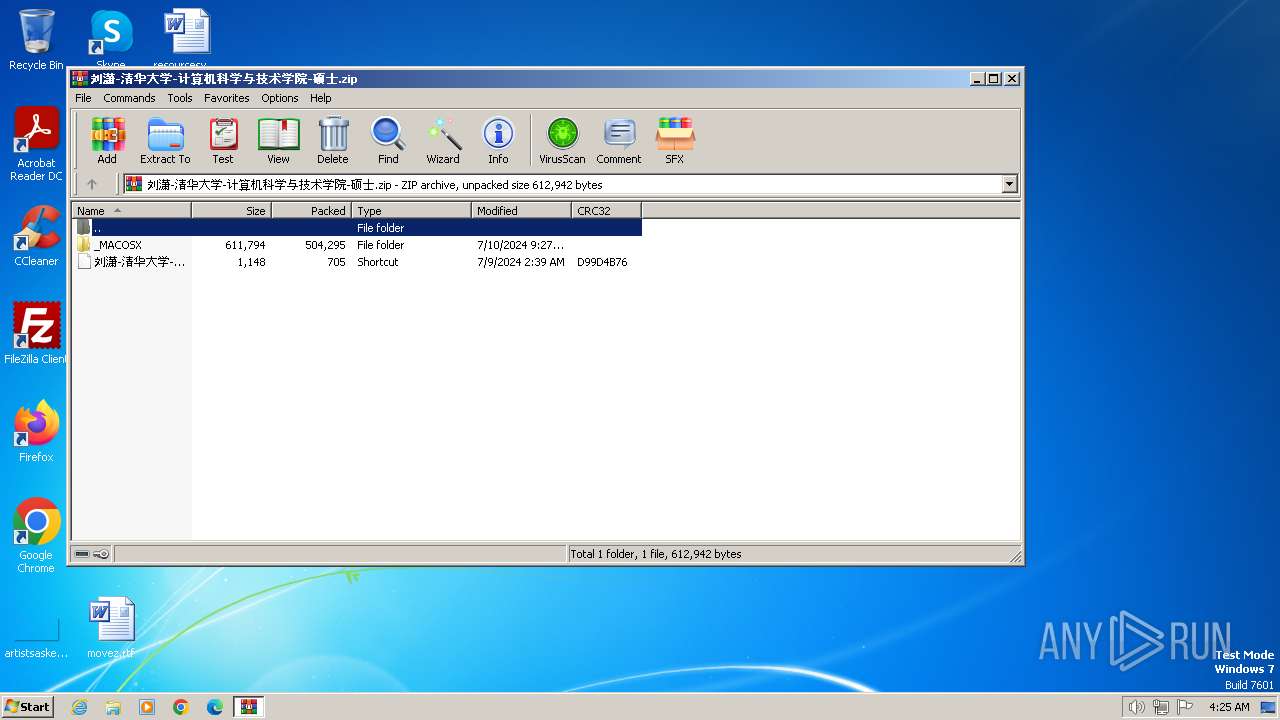
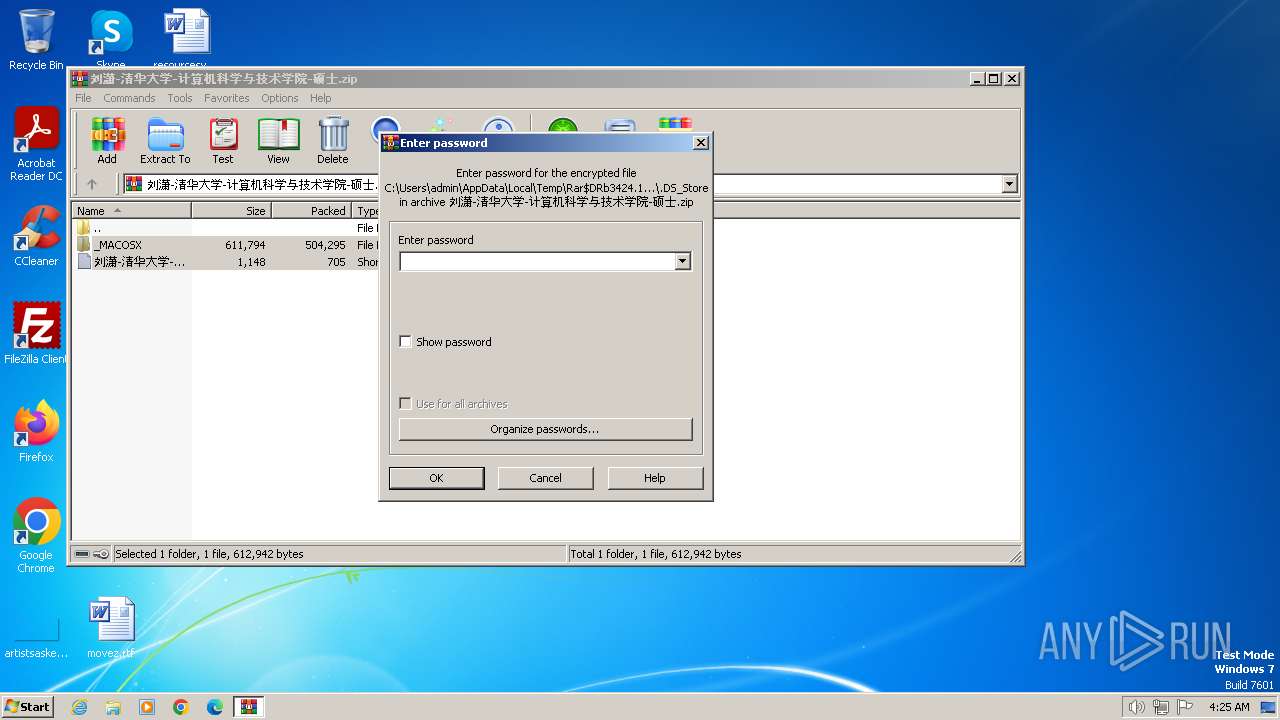
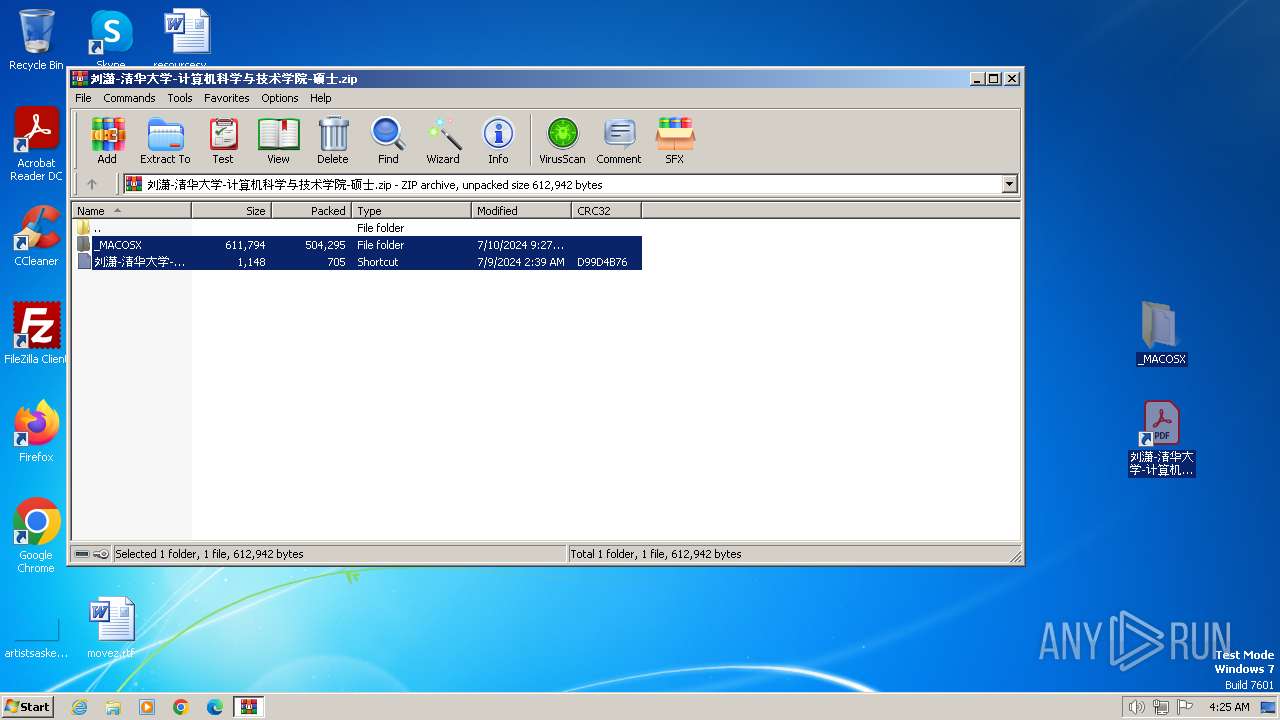
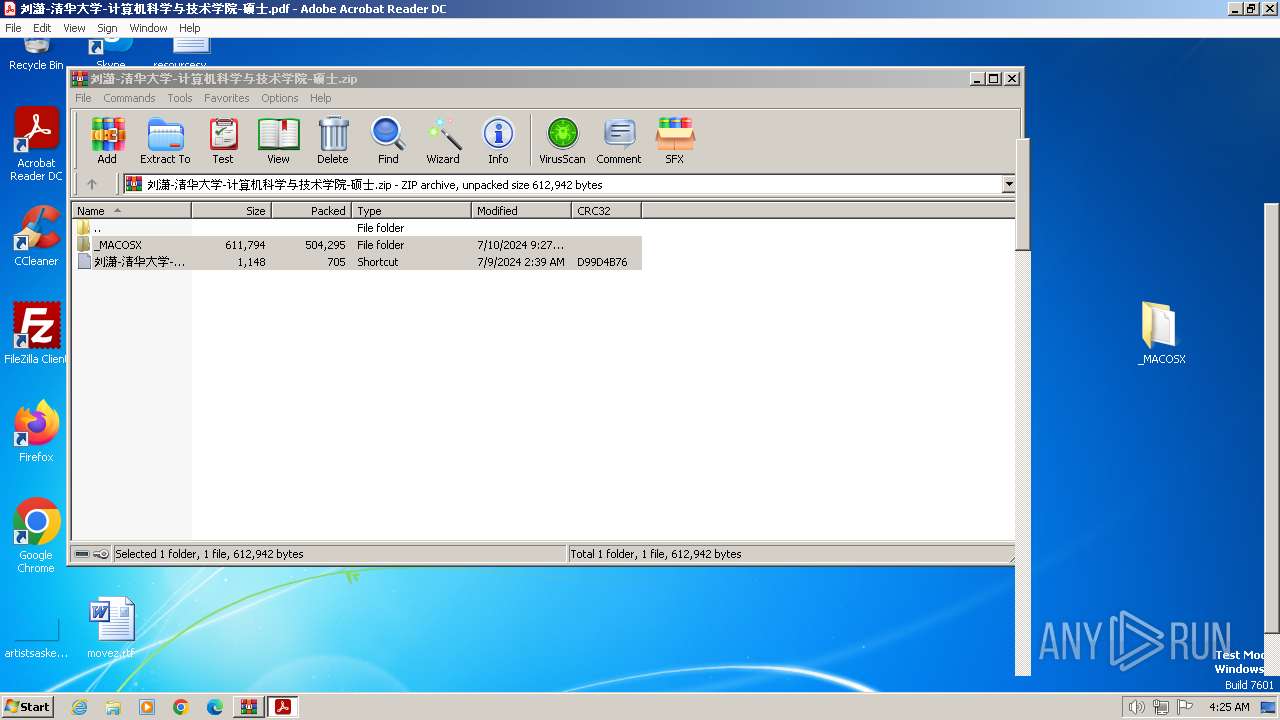
| File name: | 刘潇-清华大学-计算机科学与技术学院-硕士.zip |
| Full analysis: | https://app.any.run/tasks/ff7c7d4b-b98e-4079-abd1-2e4a134e2ed7 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2024, 03:25:14 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | B3117480E2342754E8CD49C6BC8314FB |
| SHA1: | 3F7E362B9B352FEDE8722D9C044FFF73D422B8E4 |
| SHA256: | D2C9CA5E3453E1F95AFFA57D41FF5EEBA4CDC90ED0D087D63FBF7F41DFF6C4C8 |
| SSDEEP: | 24576:/XnMfCS0q96i6DKoiZldV9cO7oxNSHE2Lr2F/wQ++EK/FPtap2feAw:/XnMfCS0q96i6DKoiZldV9cO7oHSHE29 |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3424)
Deletes a file (SCRIPT)
- cscript.exe (PID: 3708)
Copies file to a new location (SCRIPT)
- cscript.exe (PID: 3708)
Gets path to any of the special folders (SCRIPT)
- cscript.exe (PID: 3708)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 3424)
- cscript.exe (PID: 3708)
Creates file in the systems drive root
- AcroRd32.exe (PID: 1504)
Runs shell command (SCRIPT)
- cscript.exe (PID: 3708)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 3708)
Starts a Microsoft application from unusual location
- DS_Store.exe (PID: 2944)
Reads the Internet Settings
- cscript.exe (PID: 3708)
Executable content was dropped or overwritten
- cscript.exe (PID: 3708)
INFO
Reads security settings of Internet Explorer
- cscript.exe (PID: 3708)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3424)
Application launched itself
- AcroRd32.exe (PID: 2960)
- RdrCEF.exe (PID: 3364)
Reads Microsoft Office registry keys
- AcroRd32.exe (PID: 1504)
Create files in a temporary directory
- cscript.exe (PID: 3708)
Manual execution by a user
- cscript.exe (PID: 3708)
Drops the executable file immediately after the start
- cscript.exe (PID: 3708)
- RdrCEF.exe (PID: 3364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:07:10 16:27:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | _MACOSX/ |
Total processes
53
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,4524045870407399940,11302791498747551630,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=17185519566028671215 --mojo-platform-channel-handle=1188 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,4524045870407399940,11302791498747551630,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=15706667549525014358 --mojo-platform-channel-handle=1256 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1504 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Desktop\刘潇-清华大学-计算机科学与技术学院-硕士.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,4524045870407399940,11302791498747551630,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=4678032298490957663 --mojo-platform-channel-handle=1256 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2556 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1180,4524045870407399940,11302791498747551630,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16050396749110078752 --renderer-client-id=7 --mojo-platform-channel-handle=1440 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2944 | "C:\Users\admin\Desktop\_MACOSX\_MACOSX\DS_Store.exe" | C:\Users\admin\Desktop\_MACOSX\_MACOSX\DS_Store.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Character Map Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 2960 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\刘潇-清华大学-计算机科学与技术学院-硕士.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | cscript.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3364 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3424 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\刘潇-清华大学-计算机科学与技术学院-硕士.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3708 | "C:\Windows\System32\cscript.exe" _MACOSX\_MACOSX\DS_Store.vbs | C:\Windows\System32\cscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
18 271
Read events
18 175
Write events
85
Delete events
11
Modification events
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\刘潇-清华大学-计算机科学与技术学院-硕士.zip | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3424) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
3
Suspicious files
146
Text files
4
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3364 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3424.13808\_MACOSX\_MACOSX\DS_Store | executable | |
MD5:D8C348A2F27097D8689DBA4452BB76EB | SHA256:0ACEEB78564FB2B7BC93748CEBFA860198F390CAFBE671DC9123492CAADF0575 | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3424.13808\_MACOSX\.DS_Store | ds_store | |
MD5:6FB19F5FF7CB0EB696D6EC07E3E8D01E | SHA256:0A4B272064C9F8708B5B2BDF4FDEA0C9E5153DE4914A36653B16F0369BBEA8B4 | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3424.13808\_MACOSX\_MACOSX\刘潇-清华大学-计算机科学与技术学院-硕士.pdf | ||
MD5:154BF965C1C8E54540179B2D01C4202E | SHA256:D2E19495006C53C00B307BD29863A737EB041C0BEEED27D7FB45424F5AFD2601 | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3424.13808\刘潇-清华大学-计算机科学与技术学院-硕士.pdf.lnk | lnk | |
MD5:41B5D5A04CF4534550E6AC3FC9A8F42D | SHA256:2477DD3BD6D895399C7B94852C770933A0786CEC9DF6A511444B154B72D7BF7F | |||
| 3708 | cscript.exe | C:\Users\admin\Desktop\_MACOSX\_MACOSX\DS_Store.exe | executable | |
MD5:D8C348A2F27097D8689DBA4452BB76EB | SHA256:0ACEEB78564FB2B7BC93748CEBFA860198F390CAFBE671DC9123492CAADF0575 | |||
| 3708 | cscript.exe | C:\Users\admin\Desktop\刘潇-清华大学-计算机科学与技术学院-硕士.pdf | ||
MD5:154BF965C1C8E54540179B2D01C4202E | SHA256:D2E19495006C53C00B307BD29863A737EB041C0BEEED27D7FB45424F5AFD2601 | |||
| 3364 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:053D6F7CA7AF49D10D3926ABF6EBC541 | SHA256:4AC27FB865E1F3A6F0BB2431915F972634A6B6F24D37D80D3AEA99294E6EB1B8 | |||
| 3708 | cscript.exe | C:\Users\admin\AppData\Local\Temp\DS_Store.exe | executable | |
MD5:D8C348A2F27097D8689DBA4452BB76EB | SHA256:0ACEEB78564FB2B7BC93748CEBFA860198F390CAFBE671DC9123492CAADF0575 | |||
| 3424 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3424.13808\_MACOSX\_MACOSX\DS_Store.vbs | text | |
MD5:3B573C2229B43BDE50F998F6CBA17F2F | SHA256:3FD2911BE889F4FF2C00D08C8546C8BA921CF8A0996520F82D9096E8879B2243 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
22
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 87.248.204.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2b2cfb908ae71288 | unknown | — | — | unknown |
2960 | AcroRd32.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1372 | svchost.exe | 87.248.204.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
1372 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
3364 | RdrCEF.exe | 184.30.16.138:443 | geo2.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |