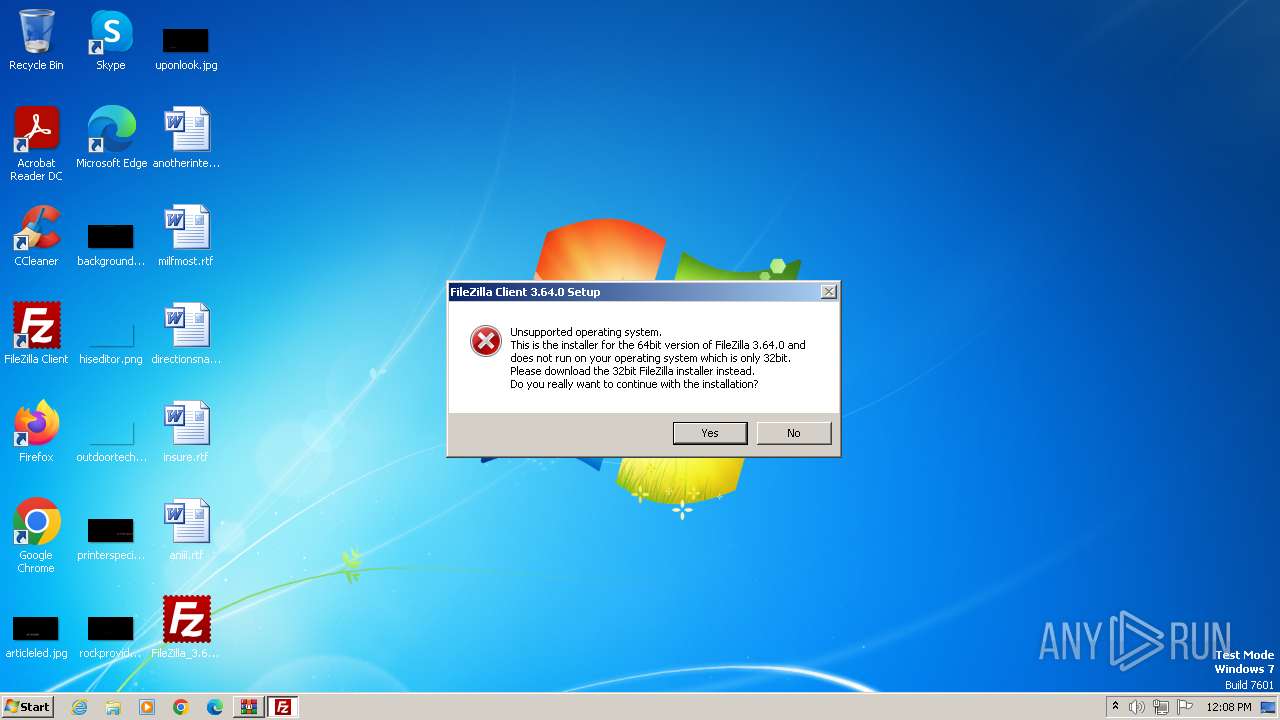
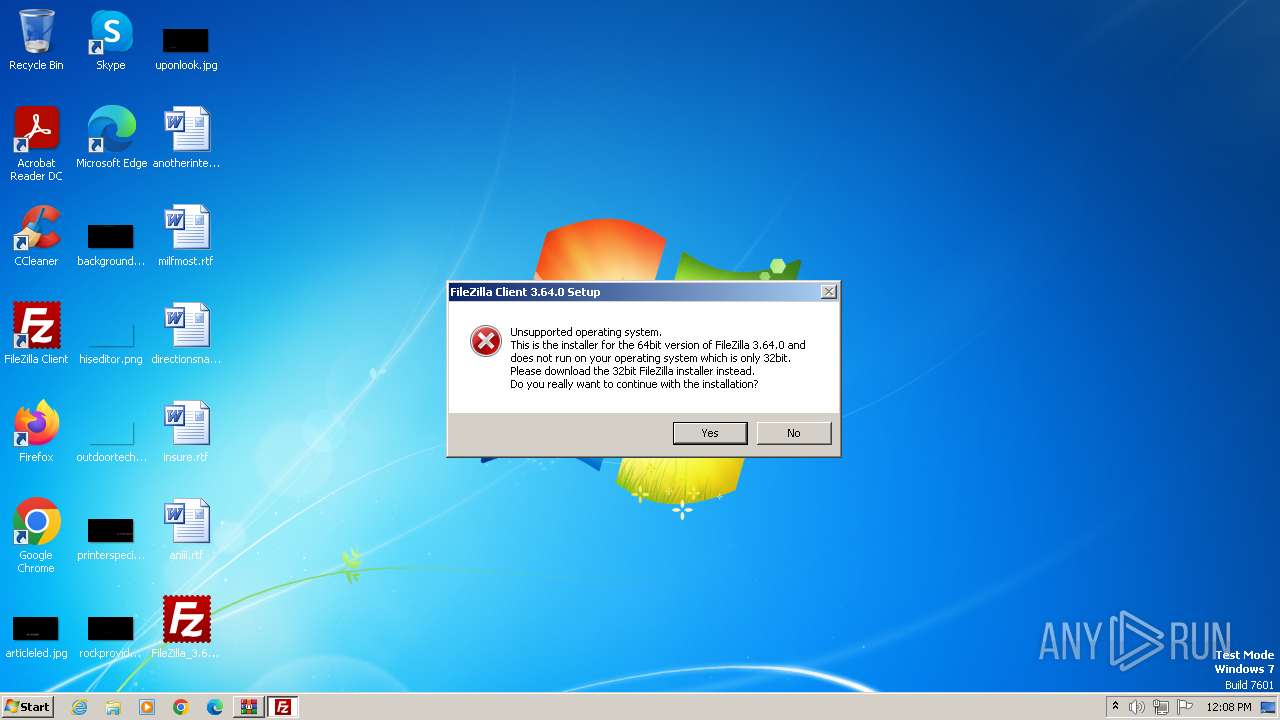
| File name: | FileZilla_3.64.0_win64_sponsored2-setup.exe.7z |
| Full analysis: | https://app.any.run/tasks/4ab89353-7cde-47fa-9791-266e17f64b49 |
| Verdict: | Malicious activity |
| Analysis date: | November 06, 2023, 12:07:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 7EE4354563B1FA0B2BD2DDCA9D3F14B9 |
| SHA1: | AF94BF7796F0545E3B832BEEC4C1D0743A38342F |
| SHA256: | D2F5EF855FE43393A15E4E04E4505683AC75575F03D6656EF7055C5FF1B873A2 |
| SSDEEP: | 98304:HKsBRyGcBEMsVK3ZESd06yVU61qg9l/AnB79JHkWh/ABiZ0DTqMFdNQUNuThoKma:LIEz/gWveL8rh+KMXeRh7ZRtTZdG |
MALICIOUS
Drops the executable file immediately after the start
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3756)
SUSPICIOUS
The process creates files with name similar to system file names
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3756)
Malware-specific behavior (creating "System.dll" in Temp)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3756)
Application launched itself
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3308)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
Checks supported languages
- wmpnscfg.exe (PID: 3308)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3756)
Reads the computer name
- wmpnscfg.exe (PID: 3308)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3756)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3448)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3308)
Create files in a temporary directory
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3500)
- FileZilla_3.64.0_win64_sponsored2-setup.exe (PID: 3756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
41
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3308 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3448 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\FileZilla_3.64.0_win64_sponsored2-setup.exe.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3500 | "C:\Users\admin\Desktop\FileZilla_3.64.0_win64_sponsored2-setup.exe" | C:\Users\admin\Desktop\FileZilla_3.64.0_win64_sponsored2-setup.exe | — | explorer.exe | |||||||||||
User: admin Company: Tim Kosse Integrity Level: MEDIUM Description: FileZilla FTP Client Exit code: 2 Version: 3.64.0 Modules
| |||||||||||||||
| 3756 | "C:\Users\admin\Desktop\FileZilla_3.64.0_win64_sponsored2-setup.exe" /UAC:A016E /NCRC | C:\Users\admin\Desktop\FileZilla_3.64.0_win64_sponsored2-setup.exe | FileZilla_3.64.0_win64_sponsored2-setup.exe | ||||||||||||
User: admin Company: Tim Kosse Integrity Level: HIGH Description: FileZilla FTP Client Exit code: 2 Version: 3.64.0 Modules
| |||||||||||||||
Total events
1 087
Read events
1 075
Write events
9
Delete events
3
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3308) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{151121FB-CF6A-4C30-9B5F-96A967A51113}\{DDCD5A81-332A-4450-9658-223223AB95A6} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3308) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{151121FB-CF6A-4C30-9B5F-96A967A51113} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3308) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{FF75C268-00A7-44AA-98B6-FAFA45AD6EB8} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
2
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3500 | FileZilla_3.64.0_win64_sponsored2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsgDECE.tmp\UserInfo.dll | executable | |
MD5:98FF85B635D9114A9F6A0CD7B9B649D0 | SHA256:933F93A30CE44DF96CBC4AC0B56A8B02EE01DA27E4EA665D1D846357A8FCA8DE | |||
| 3756 | FileZilla_3.64.0_win64_sponsored2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsl1167.tmp\System.dll | executable | |
MD5:564BB0373067E1785CBA7E4C24AAB4BF | SHA256:7A9DDEE34562CD3703F1502B5C70E99CD5BBA15DE2B6845A3555033D7F6CB2A5 | |||
| 3500 | FileZilla_3.64.0_win64_sponsored2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsgDECE.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 3448 | WinRAR.exe | C:\Users\admin\Desktop\FileZilla_3.64.0_win64_sponsored2-setup.exe | executable | |
MD5:535DC7924CCFEFCE59C70FF8B5A4C961 | SHA256:2B5D5F5F126DF5D0A7AF4EBB8B6D34EB4934FA0FAE602515B0ADA48B376BDB10 | |||
| 3756 | FileZilla_3.64.0_win64_sponsored2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsv1156.tmp | binary | |
MD5:78C01C1F481119D119A4BD2B30EE5171 | SHA256:4EB8C566620629E5558DBB1D5B4B6601D0FCB2CE941DA914339CB29AB2E58C39 | |||
| 3500 | FileZilla_3.64.0_win64_sponsored2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsgDECE.tmp\System.dll | executable | |
MD5:564BB0373067E1785CBA7E4C24AAB4BF | SHA256:7A9DDEE34562CD3703F1502B5C70E99CD5BBA15DE2B6845A3555033D7F6CB2A5 | |||
| 3500 | FileZilla_3.64.0_win64_sponsored2-setup.exe | C:\Users\admin\AppData\Local\Temp\nsqDEBD.tmp | binary | |
MD5:19063B20234CD54D90A885B627750C53 | SHA256:EDBC665B34222C1A37FC501DA2E178E2D0BBC5C3BD4DF8C66E1D7A4F6DB9DCF8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |