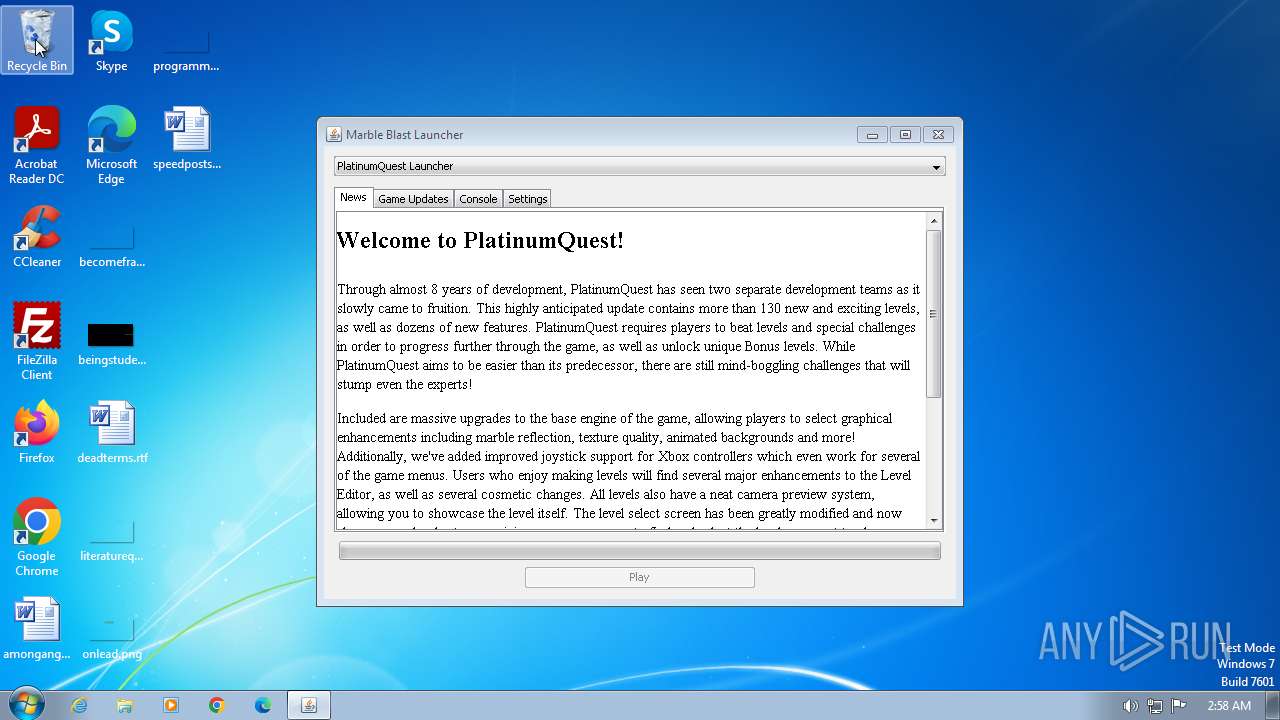
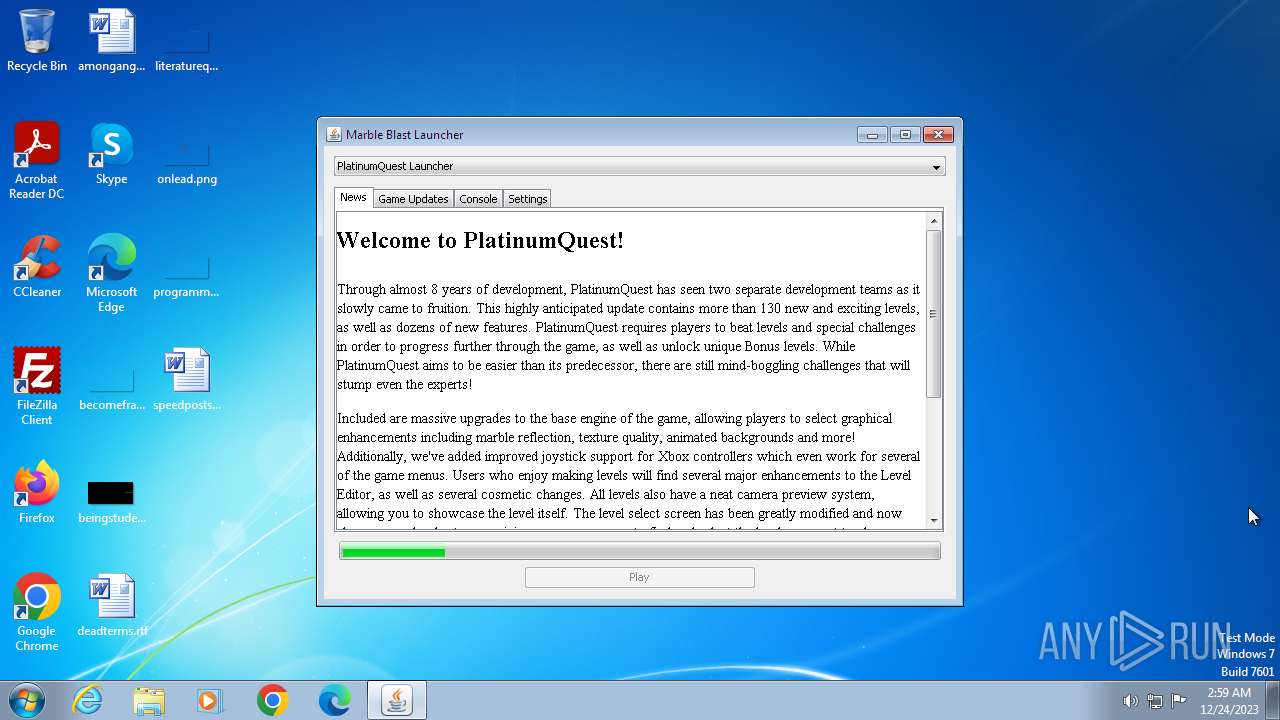
| download: | /kevinhosting/MBLauncher-Windows.jar |
| Full analysis: | https://app.any.run/tasks/4aa85de0-fd5f-4a65-a50a-f08a87998952 |
| Verdict: | Malicious activity |
| Analysis date: | December 24, 2023, 02:57:49 |
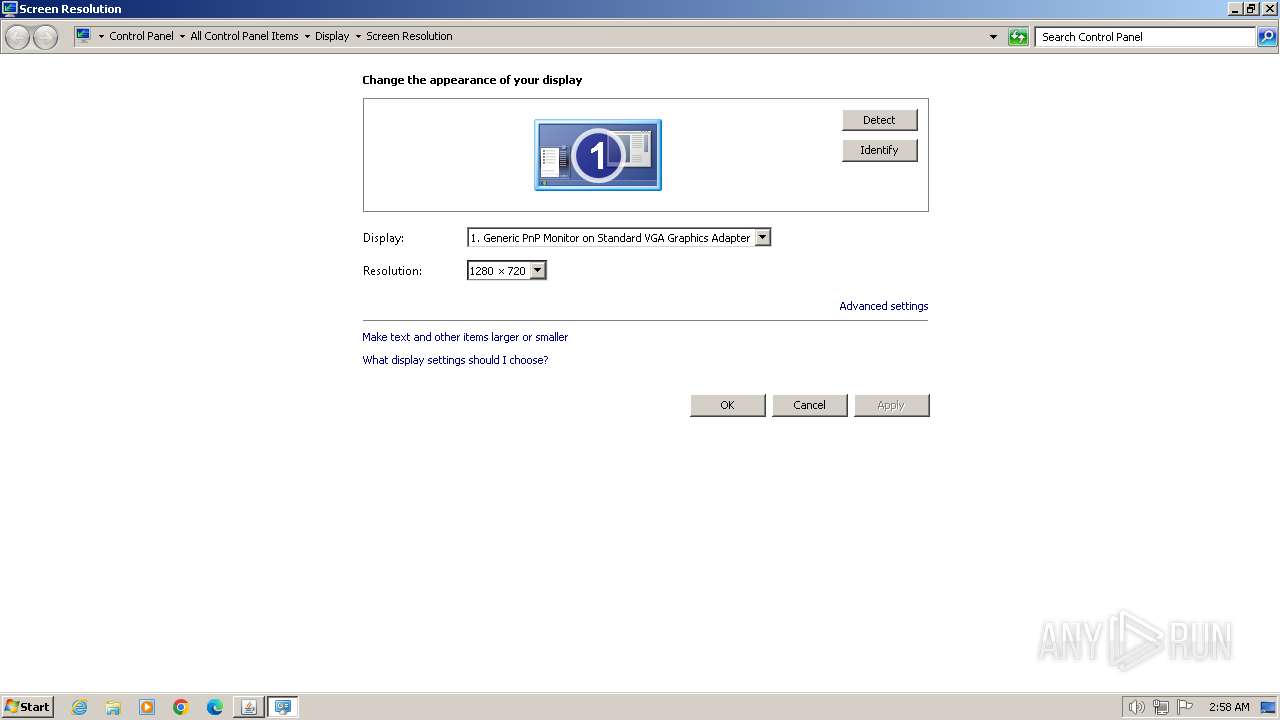
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows |
| MD5: | 0DEA918BD755D772D8CEBAA17605CAE3 |
| SHA1: | AC9241DCE3EB016085D862373581EF3D75FEFDFA |
| SHA256: | D309E9F702BA18D7F202101F89FDFF316C307C8A63542A6FAF41842166EFDB6B |
| SSDEEP: | 12288:22C4Vzs/C61PvSrcJOKJhJ4/mrSZu7hjPYMBo0/1Y:2b46/t6I0KJhJ4/mrSZyjPH60/1Y |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- MBLauncher-Windows.jar.exe (PID: 2040)
Process requests binary or script from the Internet
- javaw.exe (PID: 124)
INFO
Checks supported languages
- MBLauncher-Windows.jar.exe (PID: 2040)
- javaw.exe (PID: 124)
Reads the computer name
- javaw.exe (PID: 124)
Create files in a temporary directory
- javaw.exe (PID: 124)
Creates files in the program directory
- javaw.exe (PID: 124)
Manual execution by a user
- rundll32.exe (PID: 1892)
Drops the executable file immediately after the start
- MBLauncher-Windows.jar.exe (PID: 2040)
Reads the machine GUID from the registry
- javaw.exe (PID: 124)
Creates files or folders in the user directory
- javaw.exe (PID: 124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:06:19 08:47:56+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.22 |
| CodeSize: | 18432 |
| InitializedDataSize: | 49152 |
| UninitializedDataSize: | 36864 |
| EntryPoint: | 0x1290 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.1.0.0 |
| ProductVersionNumber: | 1.1.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Windows NT |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | The Platinum Team |
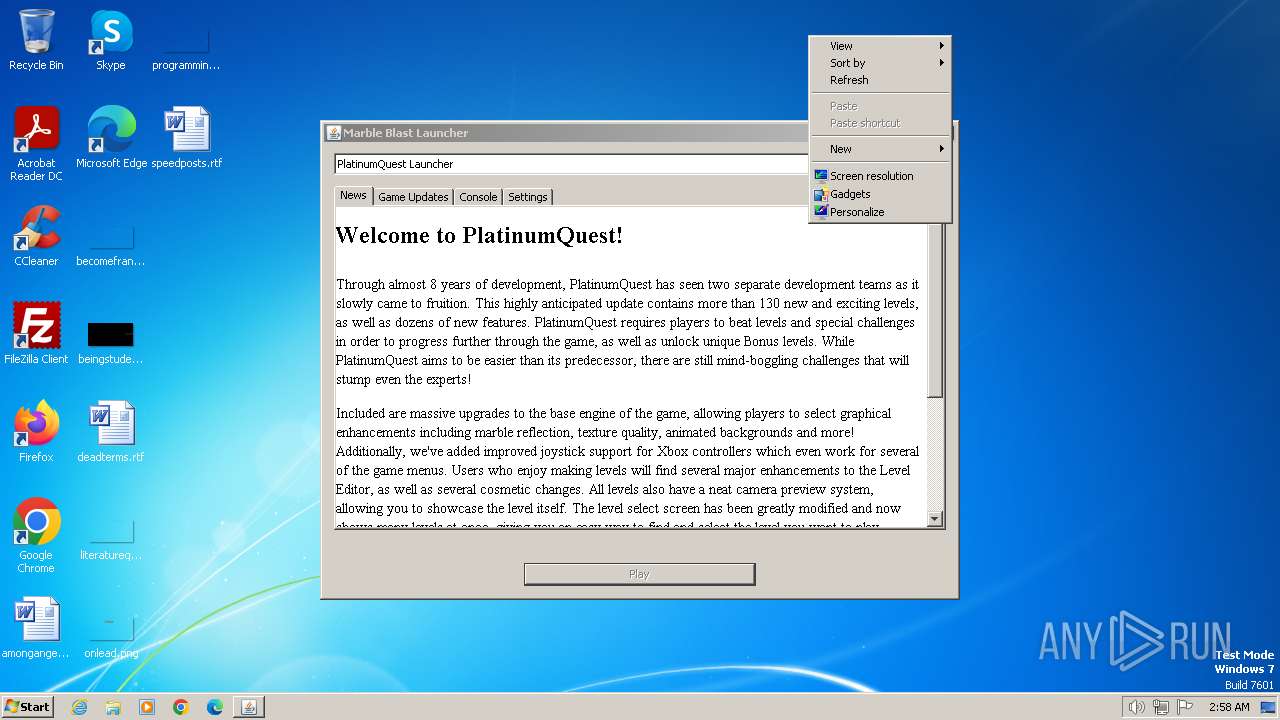
| FileDescription: | Marble Blast Launcher |
| FileVersion: | 1.1.0 |
| InternalName: | mbplauncher |
| LegalCopyright: | 2015 The Platinum Team, All Rights Reserved |
| OriginalFileName: | Marble Blast Launcher.exe |
| ProductName: | Marble Blast Launcher |
| ProductVersion: | 1.1.0 |
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -jar "C:\Users\admin\AppData\Roaming\MBLauncher-Windows.jar.exe" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | MBLauncher-Windows.jar.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 864 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1892 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,Control_RunDLL C:\Windows\System32\main.cpl ,1 | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
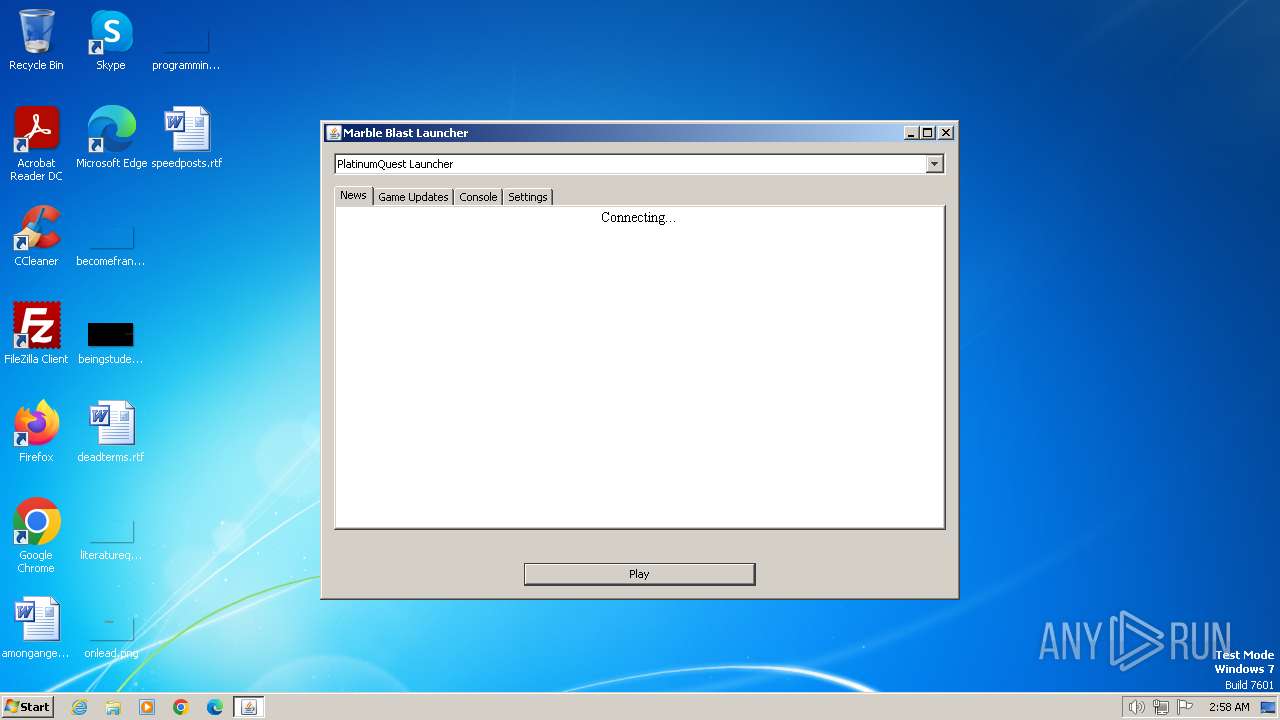
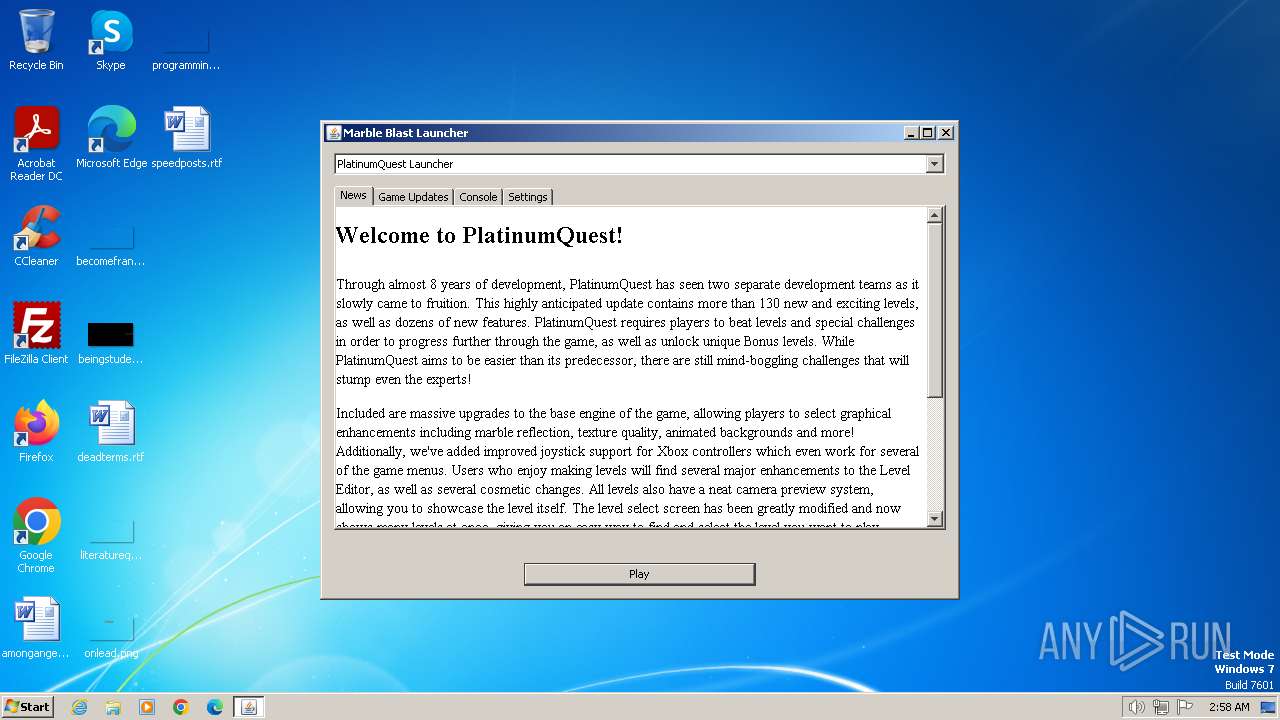
| 2040 | "C:\Users\admin\AppData\Roaming\MBLauncher-Windows.jar.exe" | C:\Users\admin\AppData\Roaming\MBLauncher-Windows.jar.exe | — | explorer.exe | |||||||||||
User: admin Company: The Platinum Team Integrity Level: MEDIUM Description: Marble Blast Launcher Exit code: 0 Version: 1.1.0 Modules
| |||||||||||||||
Total events
947
Read events
930
Write events
17
Delete events
0
Modification events
| (PID) Process: | (124) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\Prefs |
| Operation: | write | Name: | mods |
Value: pq | |||
| (PID) Process: | (124) javaw.exe | Key: | HKEY_CURRENT_USER\Software\JavaSoft\Prefs |
| Operation: | write | Name: | mod/Paths |
Value: http:\\pq.marbleblast.com\config\config.json | |||
| (PID) Process: | (124) javaw.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1892) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1892) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes |
| Operation: | write | Name: | ThemeChangesMousePointers |
Value: 1 | |||
| (PID) Process: | (1892) rundll32.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | Scheme Source |
Value: 2 | |||
Executable files
0
Suspicious files
311
Text files
274
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\.mblaunchercache\fubar\config.json | binary | |
MD5:630014F74A714DE0B02CC2EF5D401816 | SHA256:84680C00D938F6FFE23672984D125C4C5147F078E0E5F2111E4D34722089C412 | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\.mblaunchercache\pq\config.json | binary | |
MD5:E2F74C0A54FB6AE380784A57D94FB1A5 | SHA256:30C5FE189CD8F93A5AFAF25132766BE6E364F638BF1CD69F04C216AD8619E2EB | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\shapes_mbxp.zip | compressed | |
MD5:FCF7ABBEB140427CAAFDED3F3D24B5DA | SHA256:EC4B54E780581AA89D6EC8046A51D5FBD6065BFAF95D1E70947690F14BA83F42 | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\platinum\data\shapes_mbxp\empty.dts | ddi | |
MD5:ED8ED5FCAF0601235F947D23CBAC6034 | SHA256:5035A0FBE209AE97E038E93FD02D3B286BD780215E555F356DE87404888533B9 | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\platinum\data\shapes_mbxp\bumpers\bumper_glowplane2.png | image | |
MD5:0BCC1709875619AFC9134C86492318F7 | SHA256:BA4FBA0998B353255925C36F55968EC4B0024691B3BE1C3E1A7120F093BF6B2D | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\platinum\data\shapes_mbxp\bumpers\inside_ifl.ifl | text | |
MD5:B380C2CCAE2A74C543122C1AE2773FE7 | SHA256:B67B608DF2D685823059662D8F7E2A25EA44E061DB49DB37842D15A7811240BF | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\platinum\data\shapes_mbxp\bumpers\glowplane_ifl.ifl | text | |
MD5:45E3FE85D9F20DBA010844CE1F2BB5FE | SHA256:5A48B53CB7B43A5FD160D1103CA2355BD54E0AB3B4AC7E1D9D8D653E60398D61 | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\platinum\data\shapes_mbxp\bumpers\bumper_glowplane.png | image | |
MD5:54420337F3CAD20E398B11C24B9B9E29 | SHA256:DB222CB80BFFD8D579EFD75968DB5B7D4B6432228F2DC0A12CA2CE952A0BB7DF | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\.mblaunchercache\pq\packages-win.json | binary | |
MD5:1B4615B8B0E0CFD2CD59007DFF938755 | SHA256:1878EEF5E5FEFD5820FD88B2376726A22EA9C12D75D33E67B190274E64470C82 | |||
| 124 | javaw.exe | C:\Users\admin\AppData\Roaming\PlatinumQuest\platinum\data\shapes_mbxp\bumpers\kpost.jpg | image | |
MD5:0B847CD3F55C7E9B003E0893E72675CB | SHA256:42ED5D6674329897A03C183D76D0F931E8B632742B00C633257748C28A155817 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
4
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
124 | javaw.exe | GET | 200 | 168.235.75.191:80 | http://pq.marbleblast.com/config/config.json | unknown | binary | 3.03 Kb | unknown |
124 | javaw.exe | GET | 200 | 168.235.75.191:80 | http://files.marbleblast.com/launcher/config.json | unknown | binary | 798 b | unknown |
124 | javaw.exe | GET | 200 | 168.235.75.191:80 | http://pq.marbleblast.com/config/config.json | unknown | binary | 3.03 Kb | unknown |
124 | javaw.exe | GET | 200 | 168.235.75.191:80 | http://fubar.marbleblast.com/config/config.json | unknown | binary | 2.40 Kb | unknown |
124 | javaw.exe | GET | 200 | 168.235.75.191:80 | http://fubar.marbleblast.com/config/config.json | unknown | binary | 2.40 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
124 | javaw.exe | 168.235.75.191:80 | files.marbleblast.com | RAMNODE | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
124 | javaw.exe | 188.114.96.3:80 | marbleblast.com | CLOUDFLARENET | NL | unknown |
124 | javaw.exe | 188.114.96.3:443 | marbleblast.com | CLOUDFLARENET | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
files.marbleblast.com |
| unknown |
marbleblast.com |
| malicious |
pq.marbleblast.com |
| unknown |
fubar.marbleblast.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
124 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
124 | javaw.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
5 ETPRO signatures available at the full report