| URL: | https://dl.ubnt.com/aircontrol2/aircontrol-v2.1-GA3-180228-1639-win32.exe |
| Full analysis: | https://app.any.run/tasks/ec8d10fc-acbd-41e6-aca5-4abca5008599 |
| Verdict: | Malicious activity |
| Analysis date: | February 23, 2024, 12:19:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A4F17C33BC722480E26332A98F9201B4 |
| SHA1: | 1E377EA487D47255C922E983351AEECC24DF9087 |
| SHA256: | D2FF40AB489CF1DD877CF5ED611372E2AAE40F04EFE4D43C528041264C8419A8 |
| SSDEEP: | 3:N8RmGkTOkWpXXXP/MLQkAn:2sWZcLQkA |
MALICIOUS
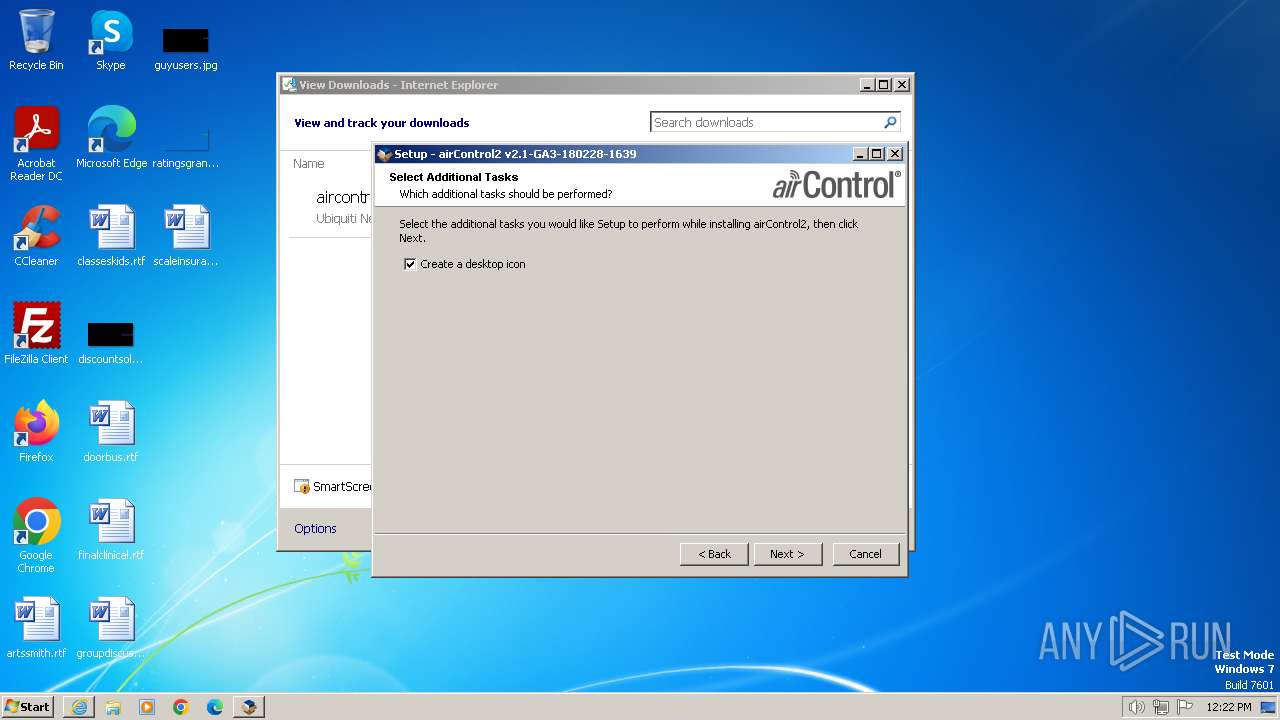
Drops the executable file immediately after the start
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
Gets information about running processes via WMI (SCRIPT)
- cscript.exe (PID: 2032)
SUSPICIOUS
Process drops legitimate windows executable
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
Executable content was dropped or overwritten
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
The process drops C-runtime libraries
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
Reads the Internet Settings
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
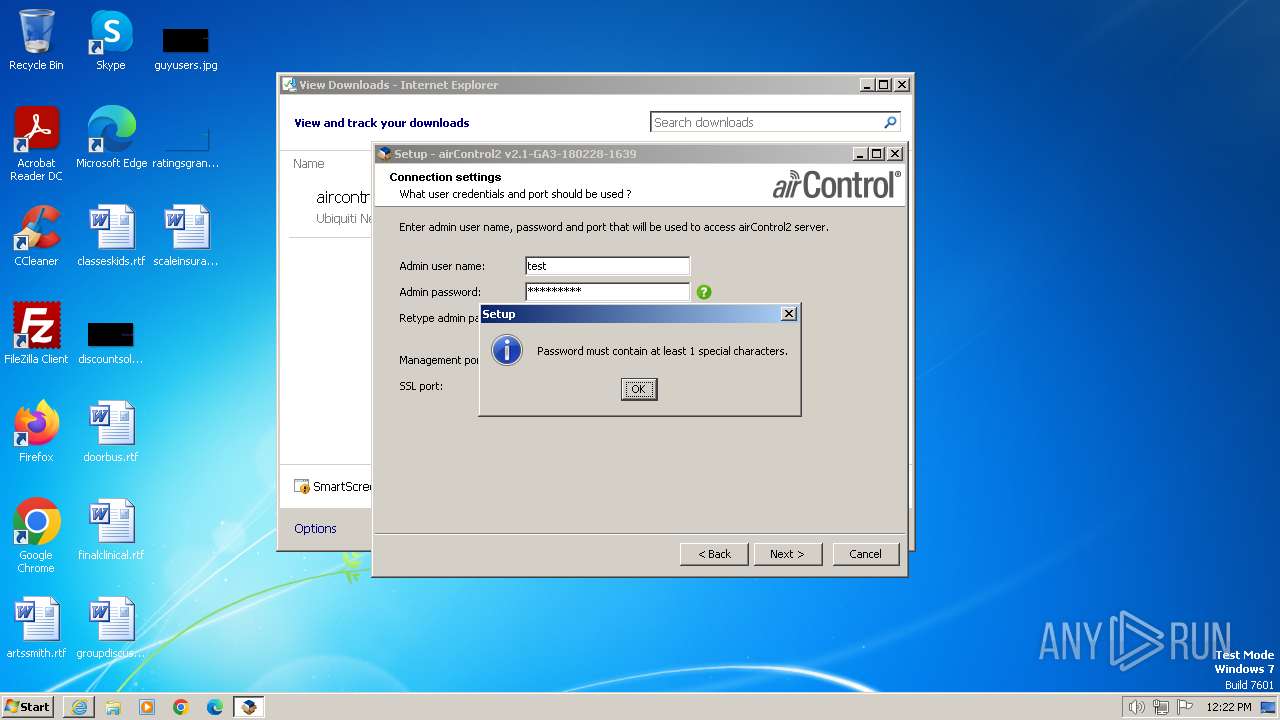
Uses ICACLS.EXE to modify access control lists
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
Reads security settings of Internet Explorer
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
Application launched itself
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
The process executes VB scripts
- cmd.exe (PID: 3044)
- cmd.exe (PID: 2380)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 3356)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 3356)
Accesses WMI object caption (SCRIPT)
- cscript.exe (PID: 3356)
Accesses operating system name via WMI (SCRIPT)
- cscript.exe (PID: 3356)
Accesses Windows installation date via WMI (SCRIPT)
- cscript.exe (PID: 3356)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 3356)
Starts CMD.EXE for commands execution
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
INFO
Executable content was dropped or overwritten
- iexplore.exe (PID: 3952)
Application launched itself
- iexplore.exe (PID: 3864)
Checks supported languages
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- unpack200.exe (PID: 1992)
- unpack200.exe (PID: 1644)
- unpack200.exe (PID: 2156)
- unpack200.exe (PID: 1576)
- unpack200.exe (PID: 1336)
- unpack200.exe (PID: 3616)
- unpack200.exe (PID: 1556)
- unpack200.exe (PID: 2320)
- unpack200.exe (PID: 2576)
- unpack200.exe (PID: 2772)
- unpack200.exe (PID: 2112)
- unpack200.exe (PID: 2384)
- unpack200.exe (PID: 1484)
- unpack200.exe (PID: 1780)
- unpack200.exe (PID: 2724)
- unpack200.exe (PID: 992)
- unpack200.exe (PID: 2396)
- unpack200.exe (PID: 924)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
- javaw.exe (PID: 3480)
- wmpnscfg.exe (PID: 2840)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3952)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3864)
Create files in a temporary directory
- unpack200.exe (PID: 2156)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- unpack200.exe (PID: 1992)
- unpack200.exe (PID: 2724)
- unpack200.exe (PID: 1644)
- unpack200.exe (PID: 1576)
- unpack200.exe (PID: 2320)
- unpack200.exe (PID: 1336)
- unpack200.exe (PID: 1556)
- unpack200.exe (PID: 2384)
- unpack200.exe (PID: 2576)
- unpack200.exe (PID: 2112)
- unpack200.exe (PID: 2772)
- unpack200.exe (PID: 3616)
- unpack200.exe (PID: 1484)
- unpack200.exe (PID: 1780)
- unpack200.exe (PID: 992)
- unpack200.exe (PID: 924)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
- unpack200.exe (PID: 2396)
- javaw.exe (PID: 3480)
The process uses the downloaded file
- iexplore.exe (PID: 3864)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
Creates files in the program directory
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
- javaw.exe (PID: 3480)
Process checks whether UAC notifications are on
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
Reads the computer name
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
- wmpnscfg.exe (PID: 2840)
Reads the machine GUID from the registry
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 1740)
- aircontrol-v2.1-GA3-180228-1639-win32.exe (PID: 2736)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2032)
- cscript.exe (PID: 3356)
Manual execution by a user
- wmpnscfg.exe (PID: 2840)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
95
Monitored processes
30
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | -r "jre\lib\ext\nashorn.jar.pack" "jre\lib\ext\nashorn.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 992 | -r "jre\lib\ext\localedata.jar.pack" "jre\lib\ext\localedata.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 1020 | icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage\48c3645fd80157b1.timestamp /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1036 | icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | -r "jre\lib\management-agent.jar.pack" "jre\lib\management-agent.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 1484 | -r "jre\lib\ext\jaccess.jar.pack" "jre\lib\ext\jaccess.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 1556 | -r "jre\lib\resources.jar.pack" "jre\lib\resources.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 1576 | -r "jre\lib\jfxswt.jar.pack" "jre\lib\jfxswt.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 1644 | -r "jre\lib\jfr.jar.pack" "jre\lib\jfr.jar" | C:\Users\admin\AppData\Local\Temp\e4jFC09.tmp_dir1708690898\jre\bin\unpack200.exe | — | aircontrol-v2.1-GA3-180228-1639-win32.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.1020.14 Modules
| |||||||||||||||
| 1740 | "C:\Users\admin\Downloads\aircontrol-v2.1-GA3-180228-1639-win32.exe" | C:\Users\admin\Downloads\aircontrol-v2.1-GA3-180228-1639-win32.exe | iexplore.exe | ||||||||||||
User: admin Company: Ubiquiti Networks, Inc. Integrity Level: MEDIUM Description: airControl2 Exit code: 0 Version: v2.1-GA3-180228-1639 Modules
| |||||||||||||||
Total events
25 023
Read events
24 883
Write events
103
Delete events
37
Modification events
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090258 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090258 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3864) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
454
Suspicious files
227
Text files
982
Unknown types
113
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:9F728F71B5C885DA6DF863032C1BCB45 | SHA256:A7584EF98153A4FE7B4A6EB174F638917D557ADD426B1EFC1006B82706F55C3A | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B436D5D7E3751F880CF0096FDE680A01 | SHA256:E694757FD45979AF8701B65251E55658A85F975311814A86EF2DC9F7738E8167 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | der | |
MD5:02C1191EE5297A87B2E85A3BED97595E | SHA256:CE64D848ACFCFDF801140E03B2AAF9E30D6CD3A4167C8051E3D0BEC037A29312 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:AC0252A6C8673FA50BDF2961DD6BD471 | SHA256:19122C391D8CC9A95017536B2C46B10BC80C2EE932AE4BB99BC10AC87F6AE130 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\versionlist.xml | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:A8C299E2D77766B909AA9CCBC4DF9A5A | SHA256:2F2B991F9D16B90D457347F1A8D39D7D3822A3BD5004B97ACBD44F31025704B8 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:5F269D75D2D9906614322FB028FEBC29 | SHA256:FF7FE1FF4947C8ADDEC0FD1D65420E634DDAAE6BE3934B60F982C092140DBAFA | |||
| 3952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_056B48C93C4964C2E64C0A8958238656 | binary | |
MD5:736B4E20FE020D6777DABE9091C40F0A | SHA256:0469290F5E1C885EC9643E7EA4B4906D4BF0CF8E86D762E77D43064BD87C75C7 | |||
| 3864 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\62RRP814.txt | text | |
MD5:13C580865A41C75A49941EE864F6E915 | SHA256:C7C4F467D3BCDA7F1F09ECDCA8D8C2E7E72BB58C85C275FB11DEBFD421D233CB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
26
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3952 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?927e0d673a39dd41 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d362edf7b65e9a48 | unknown | — | — | unknown |
3952 | iexplore.exe | GET | 200 | 108.156.61.221:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 18.65.41.80:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | binary | 1.49 Kb | unknown |
3952 | iexplore.exe | GET | 200 | 18.65.41.80:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | binary | 1.37 Kb | unknown |
3864 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?76ad697231f9b13b | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9aee5c2adfb08fdb | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d416ea50f343b89b | unknown | — | — | unknown |
3864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1b8fee253118cbef | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3952 | iexplore.exe | 52.222.140.181:443 | dl.ubnt.com | AMAZON-02 | US | unknown |
3952 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3952 | iexplore.exe | 108.156.61.221:80 | o.ss2.us | AMAZON-02 | US | unknown |
3952 | iexplore.exe | 18.65.41.80:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | unknown |
1080 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
3864 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
3864 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dl.ubnt.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |