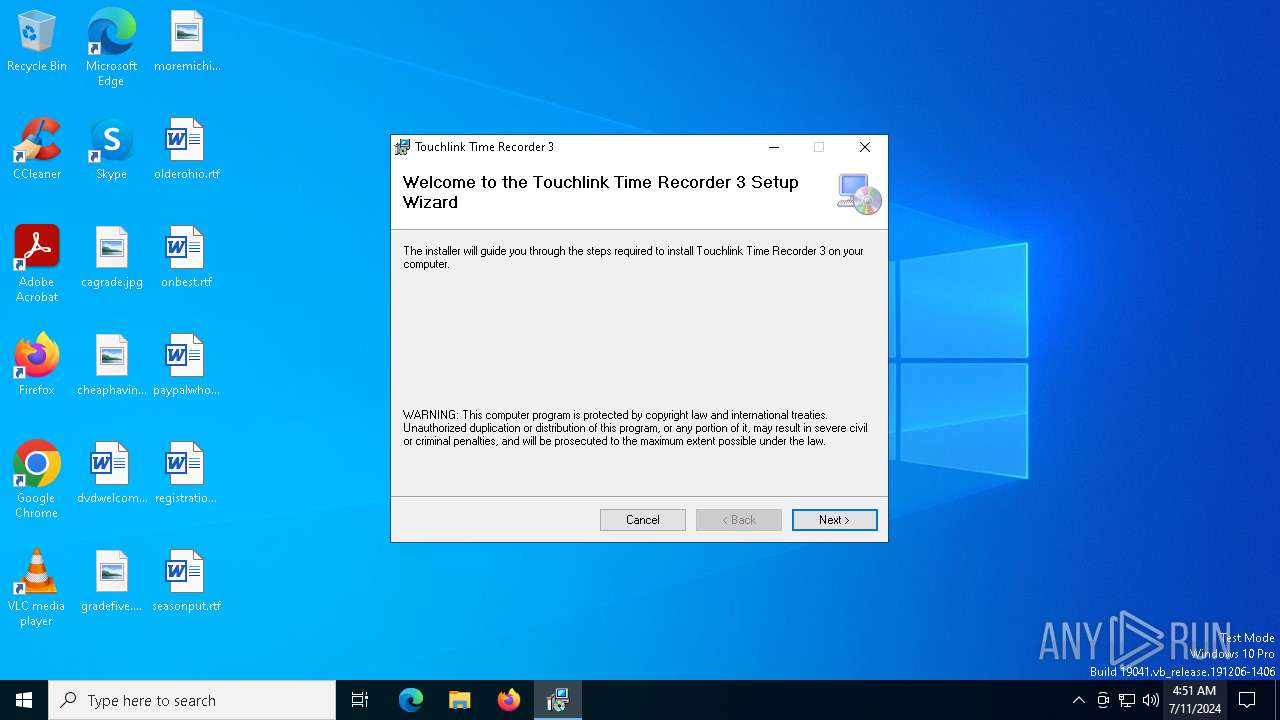
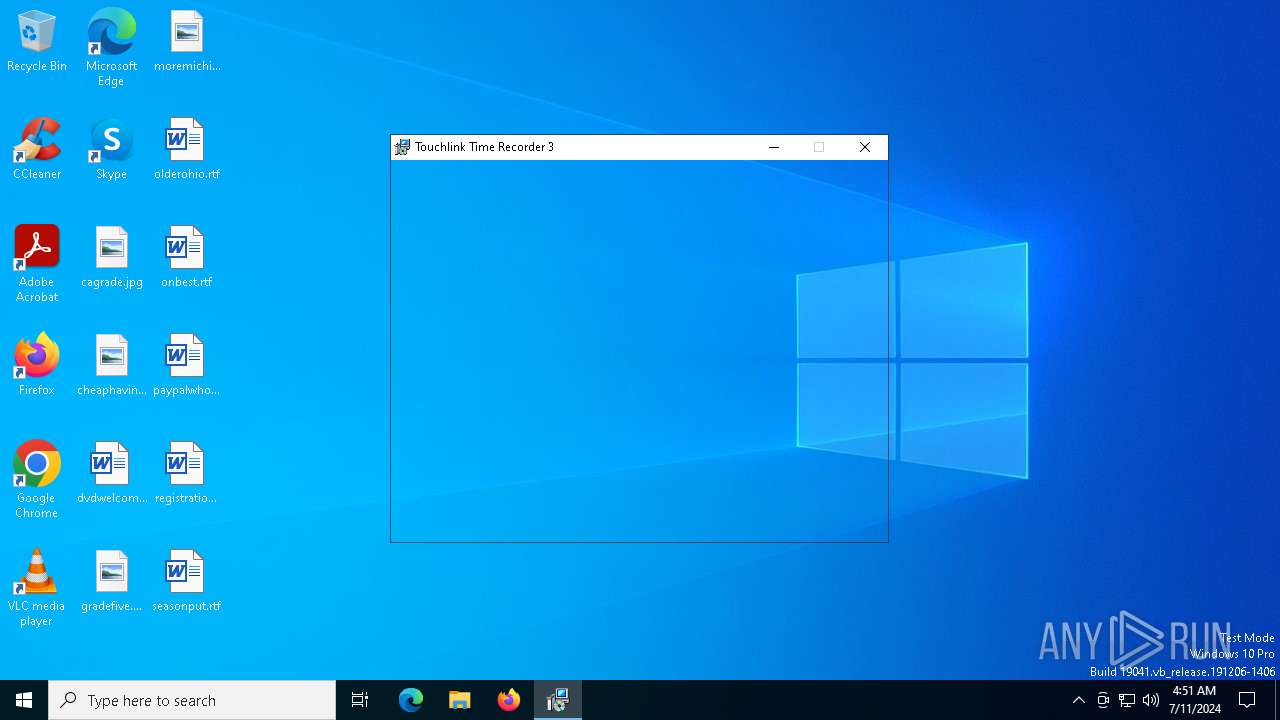
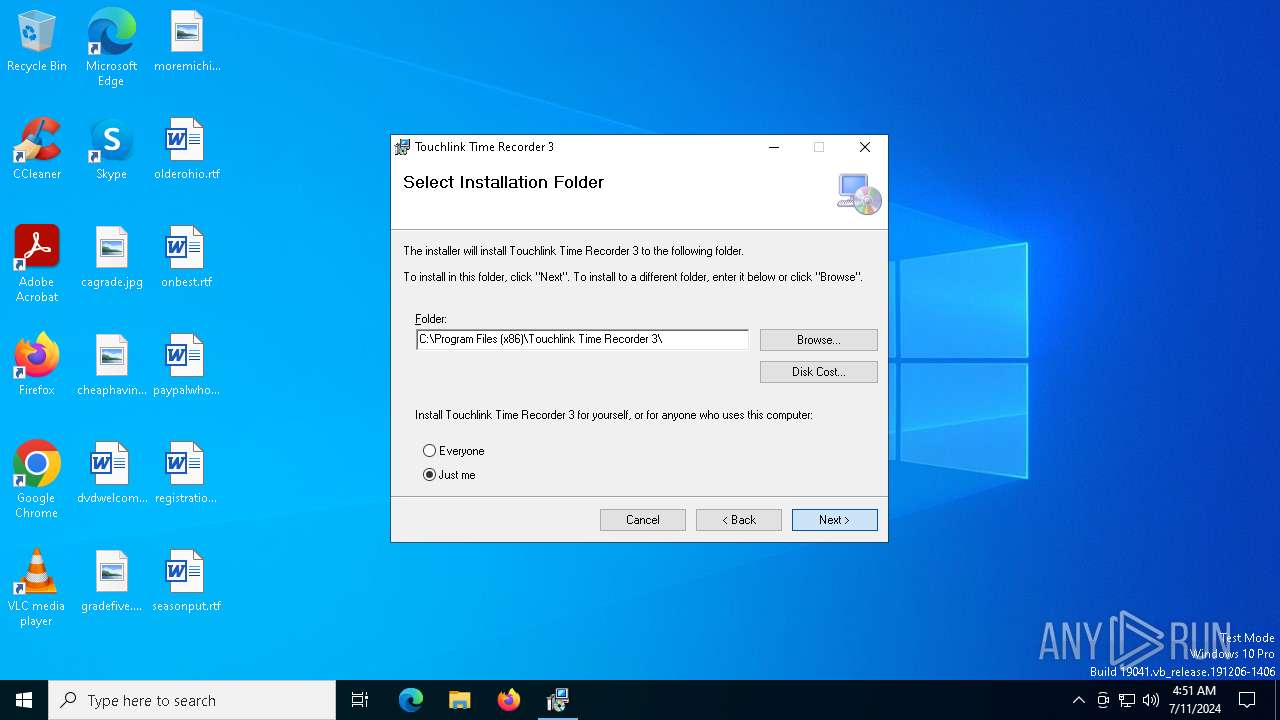
| File name: | TRSetup-Standard.msi |
| Full analysis: | https://app.any.run/tasks/7c7847dc-e2d6-4b12-ac9e-a518611e3194 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2024, 04:51:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: Intel;1033, Number of Pages: 200, Revision Number: {F49C6B4D-7C4A-4AA3-B532-4903E4DA93CC}, Title: Touchlink Time Recorder 3, Author: Mysolutions, Number of Words: 2, Last Saved Time/Date: Wed Jun 21 02:03:43 2017, Last Printed: Wed Jun 21 02:03:43 2017 |
| MD5: | BF8AEAC6A85E2326538628AE1C563F93 |
| SHA1: | 9EC75783BFFAEEE4B37AA6BB65991A8E86323D30 |
| SHA256: | D2B6F82E817403C0EF1CF7A4A136BACDDFB9AFD349D83B4F43637F01D18FDAFA |
| SSDEEP: | 98304:EWh1H143RqWgjHYjFcaED6YFvkHHHvVMrXdadYtuo8mK5KC/97r2YdlPn2rkGfRo:fyVNpq+5tek+44h2M |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 2916)
- msiexec.exe (PID: 2208)
- MSI54FB.tmp (PID: 3516)
- MSI54FB.tmp (PID: 1272)
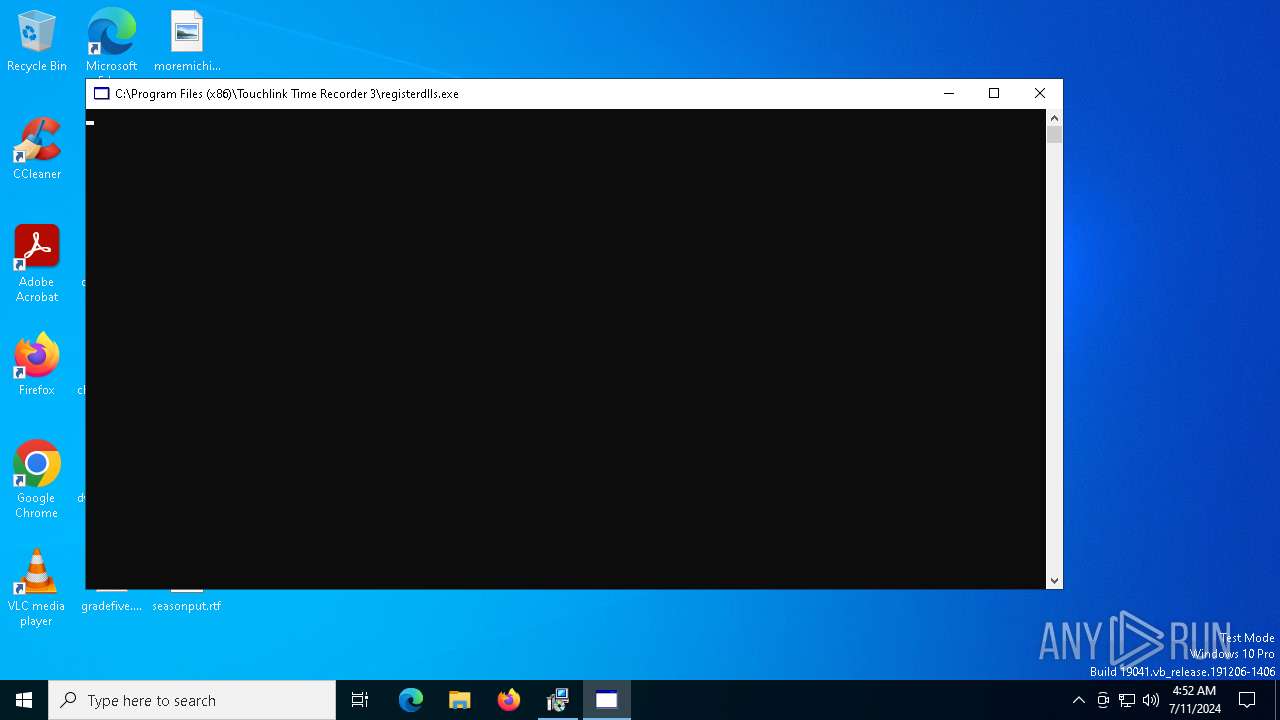
Registers / Runs the DLL via REGSVR32.EXE
- registerdlls.exe (PID: 6944)
- MSI54FB.tmp (PID: 1272)
Starts NET.EXE for service management
- net.exe (PID: 6780)
- MSI54FB.tmp (PID: 1272)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 2916)
- msiexec.exe (PID: 2208)
- MSI54FB.tmp (PID: 1272)
Executes as Windows Service
- VSSVC.exe (PID: 6852)
- iZHost.exe (PID: 6320)
Executable content was dropped or overwritten
- MSI54FB.tmp (PID: 3516)
- MSI54FB.tmp (PID: 1272)
- rundll32.exe (PID: 6536)
Drops a system driver (possible attempt to evade defenses)
- MSI54FB.tmp (PID: 1272)
- rundll32.exe (PID: 6536)
INFO
Reads the software policy settings
- msiexec.exe (PID: 2916)
Checks supported languages
- msiexec.exe (PID: 2208)
- msiexec.exe (PID: 2416)
Reads the computer name
- msiexec.exe (PID: 2208)
- msiexec.exe (PID: 2416)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2916)
Create files in a temporary directory
- msiexec.exe (PID: 2416)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2916)
- msiexec.exe (PID: 2208)
Creates files or folders in the user directory
- msiexec.exe (PID: 2916)
Starts application with an unusual extension
- msiexec.exe (PID: 2208)
Checks proxy server information
- msiexec.exe (PID: 2916)
Drops the executable file immediately after the start
- rundll32.exe (PID: 6536)
Manual execution by a user
- TAMain.exe (PID: 6812)
- TAMain.exe (PID: 6956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (90.2) |
|---|---|---|
| .msp | | | Windows Installer Patch (8.4) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1033 |
| Pages: | 200 |
| RevisionNumber: | {F49C6B4D-7C4A-4AA3-B532-4903E4DA93CC} |
| Title: | Touchlink Time Recorder 3 |
| Subject: | - |
| Author: | Mysolutions |
| Keywords: | - |
| Comments: | - |
| Words: | 2 |
| ModifyDate: | 2017:06:21 02:03:43 |
| LastPrinted: | 2017:06:21 02:03:43 |
Total processes
171
Monitored processes
37
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 740 | C:\WINDOWS\system32\net1 start "iZHost" | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Net Command Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\FPSensor\bin\DPDevAgt.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | MSI54FB.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Users\admin\AppData\Local\Temp\is-5PNQH.tmp\MSI54FB.tmp" /SL5="$50334,5626898,54272,C:\WINDOWS\Installer\MSI54FB.tmp" /Commit | C:\Users\admin\AppData\Local\Temp\is-5PNQH.tmp\MSI54FB.tmp | MSI54FB.tmp | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: Setup/Uninstall Version: 51.52.0.0 Modules
| |||||||||||||||
| 1388 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\biokey.ocx" | C:\Windows\SysWOW64\regsvr32.exe | — | MSI54FB.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\WINDOWS\system32\zkonline.ocx" | C:\Windows\SysWOW64\regsvr32.exe | — | MSI54FB.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2208 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2416 | C:\Windows\syswow64\MsiExec.exe -Embedding 4D38405DAA095EC91F7B5239520A873B C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2652 | "C:\WINDOWS\system32\runonce.exe" -r | C:\Windows\SysWOW64\runonce.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Run Once Wrapper Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2784 | "C:\WINDOWS\dpdrv\dpinst32.exe" /s | C:\Windows\dpdrv\dpinst32.exe | — | MSI54FB.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Package Installer Exit code: 2147483648 Version: 2.01 Modules
| |||||||||||||||
Total events
16 389
Read events
15 836
Write events
497
Delete events
56
Modification events
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000055982F0E4ED3DA01A0080000B41A0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000055982F0E4ED3DA01A0080000B41A0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000F5597E0E4ED3DA01A0080000B41A0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000F5597E0E4ED3DA01A0080000B41A0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000FB10830E4ED3DA01A0080000B41A0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000DA73850E4ED3DA01A0080000B41A0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000E640060F4ED3DA01A0080000B41A0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2208) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000FB90080F4ED3DA01A0080000541B0000E8030000010000000000000000000000C41C7155D7A5944AA0D58AAFA5C2C0EA00000000000000000000000000000000 | |||
| (PID) Process: | (6852) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000007C570D0F4ED3DA01C41A0000E41A0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
142
Suspicious files
31
Text files
11
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2208 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 2208 | msiexec.exe | C:\WINDOWS\Installer\1d47c9.msi | — | |
MD5:— | SHA256:— | |||
| 2208 | msiexec.exe | C:\WINDOWS\Installer\MSI4C6F.tmp | — | |
MD5:— | SHA256:— | |||
| 2416 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGFA75.tmp | xml | |
MD5:84F2F872035A2B2007494208AC3B98C4 | SHA256:F5BA88B4A9928B710C9DBF757F0C4DEE5BC6B6A56985D5BFEBA8620C8AE65B6C | |||
| 2208 | msiexec.exe | C:\WINDOWS\Installer\MSI4BB2.tmp | executable | |
MD5:79A1DC3E058699630F44EAEF8736D637 | SHA256:ADF737E044C8125286B7F0C2907597D840CA6F3DC92E8CB56A5BC20243C723D4 | |||
| 2208 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{55711cc4-a5d7-4a94-a0d5-8aafa5c2c0ea}_OnDiskSnapshotProp | binary | |
MD5:7032FDCC0225573C927D4157E896259C | SHA256:BE7D80C79B4F4E2D39798120B6FBA1BD907BF99877912A22738C958011517AD0 | |||
| 2916 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\696F3DE637E6DE85B458996D49D759AD | der | |
MD5:6872FAE8288DB34207D9E7EE350157F4 | SHA256:50795B027E2BC566D3B7ACB89913F8EFD23B70615C9DB9BF5B23323AD3132A7D | |||
| 2916 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIF489.tmp | executable | |
MD5:79A1DC3E058699630F44EAEF8736D637 | SHA256:ADF737E044C8125286B7F0C2907597D840CA6F3DC92E8CB56A5BC20243C723D4 | |||
| 2208 | msiexec.exe | C:\WINDOWS\Installer\MSI4B44.tmp | executable | |
MD5:79A1DC3E058699630F44EAEF8736D637 | SHA256:ADF737E044C8125286B7F0C2907597D840CA6F3DC92E8CB56A5BC20243C723D4 | |||
| 2916 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7396C420A8E1BC1DA97F1AF0D10BAD21 | der | |
MD5:E07178901A4EAAC2816BB238EC3A80DB | SHA256:EEBD04C1272661E1091084108083CE44F7C961013791892D866B2F92EE3DEDA8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
75
DNS requests
24
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2916 | msiexec.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
2916 | msiexec.exe | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6116 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 2.23.209.135:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6004 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2916 | msiexec.exe | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |