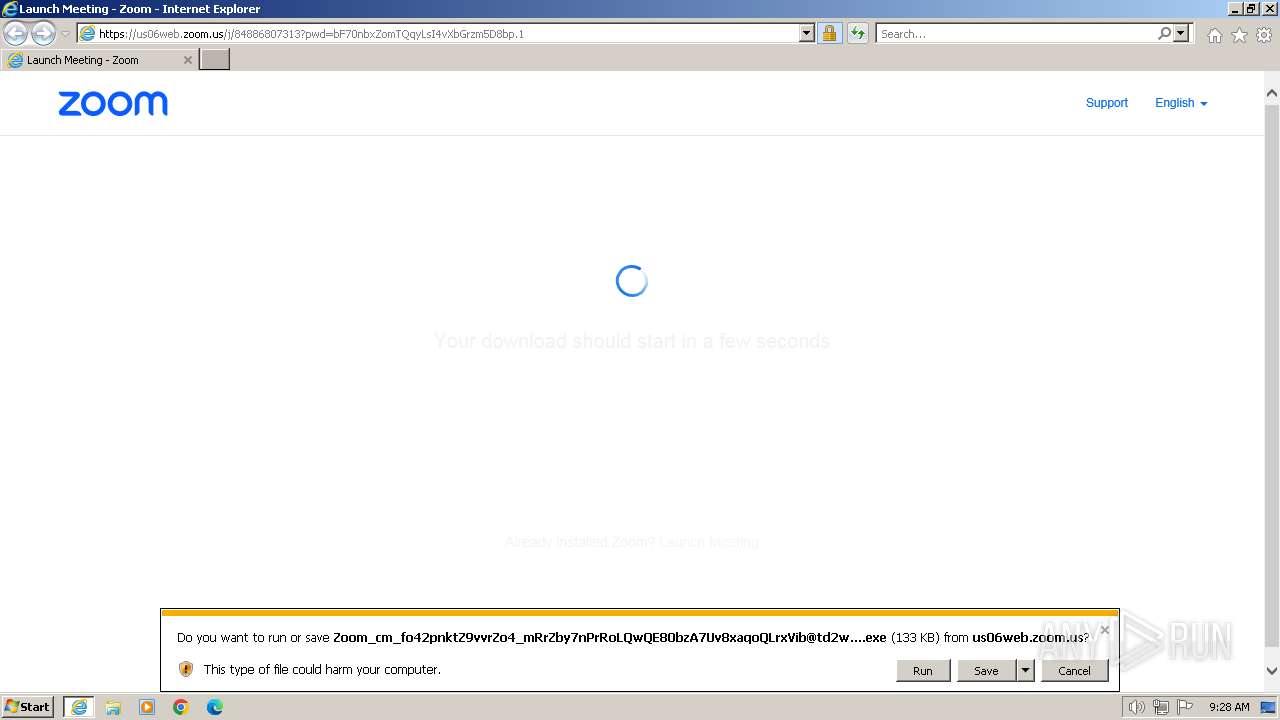
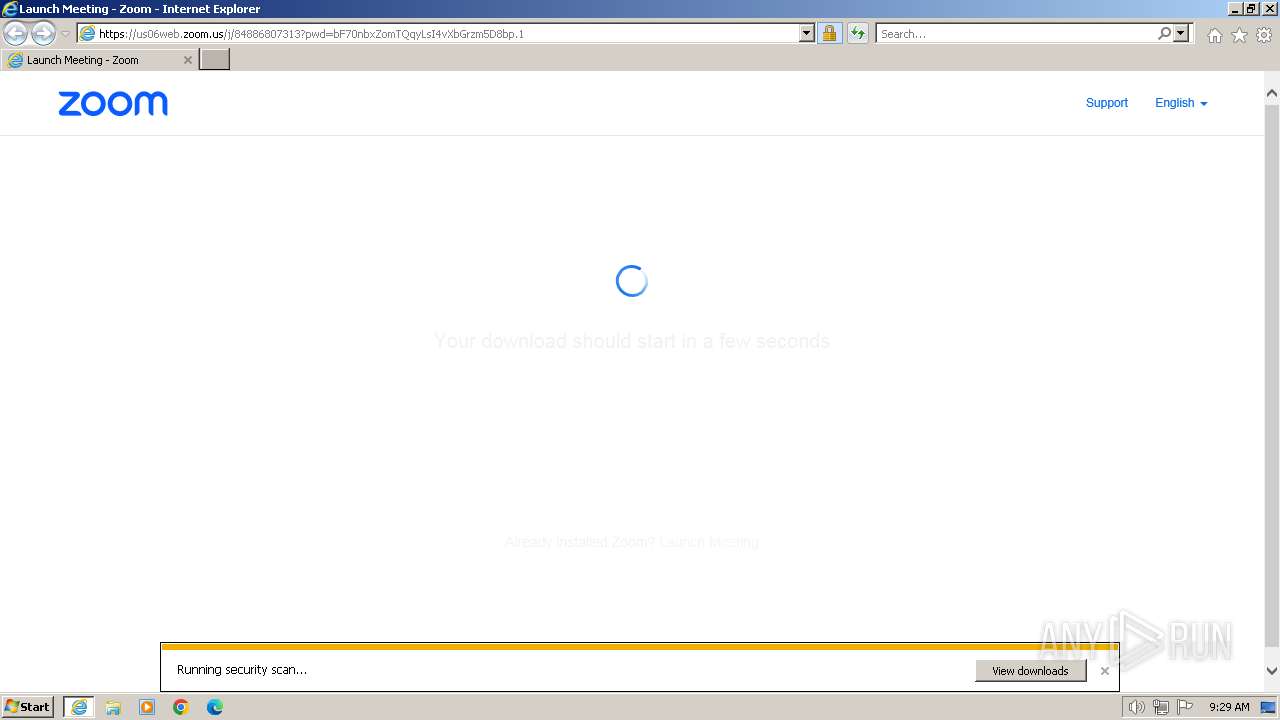
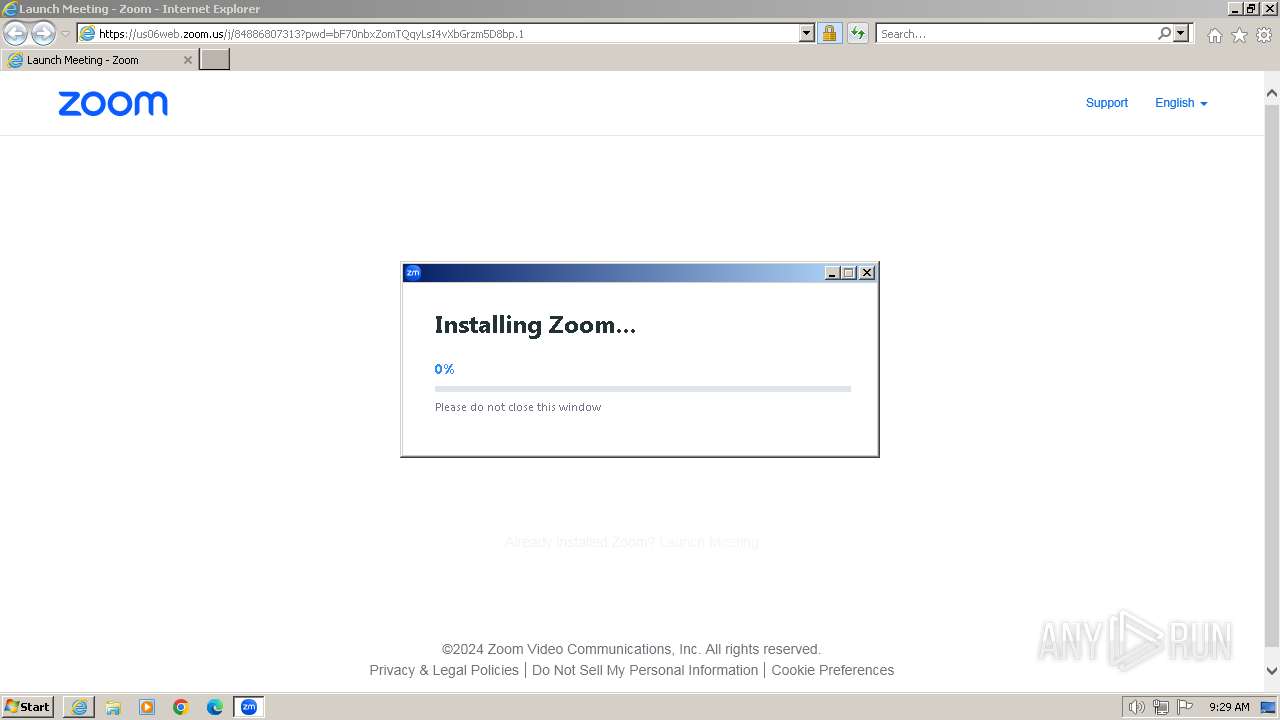
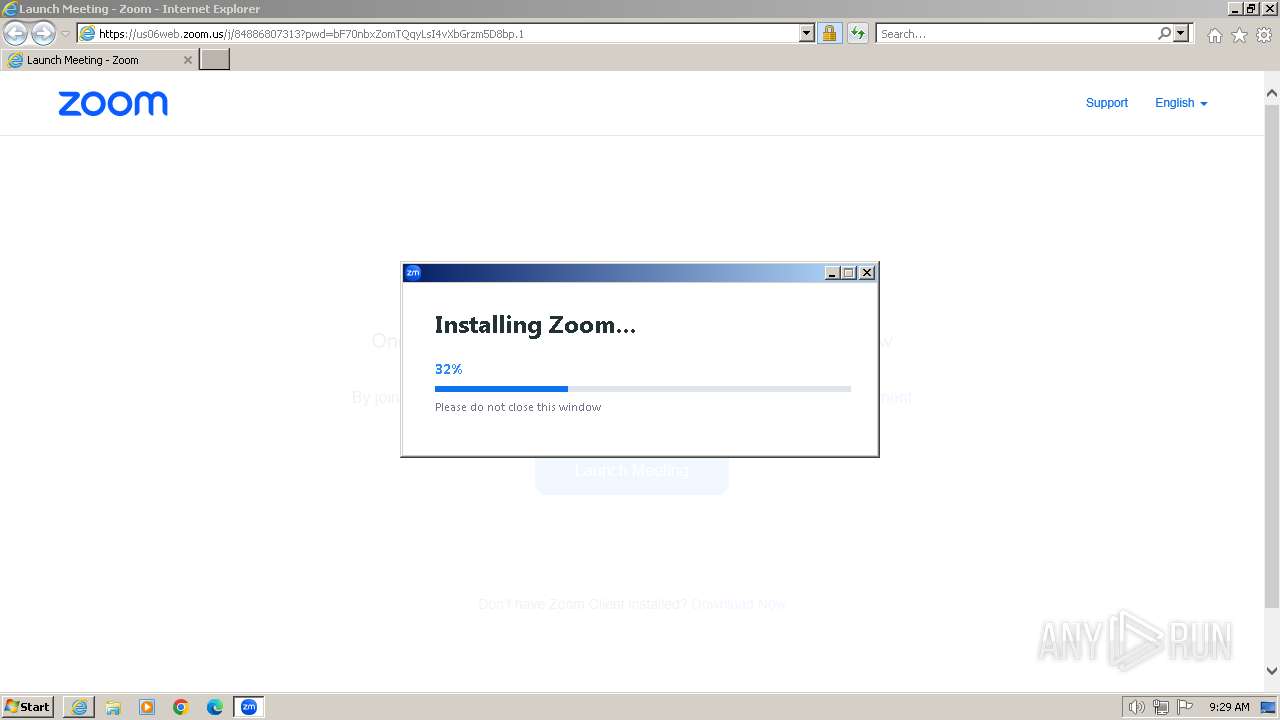
| URL: | https://us06web.zoom.us/j/84886807313?pwd=bF70nbxZomTQqyLsI4vXbGrzm5D8bp.1 |
| Full analysis: | https://app.any.run/tasks/95eec6c9-befb-4d75-b0bc-251533357849 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2024, 09:28:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3C6F5B08D4CAFE06ED124184AEF3ADEB |
| SHA1: | 81EC3AB87ABC63DC97D67FEB7A91D92B06A63C86 |
| SHA256: | D2F0A5FC6F707D8A5508E2C51DBF797555D7C29DBDF807972A68CE6C109B4C5C |
| SSDEEP: | 3:N8CAHVILQN+fT8k019Ccn:2CA19+78kwZn |
MALICIOUS
Drops the executable file immediately after the start
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
SUSPICIOUS
Reads the Internet Settings
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
Executable content was dropped or overwritten
- Installer.exe (PID: 2152)
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Zoom.exe (PID: 2484)
Reads security settings of Internet Explorer
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
- Zoom.exe (PID: 4092)
Reads settings of System Certificates
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
- Zoom.exe (PID: 4092)
Checks Windows Trust Settings
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 4092)
- Zoom.exe (PID: 924)
The process drops C-runtime libraries
- Installer.exe (PID: 2152)
Application launched itself
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
Changes Internet Explorer settings (feature browser emulation)
- Installer.exe (PID: 2152)
Creates a software uninstall entry
- Installer.exe (PID: 2152)
Starts itself from another location
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
The process creates files with name similar to system file names
- Installer.exe (PID: 2152)
Process drops legitimate windows executable
- Installer.exe (PID: 2152)
Starts application with an unusual extension
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
INFO
The process uses the downloaded file
- iexplore.exe (PID: 3668)
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3972)
- iexplore.exe (PID: 3668)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3668)
- iexplore.exe (PID: 3972)
Checks supported languages
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Installer.exe (PID: 1336)
- zmE8B5.tmp (PID: 2244)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
- Zoom.exe (PID: 4092)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3668)
Reads the computer name
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Installer.exe (PID: 1336)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
- Zoom.exe (PID: 4092)
Application launched itself
- iexplore.exe (PID: 3668)
Checks proxy server information
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
Reads the machine GUID from the registry
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
- Zoom.exe (PID: 4092)
Creates files or folders in the user directory
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 924)
Reads the software policy settings
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Installer.exe (PID: 2152)
- Zoom.exe (PID: 2484)
- Zoom.exe (PID: 4092)
- Zoom.exe (PID: 924)
Create files in a temporary directory
- Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe (PID: 3392)
- Zoom.exe (PID: 2484)
Dropped object may contain TOR URL's
- Installer.exe (PID: 2152)
Process checks computer location settings
- Zoom.exe (PID: 2484)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
9
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" --action=join --runaszvideo=TRUE | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,17,7,31859 Modules
| |||||||||||||||
| 1336 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" /addfwexception --bin_home="C:\Users\admin\AppData\Roaming\Zoom\bin" | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Installer.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: HIGH Description: Zoom Installer Exit code: 0 Version: 5,17,7,31859 Modules
| |||||||||||||||
| 2152 | "C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe" ZInstaller --conf.mode=silent --ipc_wnd=328192 | C:\Users\admin\AppData\Roaming\Zoom\ZoomDownload\Installer.exe | Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Installer Exit code: 0 Version: 5,17,7,31859 Modules
| |||||||||||||||
| 2244 | "C:\Users\admin\AppData\Local\Temp\zmE8B5.tmp" -DAF8C715436E44649F1312698287E6A5=C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe | C:\Users\admin\AppData\Local\Temp\zmE8B5.tmp | — | Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe | |||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,17,0,25 Modules
| |||||||||||||||
| 2484 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" "--url=zoommtg://win.launch?h.domain=us06web.zoom.us&h.path=join&confid=dXNzPXl5cjBEaFBDX0dfLVFKSmJXYXo4dXRIOVBQcGNONTM5WHZ5cU5WeXBNOGwzV0FjT19sRTZGM1hJMWVNczVEUHlIME9zZEJGMUtJZXhTVlN3MEdKamZfU3ZHLWJ6SXpRLlNKZ21iZmlneGJzS1V3ZE0mdGlkPTEyNTk0ZWJmNjhmMDQ4OTA5NzgyN2MxMzA0Mzk1YWIy&mcv=0.92.11227.0929&stype=0&zc=0&browser=msie&action=join&confno=84886807313&pwd=bF70nbxZomTQqyLsI4vXbGrzm5D8bp.1" | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,17,7,31859 Modules
| |||||||||||||||
| 3392 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\Zoom_cm_fo42pnktZ9vvrZo4_mRrZby7nPrRoLQwQE80bzA7Uv8xaqoQLrxVib@td2wE6w8ftW+6hqg_kf878d3298088fb43_.exe | iexplore.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Opener Exit code: 0 Version: 5,17,0,25 Modules
| |||||||||||||||
| 3668 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://us06web.zoom.us/j/84886807313?pwd=bF70nbxZomTQqyLsI4vXbGrzm5D8bp.1" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3668 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4092 | "C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe" --action=preload --runaszvideo=TRUE | C:\Users\admin\AppData\Roaming\Zoom\bin\Zoom.exe | Zoom.exe | ||||||||||||
User: admin Company: Zoom Video Communications, Inc. Integrity Level: MEDIUM Description: Zoom Meetings Exit code: 0 Version: 5,17,7,31859 Modules
| |||||||||||||||
Total events
66 252
Read events
65 938
Write events
253
Delete events
61
Modification events
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31088826 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31088826 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
215
Suspicious files
198
Text files
65
Unknown types
58
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:CAB6225B861674F37BA35D7241B4D9D6 | SHA256:07AA9F1727174FFF61ED1F695EB071AD1113190CF02A7FEBC878E38B8C38941A | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\SY9LYX2R.txt | text | |
MD5:2E478B8EAD6948774750307C9B923A67 | SHA256:4A45545DE4FF60F2B391DE4C942DC5A872028A83738B58BA06ABAA8F97A1F222 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\7JONOM7H.txt | text | |
MD5:6D953FE9BC3D0CF4AE5D03D0915240A9 | SHA256:C6960FBCCDBF04FA05D5078C6108F8C95CBDFB55EF5B3B088E56EF0996A621A0 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\060EYAQY.txt | text | |
MD5:47823C1CB6FEBA60D4F8E5F925FFBA72 | SHA256:CEE5B899D012E890F7F2780C0A7722003B5F1DEA66CF20DD3C7C999673F1CB10 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\DOTBATAV\us06web.zoom[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\5WBLIOGU.txt | text | |
MD5:0355EA8002171CD53516F277E831FACF | SHA256:2063289862576FAA4C7E7EB24F94DCD9B9411BD33F0CFB07098EAEDAD3B500EB | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\NY0CYG1G.txt | text | |
MD5:A634555A384EA084D5C6A1A650D12AE3 | SHA256:05F3A66FB6326DC33F3913A524F58F1A6FE12957D2E1C7E8A96237F715A968AE | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\meeting.ef83108d59b8955d7351[1].js | text | |
MD5:CCCD12D1DD71738906D0175D0D3CBEA5 | SHA256:63B5C8611C42203D6CFA6789113DB6E6660BE5E9BE2FAD51D44862FA8C163367 | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\59D76868C250B3240414CE3EFBB12518_878497E055E73343333D232BA96F1060 | binary | |
MD5:950E65277A606B091D872CA98493977D | SHA256:632FAA410E54C23D9F2A15617F2B25FF9BC549526A61E092BFA03514205DE7DB | |||
| 3972 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:EFD9EF2F13CFF0B49D94D335284613FF | SHA256:71C77BE7A66B109DF5883673420EBF1F2909731EC0E27508738150414C37EA0B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
52
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | iexplore.exe | GET | 304 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c9f2b763ba05a2db | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 304 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8a21c6ad756e8dd9 | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | binary | 471 b | unknown |
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTk45WiKdPUwcMf8JgMC07ACYqr2AQUt2ui6qiqhIx56rTaD5iyxZV2ufQCEAIcL6umARqJ76Z3iMZH5HA%3D | unknown | binary | 471 b | unknown |
3668 | iexplore.exe | GET | 304 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?49cb245571b3d6d6 | unknown | — | — | unknown |
3972 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnxLiz3Fu1WB6n1%2FE6xWn1b0jXiQQUdIWAwGbH3zfez70pN6oDHb7tzRcCEAu5ZUPAbR7%2FZpXMY6k3CQo%3D | unknown | binary | 471 b | unknown |
3668 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
1080 | svchost.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6776476d79efed94 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3972 | iexplore.exe | 170.114.52.6:443 | us06web.zoom.us | — | US | unknown |
3972 | iexplore.exe | 23.32.238.218:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3972 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3972 | iexplore.exe | 34.98.108.207:443 | cdn.solvvy.com | GOOGLE | US | unknown |
3972 | iexplore.exe | 52.84.151.63:443 | st1.zoom.us | AMAZON-02 | US | unknown |
3972 | iexplore.exe | 134.224.0.54:443 | log-gateway.zoom.us | AMAZON-02 | US | unknown |
3972 | iexplore.exe | 104.18.130.236:443 | cdn.cookielaw.org | CLOUDFLARENET | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
us06web.zoom.us |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
st1.zoom.us |
| whitelisted |
cdn.solvvy.com |
| shared |
log-gateway.zoom.us |
| unknown |
cdn.cookielaw.org |
| whitelisted |
geolocation.onetrust.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\zoom_install_src |
Installer.exe | |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\tmp_uninstall |
Installer.exe | |
Installer.exe | [ProductPathHelper::RecursiveRemoveDirA] Path is: |
Installer.exe | C:\Users\admin\AppData\Roaming\Zoom\tmp_bin |
Installer.exe | |
Installer.exe | C:\Users\Public\Desktop\Acrobat Reader DC.lnk |