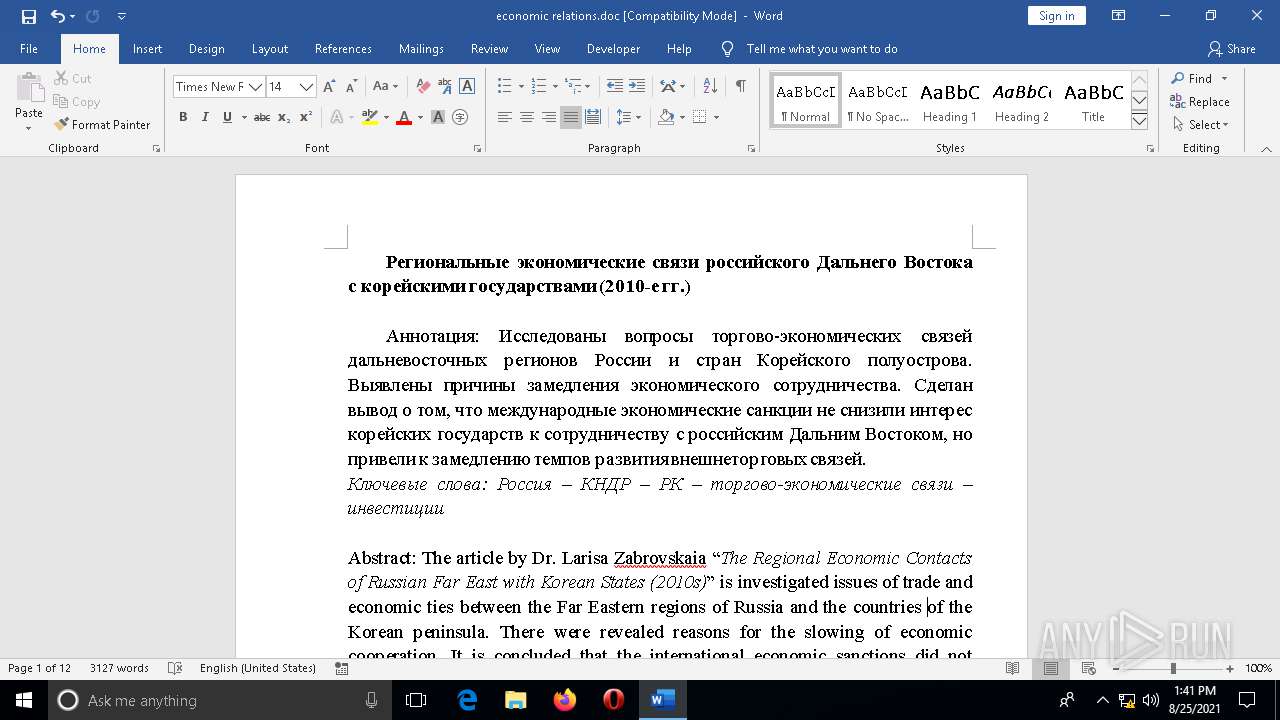
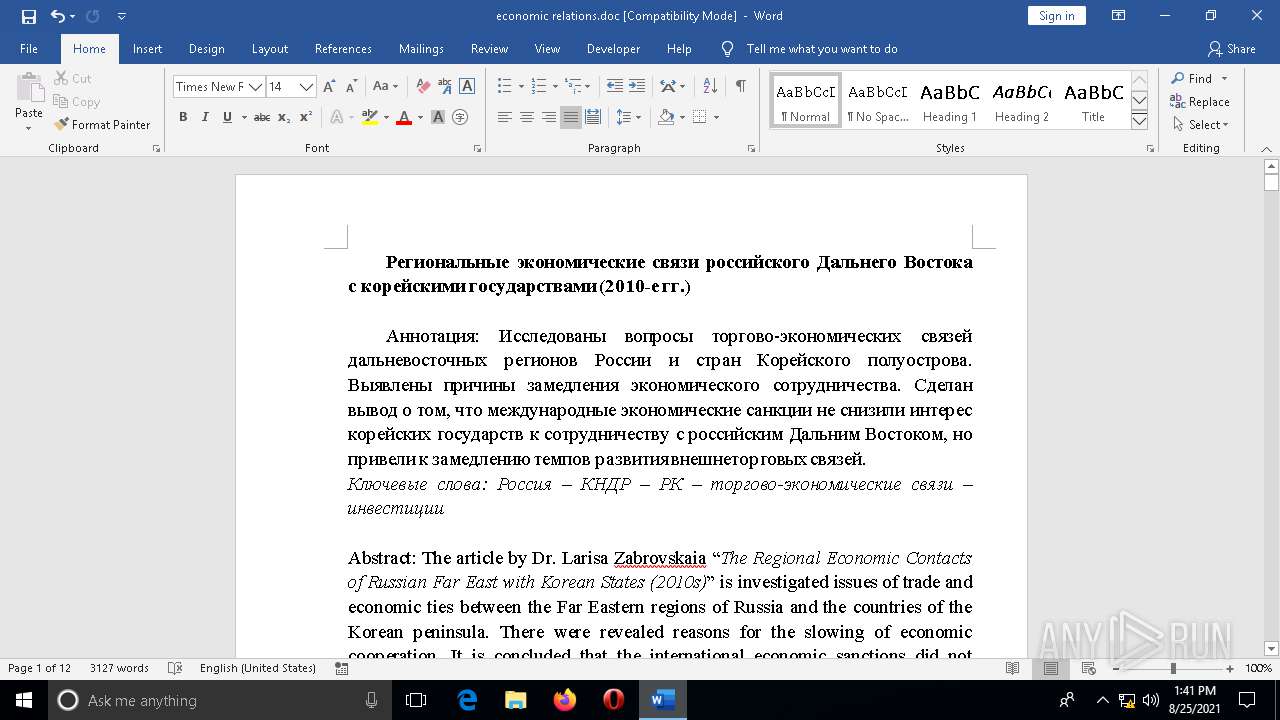
| File name: | economic relations.doc |
| Full analysis: | https://app.any.run/tasks/1be25f29-b658-4f49-993f-ba8dd2f31a5f |
| Verdict: | Malicious activity |
| Analysis date: | August 25, 2021, 13:40:29 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 949, Author: User, Template: Normal.dotm, Last Saved By: User, Revision Number: 6, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Wed Jul 28 01:32:00 2021, Last Saved Time/Date: Wed Jul 28 01:33:00 2021, Number of Pages: 12, Number of Words: 3742, Number of Characters: 21335, Security: 0 |
| MD5: | 9B1CA0408E33C43970B87C4C380B134F |
| SHA1: | 2FADFAEF5179FE69BFECBD9ADEBD8F6A50615FA4 |
| SHA256: | D283A0D5CFED4D212CD76497920CF820472C5F138FD061F25E3CDDF65190283F |
| SSDEEP: | 768:lhfdrQHFZPSu14mEJc1icjEocMBf0Nxi/qNafupsP0ZzB5:45Aoc2uxwq/v5 |
MALICIOUS
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 1864)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 1864)
Drops executable file immediately after starts
- csc.exe (PID: 1480)
Scans artifacts that could help determine the target
- powershell.exe (PID: 724)
SUSPICIOUS
Reads the date of Windows installation
- WINWORD.EXE (PID: 1864)
Reads default file associations for system extensions
- WINWORD.EXE (PID: 1864)
Checks supported languages
- conhost.exe (PID: 4376)
- cmd.exe (PID: 3536)
- cmd.exe (PID: 1324)
- conhost.exe (PID: 4416)
- cmd.exe (PID: 3484)
- cmd.exe (PID: 1828)
- conhost.exe (PID: 1328)
- wscript.exe (PID: 1400)
- wscript.exe (PID: 4584)
- conhost.exe (PID: 3636)
- powershell.exe (PID: 724)
- csc.exe (PID: 1480)
- cvtres.exe (PID: 2792)
- cmd.exe (PID: 4736)
- expand.exe (PID: 4284)
- cmd.exe (PID: 4748)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 1400)
- cmd.exe (PID: 3536)
- powershell.exe (PID: 724)
Application launched itself
- wscript.exe (PID: 1400)
- cmd.exe (PID: 3536)
Executes scripts
- wscript.exe (PID: 1400)
- cmd.exe (PID: 3536)
Reads the computer name
- wscript.exe (PID: 1400)
- powershell.exe (PID: 724)
- wscript.exe (PID: 4584)
Executes PowerShell scripts
- wscript.exe (PID: 1400)
Executable content was dropped or overwritten
- csc.exe (PID: 1480)
Drops a file with a compile date too recent
- csc.exe (PID: 1480)
INFO
Reads CPU info
- WINWORD.EXE (PID: 1864)
Reads the computer name
- WINWORD.EXE (PID: 1864)
Checks supported languages
- WINWORD.EXE (PID: 1864)
- findstr.exe (PID: 4964)
- findstr.exe (PID: 1036)
- findstr.exe (PID: 4384)
Reads settings of System Certificates
- WINWORD.EXE (PID: 1864)
- powershell.exe (PID: 724)
Reads Environment values
- WINWORD.EXE (PID: 1864)
Checks Windows Trust Settings
- wscript.exe (PID: 1400)
- wscript.exe (PID: 4584)
- powershell.exe (PID: 724)
- WINWORD.EXE (PID: 1864)
Creates files in the user directory
- WINWORD.EXE (PID: 1864)
Reads the software policy settings
- powershell.exe (PID: 724)
- WINWORD.EXE (PID: 1864)
Scans artifacts that could help determine the target
- WINWORD.EXE (PID: 1864)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| CompObjUserType: | Microsoft Word 97-2003 Document |
|---|---|
| CompObjUserTypeLen: | 32 |
| Hyperlinks: |
|
| CodePage: | Windows Korean (Unified Hangul Code) |
| HeadingPairs: |
|
| TitleOfParts: | - |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 15 |
| CharCountWithSpaces: | 25027 |
| Paragraphs: | 50 |
| Lines: | 177 |
| Company: | - |
| Security: | None |
| Characters: | 21335 |
| Words: | 3742 |
| Pages: | 12 |
| ModifyDate: | 2021:07:28 00:33:00 |
| CreateDate: | 2021:07:28 00:32:00 |
| TotalEditTime: | 1.0 minutes |
| Software: | Microsoft Office Word |
| RevisionNumber: | 6 |
| LastModifiedBy: | User |
| Template: | Normal.dotm |
| Comments: | - |
| Keywords: | - |
| Author: | User |
| Subject: | - |
| Title: | - |
Total processes
107
Monitored processes
20
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 724 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass -f ./y.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1036 | findstr /r "^QWRkL" "C:\Users\admin\Desktop\economic relations.doc" | C:\WINDOWS\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | C:\WINDOWS\system32\cmd.exe /S /D /c" type "C:\Users\admin\Desktop\economic relations.doc" " | C:\WINDOWS\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1400 | wscript y.js "C:\Users\admin\Desktop\economic relations.doc" | C:\WINDOWS\system32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 1480 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\0aj5fjcr.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.7.2556.0 built by: NET471REL1 Modules
| |||||||||||||||
| 1828 | "C:\Windows\System32\cmd.exe" /c findstr /r "^dHJ5I" "C:\Users\admin\Desktop\economic relations.doc" > temp.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1864 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\economic relations.doc" /o "" | C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 16.0.12026.20264 Modules
| |||||||||||||||
| 2792 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES12C4.tmp" "c:\Users\admin\AppData\Local\Temp\CSC8D170A9DAEA048DEA88D3F63F5CC2D85.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft� Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52519.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 3484 | "C:\Windows\System32\cmd.exe" /c findstr /r "^QWRkL" "C:\Users\admin\Desktop\economic relations.doc" > temp.txt | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 064
Read events
9 807
Write events
222
Delete events
35
Modification events
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000284FFA2E04000000000000000500000000000000 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\Common\CrashPersistence\WINWORD\1864 |
| Operation: | write | Name: | 0 |
Value: 0B0E1059B7952B449CCE4EA79ADB720BE26AF623004696998CEBECB6E6EB016A0410240044FA5D64A89E01008500A907556E6B6E6F776E00 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (1864) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
8
Text files
14
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\economic relations.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 1864 | WINWORD.EXE | C:\Users\admin\Desktop\~$onomic relations.doc | pgc | |
MD5:— | SHA256:— | |||
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF4d870b91.TMP | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\C8SAAGY97ZIEKDX65SSZ.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QZ6EUXZTEI14OEIL4AOM.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 1480 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC8D170A9DAEA048DEA88D3F63F5CC2D85.TMP | res | |
MD5:— | SHA256:— | |||
| 1864 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF4d870b52.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 1400 | wscript.exe | C:\Users\admin\y.ps1 | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
7
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1864 | WINWORD.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
724 | powershell.exe | GET | 403 | 185.176.43.106:80 | http://takemetoyouheart.c1.biz/index.php?user_id=319 | BG | html | 110 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
724 | powershell.exe | 185.176.43.106:80 | takemetoyouheart.c1.biz | Zetta Hosting Solutions LLC. | BG | malicious |
1864 | WINWORD.EXE | 13.69.109.130:443 | self.events.data.microsoft.com | Microsoft Corporation | NL | suspicious |
1864 | WINWORD.EXE | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1864 | WINWORD.EXE | 13.107.42.23:443 | config.edge.skype.com | Microsoft Corporation | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| malicious |
self.events.data.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
takemetoyouheart.c1.biz |
| malicious |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |