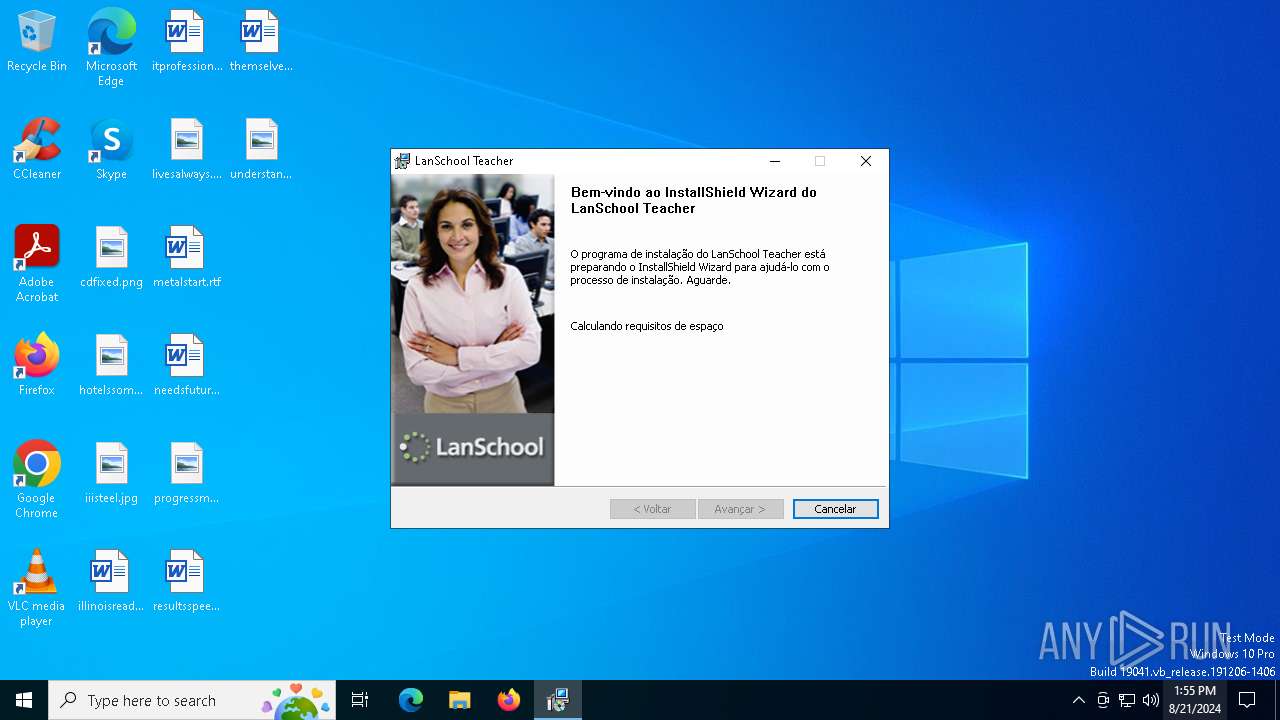
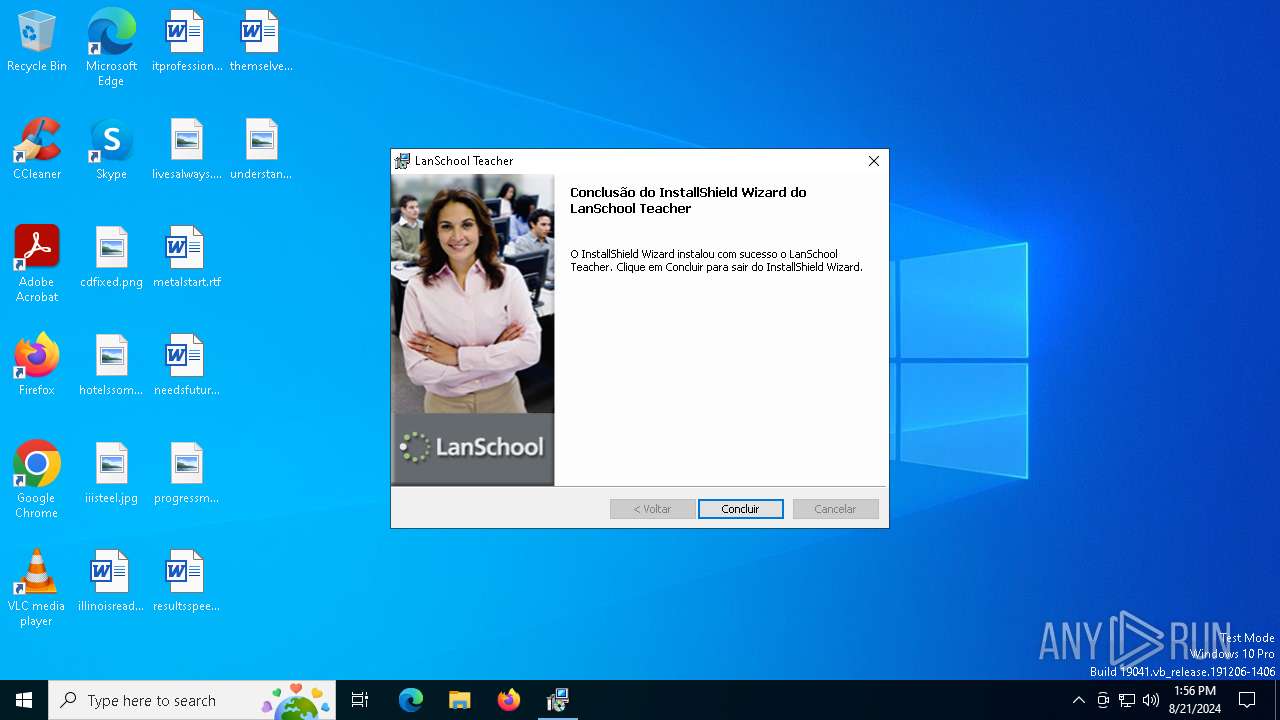
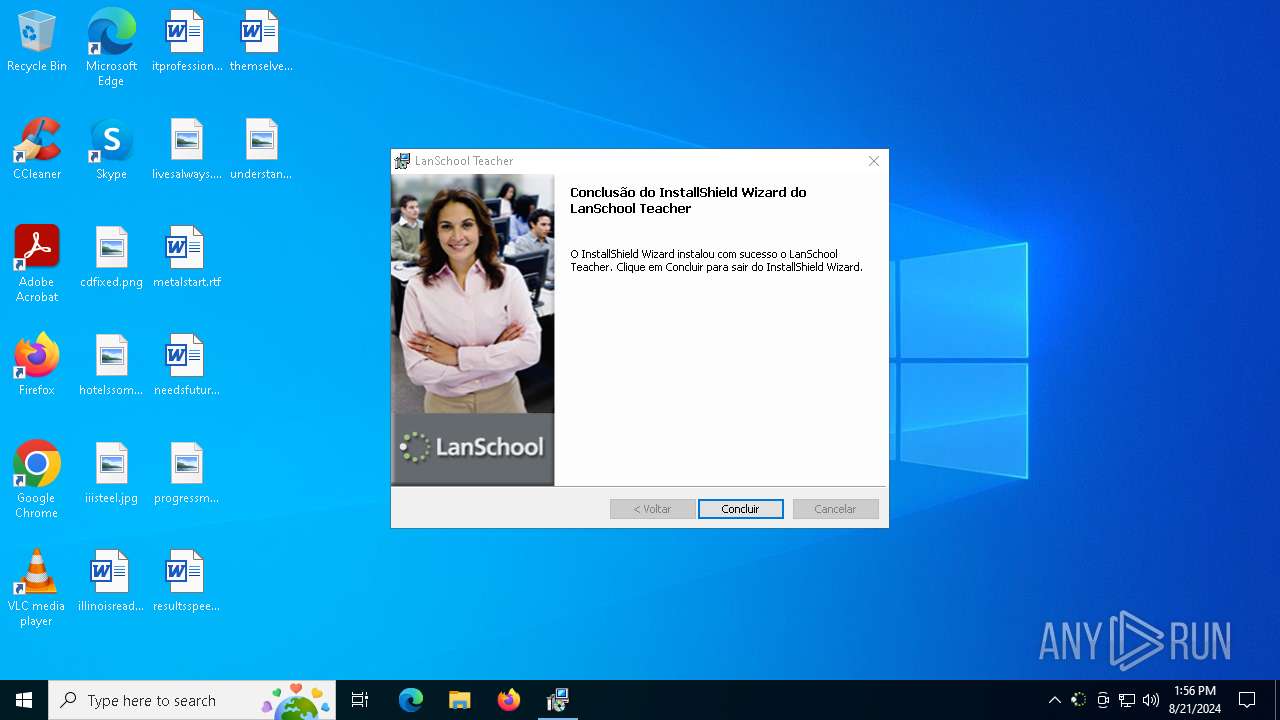
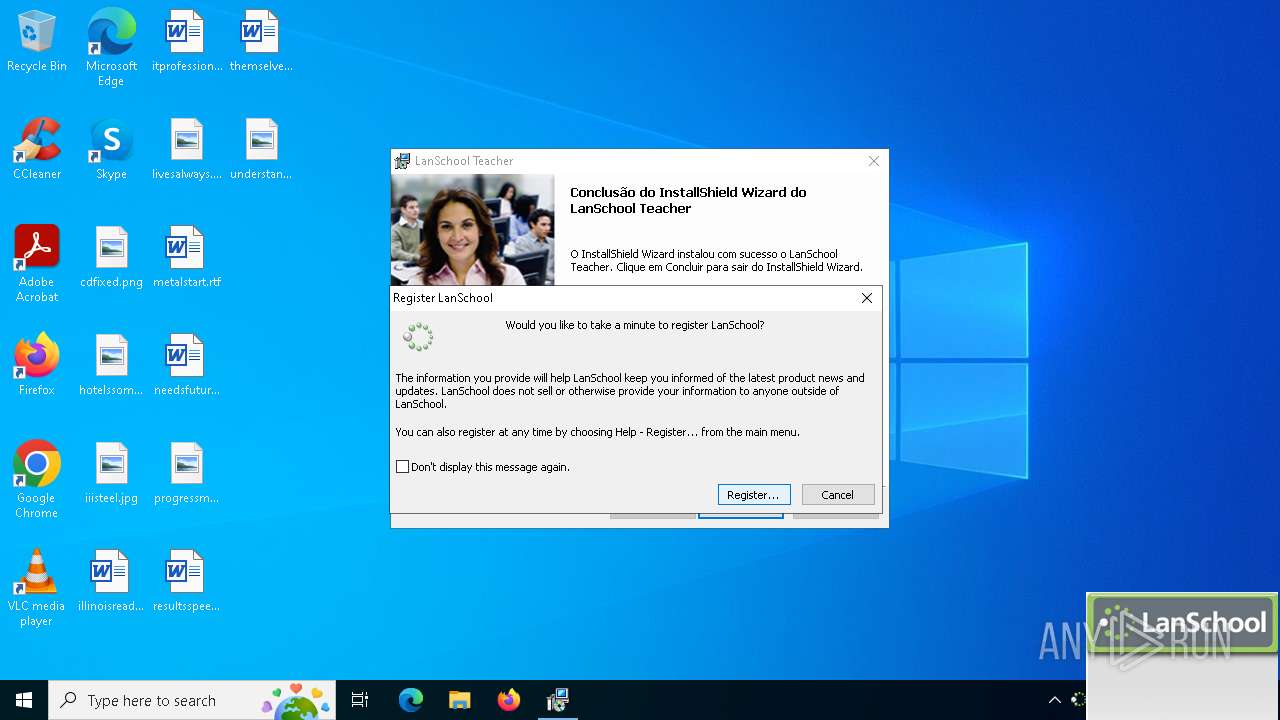
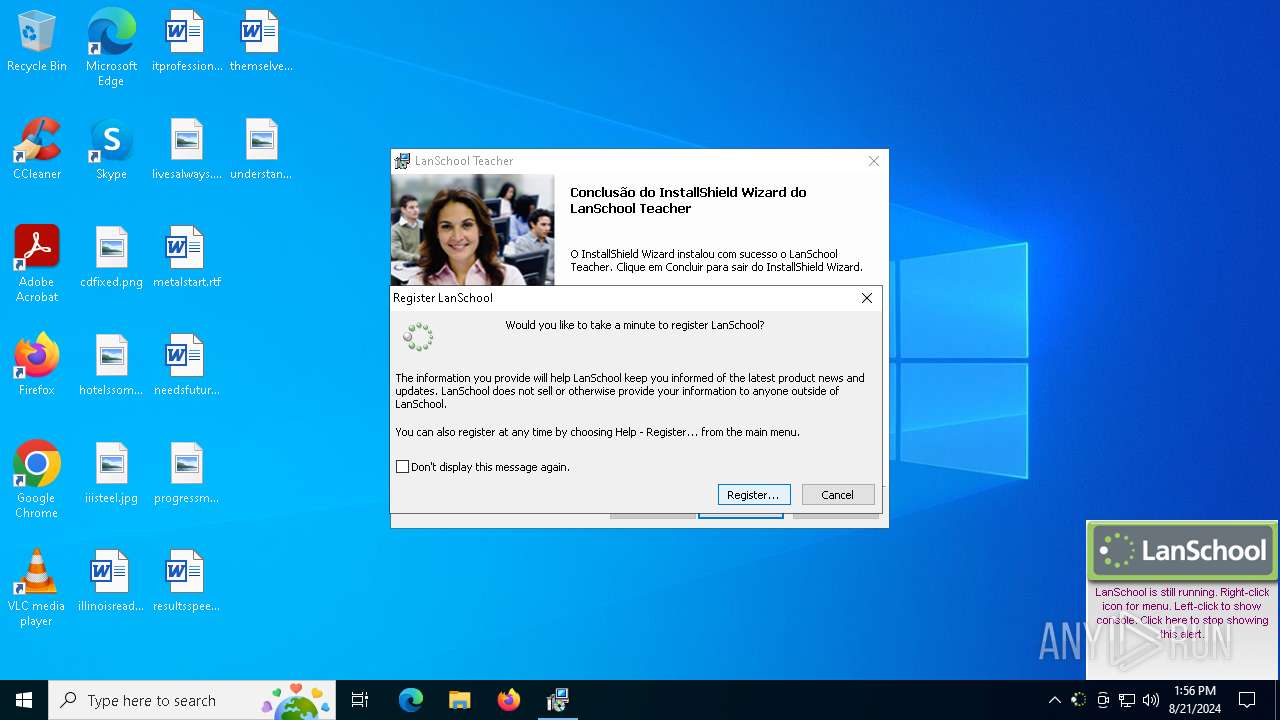
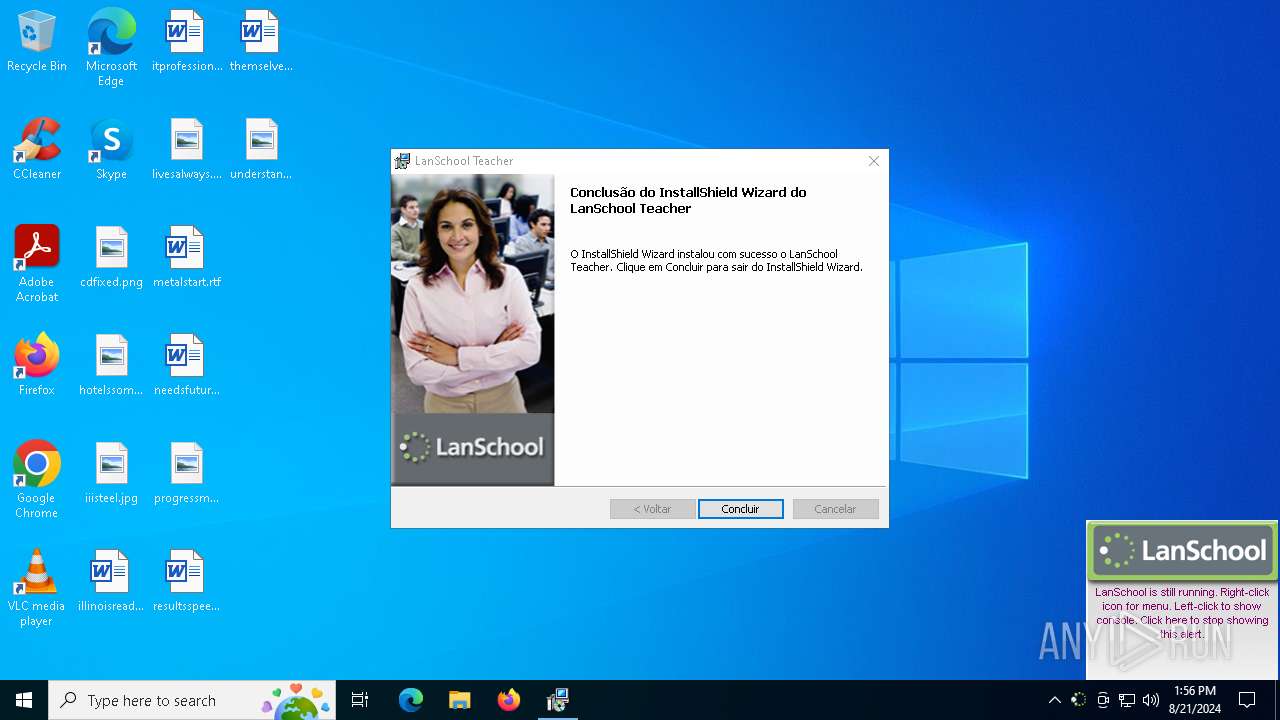
| File name: | Teacher.msi |
| Full analysis: | https://app.any.run/tasks/99652e12-c0a5-41ce-a34e-64191c608d11 |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2024, 13:55:32 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Number of Characters: 0, Last Saved By: InstallShield, Number of Words: 0, Title: Professor LanSchool, Comments: , Keywords: Installer,MSI,Database, Subject: Instalao de Professor LanSchool, Author: , Security: 1, Number of Pages: 200, Name of Creating Application: InstallShield 2014 - Professional Edition 21, Last Saved Time/Date: Wed Dec 14 18:11:09 2016, Create Time/Date: Wed Dec 14 18:11:09 2016, Last Printed: Wed Dec 14 18:11:09 2016, Revision Number: {F4105941-4843-40AD-8A86-79498825FFA9}, Code page: 1252, Template: Intel;1046 |
| MD5: | 10779569C96588555ACE415618DAFDD3 |
| SHA1: | DC236079FF9A7754E756C271D2B50735EFF8E143 |
| SHA256: | D287474C259FB16B0D66F7B5E5D15324732244FFC69F2E2CB525957D5786B45C |
| SSDEEP: | 98304:WB+ad1gvK4NRgJr5FBgwRQTDCUEbnB1e4zXGjKzgRJOHvP3unWf8IMz/+TPfWxrf:5eHvHfod8AX1mppp |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 6912)
SUSPICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 6976)
- msiexec.exe (PID: 6912)
Executes as Windows Service
- VSSVC.exe (PID: 7064)
- LskHelper.exe (PID: 6280)
Process drops legitimate windows executable
- msiexec.exe (PID: 6912)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6912)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3180)
- teacher.exe (PID: 6340)
Reads the date of Windows installation
- msiexec.exe (PID: 3180)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 6912)
Checks Windows Trust Settings
- msiexec.exe (PID: 6912)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- msiexec.exe (PID: 3180)
Uses NETSH.EXE to add a firewall rule or allowed programs
- msiexec.exe (PID: 3180)
INFO
Creates files or folders in the user directory
- msiexec.exe (PID: 6768)
Checks supported languages
- ISBEW64.exe (PID: 7164)
- msiexec.exe (PID: 6912)
- msiexec.exe (PID: 6976)
- ISBEW64.exe (PID: 7044)
- ISBEW64.exe (PID: 7124)
- ISBEW64.exe (PID: 7084)
- ISBEW64.exe (PID: 4280)
- ISBEW64.exe (PID: 6576)
- ISBEW64.exe (PID: 5248)
- ISBEW64.exe (PID: 6196)
- ISBEW64.exe (PID: 6260)
- ISBEW64.exe (PID: 368)
- LskHelper.exe (PID: 6280)
- msiexec.exe (PID: 1060)
- msiexec.exe (PID: 3180)
- teacher.exe (PID: 6340)
- lskHlpr64.exe (PID: 6560)
Reads the computer name
- msiexec.exe (PID: 6976)
- msiexec.exe (PID: 6912)
- ISBEW64.exe (PID: 7044)
- ISBEW64.exe (PID: 7084)
- ISBEW64.exe (PID: 7124)
- ISBEW64.exe (PID: 7164)
- ISBEW64.exe (PID: 5248)
- ISBEW64.exe (PID: 4280)
- ISBEW64.exe (PID: 368)
- ISBEW64.exe (PID: 6196)
- ISBEW64.exe (PID: 6260)
- ISBEW64.exe (PID: 6576)
- msiexec.exe (PID: 3180)
- LskHelper.exe (PID: 6280)
- msiexec.exe (PID: 1060)
- teacher.exe (PID: 6340)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6976)
- msiexec.exe (PID: 6768)
- msiexec.exe (PID: 6912)
An automatically generated document
- msiexec.exe (PID: 6768)
Create files in a temporary directory
- msiexec.exe (PID: 6976)
- msiexec.exe (PID: 1060)
Reads the software policy settings
- msiexec.exe (PID: 6768)
- msiexec.exe (PID: 6912)
Checks proxy server information
- msiexec.exe (PID: 6768)
- teacher.exe (PID: 6340)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6768)
Reads the machine GUID from the registry
- msiexec.exe (PID: 6912)
Creates a software uninstall entry
- msiexec.exe (PID: 6912)
Process checks computer location settings
- msiexec.exe (PID: 3180)
Reads Microsoft Office registry keys
- teacher.exe (PID: 6340)
- msedge.exe (PID: 4976)
Disables trace logs
- teacher.exe (PID: 6340)
Application launched itself
- msedge.exe (PID: 4976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (84.2) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.5) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Characters: | - |
|---|---|
| LastModifiedBy: | InstallShield |
| Words: | - |
| Title: | Professor LanSchool |
| Comments: | |
| Keywords: | Installer,MSI,Database |
| Subject: | Instala??o de Professor LanSchool |
| Author: | |
| Security: | Password protected |
| Pages: | 200 |
| Software: | InstallShield? 2014 - Professional Edition 21 |
| ModifyDate: | 2016:12:14 18:11:09 |
| CreateDate: | 2016:12:14 18:11:09 |
| LastPrinted: | 2016:12:14 18:11:09 |
| RevisionNumber: | {F4105941-4843-40AD-8A86-79498825FFA9} |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | Intel;1046 |
Total processes
184
Monitored processes
50
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Windows\syswow64\NETSH.EXE" advfirewall firewall delete rule name="LanSchool Teacher" | C:\Windows\SysWOW64\netsh.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | C:\Users\admin\AppData\Local\Temp\{80EED6C1-529F-4A51-AFE7-66B57D0B8310}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{7AADF77A-76D1-4977-BAA9-DD718E74009A} | C:\Users\admin\AppData\Local\Temp\{80EED6C1-529F-4A51-AFE7-66B57D0B8310}\ISBEW64.exe | — | msiexec.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 448 | "C:\Windows\syswow64\NETSH.EXE" advfirewall firewall add rule name="LanSchool Teacher" dir=in program="C:\Program Files (x86)\LanSchool\Teacher.exe" action=allow | C:\Windows\SysWOW64\netsh.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | C:\Windows\syswow64\MsiExec.exe -Embedding BFE9352CF908D1FB6ED4ABA78118CF58 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4036 --field-trial-handle=2336,i,3730417162520016497,17406100787066518423,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 2024 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2540 --field-trial-handle=2336,i,3730417162520016497,17406100787066518423,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3180 | C:\Windows\syswow64\MsiExec.exe -Embedding 8FE97BDD41E89BEE574DE4D57F6CCB3F E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=4240 --field-trial-handle=2336,i,3730417162520016497,17406100787066518423,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 3292 | "C:\Windows\syswow64\NETSH.EXE" advfirewall firewall add rule name="LanSchool Student" dir=in program="C:\Program Files (x86)\LanSchool\Student.exe" action=allow | C:\Windows\SysWOW64\netsh.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
22 493
Read events
21 996
Write events
473
Delete events
24
Modification events
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000FEB0C1D8D1F3DA01001B00009C1B0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000FEB0C1D8D1F3DA01001B00009C1B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000006CA5FFD8D1F3DA01001B00009C1B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000006CA5FFD8D1F3DA01001B00009C1B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000030902D9D1F3DA01001B00009C1B0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000006E04D9D1F3DA01001B00009C1B0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000EAAF8ED9D1F3DA01001B00009C1B0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6912) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000F01291D9D1F3DA01001B0000A0190000E80300000100000000000000000000001C8F99F2277A744BAD2893142C467FB200000000000000000000000000000000 | |||
| (PID) Process: | (7064) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000BCBFA1D9D1F3DA01981B0000B81B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
63
Suspicious files
60
Text files
34
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6768 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_BC00434159DAE8351451CCE9C748F5D7 | der | |
MD5:12C28927E0DE052BFADF7420CF437EBE | SHA256:05E22143973F441722148BAB18C9F54CBFC3A5FA474B55D5770E129B70410739 | |||
| 6912 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6912 | msiexec.exe | C:\Windows\Installer\12500c.msi | — | |
MD5:— | SHA256:— | |||
| 6768 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5457A8CE4B2A7499F8299A013B6E1C7C_CE50F893881D43DC0C815E4D80FAF2B4 | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 6768 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIE4B2.tmp | executable | |
MD5:0E4C58D0D2B3B19FAC142615839E1B9A | SHA256:0AC8FB07A5013B0C149C8A76510E8B0E5999EC0C46EA226061B96A8108783357 | |||
| 6976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{80EED6C1-529F-4A51-AFE7-66B57D0B8310}\_isres_0x0416.dll | executable | |
MD5:8D88BF0185BEFC9436BEF349276F8418 | SHA256:79CEDA4CD6D483BBFACC6124EEE57A72932C790536D1C370A6B414F2FD77DA5C | |||
| 6768 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_BC00434159DAE8351451CCE9C748F5D7 | binary | |
MD5:03BF975960E91948ADD83BE12799CA9D | SHA256:6528C2DECB3867C8E23404AD59BB71B2062BFAB0355B161A627A98CF73AA7B84 | |||
| 6976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{80EED6C1-529F-4A51-AFE7-66B57D0B8310}\setup.inx | binary | |
MD5:87F25DD760BE72C87D00D2B0812FF202 | SHA256:CE5B96F5EC0B0BE7AA64730E9074E6ACE496A4C2CE3BAB1FD6E370120E18E21B | |||
| 6976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{80EED6C1-529F-4A51-AFE7-66B57D0B8310}\ISBEW64.exe | executable | |
MD5:663BA0B4E639B2834C4CDBB3CA7944A2 | SHA256:79282DB091F3AE212B7F253C06C502C06893D1539423B2213E1D2E561D167A0D | |||
| 6976 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{80EED6C1-529F-4A51-AFE7-66B57D0B8310}\IsConfig.ini | ini | |
MD5:92F13291083D4860130830E204121B19 | SHA256:5019EFE2C7455CE26D27A1851C80273A3D048DF99F181EA07227A2C0C41A9039 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
45
DNS requests
38
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6768 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | — | — | whitelisted |
6768 | msiexec.exe | GET | 404 | 172.64.149.23:80 | http://crl.usertrust.com/AddTrustExternalCARoot.crl | unknown | — | — | whitelisted |
6768 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | — | — | whitelisted |
6768 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEC58h8wOk0pS%2FpT9HLfNNK8%3D | unknown | — | — | whitelisted |
6768 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSSdxXdG447ymkRNPVViULv3rkBzQQUKZFg%2F4pN%2Buv5pmq4z%2FnmS71JzhICEQCkusQnzXQyyHiOtzNWAbkI | unknown | — | — | whitelisted |
4132 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6912 | msiexec.exe | GET | 404 | 172.64.149.23:80 | http://crl.usertrust.com/AddTrustExternalCARoot.crl | unknown | — | — | whitelisted |
6912 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | — | — | whitelisted |
6912 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | — | — | whitelisted |
6364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
608 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1492 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6768 | msiexec.exe | 104.18.38.233:80 | ocsp.usertrust.com | CLOUDFLARENET | — | shared |
6768 | msiexec.exe | 172.64.149.23:80 | ocsp.usertrust.com | CLOUDFLARENET | US | unknown |
1492 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4132 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4132 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
crl.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
lskHlpr64.exe | At the start of LskHlpr64.exe
|