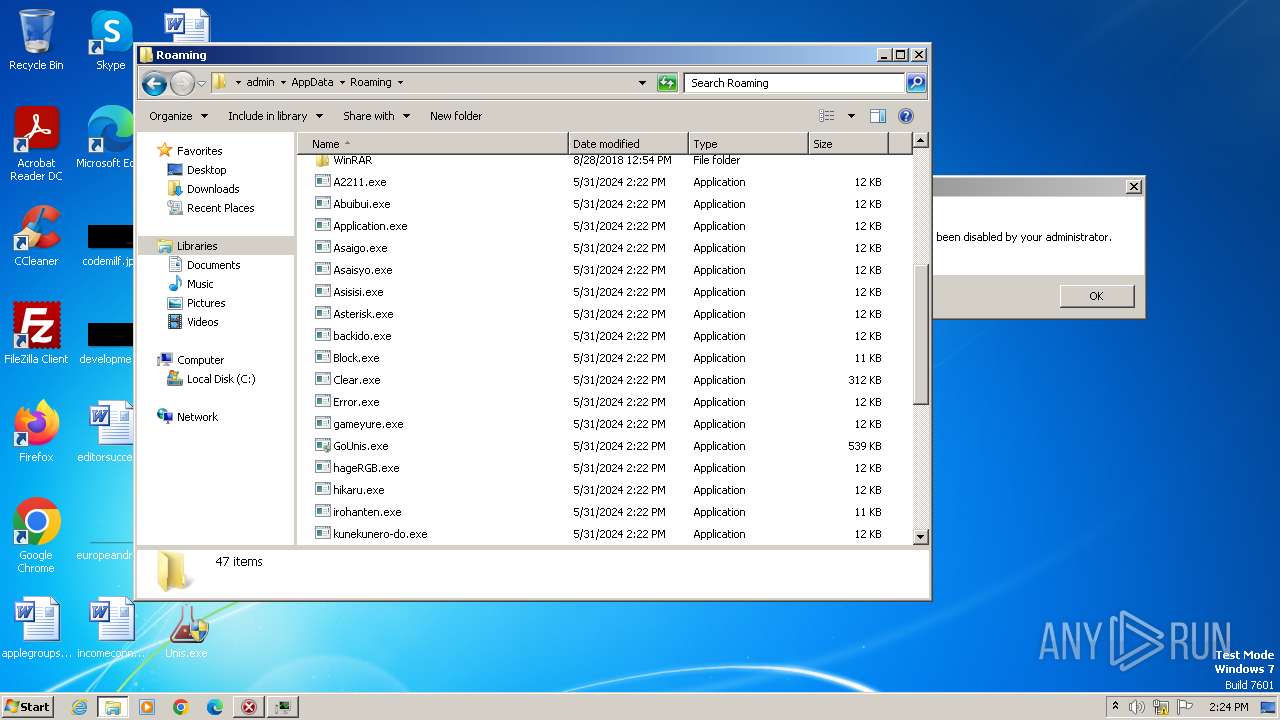
| File name: | Unis.exe |
| Full analysis: | https://app.any.run/tasks/765891a1-21da-46d6-9d6e-7f63c38d3152 |
| Verdict: | Malicious activity |
| Analysis date: | May 31, 2024, 13:22:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | E72088233E9D7D1D9826A35604C49FD7 |
| SHA1: | FA8A5990E2E1B7FB8E23AF3AE54BE58FCE2125C2 |
| SHA256: | D2E3B68594BA8A21EB03056554DCC6ED43030E6E2969CAEF6F205FE86390339C |
| SSDEEP: | 24576:dwMaKYUcTqan0p4Vm7hTG/0ObcPljW3xyK6yvAWHLqTAI0NkwDRLE:dwfvUcTqanw4Vm7hTG/0ObcPljW3xyT7 |
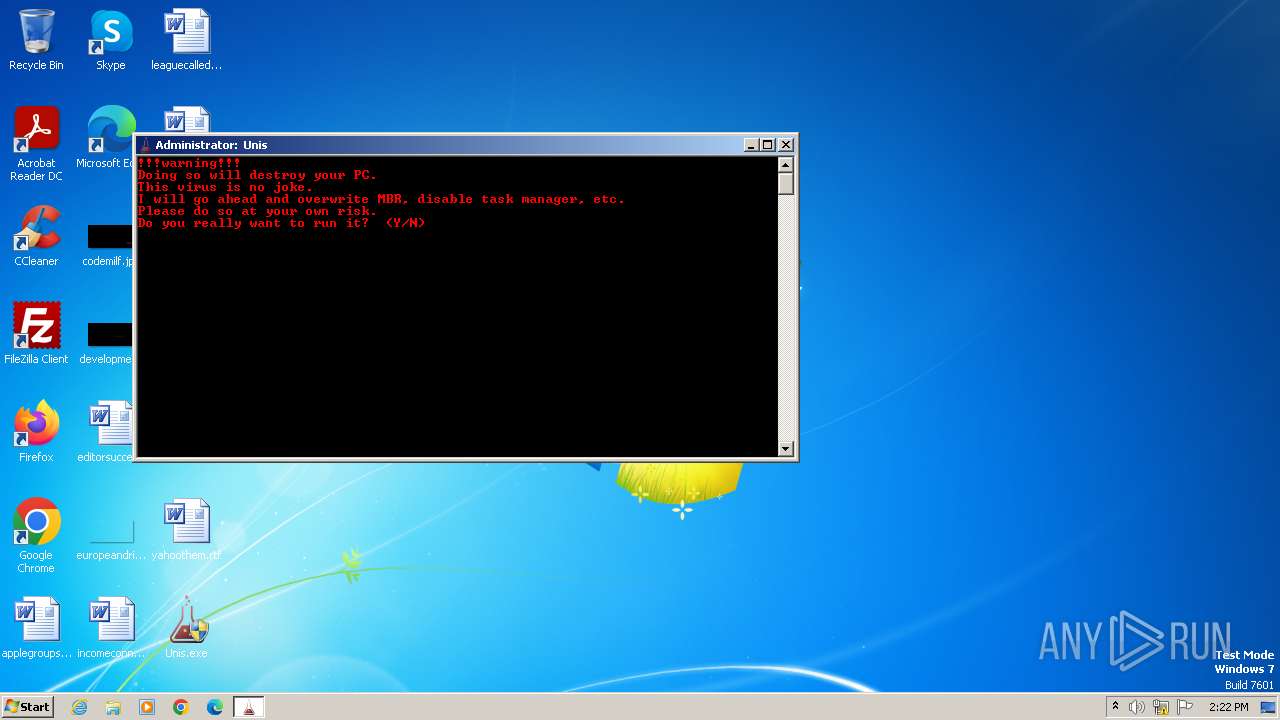
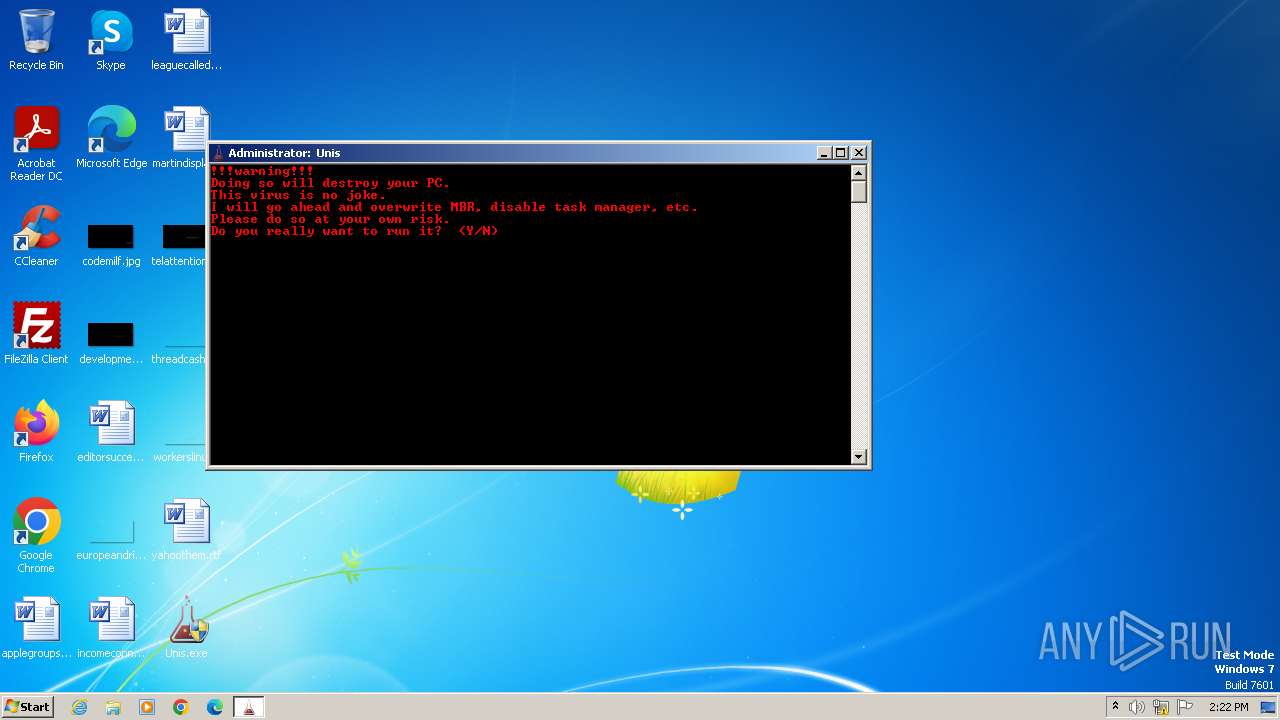
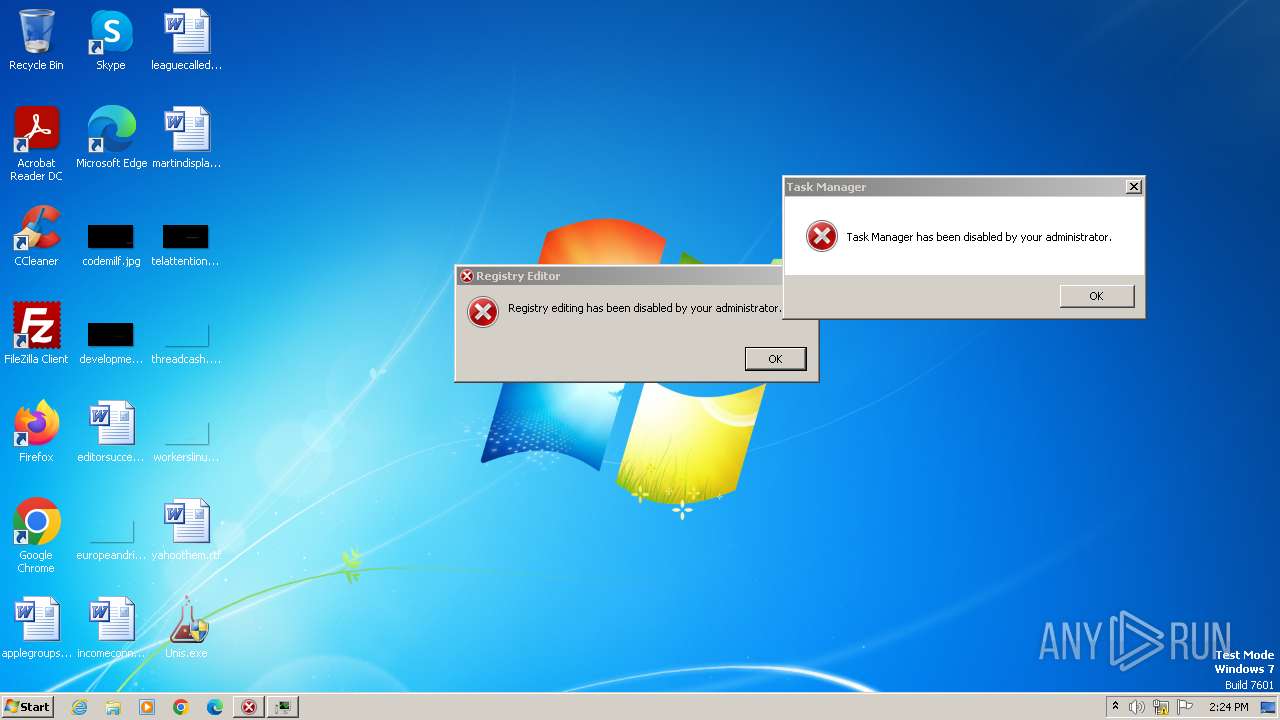
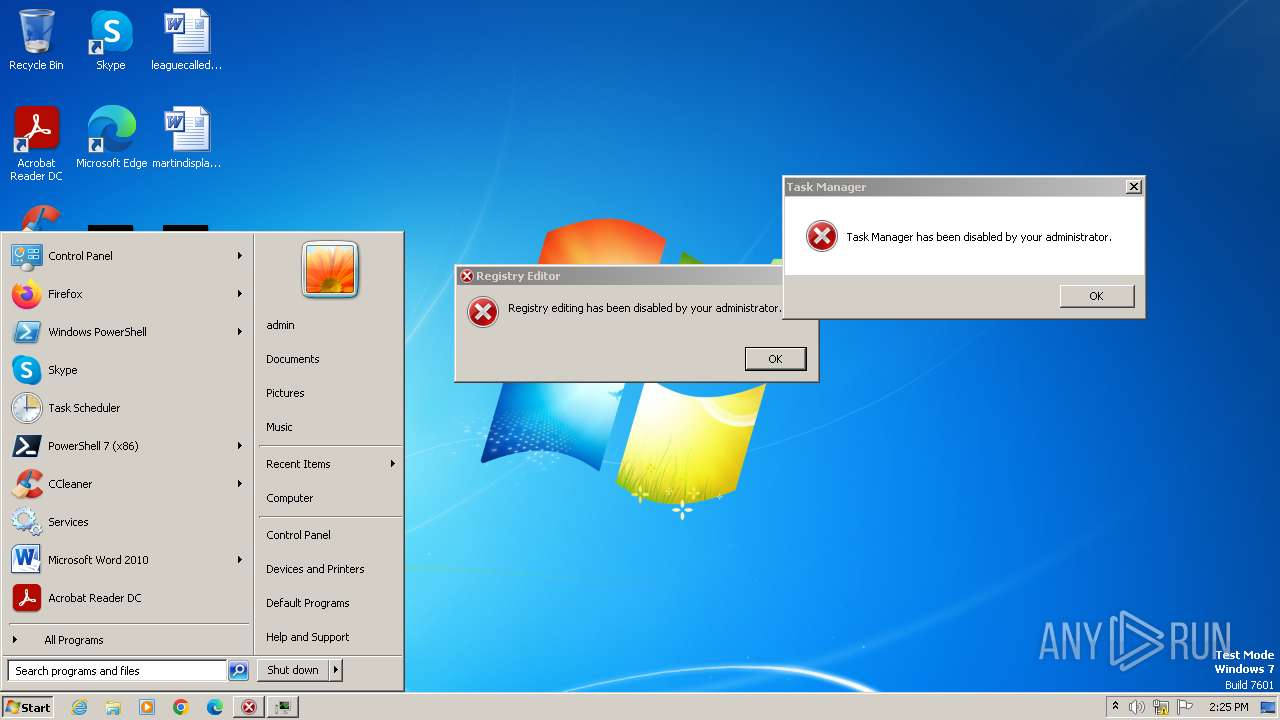
MALICIOUS
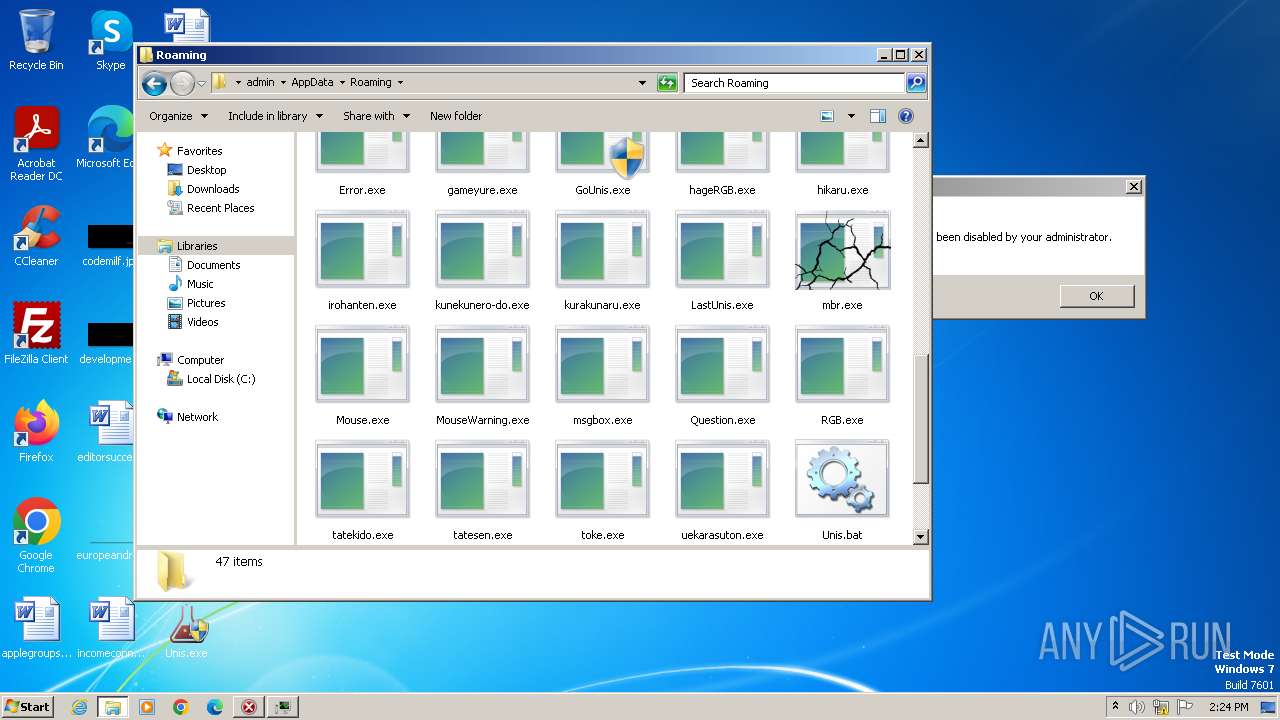
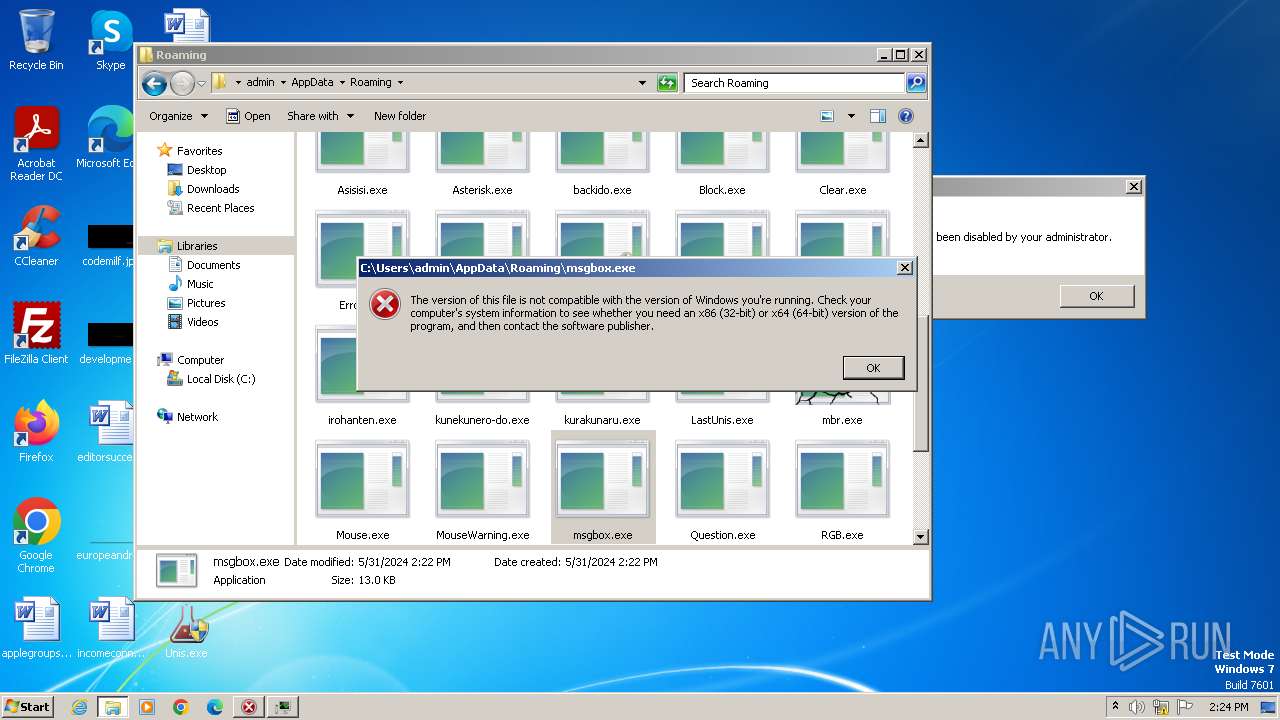
Drops the executable file immediately after the start
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
- cmd.exe (PID: 1184)
Create files in the Startup directory
- cmd.exe (PID: 1184)
SUSPICIOUS
Executing commands from a ".bat" file
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
Starts CMD.EXE for commands execution
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
The executable file from the user directory is run by the CMD process
- GoUnis.exe (PID: 2028)
- mbr.exe (PID: 1764)
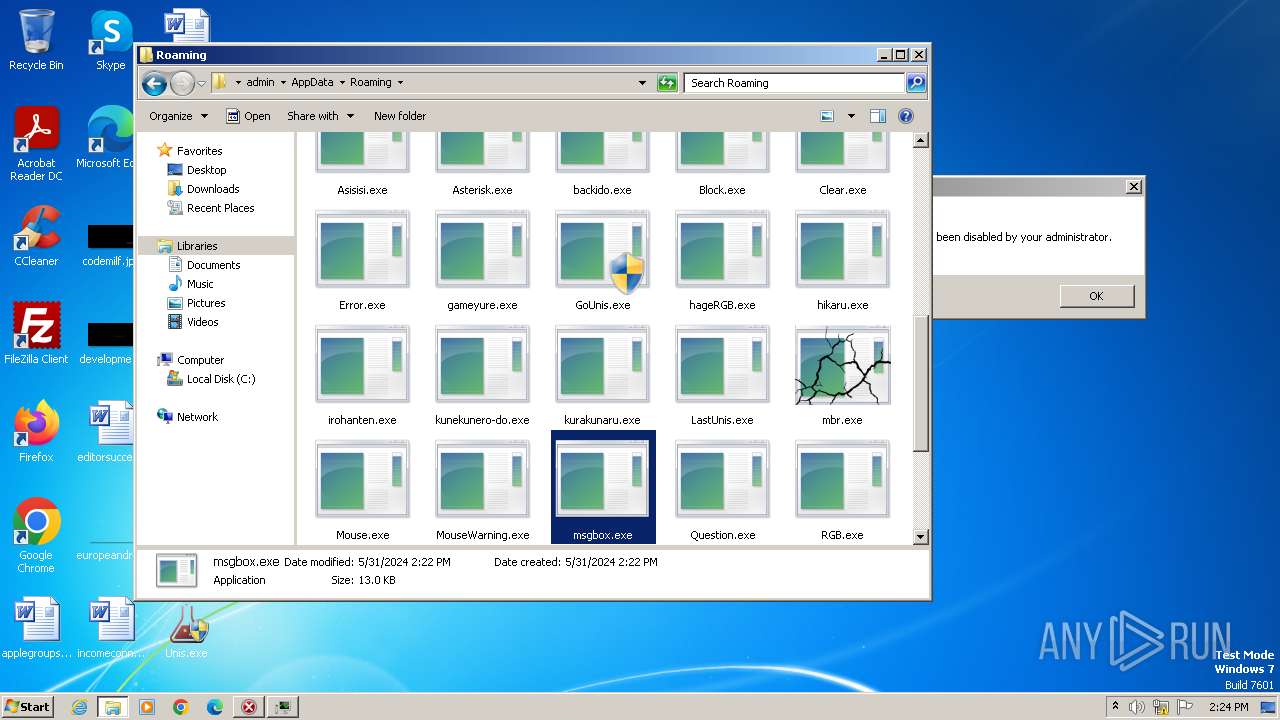
Executable content was dropped or overwritten
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
- cmd.exe (PID: 1184)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1064)
- cmd.exe (PID: 1184)
Reads the Internet Settings
- GoUnis.exe (PID: 2028)
- msdt.exe (PID: 2012)
Reads security settings of Internet Explorer
- GoUnis.exe (PID: 2028)
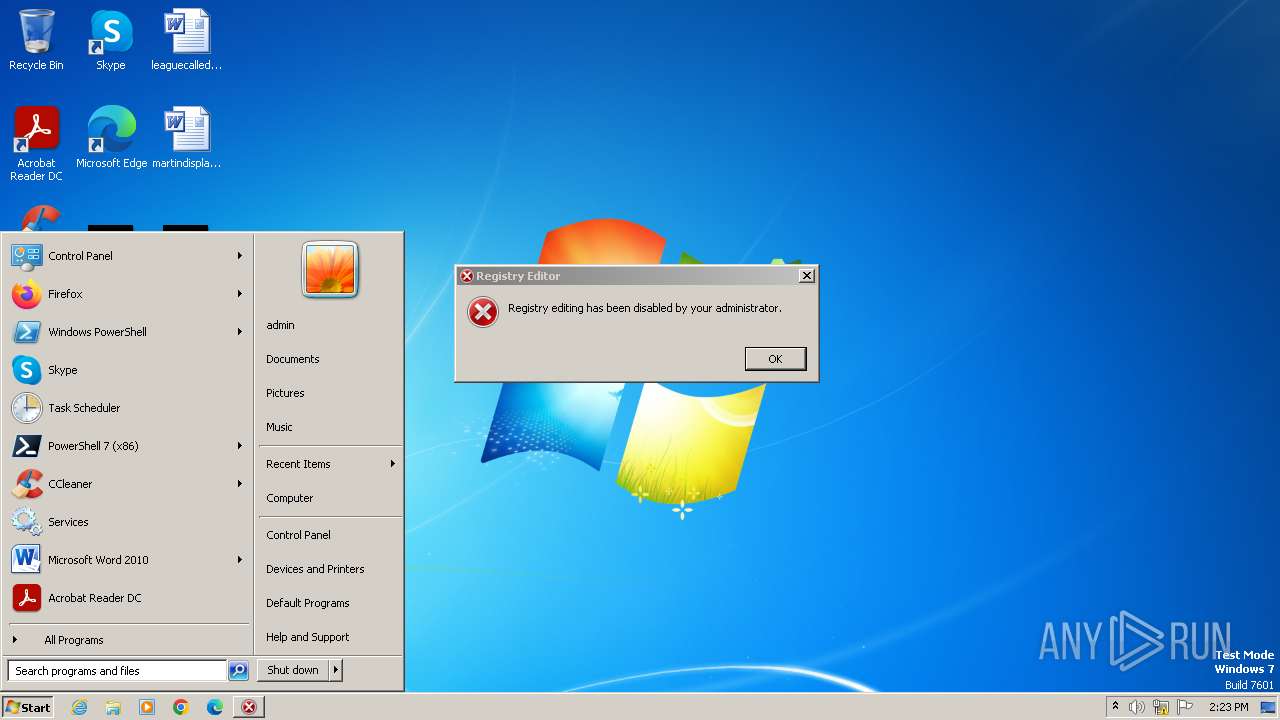
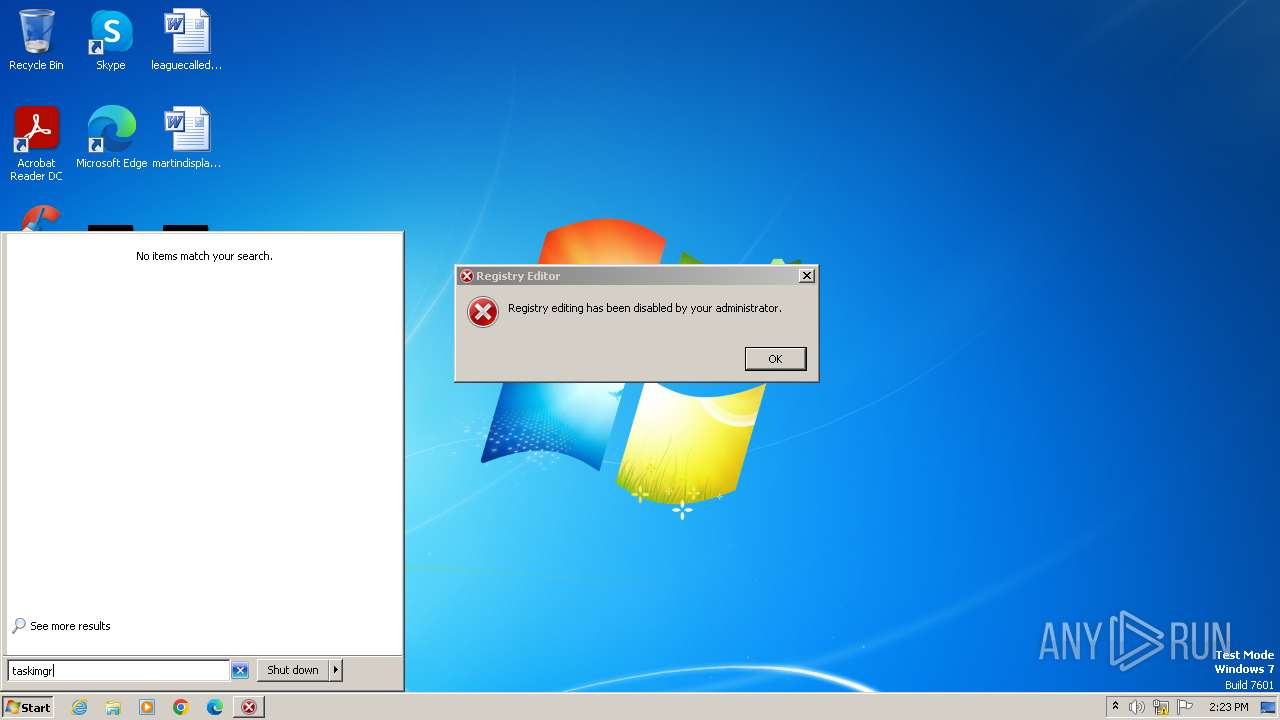
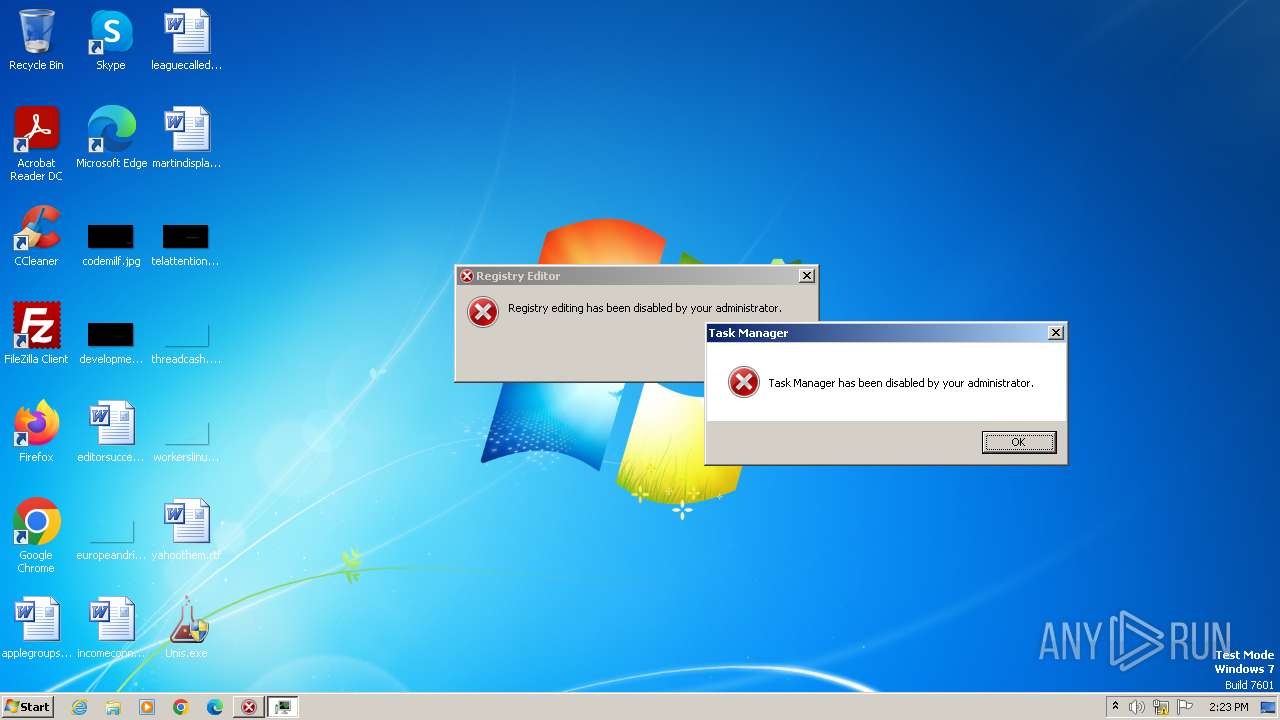
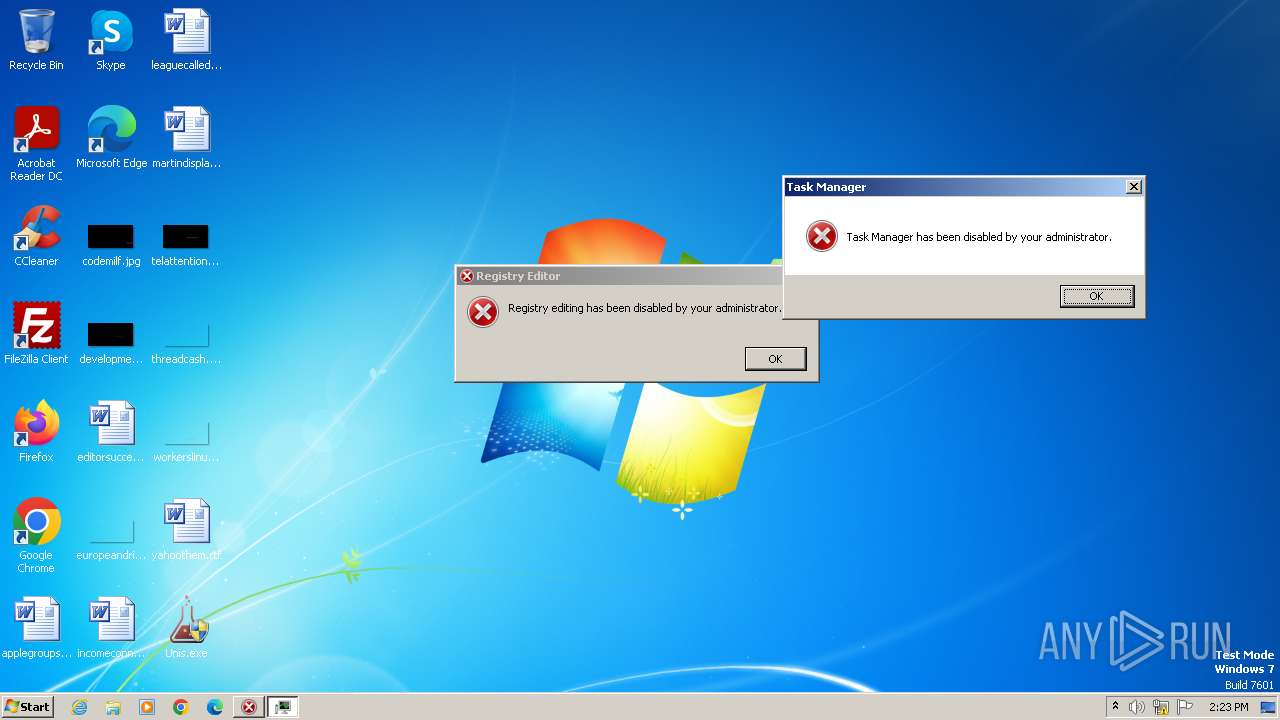
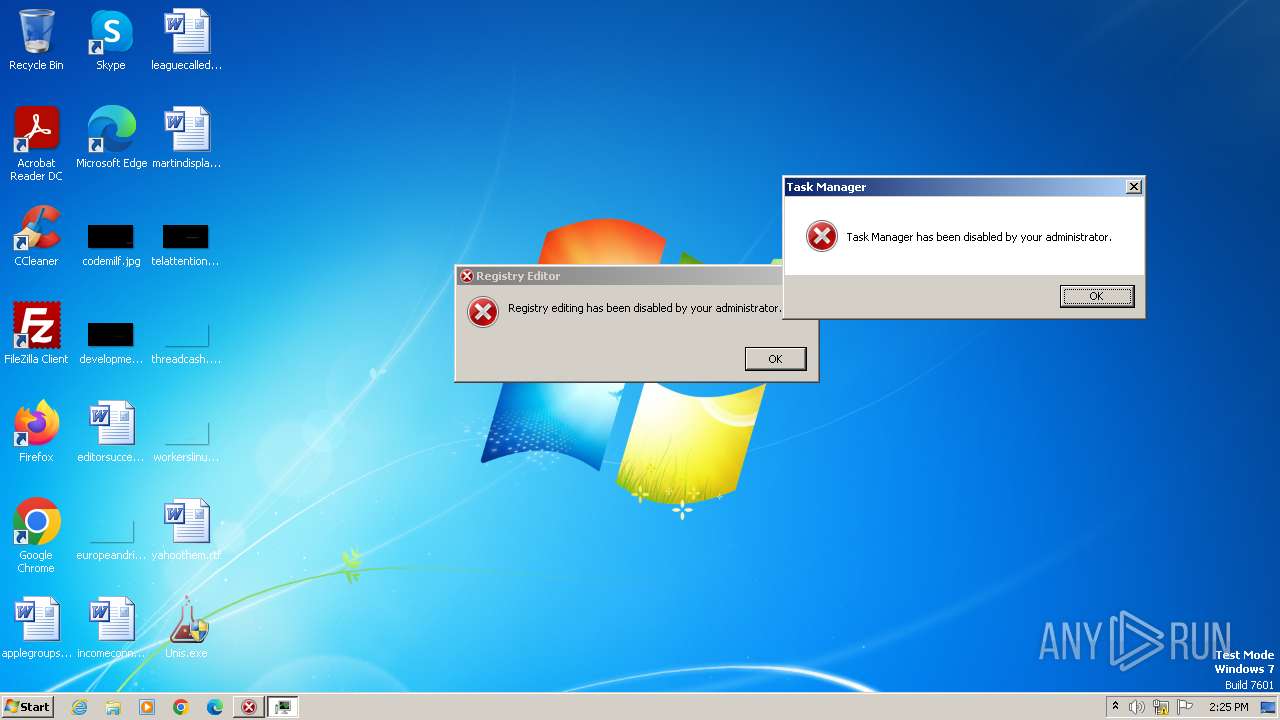
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1184)
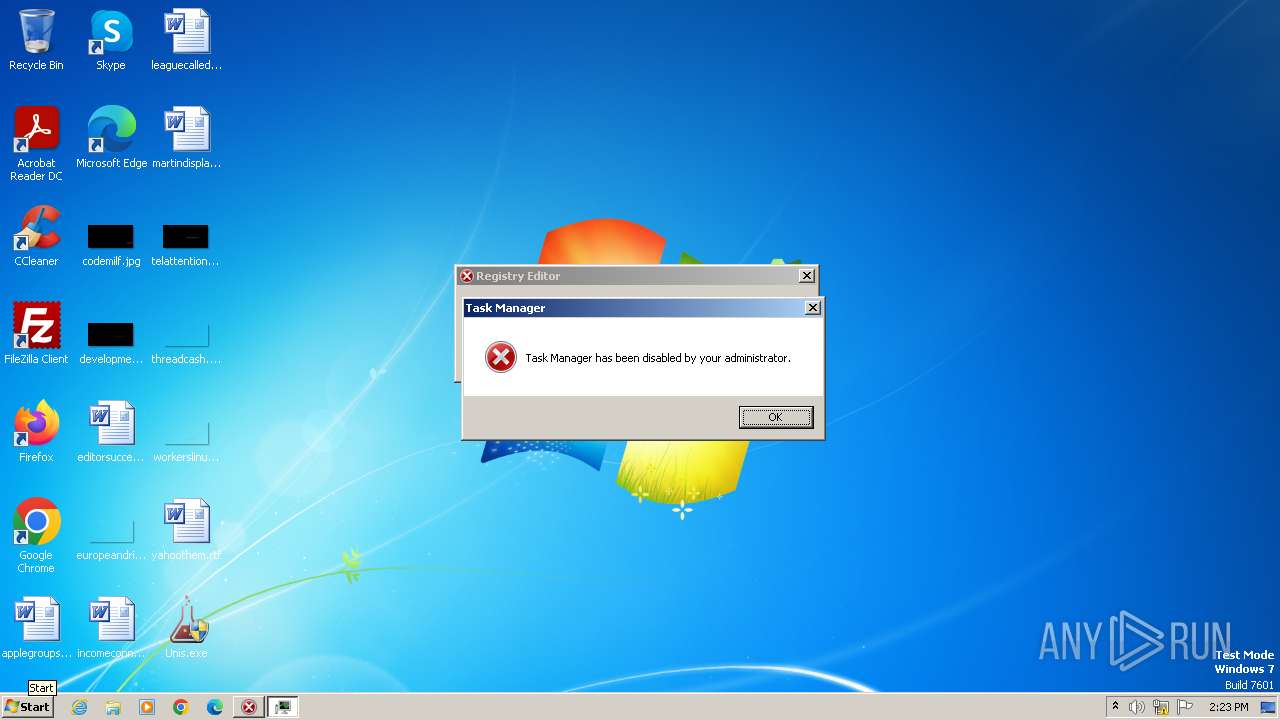
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1184)
INFO
Reads the computer name
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
Checks supported languages
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
- mbr.exe (PID: 1764)
Creates files or folders in the user directory
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
Create files in a temporary directory
- Unis.exe (PID: 2104)
- GoUnis.exe (PID: 2028)
- msdt.exe (PID: 2012)
Manual execution by a user
- regedit.exe (PID: 2236)
- regedit.exe (PID: 1132)
- taskmgr.exe (PID: 2328)
- explorer.exe (PID: 2656)
- msdt.exe (PID: 2012)
Reads security settings of Internet Explorer
- msdt.exe (PID: 2012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Win16/32 Executable Delphi generic (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:07:30 08:52:45+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 70656 |
| InitializedDataSize: | 842240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 3.6.5.4 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 3.6.5.4 |
| ProductVersion: | 4.2.2 |
| ProductName: | Unis |
| FileDescription: | Science |
| LegalCopyright: | Copyright © 2022 System64Intel |
Total processes
114
Monitored processes
52
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 524 | timeout /t 10 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 600 | taskkill /im gameyure.exe /f | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | timeout /t 25 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1060 | timeout /t 10 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1064 | "C:\Windows\system32\cmd" /c "C:\Users\admin\AppData\Local\Temp\4344.tmp\4345.tmp\4346.bat C:\Users\admin\Desktop\Unis.exe" | C:\Windows\System32\cmd.exe | — | Unis.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1112 | reg add "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System" /v "DisableTaskMgr" /t REG_DWORD /d "1" /f | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1132 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1184 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\667C.tmp\667D.tmp\667E.bat C:\Users\admin\AppData\Roaming\GoUnis.exe" | C:\Windows\System32\cmd.exe | GoUnis.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1628 | timeout /t 5 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1652 | timeout /t 10 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 332
Read events
3 314
Write events
18
Delete events
0
Modification events
| (PID) Process: | (2028) GoUnis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2028) GoUnis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2028) GoUnis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2028) GoUnis.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1112) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | DisableTaskMgr |
Value: 1 | |||
| (PID) Process: | (2204) reg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | disableregistrytools |
Value: 1 | |||
| (PID) Process: | (2012) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2012) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2012) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2012) msdt.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
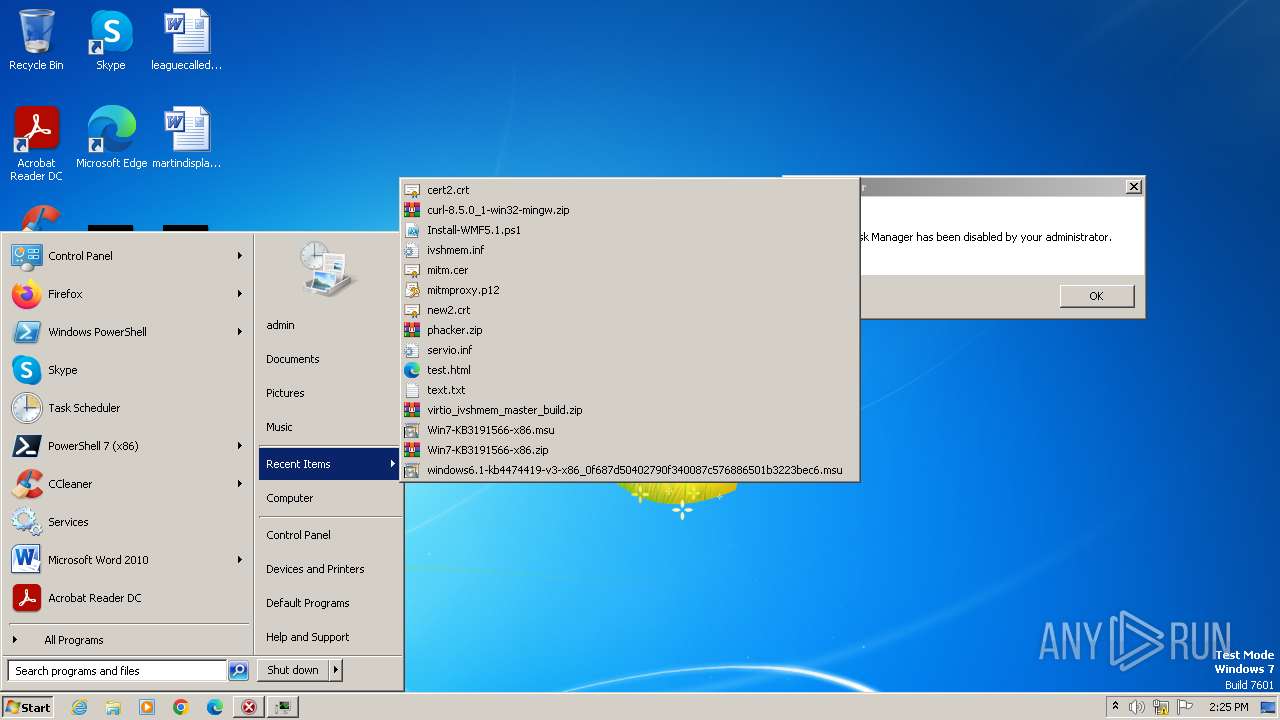
Executable files
32
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2104 | Unis.exe | C:\Users\admin\AppData\Local\Temp\4344.tmp\4345.tmp\4346.bat | text | |
MD5:C645904EFC201E9CC2660D251A08F3CB | SHA256:4E254EC30432A08D7A2A11ED188BD017FD555BD998C7233C1F444541FAC5001B | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\Application.exe | executable | |
MD5:785094FDEB43EAF43AE715662772A07F | SHA256:9943A45B24B708EBAD02A83E341165E5058BF69CB5B73A085CA45E857BEB9522 | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\Asterisk.exe | executable | |
MD5:232A57B4C032887A85CAC1E82E372C02 | SHA256:4753AD0F4174149BC8A68F57F9D0F2BF1F96047613A92136D7FBE9DF52516E3F | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\Block.exe | executable | |
MD5:BA78D9B2BCC0DF8A78BD3EC81ECFBA4A | SHA256:BE03DC7957DDE60B64B0D4E5D649C0C68647FABF8396ED66137A3181CEF17913 | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Local\Temp\667C.tmp\667D.tmp\667E.bat | text | |
MD5:28520D83631EC5C7B0FF87050628DEC5 | SHA256:80E2CA2B9A0DE0C06551D9B017475314D5DFC5C3F2E4777D7E54D7FB6002A29F | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\Error.exe | executable | |
MD5:55125DBA1C296FD625DD13F304BE9805 | SHA256:C377CF246D2704DCC824A524C756CAE264001A9D841CEA6A6A8FB78BC6BF088D | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\hikaru.exe | executable | |
MD5:28B5A314AAD4EE9F5EC2AAD0B53EB8B6 | SHA256:70C4274358116990F1490073B7F329AB2A47D2F54B515E3E3493CAA710DA1DD8 | |||
| 2104 | Unis.exe | C:\Users\admin\AppData\Roaming\GoUnis.exe | executable | |
MD5:85884CBDD3C559B1AD29842351C7B5B1 | SHA256:85EA504D09AFF70110DA72697F1252014CFDCB6B12142CDF301FDCCB9033D333 | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\hageRGB.exe | executable | |
MD5:C147F1C5F93C872182A69DCC222ED554 | SHA256:B446DD815EE9D23CEDDA8C08798041FE1FF52C0316B7FB701BE9AB341466839E | |||
| 2028 | GoUnis.exe | C:\Users\admin\AppData\Roaming\MouseWarning.exe | executable | |
MD5:984D42A8D0560AE444CCD4B5BEDFA21F | SHA256:3E363DA23D980894A490D4D5C6D5FBDB66E90A56AFED12E23BEA564237A687C9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |