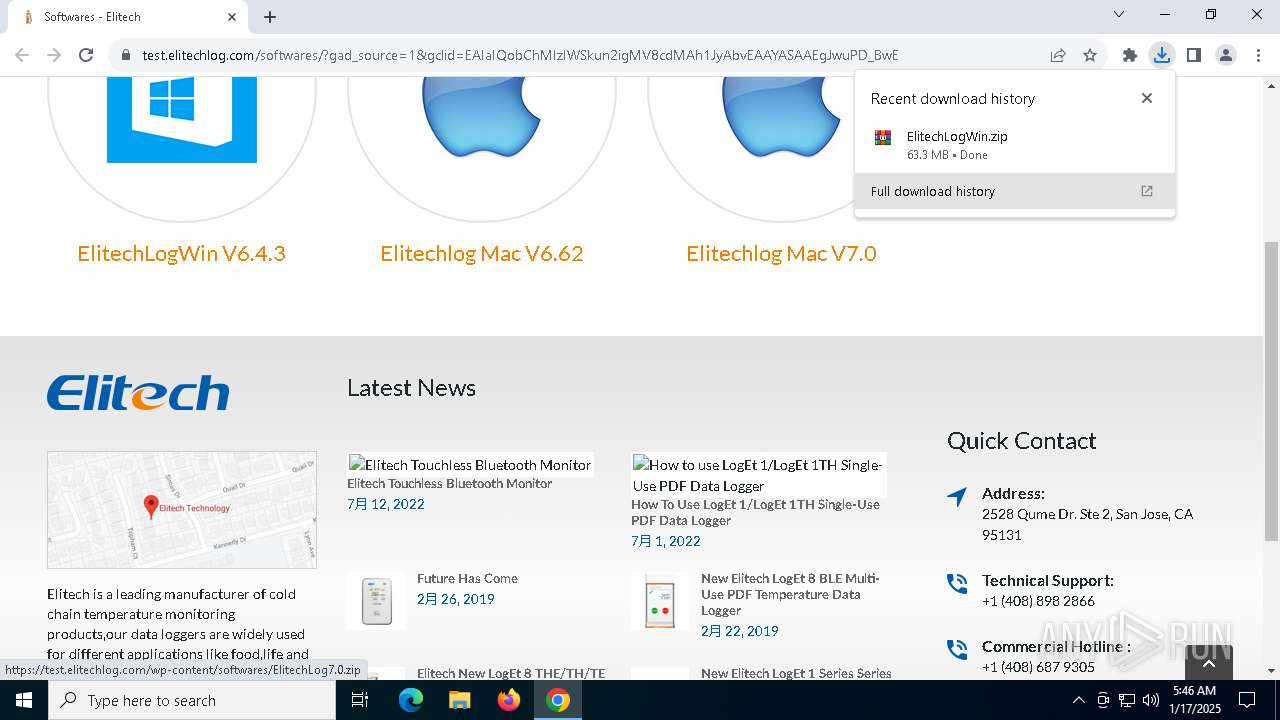
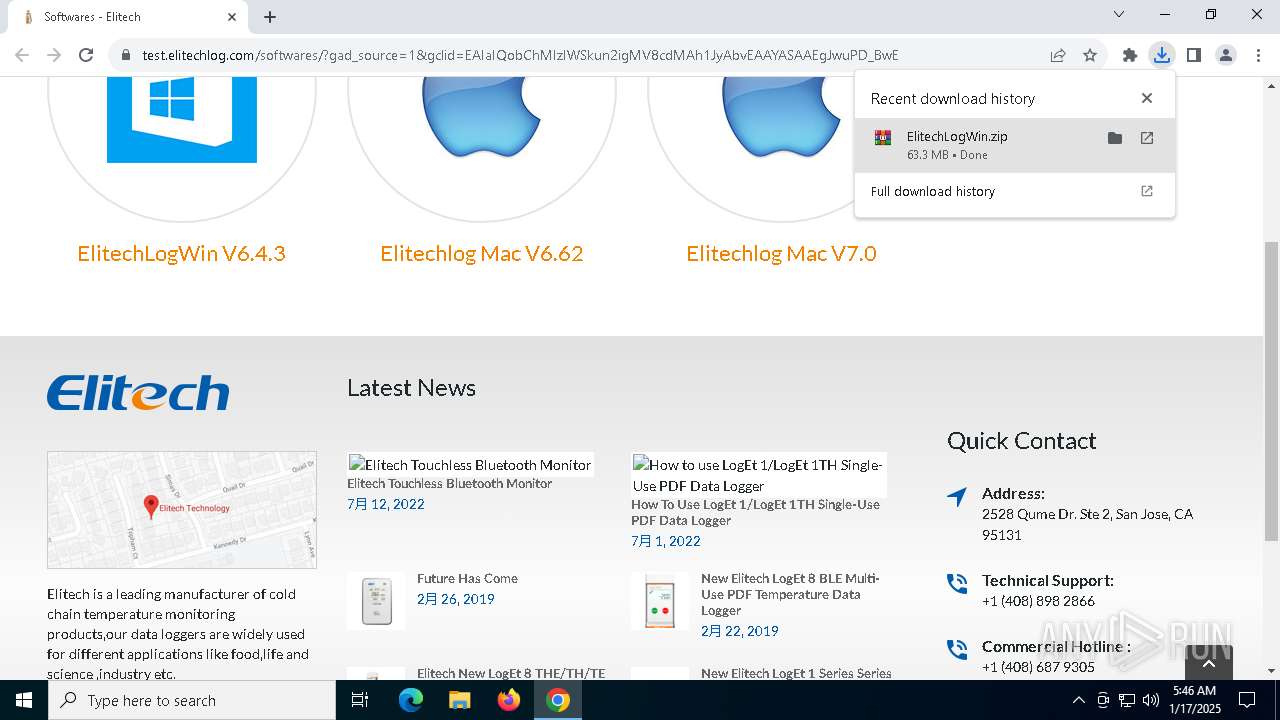
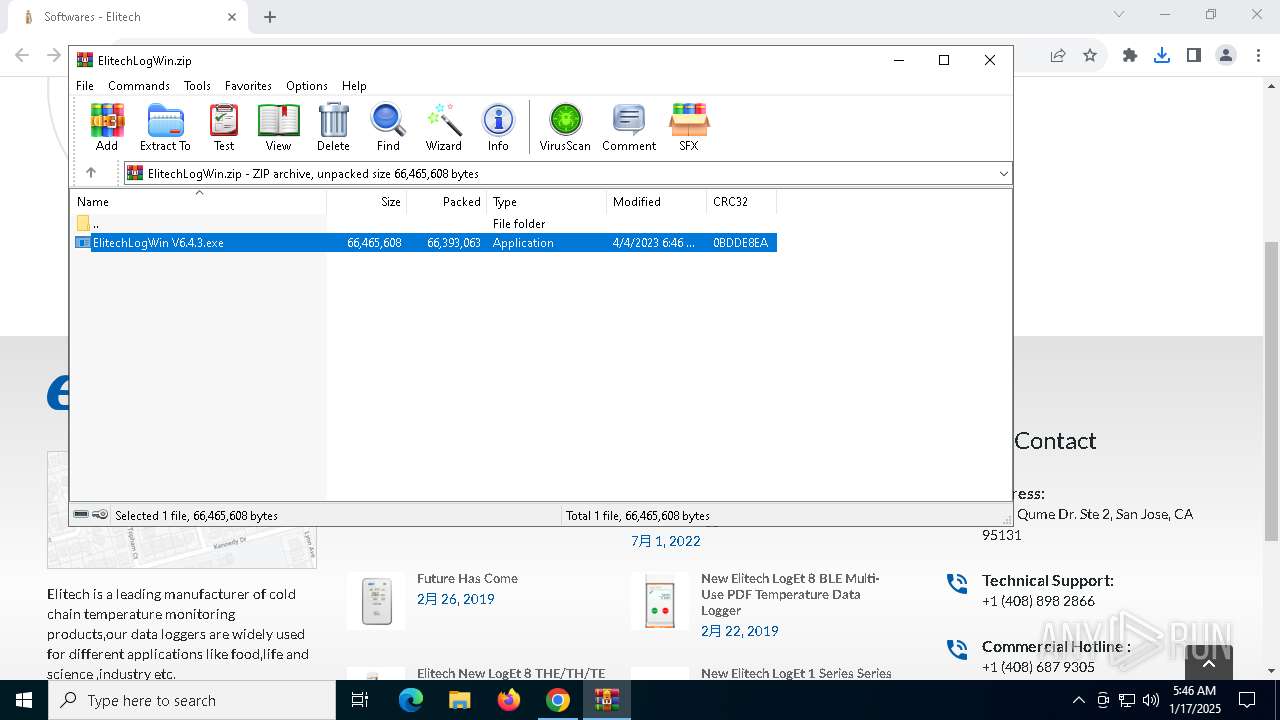
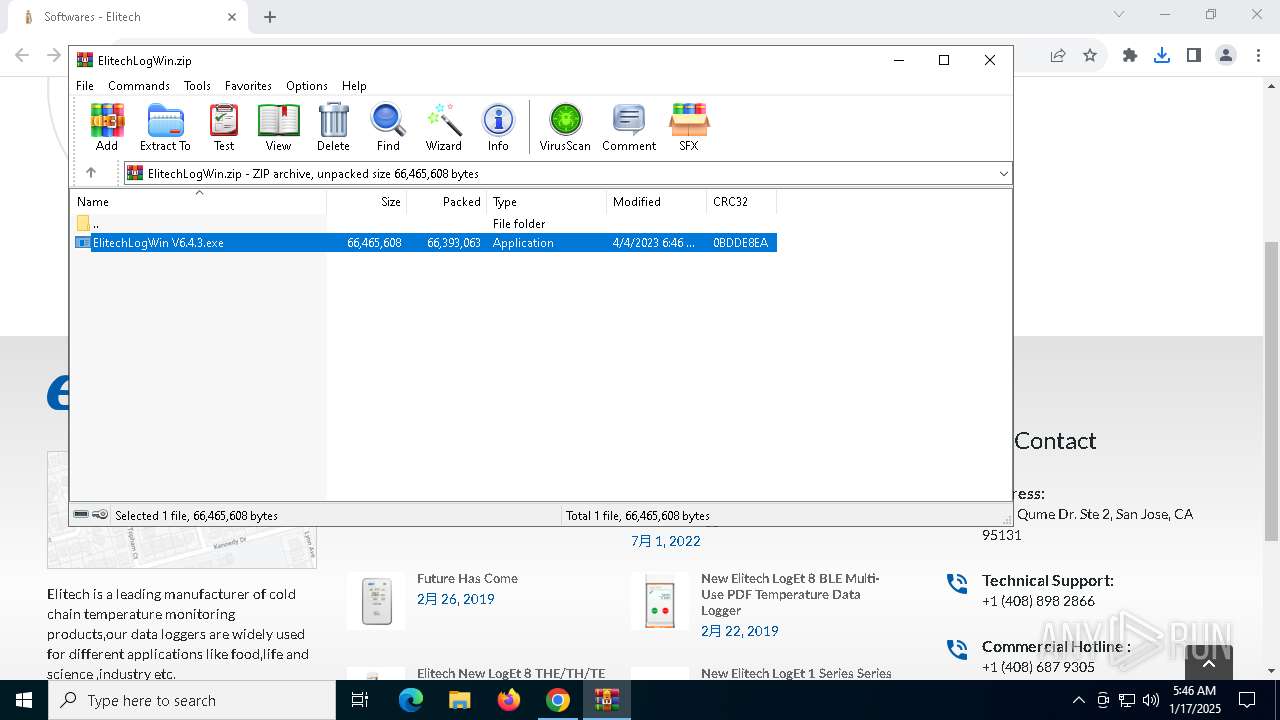
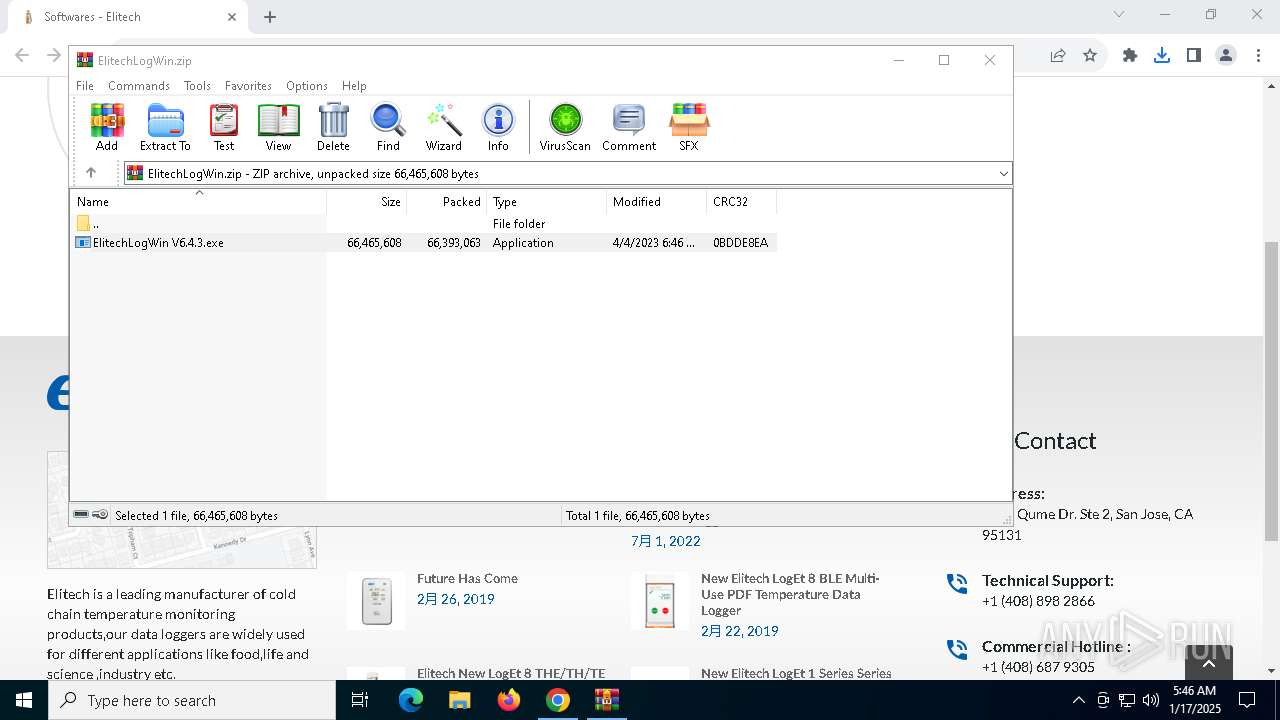
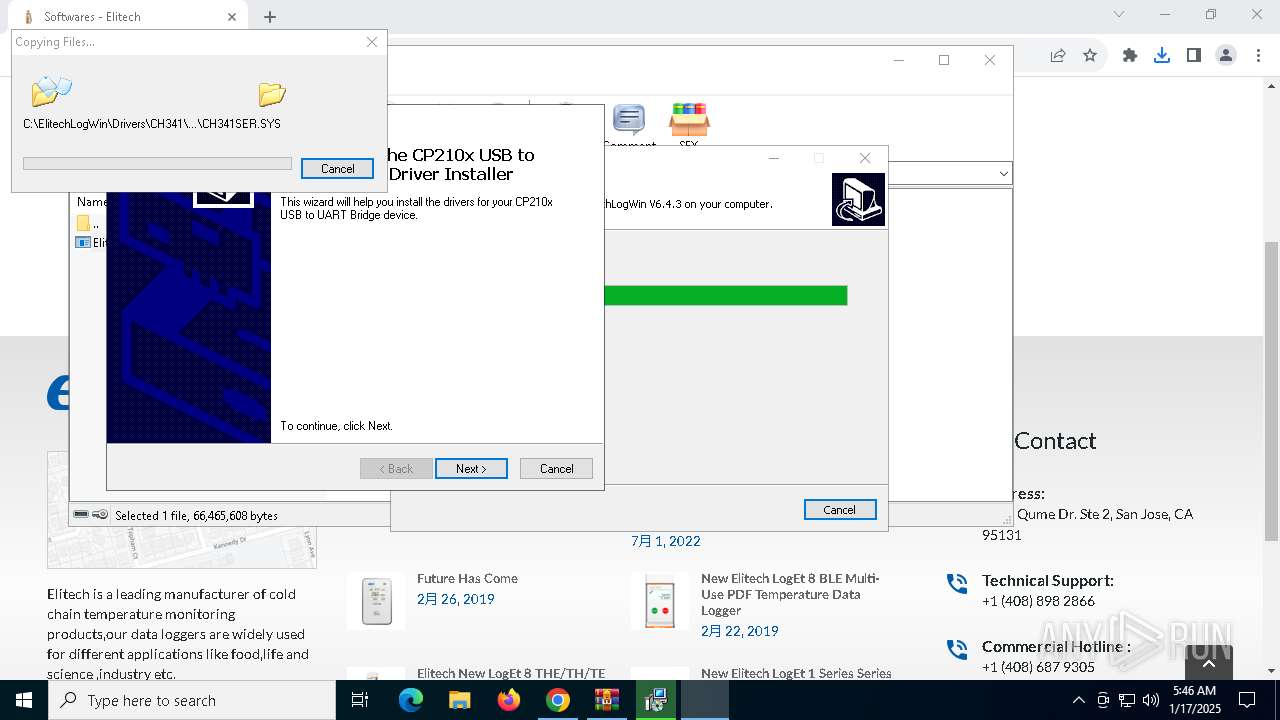
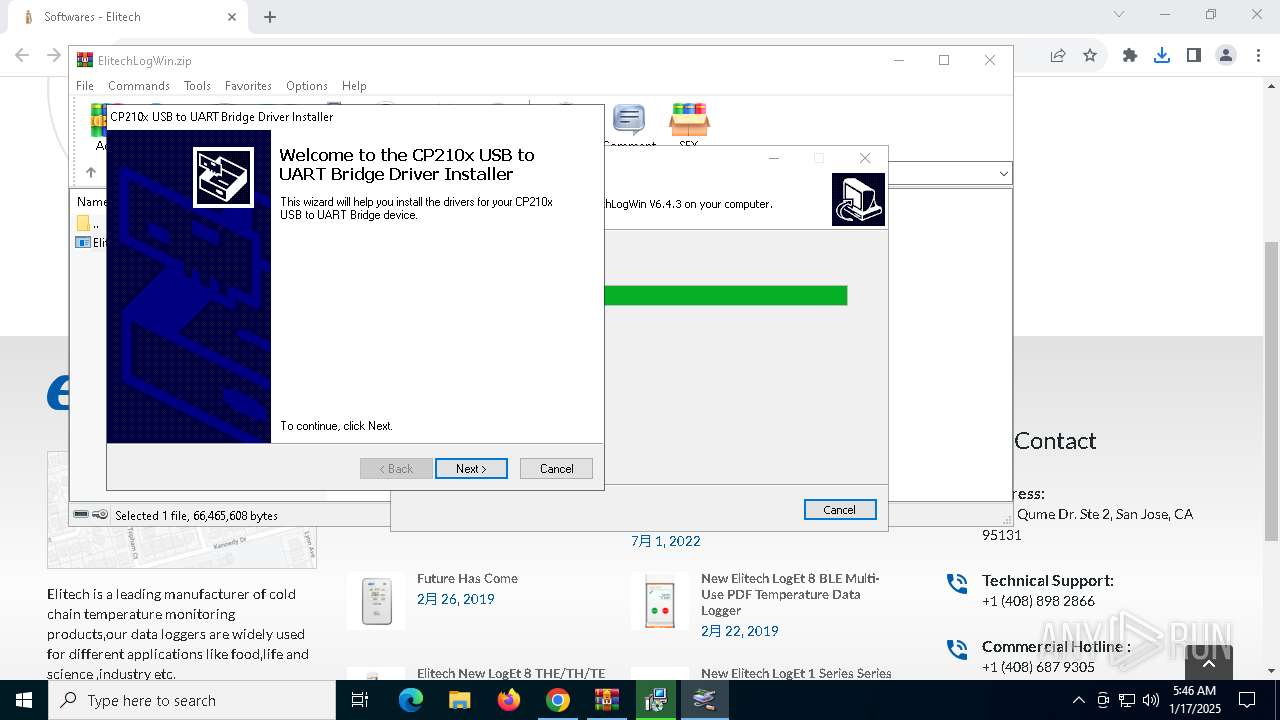
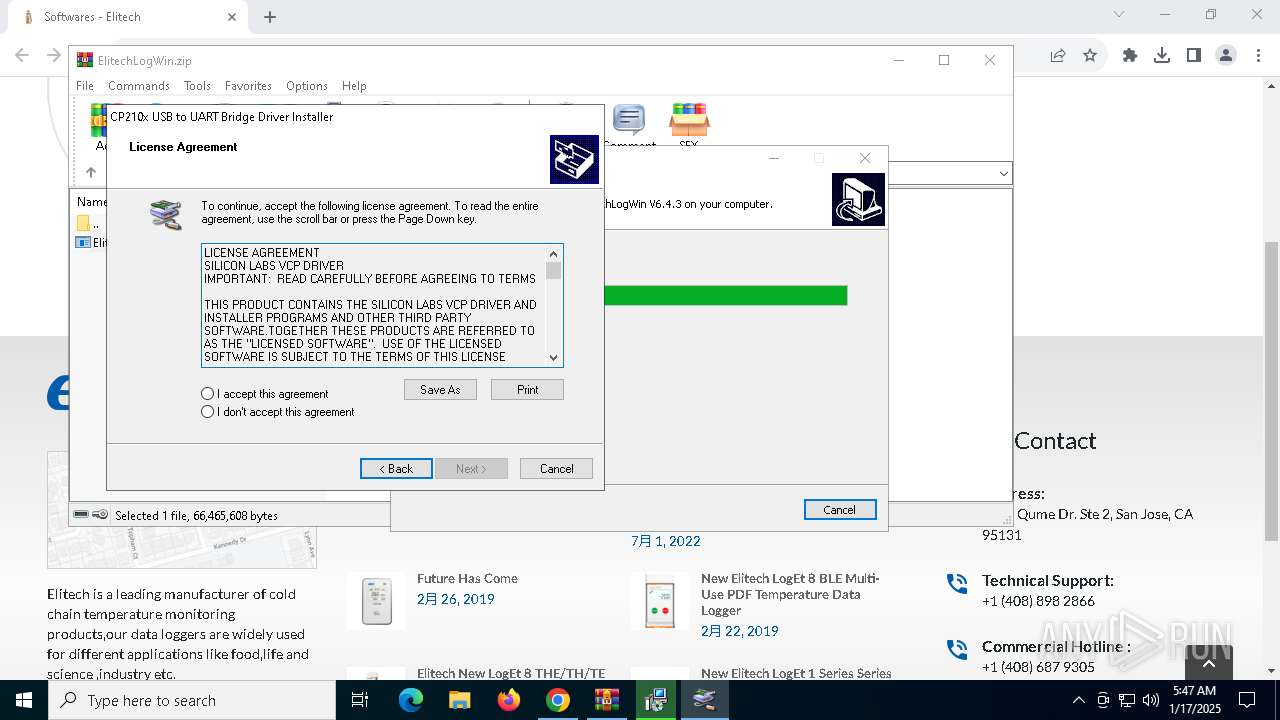
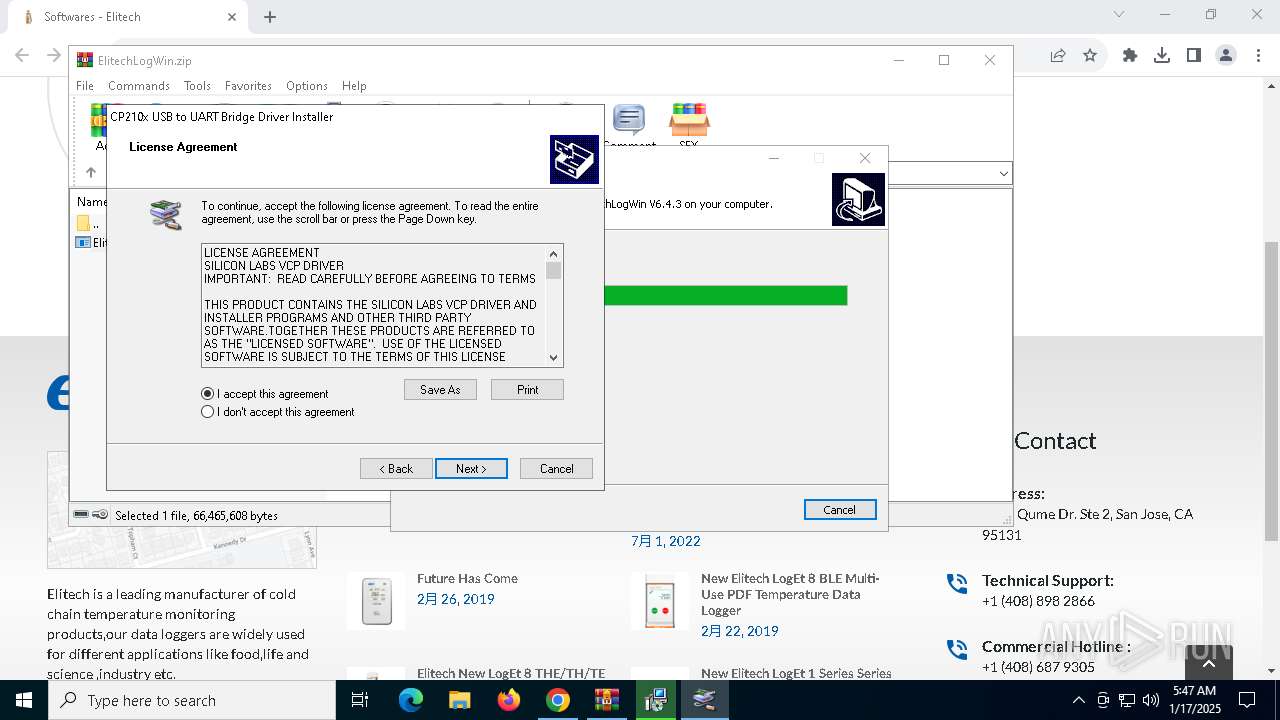
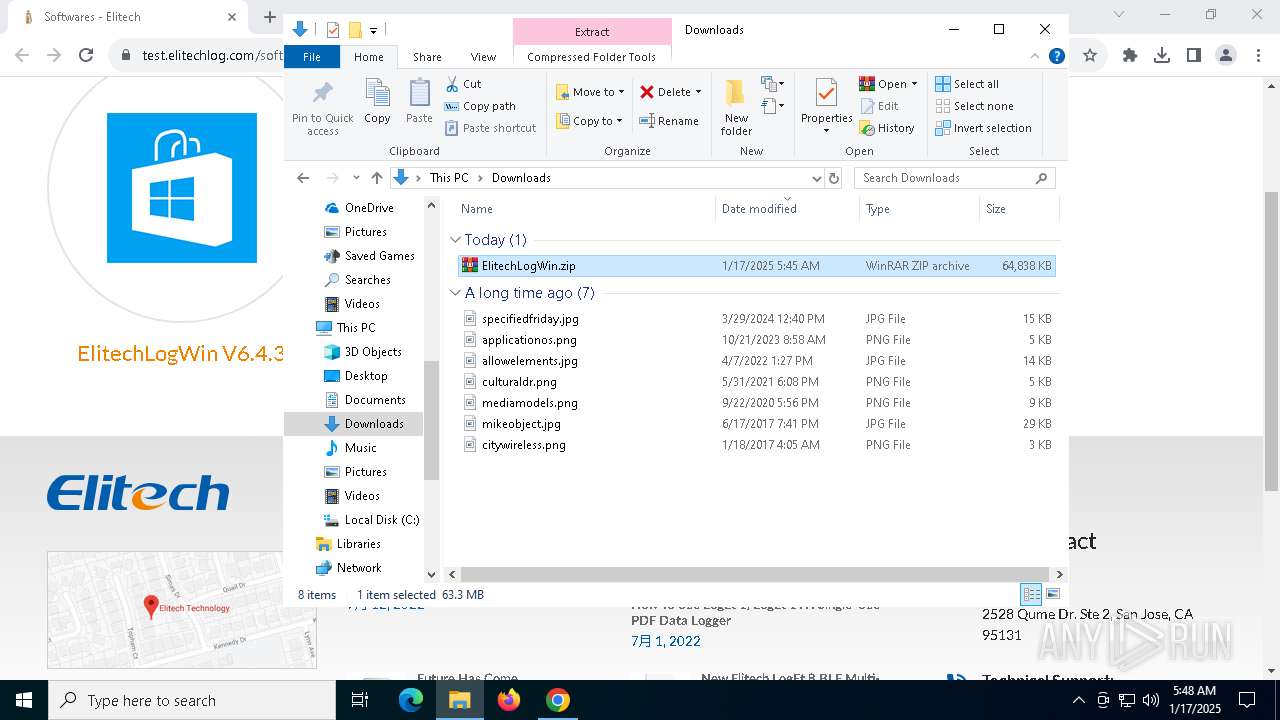
| URL: | https://test.elitechlog.com/softwares/?gad_source=1&gclid=EAIaIQobChMIzIWSkun2igMV8cdMAh1JyAbvEAAYASAAEgJwuPD_BwE |
| Full analysis: | https://app.any.run/tasks/71b333b4-6580-4e7b-b95c-029192d3d695 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2025, 05:45:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 12FF0C5DB299B62A31D0894B8D9A423D |
| SHA1: | DA7F3D52EA805FCE9462EB502B2023BD1587A207 |
| SHA256: | D29D2F9788F1C66A93882578F3C299CECA0CDE0F6B4654F664F9EBD13035EB77 |
| SSDEEP: | 3:N8IBCeNKMKXKQ9z9glF0XHb+jDu1kGNzy8/k9LT:2I/NJfo7+3VGA8EX |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6004)
- ElitechLogWin V6.4.3.tmp (PID: 1144)
- ElitechLogWin V6.4.3.tmp (PID: 4500)
Executable content was dropped or overwritten
- ElitechLogWin V6.4.3.exe (PID: 3564)
- ElitechLogWin V6.4.3.exe (PID: 4328)
- ElitechLogWin V6.4.3.exe (PID: 4420)
- ElitechLogWin V6.4.3.tmp (PID: 6240)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- drvinst.exe (PID: 6844)
- ElitechLogWin V6.4.3.exe (PID: 7044)
- DRVSETUP64.exe (PID: 236)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
Reads the Windows owner or organization settings
- ElitechLogWin V6.4.3.tmp (PID: 6240)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
Process drops legitimate windows executable
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
Drops a system driver (possible attempt to evade defenses)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- DRVSETUP64.exe (PID: 236)
- drvinst.exe (PID: 6844)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
Creates file in the systems drive root
- ElitechLogWin V6.4.3.tmp (PID: 6632)
Creates files in the driver directory
- drvinst.exe (PID: 6844)
- DRVSETUP64.exe (PID: 236)
- drvinst.exe (PID: 1076)
Checks Windows Trust Settings
- drvinst.exe (PID: 6844)
- drvinst.exe (PID: 1076)
Creates a software uninstall entry
- CP210xVCPInstaller_x64.exe (PID: 448)
Searches for installed software
- ElitechLogWin V6.4.3.tmp (PID: 6632)
INFO
The process uses the downloaded file
- chrome.exe (PID: 4076)
- chrome.exe (PID: 1668)
- WinRAR.exe (PID: 6004)
Reads Microsoft Office registry keys
- chrome.exe (PID: 1668)
Create files in a temporary directory
- ElitechLogWin V6.4.3.exe (PID: 3564)
- ElitechLogWin V6.4.3.exe (PID: 4328)
- ElitechLogWin V6.4.3.exe (PID: 4420)
- ElitechLogWin V6.4.3.exe (PID: 7044)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- ElitechLogWin V6.4.3.tmp (PID: 6240)
- DRVSETUP64.exe (PID: 236)
- CP210xVCPInstaller_x64.exe (PID: 448)
Checks supported languages
- ElitechLogWin V6.4.3.exe (PID: 3564)
- ElitechLogWin V6.4.3.tmp (PID: 1144)
- ElitechLogWin V6.4.3.exe (PID: 4328)
- ElitechLogWin V6.4.3.exe (PID: 4420)
- ElitechLogWin V6.4.3.tmp (PID: 4500)
- ElitechLogWin V6.4.3.exe (PID: 7044)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- ElitechLogWin V6.4.3.tmp (PID: 6240)
- DRVSETUP64.exe (PID: 236)
- SETUP.EXE (PID: 6992)
- drvinst.exe (PID: 6844)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
Reads the computer name
- ElitechLogWin V6.4.3.tmp (PID: 1144)
- ElitechLogWin V6.4.3.tmp (PID: 4500)
- ElitechLogWin V6.4.3.tmp (PID: 6240)
- DRVSETUP64.exe (PID: 236)
- drvinst.exe (PID: 6844)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
Application launched itself
- chrome.exe (PID: 1668)
Process checks computer location settings
- ElitechLogWin V6.4.3.tmp (PID: 1144)
- ElitechLogWin V6.4.3.tmp (PID: 4500)
The sample compiled with arabic language support
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- CP210xVCPInstaller_x64.exe (PID: 448)
The sample compiled with chinese language support
- ElitechLogWin V6.4.3.tmp (PID: 6632)
The sample compiled with english language support
- ElitechLogWin V6.4.3.tmp (PID: 6632)
- drvinst.exe (PID: 6844)
- DRVSETUP64.exe (PID: 236)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
- chrome.exe (PID: 1296)
- chrome.exe (PID: 2408)
SQLite executable
- ElitechLogWin V6.4.3.tmp (PID: 6632)
Reads the machine GUID from the registry
- drvinst.exe (PID: 6844)
- drvinst.exe (PID: 1076)
- CP210xVCPInstaller_x64.exe (PID: 448)
Reads the software policy settings
- drvinst.exe (PID: 6844)
- CP210xVCPInstaller_x64.exe (PID: 448)
- drvinst.exe (PID: 1076)
Creates files in the program directory
- CP210xVCPInstaller_x64.exe (PID: 448)
- ElitechLogWin V6.4.3.tmp (PID: 6632)
Creates a software uninstall entry
- ElitechLogWin V6.4.3.tmp (PID: 6632)
Executable content was dropped or overwritten
- chrome.exe (PID: 1296)
- chrome.exe (PID: 2408)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
167
Monitored processes
34
Malicious processes
9
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
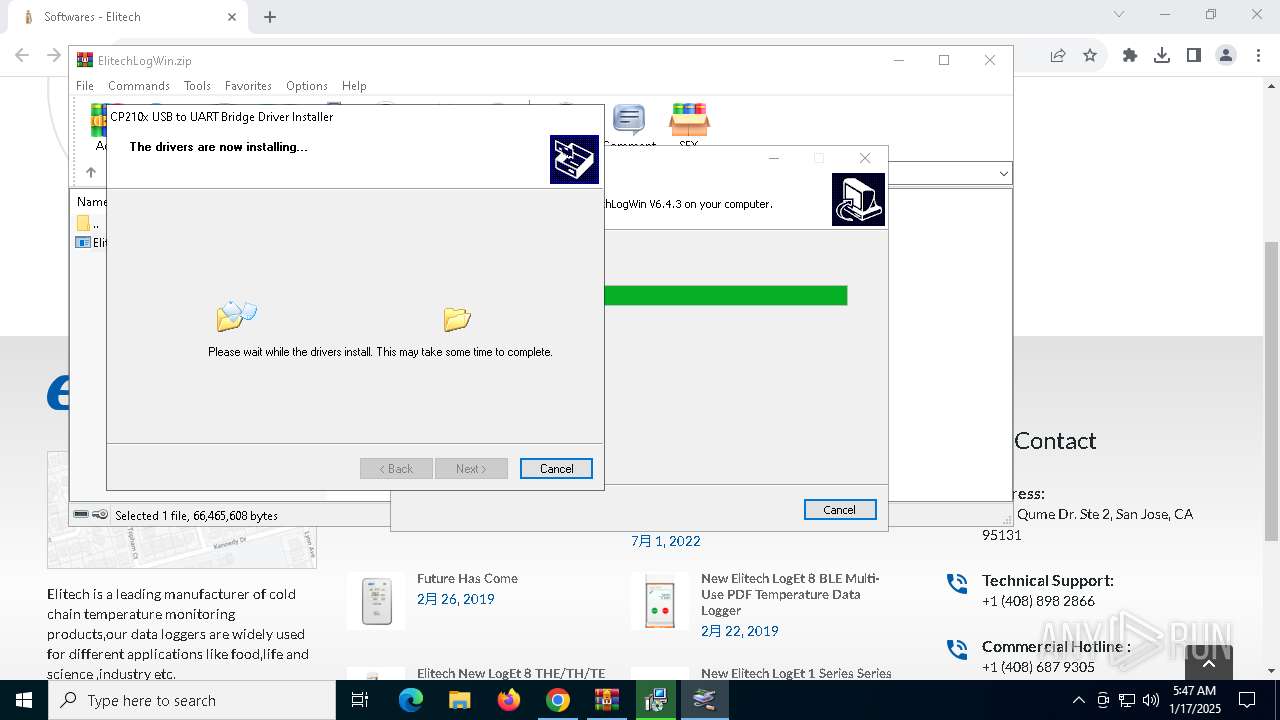
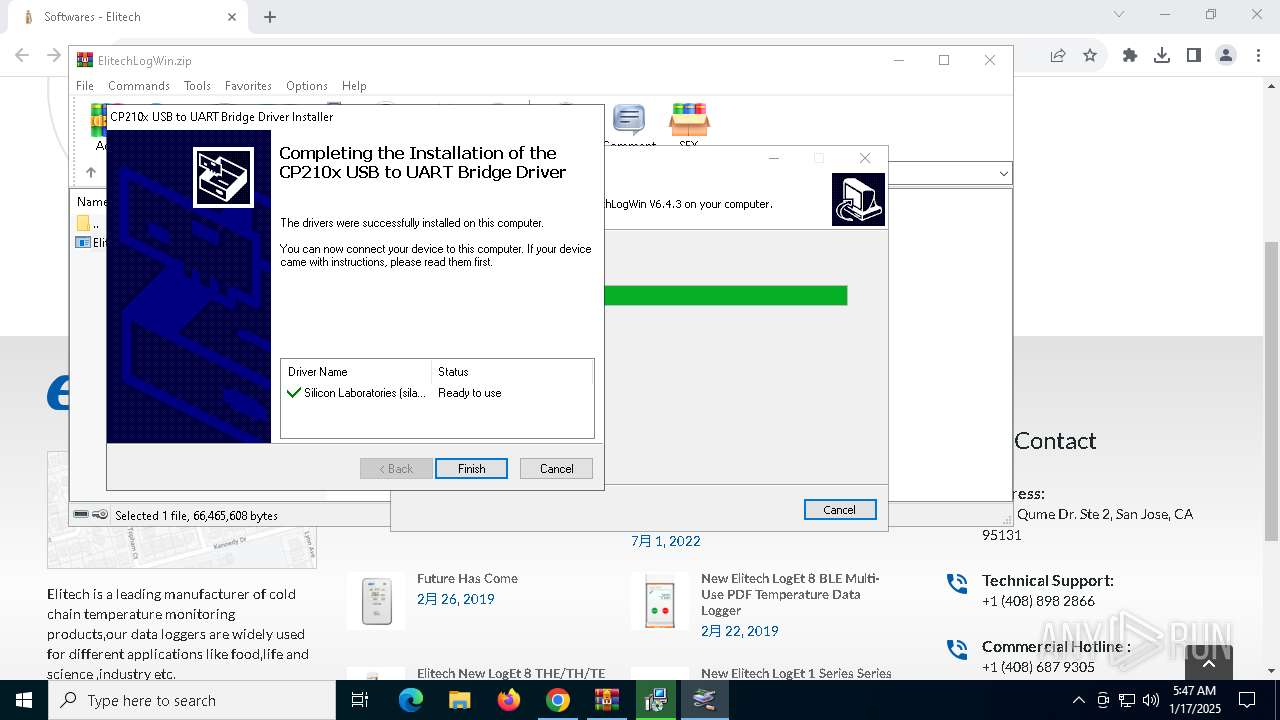
| 236 | C:\ElitechLogWin\Drivers\CH341\DRVSETUP64\DRVSETUP64.EXE \s | C:\ElitechLogWin\Drivers\CH341\DRVSETUP64\DRVSETUP64.exe | SETUP.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 0 Version: 1, 7, 2, 0 Modules
| |||||||||||||||
| 448 | "C:\ElitechLogWin\Drivers\CP210x\CP210xVCPInstaller_x64.exe" /S | C:\ElitechLogWin\Drivers\CP210x\CP210xVCPInstaller_x64.exe | ElitechLogWin V6.4.3.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Driver Package Installer Exit code: 256 Version: 2.1 Modules
| |||||||||||||||
| 1076 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{0f9c6350-2ef9-0d4c-9b87-0eaf51dbd344}\slabvcp.inf" "9" "43ef4524b" "00000000000001E4" "WinSta0\Default" "000000000000019C" "208" "c:\elitechlogwin\drivers\cp210x" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
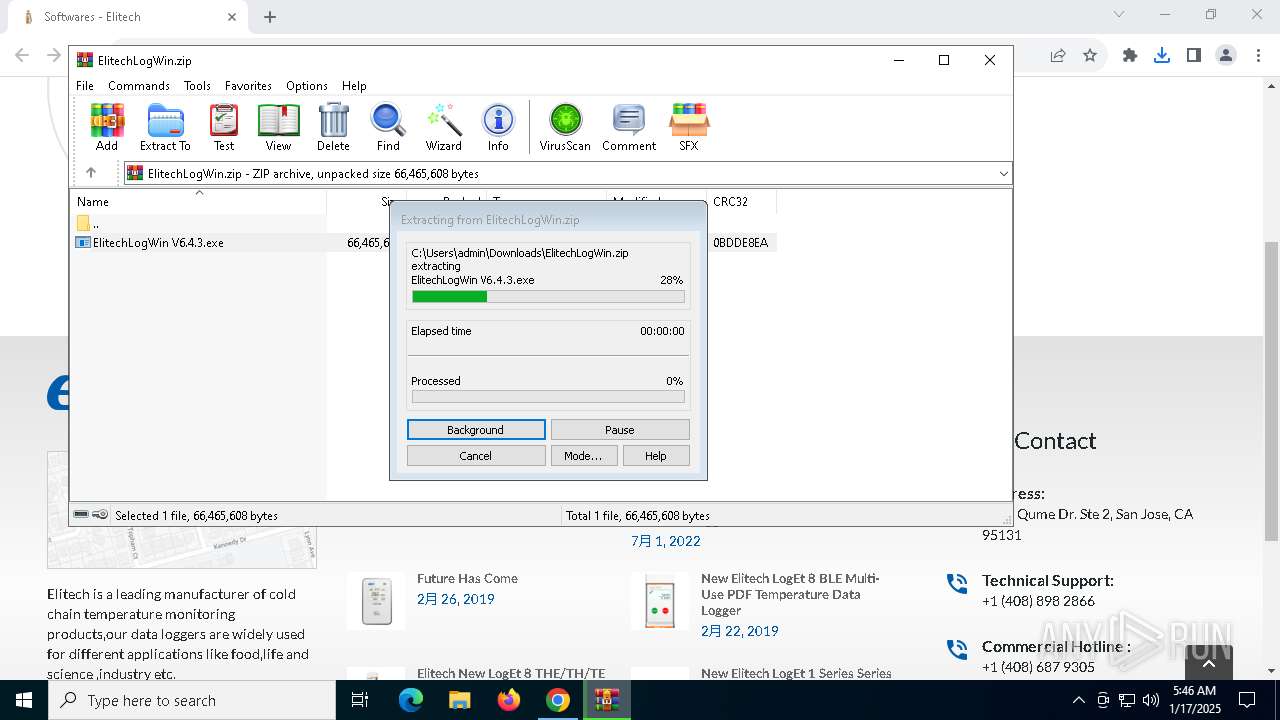
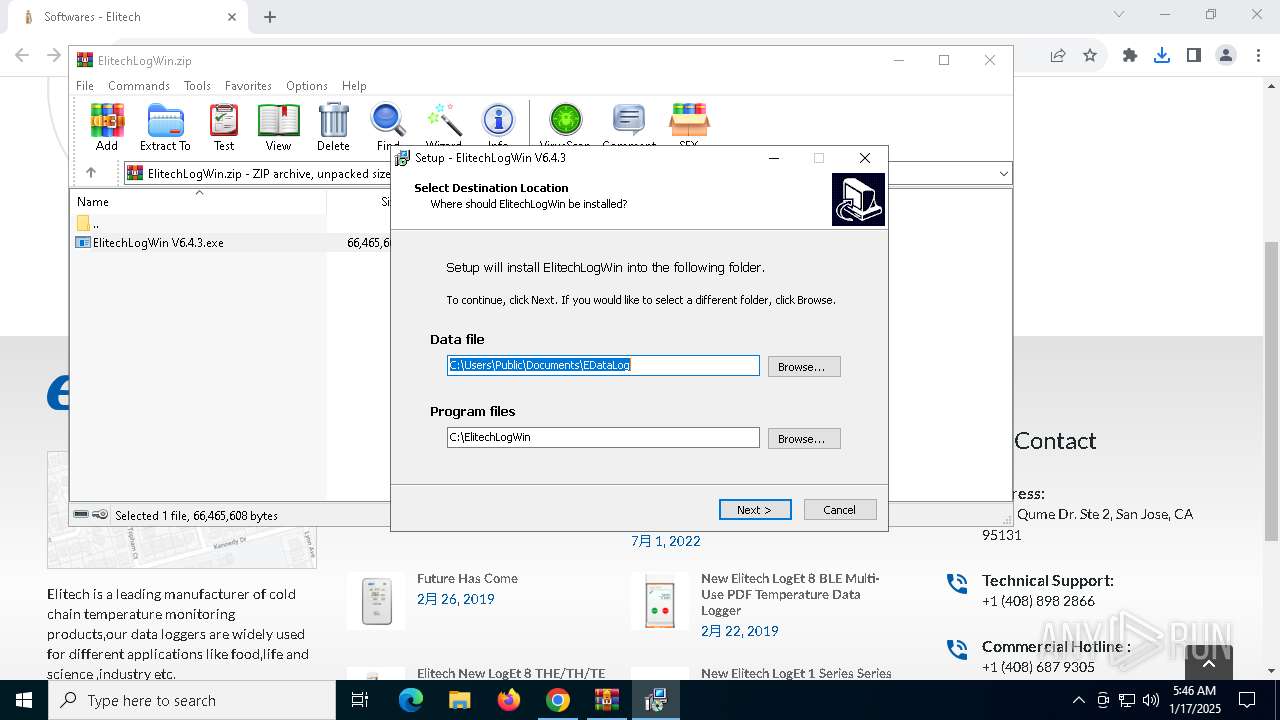
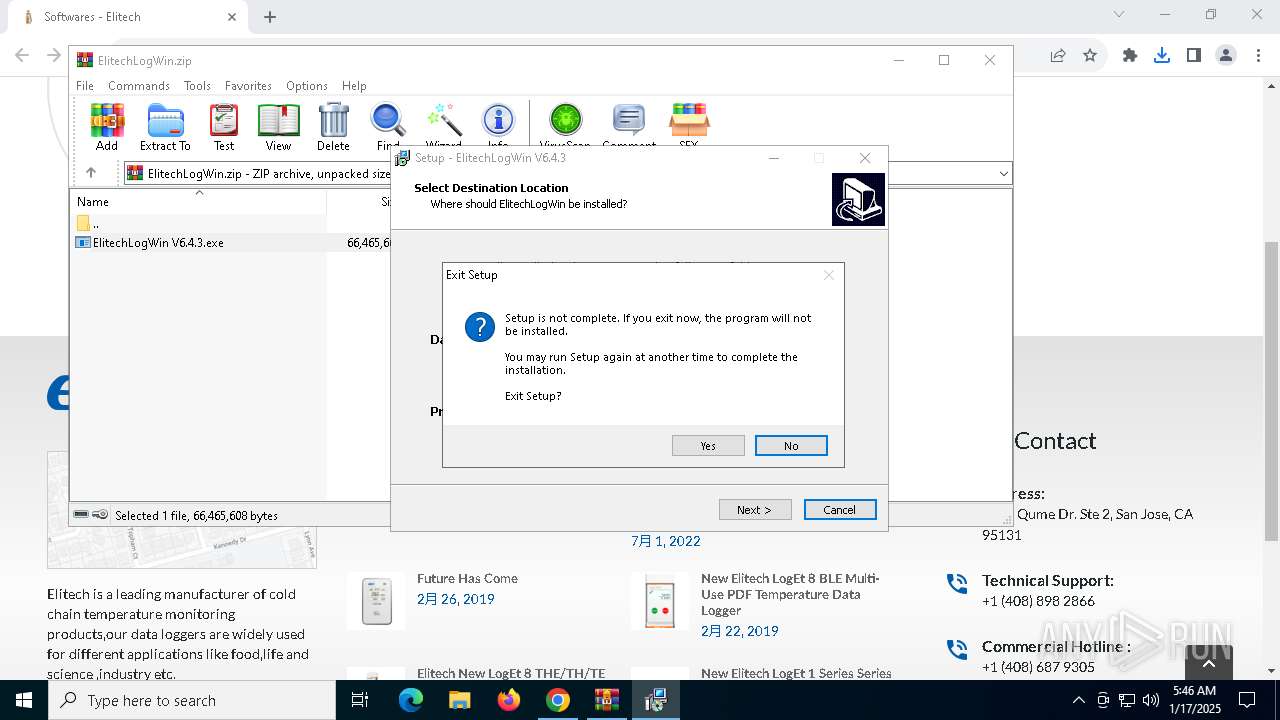
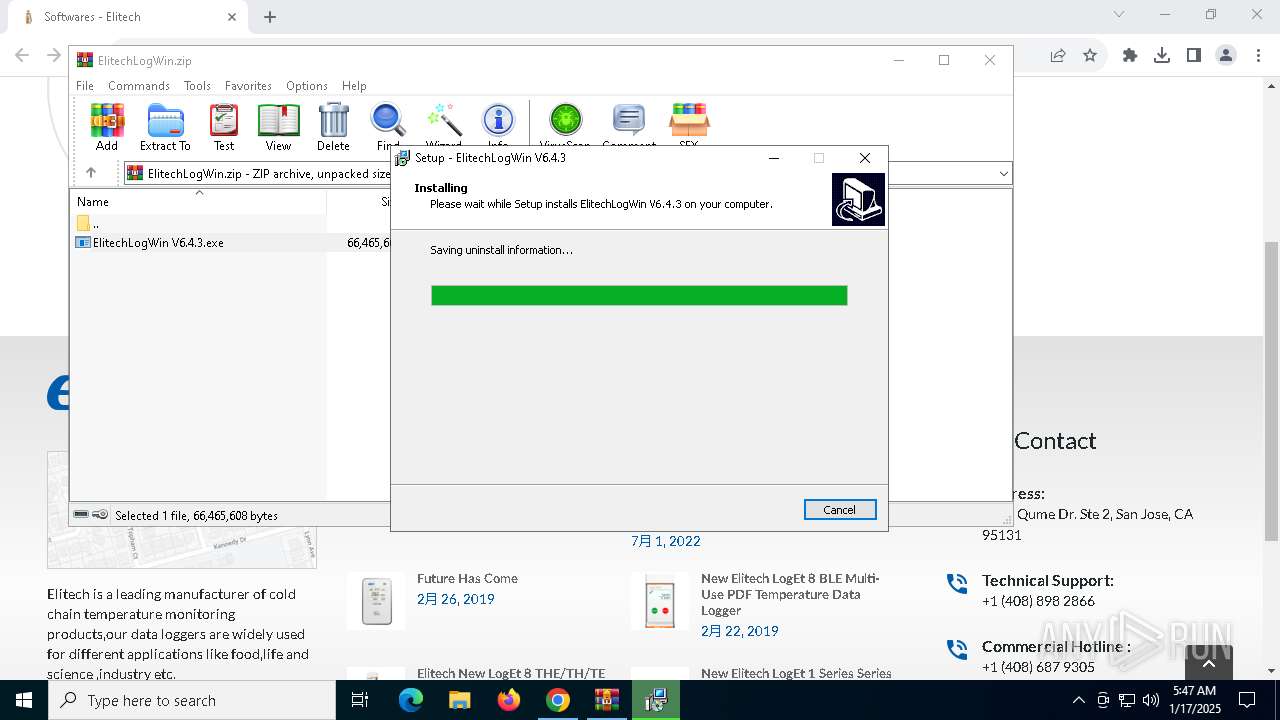
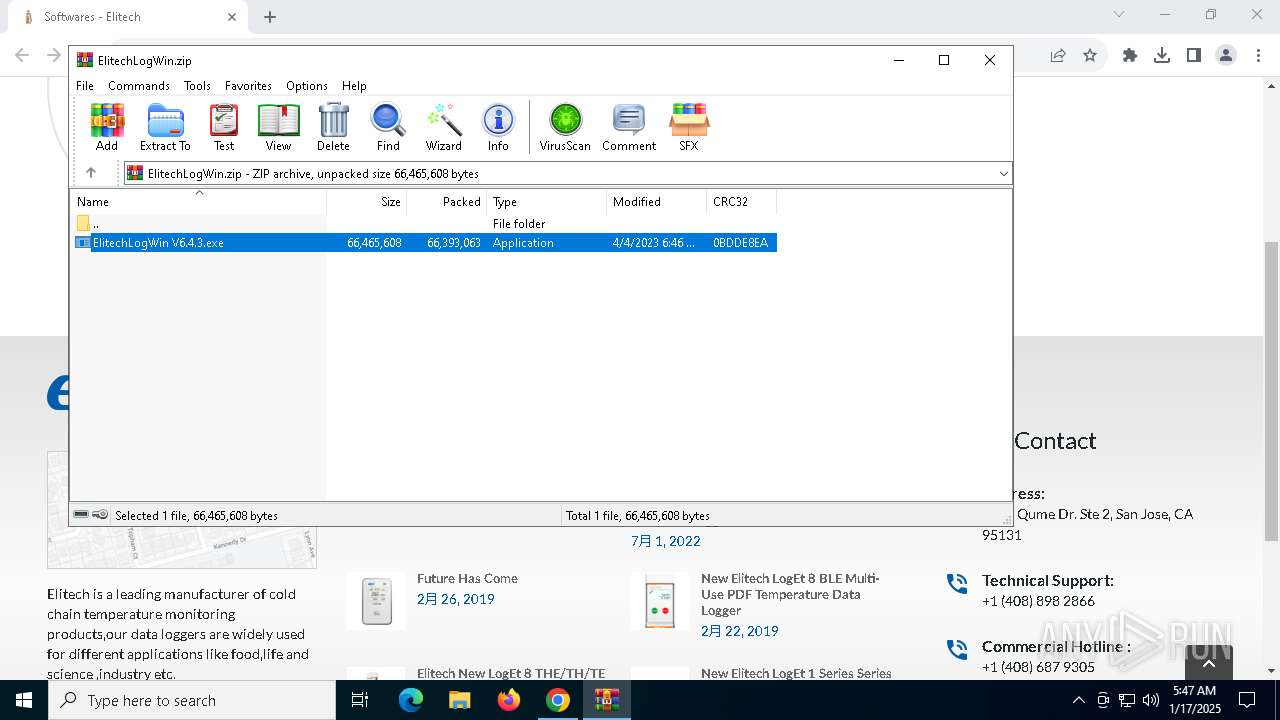
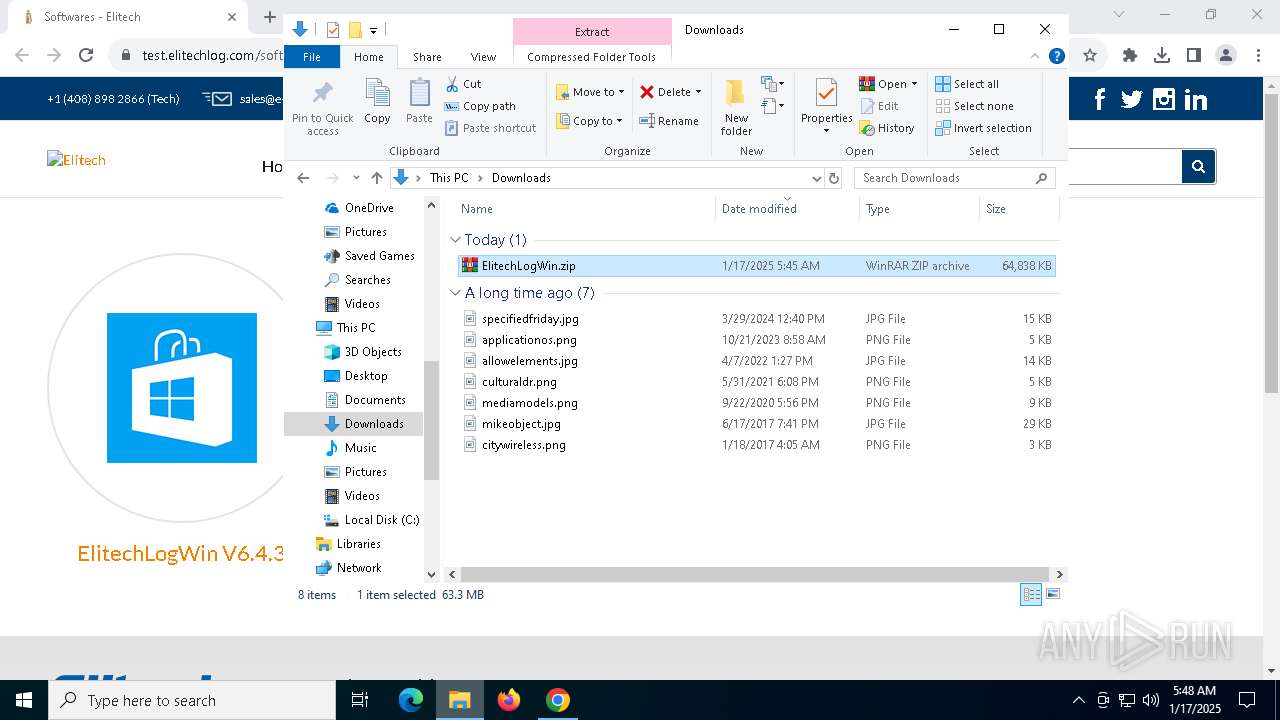
| 1144 | "C:\Users\admin\AppData\Local\Temp\is-90UH2.tmp\ElitechLogWin V6.4.3.tmp" /SL5="$30284,66039552,121344,C:\Users\admin\AppData\Local\Temp\Rar$EXa6004.7768\ElitechLogWin V6.4.3.exe" | C:\Users\admin\AppData\Local\Temp\is-90UH2.tmp\ElitechLogWin V6.4.3.tmp | — | ElitechLogWin V6.4.3.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5680 --field-trial-handle=1908,i,2742170741569571169,425310413108730011,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://test.elitechlog.com/softwares/?gad_source=1&gclid=EAIaIQobChMIzIWSkun2igMV8cdMAh1JyAbvEAAYASAAEgJwuPD_BwE" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4364 --field-trial-handle=1908,i,2742170741569571169,425310413108730011,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
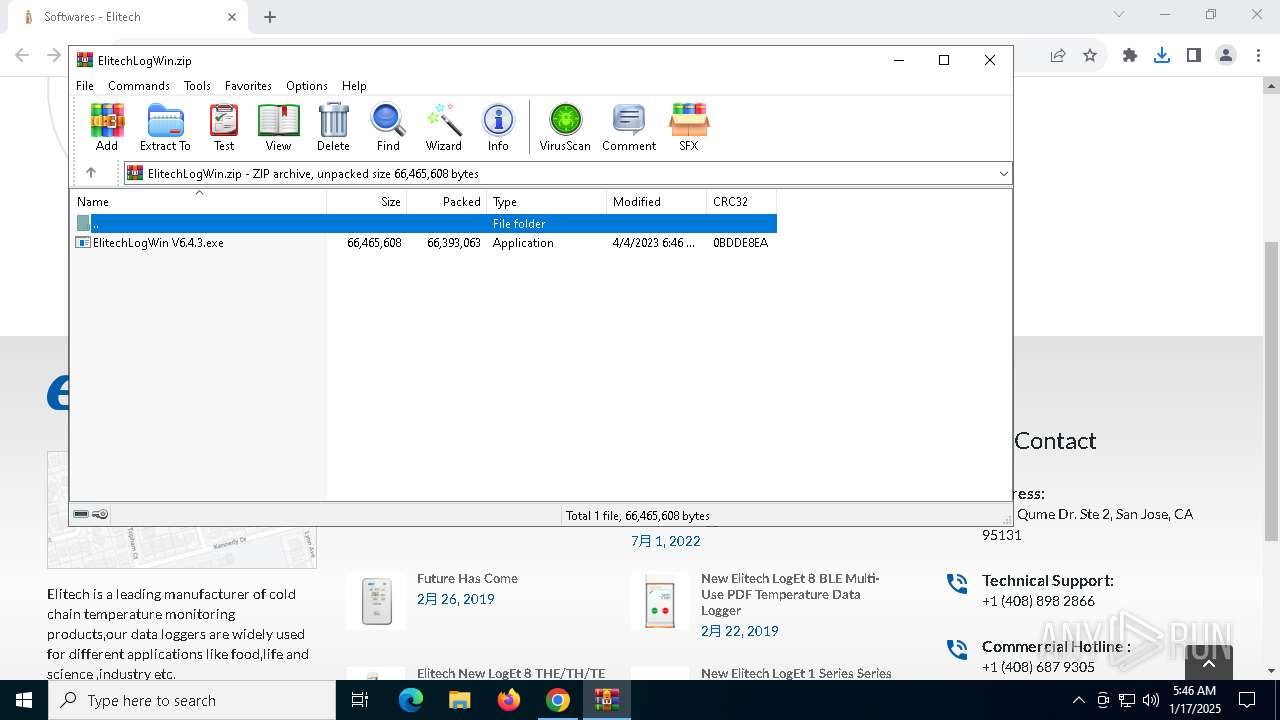
| 3564 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6004.7768\ElitechLogWin V6.4.3.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6004.7768\ElitechLogWin V6.4.3.exe | WinRAR.exe | ||||||||||||
User: admin Company: Elitech Technology, Inc. Integrity Level: MEDIUM Description: ElitechLogWin V6.4.3 Setup Exit code: 2 Version: Modules
| |||||||||||||||
| 3608 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5688 --field-trial-handle=1908,i,2742170741569571169,425310413108730011,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5840 --field-trial-handle=1908,i,2742170741569571169,425310413108730011,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
19 238
Read events
19 159
Write events
73
Delete events
6
Modification events
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000005A038014A368DB01 | |||
| (PID) Process: | (1668) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (6004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
199
Suspicious files
353
Text files
421
Unknown types
45
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF137022.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF137022.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF137032.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF137032.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF137032.TMP | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1668 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF137032.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
42
TCP/UDP connections
92
DNS requests
100
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6500 | chrome.exe | GET | 301 | 104.21.60.12:80 | http://placehold.it/45x45/f0f0f0/ccc | unknown | — | — | whitelisted |
6500 | chrome.exe | GET | 301 | 104.21.60.12:80 | http://placehold.it/45x45/f0f0f0/ccc | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6500 | chrome.exe | GET | 301 | 8.210.36.43:80 | http://www.elitechlog.com/wp-content/uploads/2016/08/logo.png | unknown | — | — | unknown |
6500 | chrome.exe | GET | 301 | 8.210.36.43:80 | http://www.elitechlog.com/wp-content/uploads/2016/08/logo.png | unknown | — | — | unknown |
6500 | chrome.exe | GET | 301 | 104.21.60.12:80 | http://placehold.it/45x45/f0f0f0/ccc | unknown | — | — | whitelisted |
6500 | chrome.exe | GET | 301 | 104.21.60.12:80 | http://placehold.it/45x45/f0f0f0/ccc | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6092 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 184.28.89.167:443 | go.microsoft.com | AKAMAI-AS | US | whitelisted |
1668 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
test.elitechlog.com |
| unknown |
accounts.google.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
translate.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6500 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6500 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6500 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
6500 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |