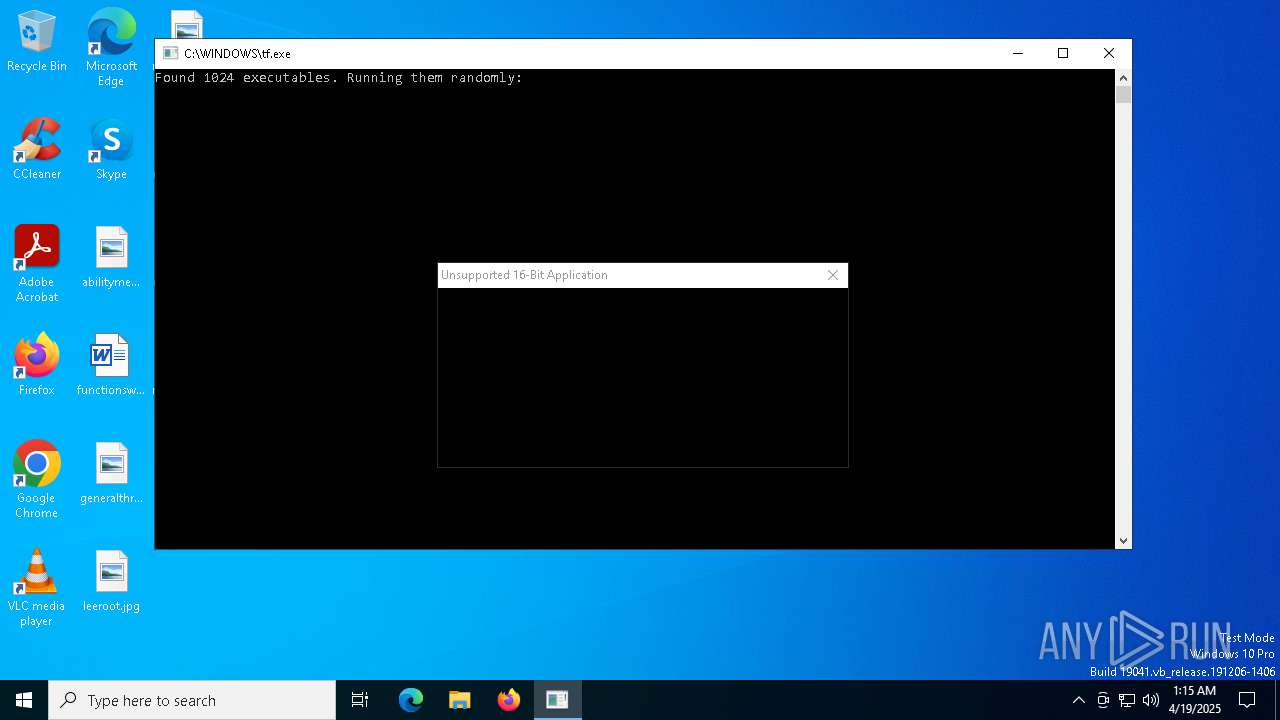
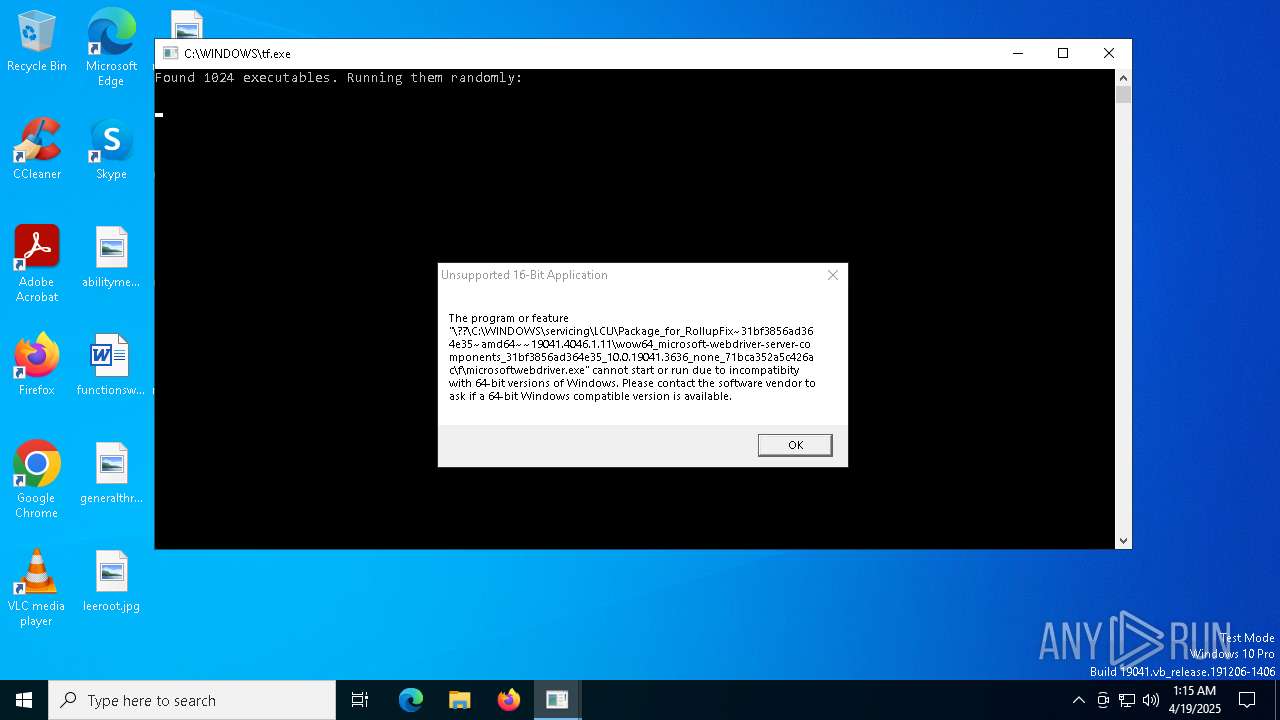
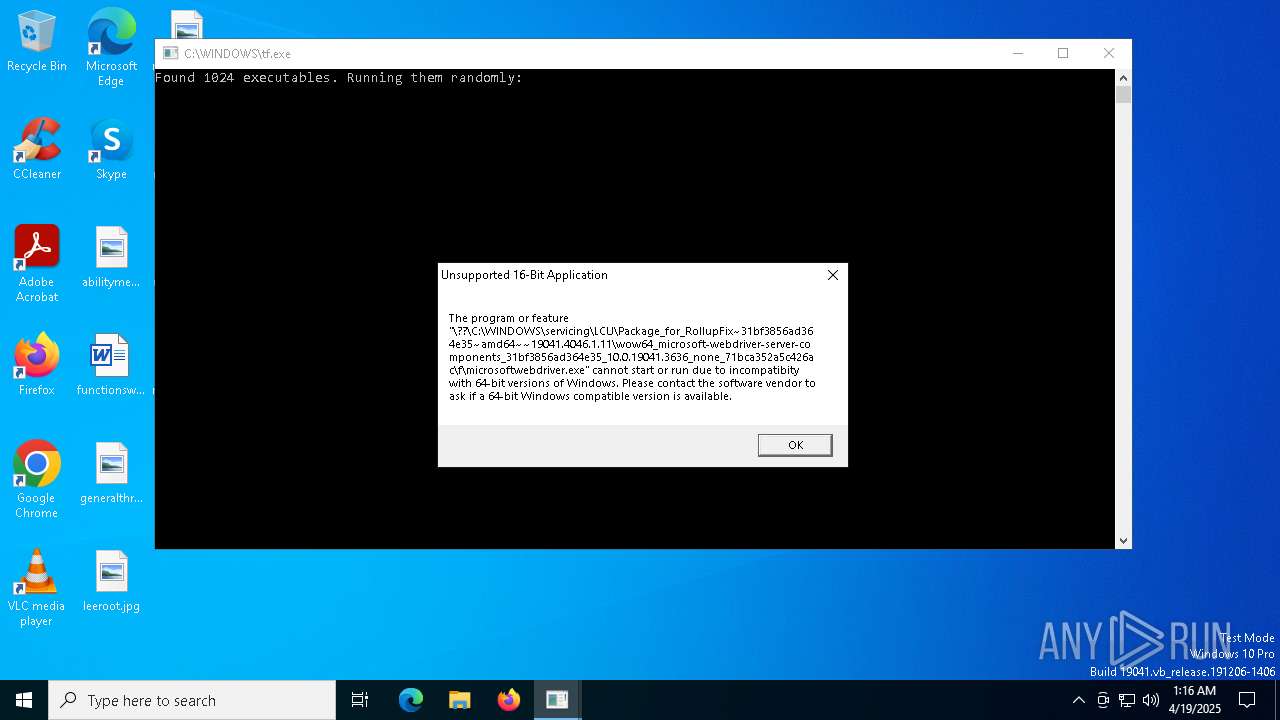
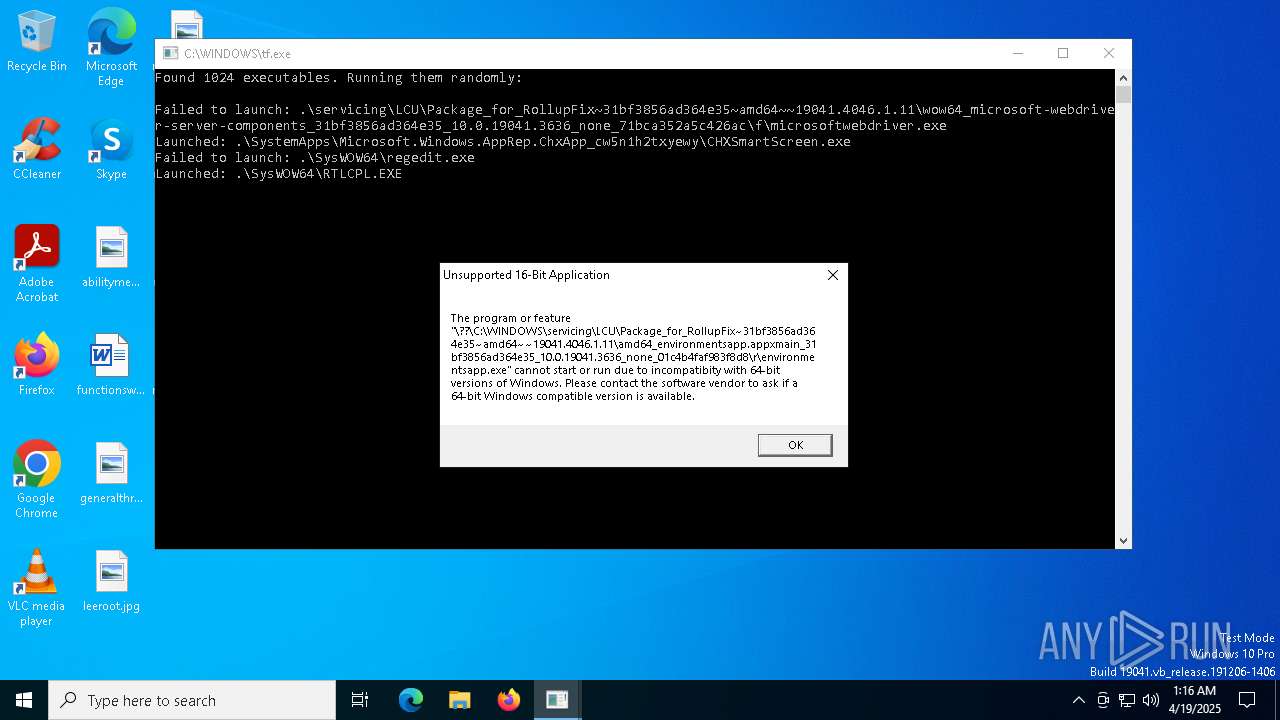
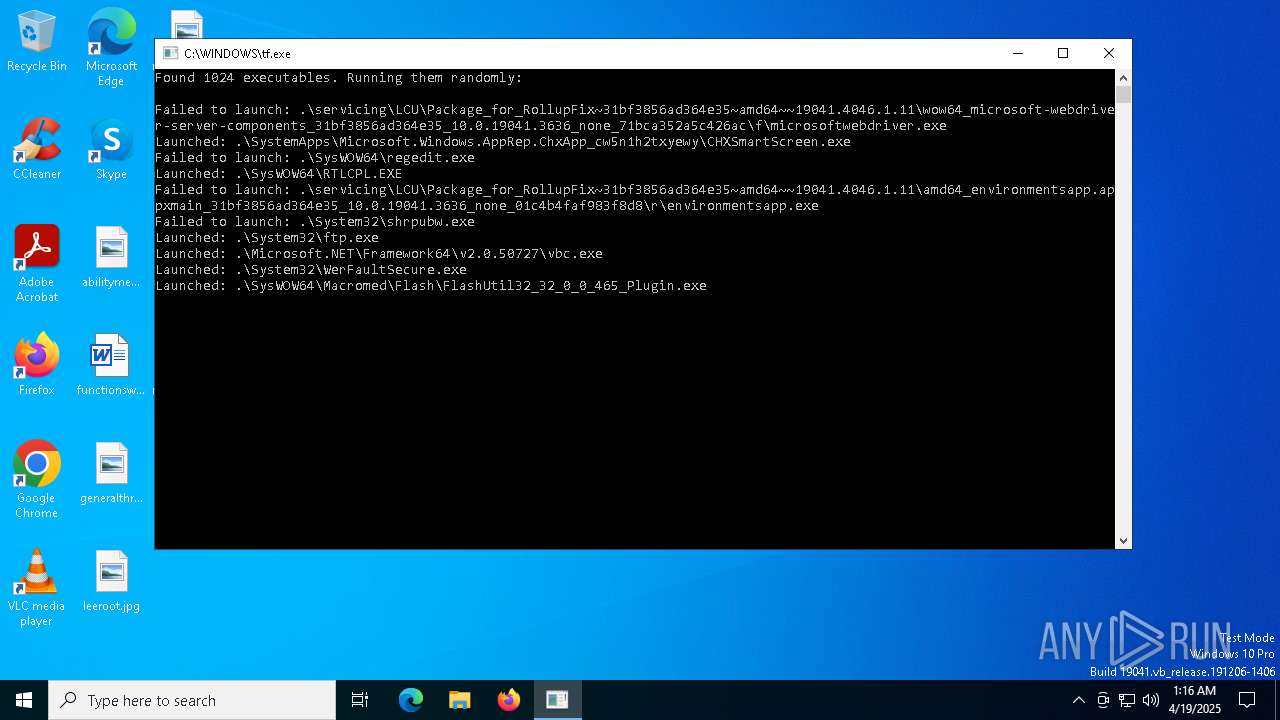
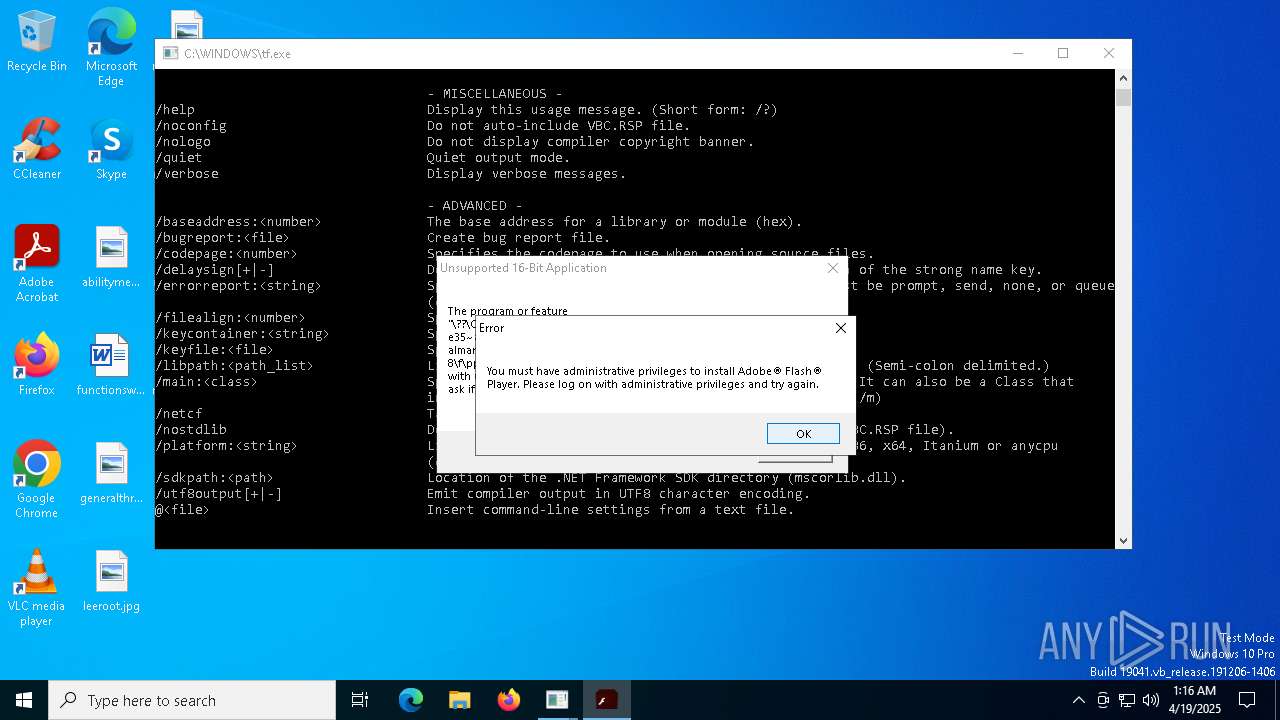
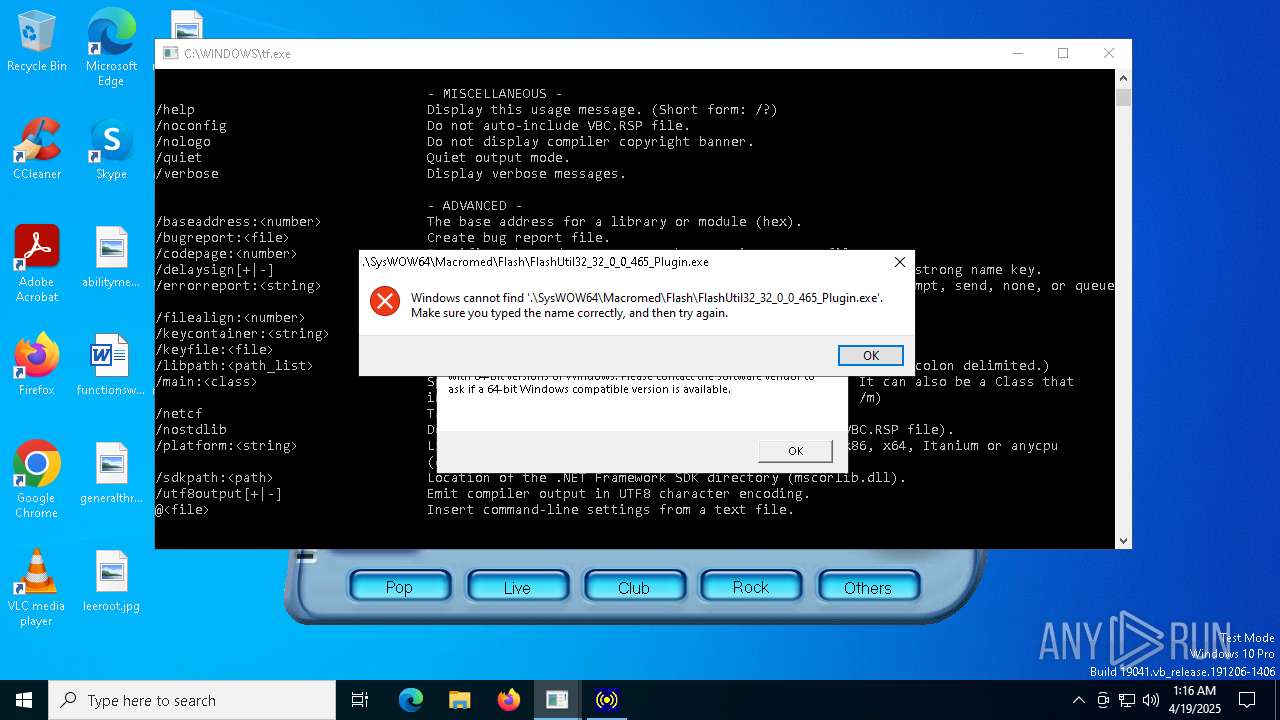
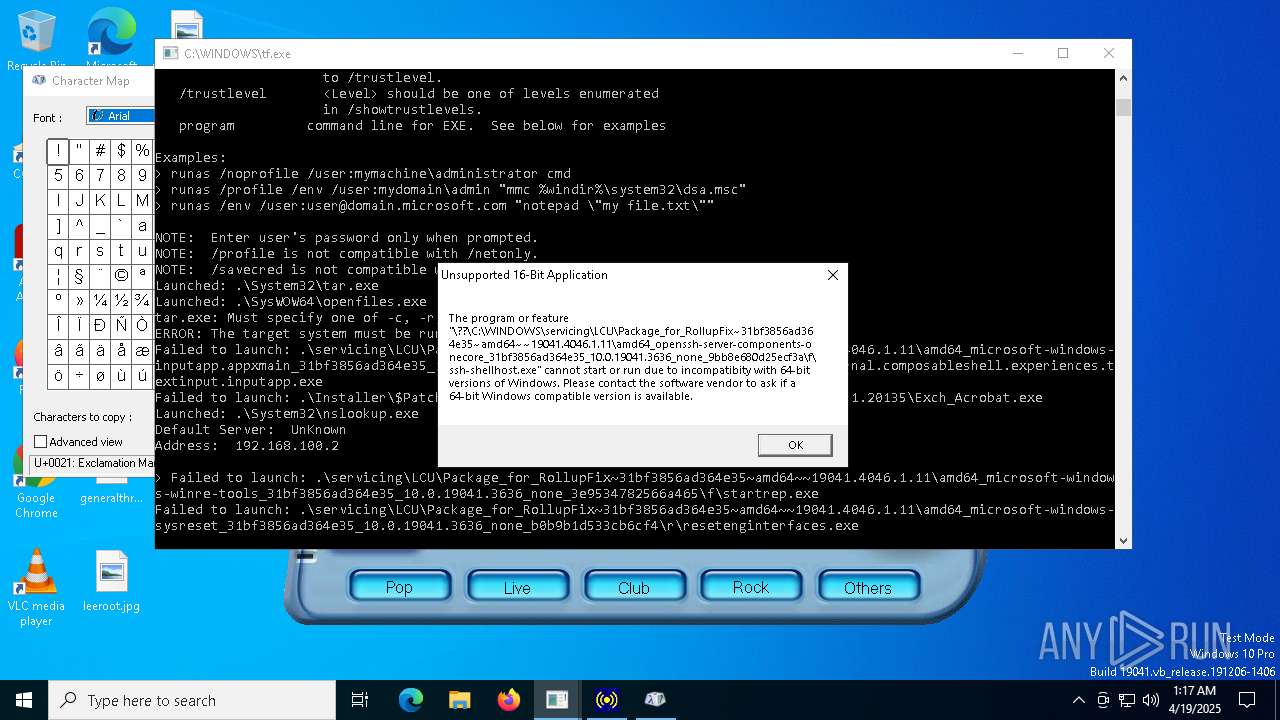
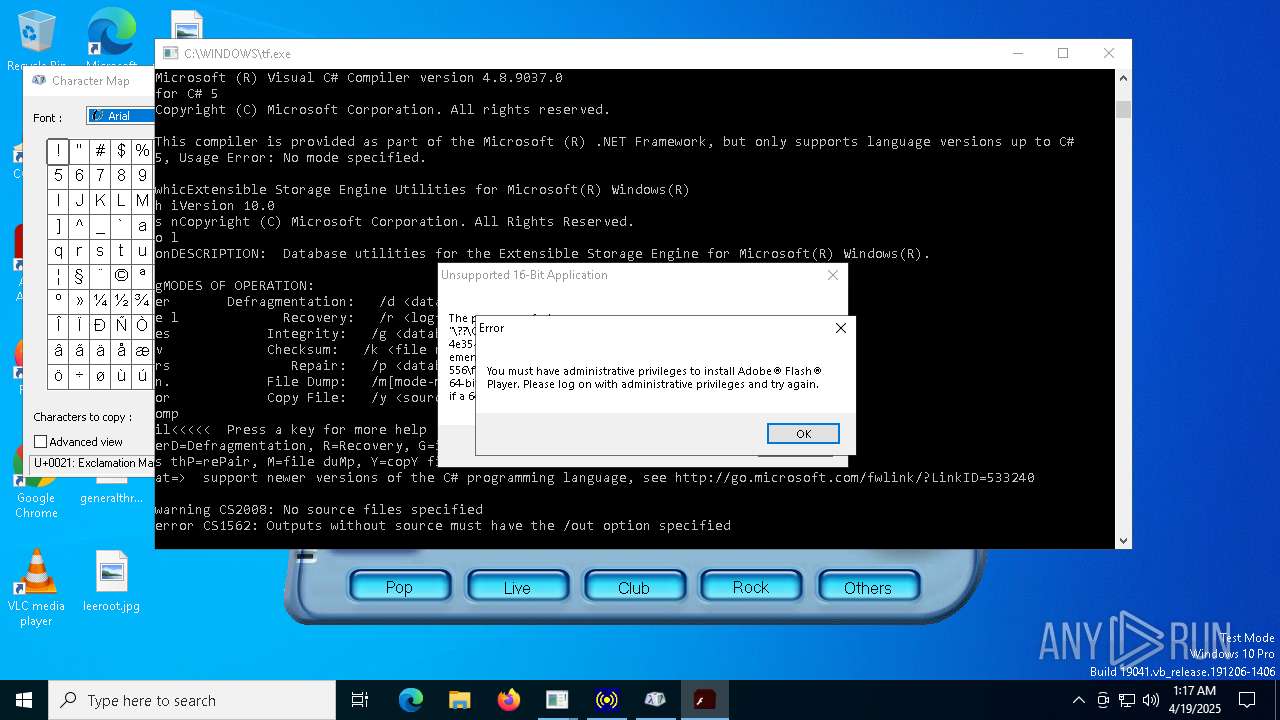
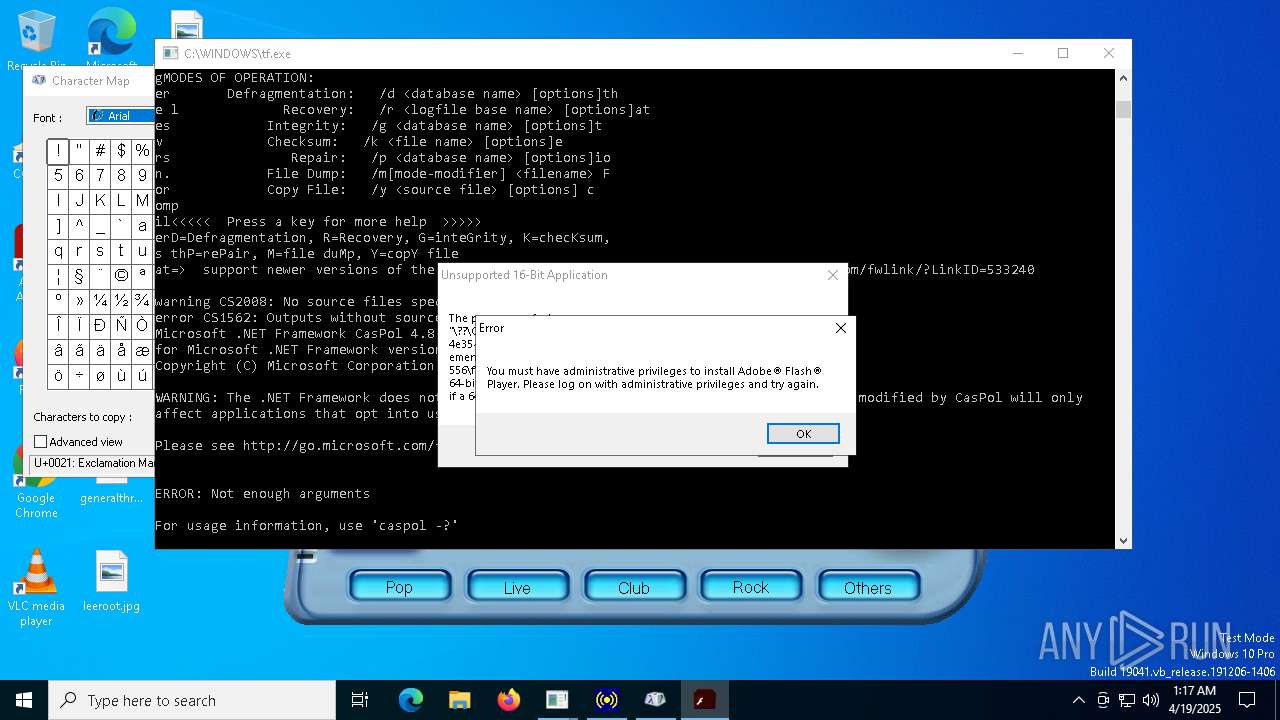
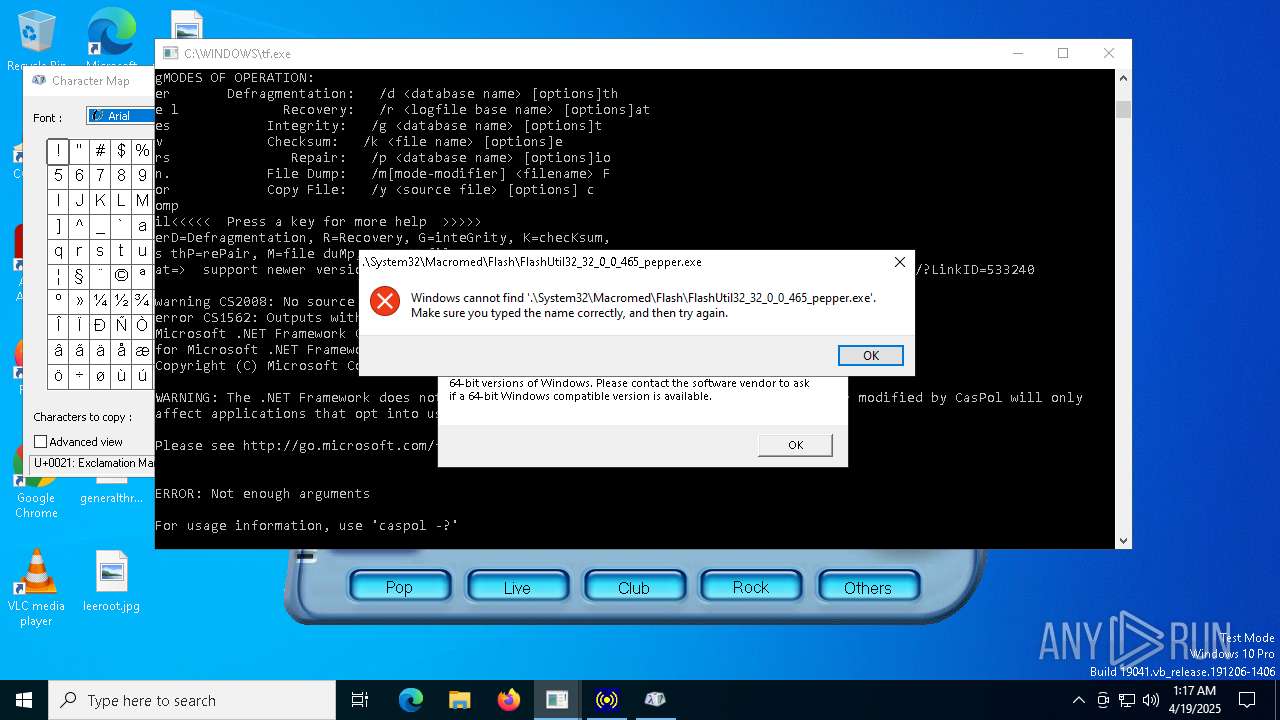
| File name: | tf.exe |
| Full analysis: | https://app.any.run/tasks/46705aa8-046c-4f69-831f-db8e7e022026 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 01:14:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 4 sections |
| MD5: | 1453B76FAECEDA78A408287799CA5C40 |
| SHA1: | A8E815A62389523216639CDE22148F919E782727 |
| SHA256: | D28CD43A927F71D058B752703416C42B4C7C5A1D35E6BF99D9A53EACE2D1563C |
| SSDEEP: | 768:LB1TVTxyxEMlpSQq3aoUWckZYM6RE+HRmzPm9Fz:dlVgxDlguxWckuRE+6Kz |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- sfc.exe (PID: 6940)
SUSPICIOUS
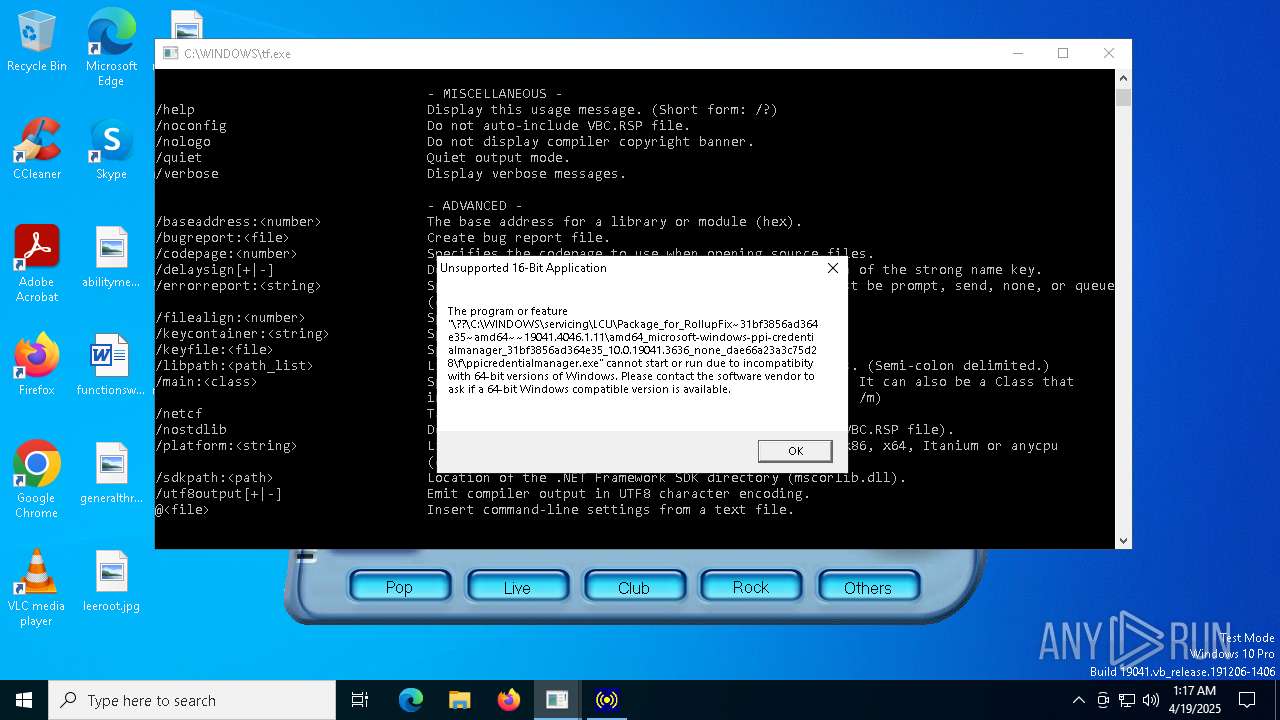
Executes application which crashes
- CHXSmartScreen.exe (PID: 5428)
- AddSuggestedFoldersToLibraryDialog.exe (PID: 4608)
- SecHealthUI.exe (PID: 5376)
- NarratorQuickStart.exe (PID: 5188)
- OOBENetworkCaptivePortal.exe (PID: 4040)
- Microsoft.AAD.BrokerPlugin.exe (PID: 1128)
Executable content was dropped or overwritten
- RTLCPL.EXE (PID: 6872)
- OneDriveSetup.exe (PID: 5244)
Creates file in the systems drive root
- RTLCPL.EXE (PID: 6872)
There is functionality for taking screenshot (YARA)
- RTBK.EXE (PID: 2516)
Uses ICACLS.EXE to modify access control lists
- tf.exe (PID: 2320)
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 2896)
Uses NSLOOKUP.EXE to check DNS info
- tf.exe (PID: 2320)
Reads security settings of Internet Explorer
- CasPol.exe (PID: 1128)
- ComSvcConfig.exe (PID: 7812)
Reads the date of Windows installation
- dw20.exe (PID: 5984)
Starts POWERSHELL.EXE for commands execution
- tf.exe (PID: 2320)
Get information on the list of running processes
- tf.exe (PID: 2320)
Application launched itself
- OneDriveSetup.exe (PID: 3796)
Reads Microsoft Outlook installation path
- mshta.exe (PID: 5212)
Reads Internet Explorer settings
- mshta.exe (PID: 5212)
Uses SYSTEMINFO.EXE to read the environment
- stordiag.exe (PID: 3992)
Process copies executable file
- tf.exe (PID: 2320)
Searches and executes a command on selected files
- forfiles.exe (PID: 4884)
Starts CMD.EXE for commands execution
- forfiles.exe (PID: 4884)
The process creates files with name similar to system file names
- OneDriveSetup.exe (PID: 5244)
Reads the history of recent RDP connections
- mstsc.exe (PID: 7624)
- mstsc.exe (PID: 8060)
The process drops C-runtime libraries
- OneDriveSetup.exe (PID: 5244)
INFO
Reads the software policy settings
- slui.exe (PID: 5124)
- slui.exe (PID: 5260)
- powershell.exe (PID: 1748)
- dw20.exe (PID: 5984)
- OneDriveSetup.exe (PID: 3796)
- OneDriveSetup.exe (PID: 5244)
- stordiag.exe (PID: 3992)
- ComSvcConfig.exe (PID: 7812)
Reads the computer name
- tf.exe (PID: 2320)
- RTBK.EXE (PID: 2516)
- RTLCPL.EXE (PID: 6872)
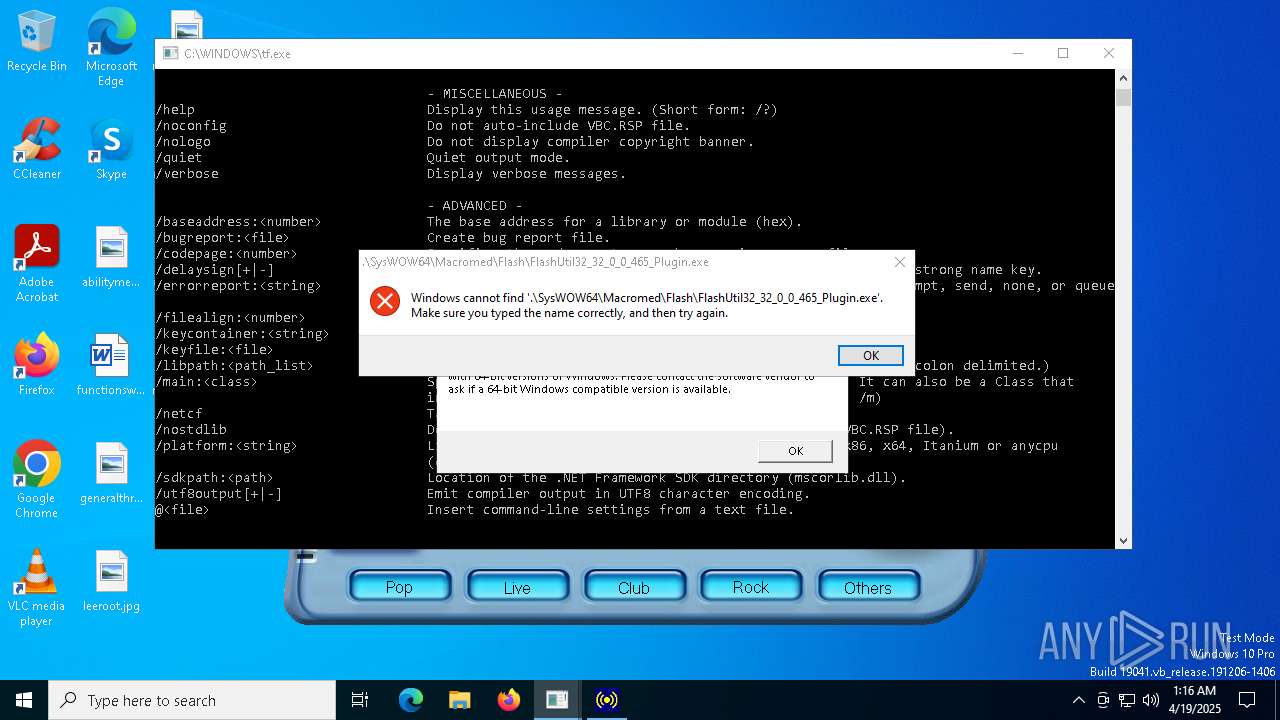
- FlashUtil32_32_0_0_465_Plugin.exe (PID: 2244)
- FlashUtil32_32_0_0_465_pepper.exe (PID: 680)
- CasPol.exe (PID: 1128)
- dw20.exe (PID: 5984)
- aspnet_state.exe (PID: 1184)
- aspnet_regsql.exe (PID: 7136)
- TrustedInstaller.exe (PID: 5188)
- WsatConfig.exe (PID: 3800)
- MSBuild.exe (PID: 6516)
- AddInProcess32.exe (PID: 720)
- RegSvcs.exe (PID: 4164)
- BitLockerToGo.exe (PID: 6640)
- logtransport2.exe (PID: 1812)
- PSEXESVC.exe (PID: 6744)
- AddInUtil.exe (PID: 7228)
- WsatConfig.exe (PID: 1128)
- acrobroker.exe (PID: 7584)
- MSBuild.exe (PID: 7636)
- aspnet_regsql.exe (PID: 7792)
- ComSvcConfig.exe (PID: 7812)
Checks supported languages
- tf.exe (PID: 2320)
- RTLCPL.EXE (PID: 6872)
- CHXSmartScreen.exe (PID: 5428)
- RTBK.EXE (PID: 2516)
- CPLUtl64.exe (PID: 4164)
- vbc.exe (PID: 6372)
- ilasm.exe (PID: 3124)
- AddInProcess.exe (PID: 5452)
- tar.exe (PID: 6980)
- FlashUtil32_32_0_0_465_pepper.exe (PID: 680)
- CasPol.exe (PID: 1128)
- FlashUtil32_32_0_0_465_Plugin.exe (PID: 2244)
- IEExec.exe (PID: 2420)
- dw20.exe (PID: 5984)
- AddSuggestedFoldersToLibraryDialog.exe (PID: 4608)
- aspnet_state.exe (PID: 1184)
- TrustedInstaller.exe (PID: 5188)
- SecHealthUI.exe (PID: 5376)
- PresentationHost.exe (PID: 4884)
- aspnet_compiler.exe (PID: 1128)
- CasPol.exe (PID: 2776)
- WsatConfig.exe (PID: 3800)
- aspnet_regsql.exe (PID: 7136)
- AddInProcess32.exe (PID: 720)
- NarratorQuickStart.exe (PID: 5188)
- aspnet_regbrowsers.exe (PID: 2384)
- MSBuild.exe (PID: 6516)
- BitLockerToGo.exe (PID: 6640)
- csc.exe (PID: 2776)
- UndockedDevKit.exe (PID: 2560)
- dw20.exe (PID: 1040)
- RegSvcs.exe (PID: 4164)
- logtransport2.exe (PID: 1812)
- OOBENetworkCaptivePortal.exe (PID: 4040)
- RegSvcs.exe (PID: 2568)
- csc.exe (PID: 7052)
- Microsoft.AAD.BrokerPlugin.exe (PID: 1128)
- PSEXESVC.exe (PID: 6744)
- WsatConfig.exe (PID: 1128)
- AddInUtil.exe (PID: 7228)
- acrobroker.exe (PID: 7584)
- MSBuild.exe (PID: 7636)
- aspnet_regsql.exe (PID: 7792)
- ComSvcConfig.exe (PID: 7812)
- AddInUtil.exe (PID: 8168)
Checks proxy server information
- slui.exe (PID: 5260)
- dw20.exe (PID: 5984)
- ComSvcConfig.exe (PID: 7812)
Create files in a temporary directory
- RTLCPL.EXE (PID: 6872)
- powershell.exe (PID: 1748)
- OneDriveSetup.exe (PID: 3796)
- OneDriveSetup.exe (PID: 5244)
- stordiag.exe (PID: 3992)
The sample compiled with english language support
- RTLCPL.EXE (PID: 6872)
- OneDriveSetup.exe (PID: 5244)
Creates files or folders in the user directory
- WerFault.exe (PID: 4336)
- WerFault.exe (PID: 6268)
- WerFault.exe (PID: 6576)
- dw20.exe (PID: 5984)
- WerFault.exe (PID: 3804)
- RMActivate.exe (PID: 4652)
- OneDriveSetup.exe (PID: 3796)
- WerFault.exe (PID: 3016)
- OneDriveSetup.exe (PID: 5244)
- WerFault.exe (PID: 2340)
- ComSvcConfig.exe (PID: 7812)
Process checks whether UAC notifications are on
- FlashUtil32_32_0_0_465_Plugin.exe (PID: 2244)
- FlashUtil32_32_0_0_465_pepper.exe (PID: 680)
Compiled with Borland Delphi (YARA)
- RTLCPL.EXE (PID: 6872)
Disables trace logs
- cmstp.exe (PID: 5308)
- cmmon32.exe (PID: 5116)
- rasphone.exe (PID: 132)
Reads the machine GUID from the registry
- dw20.exe (PID: 5984)
- aspnet_regsql.exe (PID: 7136)
- aspnet_regsql.exe (PID: 7792)
- ComSvcConfig.exe (PID: 7812)
Process checks computer location settings
- dw20.exe (PID: 5984)
Reads Environment values
- dw20.exe (PID: 5984)
Creates files in the program directory
- dw20.exe (PID: 5984)
- wermgr.exe (PID: 7552)
Reads CPU info
- dw20.exe (PID: 5984)
Reads product name
- dw20.exe (PID: 5984)
Reads security settings of Internet Explorer
- certreq.exe (PID: 3976)
- powershell.exe (PID: 1748)
- OneDriveSetup.exe (PID: 3796)
- OneDriveSetup.exe (PID: 5244)
- mshta.exe (PID: 5212)
- mstsc.exe (PID: 7624)
- mstsc.exe (PID: 8060)
- stordiag.exe (PID: 3992)
Checks current location (POWERSHELL)
- powershell.exe (PID: 1748)
Reads the time zone
- runonce.exe (PID: 6372)
Checks transactions between databases Windows and Oracle
- ComSvcConfig.exe (PID: 7812)
The sample compiled with chinese language support
- OneDriveSetup.exe (PID: 5244)
Checks if a key exists in the options dictionary (POWERSHELL)
- stordiag.exe (PID: 3992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win16/32 Executable Delphi generic (34.1) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (32.9) |
| .exe | | | DOS Executable Generic (32.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:19 01:12:53+00:00 |
| ImageFileCharacteristics: | Executable, Bytes reversed lo, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.18 |
| CodeSize: | 28672 |
| InitializedDataSize: | 3584 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1898 |
| OSVersion: | 1.11 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
Total processes
434
Monitored processes
283
Malicious processes
3
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | .\System32\secinit.exe | C:\Windows\SysWOW64\secinit.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Security Init Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 132 | .\SysWOW64\rasphone.exe | C:\Windows\SysWOW64\rasphone.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Access Phonebook Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | /c echo "Vss" | C:\Windows\SysWOW64\cmd.exe | — | forfiles.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | .\regedit.exe | C:\Windows\SysWOW64\regedit.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | .\System32\xcopy.exe | C:\Windows\SysWOW64\xcopy.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extended Copy Utility Exit code: 4 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | .\SysWOW64\PackagedCWALauncher.exe | C:\Windows\SysWOW64\PackagedCWALauncher.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Packaged CWA Launcher Exit code: 2147942487 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | .\System32\isoburn.exe | C:\Windows\SysWOW64\isoburn.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Disc Image Burning Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | .\System32\WerFaultSecure.exe | C:\Windows\SysWOW64\WerFaultSecure.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Fault Reporting Exit code: 1 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | .\System32\SearchProtocolHost.exe | C:\Windows\SysWOW64\SearchProtocolHost.exe | — | tf.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
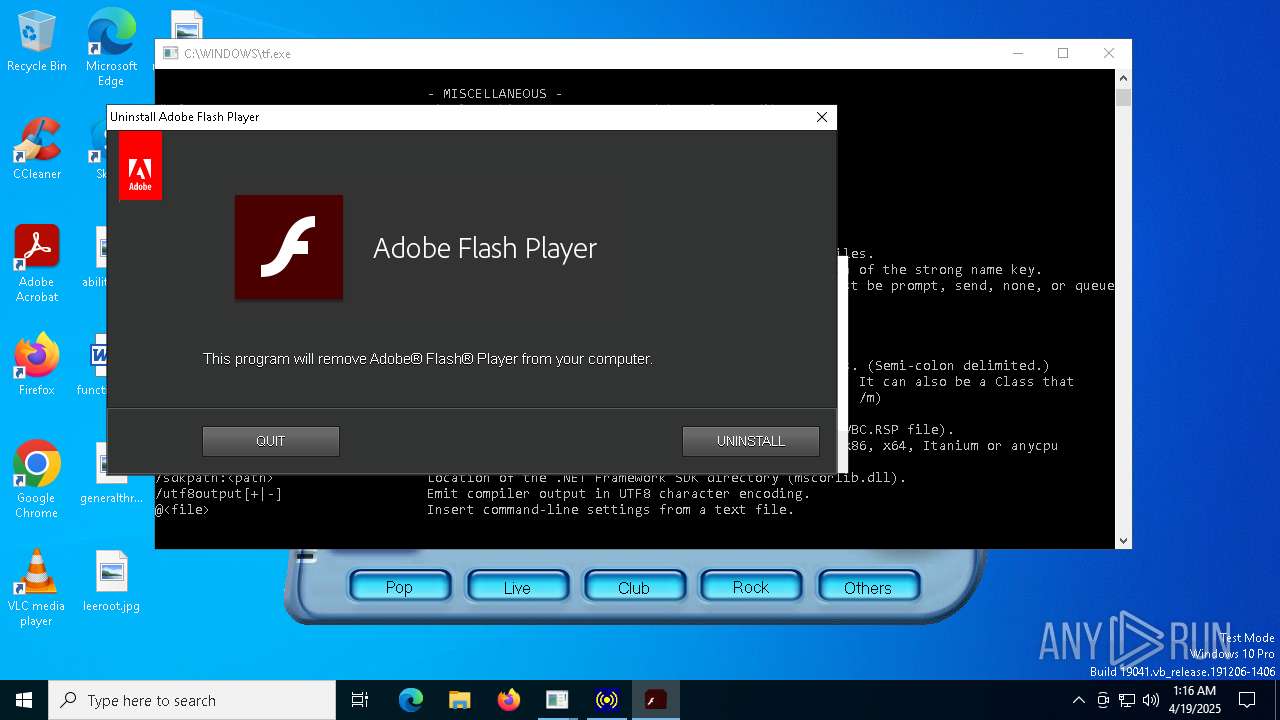
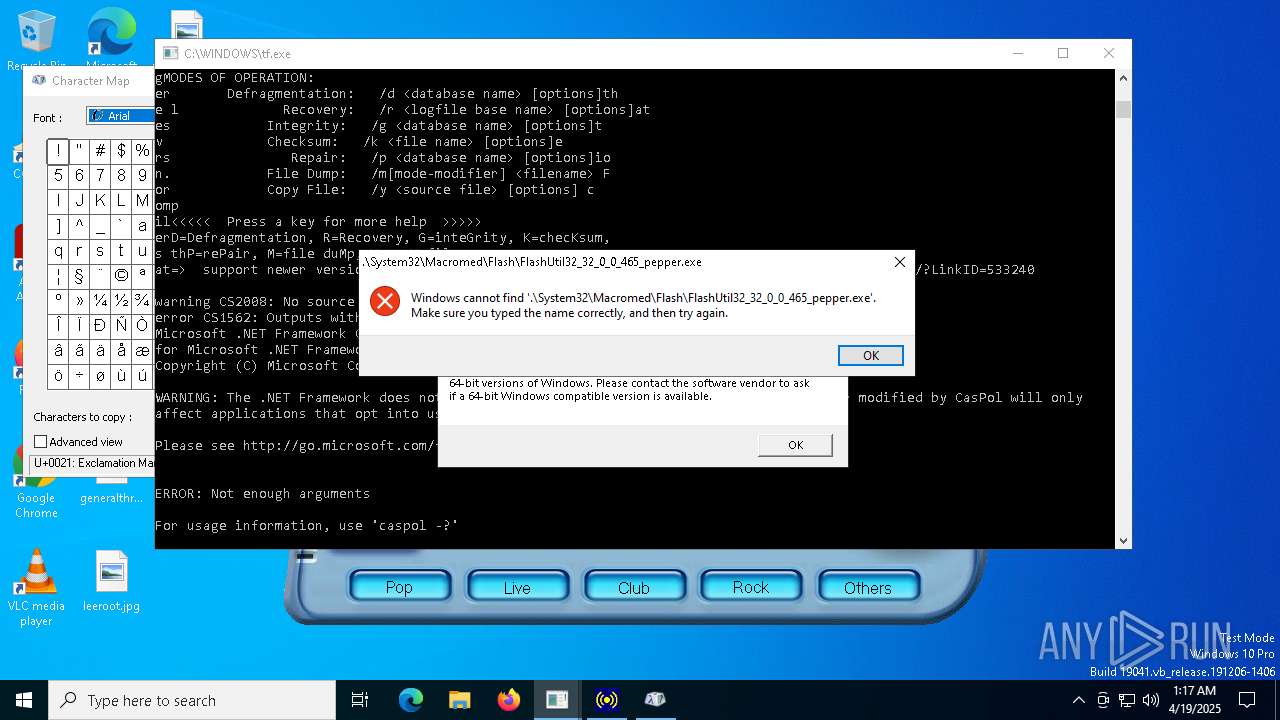
| 680 | .\System32\Macromed\Flash\FlashUtil32_32_0_0_465_pepper.exe | C:\Windows\SysWOW64\Macromed\Flash\FlashUtil32_32_0_0_465_pepper.exe | — | tf.exe | |||||||||||
User: admin Company: Adobe Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 32.0 r0 Exit code: 1039 Version: 32,0,0,465 Modules
| |||||||||||||||
Total events
55 694
Read events
55 535
Write events
157
Delete events
2
Modification events
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | guidDXsoundW |
Value: {9A7A2494-D921-4B91-8899-38D44CD79857} | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | APO |
Value: 01 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | VoiceCancel |
Value: 00 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | KeyValue |
Value: 0 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | EQEnable |
Value: 0 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | EQGain0 |
Value: 3997797 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | EQGain1 |
Value: 3801155 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | EQGain2 |
Value: 5439488 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | EQGain3 |
Value: 7536761 | |||
| (PID) Process: | (2516) RTBK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Realtek\RTBK |
| Operation: | write | Name: | EQGain4 |
Value: 6619252 | |||
Executable files
178
Suspicious files
35
Text files
109
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_CHXSmartScreen.e_c5bda8729b4e8fabe3e5eb81f2d3493db3d727e_8ca06682_7d1e5853-92d6-42fc-9afa-84f790a9c617\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5280 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2025-04-19.0114.5280.1.aodl | binary | |
MD5:28DCA2FF4B34B5A52A2E59DF202A6ED3 | SHA256:33BACCB7296F1ED1F995FC77A23049F261CF391AC0388F9E8DD161F8C17B7F94 | |||
| 6872 | RTLCPL.EXE | C:\Users\admin\AppData\Local\Temp\RTBK.EXE | executable | |
MD5:2CE4EC25271A7EB106787C63B5BD5F79 | SHA256:2838CC2653AD5132484A6DB00E5D386AA6EB4AA7A8B0BD71C64FCAF21C1676F6 | |||
| 4336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER812.tmp.dmp | binary | |
MD5:93A8454D03313F414C9A19A523276334 | SHA256:BA762ADD0B21DB58EB083F64D15CECBCA6897B4E53E4D1CBAD6C88FB4D4C89BC | |||
| 4336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER99A.tmp.xml | xml | |
MD5:CE96577D5F8883B2BF8DC8DDD7A7FBF1 | SHA256:017A6B612780627656FEB9E01B5A345FD45E0BF12059763F9531F0D1C7566B8B | |||
| 5280 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2025-04-19.0114.5280.1.odl | binary | |
MD5:F7259D1FF2E1652A71BAE54D0505815B | SHA256:973F824FC254DDB6DEC3CD87E1FD6D4791ED86BE45006F89389C367C3CAECE5F | |||
| 4336 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER97A.tmp.WERInternalMetadata.xml | binary | |
MD5:8030C74D71F08458EFBFE20EC5F5175E | SHA256:41BED4A9112957EF6B9A238CE0868077049758310CC3E6CFC1BADD58F78A9E45 | |||
| 6872 | RTLCPL.EXE | C:\Users\admin\AppData\Local\Temp\Lang\German.bin | text | |
MD5:7147EACA00AF72F09D3F1D20B7F944A5 | SHA256:92CDBCCE444D68AD2306410A66ED35F809D1AB1FAA3F7B1DCA274E98378E6131 | |||
| 6872 | RTLCPL.EXE | C:\Users\admin\AppData\Local\Temp\Lang\Italian.bin | text | |
MD5:6A690A5222E98F3EF051C7D6D82F98BE | SHA256:788629EDDBA70708E4E5C7A76FB38EFC186B992F847A9B695B3E102D190E45BD | |||
| 6872 | RTLCPL.EXE | C:\Users\admin\AppData\Local\Temp\Lang\Russian.bin | text | |
MD5:9B7CDBAB54BA67BE883F71E54F291EBD | SHA256:F963433C6EBFF048CE1355691E43D77B6E90EA1C596A1115CB7BE4F45D146D4B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
35
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
976 | RUXIMICS.exe | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5112 | SIHClient.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5112 | SIHClient.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5984 | dw20.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5984 | dw20.exe | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7812 | ComSvcConfig.exe | GET | 200 | 23.222.86.92:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.21.245.142:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
976 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
976 | RUXIMICS.exe | 2.21.245.142:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.21.245.142:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.21.245.142:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |