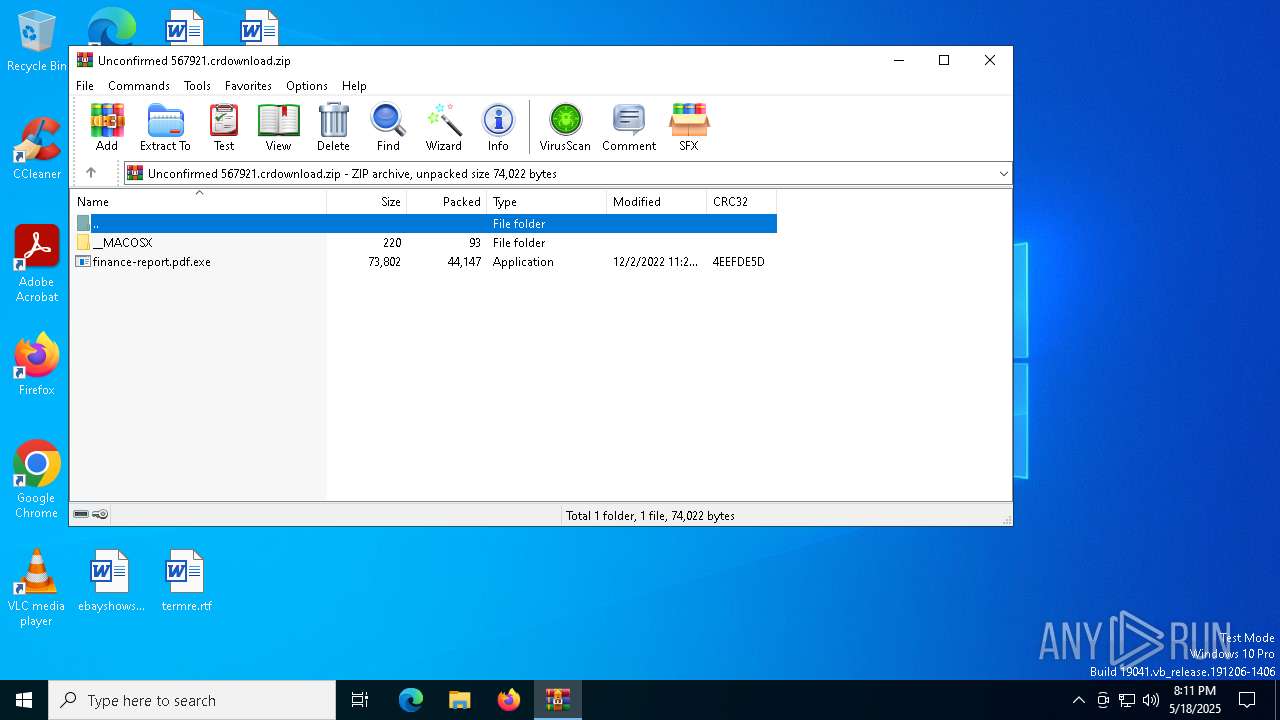
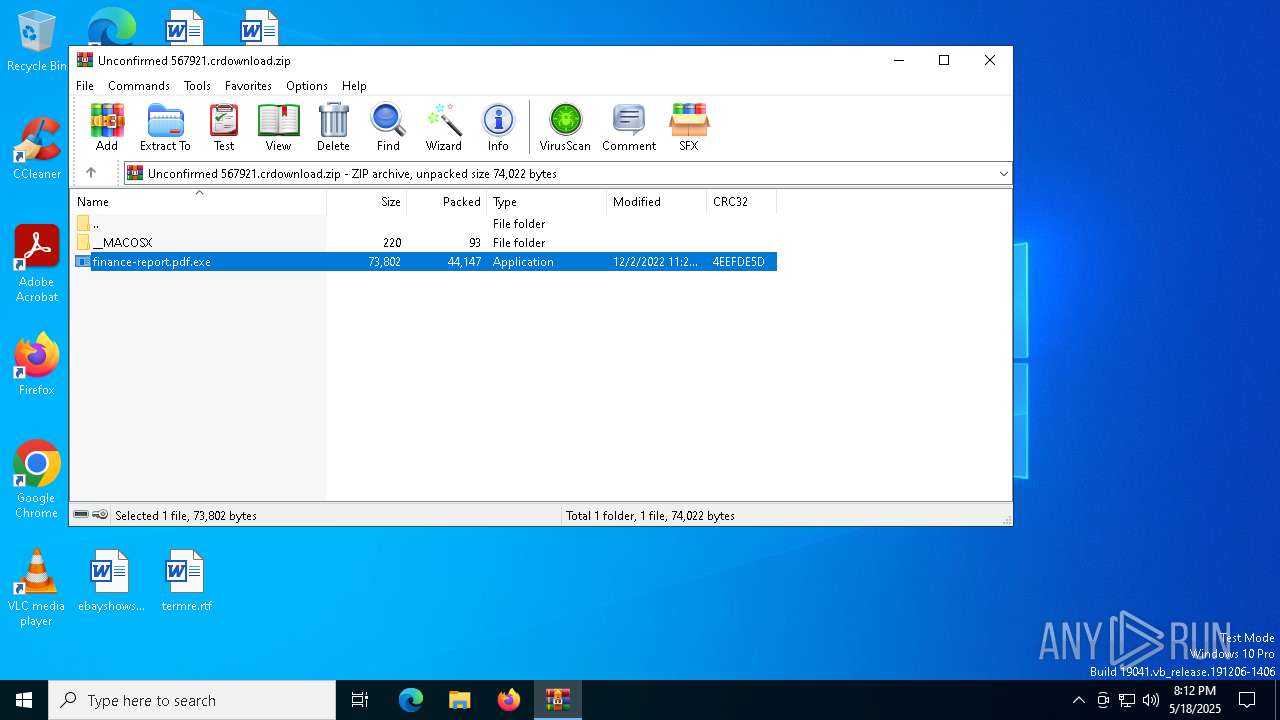
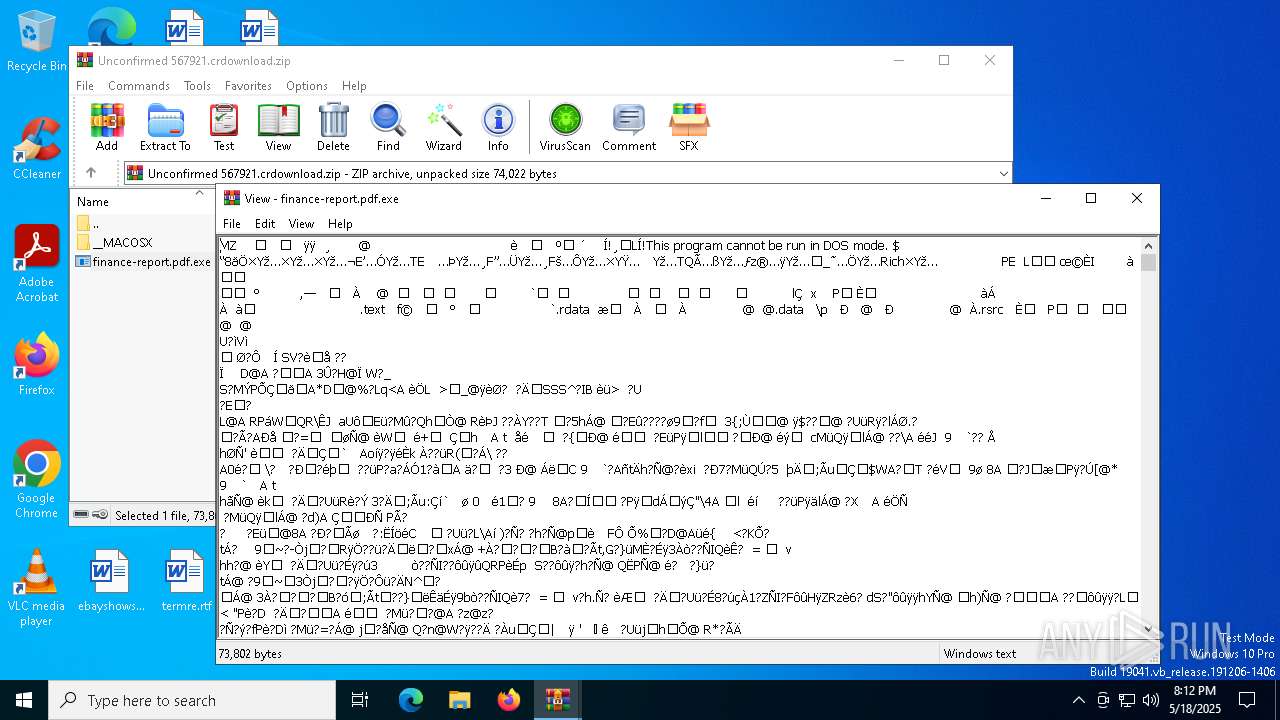
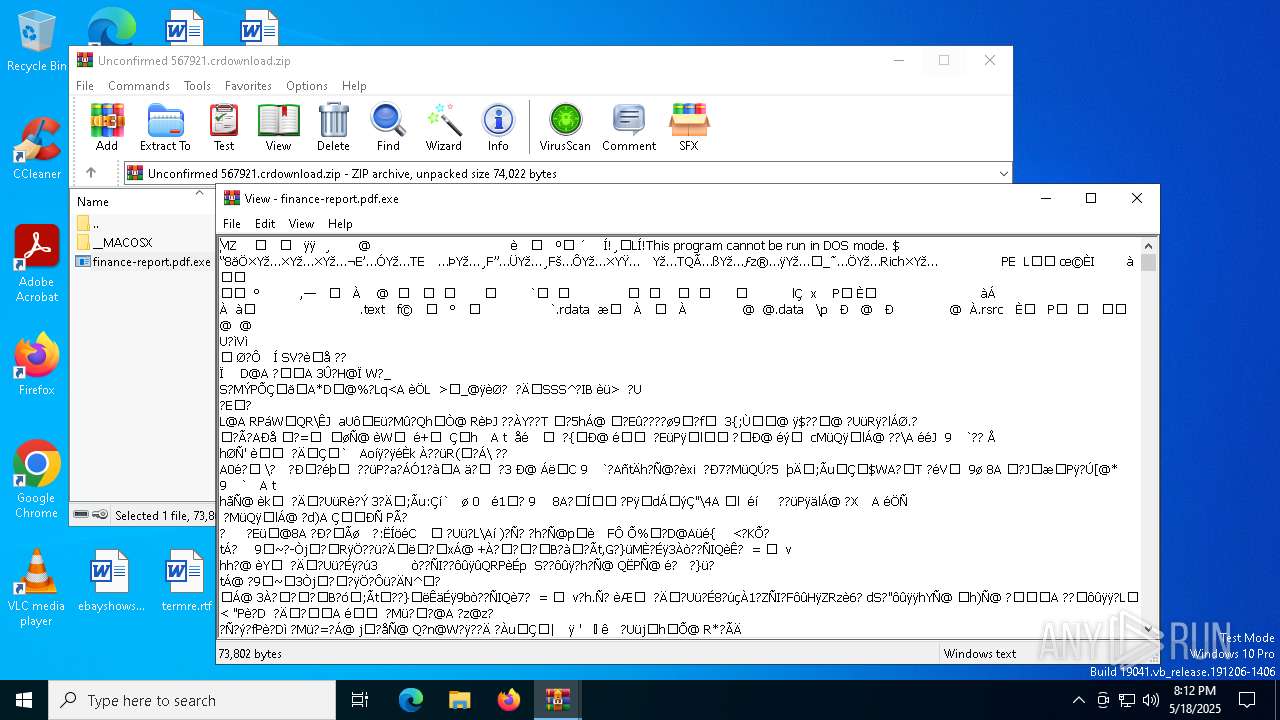
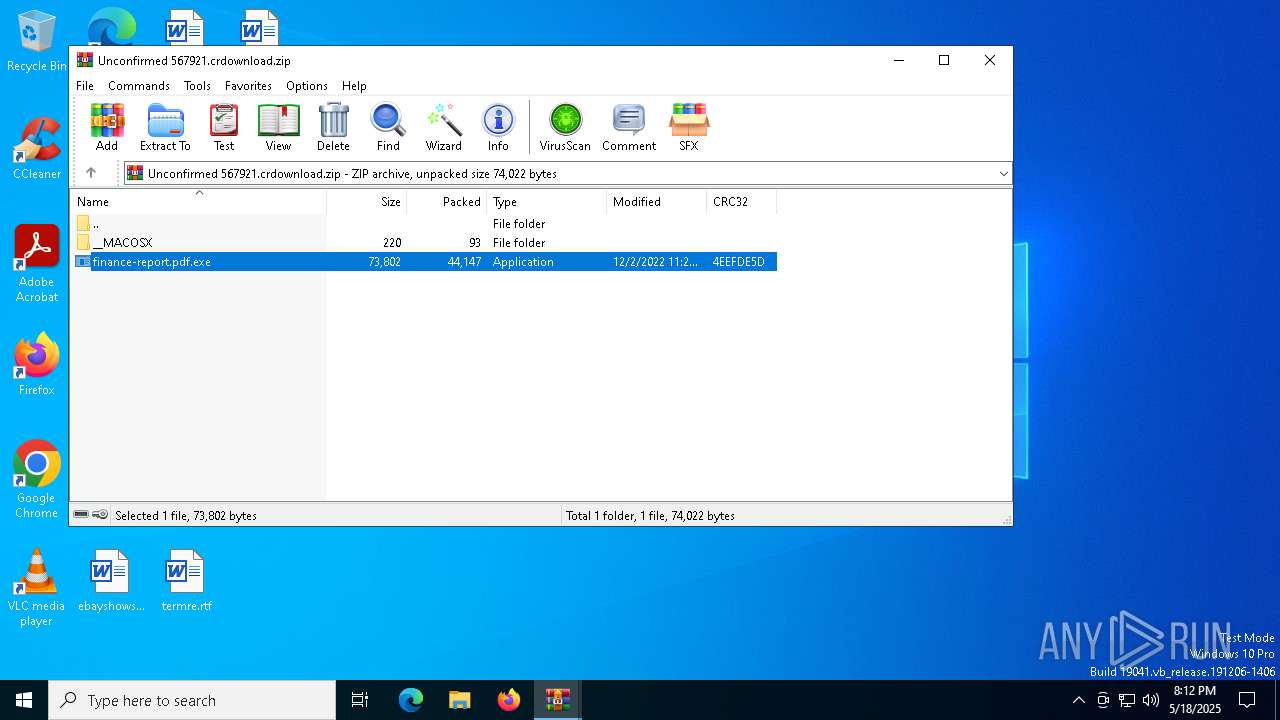
| File name: | Unconfirmed 567921.crdownload |
| Full analysis: | https://app.any.run/tasks/33e58d0b-88e4-4813-a844-9a011b2546c6 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 20:11:39 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A9795881D9B006E34EBCAB3AF6039430 |
| SHA1: | EAB993CB8553BCF03BC1368A186E2F7AC85A3152 |
| SHA256: | D3A1E358B890A53F8881A5A30389B9F17830FD2BD91B3F428E756A8B14FD8B17 |
| SSDEEP: | 768:3mTIhVA+ADy83peIUMBPytTmym6t60vqxQzosbCD1a18iJ5zUUsqS67vO3HKzrre:WTIhVA+Ky4Cx/t6USQU8CDc1P5iqS67M |
MALICIOUS
METASPLOIT has been detected (YARA)
- finance-report.pdf.exe (PID: 7860)
- finance-report.pdf.exe (PID: 7812)
SUSPICIOUS
Connects to unusual port
- finance-report.pdf.exe (PID: 7860)
- finance-report.pdf.exe (PID: 7812)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7468)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7468)
Checks supported languages
- finance-report.pdf.exe (PID: 7812)
- finance-report.pdf.exe (PID: 7860)
The sample compiled with english language support
- WinRAR.exe (PID: 7468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:12:02 18:20:14 |
| ZipCRC: | 0x4eefde5d |
| ZipCompressedSize: | 44147 |
| ZipUncompressedSize: | 73802 |
| ZipFileName: | finance-report.pdf.exe |
Total processes
131
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7468 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Unconfirmed 567921.crdownload.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7812 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.42961\finance-report.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.42961\finance-report.pdf.exe | WinRAR.exe | ||||||||||||
User: admin Company: Apache Software Foundation Integrity Level: MEDIUM Description: ApacheBench command line utility Version: 2.2.14 Modules
| |||||||||||||||
| 7860 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.43365\finance-report.pdf.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.43365\finance-report.pdf.exe | WinRAR.exe | ||||||||||||
User: admin Company: Apache Software Foundation Integrity Level: MEDIUM Description: ApacheBench command line utility Version: 2.2.14 Modules
| |||||||||||||||
Total events
2 270
Read events
2 262
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Unconfirmed 567921.crdownload.zip | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7468) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
3
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.42961\__MACOSX\._finance-report.pdf.exe | binary | |
MD5:4BCA2777F46100E11969E83EEEDC8885 | SHA256:7436ABB12CB3F3A9E1A4E1584D705A2AD3D5176216E6BFDD04CCA2866B585BE9 | |||
| 7468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.43365\finance-report.pdf.exe | executable | |
MD5:8A6F0157BCC6CB3CF6B2725BD7F097F9 | SHA256:81AEDC01DF5AEB5DC936E3D5D887822760FA4B395195EC5D521D6BB3CE2DD93A | |||
| 7468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.42961\finance-report.pdf.exe | executable | |
MD5:8A6F0157BCC6CB3CF6B2725BD7F097F9 | SHA256:81AEDC01DF5AEB5DC936E3D5D887822760FA4B395195EC5D521D6BB3CE2DD93A | |||
| 7468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa7468.43907\finance-report.pdf.exe | executable | |
MD5:8A6F0157BCC6CB3CF6B2725BD7F097F9 | SHA256:81AEDC01DF5AEB5DC936E3D5D887822760FA4B395195EC5D521D6BB3CE2DD93A | |||
| 7468 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7468.43365\__MACOSX\._finance-report.pdf.exe | binary | |
MD5:4BCA2777F46100E11969E83EEEDC8885 | SHA256:7436ABB12CB3F3A9E1A4E1584D705A2AD3D5176216E6BFDD04CCA2866B585BE9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
24
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8020 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8020 | SIHClient.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.161:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.161:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |