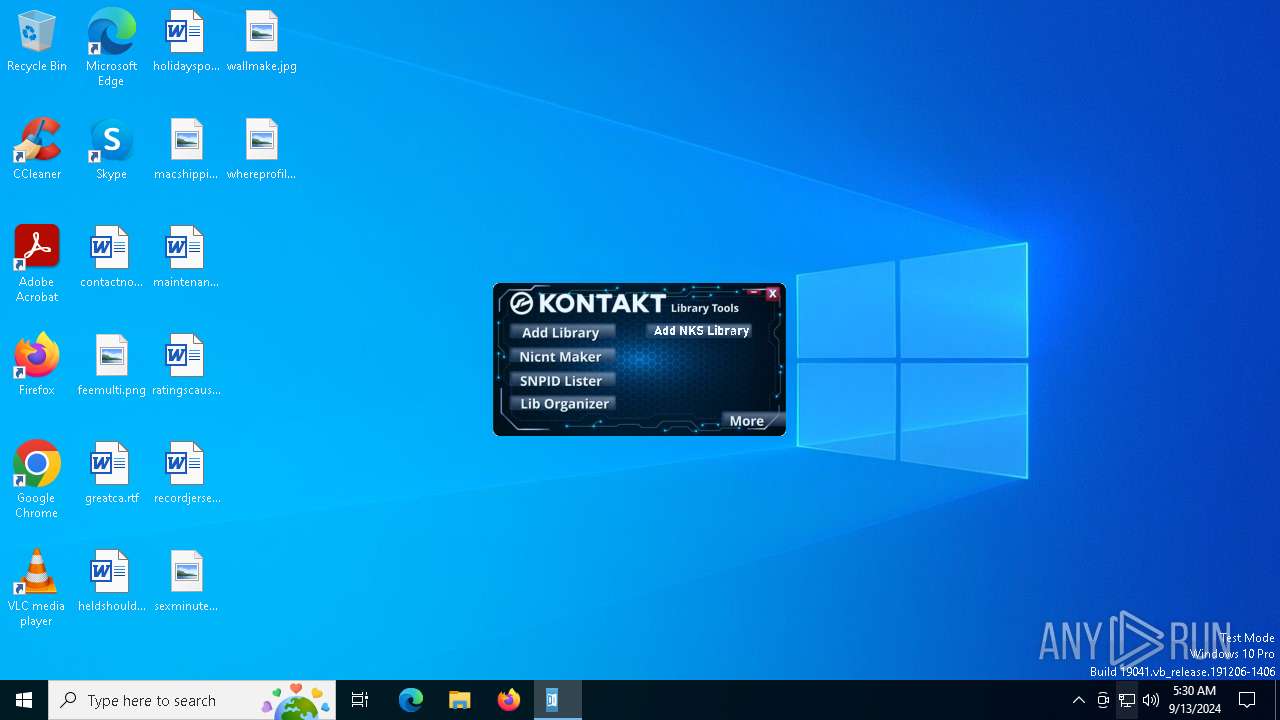
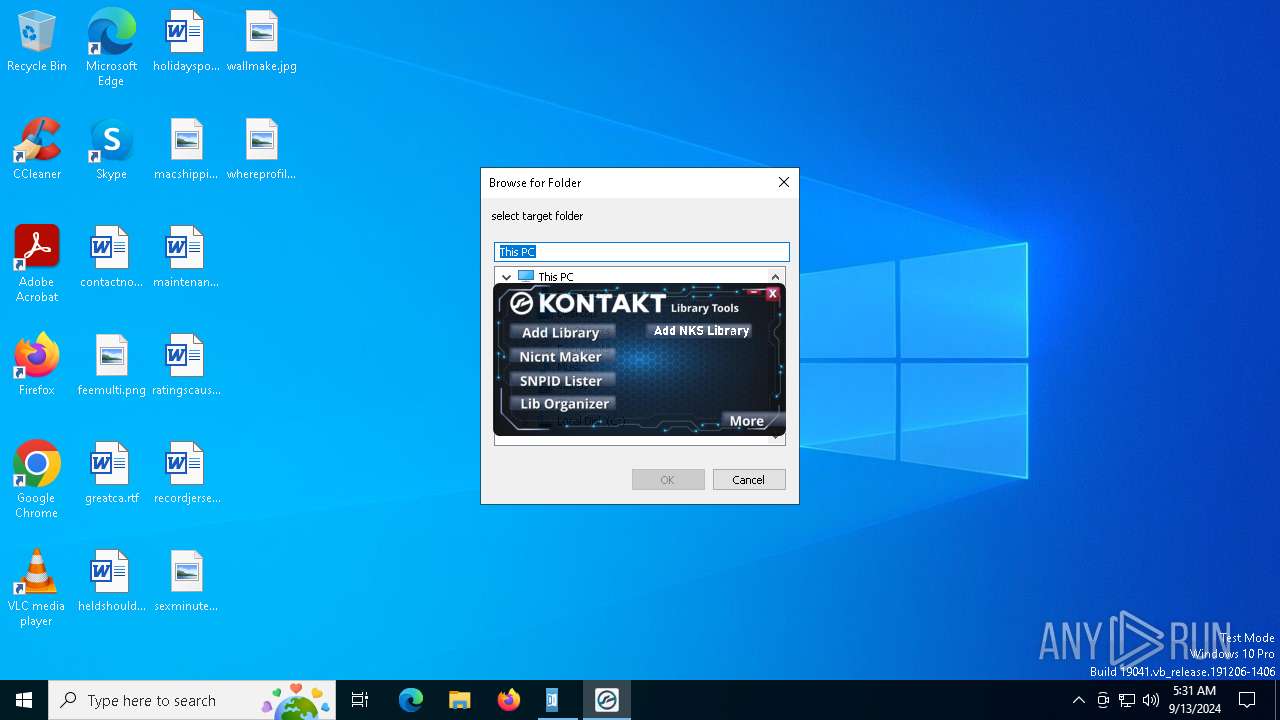
| File name: | Kontakt_Button.exe |
| Full analysis: | https://app.any.run/tasks/268d2161-3c7e-41bc-86f1-e6f67eb3b62b |
| Verdict: | Malicious activity |
| Analysis date: | September 13, 2024, 05:30:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 8004BAAC30D89D12AD6451963822D83F |
| SHA1: | 28EE4629801933E5C41955D26ED1909F67EF84A3 |
| SHA256: | D2AAECF14E2EC86E964B0782D539A1EA661D4AD6E46DF8565966D38BD54074BE |
| SSDEEP: | 98304:lWqTK7zpN+Vj3bPjOlrwf4+18Rka8FIwcAbcrCgMw38FZ5L5txL4P8F8vvYzYFpD:53GXGHsEehM39HsBgdSYWnGTM |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- Kontakt_Button.exe (PID: 6152)
Reads security settings of Internet Explorer
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
Drops 7-zip archiver for unpacking
- Kontakt_Button.exe (PID: 6152)
Executable content was dropped or overwritten
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
Reads the date of Windows installation
- Kontakt_Button.exe (PID: 6152)
- Add Library.exe (PID: 6712)
Reads Microsoft Outlook installation path
- Kontakt_button.exe (PID: 5692)
Reads Internet Explorer settings
- Kontakt_button.exe (PID: 5692)
There is functionality for taking screenshot (YARA)
- Kontakt_button.exe (PID: 5692)
INFO
Checks supported languages
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
- Add Library.exe (PID: 3272)
Create files in a temporary directory
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
Reads the computer name
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
- Add Library.exe (PID: 3272)
Process checks computer location settings
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
The process uses the downloaded file
- Kontakt_Button.exe (PID: 6152)
- Kontakt_button.exe (PID: 5692)
- Add Library.exe (PID: 6712)
Checks proxy server information
- Kontakt_button.exe (PID: 5692)
Creates files or folders in the user directory
- Kontakt_button.exe (PID: 5692)
UPX packer has been detected
- Kontakt_button.exe (PID: 5692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:06:11 09:16:51+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 223744 |
| InitializedDataSize: | 115200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x24b40 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.0.0 |
| ProductVersionNumber: | 7.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Kontakt Library Tools 7.0.0 |
| CompanyName: | Native Instruments |
| FileDescription: | Kontakt Library Tools |
| FileVersion: | 7.0.0.0 |
| LegalCopyright: | Bob Dule |
| ProductName: | Kontakt Library Tools 7 |
| ProductVersion: | 7 |
Total processes
129
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3268 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\Add Library.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\Add Library.exe | — | Add Library.exe | |||||||||||
User: admin Company: Native Instruments Integrity Level: MEDIUM Description: Add Library Assistant for Kontakt 6.5.3+ Exit code: 3221226540 Version: 1.0.7.0 Modules
| |||||||||||||||
| 3272 | "C:\Users\admin\AppData\Local\Temp\RarSFX1\Add Library.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX1\Add Library.exe | Add Library.exe | ||||||||||||
User: admin Company: Native Instruments Integrity Level: HIGH Description: Add Library Assistant for Kontakt 6.5.3+ Version: 1.0.7.0 Modules
| |||||||||||||||
| 5692 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\Kontakt_Button.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\Kontakt_button.exe | Kontakt_Button.exe | ||||||||||||
User: admin Company: Native Instruments Integrity Level: MEDIUM Description: Kontakt Debrider Version: 1.0.0.1 Modules
| |||||||||||||||
| 6152 | "C:\Users\admin\AppData\Local\Temp\Kontakt_Button.exe" | C:\Users\admin\AppData\Local\Temp\Kontakt_Button.exe | explorer.exe | ||||||||||||
User: admin Company: Native Instruments Integrity Level: MEDIUM Description: Kontakt Library Tools Version: 7.0.0.0 Modules
| |||||||||||||||
| 6712 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\Add Library.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\Add Library.exe | Kontakt_button.exe | ||||||||||||
User: admin Company: Native Instruments Integrity Level: MEDIUM Description: Kontakt Add Library Tool Version: 1.0.7.0 Modules
| |||||||||||||||
Total events
2 292
Read events
2 289
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5692) Kontakt_button.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5692) Kontakt_button.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5692) Kontakt_button.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
46
Suspicious files
6
Text files
79
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\parser\Native_Access_Parser.bat | text | |
MD5:5B43C8E27141342EB08ABC24BF5EB25B | SHA256:028F7E2F33CE3C25914A3AA1D481196104EFFB86CD751DD838156D276AC8F727 | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\KontaktLibOrganizer.exe | executable | |
MD5:02AF6843BAE1B664C1CB0D05E0144A63 | SHA256:A62D2B0230C67922D15E738F769ACAA3A980D080C671E5D42A84628735F54C9B | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\Nicnt Maker\Nicnt Maker.exe | executable | |
MD5:A91146F968309552C2ABEA48EA0DD7CF | SHA256:58ADCCEE4172191838DD38398D73B0C024AD47E36D48057DB376D3E445A87C9C | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\Key Adder.exe | executable | |
MD5:8907D44D562DEF8BFE7C40340EF9DE45 | SHA256:45057C04BD25C1DD25310B616ABC9197020984E57C7362AD163A85E2B3E0E333 | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\totalcmd\CGLPTNT.SYS | executable | |
MD5:C9503EED292DB41937C22F620FDAA39C | SHA256:F39E2CD0F0A458E6012C97284BB636A785815353FF09E59DD5AB96C36E2EC5D0 | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\totalcmd\CGLPT64.SYS | executable | |
MD5:C6E5B7ECFB1AA7A104BC3C0C081E36E0 | SHA256:0108B00762DE94C189224874DD064E6EC65EE8F3BFF65801A6FB8D25AF7DE617 | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\totalcmd\CGLPT9X.VXD | executable | |
MD5:7DF5AEB3ABF3762B75EC888819C53FB0 | SHA256:1447FD7E408C368396F46466808399FFF3FF90B67D0FF7807DA4A746E0B77E6B | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\totalcmd\default.br2 | binary | |
MD5:3A6B27EDADAB326BBE5D47E0EB6DCAAE | SHA256:6842AB1E7E498E3EB015E92ACDF09DAF95B480D48F6F3B5F3256DFB277690ED6 | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\totalcmd\FILTER64\SoundTouchDLL_License.txt | text | |
MD5:1AF6A2E5C3E0B3BEB6E30936578983E1 | SHA256:FF28C845D90F91E140E79FC82CE0181E15E02590C7D7153CFEF8AA9C328CADF2 | |||
| 6152 | Kontakt_Button.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\Data\totalcmd\DEFAULT.BAR | text | |
MD5:F103B23C658D801D5C31CB056BAFDC16 | SHA256:8159C946398EEC59D8065342C06B957AE38165E664850FB57F5D9971CFFB7C21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
32
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2028 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
8 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6012 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2028 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2028 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6012 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |