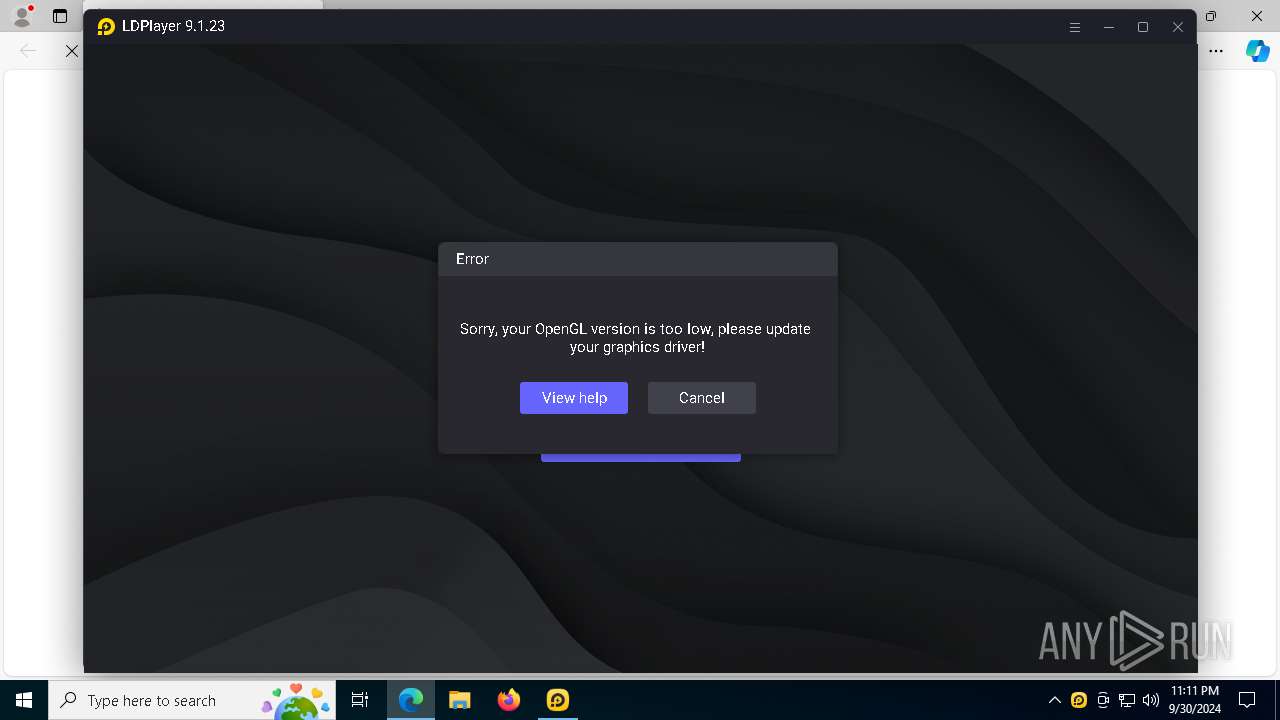
| File name: | LDPlayer9_ens_1001_ld.exe |
| Full analysis: | https://app.any.run/tasks/415244de-a54a-4d50-8fd9-27c7af9b9d13 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2024, 23:06:57 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | A64BD549D95BFC8BE592833460F79FCC |
| SHA1: | 0AEEB9507ED39F14D82149C56011EC3AAED1BEC9 |
| SHA256: | D285B5242F4583D49C63A7C7F83A72F082AB395F9EAFF674FF56C8D2D0FA063D |
| SSDEEP: | 98304:X8FjyxBkMZyzOLENk9zbz5VEmy2slI2Vrr9EhZShEBBRRL+rssQarhYfLrt2CPSM: |
MALICIOUS
Starts NET.EXE for service management
- dnrepairer.exe (PID: 2868)
- net.exe (PID: 6852)
Registers / Runs the DLL via REGSVR32.EXE
- dnrepairer.exe (PID: 2868)
SUSPICIOUS
Reads security settings of Internet Explorer
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Executable content was dropped or overwritten
- LDPlayer.exe (PID: 6680)
- dnrepairer.exe (PID: 2868)
- Dism.exe (PID: 1568)
- dnplayer.exe (PID: 2616)
Checks Windows Trust Settings
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Drops 7-zip archiver for unpacking
- LDPlayer.exe (PID: 6680)
The process drops C-runtime libraries
- LDPlayer.exe (PID: 6680)
- dnrepairer.exe (PID: 2868)
- dnplayer.exe (PID: 2616)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 2636)
Drops a system driver (possible attempt to evade defenses)
- dnrepairer.exe (PID: 2868)
Process drops legitimate windows executable
- dnrepairer.exe (PID: 2868)
- dnplayer.exe (PID: 2616)
- Dism.exe (PID: 1568)
- LDPlayer.exe (PID: 6680)
Starts POWERSHELL.EXE for commands execution
- dnrepairer.exe (PID: 2868)
Takes ownership (TAKEOWN.EXE)
- LDPlayer.exe (PID: 6680)
- dnrepairer.exe (PID: 2868)
Uses ICACLS.EXE to modify access control lists
- LDPlayer.exe (PID: 6680)
- dnrepairer.exe (PID: 2868)
INFO
Checks supported languages
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Creates files or folders in the user directory
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Reads the computer name
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Reads the software policy settings
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Reads the machine GUID from the registry
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Checks proxy server information
- LDPlayer9_ens_1001_ld.exe (PID: 6244)
Application launched itself
- msedge.exe (PID: 652)
- msedge.exe (PID: 5436)
Manual execution by a user
- msedge.exe (PID: 652)
- dnplayer.exe (PID: 7992)
Attempting to use instant messaging service
- msedge.exe (PID: 6832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:08:27 09:25:08+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 1215488 |
| InitializedDataSize: | 1440256 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xec8bc |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
258
Monitored processes
115
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "regsvr32" Wintrust.dll /s | C:\Windows\SysWOW64\regsvr32.exe | — | dnrepairer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | "regsvr32" dssenh.dll /s | C:\Windows\SysWOW64\regsvr32.exe | — | dnrepairer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 420 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | takeown.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 652 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate --single-argument https://discord.gg/4bUcwDd53d | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 992 | C:\WINDOWS\system32\net1 start cryptsvc | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | "C:\LDPlayer\LDPlayer9\driverconfig.exe" | C:\LDPlayer\LDPlayer9\driverconfig.exe | — | LDPlayer.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1168 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=video_capture.mojom.VideoCaptureService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3716 --field-trial-handle=2236,i,2447816446712689224,6414644317574273726,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1172 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=audio.mojom.AudioService --lang=en-US --service-sandbox-type=audio --no-appcompat-clear --mojo-platform-channel-handle=5272 --field-trial-handle=2236,i,2447816446712689224,6414644317574273726,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
68 992
Read events
68 491
Write events
472
Delete events
29
Modification events
| (PID) Process: | (6244) LDPlayer9_ens_1001_ld.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lden |
| Operation: | write | Name: | pcmac |
Value: 5f91dca989018bdb17e77e4384076fba | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Usages\1.3.6.1.5.5.7.3.3 |
| Operation: | write | Name: | DefaultId |
Value: {00AAC56B-CD44-11D0-8CC2-00C04FC295EE} | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\FinalPolicy\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\FinalPolicy\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE} |
| Operation: | write | Name: | $Function |
Value: SoftpubAuthenticode | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Initialization\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Initialization\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $Function |
Value: SoftpubInitialize | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Message\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Message\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $Function |
Value: SoftpubLoadMessage | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Signature\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2064) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Signature\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $Function |
Value: SoftpubLoadSignature | |||
Executable files
476
Suspicious files
132
Text files
163
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6244 | LDPlayer9_ens_1001_ld.exe | C:\LDPlayer\LDPlayer9\LDPlayer.exe.tmp | — | |
MD5:— | SHA256:— | |||
| 6244 | LDPlayer9_ens_1001_ld.exe | C:\LDPlayer\LDPlayer9\LDPlayer.exe | — | |
MD5:— | SHA256:— | |||
| 6680 | LDPlayer.exe | C:\Users\admin\AppData\Roaming\XuanZhi\fonts\NotoSans-Regular.otf | — | |
MD5:— | SHA256:— | |||
| 6680 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\data-3G.vmdk | — | |
MD5:— | SHA256:— | |||
| 6680 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\data.vmdk | — | |
MD5:— | SHA256:— | |||
| 6680 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\dnresource.rcc | — | |
MD5:— | SHA256:— | |||
| 6244 | LDPlayer9_ens_1001_ld.exe | C:\Users\admin\AppData\Roaming\lddownloader_en\fonts\NanumGothicLight.otf | binary | |
MD5:E2E37D20B47D7EE294B91572F69E323A | SHA256:153161AB882DB768C70A753AF5E8129852B9C9CAE5511A23653BEB6414D834A2 | |||
| 6680 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\appName.text | text | |
MD5:B88F5E1E8443F65538D157DB8E3FFBA3 | SHA256:E69EAB737FCA991062800CB339B6D3900B21AAD13C8B4C5614DCB068DBDFBD40 | |||
| 6680 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\launcherskin\blue_h.jpg | image | |
MD5:CF4A84BC58624F977868220E0A765ABF | SHA256:47F3090ECCFA65625DC64EB6E1592861555D9BF7B9433D723C4DEA2EF2E9CF72 | |||
| 6244 | LDPlayer9_ens_1001_ld.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | der | |
MD5:4AED9A1CF042CB8A23BB64FEC46AFB68 | SHA256:750F6AC90E0819E19945BEE3CEBD78BF9593A17659F4D269869828F4C4A4A857 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
127
DNS requests
75
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6244 | LDPlayer9_ens_1001_ld.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
2120 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6244 | LDPlayer9_ens_1001_ld.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEH6Hwxq9kZ5xalNEESzfRqk%3D | unknown | — | — | whitelisted |
3852 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5116 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4196 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4196 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2616 | dnplayer.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ5rEWLwbJFq%2FmAU80sm7E%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2616 | dnplayer.exe | GET | 200 | 142.250.74.195:80 | http://c.pki.goog/r/r1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3928 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6244 | LDPlayer9_ens_1001_ld.exe | 163.181.92.229:443 | res.ldrescdn.com | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
6244 | LDPlayer9_ens_1001_ld.exe | 104.18.20.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | whitelisted |
6244 | LDPlayer9_ens_1001_ld.exe | 142.250.186.78:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
6244 | LDPlayer9_ens_1001_ld.exe | 52.222.214.107:443 | apien.ldmnq.com | AMAZON-02 | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
res.ldrescdn.com |
| unknown |
ocsp2.globalsign.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
apien.ldmnq.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6832 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
Process | Message |
|---|---|
Dism.exe | PID=1568 TID=3476 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=1568 TID=3476 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=1568 TID=3476 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=1568 TID=3476 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=1568 TID=3476 Loading Provider from location C:\WINDOWS\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=1568 TID=3476 Connecting to the provider located at C:\WINDOWS\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=2636 TID=6028 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=2636 TID=6028 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=2636 TID=6028 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=1568 TID=3476 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |