| File name: | Oden_PO2339.exe |
| Full analysis: | https://app.any.run/tasks/360448a1-5786-42b3-a8f8-d21c889eb05f |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2023, 07:49:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7CE47DEE0EF61A16D0811FBE451E02F2 |
| SHA1: | 3C7271B7AB2E80EF40BE568D7CD4C36A2212EC64 |
| SHA256: | D2D549D6DD5D017CE1B853932513EC389DE11E6443FE466487B2ED2E1528B857 |
| SSDEEP: | 49152:waeK3eJrsU//aUEORYXfXaIGoMT1QFt5NBcQMvyM88TJuHK8WMxeitSexEsat7OZ:waeKyN/aUEvXfXPt4ytPou8oHK8TIith |
MALICIOUS
Drops the executable file immediately after the start
- Oden_PO2339.exe (PID: 2544)
- zxfvzxvr.exe (PID: 388)
- drgsfszs.sfx.exe (PID: 2444)
- drgsfszs.exe (PID: 2148)
- zxfvzxvr.sfx.exe (PID: 1792)
WARZONE has been detected (YARA)
- mimages.exe (PID: 2044)
SUSPICIOUS
Reads the Internet Settings
- Oden_PO2339.exe (PID: 2544)
- zxfvzxvr.exe (PID: 388)
- drgsfszs.sfx.exe (PID: 2444)
- zxfvzxvr.sfx.exe (PID: 1792)
Executing commands from a ".bat" file
- zxfvzxvr.exe (PID: 388)
Starts CMD.EXE for commands execution
- zxfvzxvr.exe (PID: 388)
- Oden_PO2339.exe (PID: 2544)
Connects to unusual port
- mimages.exe (PID: 2044)
Executing commands from ".cmd" file
- Oden_PO2339.exe (PID: 2544)
INFO
Checks supported languages
- Oden_PO2339.exe (PID: 2544)
- drgsfszs.sfx.exe (PID: 2444)
- drgsfszs.exe (PID: 2148)
- drgsfszs.exe (PID: 1504)
- mimages.exe (PID: 2044)
- mimages.exe (PID: 3000)
- zxfvzxvr.sfx.exe (PID: 1792)
- zxfvzxvr.exe (PID: 388)
Reads the computer name
- Oden_PO2339.exe (PID: 2544)
- zxfvzxvr.sfx.exe (PID: 1792)
- zxfvzxvr.exe (PID: 388)
- drgsfszs.sfx.exe (PID: 2444)
- drgsfszs.exe (PID: 1504)
- drgsfszs.exe (PID: 2148)
- mimages.exe (PID: 3000)
- mimages.exe (PID: 2044)
Creates files or folders in the user directory
- Oden_PO2339.exe (PID: 2544)
- zxfvzxvr.sfx.exe (PID: 1792)
- drgsfszs.exe (PID: 2148)
Application launched itself
- chrome.exe (PID: 2996)
- drgsfszs.exe (PID: 1504)
- mimages.exe (PID: 3000)
The executable file from the user directory is run by the CMD process
- zxfvzxvr.sfx.exe (PID: 1792)
- drgsfszs.sfx.exe (PID: 2444)
Starts itself from another location
- zxfvzxvr.sfx.exe (PID: 1792)
- drgsfszs.exe (PID: 2148)
Create files in a temporary directory
- zxfvzxvr.exe (PID: 388)
- drgsfszs.sfx.exe (PID: 2444)
Reads the machine GUID from the registry
- drgsfszs.exe (PID: 1504)
- mimages.exe (PID: 3000)
The process uses the downloaded file
- chrome.exe (PID: 2484)
- chrome.exe (PID: 2800)
- chrome.exe (PID: 388)
Drops the executable file immediately after the start
- chrome.exe (PID: 2472)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
WarZone
(PID) Process(2044) mimages.exe
C2 (1)glotreobmoenry.sytes.net:5210
BuildIDT37PC1JH48
Options
Install FlagTrue
Install namemimages.exe
Startup FlagTrue
Startup nameMImages
Reverse Proxy local port5000
Offline logFalse
PersistanceFalse
UAC bypassFalse
Defender bypassFalse
Use ADSFalse
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:04:27 22:03:27+02:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 190976 |
| InitializedDataSize: | 71680 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1d759 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
70
Monitored processes
35
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Users\admin\AppData\Roaming\zxfvzxvr.exe" | C:\Users\admin\AppData\Roaming\zxfvzxvr.exe | — | zxfvzxvr.sfx.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 388 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3624 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 756 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1328 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1096 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1132 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:2 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1100 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2136 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1368 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3512 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1488 | "C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\112.300.200\software_reporter_tool.exe" --engine=2 --scan-locations=1,2,3,4,5,6,7,8,10 --disabled-locations=9,11 --session-id=B2i5awYBScXxNpEhuXJb+MuwnTKPHuJgt0ttZqME --registry-suffix=ESET | C:\Users\admin\AppData\Local\Google\Chrome\User Data\SwReporter\112.300.200\software_reporter_tool.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Integrity Level: MEDIUM Description: Software Reporter Tool Exit code: 3221225785 Version: 112.300.200 Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\AppData\Local\Temp\drgsfszs.exe" | C:\Users\admin\AppData\Local\Temp\drgsfszs.exe | — | drgsfszs.sfx.exe | |||||||||||
User: admin Company: Vopth View Vitch Integrity Level: MEDIUM Description: Vopth View Exit code: 0 Version: 9.8.8.8 Modules
| |||||||||||||||
| 1644 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3696 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:8 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1644 | "C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --mojo-platform-channel-handle=3720 --field-trial-handle=1248,i,1687315606856097483,14012608080577865884,131072 /prefetch:1 | C:\Program Files (x86)\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
6 756
Read events
6 628
Write events
127
Delete events
1
Modification events
| (PID) Process: | (2544) Oden_PO2339.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2544) Oden_PO2339.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2544) Oden_PO2339.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2544) Oden_PO2339.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2996) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1792) zxfvzxvr.sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1792) zxfvzxvr.sfx.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
9
Suspicious files
114
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF108280.TMP | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C7925A6B262C5676D1C36638981A6EA | SHA256:07F6FB1E9CBCE4D15C00A9FBF9A95C1F31DE20C4C48B433198862E8759CD128D | |||
| 2544 | Oden_PO2339.exe | C:\Users\admin\AppData\Roaming\zxfvzxvr.sfx.exe | executable | |
MD5:2ED7448479CC04EB63F750814199AE6F | SHA256:74BD13647CE1BC6B000510E88DC437403AD83483F9A12757F980B2D98170967F | |||
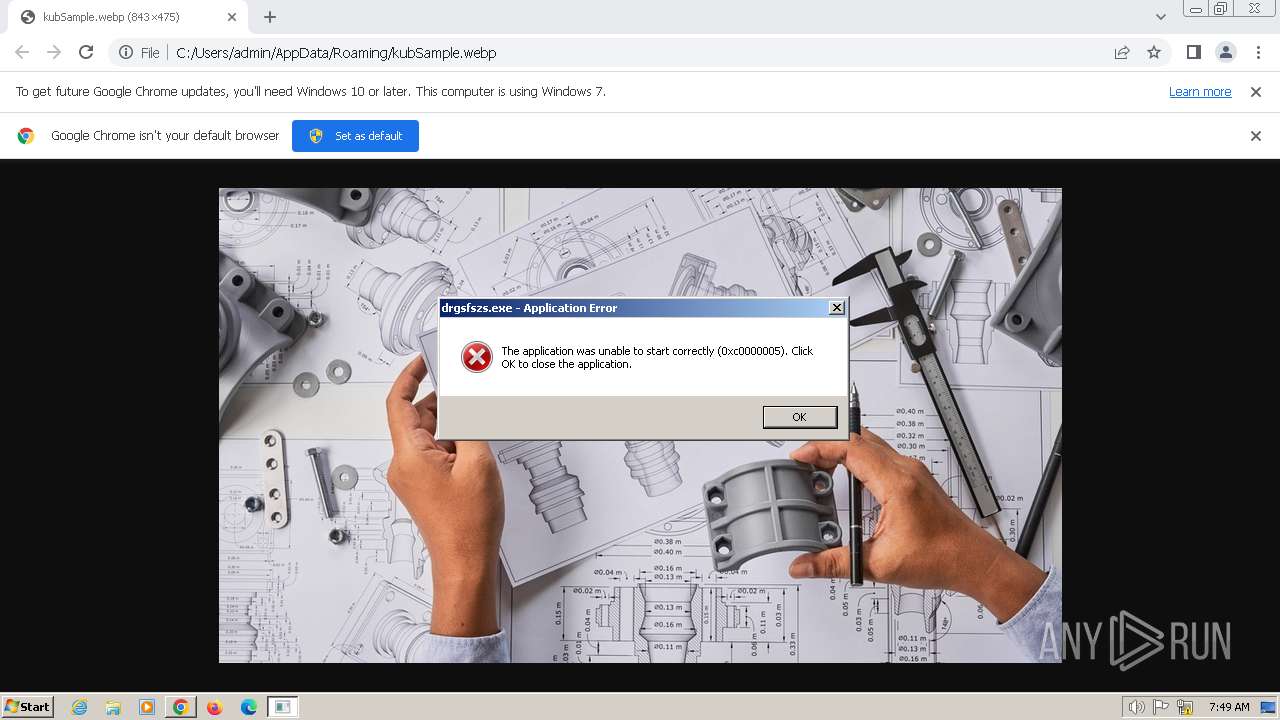
| 2544 | Oden_PO2339.exe | C:\Users\admin\AppData\Roaming\kubSample.webp | image | |
MD5:550C8AD1E9FA820795B6087624C05BD4 | SHA256:520F8F4599399887EAA61010D27F48036611F1D4410D199E929BB4B6D9ACB9AC | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF1083a9.TMP | text | |
MD5:83DFA02A36C9307E698CB66E868BF1B6 | SHA256:— | |||
| 2996 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 2544 | Oden_PO2339.exe | C:\Users\admin\AppData\Roaming\hycxhxtr.cmd | text | |
MD5:29E365C43A5C339CF02E30A520EDAC31 | SHA256:347AE171E7BD0F8AAC406AD585C241FA76E54FEC61CD6DB92F5071108ECE58EB | |||
| 388 | zxfvzxvr.exe | C:\Users\admin\AppData\Local\Temp\hjbhsfhxtr.bat | text | |
MD5:3F149C4F4A1996114DA1D147B7CD5989 | SHA256:595DCFB1DF46752EA2F0BE4B75E2770397BFEF329D19E2D471871BDC6D5A74BC | |||
| 1792 | zxfvzxvr.sfx.exe | C:\Users\admin\AppData\Roaming\zxfvzxvr.exe | executable | |
MD5:2A0C5B7AF46C1EA79907CD7957C4779C | SHA256:F1B234DA3066573E18CE57C1DEE3B4B4DFA3D152268FC5544D9F5CC0F52F17E2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
45
DNS requests
50
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | — | — | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 10.1 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 5.64 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 9.88 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 10.0 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 44.5 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 21.4 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 90.5 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 181 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ncrr3jrkc3nerq4tdp7lehlppe_112.300.200/gkmgaooipdjhmangpemjhigmamcehddo_112.300.200_win64_nrpvirsu5aw3cszevrlqbmhv34.crx3 | unknown | binary | 342 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1220 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
352 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
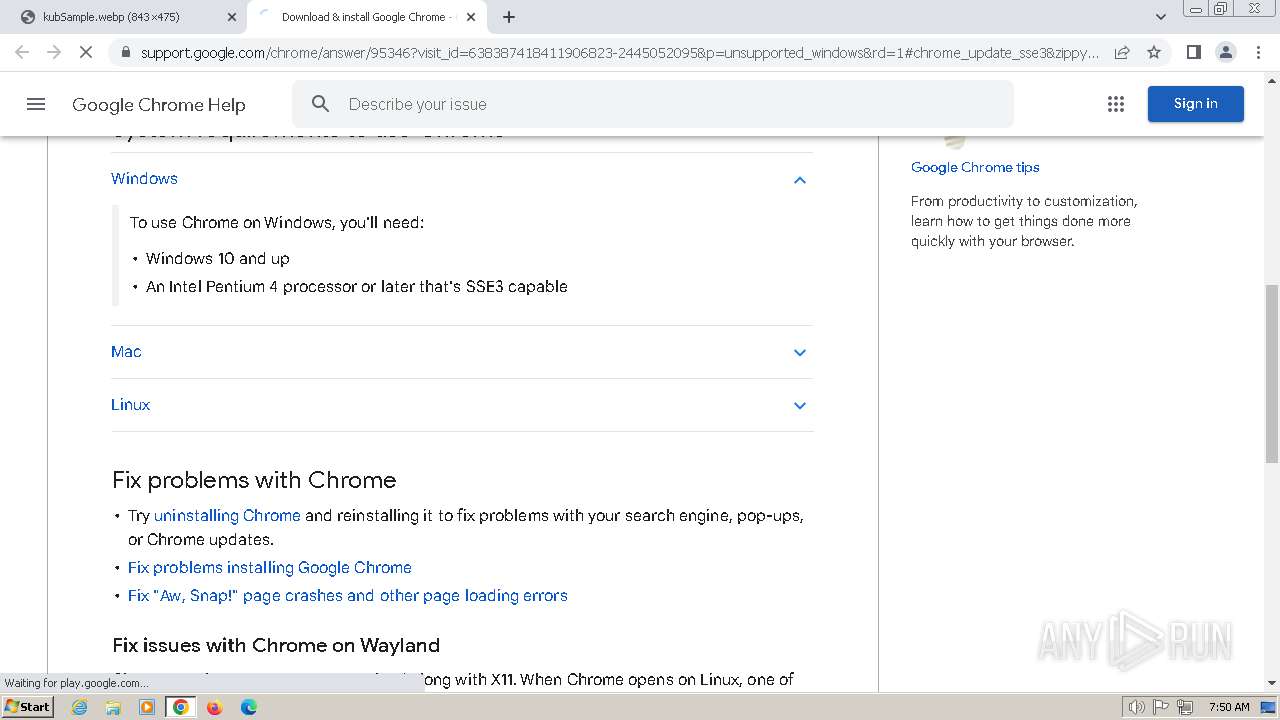
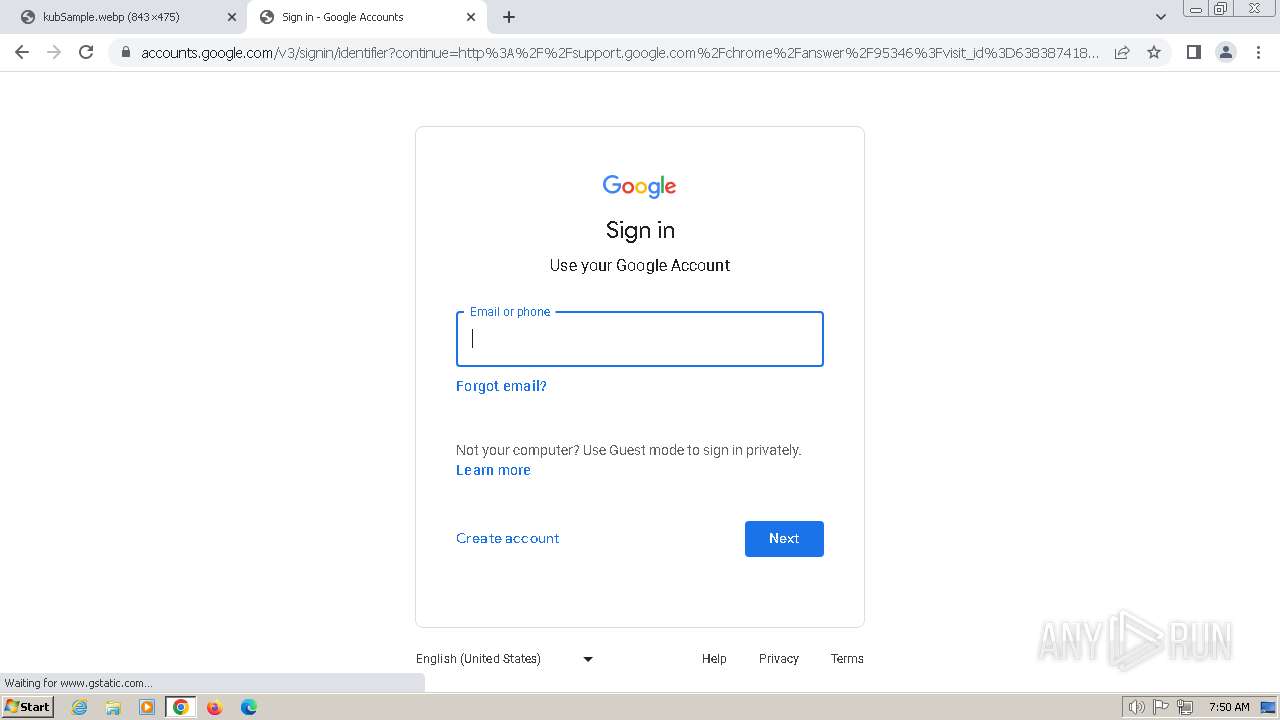
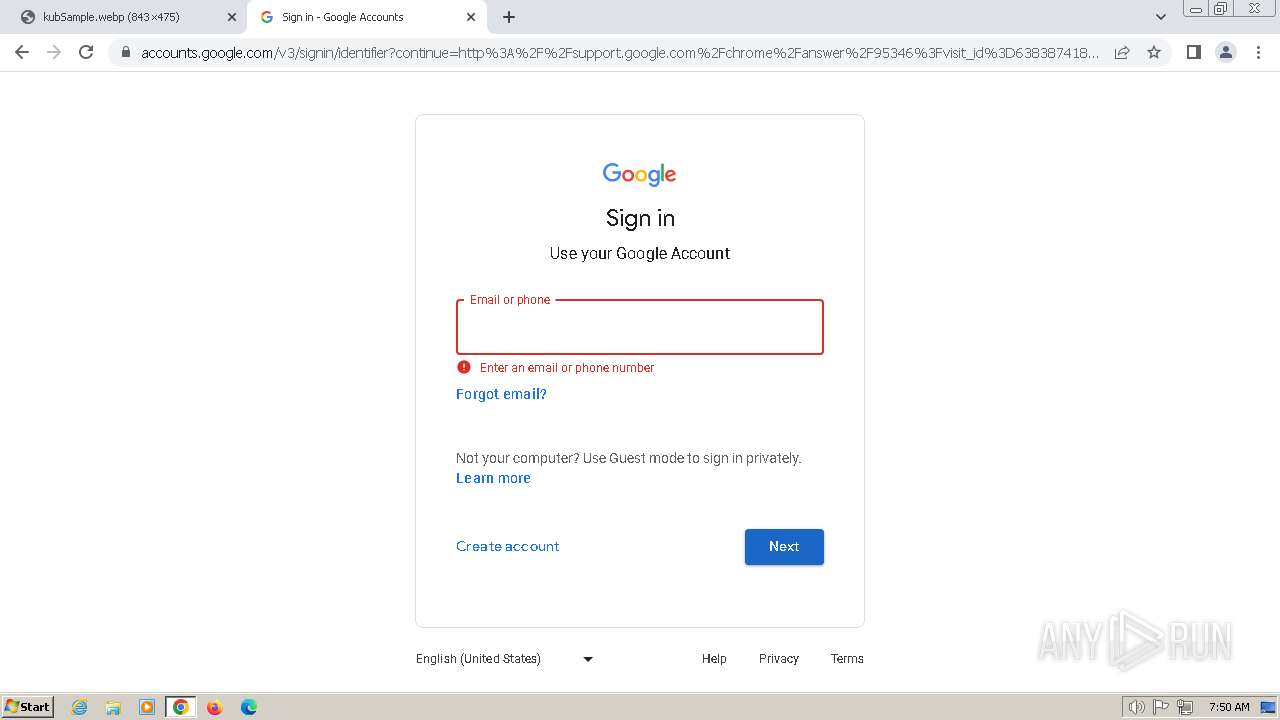
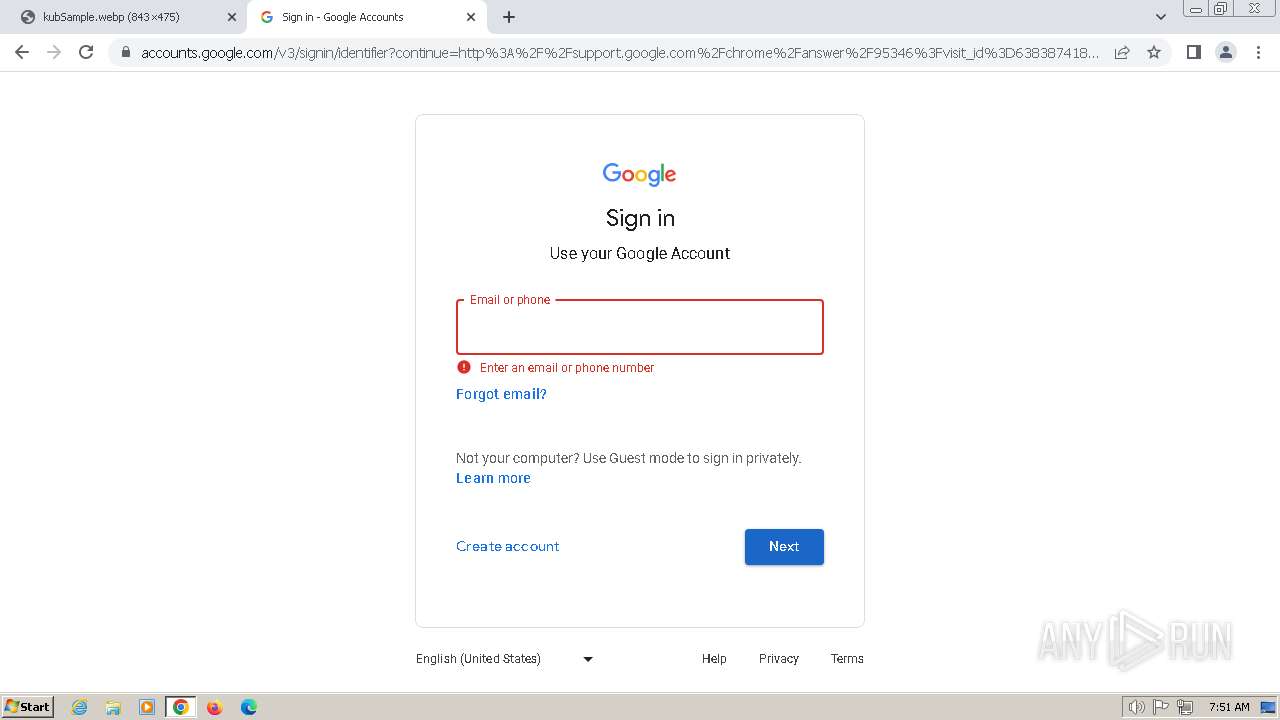
2136 | chrome.exe | 172.217.23.99:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2996 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2136 | chrome.exe | 173.194.76.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2996 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
2136 | chrome.exe | 142.250.186.67:443 | update.googleapis.com | GOOGLE | US | whitelisted |
2044 | mimages.exe | 91.92.252.239:5210 | glotreobmoenry.sytes.net | — | BG | malicious |
2136 | chrome.exe | 142.250.185.170:443 | optimizationguide-pa.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
update.googleapis.com |
| whitelisted |
glotreobmoenry.sytes.net |
| unknown |
optimizationguide-pa.googleapis.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
support.google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
352 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.sytes.net Domain |
352 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.sytes.net Domain |