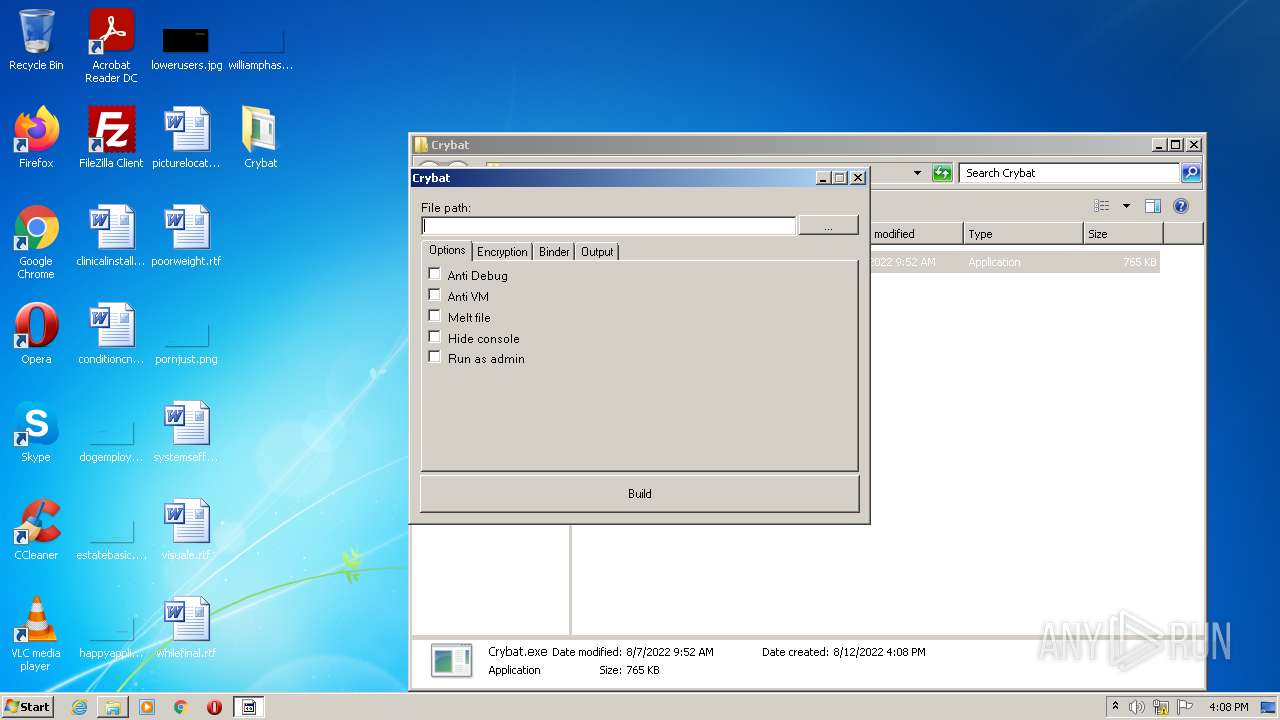
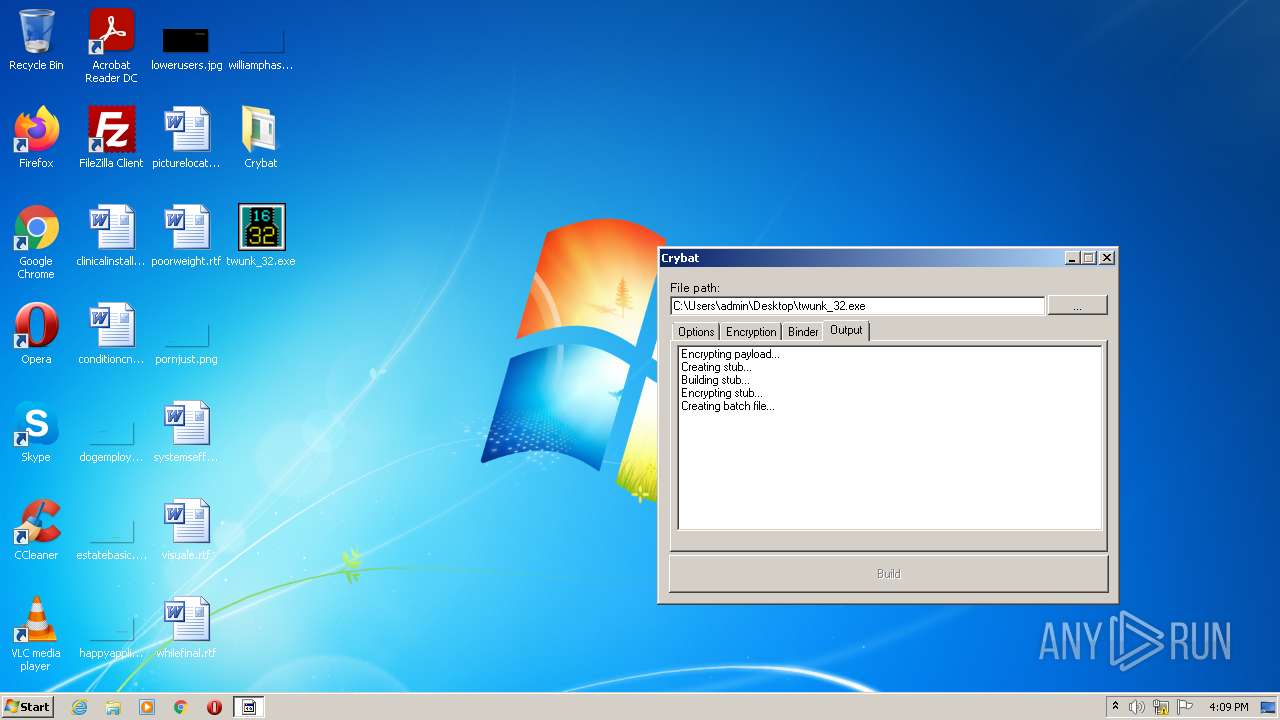
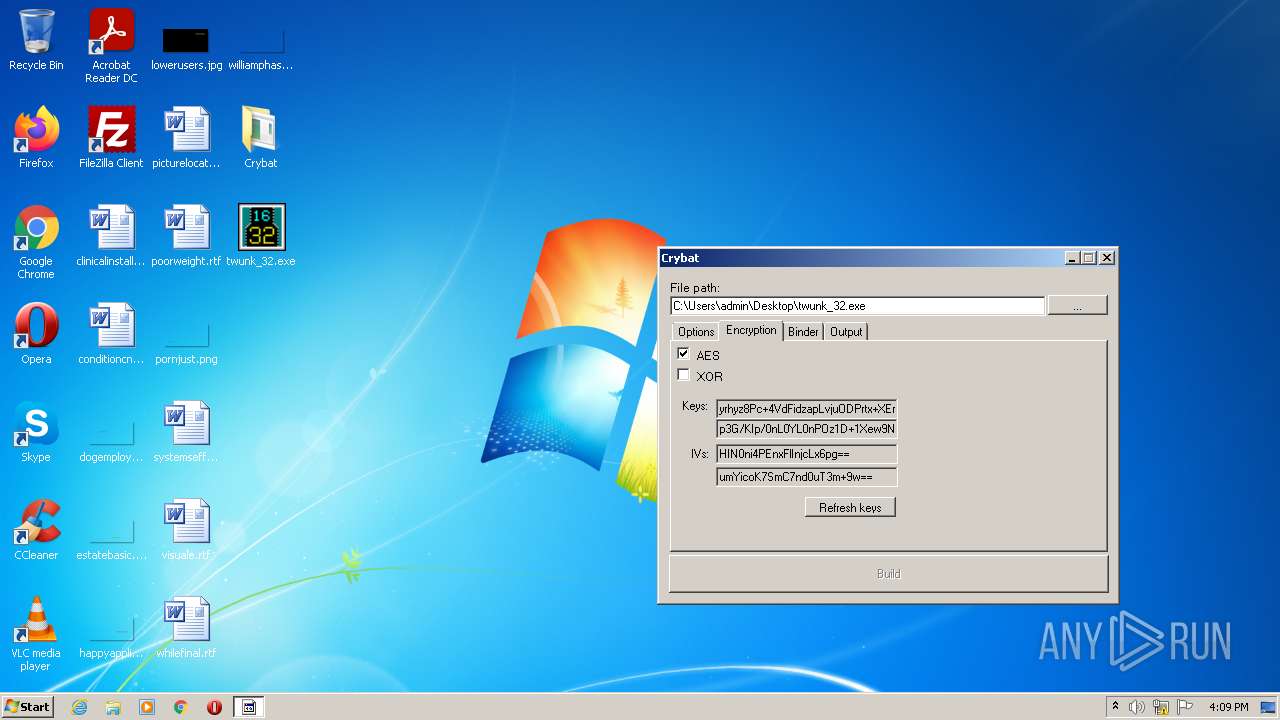
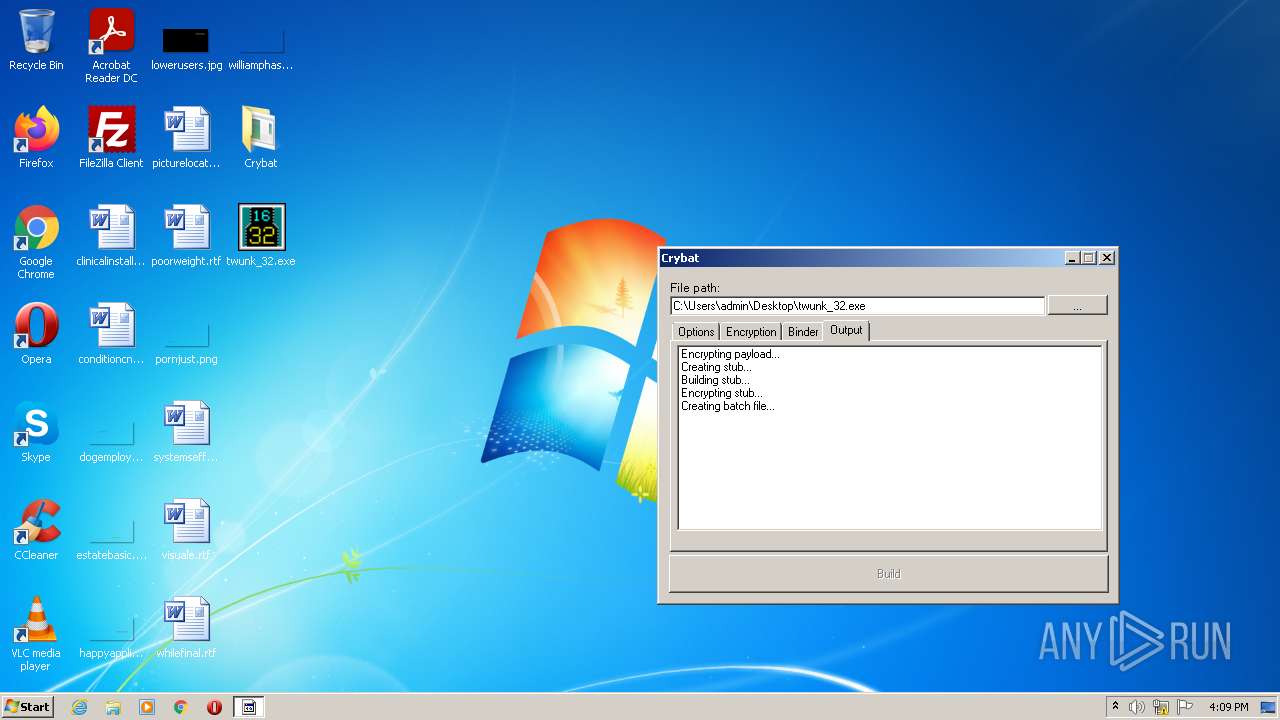
| File name: | Crybat.zip |
| Full analysis: | https://app.any.run/tasks/e032408b-3437-49f0-8e56-c30dd1f9642b |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 15:08:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F84393EF80A184696BF1C4172E931FDA |
| SHA1: | 678492E07E1B9E06F106FB289E6A0B232709B2E5 |
| SHA256: | D335DEA910391C6A22AB5E1B93908E4D2345DED546A28D4DD3546B0A91D04281 |
| SSDEEP: | 12288:YlCGFDJ908YfklCdBNNbaG6Gx/ufegY9Hqrlr/LZdLn/yGJaw6L9/m/6Wz:YUGMdLNbXxmfewr/L3aGJaw6R/m/6U |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3096)
- csc.exe (PID: 3944)
Application was dropped or rewritten from another process
- Crybat.exe (PID: 2044)
Starts Visual C# compiler
- Crybat.exe (PID: 2044)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 3096)
- Crybat.exe (PID: 2044)
Checks supported languages
- WinRAR.exe (PID: 3096)
- Crybat.exe (PID: 2044)
- csc.exe (PID: 3944)
- cvtres.exe (PID: 712)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3096)
- csc.exe (PID: 3944)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3096)
- csc.exe (PID: 3944)
Reads Environment values
- Crybat.exe (PID: 2044)
Reads default file associations for system extensions
- Crybat.exe (PID: 2044)
INFO
Manual execution by user
- Crybat.exe (PID: 2044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Crybat/Crybat.exe |
|---|---|
| ZipUncompressedSize: | 783360 |
| ZipCompressedSize: | 737053 |
| ZipCRC: | 0xad535c20 |
| ZipModifyDate: | 2022:08:07 09:52:27 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESC33.tmp" "c:\Users\admin\AppData\Local\Temp\CSCDCC25467BB6945019CABC0F2E9BE1375.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.51209.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 2044 | "C:\Users\admin\Desktop\Crybat\Crybat.exe" | C:\Users\admin\Desktop\Crybat\Crybat.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Crybat Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3096 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Crybat.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3944 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\thwdkhhp.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | Crybat.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
3 446
Read events
3 350
Write events
95
Delete events
1
Modification events
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Crybat.zip | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3096) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
2
Suspicious files
2
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3096 | WinRAR.exe | C:\Users\admin\Desktop\Crybat\Crybat.exe | executable | |
MD5:— | SHA256:— | |||
| 2044 | Crybat.exe | C:\Users\admin\Desktop\Crybat\runpe.dll | binary | |
MD5:— | SHA256:— | |||
| 3944 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCDCC25467BB6945019CABC0F2E9BE1375.TMP | res | |
MD5:— | SHA256:— | |||
| 2044 | Crybat.exe | C:\Users\admin\Desktop\Crybat\payload.exe | binary | |
MD5:— | SHA256:— | |||
| 2044 | Crybat.exe | C:\Users\admin\AppData\Local\Temp\thwdkhhp.0.cs | text | |
MD5:— | SHA256:— | |||
| 2044 | Crybat.exe | C:\Users\admin\AppData\Local\Temp\thwdkhhp.cmdline | text | |
MD5:— | SHA256:— | |||
| 712 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESC33.tmp | o | |
MD5:— | SHA256:— | |||
| 3944 | csc.exe | C:\Users\admin\AppData\Local\Temp\tmpB39.tmp | executable | |
MD5:— | SHA256:— | |||
| 3944 | csc.exe | C:\Users\admin\AppData\Local\Temp\thwdkhhp.out | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2044 | Crybat.exe | 185.199.110.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | malicious |
2044 | Crybat.exe | 185.199.109.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | malicious |
2044 | Crybat.exe | 185.199.111.133:443 | raw.githubusercontent.com | GitHub, Inc. | NL | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
dns.msftncsi.com |
| shared |