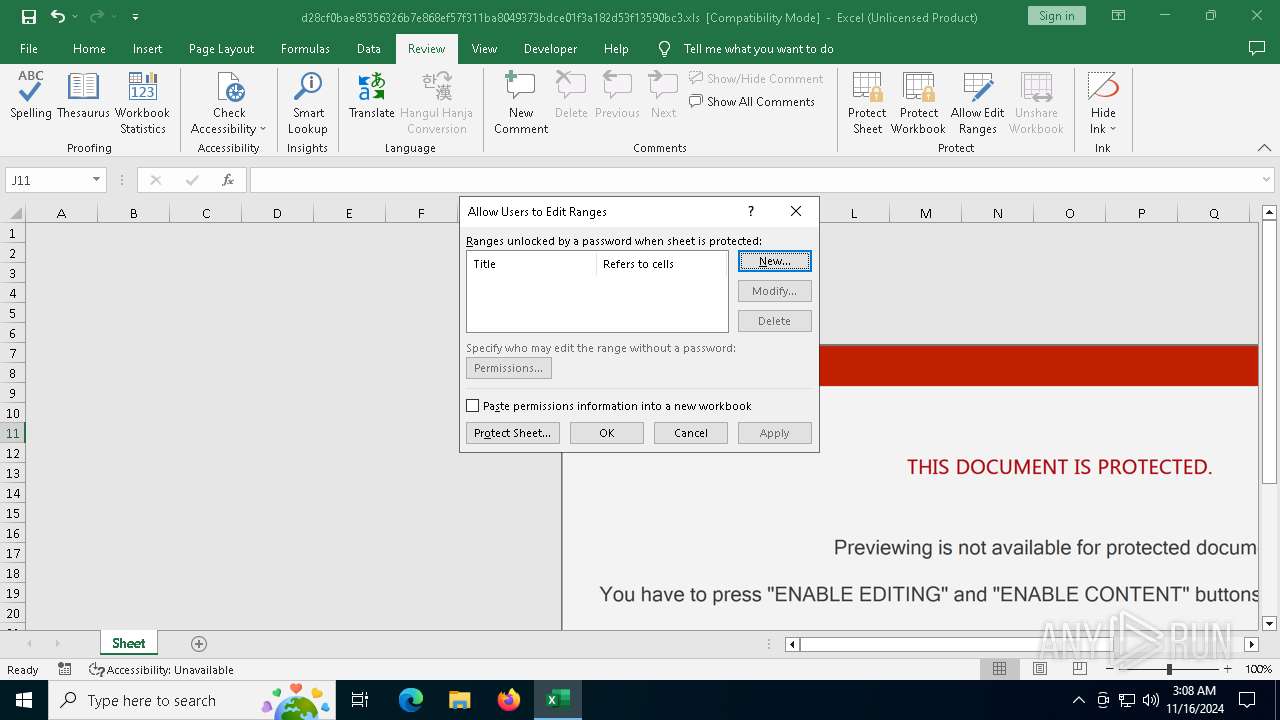
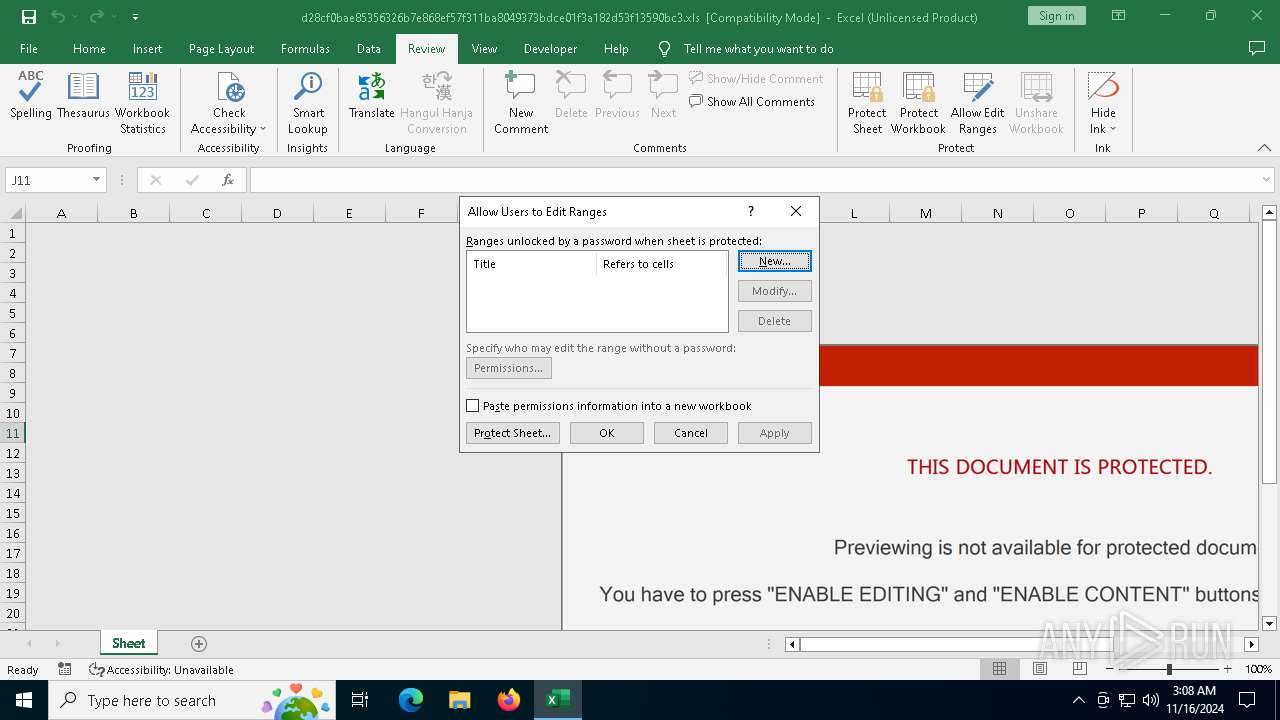
| File name: | d28cf0bae85356326b7e868ef57f311ba8049373bdce01f3a182d53f13590bc3 |
| Full analysis: | https://app.any.run/tasks/cbfb9ceb-39c9-424a-b7e2-cf0cd6809a9f |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2024, 03:07:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
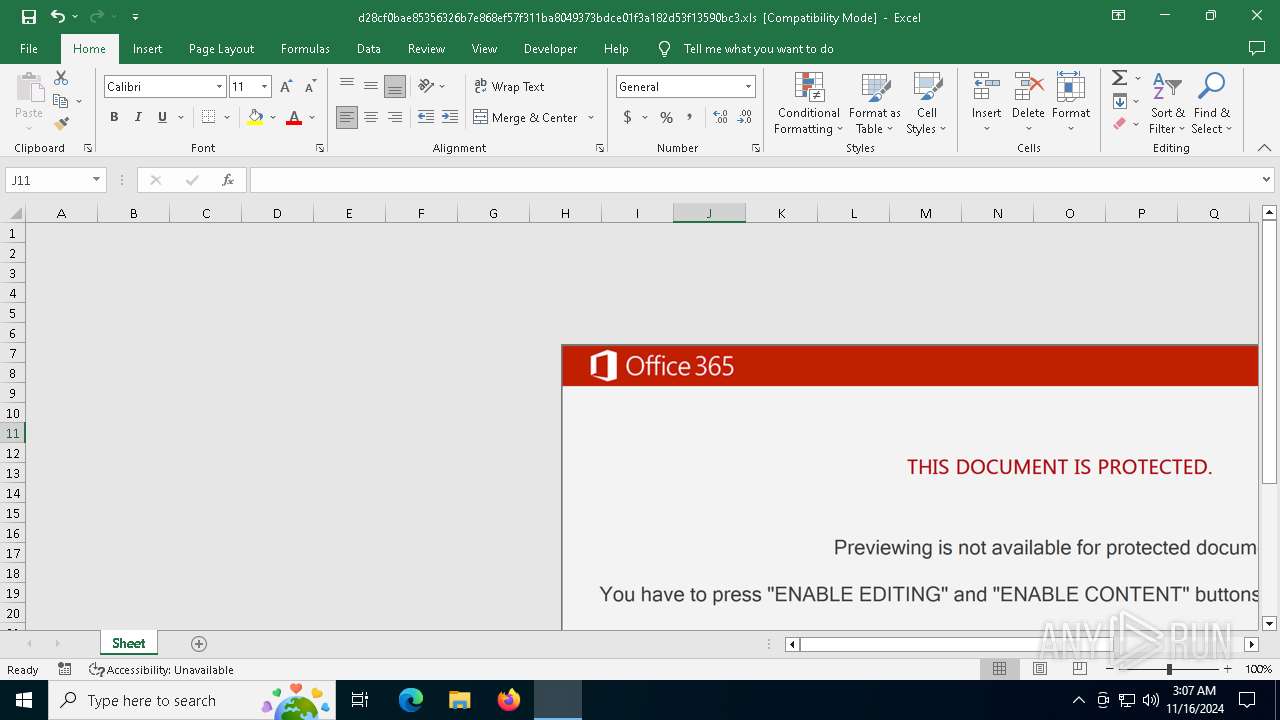
| MIME: | application/vnd.ms-excel |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Author: Admin, Last Saved By: Admin, Name of Creating Application: Microsoft Excel, Create Time/Date: Fri Jun 5 18:19:34 2015, Last Saved Time/Date: Wed Feb 23 12:16:06 2022, Security: 0 |
| MD5: | 16912EDCD428EC1A791A9D715101F8A2 |
| SHA1: | 0D12072E3ACBD8715BF6A2ED232012407D114068 |
| SHA256: | D28CF0BAE85356326B7E868EF57F311BA8049373BDCE01F3A182D53F13590BC3 |
| SSDEEP: | 6144:eB/PWRViukoamHNo+5t3JNi/rj9s1BH2whBrmg:eB/4JjaqNoS5U/yrWU |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- EXCEL.EXE (PID: 6704)
Calls Win API functions (MACROS)
- EXCEL.EXE (PID: 6704)
Unusual execution from MS Office
- EXCEL.EXE (PID: 6704)
SUSPICIOUS
No suspicious indicators.INFO
The process uses the downloaded file
- EXCEL.EXE (PID: 6704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | Admin |
|---|---|
| LastModifiedBy: | Admin |
| Software: | Microsoft Excel |
| CreateDate: | 2015:06:05 18:19:34 |
| ModifyDate: | 2022:02:23 12:16:06 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
129
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1732 | C:\Windows\SysWow64\regsvr32.exe /s ..\xxw1.ocx | C:\Windows\SysWOW64\regsvr32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 3 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6704 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" C:\Users\admin\Desktop\d28cf0bae85356326b7e868ef57f311ba8049373bdce01f3a182d53f13590bc3.xls | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
9 422
Read events
9 179
Write events
223
Delete events
20
Modification events
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 1 |
Value: 01D014000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\EXCEL\6704 |
| Operation: | write | Name: | 0 |
Value: 0B0E10110B69EC7505134D901377833E8EC525230046999188F4CAFACDED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B034D2120965007800630065006C002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6704) EXCEL.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
14
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6704 | EXCEL.EXE | C:\Users\admin\xxw1.ocx | binary | |
MD5:A446832E3B35686DAE1C6B72CFE7746F | SHA256:8181E261F4AE67D25C64502E14ACF38E6057579E0EB2A63DADE029A1335075DA | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\DX1C3E7XE6YT3SMV098I.temp | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\F7P4XGHISY4CIGK692QD.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms~RF923d8.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\d28cf0bae85356326b7e868ef57f311ba8049373bdce01f3a182d53f13590bc3.xls.LNK | binary | |
MD5:7CD68318449C98A31F17D3B1FB9B7EF9 | SHA256:E64AB919A9462FE4A1911D27E55779A2230156E8D42B1368673161213A67BCCB | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:DAC91D93B7D25EA9E3661CEC023033CB | SHA256:BCF752F6FA8893976B27385997BD3957715C7FDD147EC908F386C27B2E87C86A | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\9C2AAAED-6435-47A2-8AF9-D5288E683F39 | xml | |
MD5:1C186F5A4C09BB8B53A318FDAE68F94C | SHA256:8C7CFD62111B4E57BA92B8193CD626E55D867F42928AF1D1B5AECA5258E4E52D | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\b8ab77100df80ab2.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\YWRB9EAG.htm | binary | |
MD5:A446832E3B35686DAE1C6B72CFE7746F | SHA256:8181E261F4AE67D25C64502E14ACF38E6057579E0EB2A63DADE029A1335075DA | |||
| 6704 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Excel\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:1048CFFCDB1210A046BA43CF6F1B50D7 | SHA256:F0EDB7196CBBB51DA3D77391703E2370C8EBBD9C306C1EF5AAAB79935824BC74 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
34
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6944 | svchost.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6908 | RUXIMICS.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 404 | 18.245.46.75:443 | https://dalgahavuzu.com/pwkfky/LF0WU/ | unknown | — | — | unknown |
— | — | GET | 302 | 86.105.245.69:443 | https://sandiegoinsuranceagents.com/cgi-bin/XK1VSXZddLdN/ | unknown | — | — | unknown |
— | — | HEAD | 200 | 2.18.160.41:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/version.json | unknown | — | — | unknown |
— | — | GET | 200 | 2.18.160.41:443 | https://uci.cdn.office.net/mirrored/smartlookup/current/version.json | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6908 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
5488 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.23.209.140:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6908 | RUXIMICS.exe | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
6944 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
dalgahavuzu.com |
| malicious |
ecs.office.com |
| whitelisted |
dolphinsupremehavuzrobotu.com |
| malicious |
sandiegoinsuranceagents.com |
| malicious |