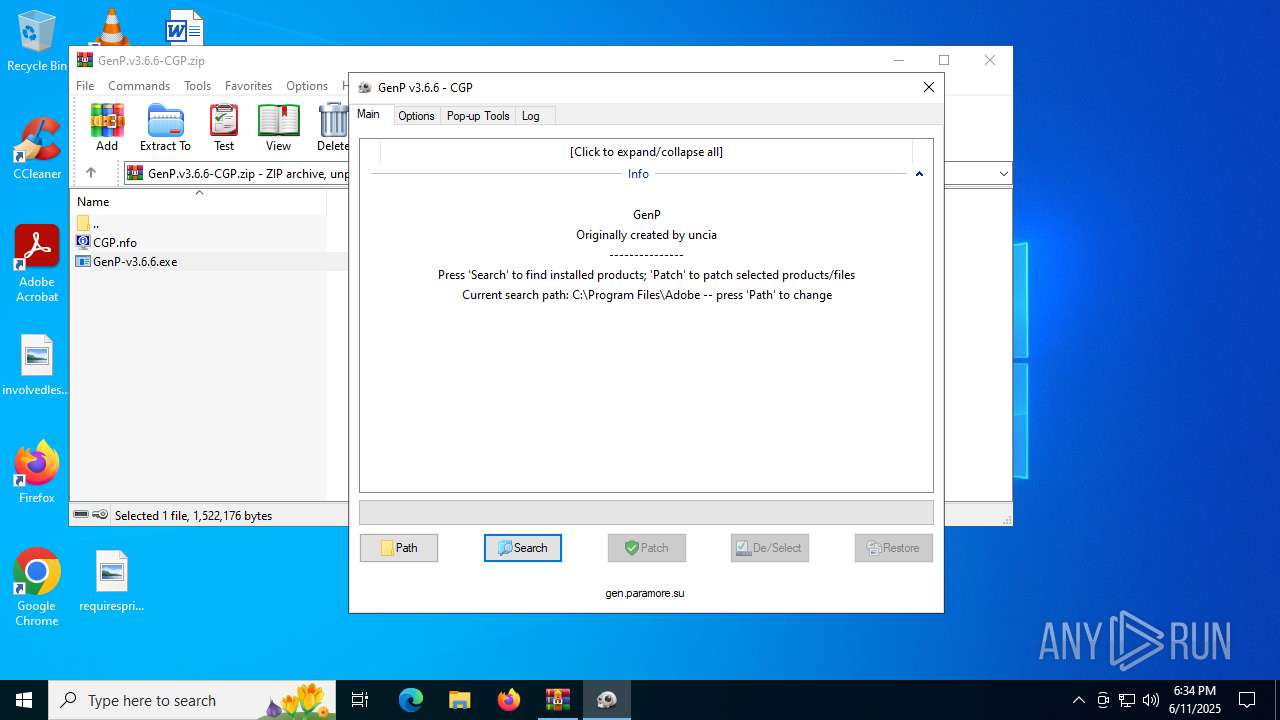
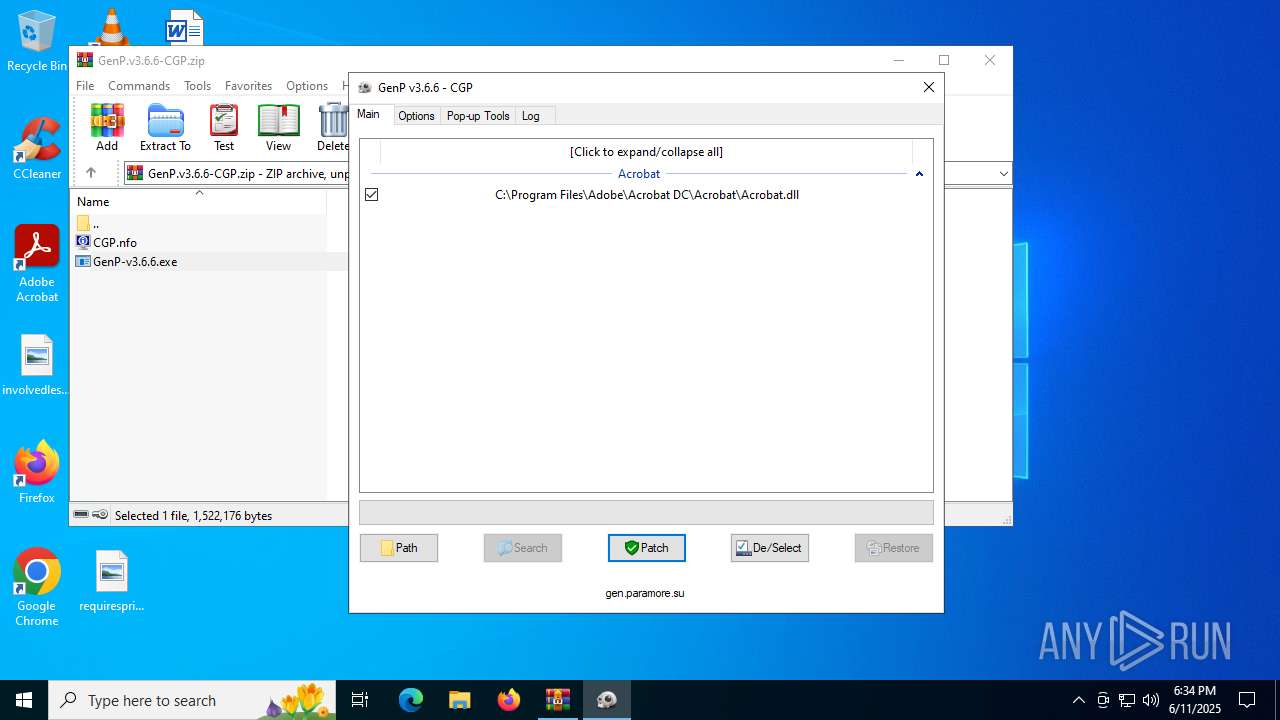
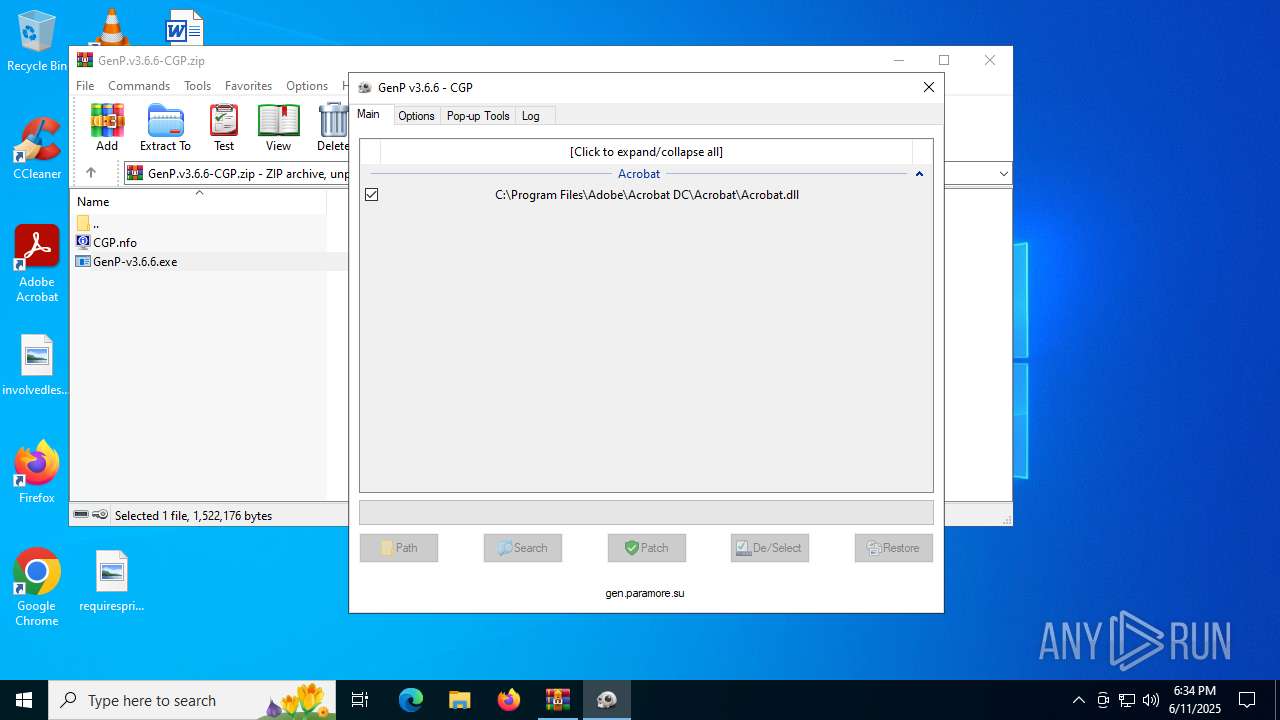
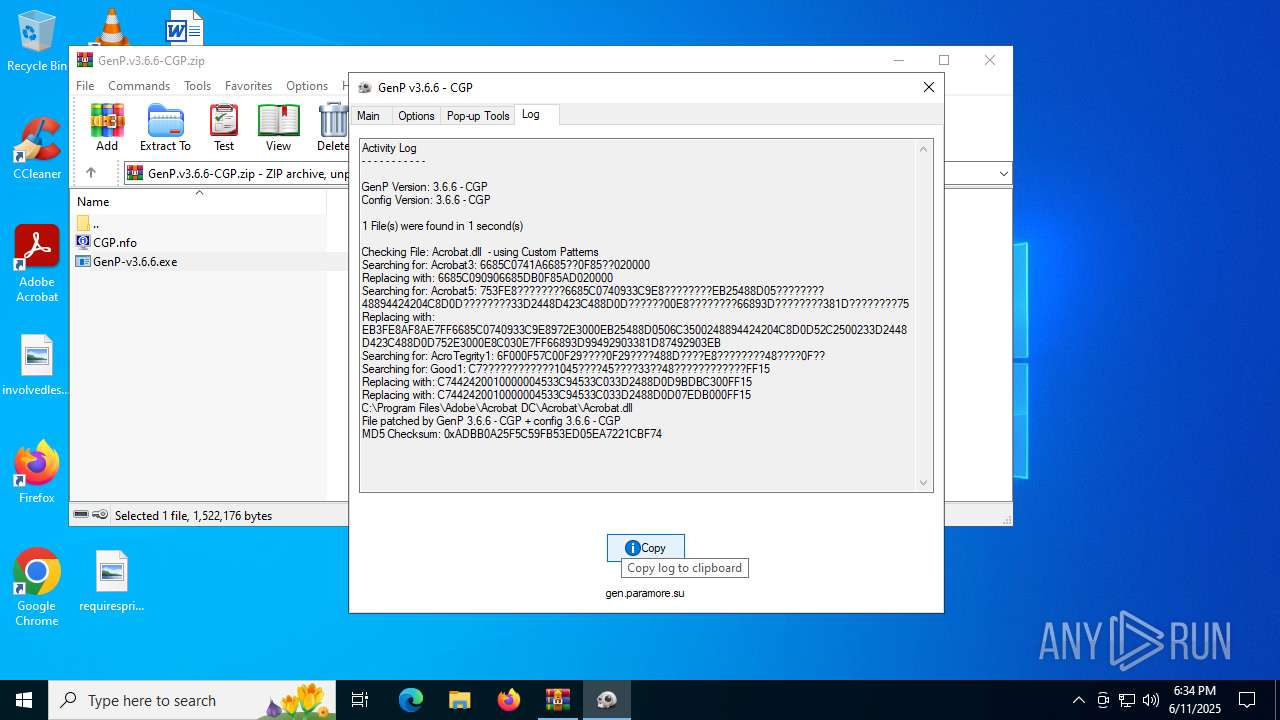
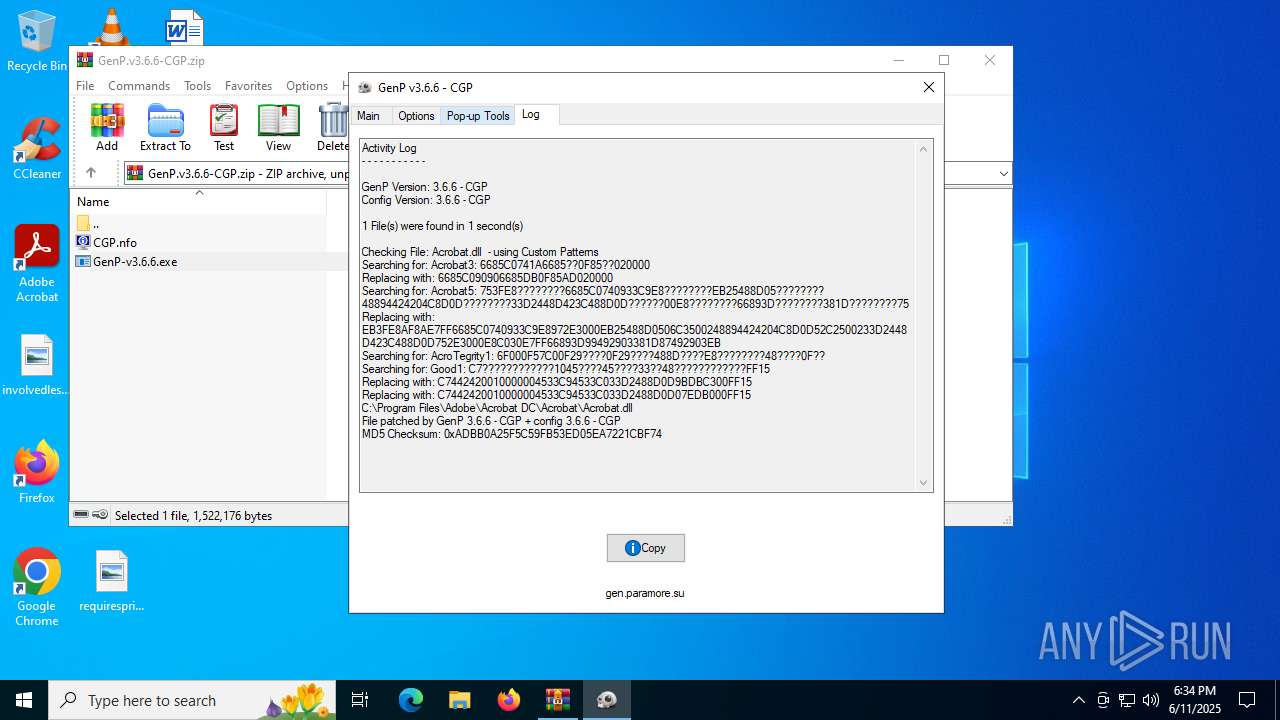
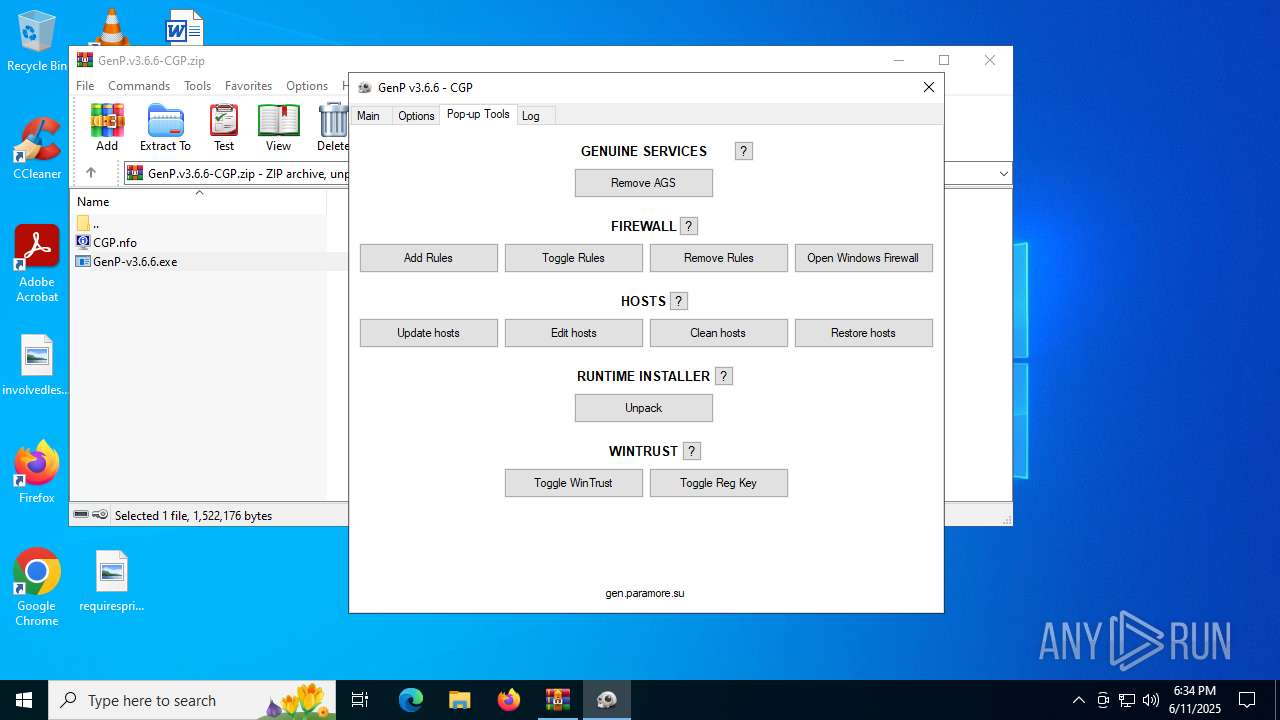
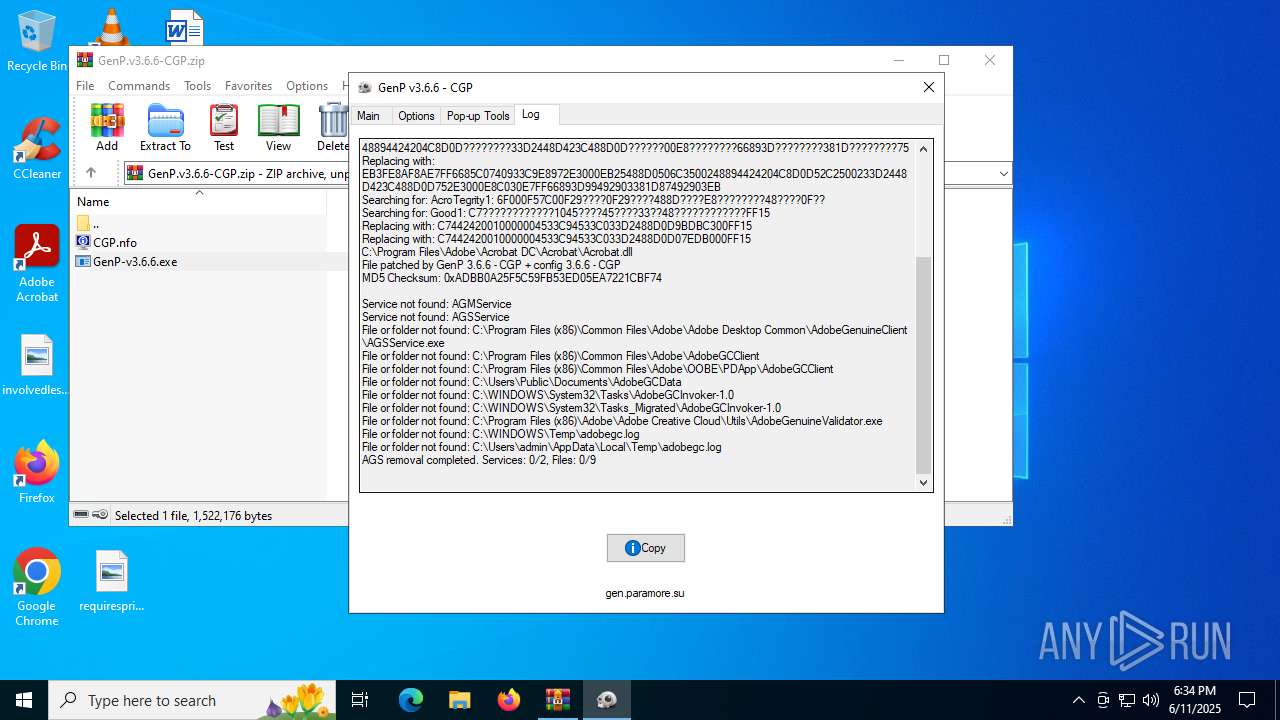
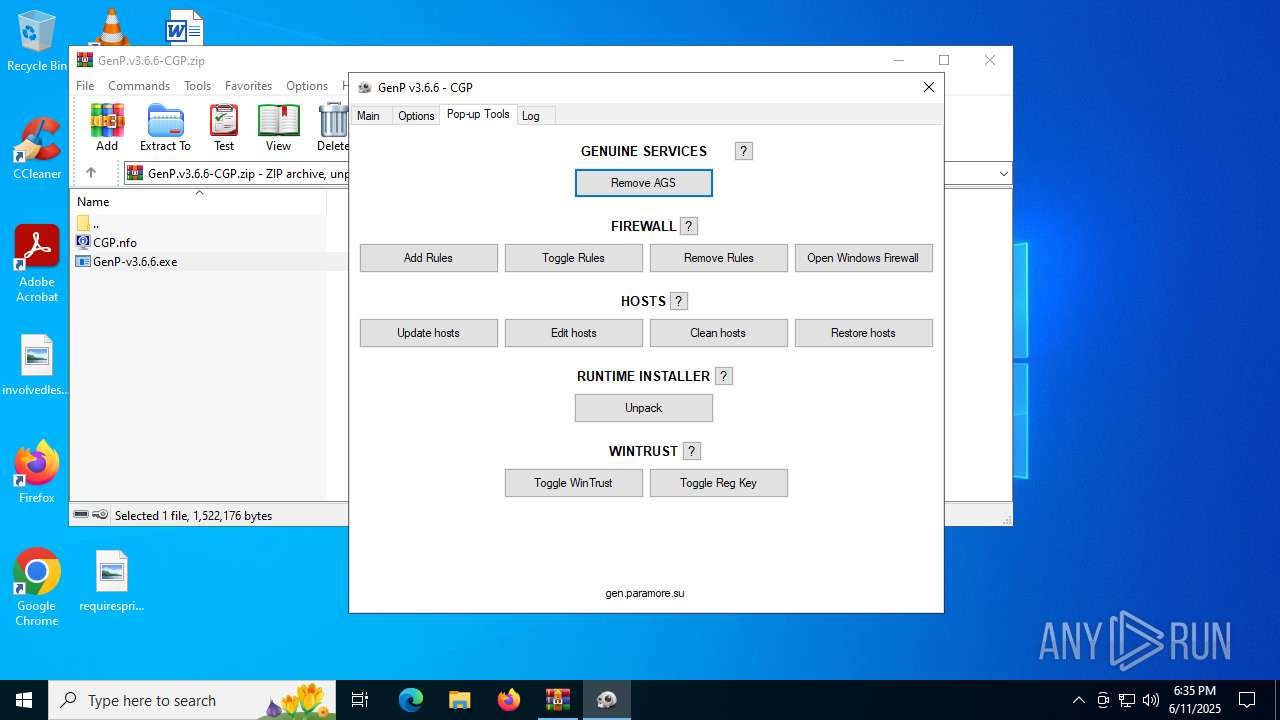
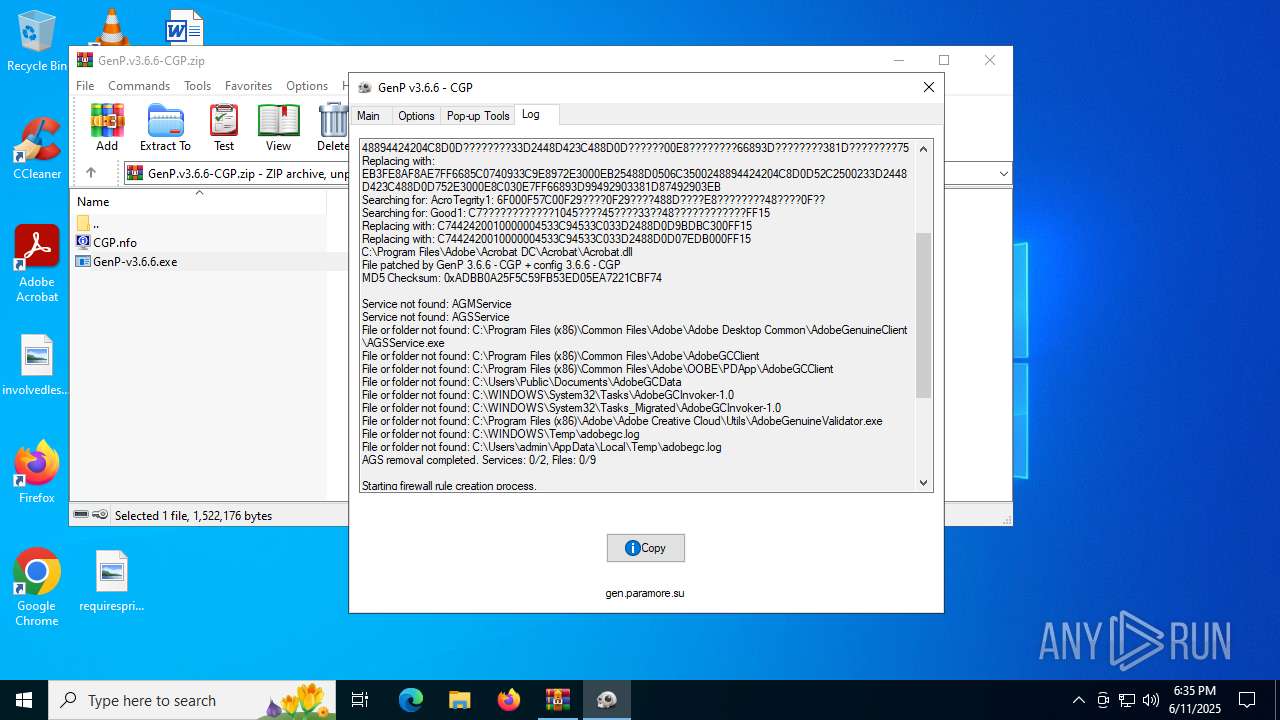
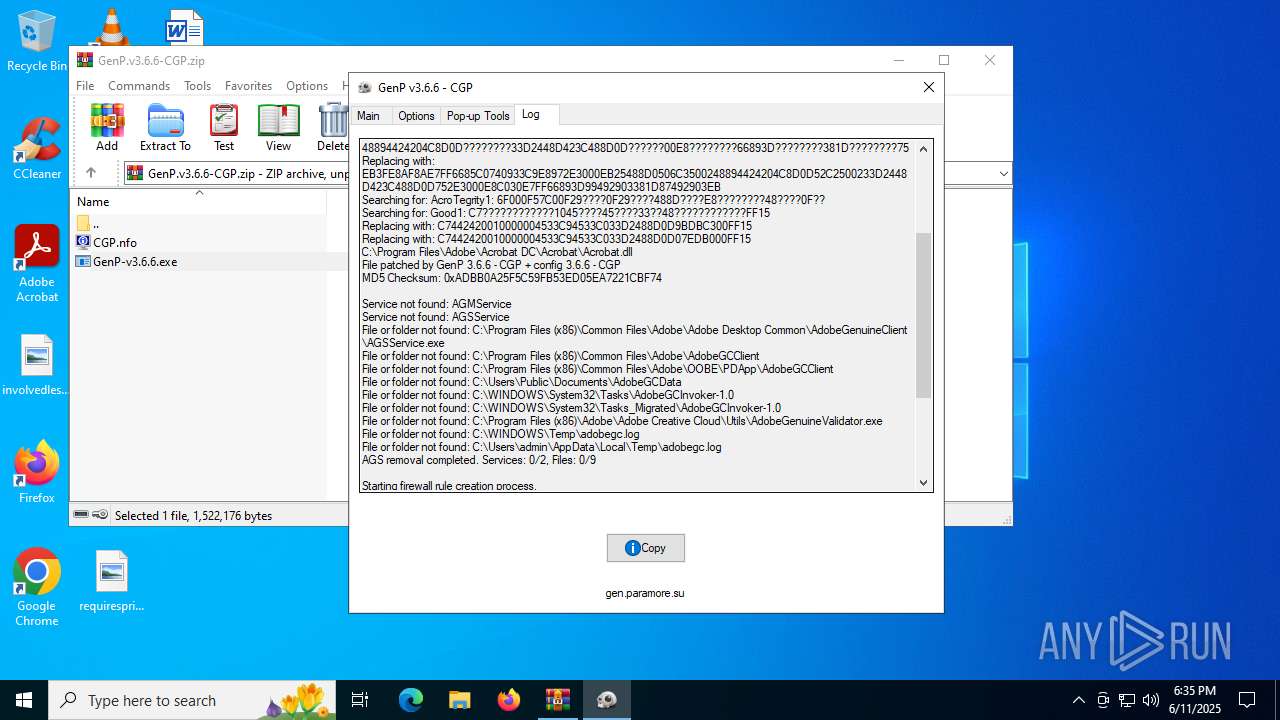
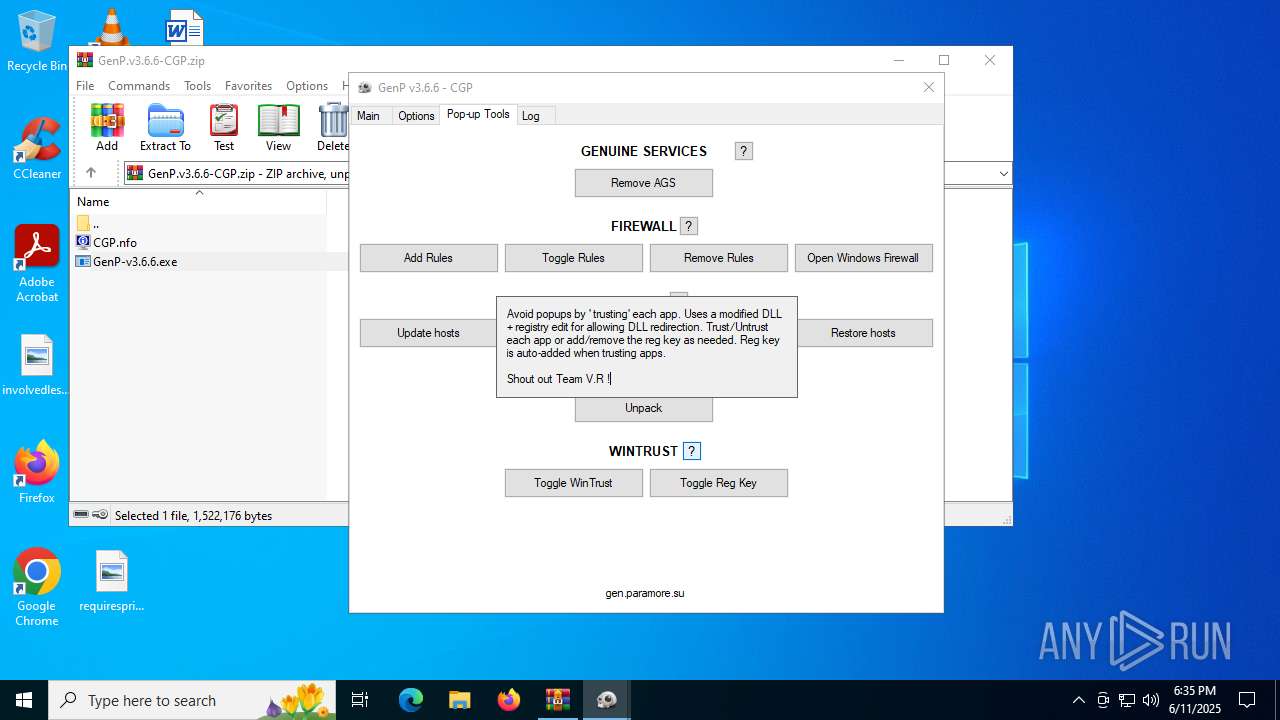
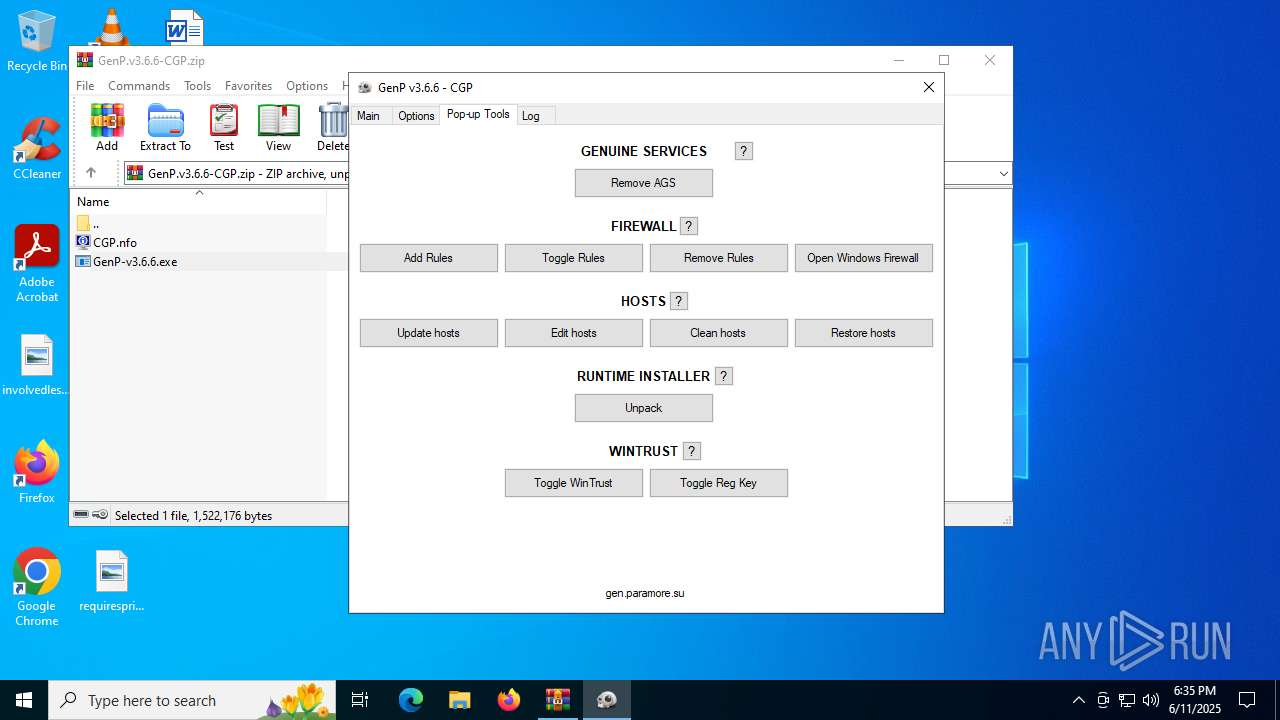
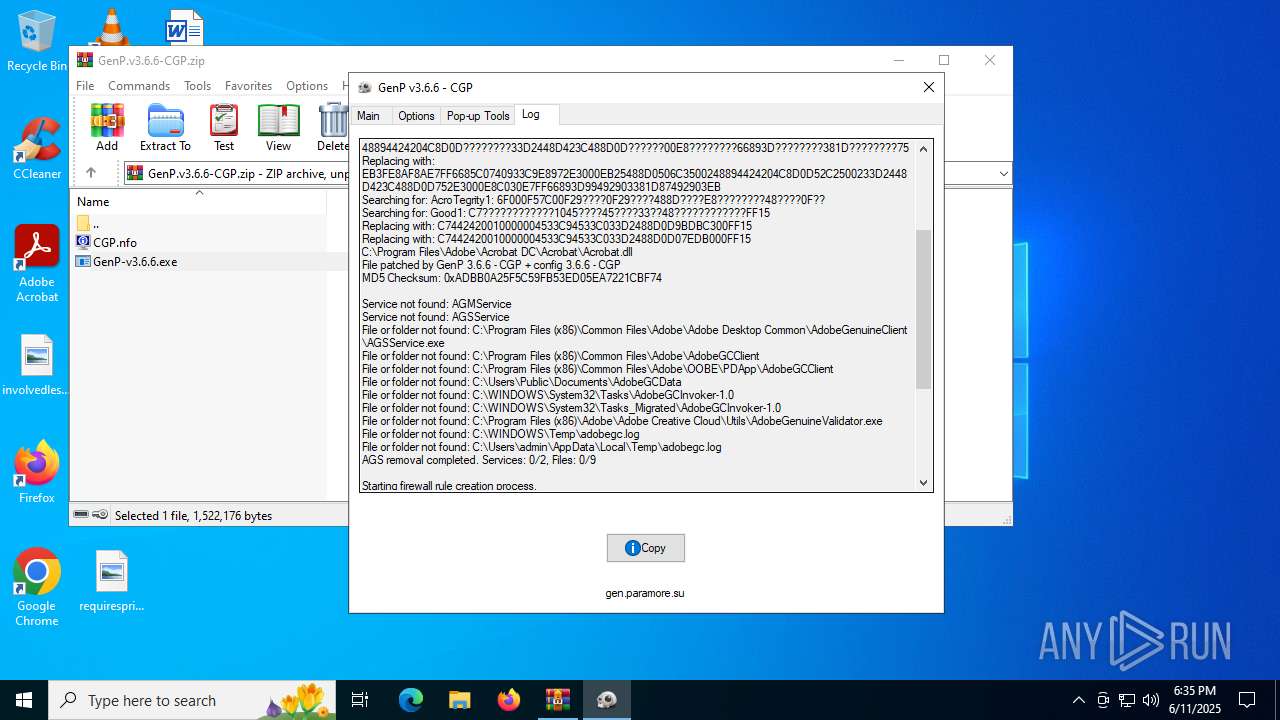
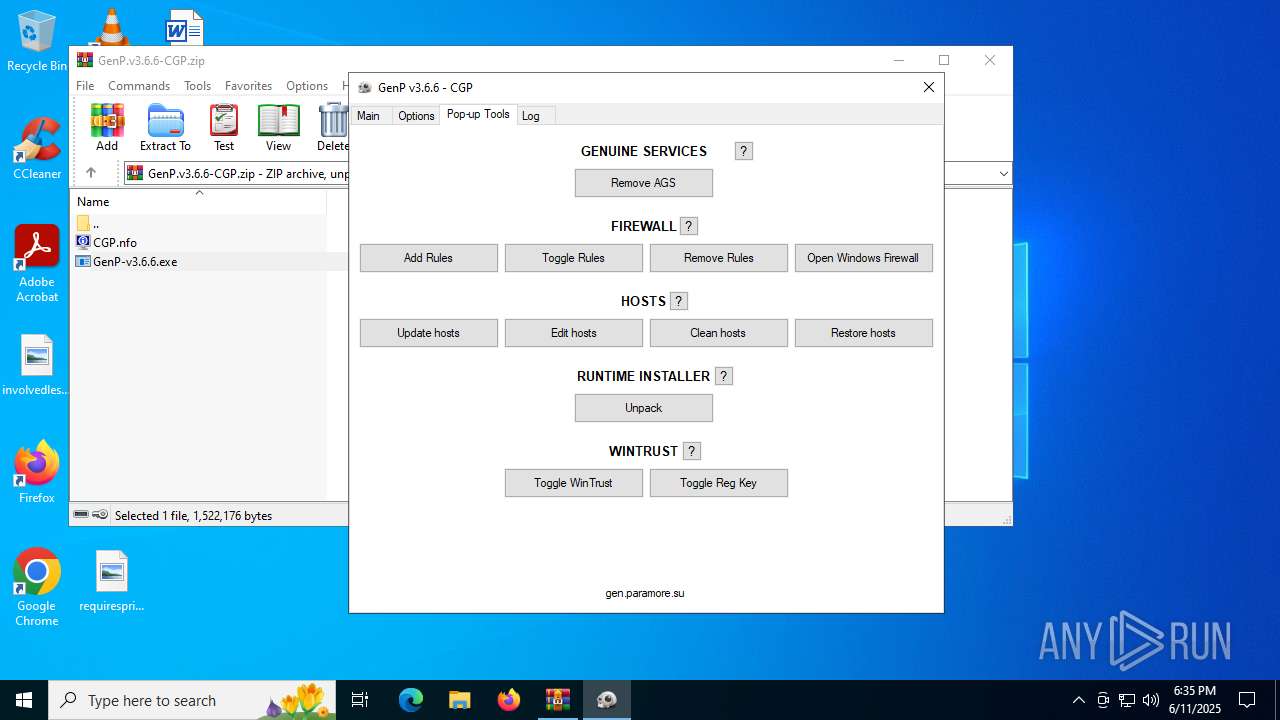
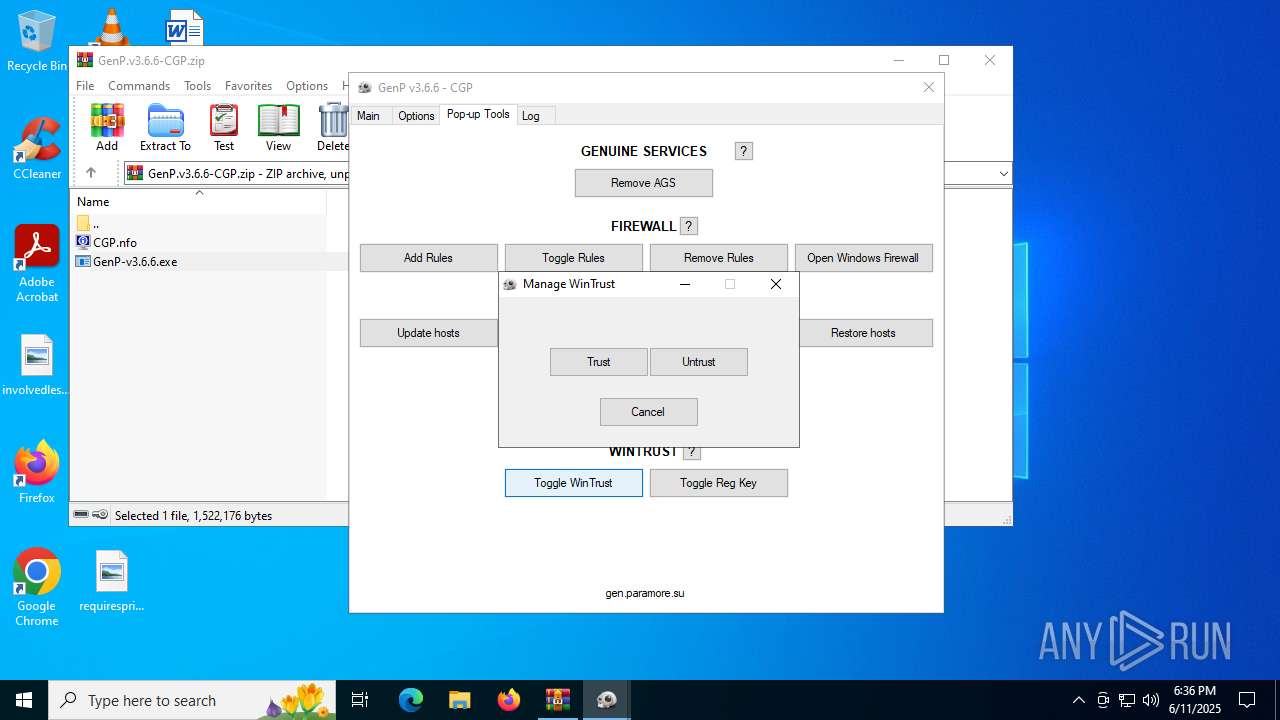
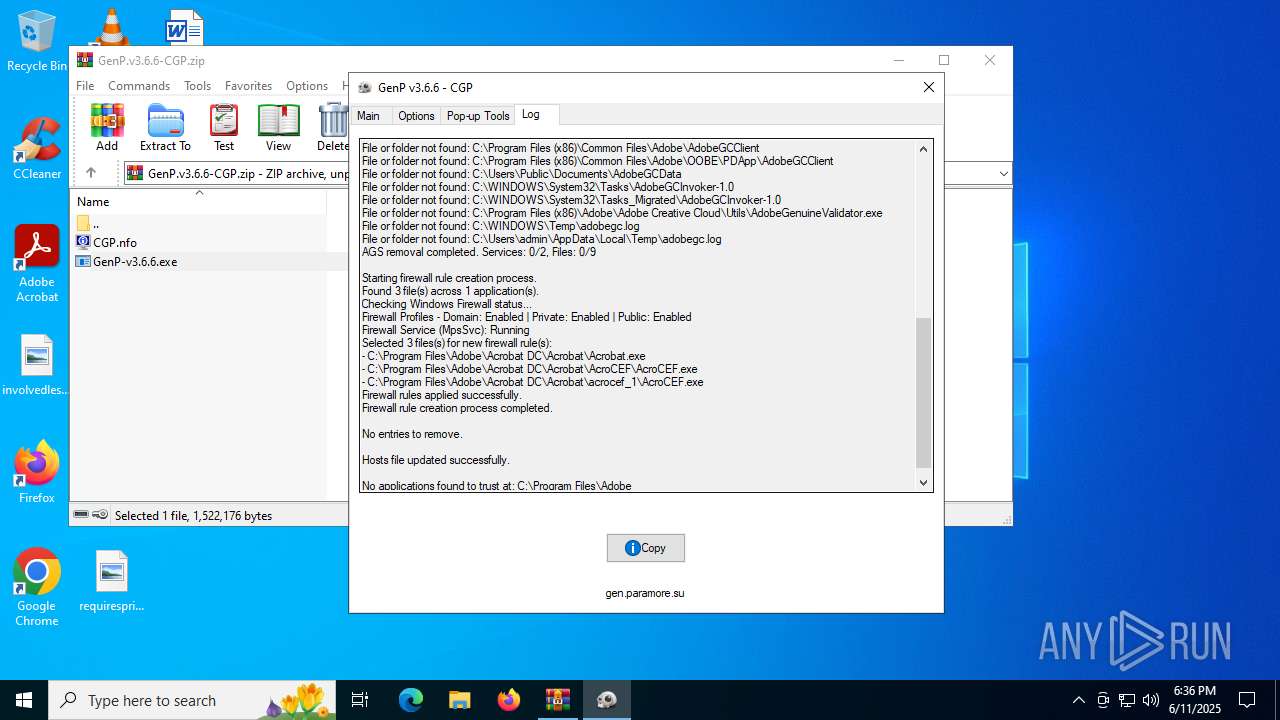
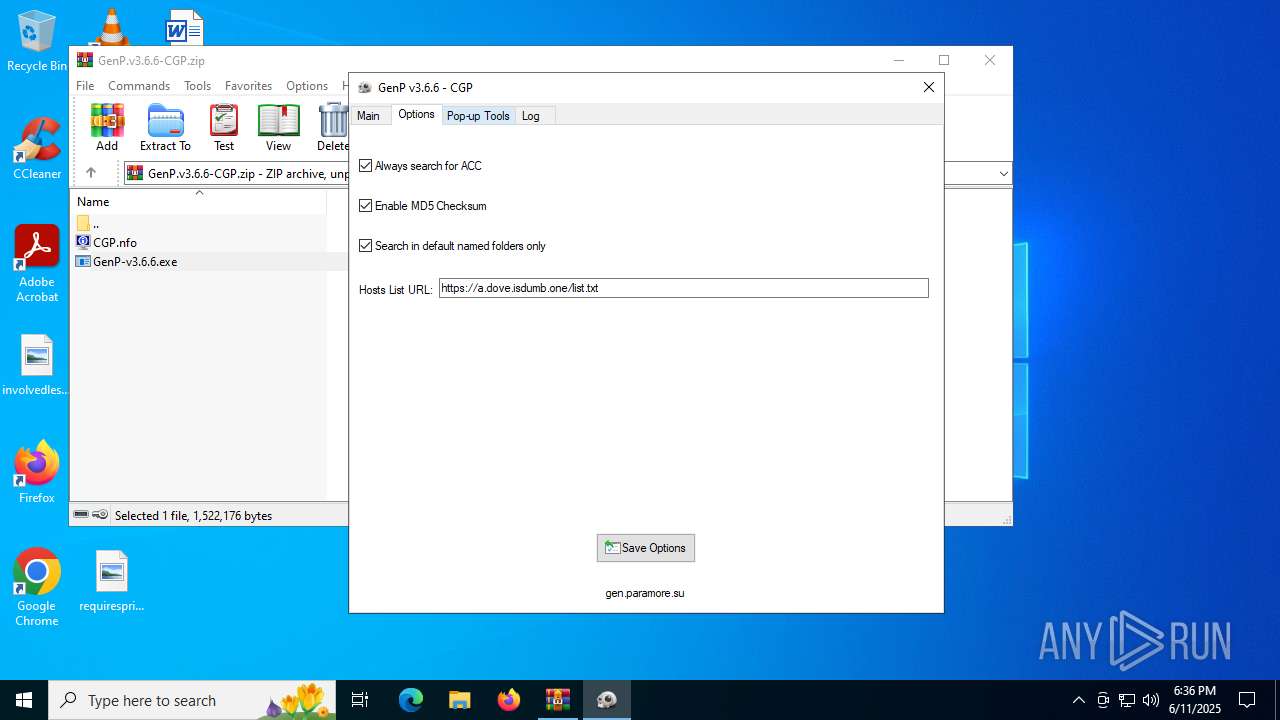
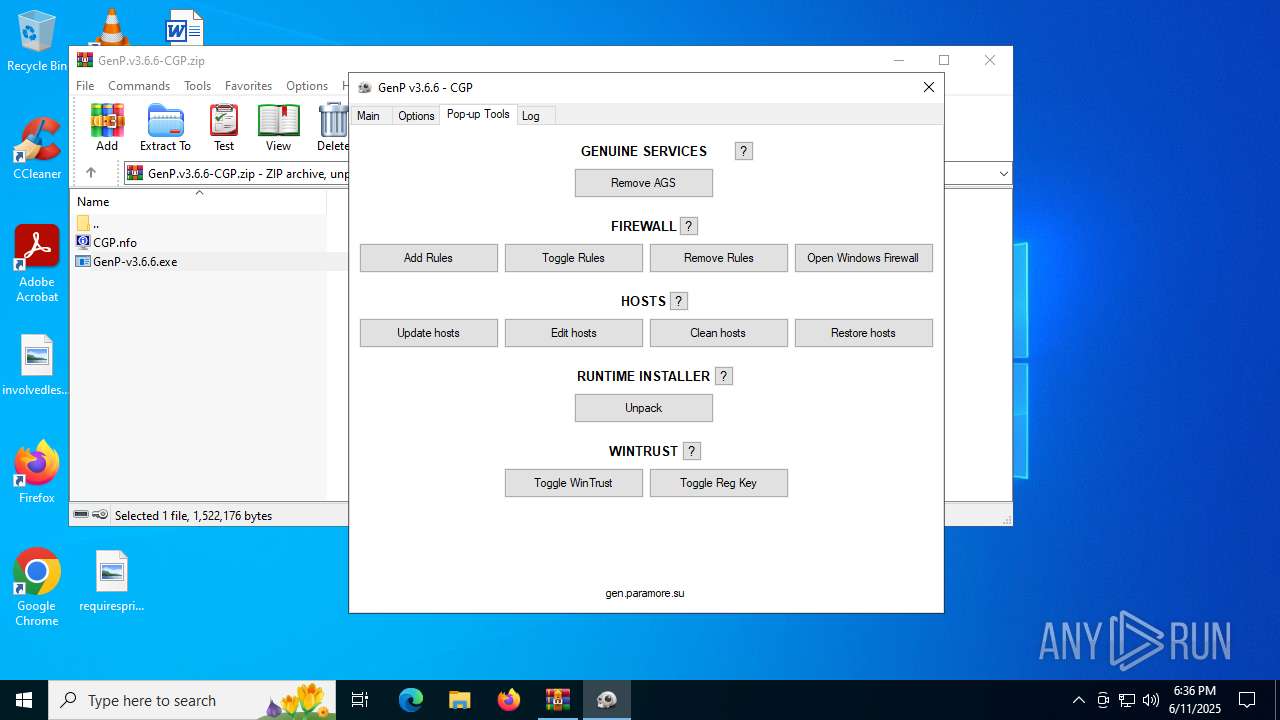
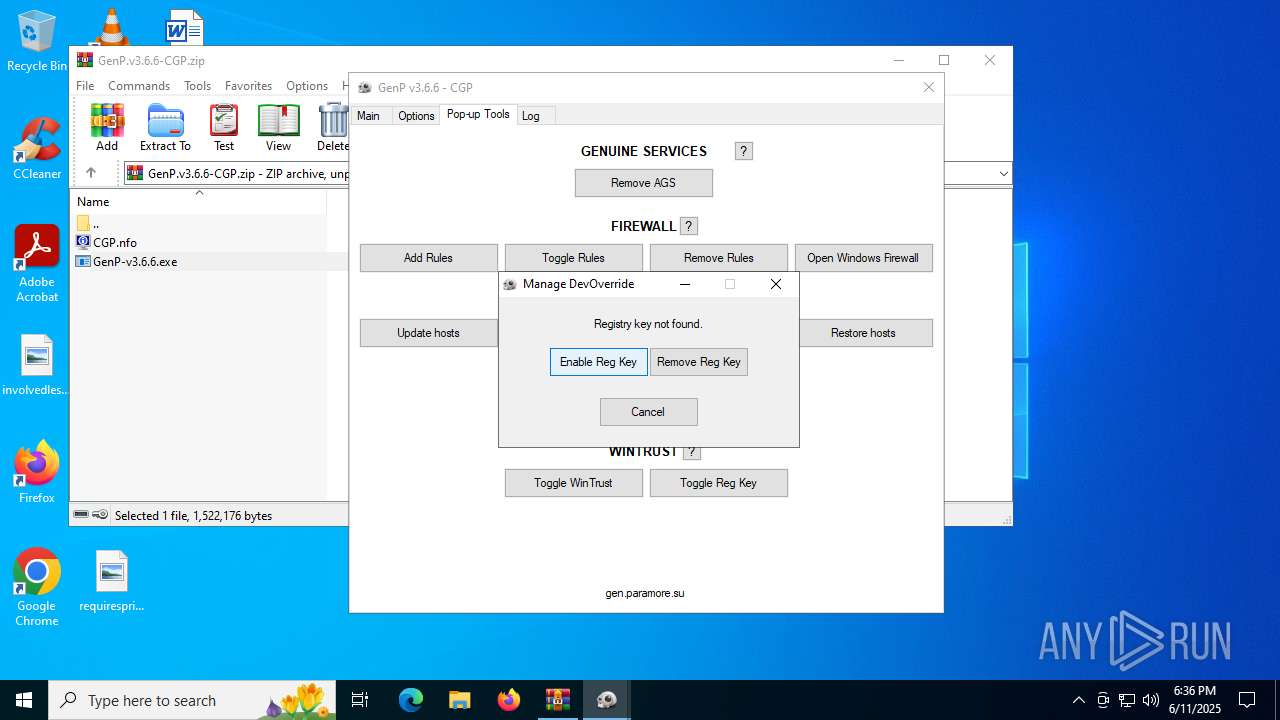
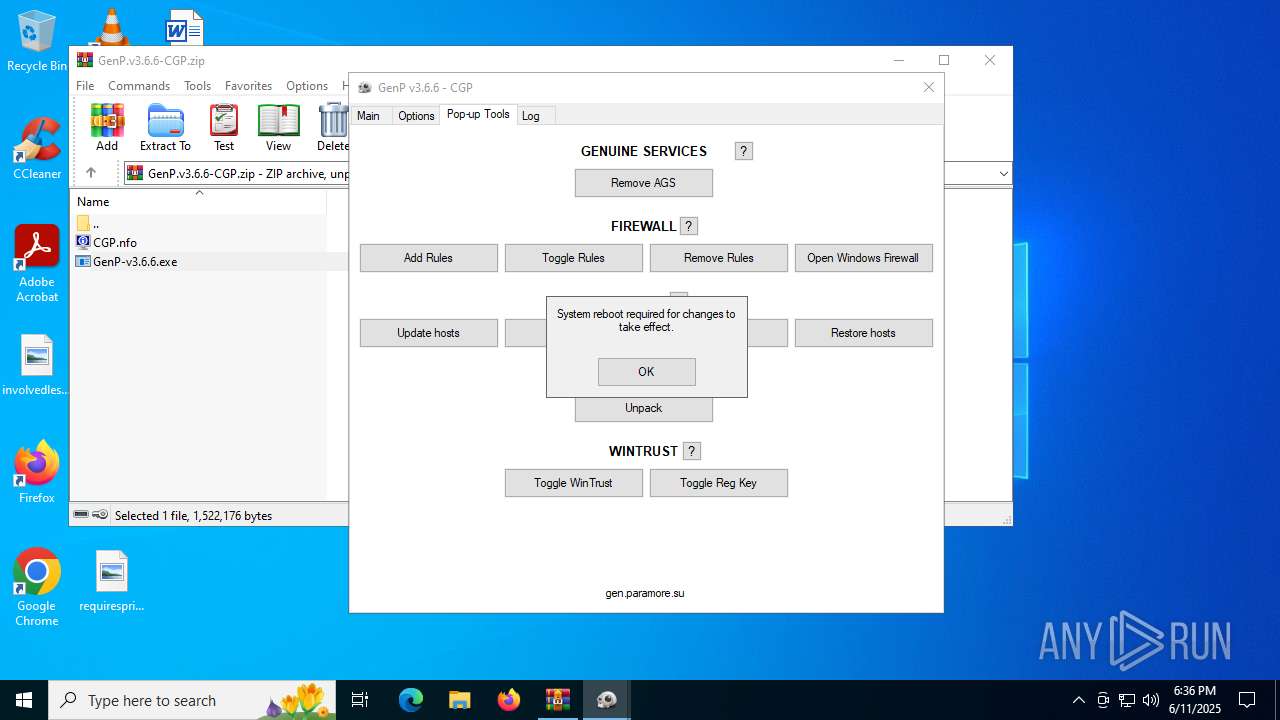
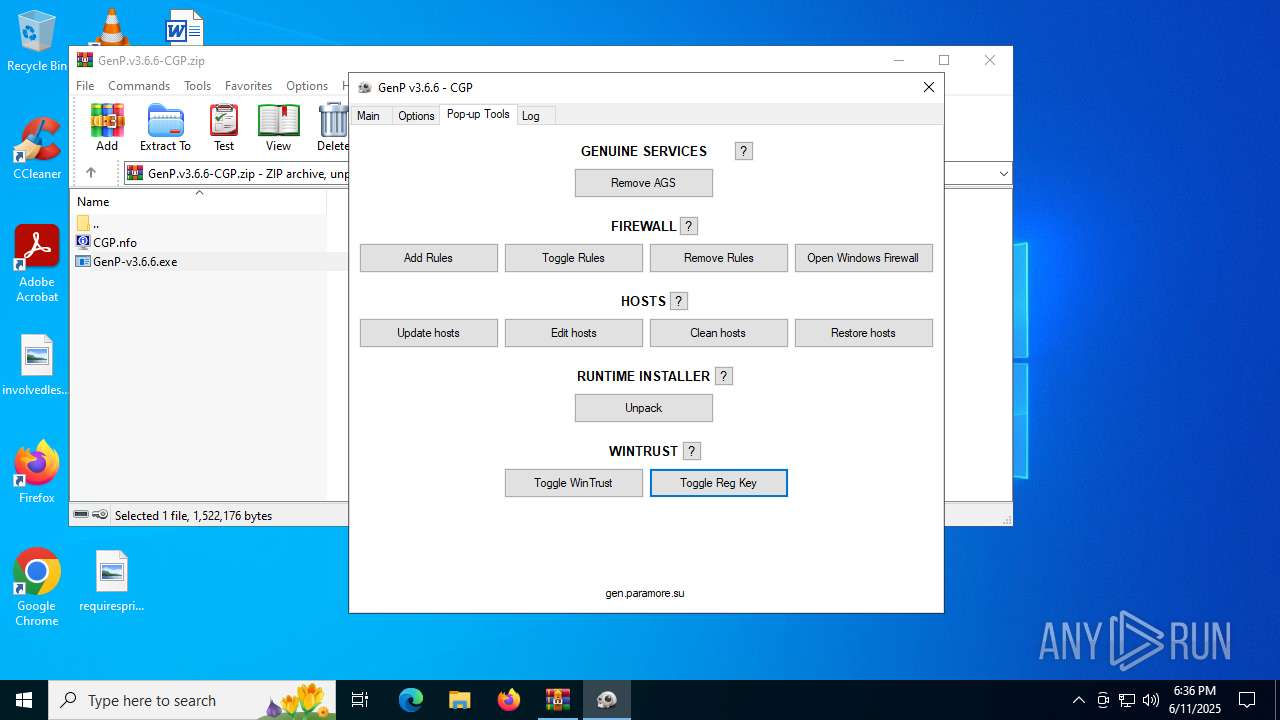
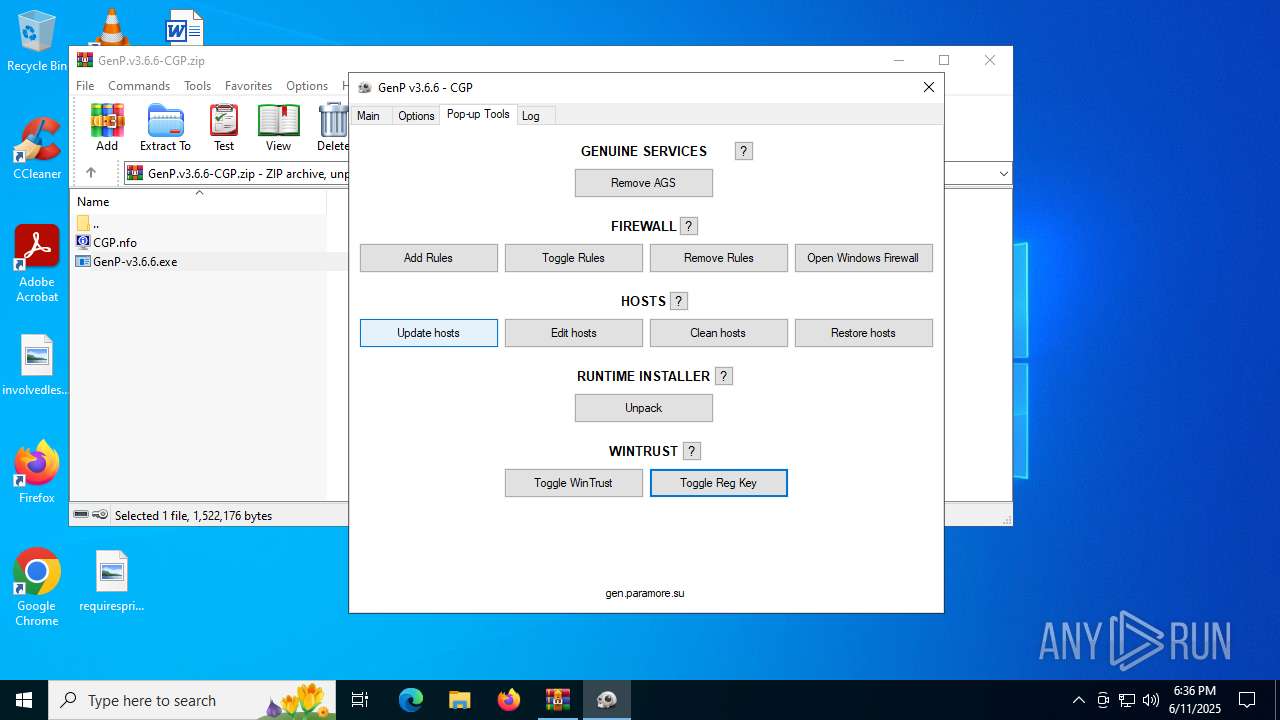
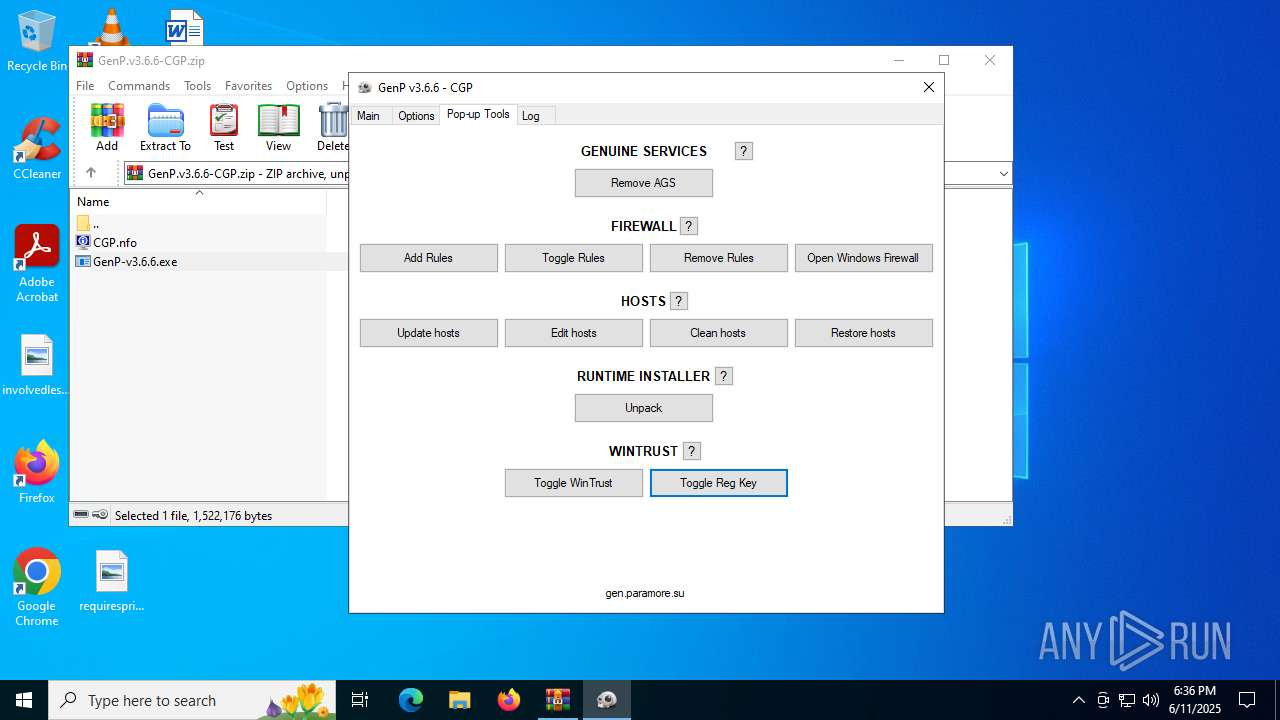
| File name: | GenP.v3.6.6-CGP.zip |
| Full analysis: | https://app.any.run/tasks/4b8cf481-9439-4035-b504-60eb7e03966e |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2025, 18:34:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C603FF4D504ACF9D87EE82769D32C5F2 |
| SHA1: | 9235C1B0E5DF44E613E651B8F79F232EDF14FD65 |
| SHA256: | D327A3BAE0195E89F529F4923D210D2203887204C8AE1CDF80E7DBEB316755E3 |
| SSDEEP: | 49152:vHqZ6FxfJVkvB+YFRsOhpLFoD4dLUEhoobkR91a/KlNKYOJCeOm2UV0wv/q0KdR8:vpVK+4jpLCD8UETbAjUOKYYCeO5Kv/q4 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 504)
SUSPICIOUS
Windows service management via SC.EXE
- sc.exe (PID: 6016)
- sc.exe (PID: 1036)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 724)
- cmd.exe (PID: 4984)
- cmd.exe (PID: 620)
- cmd.exe (PID: 3836)
- cmd.exe (PID: 6756)
- GenP-v3.6.6.exe (PID: 3476)
- cmd.exe (PID: 6516)
Starts SC.EXE for service management
- GenP-v3.6.6.exe (PID: 3476)
Starts CMD.EXE for commands execution
- GenP-v3.6.6.exe (PID: 3476)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 4864)
INFO
Reads mouse settings
- GenP-v3.6.6.exe (PID: 3476)
The sample compiled with english language support
- WinRAR.exe (PID: 504)
Manual execution by a user
- GenP-v3.6.6.exe (PID: 2148)
- GenP-v3.6.6.exe (PID: 3476)
Checks supported languages
- GenP-v3.6.6.exe (PID: 3476)
Create files in a temporary directory
- GenP-v3.6.6.exe (PID: 3476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 504)
Reads the computer name
- GenP-v3.6.6.exe (PID: 3476)
Creates files in the program directory
- GenP-v3.6.6.exe (PID: 3476)
Reads the machine GUID from the registry
- GenP-v3.6.6.exe (PID: 3476)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5908)
- powershell.exe (PID: 5896)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:05 06:06:40 |
| ZipCRC: | 0x1a5ff461 |
| ZipCompressedSize: | 3179 |
| ZipUncompressedSize: | 34494 |
| ZipFileName: | CGP.nfo |
Total processes
166
Monitored processes
31
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 504 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\GenP.v3.6.6-CGP.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 620 | C:\WINDOWS\system32\cmd.exe /c powershell.exe -Command "Get-Service MpsSvc | Select-Object -Property Status,DisplayName | Format-List" | C:\Windows\System32\cmd.exe | — | GenP-v3.6.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 724 | C:\WINDOWS\system32\cmd.exe /c powershell.exe -Command "Get-CimInstance -ClassName FirewallProduct -Namespace 'root\SecurityCenter2' | Where-Object { $_.ProductName -notlike '*Windows*' } | Select-Object -Property ProductName" | C:\Windows\System32\cmd.exe | — | GenP-v3.6.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | sc query AGSService | C:\Windows\System32\sc.exe | — | GenP-v3.6.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1060 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1472 | powershell.exe -Command "Get-CimInstance -ClassName FirewallProduct -Namespace 'root\SecurityCenter2' | Where-Object { $_.ProductName -notlike '*Windows*' } | Select-Object -Property ProductName" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1496 | powershell.exe -Command "Get-Service MpsSvc | Select-Object -Property Status,DisplayName | Format-List" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\Desktop\GenP-v3.6.6.exe" | C:\Users\admin\Desktop\GenP-v3.6.6.exe | — | explorer.exe | |||||||||||
User: admin Company: GenP Integrity Level: MEDIUM Description: GenP Exit code: 3221226540 Version: 3.6.6.0 Modules
| |||||||||||||||
| 2468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3476 | "C:\Users\admin\Desktop\GenP-v3.6.6.exe" | C:\Users\admin\Desktop\GenP-v3.6.6.exe | explorer.exe | ||||||||||||
User: admin Company: GenP Integrity Level: HIGH Description: GenP Version: 3.6.6.0 Modules
| |||||||||||||||
| 3836 | C:\WINDOWS\system32\cmd.exe /c powershell.exe -Command "Get-NetFirewallRule -DisplayName 'Adobe-Block - C:\Program Files\Adobe\Acrobat DC\Acrobat\AcroCEF\AcroCEF.exe' | Measure-Object | Select-Object -ExpandProperty Count" | C:\Windows\System32\cmd.exe | — | GenP-v3.6.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 106
Read events
45 091
Write events
15
Delete events
0
Modification events
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\GenP.v3.6.6-CGP.zip | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | write | Name: | @C:\WINDOWS\system32\msinfo32.exe,-10001 |
Value: System Information File | |||
| (PID) Process: | (504) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
Executable files
1
Suspicious files
4
Text files
20
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3476 | GenP-v3.6.6.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.dll.bak | — | |
MD5:— | SHA256:— | |||
| 3476 | GenP-v3.6.6.exe | C:\Program Files\Adobe\Acrobat DC\Acrobat\Acrobat.dll | — | |
MD5:— | SHA256:— | |||
| 3476 | GenP-v3.6.6.exe | C:\Users\admin\Desktop\config.ini | ini | |
MD5:A7BC5A7ADC2E89426BF18A6F1EC1AE4B | SHA256:35916985B869D72085BDB3D10B146D751631B10E4C61099EF339C3E72E2182F8 | |||
| 5908 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rhvi2aoy.gxb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1472 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_5kv5xllu.3h1.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1472 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_f2fj3pf4.4ic.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1472 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:B3006C4B374F92061ED3B70B5BC453A3 | SHA256:03411650A070768E18C36F45358A6EA26C9F16CA3322B6AD63E192E0430A5D70 | |||
| 1496 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_iq5y5emg.zfa.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 504 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa504.18903\GenP-v3.6.6.exe | executable | |
MD5:F7CDC7B76C80DCED39E24BC5E0995F0F | SHA256:1DCB04625F4555B6988C7D9309C49E872FFF584E913AAD8530227CF641FD018D | |||
| 5908 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_fj3isnur.zki.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
24
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3944 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3944 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2552 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.16.252.233:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
3476 | GenP-v3.6.6.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3476 | GenP-v3.6.6.exe | GET | 200 | 142.250.184.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5904 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 2.16.253.202:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3944 | SIHClient.exe | 20.12.23.50:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |