| File name: | IPCPlayerInstall.exe |
| Full analysis: | https://app.any.run/tasks/d23dd36f-6e76-4324-be87-717c7d3540a6 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 12:16:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | CE7977D932913B7E1D1DF12BF607644E |
| SHA1: | 014C294E14C5B2B3590026D7057E716C52AC58C1 |
| SHA256: | D3C255178D9A42C9CFA8052ABE4EBEBF9E708F33D7367E2B60DE85058273B827 |
| SSDEEP: | 98304:T3j8kD1cVNo8Uzwdik2/izjqEORfchNMuGyFF+fOGW/jt2JNz76miHS7GkIE:0kgNmzwddhnUfSNntYfO/oNz76dmJIE |
MALICIOUS
Changes the autorun value in the registry
- rundll32.exe (PID: 1880)
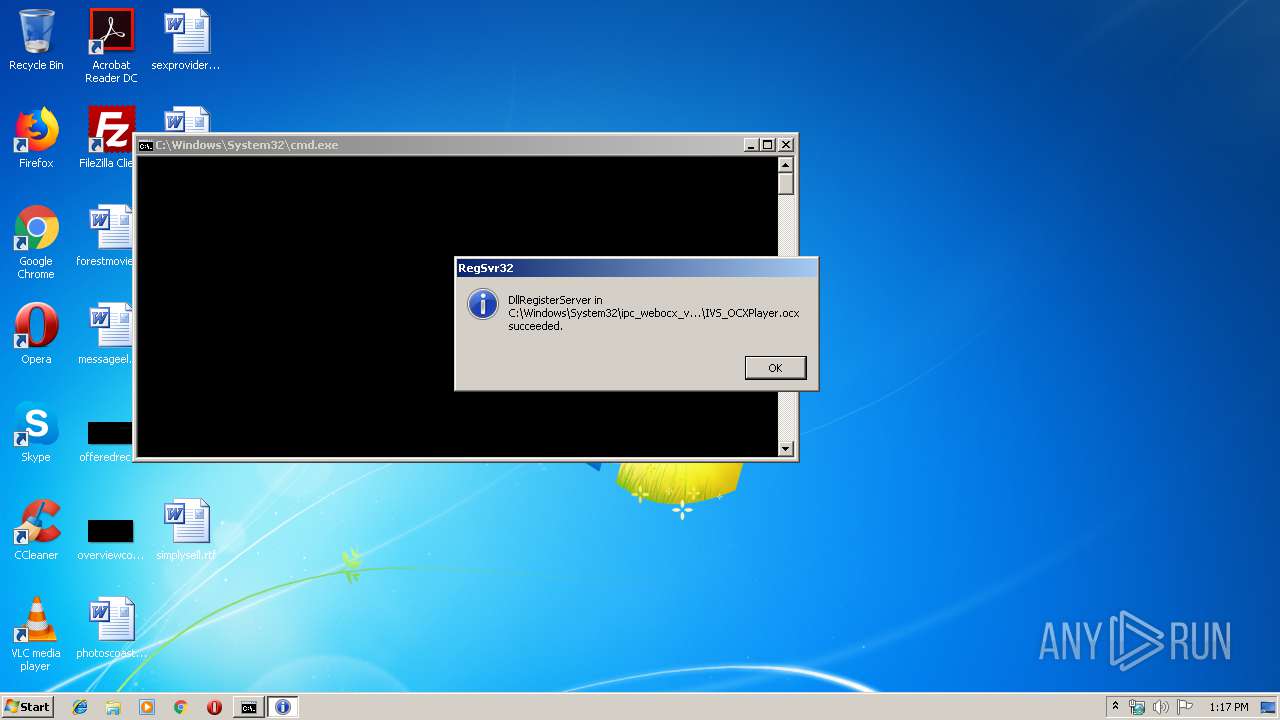
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3936)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2644)
SUSPICIOUS
Removes files from Windows directory
- rundll32.exe (PID: 1880)
Executes scripts
- IPCPlayerInstall.exe (PID: 3652)
Executable content was dropped or overwritten
- IPCPlayerInstall.exe (PID: 3652)
- rundll32.exe (PID: 1880)
Reads internet explorer settings
- IPCPlayerInstall.exe (PID: 3652)
Uses RUNDLL32.EXE to load library
- WScript.exe (PID: 3828)
Creates files in the program directory
- IPCPlayerInstall.exe (PID: 3652)
Starts CMD.EXE for commands execution
- WScript.exe (PID: 3828)
Creates files in the Windows directory
- rundll32.exe (PID: 1880)
Uses REG.EXE to modify Windows registry
- WScript.exe (PID: 3828)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.8) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.2) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Generic Win/DOS Executable (0.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2008:09:16 16:17:44+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 81920 |
| InitializedDataSize: | 22528 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 16-Sep-2008 14:17:44 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 16-Sep-2008 14:17:44 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00014000 | 0x00013A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.48361 |
.data | 0x00015000 | 0x00008000 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.93186 |
.idata | 0x0001D000 | 0x00002000 | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.78952 |
.rsrc | 0x0001F000 | 0x00003BB0 | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.72086 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.08342 | 831 | Latin 1 / Western European | Russian - Russia | RT_MANIFEST |
2 | 3.88998 | 1384 | Latin 1 / Western European | Russian - Russia | RT_ICON |
3 | 4.12176 | 744 | Latin 1 / Western European | Russian - Russia | RT_ICON |
4 | 4.68705 | 2216 | Latin 1 / Western European | Russian - Russia | RT_ICON |
7 | 3.24143 | 556 | Latin 1 / Western European | Russian - Russia | RT_STRING |
8 | 3.28574 | 946 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 3.04375 | 530 | Latin 1 / Western European | Russian - Russia | RT_STRING |
10 | 3.15563 | 638 | Latin 1 / Western European | Russian - Russia | RT_STRING |
100 | 2.6902 | 62 | Latin 1 / Western European | Russian - Russia | RT_GROUP_ICON |
101 | 4.19099 | 2998 | Latin 1 / Western European | Russian - Russia | RT_BITMAP |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
47
Monitored processes
9
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
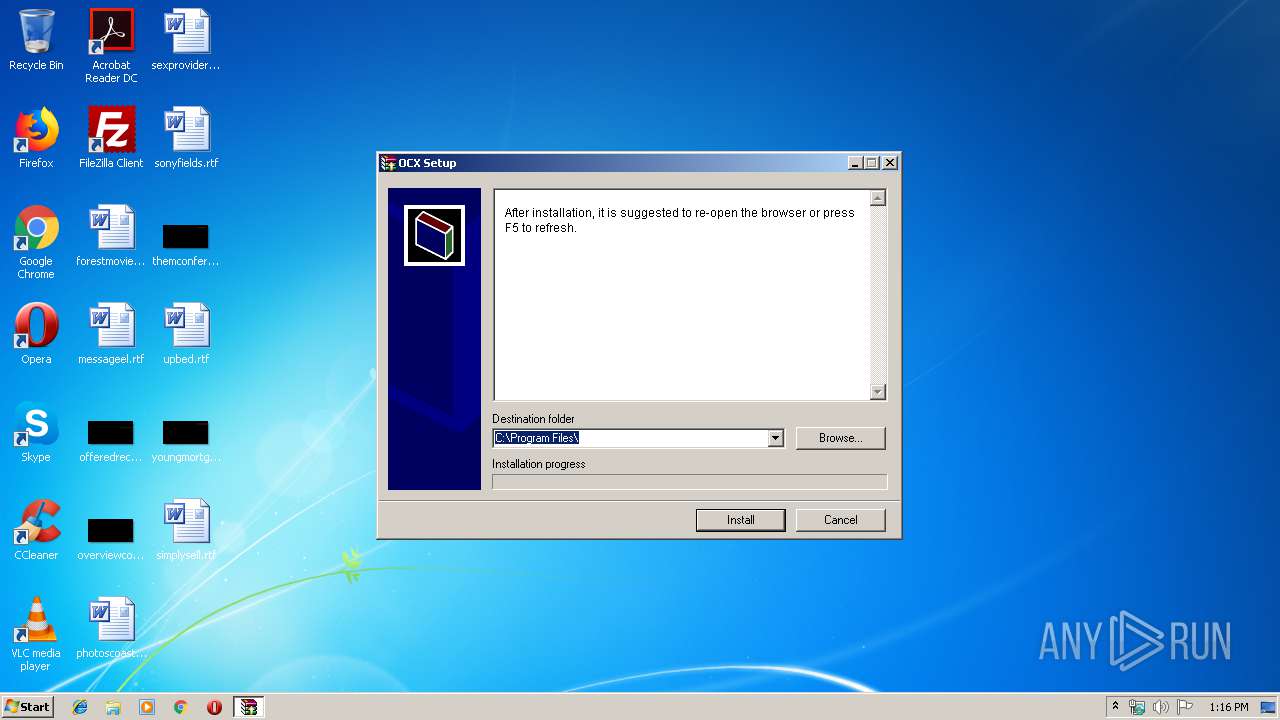
| 1880 | "C:\Windows\System32\rundll32.exe" SETUPAPI.DLL,InstallHinfSection DefaultInstall 132 C:\Program Files\IPCPlayerInstall\IVS_OCXPlayer.inf | C:\Windows\System32\rundll32.exe | WScript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2380 | "C:\Windows\System32\reg.exe" add "HKEY_LOCAL_MACHINE\SOFTWARE\MozillaPlugins\IVS_Media\MimeTypes\application/IVS_MediaPlay-plugin" | C:\Windows\System32\reg.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | regsvr32 C:\Windows\System32\ipc_webocx_vware\3.3.0.9\IVS_OCXPlayer.ocx | C:\Windows\system32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2972 | "C:\Windows\system32\runonce.exe" -r | C:\Windows\system32\runonce.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Run Once Wrapper Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3184 | "C:\Users\admin\AppData\Local\Temp\IPCPlayerInstall.exe" | C:\Users\admin\AppData\Local\Temp\IPCPlayerInstall.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
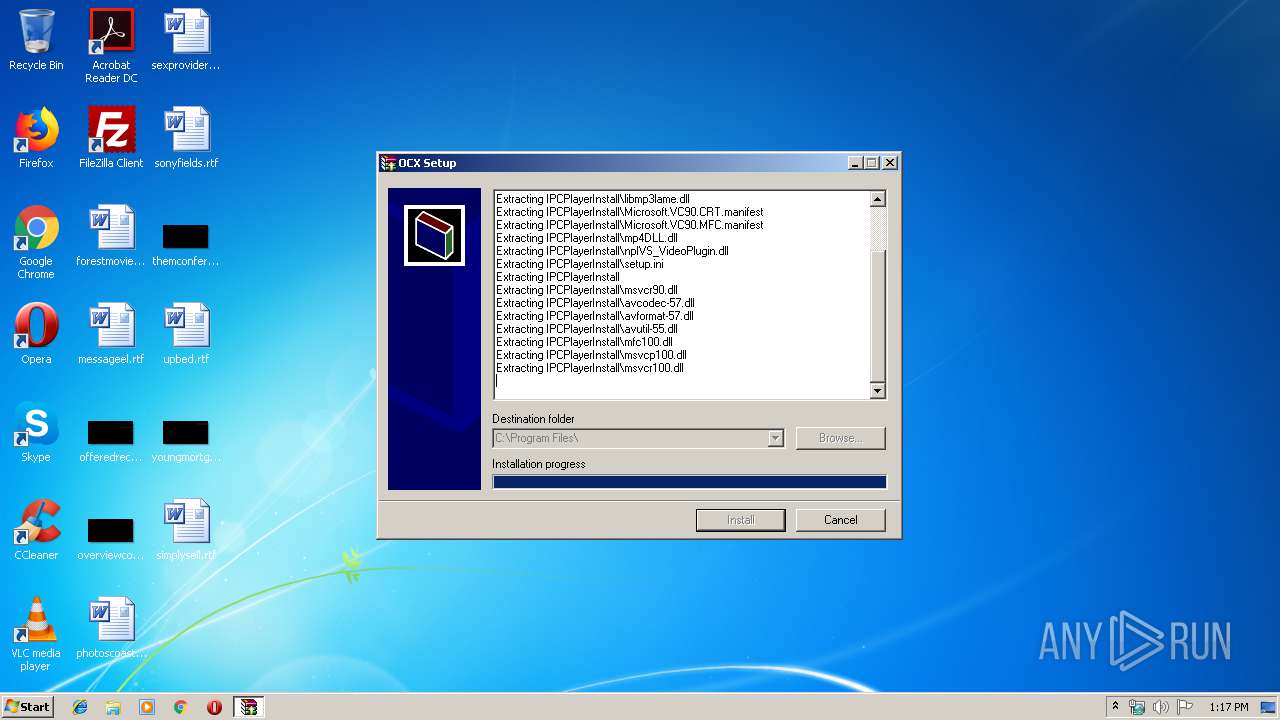
| 3652 | "C:\Users\admin\AppData\Local\Temp\IPCPlayerInstall.exe" | C:\Users\admin\AppData\Local\Temp\IPCPlayerInstall.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3816 | "C:\Windows\System32\grpconv.exe" -o | C:\Windows\System32\grpconv.exe | — | runonce.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3828 | "C:\Windows\System32\WScript.exe" "C:\Program Files\IPCPlayerInstall\Install.vbe" | C:\Windows\System32\WScript.exe | — | IPCPlayerInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3936 | "C:\Windows\System32\cmd.exe" /c regsvr32 C:\Windows\System32\ipc_webocx_vware\3.3.0.9\IVS_OCXPlayer.ocx | C:\Windows\System32\cmd.exe | — | WScript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
255
Read events
192
Write events
62
Delete events
1
Modification events
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3652) IPCPlayerInstall.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\IPCPlayerInstall_RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
28
Suspicious files
0
Text files
37
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3652 | IPCPlayerInstall.exe | C:\Program Files\IPCPlayerInstall\npIVS_VideoPlugin.dll | executable | |
MD5:— | SHA256:— | |||
| 1880 | rundll32.exe | C:\Windows\system32\ipc_webocx_vware\3.3.0.9\SET17D1.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | IPCPlayerInstall.exe | C:\Program Files\IPCPlayerInstall\Install.vbe | text | |
MD5:— | SHA256:— | |||
| 1880 | rundll32.exe | C:\Windows\system32\ipc_webocx_vware\3.3.0.9\SET17D2.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | IPCPlayerInstall.exe | C:\Program Files\IPCPlayerInstall\IPC_V2R2_Player.dll | executable | |
MD5:— | SHA256:— | |||
| 1880 | rundll32.exe | C:\Windows\system32\ipc_webocx_vware\3.3.0.9\SET17E2.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | IPCPlayerInstall.exe | C:\Program Files\IPCPlayerInstall\avcodec-57.dll | executable | |
MD5:— | SHA256:— | |||
| 1880 | rundll32.exe | C:\Windows\system32\ipc_webocx_vware\3.3.0.9\SET17E3.tmp | — | |
MD5:— | SHA256:— | |||
| 3652 | IPCPlayerInstall.exe | C:\Program Files\IPCPlayerInstall\libmp3lame.dll | executable | |
MD5:— | SHA256:— | |||
| 1880 | rundll32.exe | C:\Windows\system32\ipc_webocx_vware\3.3.0.9\SET17F4.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report