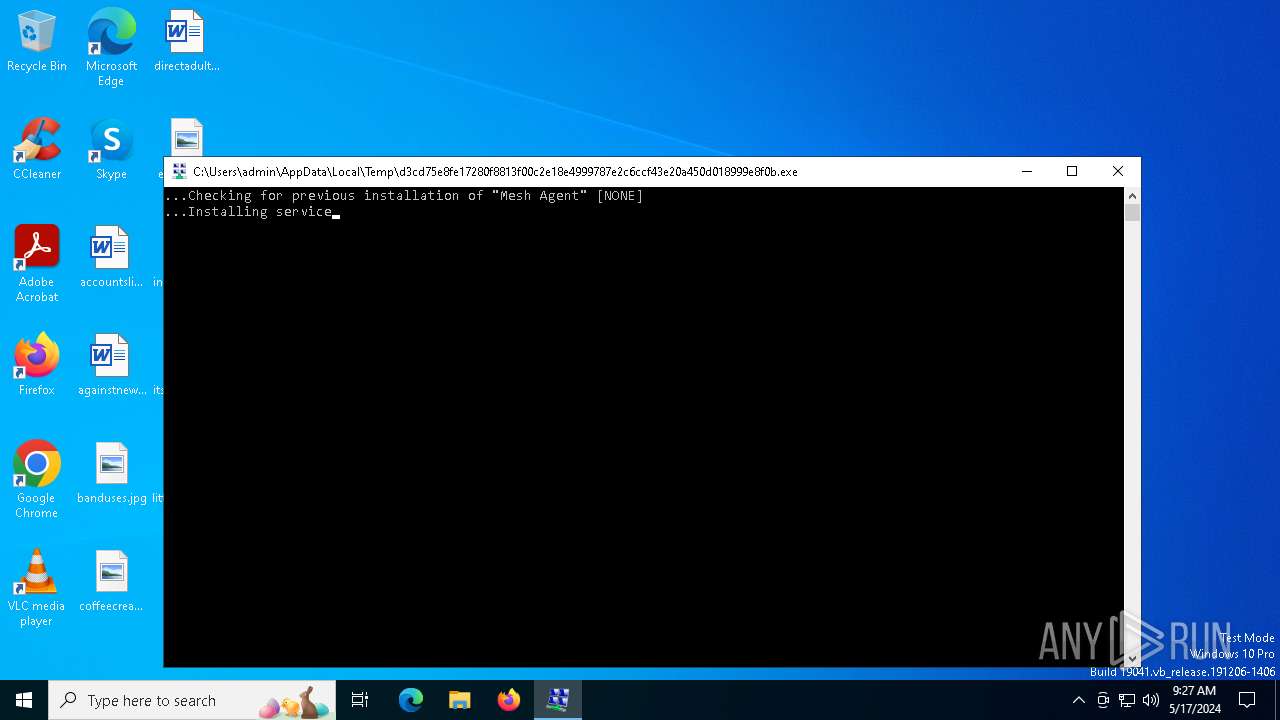
- MeshAgent.exe (PID: 6904)
- powershell.exe (PID: 1724)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 1724)
SUSPICIOUS
Reads the date of Windows installation
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
Reads security settings of Internet Explorer
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
- MeshAgent.exe (PID: 6904)
Uses WMIC.EXE to obtain operating system information
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
- MeshAgent.exe (PID: 6904)
Application launched itself
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
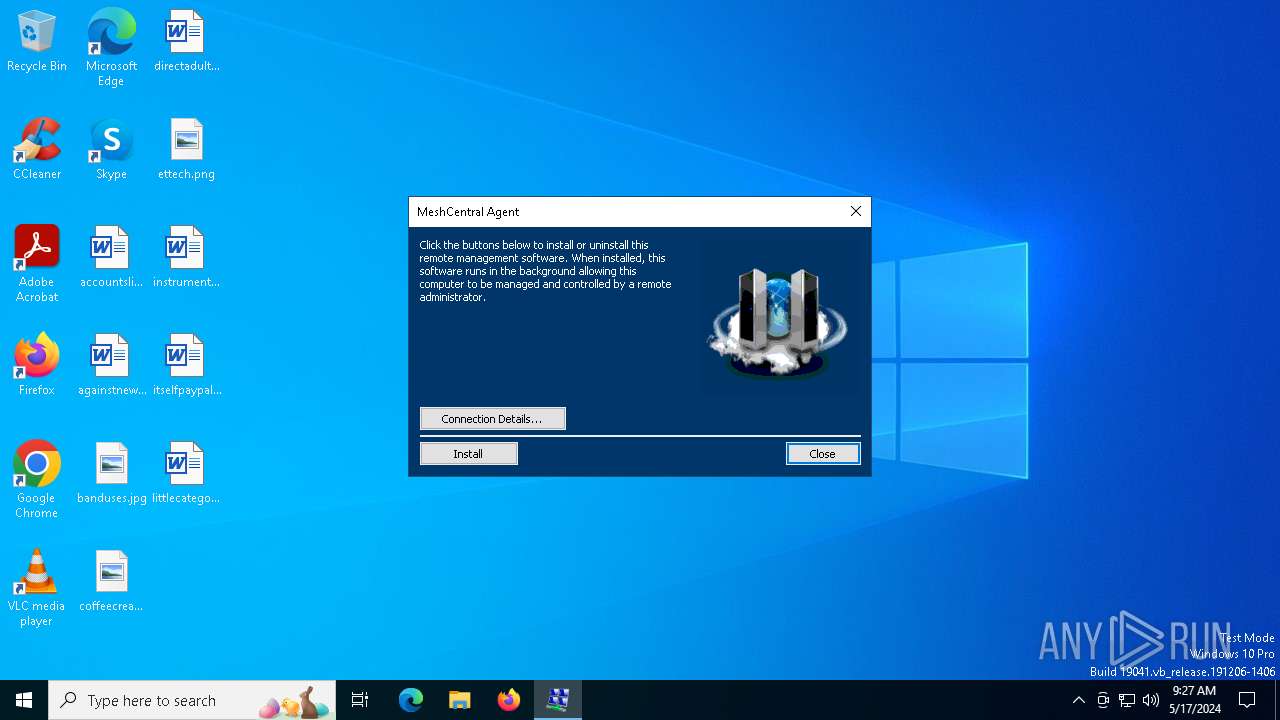
Creates or modifies Windows services
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
Creates a software uninstall entry
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
- MeshAgent.exe (PID: 6904)
Executable content was dropped or overwritten
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
Executes as Windows Service
- MeshAgent.exe (PID: 6904)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1724)
Uses WMIC.EXE to obtain system information
- MeshAgent.exe (PID: 6904)
Uses WMIC.EXE to obtain computer system information
- MeshAgent.exe (PID: 6904)
The process bypasses the loading of PowerShell profile settings
- MeshAgent.exe (PID: 6904)
The process hides Powershell's copyright startup banner
- MeshAgent.exe (PID: 6904)
Starts POWERSHELL.EXE for commands execution
- MeshAgent.exe (PID: 6904)
Starts CMD.EXE for commands execution
- MeshAgent.exe (PID: 6904)
INFO
Checks supported languages
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
- MeshAgent.exe (PID: 6904)
Reads the computer name
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
- MeshAgent.exe (PID: 6904)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6424)
- WMIC.exe (PID: 7036)
- WMIC.exe (PID: 7116)
- WMIC.exe (PID: 1848)
- WMIC.exe (PID: 5712)
- WMIC.exe (PID: 3500)
- WMIC.exe (PID: 2252)
Reads the machine GUID from the registry
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
- MeshAgent.exe (PID: 6904)
Process checks computer location settings
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6328)
Creates files in the program directory
- d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe (PID: 6796)
- MeshAgent.exe (PID: 6904)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5228)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 5228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:12:09 20:13:19+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 2458112 |
| InitializedDataSize: | 1511936 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c1570 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x0017 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | MeshCentral Background Service Agent |
| FileVersion: | 2022-Dec-2 11:42:16-0800 |
| LegalCopyright: | Apache 2.0 License |
| ProductName: | MeshCentral Agent |
| ProductVersion: | Commit: 2022-Dec-2 11:42:16-0800 |
Total processes
161
Monitored processes
30
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1724 | powershell -noprofile -nologo -command - | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1848 | wmic ComputerSystem get PCSystemType /FORMAT:"C:\WINDOWS\system32\wbem\en-US\csv" | C:\Windows\SysWOW64\wbem\WMIC.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2252 | wmic ComputerSystem get PCSystemType /FORMAT:"C:\WINDOWS\system32\wbem\en-US\csv" | C:\Windows\SysWOW64\wbem\WMIC.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2528 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3500 | wmic SystemEnclosure get ChassisTypes | C:\Windows\SysWOW64\wbem\WMIC.exe | — | MeshAgent.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3528 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 3700 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | WMIC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
37 018
Read events
36 950
Write events
68
Delete events
0
Modification events
| (PID) Process: | (6328) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6328) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6328) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6328) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6796) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Mesh Agent |
| Operation: | write | Name: | ImagePath |
Value: "C:\Program Files (x86)\Mesh Agent\MeshAgent.exe" --installedByUser="S-1-5-21-1693682860-607145093-2874071422-1001" | |||
| (PID) Process: | (6796) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Mesh Agent |
| Operation: | write | Name: | _InstalledBy |
Value: S-1-5-21-1693682860-607145093-2874071422-1001 | |||
| (PID) Process: | (6796) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Mesh Agent |
| Operation: | write | Name: | DisplayName |
Value: Mesh Agent | |||
| (PID) Process: | (6796) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Mesh Agent |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Mesh Agent\MeshAgent.exe | |||
| (PID) Process: | (6796) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Mesh Agent |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Mesh Agent\ | |||
| (PID) Process: | (6796) d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Mesh Agent |
| Operation: | write | Name: | EstimatedSize |
Value: 3751 | |||
Executable files
1
Suspicious files
9
Text files
15
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6904 | MeshAgent.exe | C:\Program Files (x86)\Mesh Agent\MeshAgent.msh | text | |
MD5:BD35E8EF92A95D68A7D64F7B980D277C | SHA256:138DC0CF2F475477C3FC4922B0F5BB2C962DDC3D49EF9351B25BDDEC19261234 | |||
| 6796 | d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | C:\Program Files (x86)\Mesh Agent\MeshAgent.exe | executable | |
MD5:AB7F39826E8FA9EFD5E429BF45DF882E | SHA256:D3CD75E8FE17280F8813F00C2E18E4999787E2C6CCF43E20A450D018999E8F0B | |||
| 1724 | powershell.exe | C:\WINDOWS\TEMP\__PSScriptPolicyTest_to3butyx.2jo.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6904 | MeshAgent.exe | C:\Program Files (x86)\Mesh Agent\MeshAgent.db | binary | |
MD5:3EA30E3BAE63193A411F2B0C609F6167 | SHA256:CED933993F5A90E069CAF1CE58BD7DAB06673DFD248E78BA9BC58D9E27B70D14 | |||
| 6368 | powershell.exe | C:\WINDOWS\TEMP\__PSScriptPolicyTest_g4i111rc.q54.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6444 | powershell.exe | C:\WINDOWS\TEMP\__PSScriptPolicyTest_b4c5blvu.ngn.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6904 | MeshAgent.exe | C:\Program Files (x86)\Mesh Agent\MeshAgent.db.tmp | binary | |
MD5:04B19A6051B8A6876A85739C87E3769C | SHA256:9712D1B1DF26272D9E6DAAA3DE6BAD5A953C11C14ED90D31B63FEE5C11098D5F | |||
| 1724 | powershell.exe | C:\WINDOWS\SysWOW64\config\systemprofile\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-Interactive | binary | |
MD5:FA1FDFF13790F7422478BCFAF5EADF6B | SHA256:83CD23F953DF8F38B49ABF6345A91F3C56914B8B2733121A23530FC0F6212ECC | |||
| 6904 | MeshAgent.exe | C:\WINDOWS\system32\config\systemprofile\AppData\Roaming\Microsoft\SystemCertificates\My\Keys\43BA8B9D32180B803BB22F5ADB728DA6226022D9 | binary | |
MD5:B307617C0FB1753507330E29628B93A2 | SHA256:98F4E9D5785B1CC4725AAA66B68D11AA8B150D21987AD696DA7DD9D656BE48DD | |||
| 6368 | powershell.exe | C:\WINDOWS\TEMP\__PSScriptPolicyTest_0jq0kv5c.otl.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
47
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4380 | svchost.exe | GET | 200 | 23.53.41.90:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
4380 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
3052 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
4620 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
4620 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
1012 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4380 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5504 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4380 | svchost.exe | 23.53.41.90:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
4380 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
6904 | MeshAgent.exe | 3.122.76.20:443 | manage.clientdesk.help | AMAZON-02 | DE | unknown |
4680 | SearchApp.exe | 104.126.37.136:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
manage.clientdesk.help |
| unknown |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
Process | Message |
|---|---|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | normal block at 0x04489868, 89 bytes long.
|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | ..\microscript\ILibDuktape_ScriptContainer.c(1612) : |
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | normal block at 0x04666E38, 101 bytes long.
|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Dumping objects ->
|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | ..\microscript\ILibDuktape_ScriptContainer.c(1612) : |
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Data: <7 broe > 37 00 00 00 04 00 00 00 62 72 6F 65 00 00 00 00
|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Data: <( broe > 28 00 00 00 04 00 00 00 62 72 6F 65 00 00 00 00
|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | normal block at 0x0463C6A0, 76 bytes long.
|
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | {82164} |
d3cd75e8fe17280f8813f00c2e18e4999787e2c6ccf43e20a450d018999e8f0b.exe | Data: <9 broe > 39 00 00 00 04 00 00 00 62 72 6F 65 00 00 00 00
|