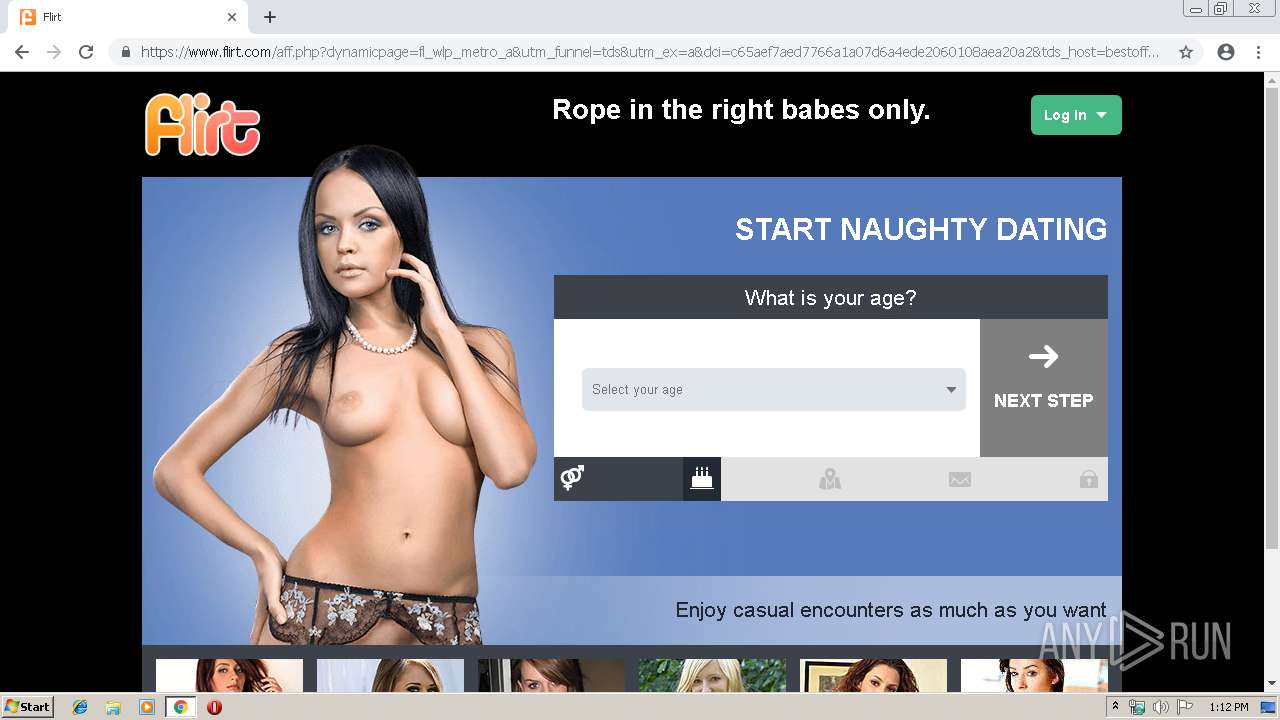
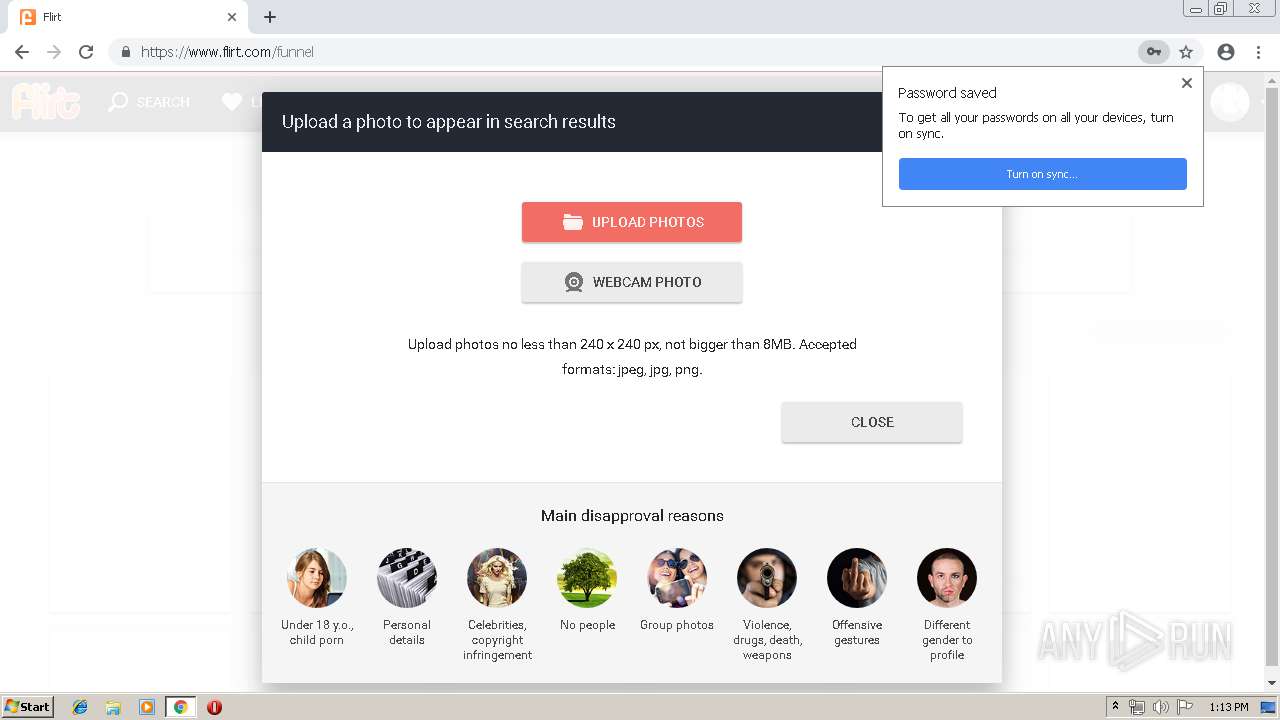
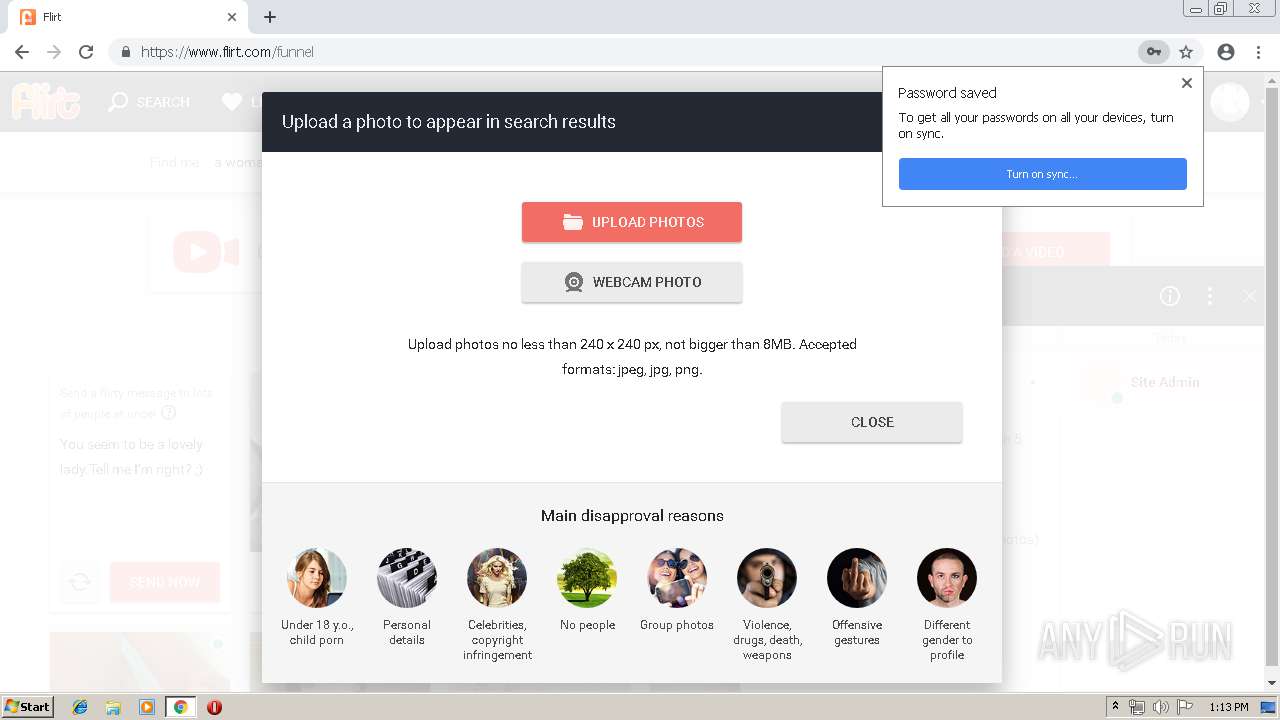
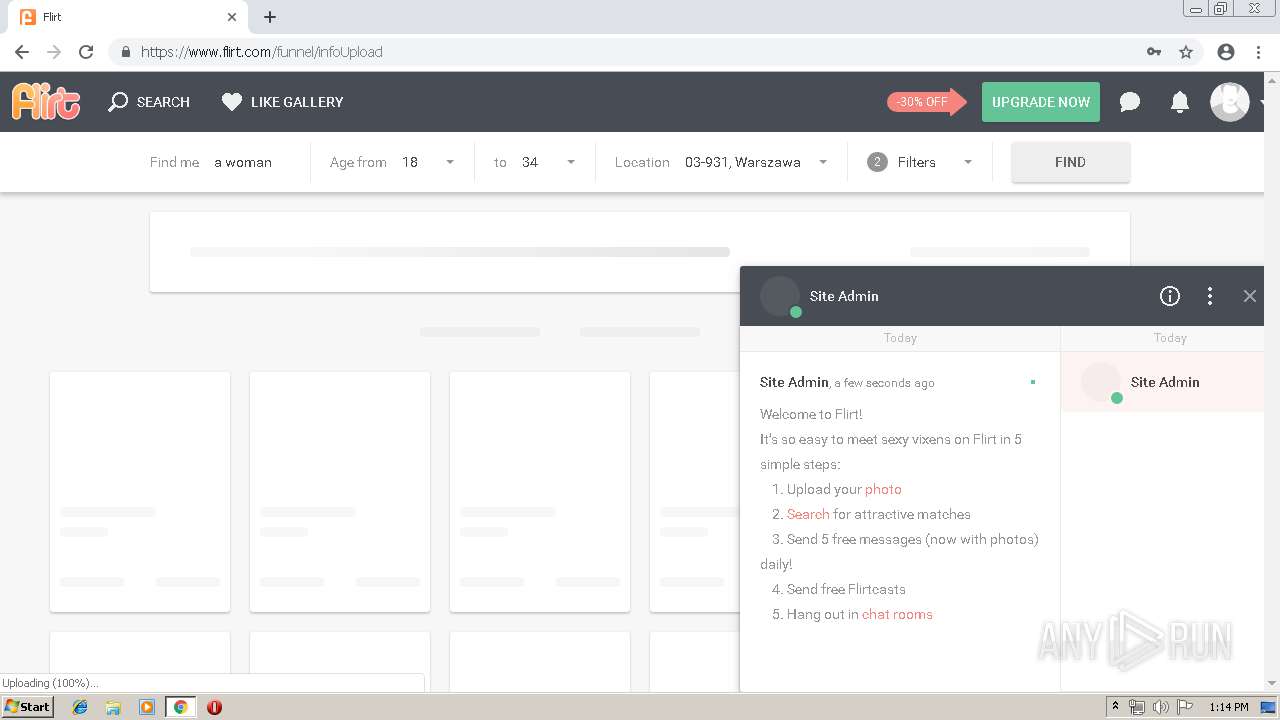
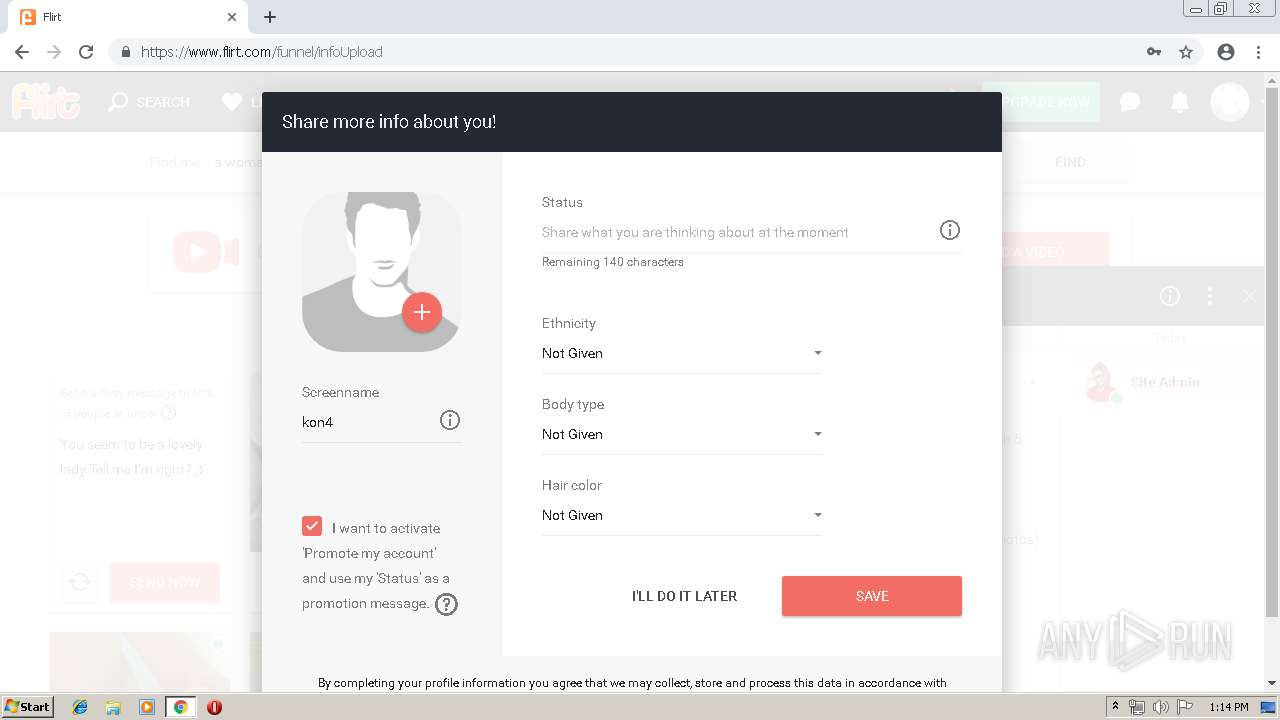
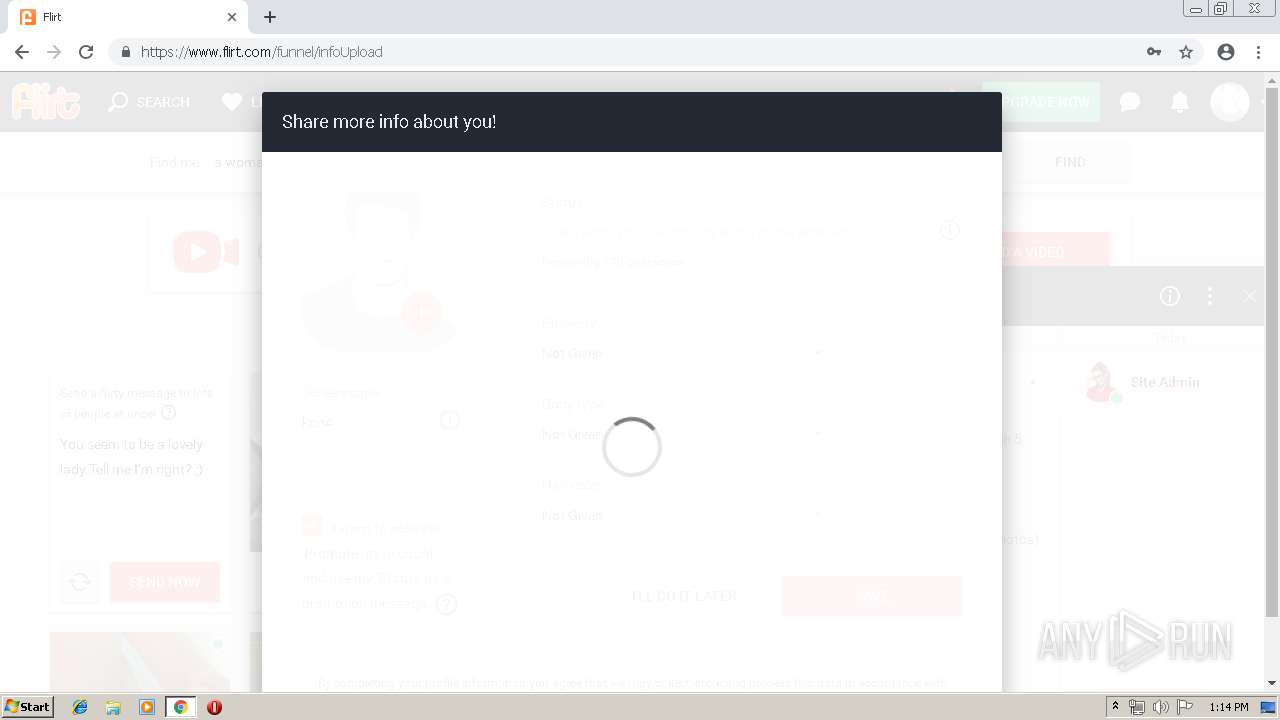
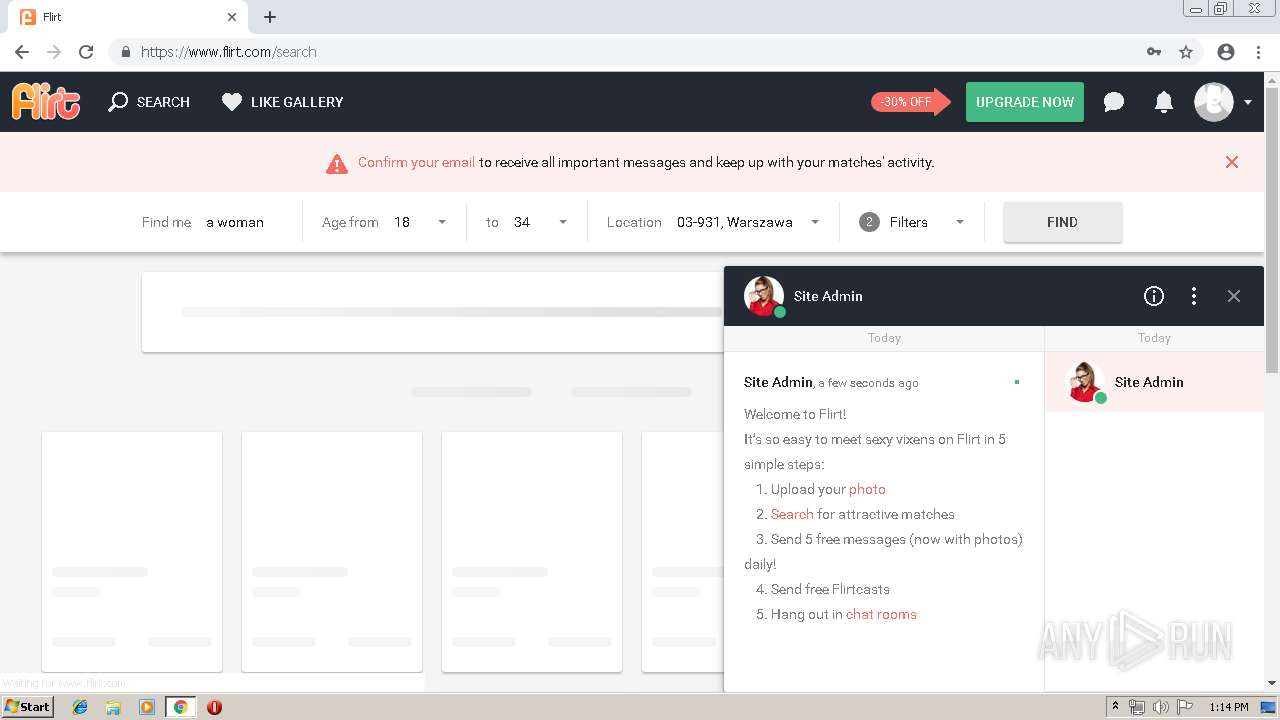
analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| URL: | http://rt-df.info/iiigle/ |
| Full analysis: | https://app.any.run/tasks/ad6ca1c8-663b-4303-a291-d20e02decc1f |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 12:11:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8345B1E8D98010EAB6DDA92E45482942 |
| SHA1: | 865E4E951CEBE2F3563CAEA60FF49CB079D7A998 |
| SHA256: | D3083B74880EE78B496C3CF7C99A03792184A7F94AE001228990A8E5565B84C3 |
| SSDEEP: | 3:N1KMs43hn:CMs4R |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2844)
INFO
Application launched itself
- chrome.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
56
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 2844 | "C:\Program Files\Google\Chrome\Application\chrome.exe" http://rt-df.info/iiigle/ | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Version: 73.0.3683.75 | ||||
| 3468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=73.0.3683.75 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6ebb0f18,0x6ebb0f28,0x6ebb0f34 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Version: 73.0.3683.75 | ||||
| 2600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2848 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Version: 73.0.3683.75 | ||||
| 3828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwAAAQAAAAAAAAAAAGAAAAAAAAEAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=14520903678509141690 --mojo-platform-channel-handle=944 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Version: 73.0.3683.75 | ||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=3131710883701112424 --mojo-platform-channel-handle=1504 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | |
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Version: 73.0.3683.75 | ||||
| 2648 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --service-pipe-token=7836858018030009965 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7836858018030009965 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2044 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 3084 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --service-pipe-token=9373194872295876974 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9373194872295876974 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2068 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 3388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --service-pipe-token=8839171925368150895 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8839171925368150895 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2176 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 2360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6834753143685740870 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6834753143685740870 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3052 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
| 3888 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,8145731737619825880,15429340508233278846,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=10561185956347705369 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10561185956347705369 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2112 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe |
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 | ||||
Total events
610
Read events
499
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
117
Text files
201
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\43c684f1-27af-400b-9771-1b5738c87902.tmp | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 2844 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
77
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
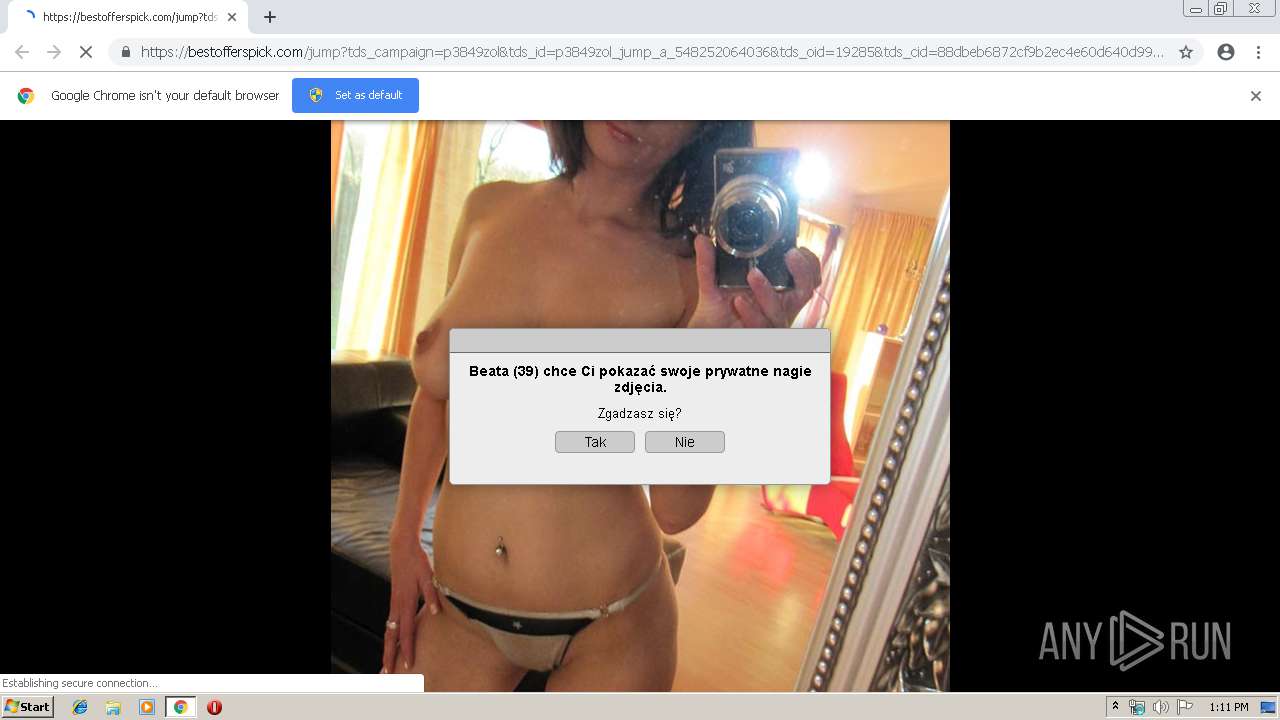
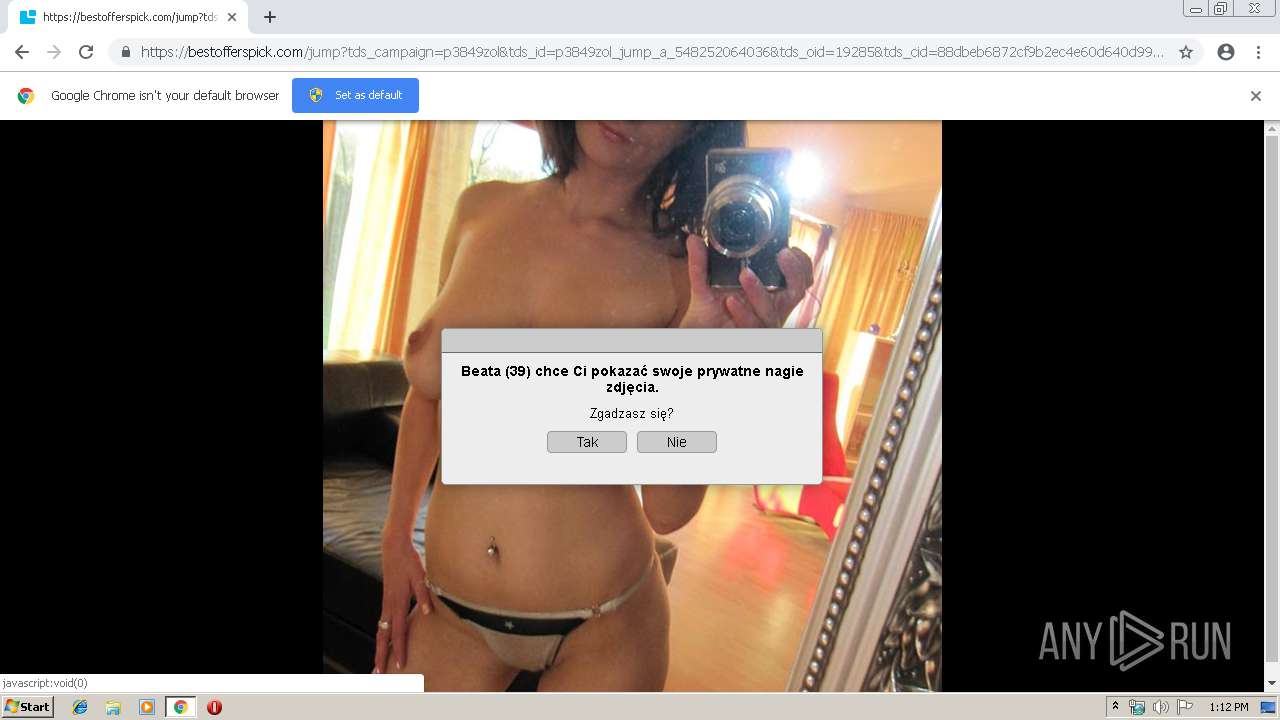
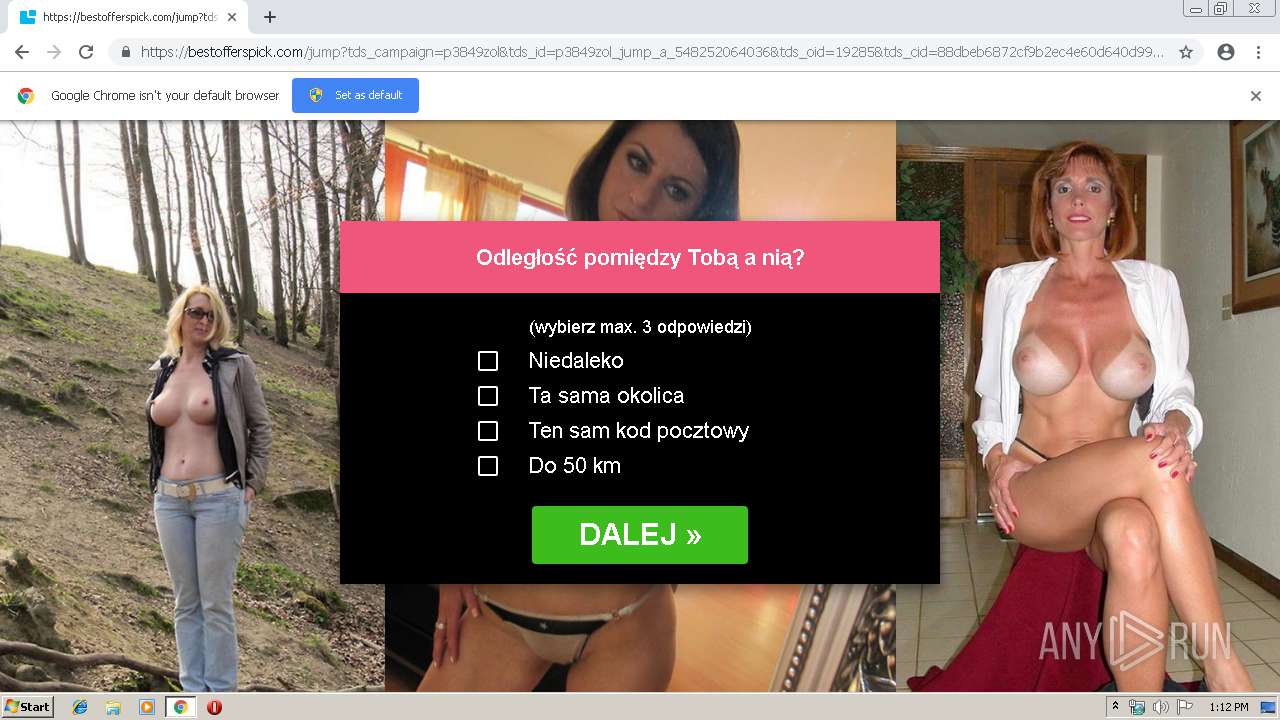
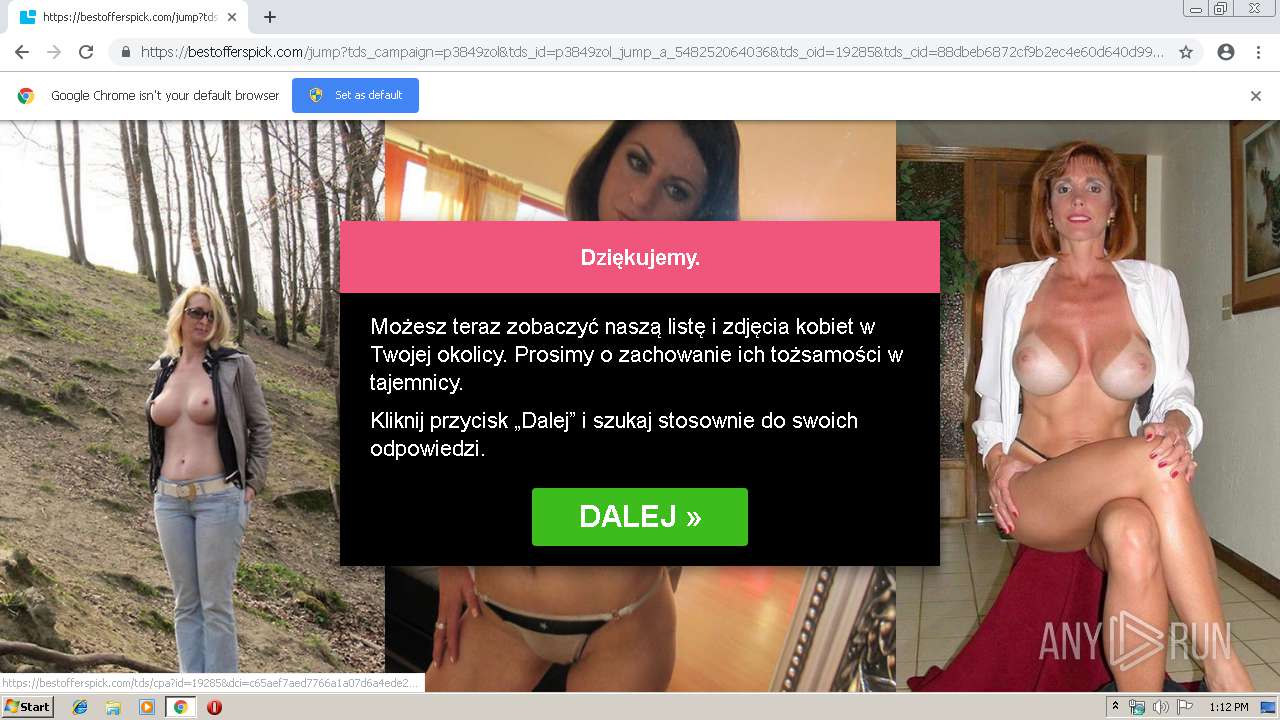
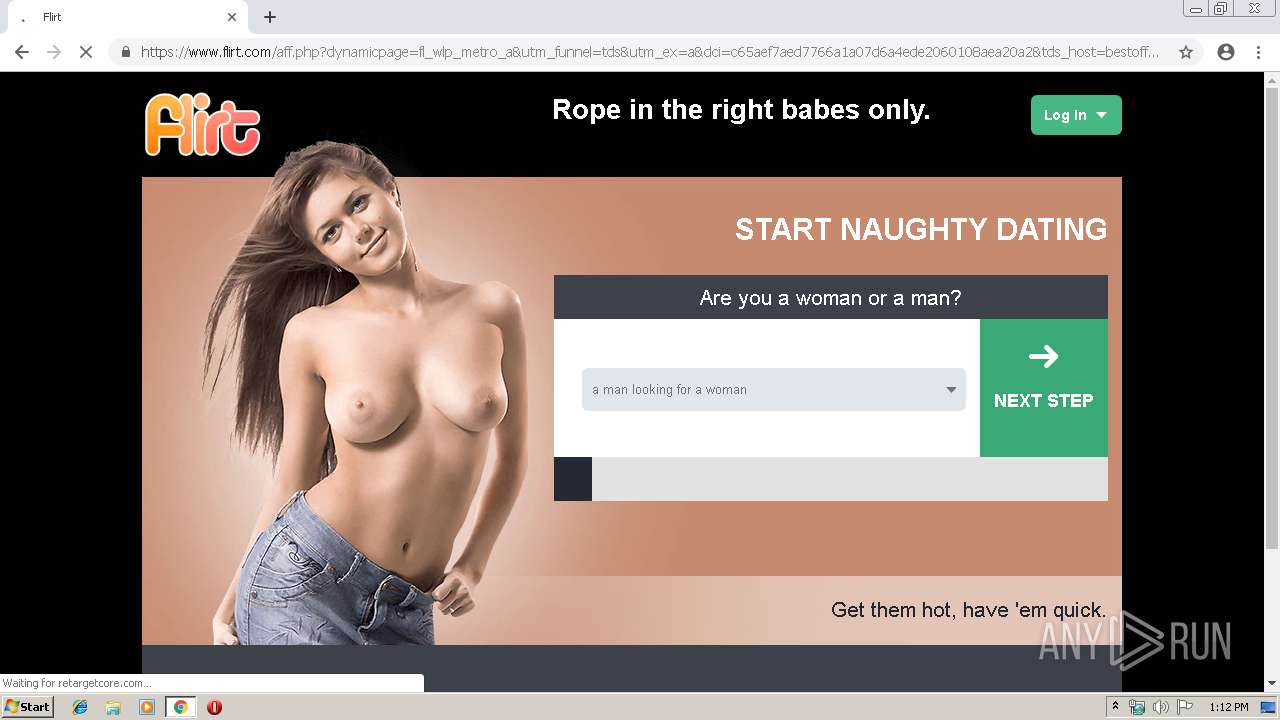
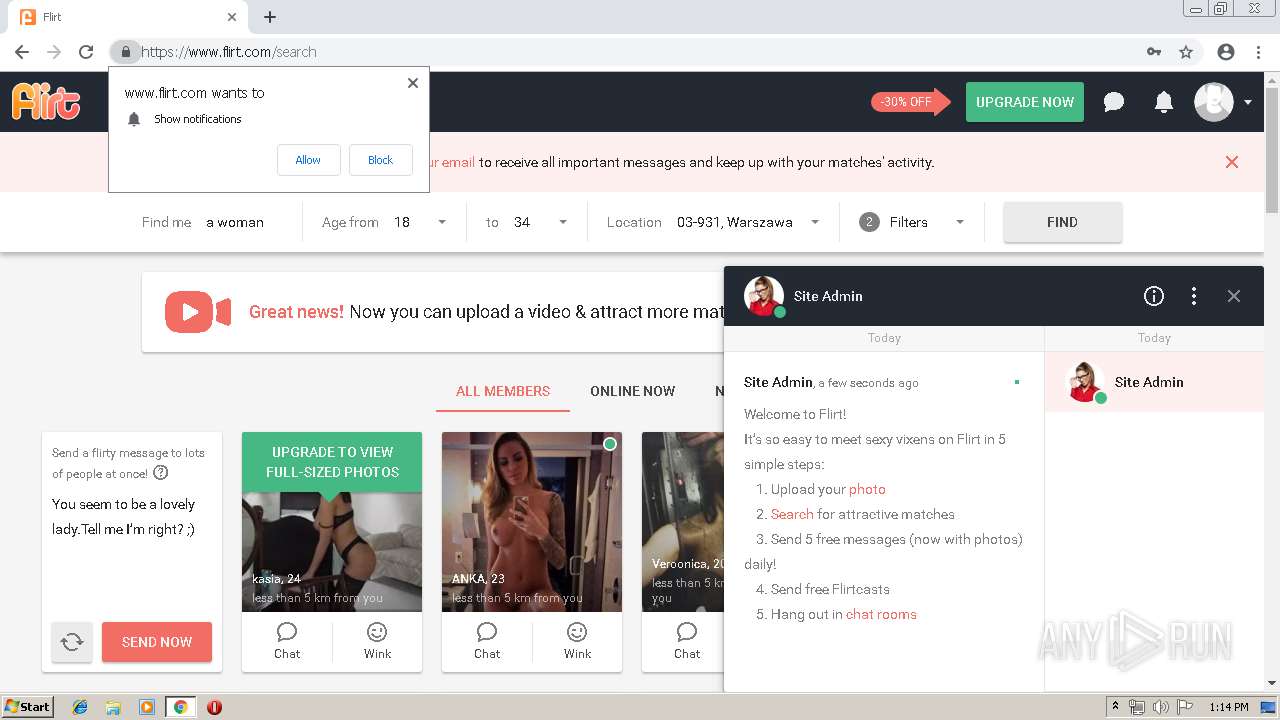
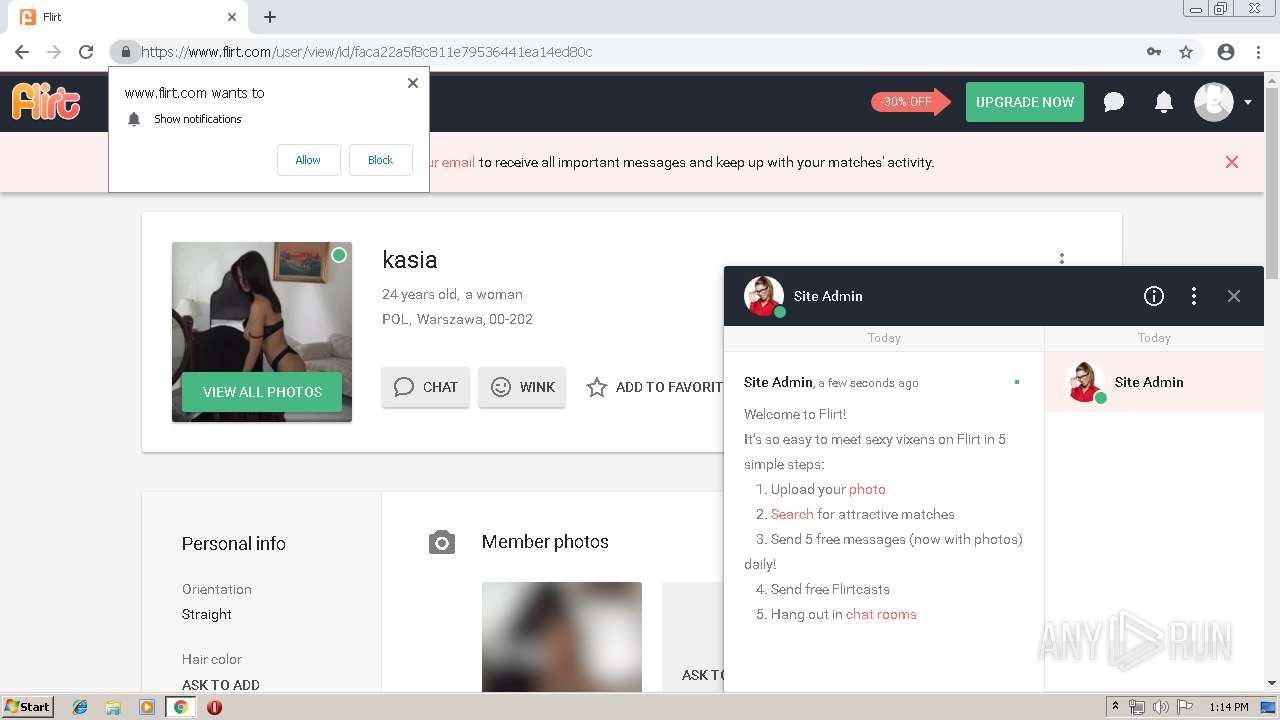
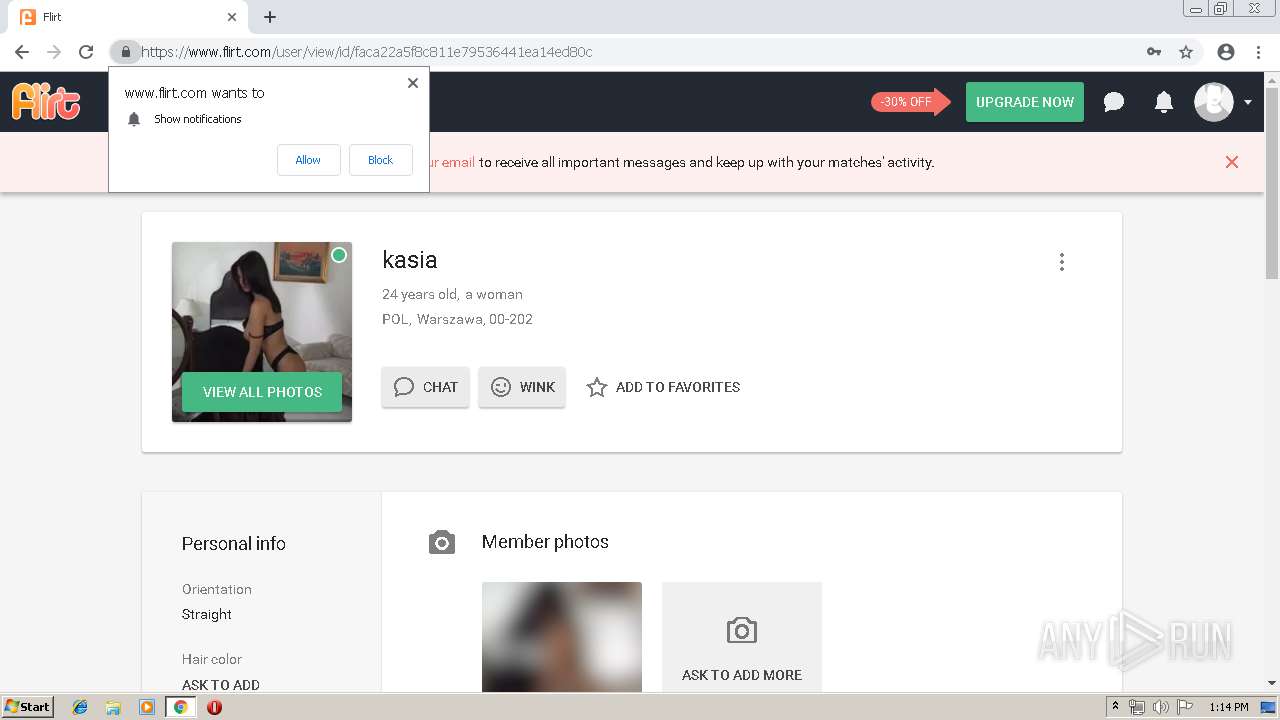
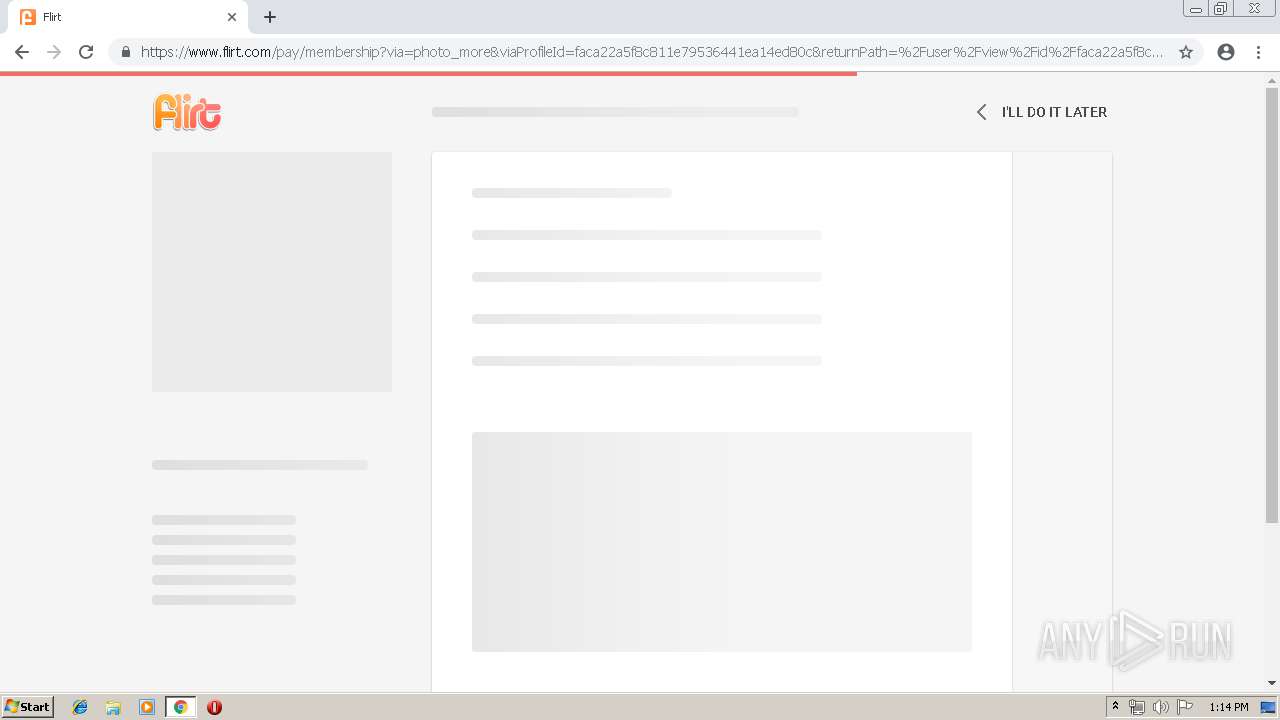
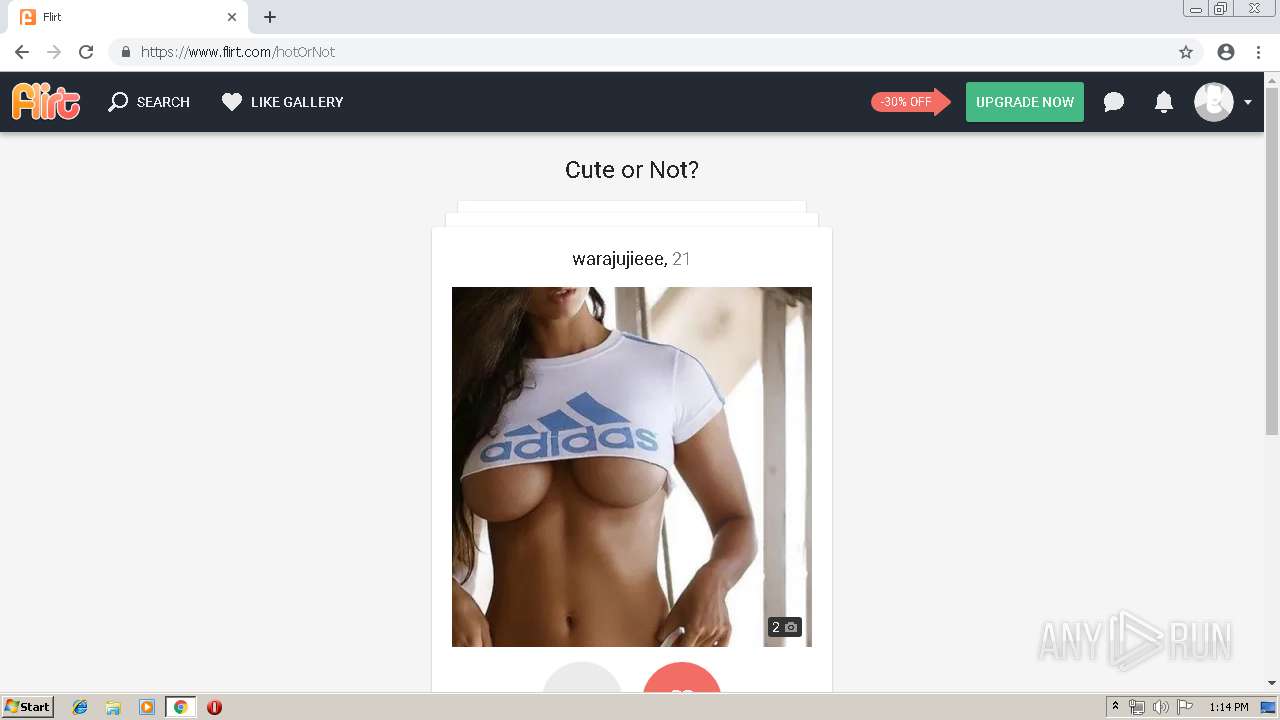
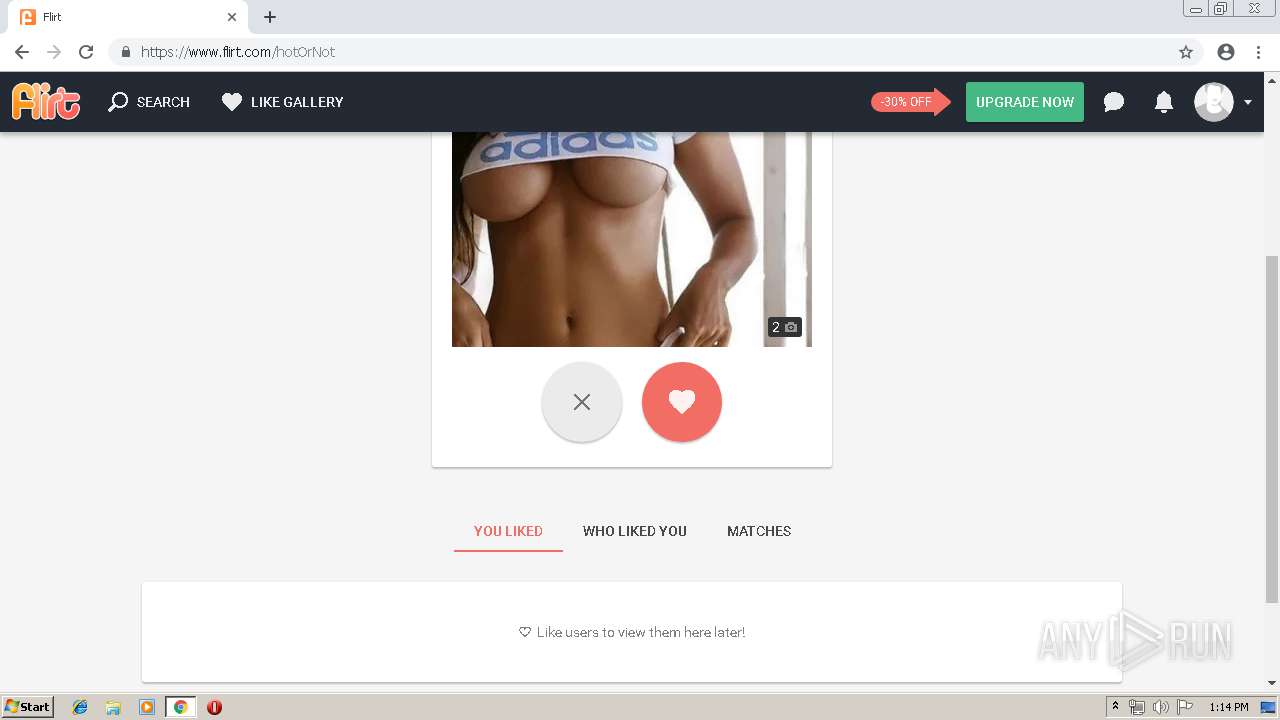
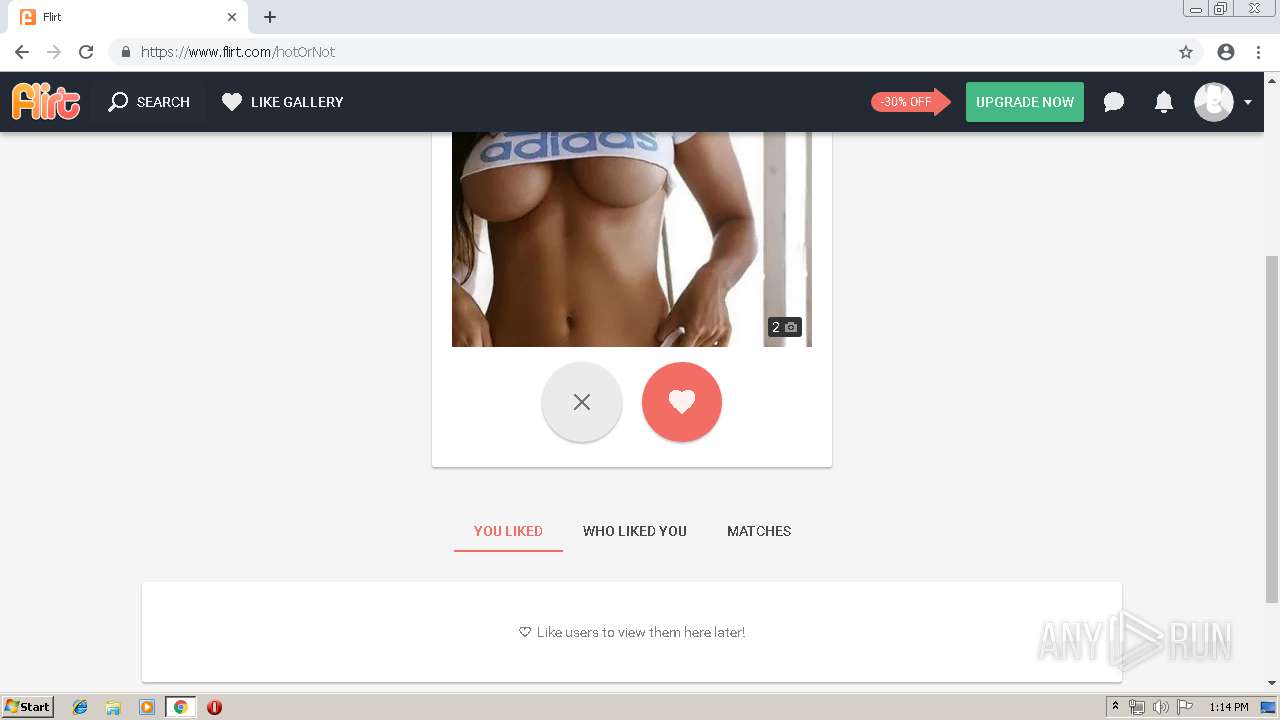
2188 | chrome.exe | GET | 302 | 92.63.197.83:80 | http://rt-df.info/iiigle/ | RU | html | 212 b | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/post-photo.jpg | RU | image | 52.6 Kb | unknown |
2188 | chrome.exe | GET | 302 | 213.252.246.43:80 | http://er-er.info/track/dat/source/campaign-ads | LT | — | — | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/avatar.png | RU | image | 21.0 Kb | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/photo-1.jpg | RU | image | 10.2 Kb | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/index.css | RU | text | 2.45 Kb | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/about.jpg | RU | image | 19.1 Kb | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/index.html | RU | html | 3.40 Kb | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/photo-3.jpg | RU | image | 11.4 Kb | unknown |
2188 | chrome.exe | GET | 200 | 92.63.197.83:80 | http://rt-df.info/screen.jpg | RU | image | 45.1 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2188 | chrome.exe | 92.63.197.83:80 | rt-df.info | — | RU | unknown |
2188 | chrome.exe | 93.184.221.240:80 | www.download.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2188 | chrome.exe | 216.58.206.14:443 | clients2.google.com | Google Inc. | US | whitelisted |
2188 | chrome.exe | 172.217.18.110:80 | redirector.gvt1.com | Google Inc. | US | whitelisted |
2188 | chrome.exe | 213.252.246.43:80 | er-er.info | Informacines sistemos ir technologijos, UAB | LT | unknown |
2188 | chrome.exe | 172.217.22.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2188 | chrome.exe | 52.58.198.163:443 | bestofferspick.com | Amazon.com, Inc. | DE | unknown |
2188 | chrome.exe | 52.222.168.85:80 | x.ss2.us | Amazon.com, Inc. | US | suspicious |
2188 | chrome.exe | 172.217.18.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2188 | chrome.exe | 172.217.16.141:443 | accounts.google.com | Google Inc. | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
rt-df.info |
| unknown |
accounts.google.com |
| shared |
er-er.info |
| unknown |
bestofferspick.com |
| unknown |
x.ss2.us |
| whitelisted |
www.download.windowsupdate.com |
| whitelisted |
clients2.google.com |
| whitelisted |
www.cdnreference.com |
| shared |
redirector.gvt1.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2188 | chrome.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2188 | chrome.exe | Attempted User Privilege Gain | ET INFO Session Traversal Utilities for NAT (STUN Binding Request) |