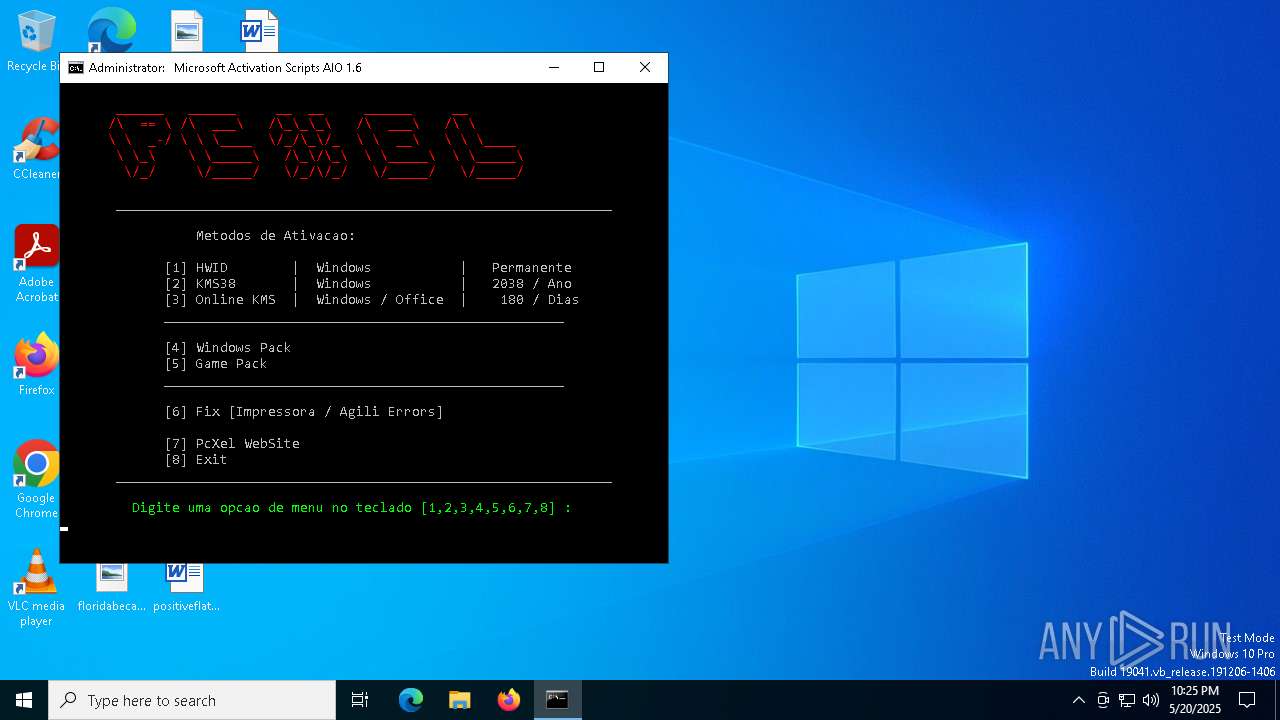
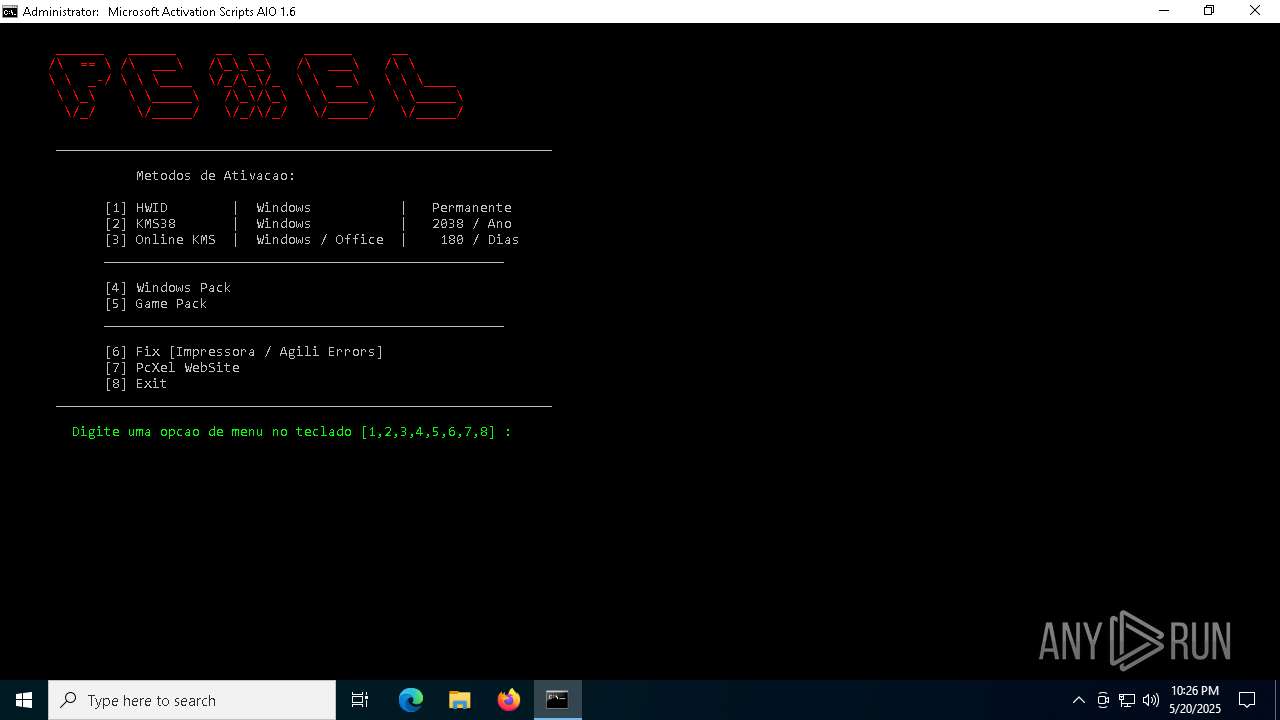
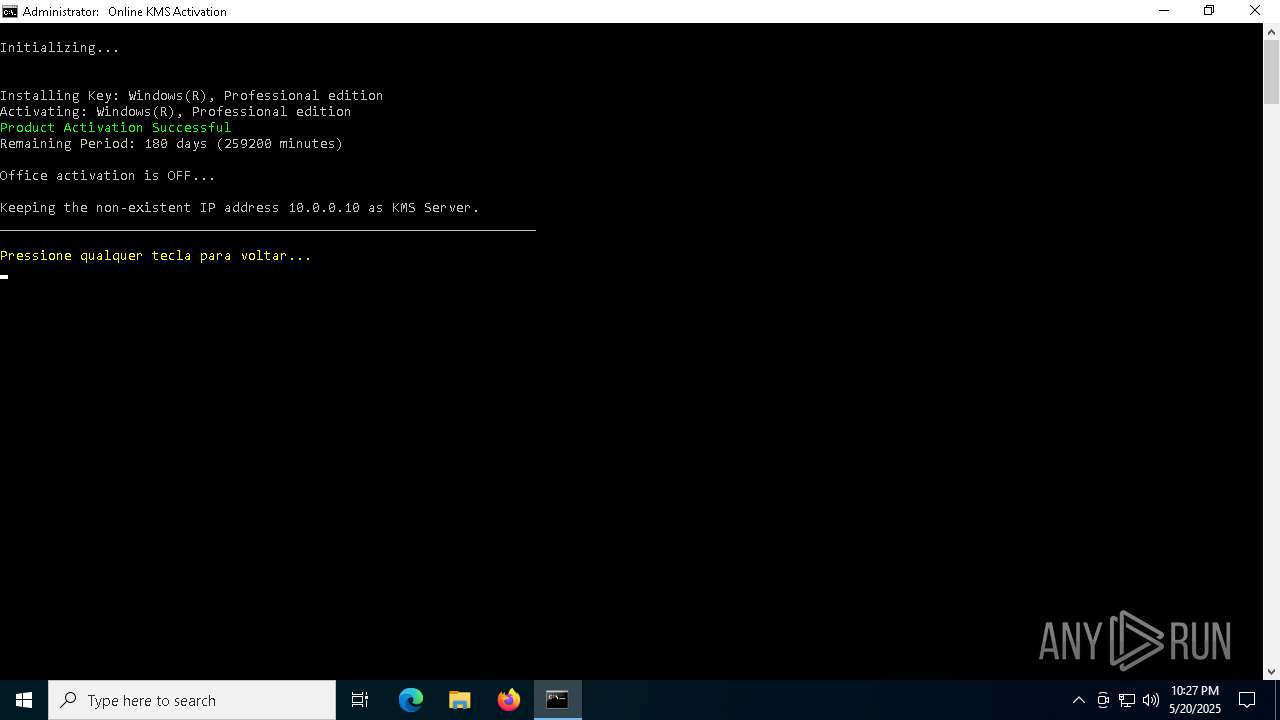
| File name: | MAS_AIO.cmd |
| Full analysis: | https://app.any.run/tasks/ac978fbe-eb95-4879-bbe7-26796cd34973 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2025, 22:25:48 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with very long lines (322), with CRLF line terminators |
| MD5: | C629E3FC83392E4BC921FFF9C4744ECD |
| SHA1: | 5FE666236F165A925967EF542B618AD297B747AF |
| SHA256: | D2D9A971593F588196FE6CE131B8E40FC23614B6AD833E76C8E9E6D5C8260A92 |
| SSDEEP: | 6144:6d94QImQ+5/T5ntq3kX1vT6lDrGtSNFX/QG+Dw3KWXbgu1p+fzGnFSQixBrSQ:6T4y5TDq4sDqKXl+E7XbnpPi3eQ |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 7572)
- net.exe (PID: 2240)
- net.exe (PID: 5344)
- net.exe (PID: 6632)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4996)
- cmd.exe (PID: 6108)
- powershell.exe (PID: 7260)
- cmd.exe (PID: 7572)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 5392)
Application launched itself
- cmd.exe (PID: 4996)
- cmd.exe (PID: 7732)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 7572)
- cmd.exe (PID: 5392)
Executing commands from ".cmd" file
- powershell.exe (PID: 7260)
- cmd.exe (PID: 6108)
- cmd.exe (PID: 7572)
Executing commands from a ".bat" file
- cmd.exe (PID: 6108)
- cmd.exe (PID: 7572)
- powershell.exe (PID: 7260)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6108)
- cmd.exe (PID: 7572)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7572)
- cmd.exe (PID: 6108)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7572)
Hides command output
- cmd.exe (PID: 8080)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 300)
- cmd.exe (PID: 3140)
- cmd.exe (PID: 1052)
- cmd.exe (PID: 680)
- cmd.exe (PID: 2800)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 7324)
- cmd.exe (PID: 2904)
- cmd.exe (PID: 5328)
- cmd.exe (PID: 7020)
- cmd.exe (PID: 8132)
Starts SC.EXE for service management
- cmd.exe (PID: 7572)
Windows service management via SC.EXE
- sc.exe (PID: 1280)
- sc.exe (PID: 632)
- sc.exe (PID: 6592)
- sc.exe (PID: 5960)
- sc.exe (PID: 1600)
- sc.exe (PID: 4152)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7572)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 3140)
- cmd.exe (PID: 4736)
- cmd.exe (PID: 7572)
- cmd.exe (PID: 7752)
- cmd.exe (PID: 7880)
- cmd.exe (PID: 7964)
- cmd.exe (PID: 7392)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7148)
- cmd.exe (PID: 7572)
The process executes VB scripts
- cmd.exe (PID: 7572)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 7672)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7672)
Connects to unusual port
- SppExtComObj.Exe (PID: 8036)
INFO
Checks operating system version
- cmd.exe (PID: 6108)
- cmd.exe (PID: 7572)
Starts MODE.COM to configure console settings
- mode.com (PID: 7904)
- mode.com (PID: 7328)
- mode.com (PID: 7000)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 2088)
- WMIC.exe (PID: 7828)
- WMIC.exe (PID: 6388)
- WMIC.exe (PID: 616)
- WMIC.exe (PID: 5408)
- WMIC.exe (PID: 4756)
- WMIC.exe (PID: 7336)
- WMIC.exe (PID: 4448)
- WMIC.exe (PID: 7548)
- WMIC.exe (PID: 7524)
- WMIC.exe (PID: 6468)
- WMIC.exe (PID: 5956)
- WMIC.exe (PID: 4528)
- cscript.exe (PID: 7672)
- WMIC.exe (PID: 7784)
- WMIC.exe (PID: 7792)
- WMIC.exe (PID: 7856)
- WMIC.exe (PID: 7980)
- WMIC.exe (PID: 6744)
- WMIC.exe (PID: 5376)
- WMIC.exe (PID: 6208)
- WMIC.exe (PID: 5984)
- WMIC.exe (PID: 1228)
- WMIC.exe (PID: 6404)
- WMIC.exe (PID: 456)
- WMIC.exe (PID: 6080)
- WMIC.exe (PID: 7316)
- WMIC.exe (PID: 4180)
- WMIC.exe (PID: 2316)
- WMIC.exe (PID: 8116)
- WMIC.exe (PID: 4452)
- WMIC.exe (PID: 904)
- WMIC.exe (PID: 864)
- WMIC.exe (PID: 7244)
- WMIC.exe (PID: 7388)
Checks supported languages
- mode.com (PID: 7328)
- mode.com (PID: 7000)
- mode.com (PID: 7904)
Reads Microsoft Office registry keys
- reg.exe (PID: 5228)
- reg.exe (PID: 2568)
- reg.exe (PID: 6132)
- reg.exe (PID: 5956)
- reg.exe (PID: 4152)
- reg.exe (PID: 8188)
- reg.exe (PID: 7920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
422
Monitored processes
281
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\WINDOWS\system32\cmd.exe /c REG QUERY "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing\Packages" /f "Microsoft-Windows-*Edition~31bf3856ad364e35" /k 2>nul | FIND /I "CurrentVersion" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | findstr /I /C:"O365BusinessRetail" "C:\WINDOWS\Temp\c2rchk.txt" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | wmic path SoftwareLicensingProduct where (ID='3f1afc82-f8ac-4f6c-8005-1d233e606eee') get LicenseStatus /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | UCPDMgr.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 516 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663" /f /v KeyManagementServiceName /t REG_SZ /d "124.223.166.218" /reg:32 | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | findstr /i "e0c42288-980c-4788-a014-c080d2e1926e" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | wmic path SoftwareLicensingProduct where (Description like '%KMSCLIENT%' ) get Name /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | sc query sppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\cmd.exe /c ECHO Microsoft-Windows-ProfessionalEdition~31bf3856ad364e35~amd64~~10.0.19041.4046 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform" /f /v KeyManagementServicePort /t REG_SZ /d "1688" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 997
Read events
27 968
Write events
22
Delete events
7
Modification events
| (PID) Process: | (5972) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\CurrentVersion\Software Protection Platform |
| Operation: | write | Name: | NoGenTicket |
Value: 1 | |||
| (PID) Process: | (5228) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 124.223.166.218 | |||
| (PID) Process: | (2568) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (5056) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 124.223.166.218 | |||
| (PID) Process: | (4488) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (6388) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663 |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (4408) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663 |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 124.223.166.218 | |||
| (PID) Process: | (516) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663 |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 124.223.166.218 | |||
| (PID) Process: | (4452) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\0ff1ce15-a989-479d-af46-f275c6370663 |
| Operation: | write | Name: | KeyManagementServicePort |
Value: 1688 | |||
| (PID) Process: | (8188) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform |
| Operation: | write | Name: | KeyManagementServiceName |
Value: 101.32.163.10 | |||
Executable files
0
Suspicious files
1
Text files
6
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1iooeqql.3g5.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7260 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tapvy5m0.ekb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_x3vwnqfb.ggy.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7976 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_3f5qgik2.yc4.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7260 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:D4280B15F1B5DB0CAC13AB6E6B1F70B4 | SHA256:B4CAF5B981C37E166CA184495C8D2CCC8685F4971E30DE9BD9F10AA306D0B84C | |||
| 7572 | cmd.exe | C:\Windows\Temp\slmgr.vbs | text | |
MD5:3903BCAB32A4A853DFA54962112D4D02 | SHA256:95FC646D222D324DB46F603A7F675C329FE59A567ED27FDAED2A572A19206816 | |||
| 7572 | cmd.exe | C:\Windows\Temp\c2rchk.txt | text | |
MD5:D57FBDD4D9B2D0BBACC4088E18EAF010 | SHA256:D4F290F488267D8076273CD57451947C2EAF895E6DDB28BD41F252955C236E8F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
48
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7648 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7648 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
win.kms.pub |
| unknown |