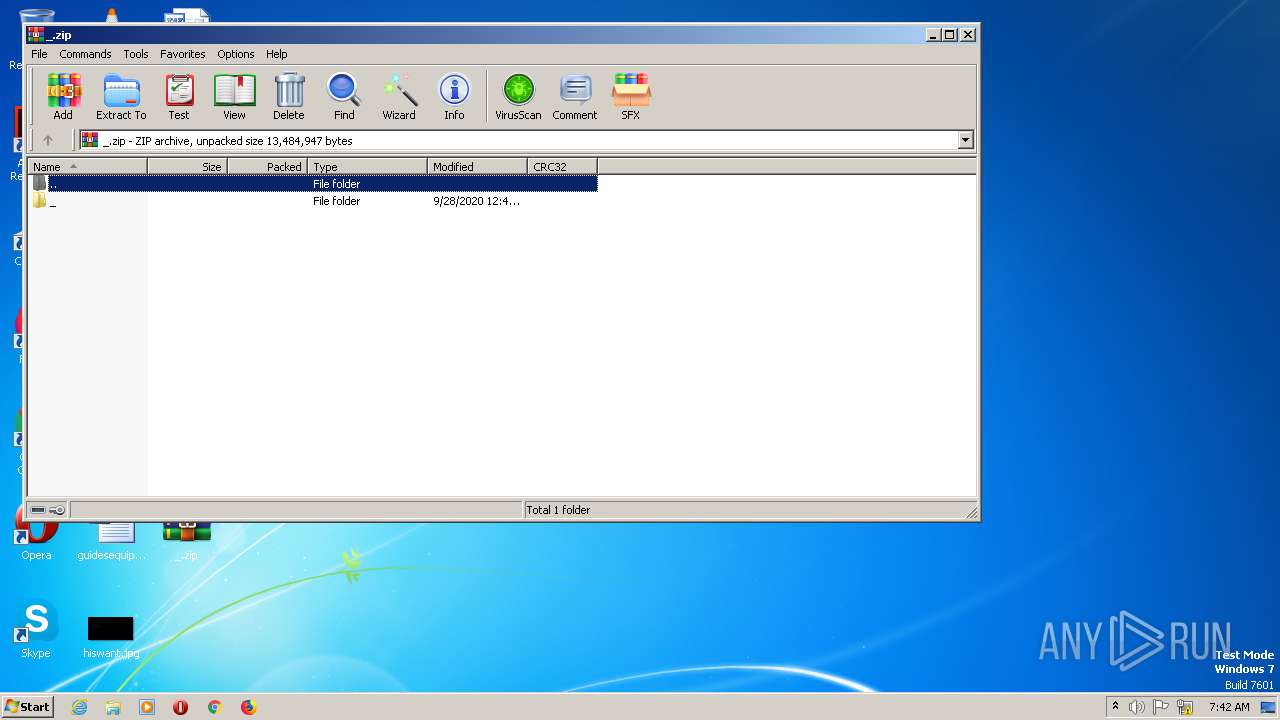
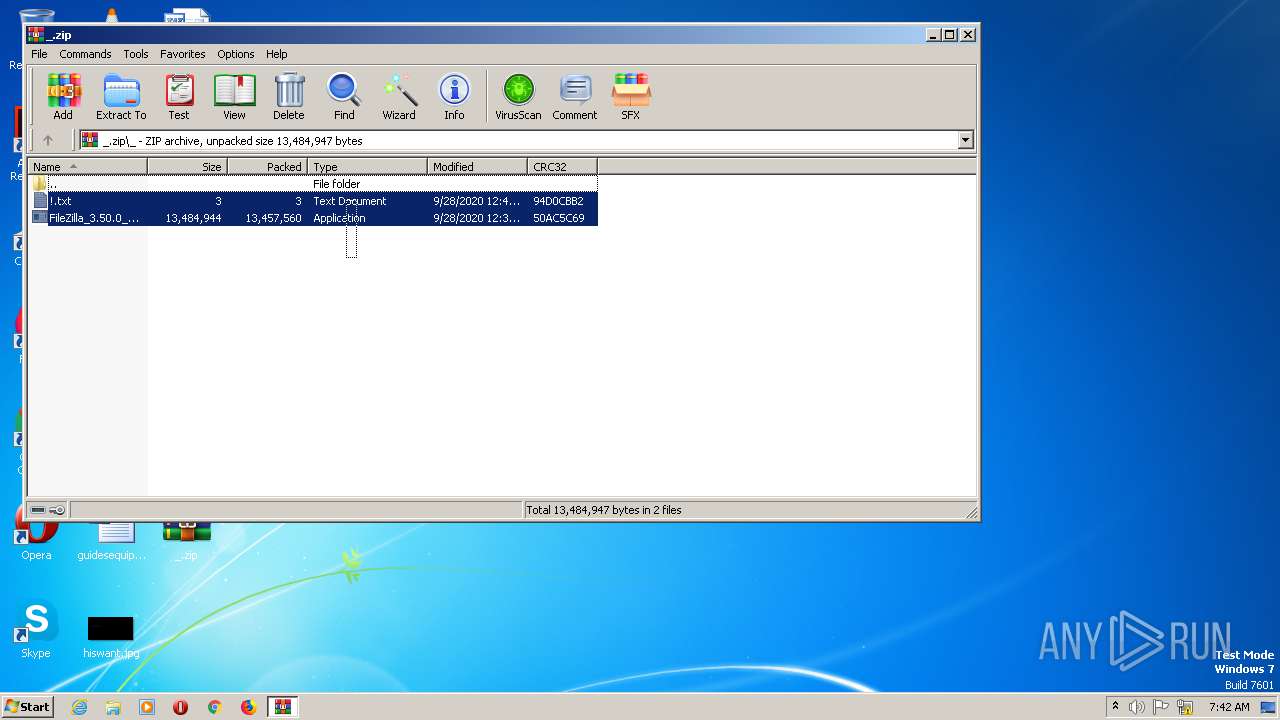
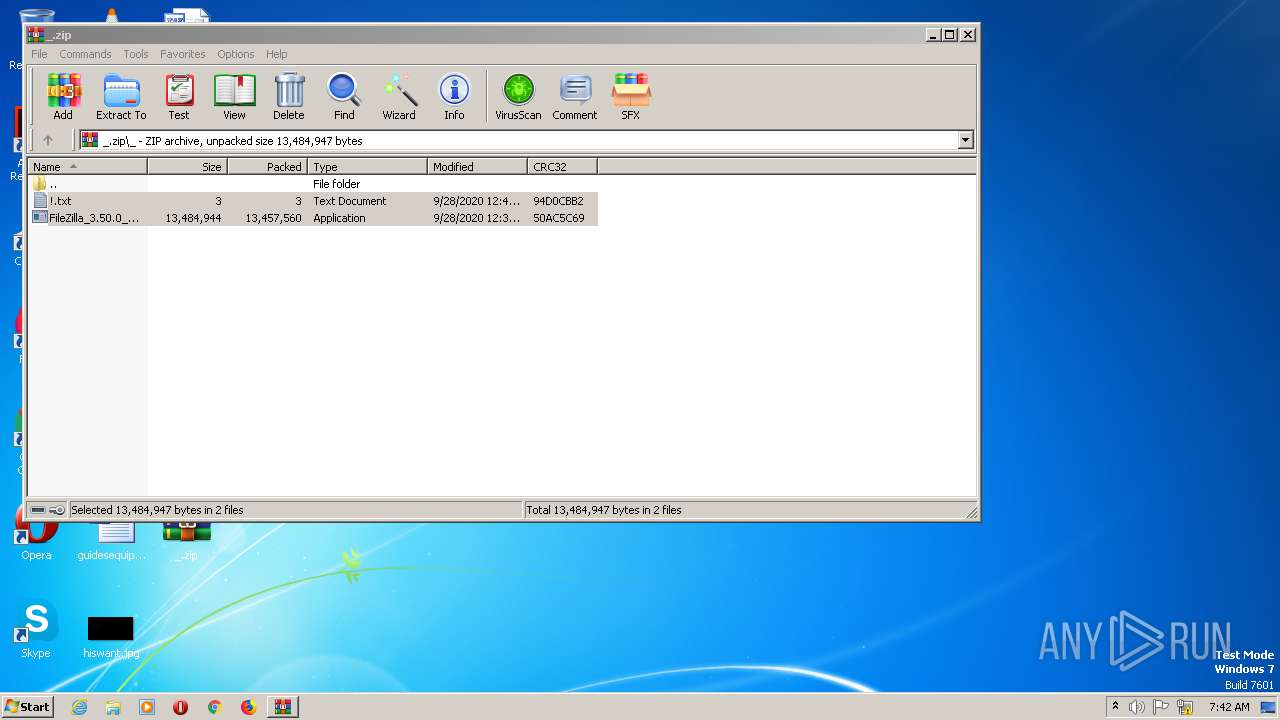
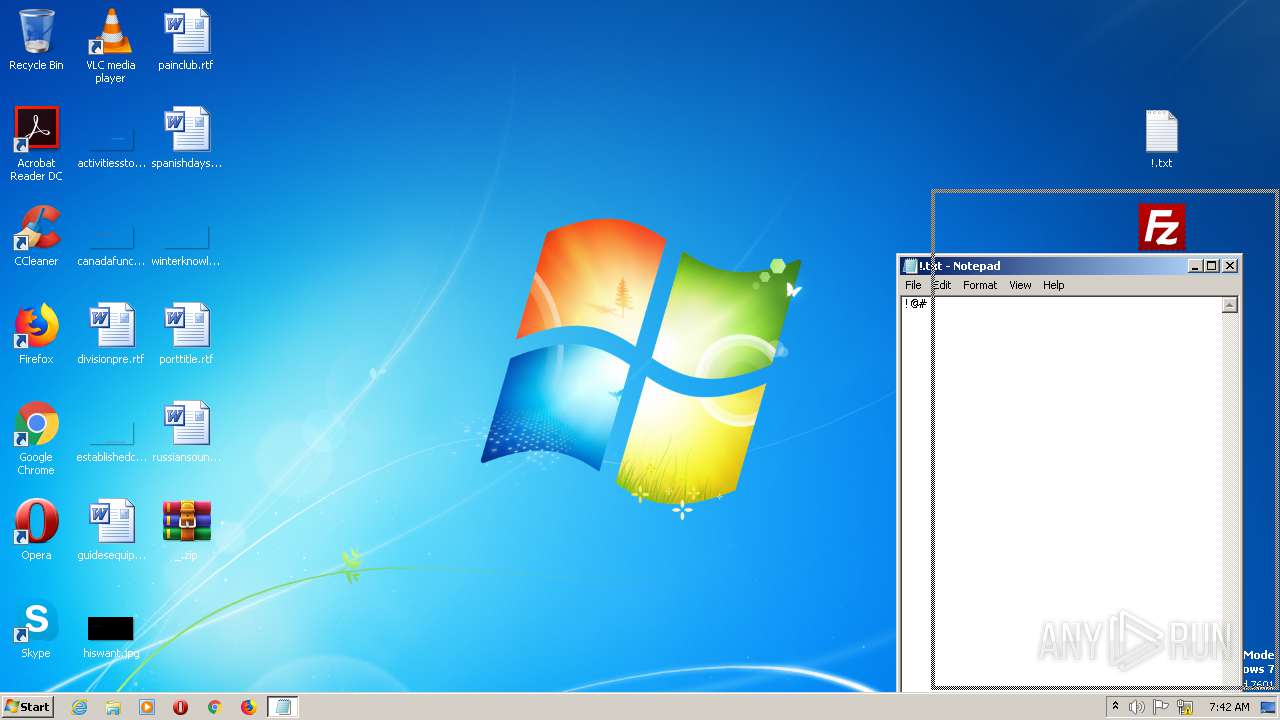
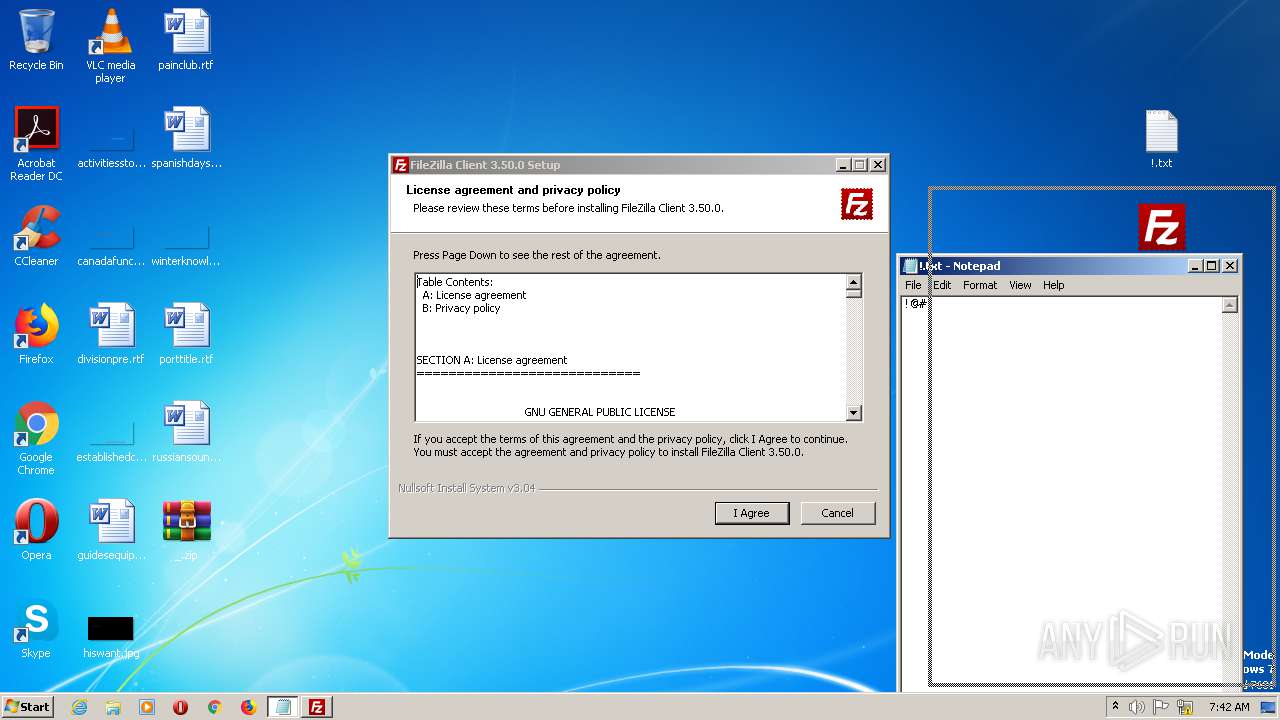
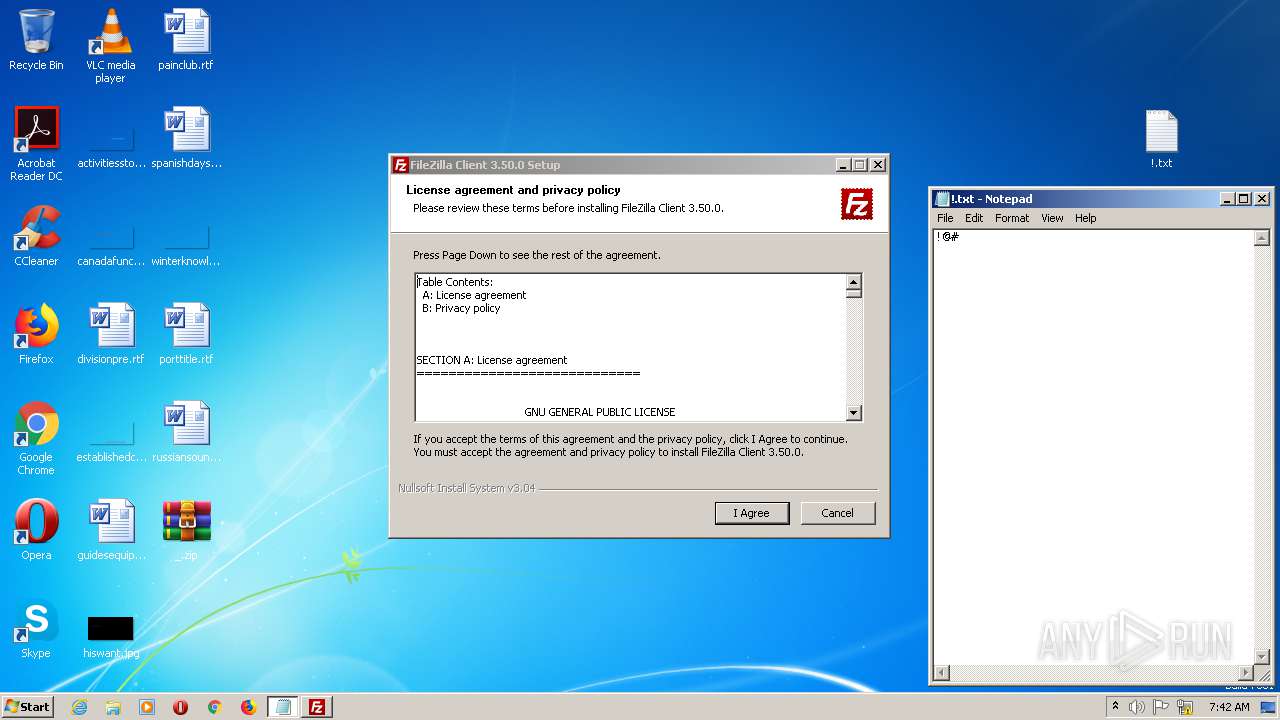
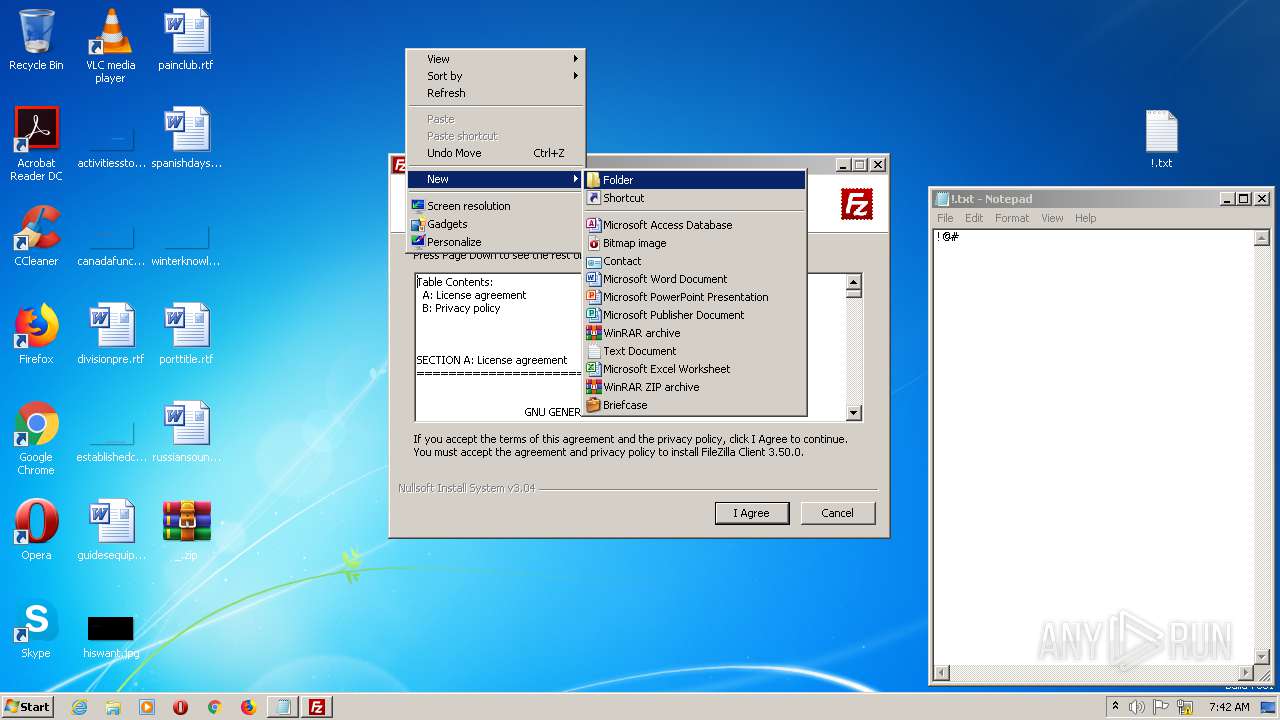
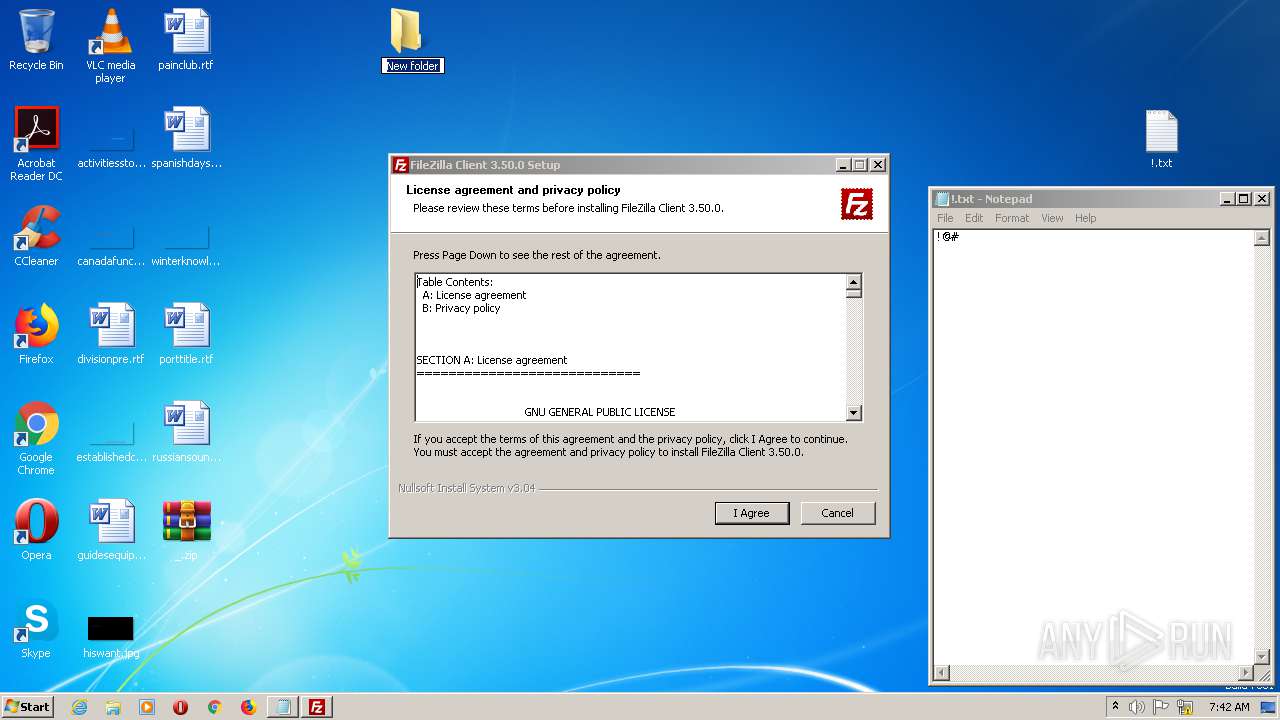
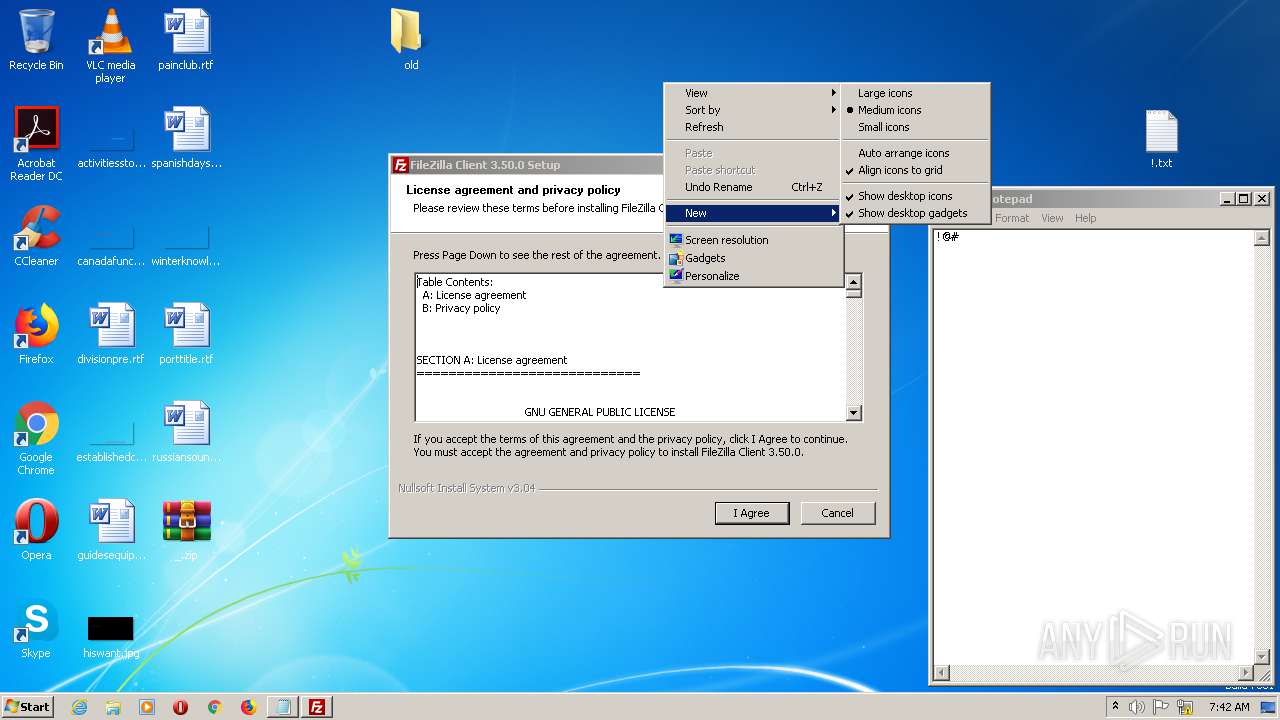
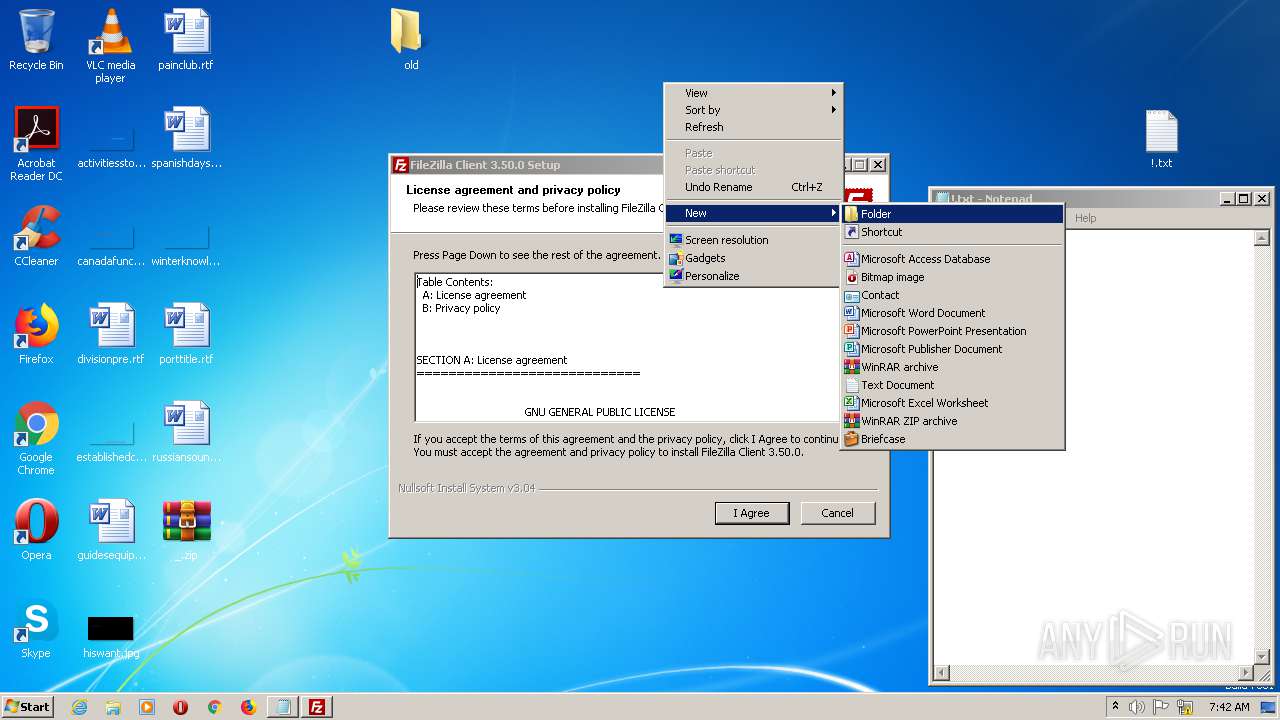
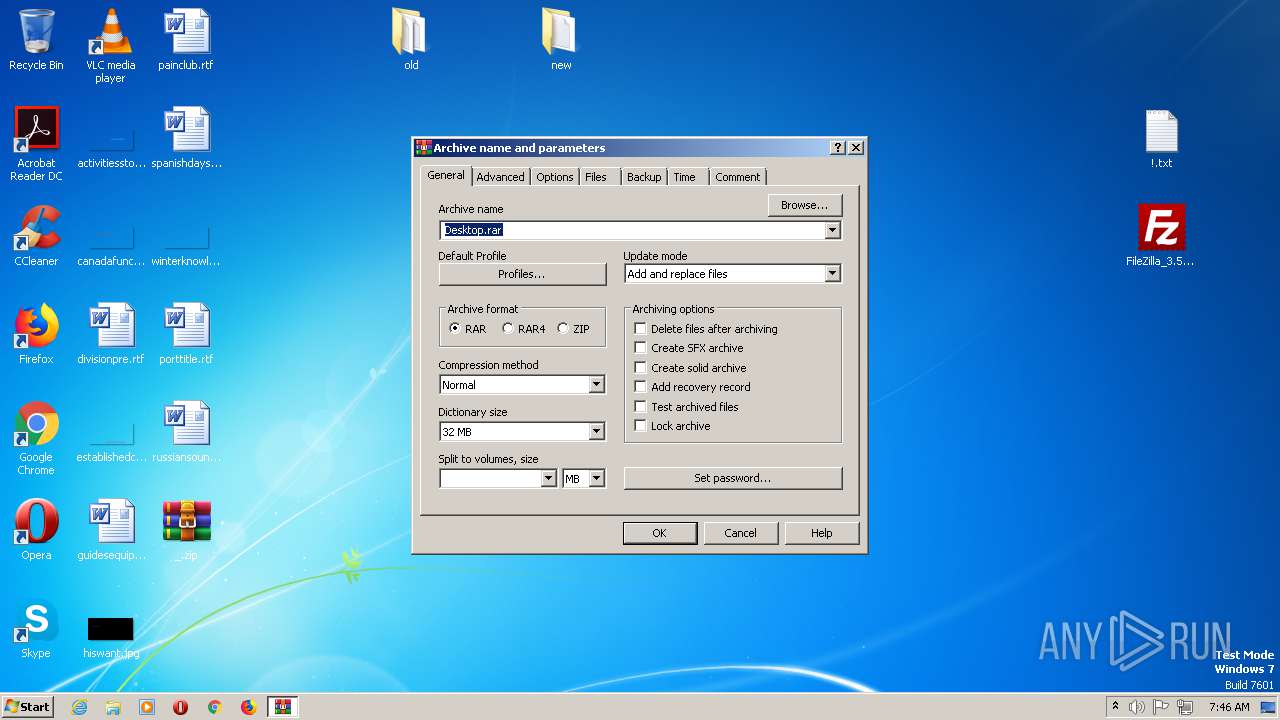
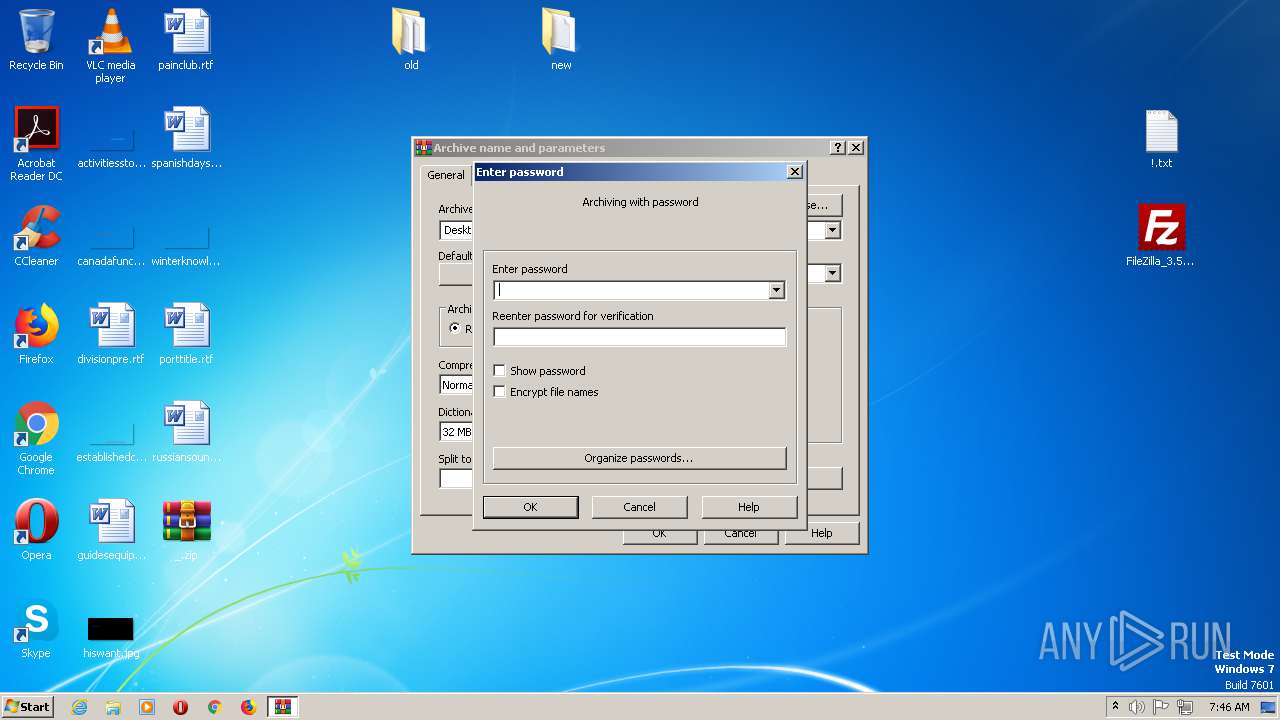
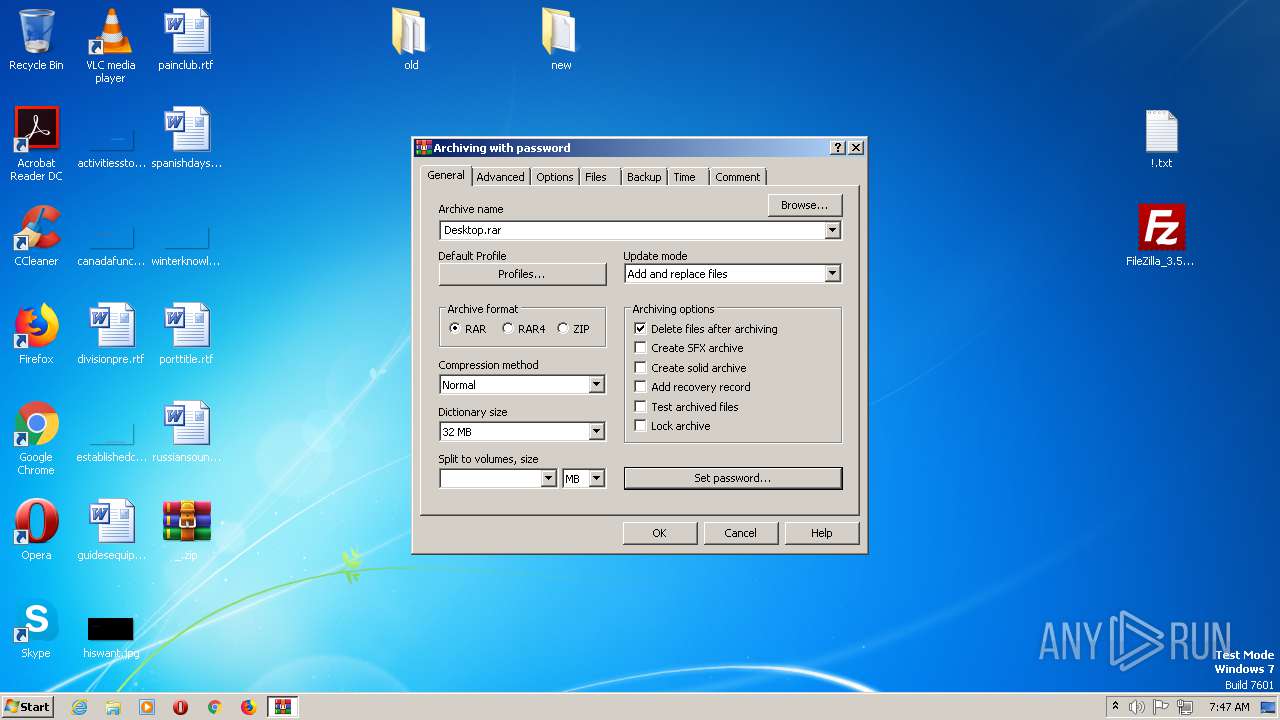
| File name: | _.zip |
| Full analysis: | https://app.any.run/tasks/13ddd915-956c-473c-8485-1786bac13a5b |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 07:41:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 5DBF41454F3F9AA46B310010ACB83A69 |
| SHA1: | F7A9210F64F297F6602950AD868585DB53823D68 |
| SHA256: | D3160823838521D5E2AFD1F10AE47BA38CFAF0F63E3E27C943073890A1A1238D |
| SSDEEP: | 196608:NHw3N4MyGZpkrURxw8IqXMkM8FukVTiu3hUYel+ACtnpTknzyt5s2iL973wXFFq:NHun+URxwlPitliu3O3CpTkzOd45w1Fq |
MALICIOUS
Application was dropped or rewritten from another process
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1240)
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
- filezilla.exe (PID: 1884)
Loads dropped or rewritten executable
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1240)
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
- regsvr32.exe (PID: 2336)
- filezilla.exe (PID: 1884)
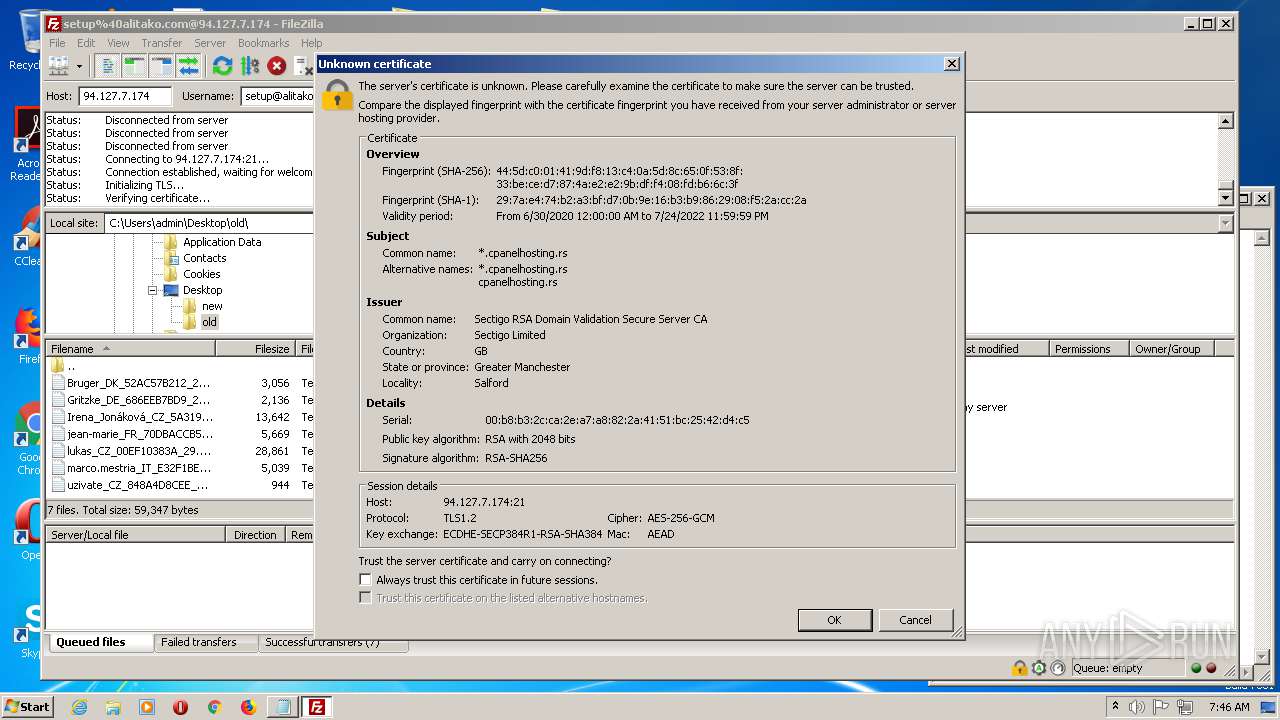
Changes settings of System certificates
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
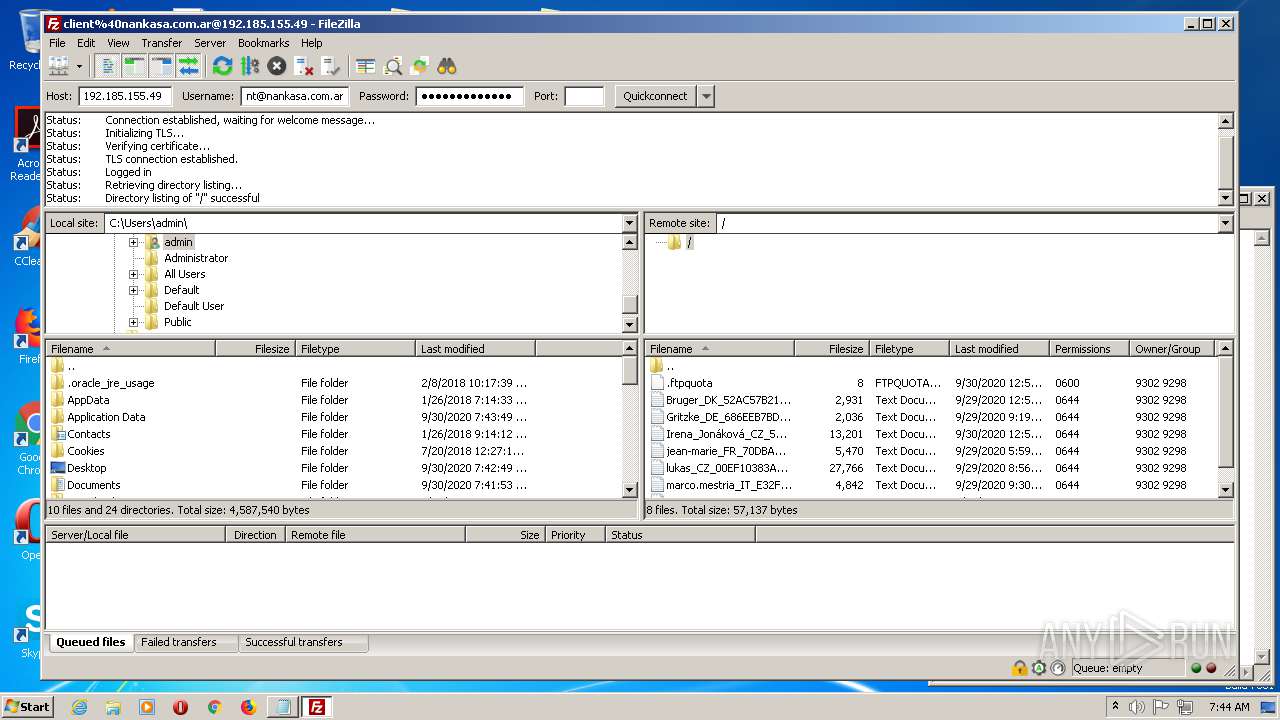
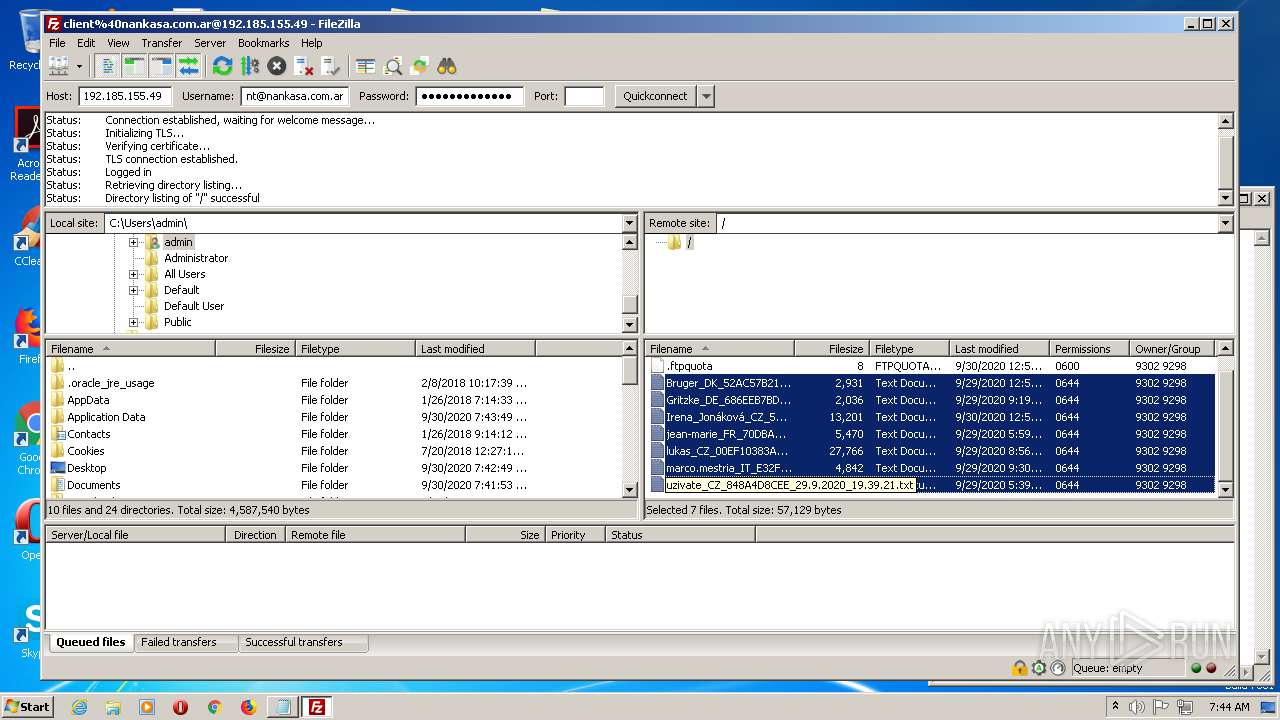
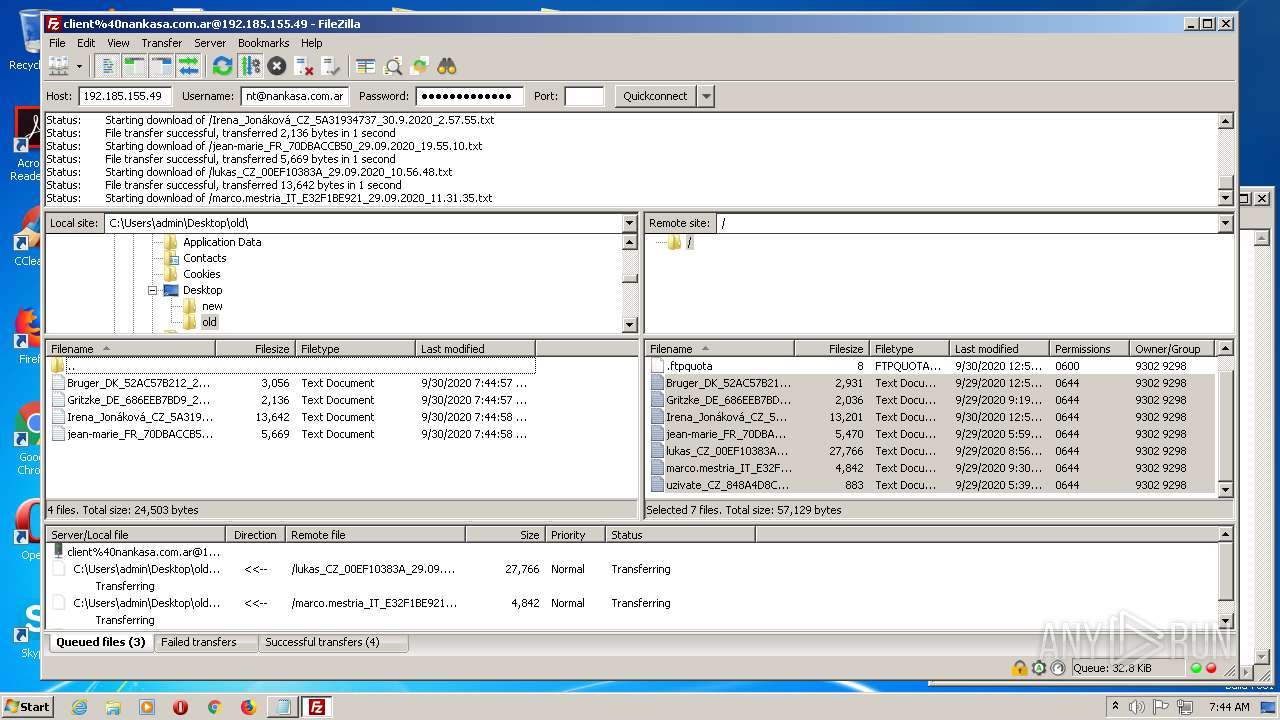
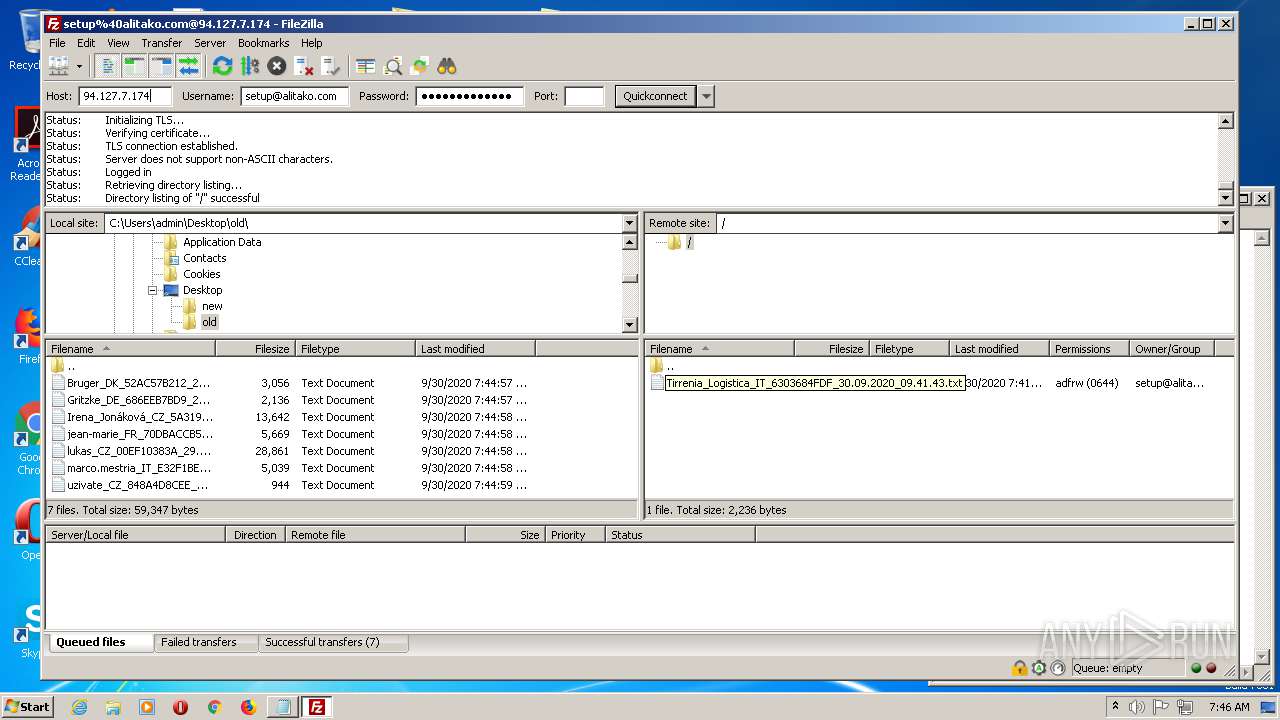
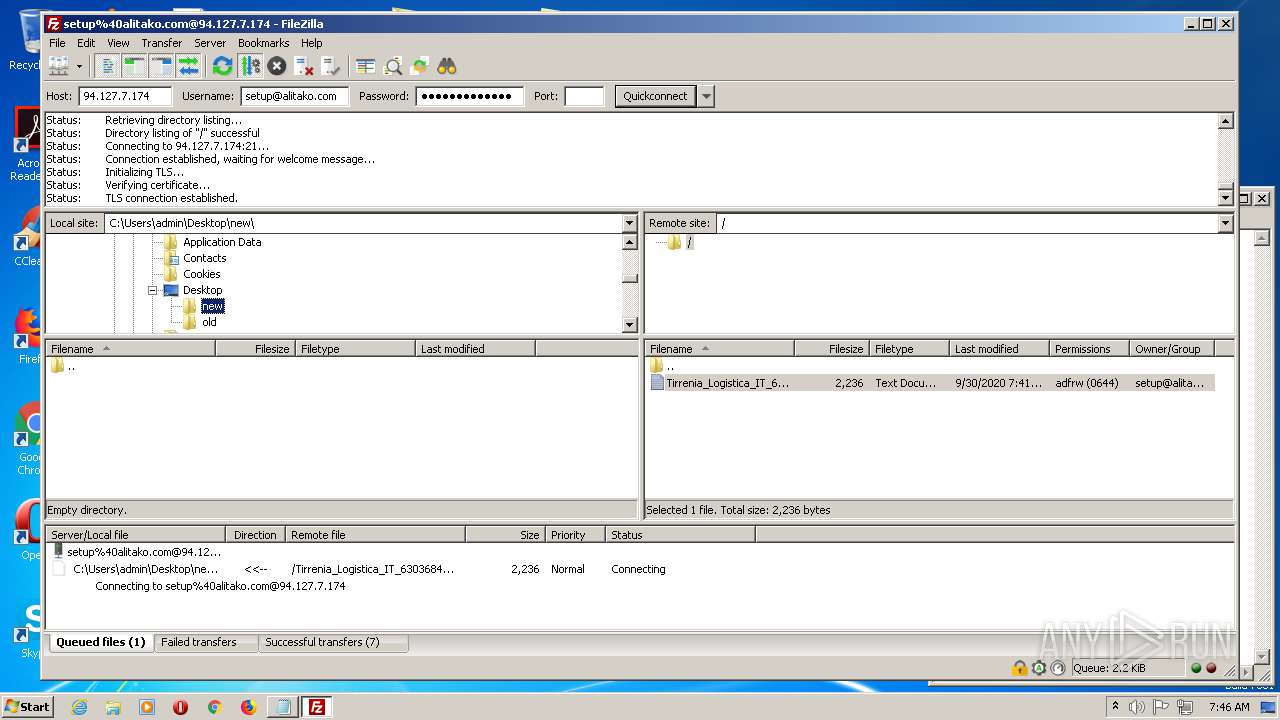
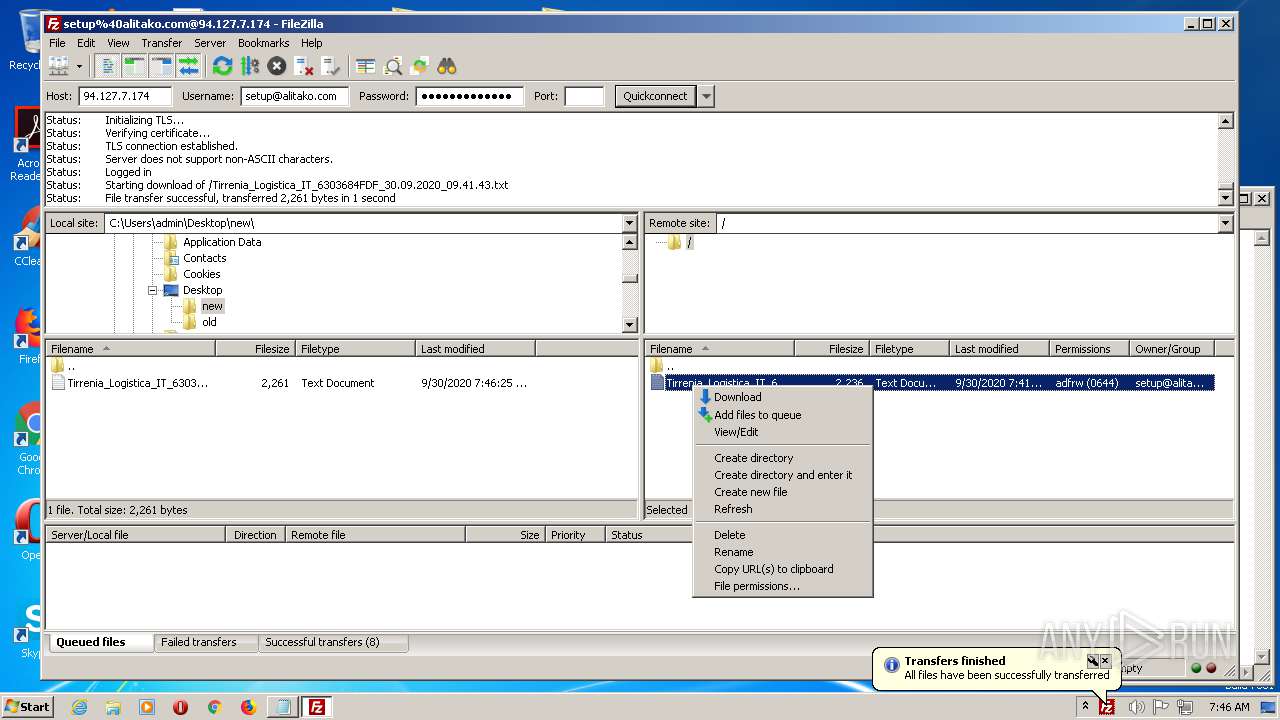
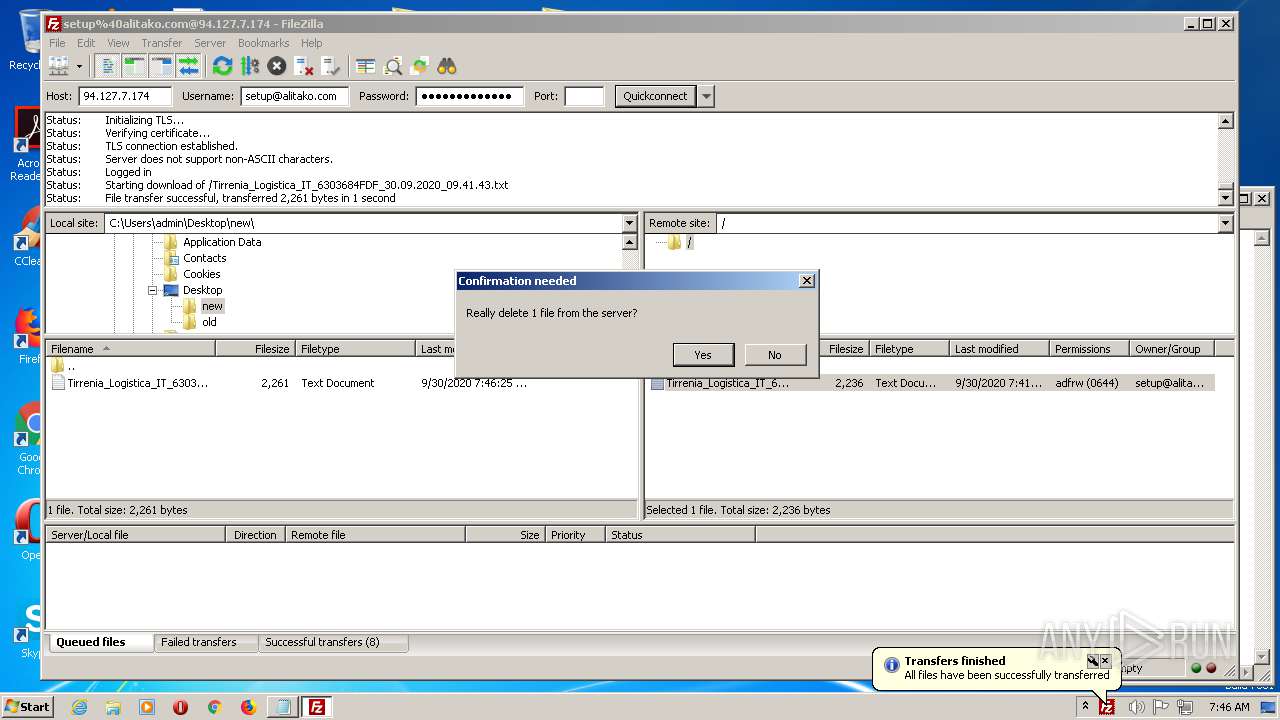
Actions looks like stealing of personal data
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Registers / Runs the DLL via REGSVR32.EXE
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
SUSPICIOUS
Executable content was dropped or overwritten
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1240)
- WinRAR.exe (PID: 2596)
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Reads the machine GUID from the registry
- WinRAR.exe (PID: 2596)
- WinRAR.exe (PID: 2624)
- filezilla.exe (PID: 1884)
Application launched itself
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1240)
Reads Environment values
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Reads internet explorer settings
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Creates a software uninstall entry
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Creates COM task schedule object
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
- regsvr32.exe (PID: 2336)
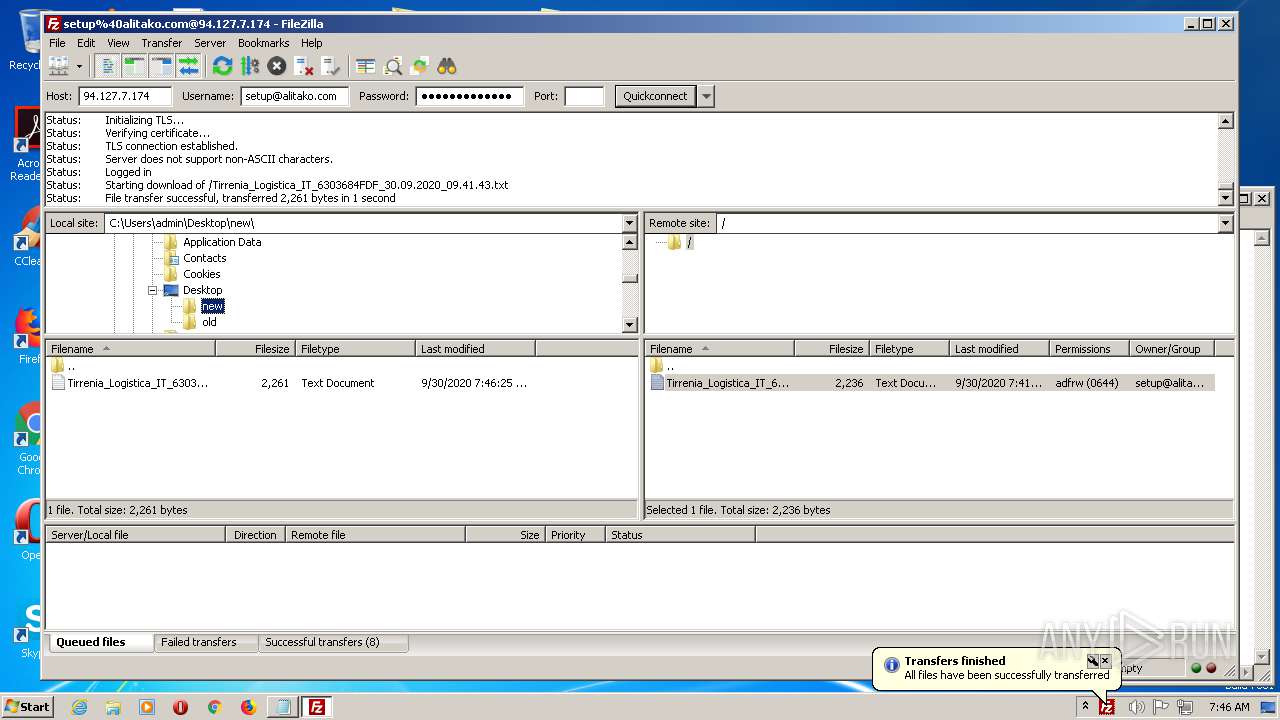
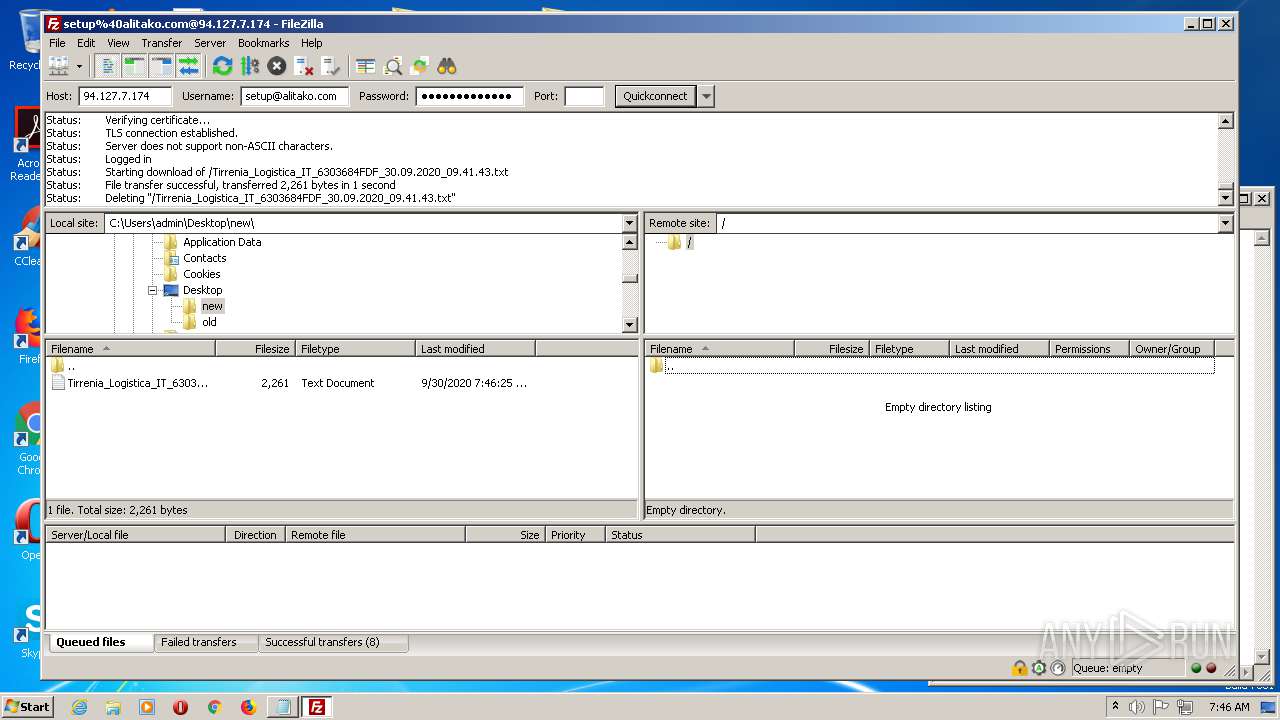
Creates files in the user directory
- filezilla.exe (PID: 1884)
Creates files in the program directory
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
INFO
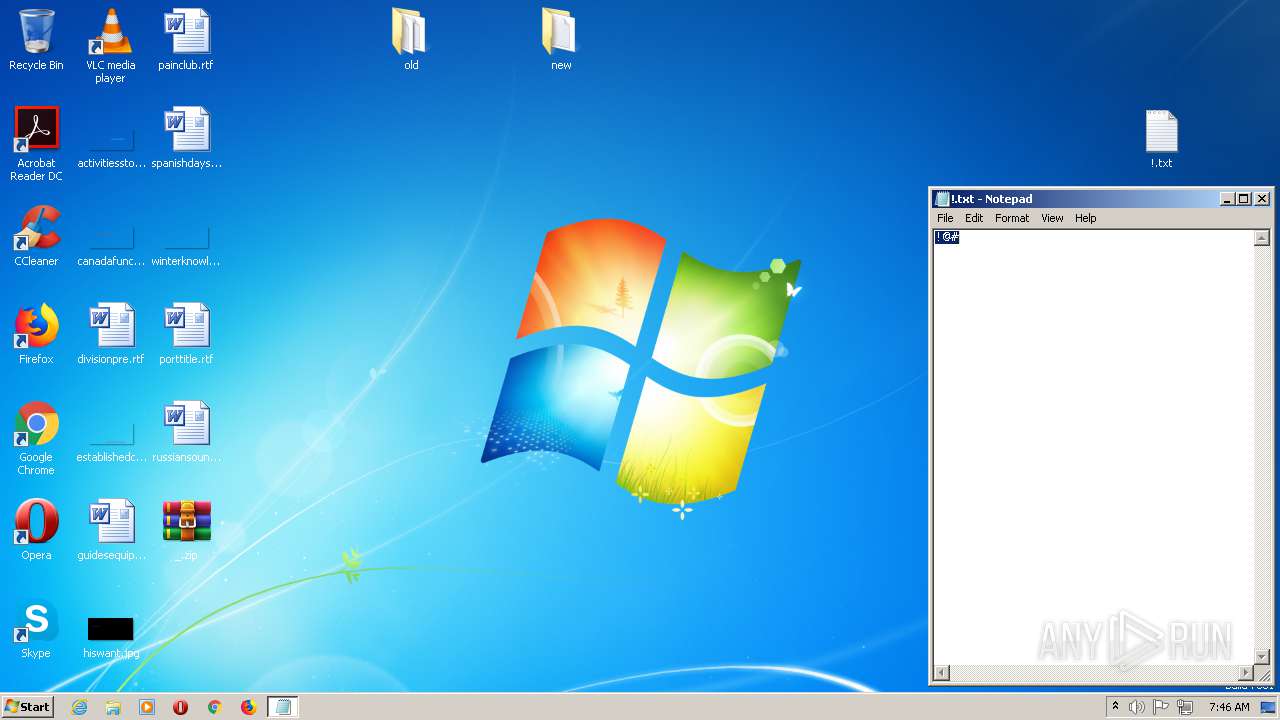
Manual execution by user
- NOTEPAD.EXE (PID: 1704)
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1240)
- WinRAR.exe (PID: 2624)
Reads settings of System Certificates
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Dropped object may contain Bitcoin addresses
- FileZilla_3.50.0_win64_sponsored-setup.exe (PID: 1728)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .kmz | | | Google Earth saved working session (60) |
|---|---|---|
| .zip | | | ZIP compressed archive (40) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:09:28 14:44:22 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | _/ |
Total processes
59
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
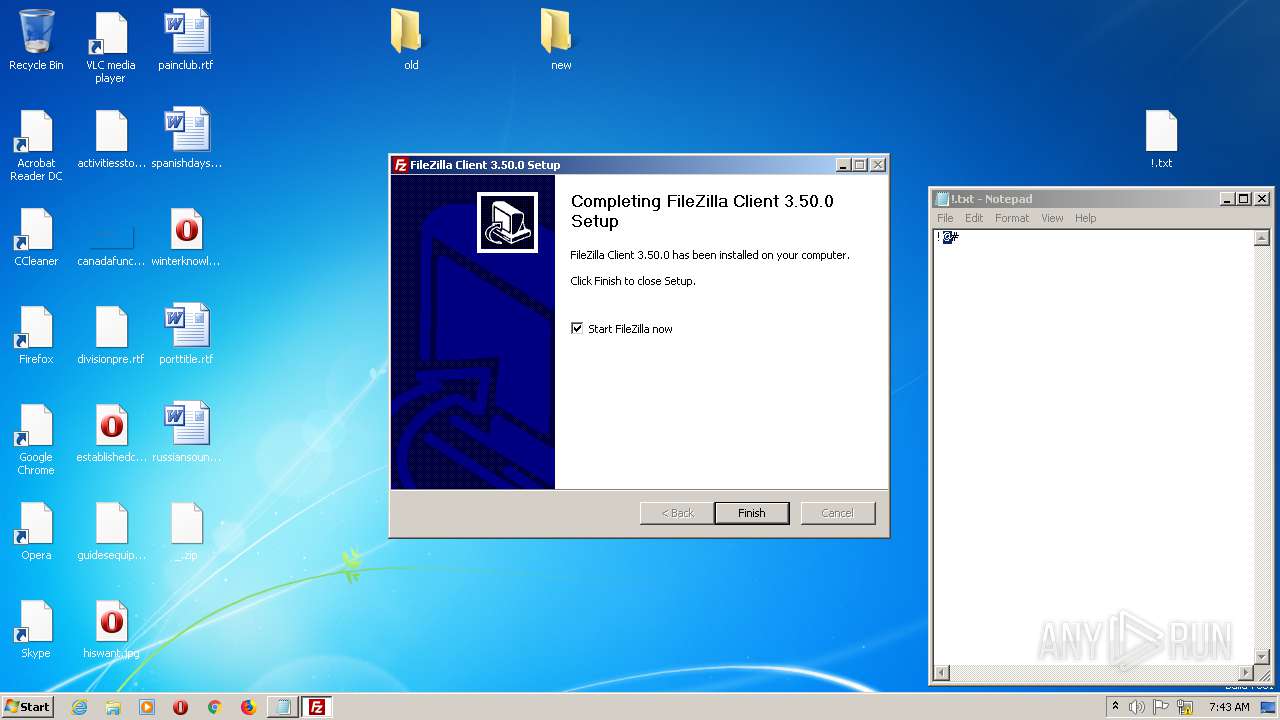
| 1240 | "C:\Users\admin\Desktop\FileZilla_3.50.0_win64_sponsored-setup.exe" | C:\Users\admin\Desktop\FileZilla_3.50.0_win64_sponsored-setup.exe | explorer.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: MEDIUM Description: FileZilla FTP Client Exit code: 0 Version: 3.50.0 Modules
| |||||||||||||||
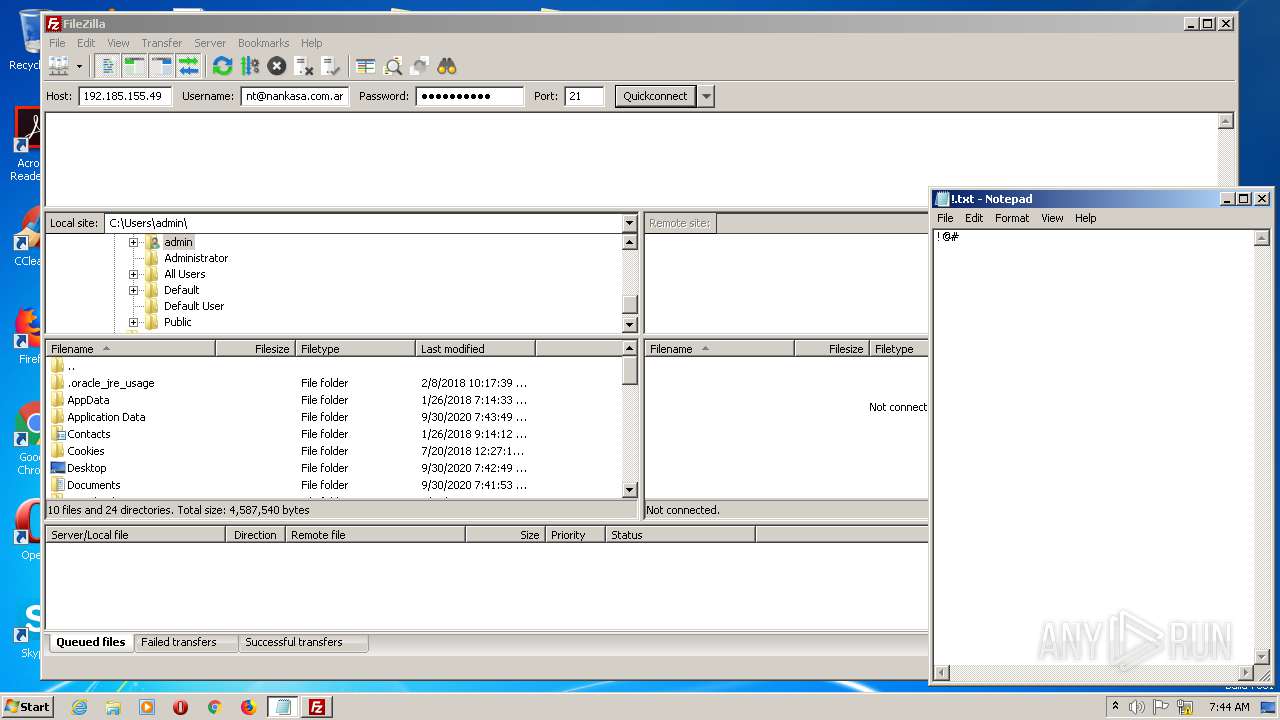
| 1704 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\!.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
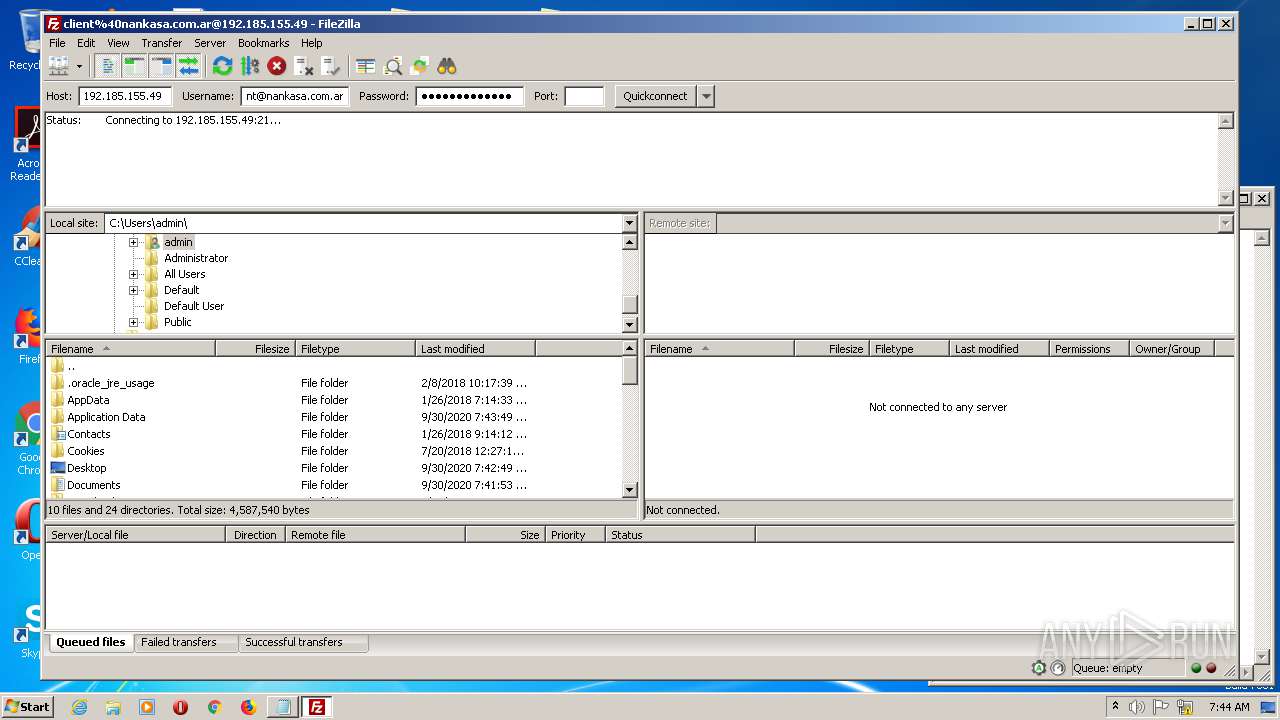
| 1728 | "C:\Users\admin\Desktop\FileZilla_3.50.0_win64_sponsored-setup.exe" /UAC:60152 /NCRC | C:\Users\admin\Desktop\FileZilla_3.50.0_win64_sponsored-setup.exe | FileZilla_3.50.0_win64_sponsored-setup.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: HIGH Description: FileZilla FTP Client Exit code: 0 Version: 3.50.0 Modules
| |||||||||||||||
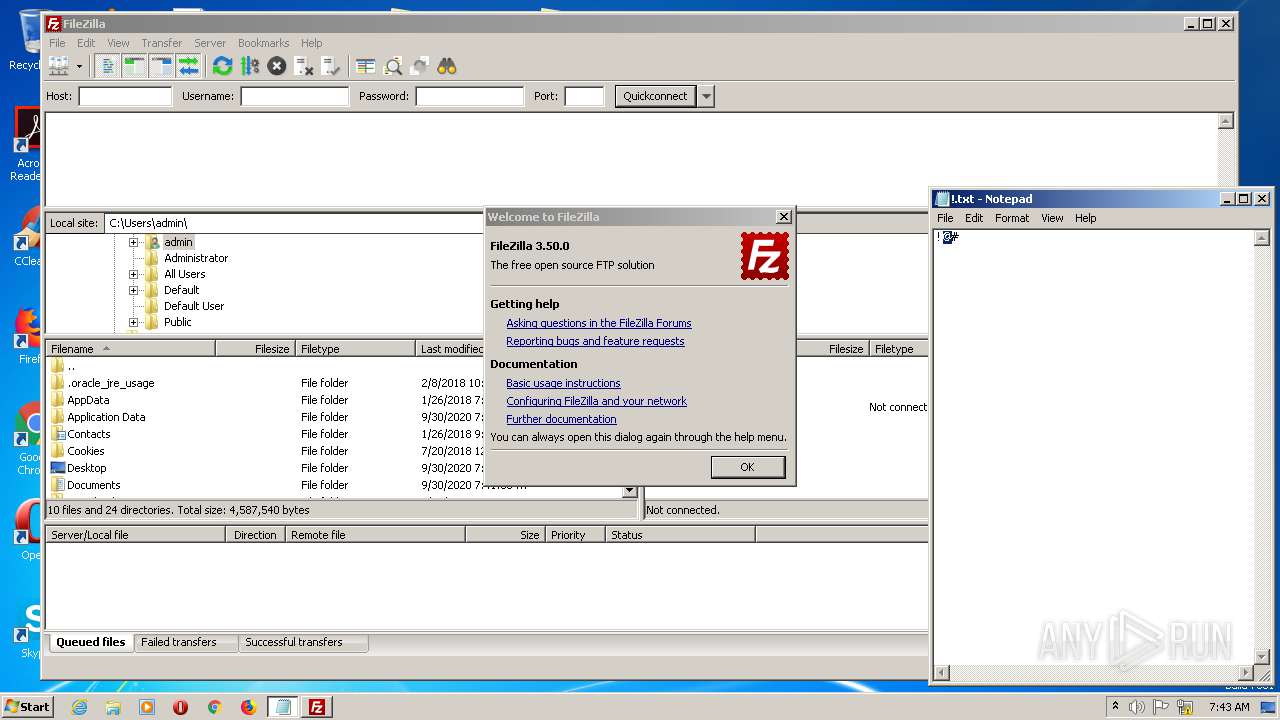
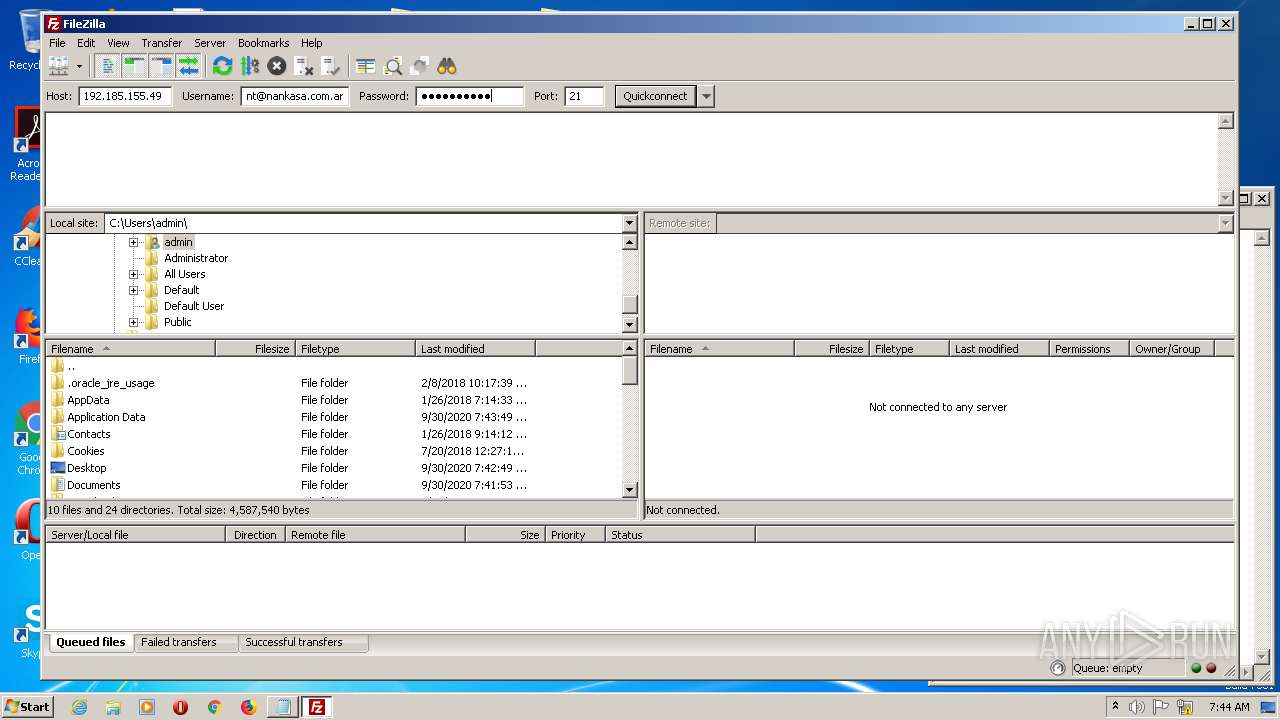
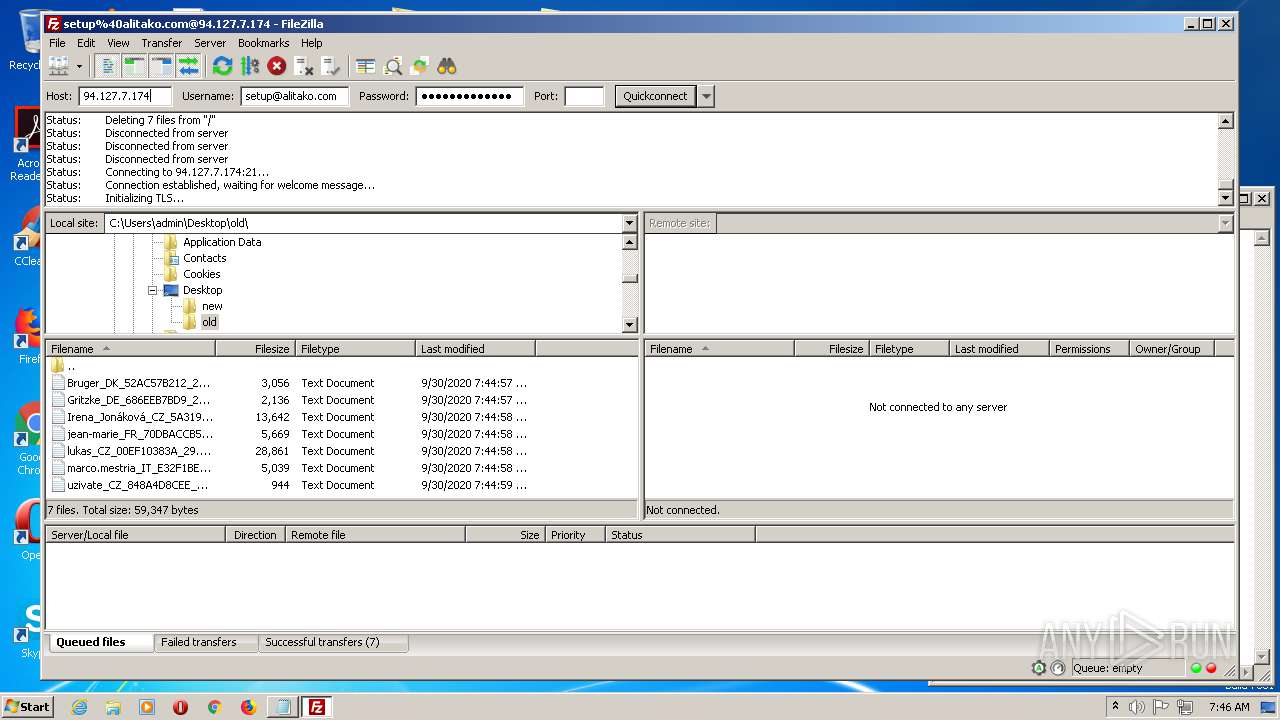
| 1884 | "C:\Program Files\FileZilla FTP Client\filezilla.exe" | C:\Program Files\FileZilla FTP Client\filezilla.exe | FileZilla_3.50.0_win64_sponsored-setup.exe | ||||||||||||
User: admin Company: FileZilla Project Integrity Level: MEDIUM Description: FileZilla FTP Client Exit code: 0 Version: 3, 50, 0, 0 Modules
| |||||||||||||||
| 2336 | "C:\Windows\system32\regsvr32.exe" /s "C:\Program Files\FileZilla FTP Client\fzshellext_64.dll" | C:\Windows\system32\regsvr32.exe | — | FileZilla_3.50.0_win64_sponsored-setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
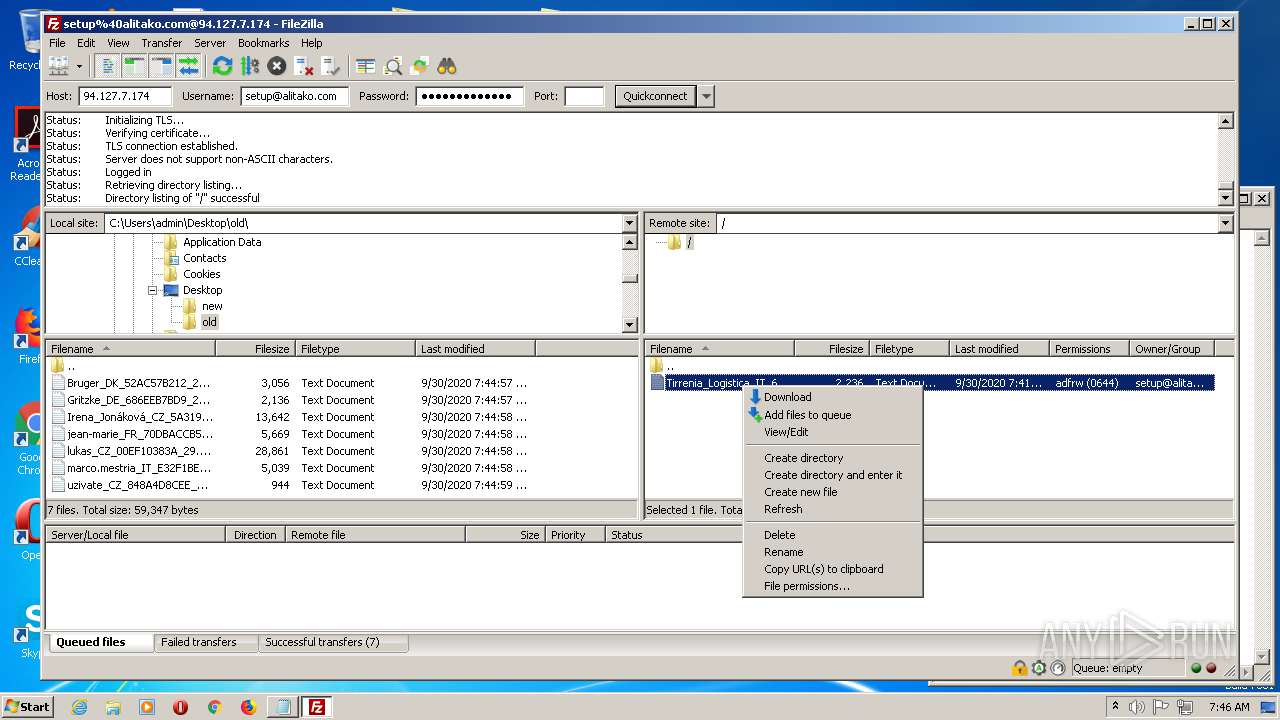
| 2596 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\_.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
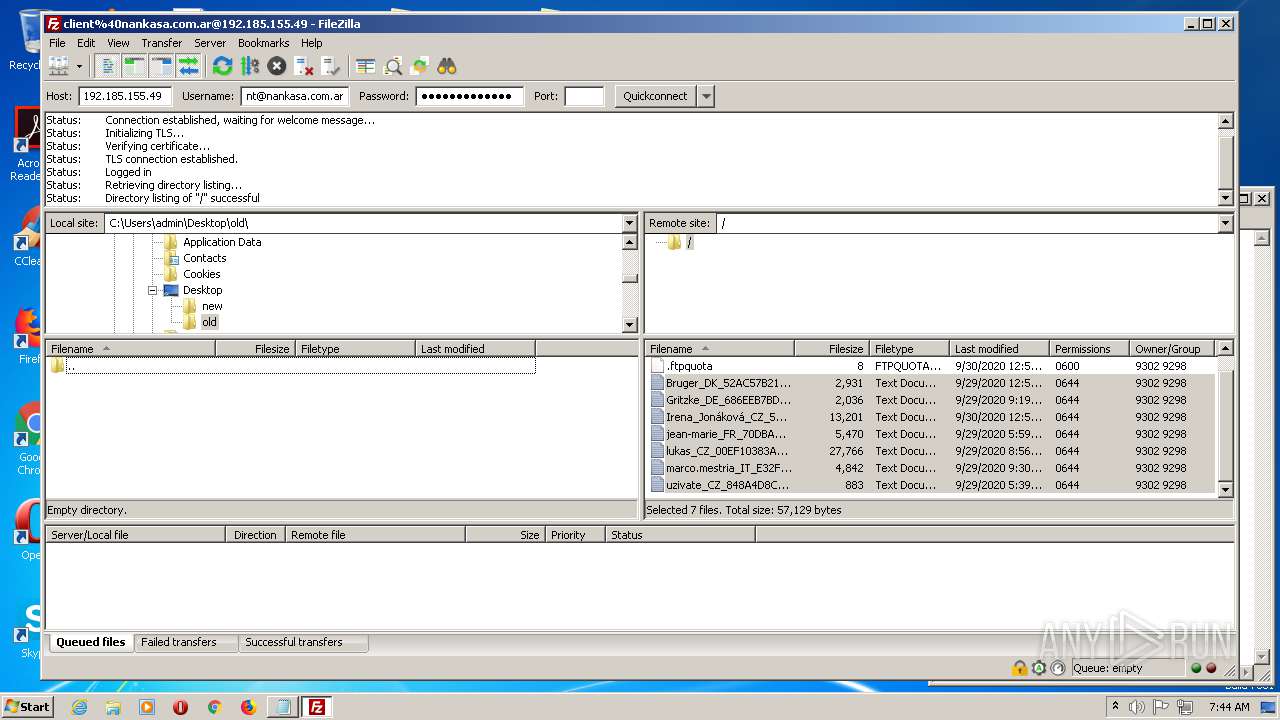
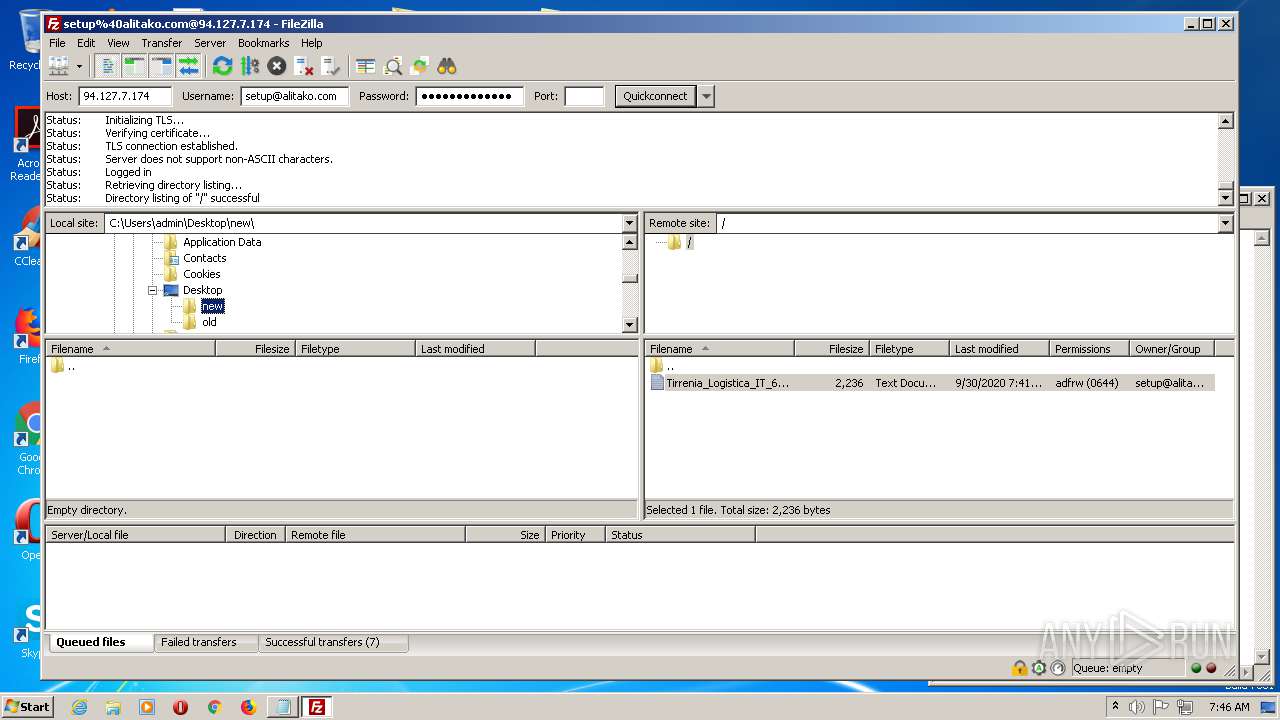
| 2624 | "C:\Program Files\WinRAR\WinRAR.exe" a -ep1 -scul -r0 -iext -- . C:\Users\admin\Desktop\old C:\Users\admin\Desktop\new | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 257
Read events
1 150
Write events
107
Delete events
0
Modification events
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\_.zip | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2596) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF1600000016000000D60300000B020000 | |||
Executable files
31
Suspicious files
113
Text files
773
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\0018E327.log | — | |
MD5:— | SHA256:— | |||
| 2596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2596.6582\_\!.txt | text | |
MD5:— | SHA256:— | |||
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsd16310159593\css\sdk-ui\images\button-bg.png | image | |
MD5:98B1DE48DFA64DC2AA1E52FACFBEE3B0 | SHA256:2693930C474FE640E2FE8D6EF98ABE2ECD303D2392C3D8B2E006E8942BA8F534 | |||
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsd16310159593\csshover3.htc | html | |
MD5:52FA0DA50BF4B27EE625C80D36C67941 | SHA256:E37E99DDFC73AC7BA774E23736B2EF429D9A0CB8C906453C75B14C029BDD5493 | |||
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsd16310159593\css\sdk-ui\button.css | text | |
MD5:37E1FF96E084EC201F0D95FEEF4D5E94 | SHA256:8E806F5B94FC294E918503C8053EF1284E4F4B1E02C7DA4F4635E33EC33E0534 | |||
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh852B.tmp\nsDialogs.dll | executable | |
MD5:466179E1C8EE8A1FF5E4427DBB6C4A01 | SHA256:1E40211AF65923C2F4FD02CE021458A7745D28E2F383835E3015E96575632172 | |||
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh852B.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
| 2596 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2596.6582\_\FileZilla_3.50.0_win64_sponsored-setup.exe | executable | |
MD5:90F560CE71CC77FC2E121761EEEF265C | SHA256:D04BBCD2855D3BBA4627CBB1DA3A0E5FA79FE0B27B371024605FF1382EA94C58 | |||
| 1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsh852B.tmp\modern-wizard.bmp | image | |
MD5:CBE40FD2B1EC96DAEDC65DA172D90022 | SHA256:3AD2DC318056D0A2024AF1804EA741146CFC18CC404649A44610CBF8B2056CF2 | |||
| 1240 | FileZilla_3.50.0_win64_sponsored-setup.exe | C:\Users\admin\AppData\Local\Temp\nsf7F9D.tmp\System.dll | executable | |
MD5:0D7AD4F45DC6F5AA87F606D0331C6901 | SHA256:3EB38AE99653A7DBC724132EE240F6E5C4AF4BFE7C01D31D23FAF373F9F2EACA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
532 | svchost.exe | GET | 200 | 49.12.121.47:443 | https://offers.filezilla-project.org/offerinfo.php | IN | — | — | whitelisted |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | GET | 200 | 143.204.94.91:80 | http://cloud.nitehe-nutete.com/ | US | — | — | whitelisted |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | POST | 200 | 143.204.94.91:443 | https://cloud.nitehe-nutete.com/ | US | — | — | whitelisted |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | POST | 200 | 13.225.73.25:443 | https://remote.nitehe-nutete.com/ | US | binary | 654 Kb | shared |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | POST | 200 | 143.204.94.91:443 | https://cloud.nitehe-nutete.com/ | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | 49.12.121.47:443 | offers.filezilla-project.org | — | IN | suspicious |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | 143.204.94.91:80 | cloud.nitehe-nutete.com | — | US | unknown |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | 13.225.73.25:443 | remote.nitehe-nutete.com | — | US | suspicious |
1728 | FileZilla_3.50.0_win64_sponsored-setup.exe | 143.204.94.91:443 | cloud.nitehe-nutete.com | — | US | unknown |
1884 | filezilla.exe | 49.12.121.47:443 | offers.filezilla-project.org | — | IN | suspicious |
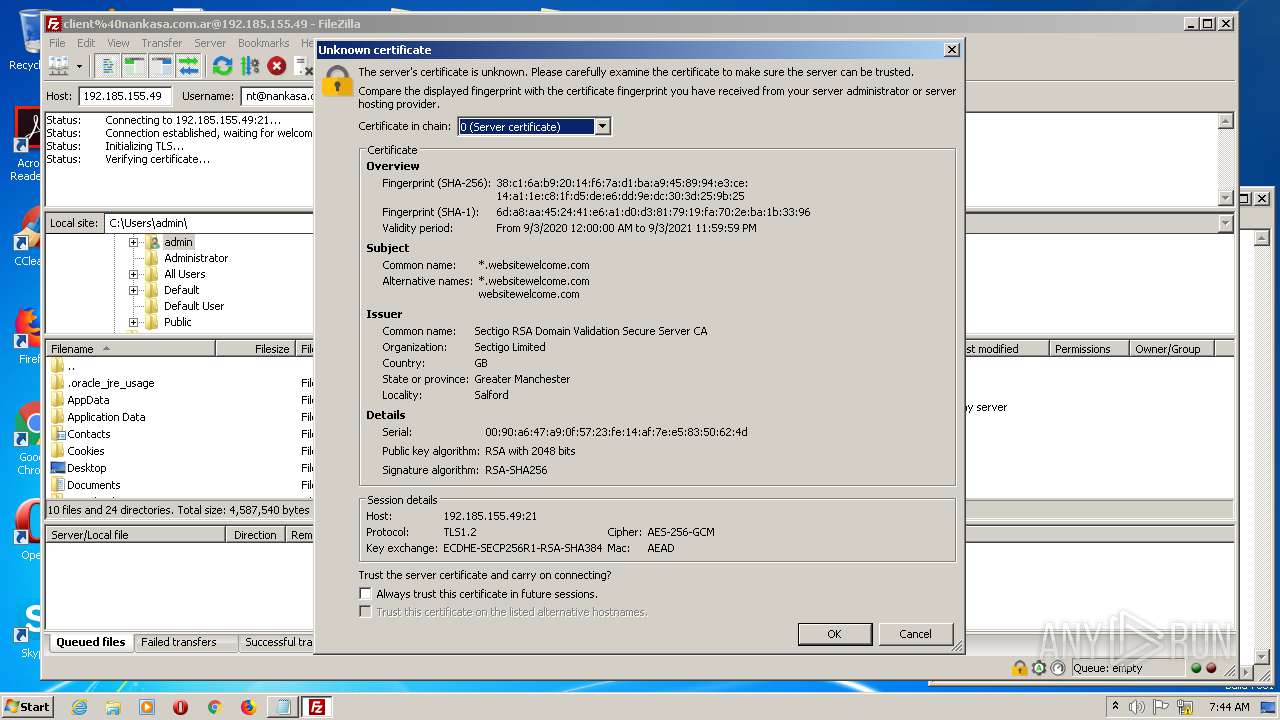
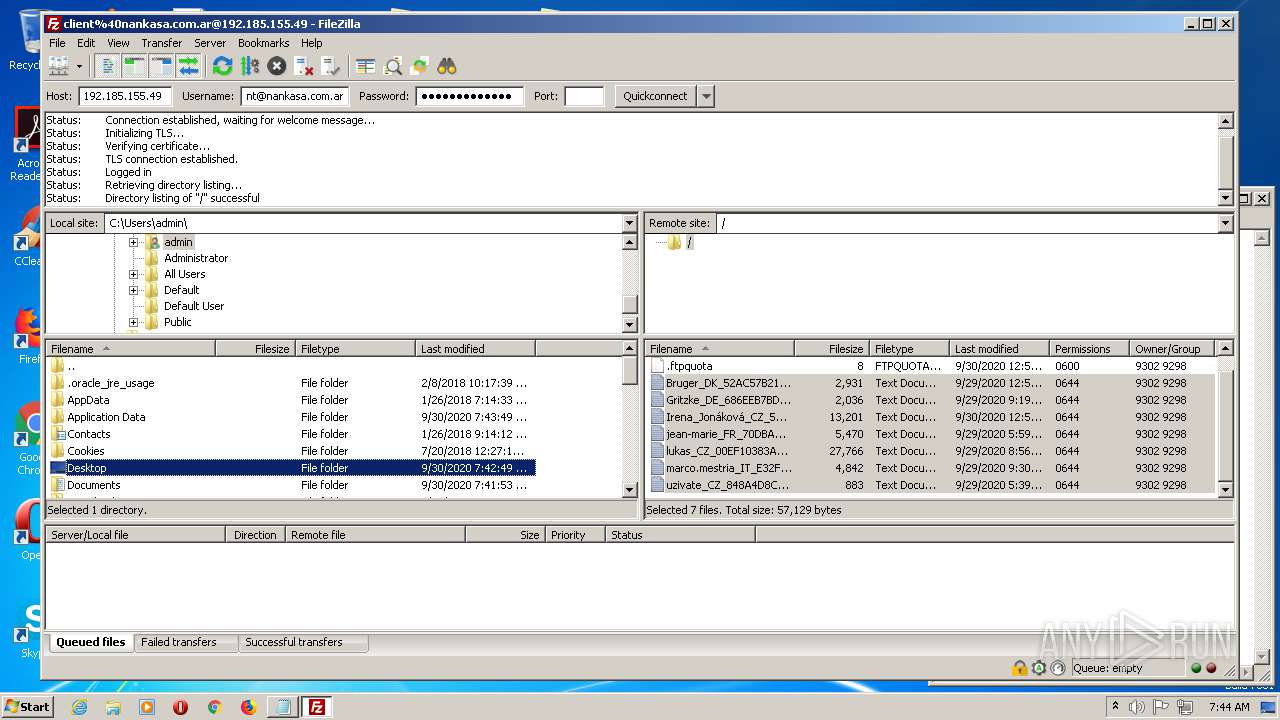
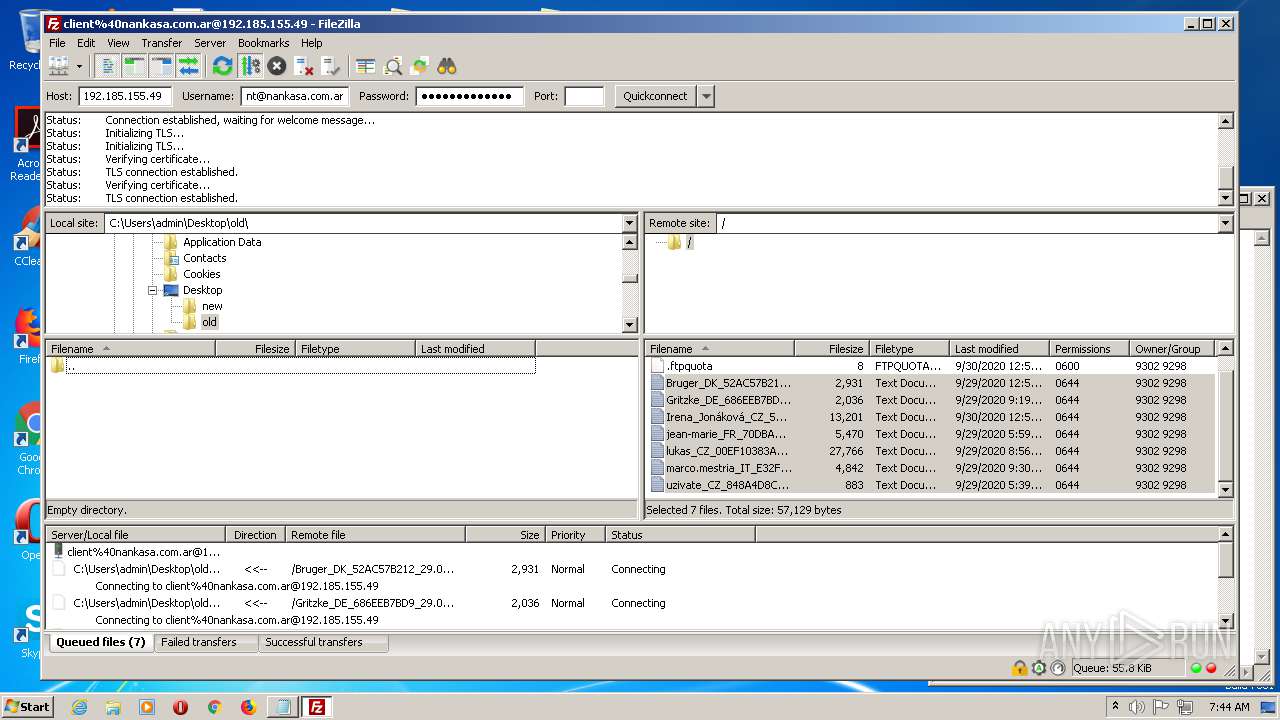
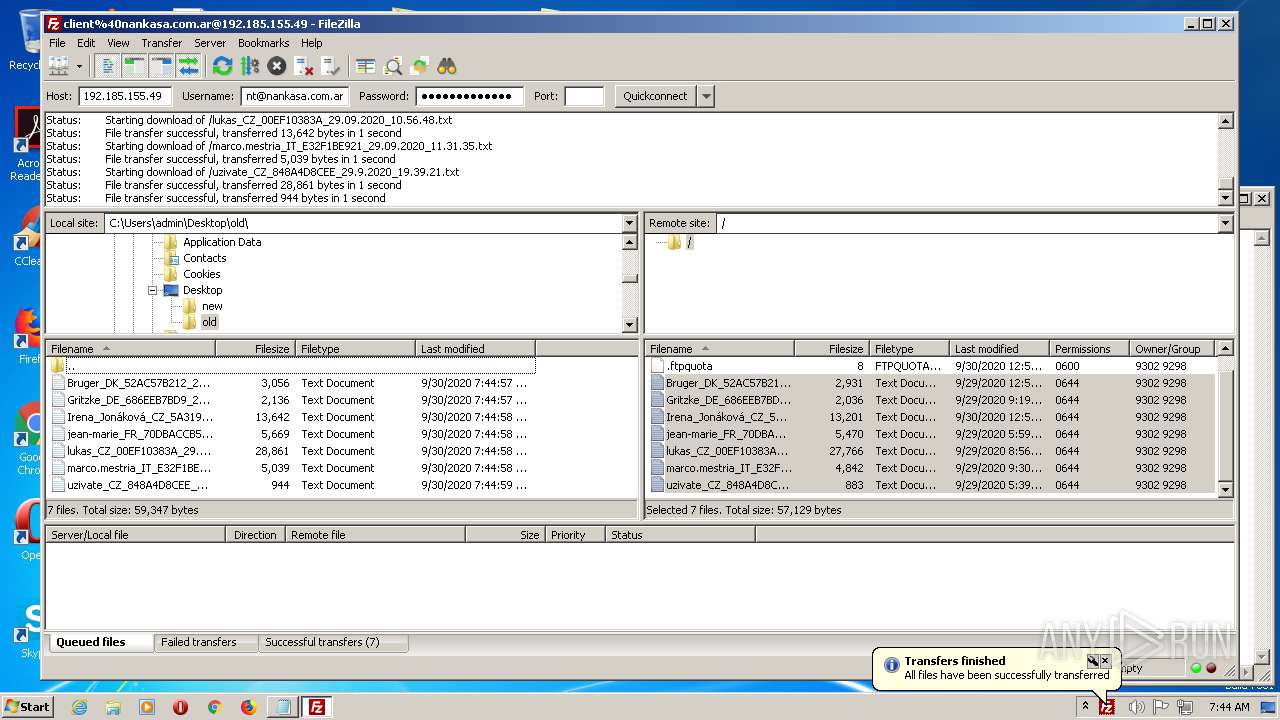
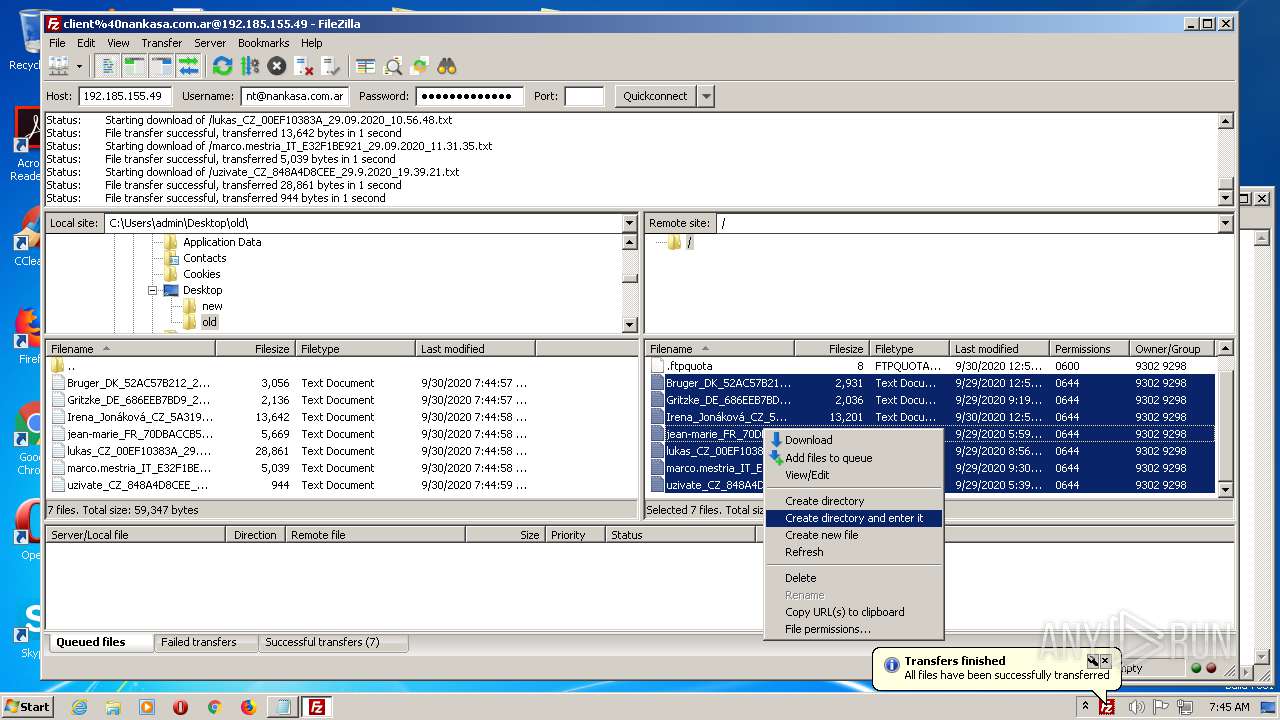
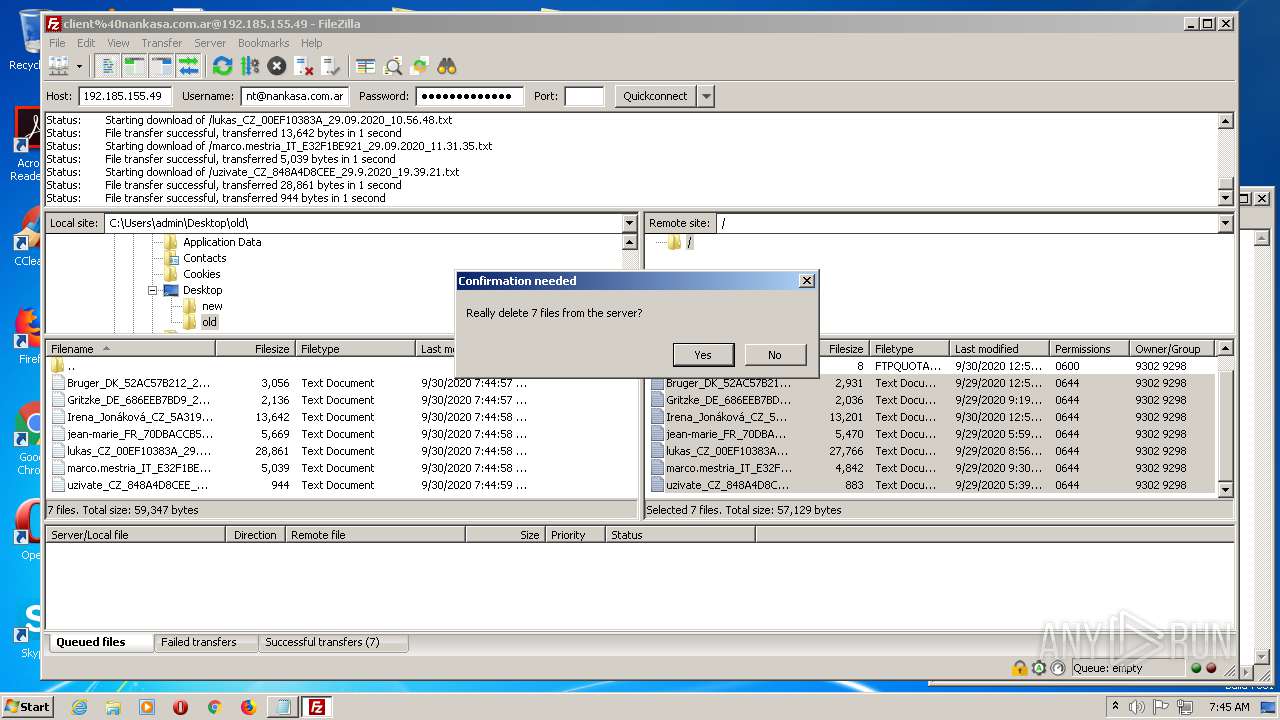
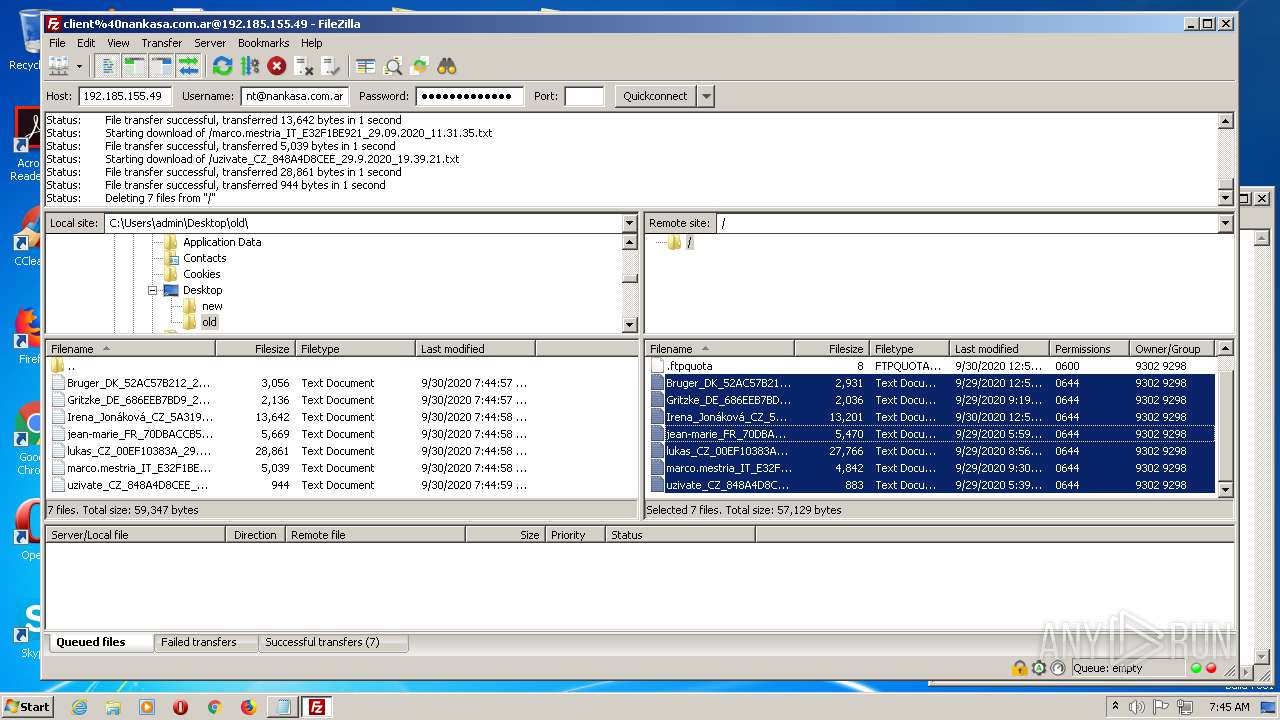
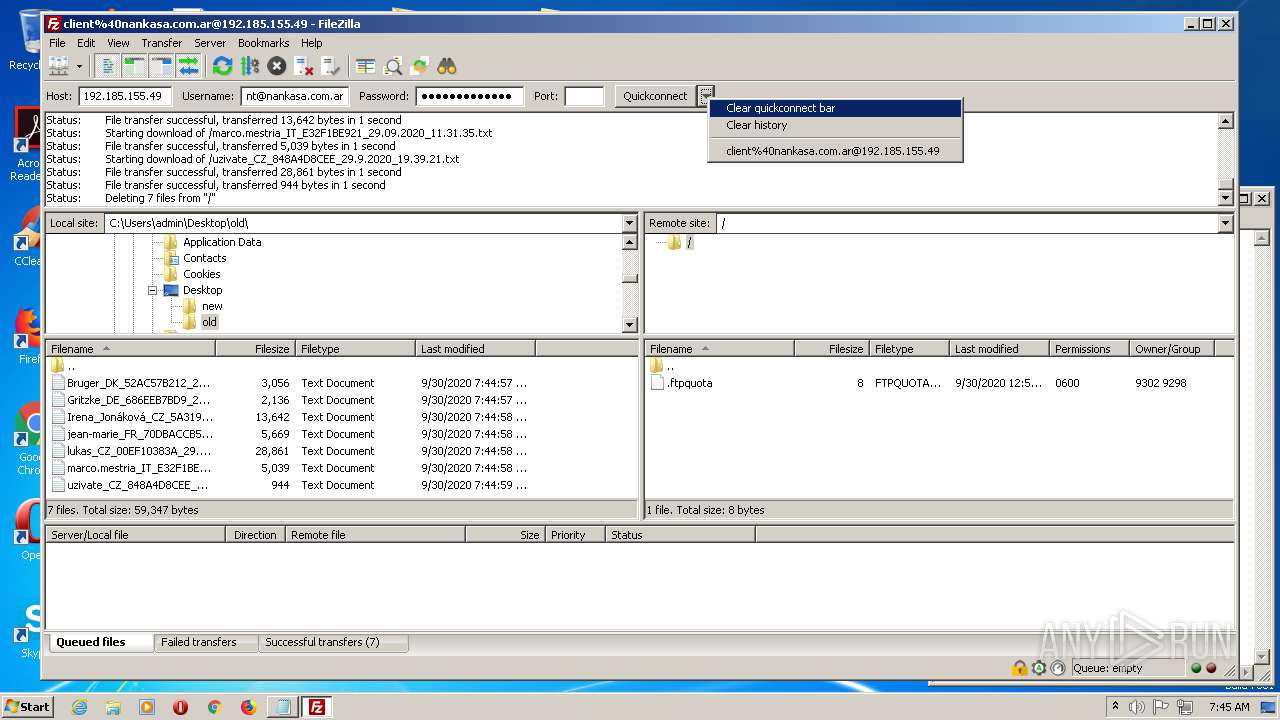
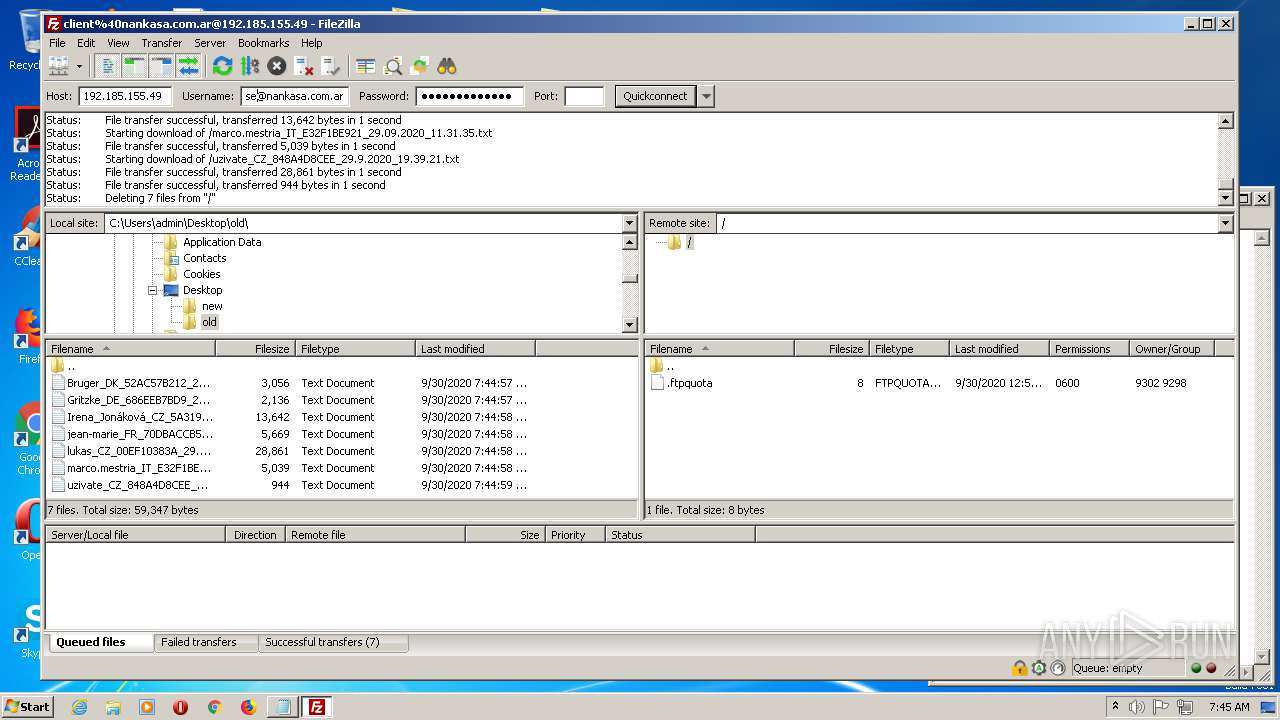
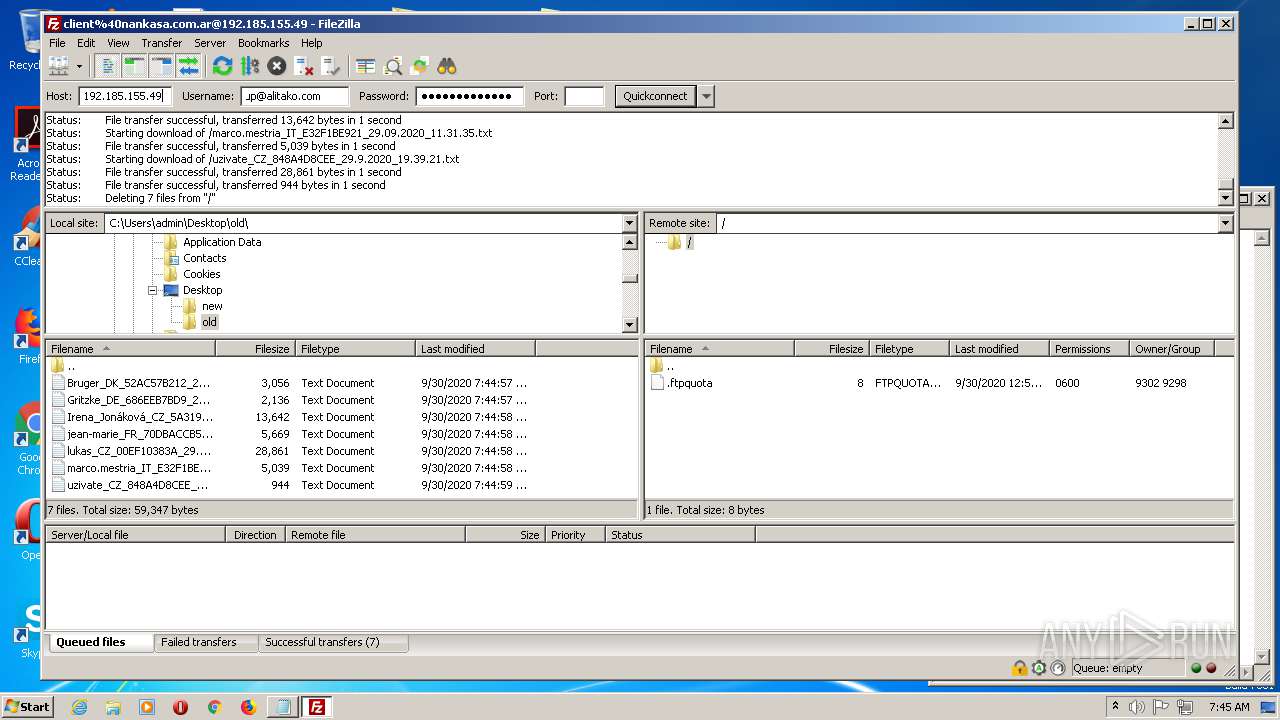
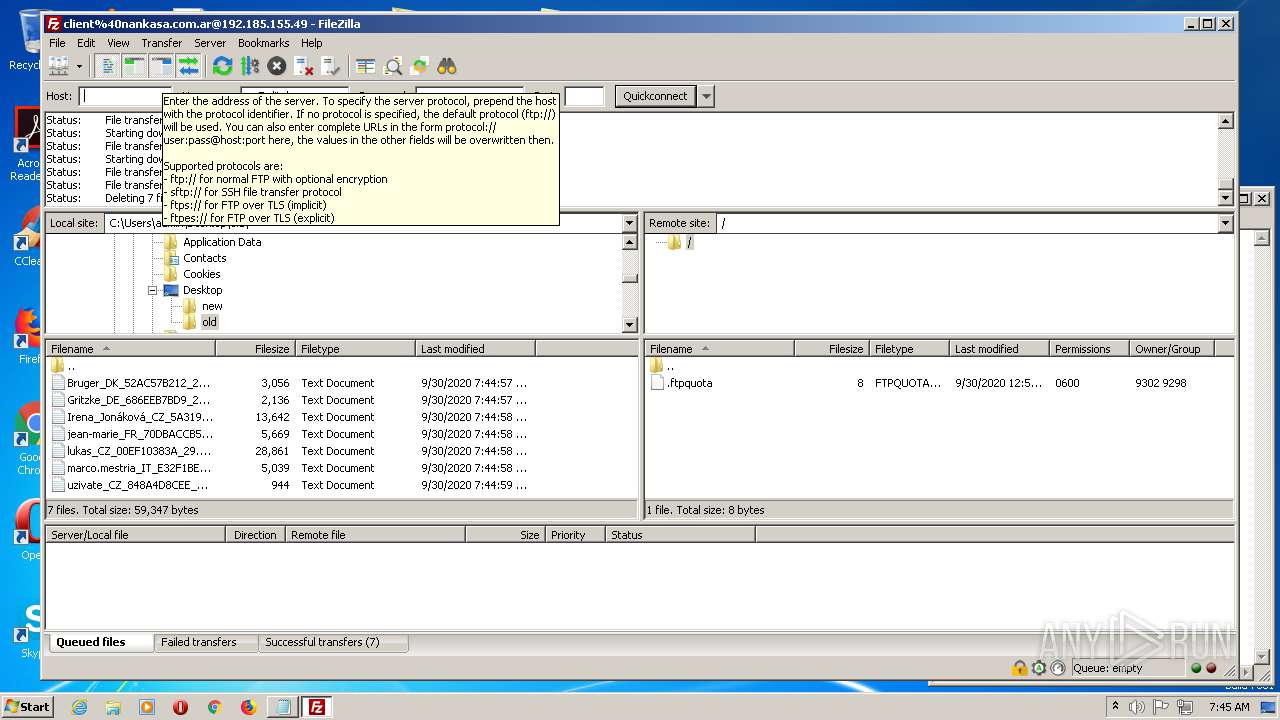
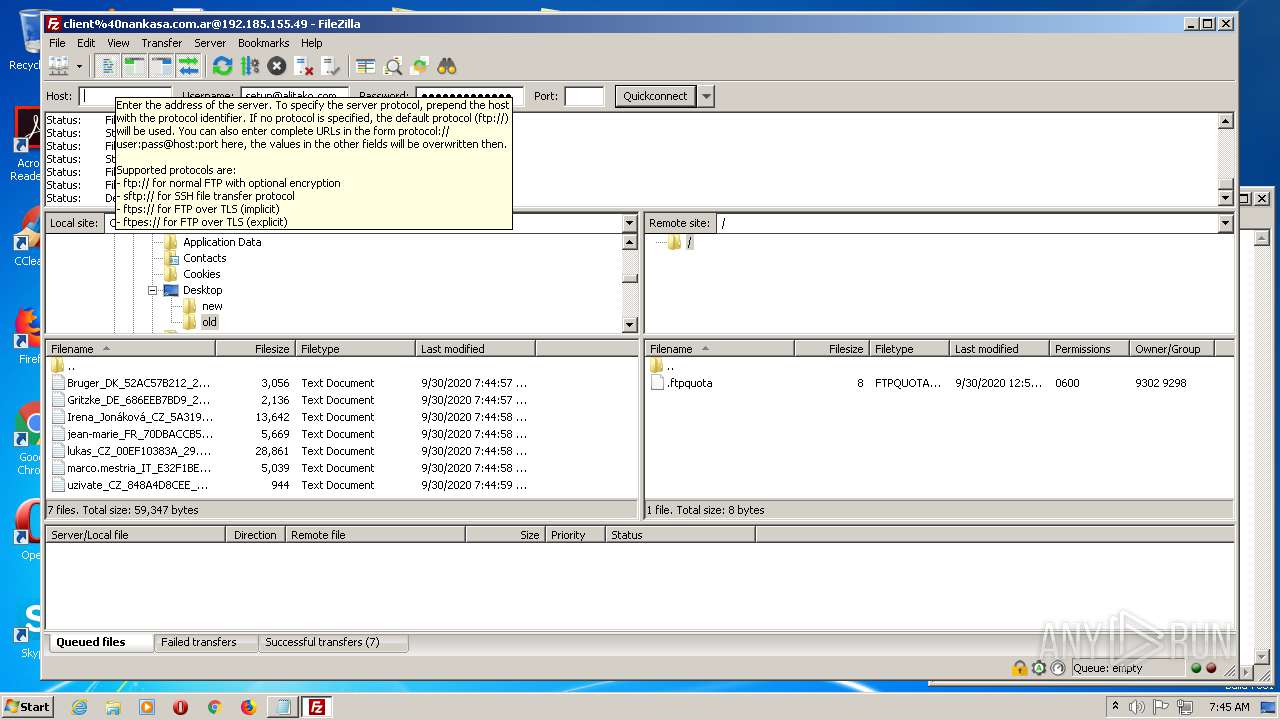
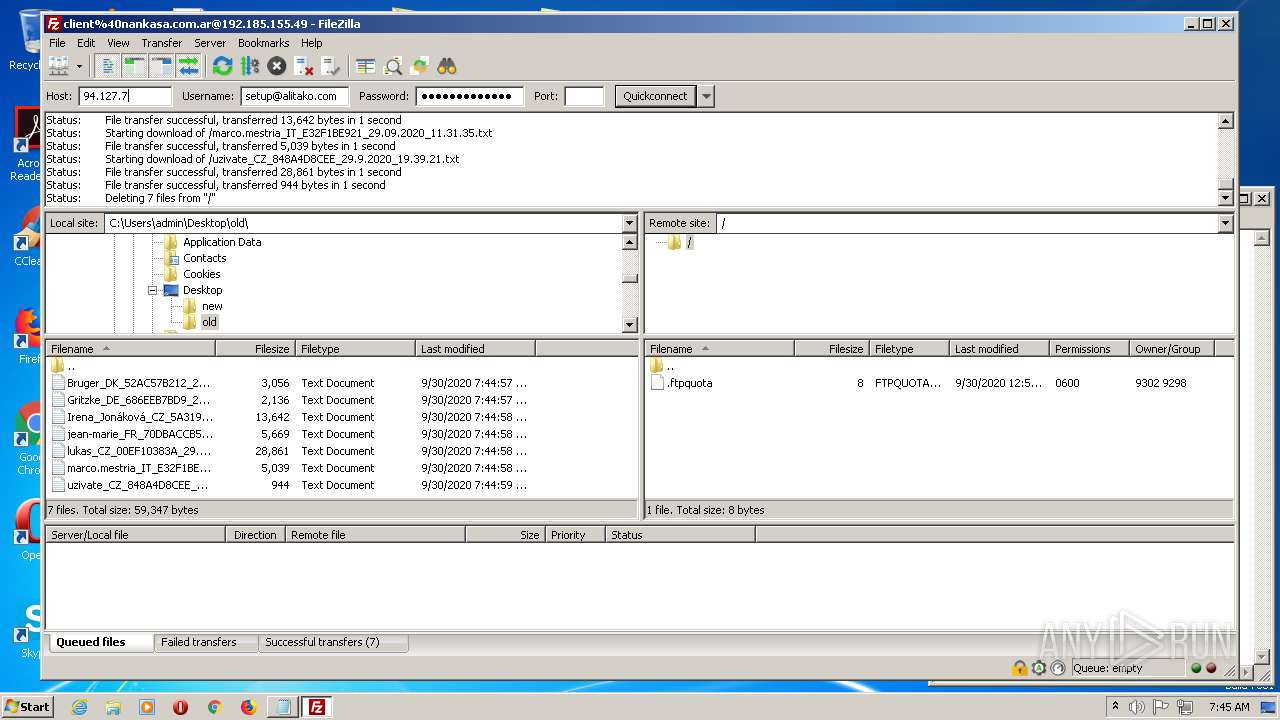
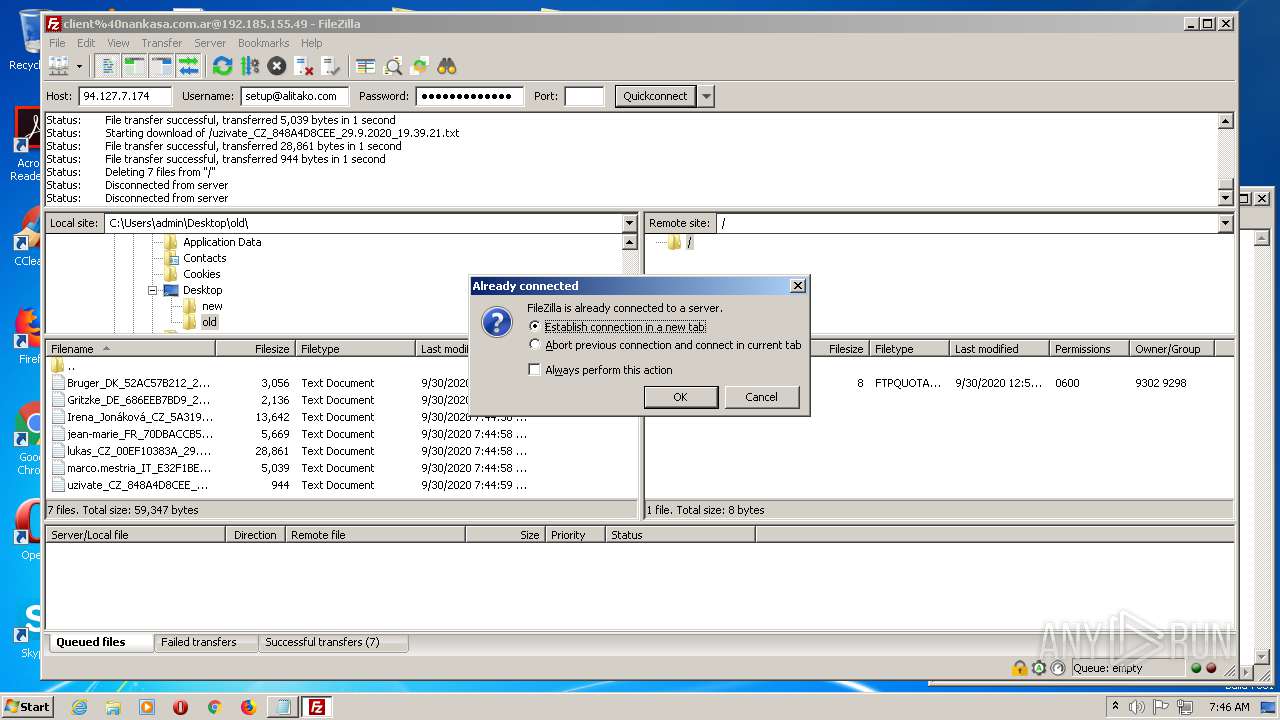
1884 | filezilla.exe | 192.185.155.49:21 | — | CyrusOne LLC | US | malicious |
1884 | filezilla.exe | 192.185.155.49:49890 | — | CyrusOne LLC | US | malicious |
1884 | filezilla.exe | 192.185.155.49:47566 | — | CyrusOne LLC | US | malicious |
1884 | filezilla.exe | 192.185.155.49:38758 | — | CyrusOne LLC | US | malicious |
1884 | filezilla.exe | 192.185.155.49:48452 | — | CyrusOne LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
offers.filezilla-project.org |
| whitelisted |
cloud.nitehe-nutete.com |
| whitelisted |
remote.nitehe-nutete.com |
| shared |
update.filezilla-project.org |
| whitelisted |