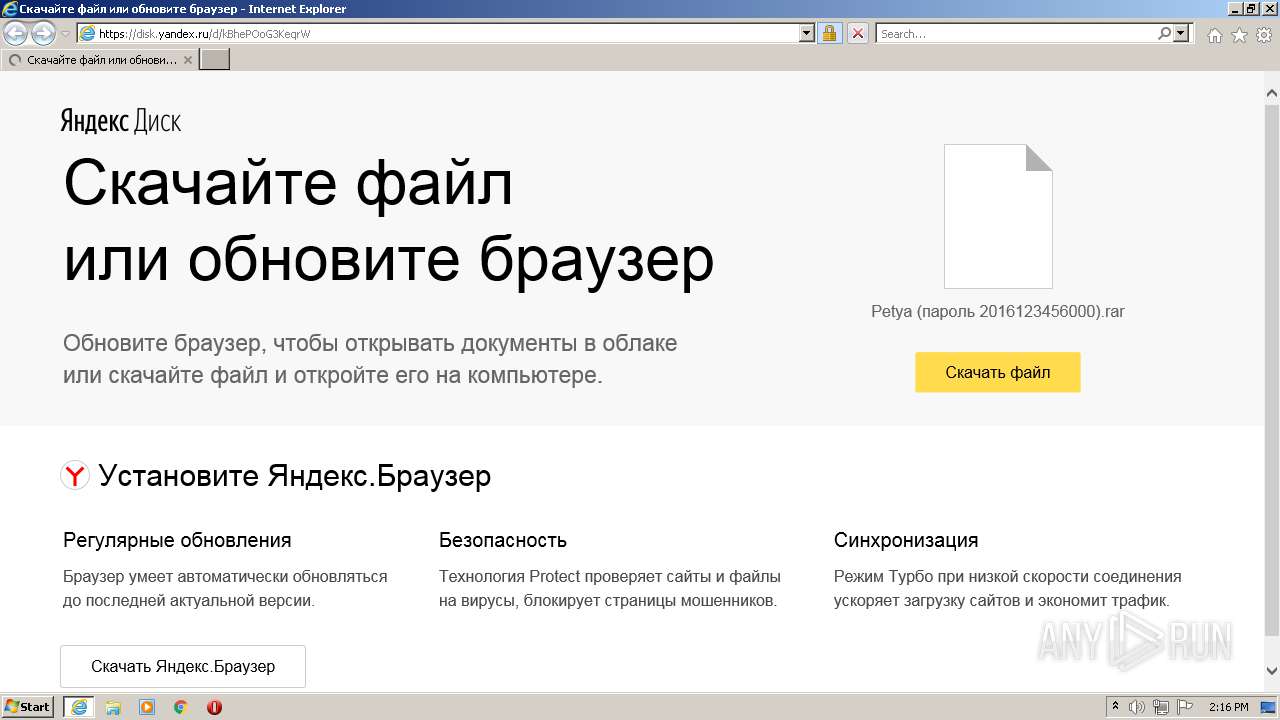
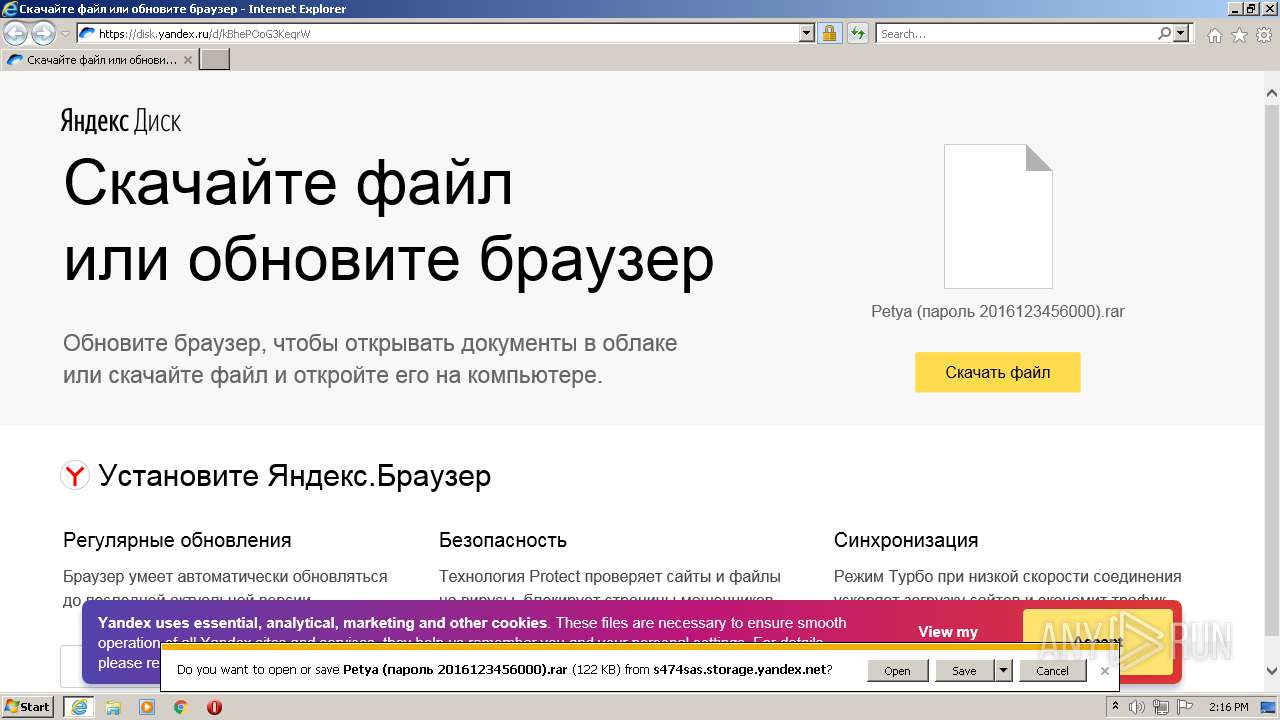
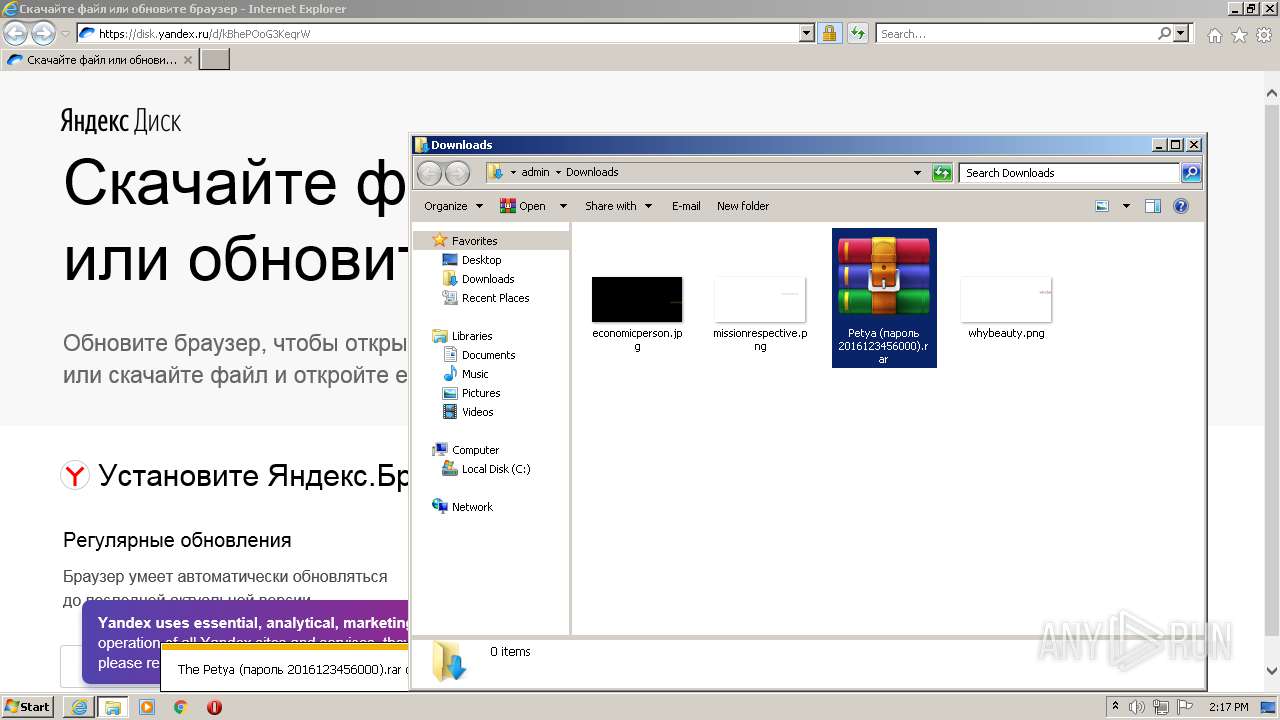
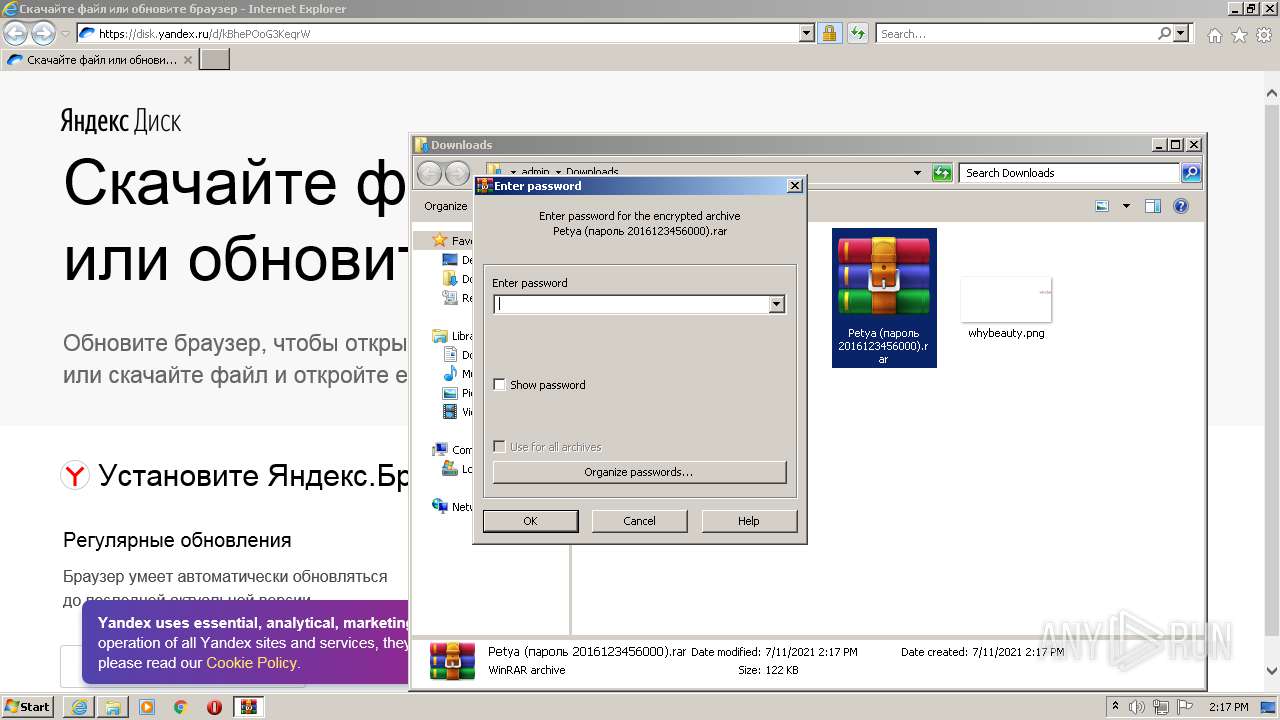
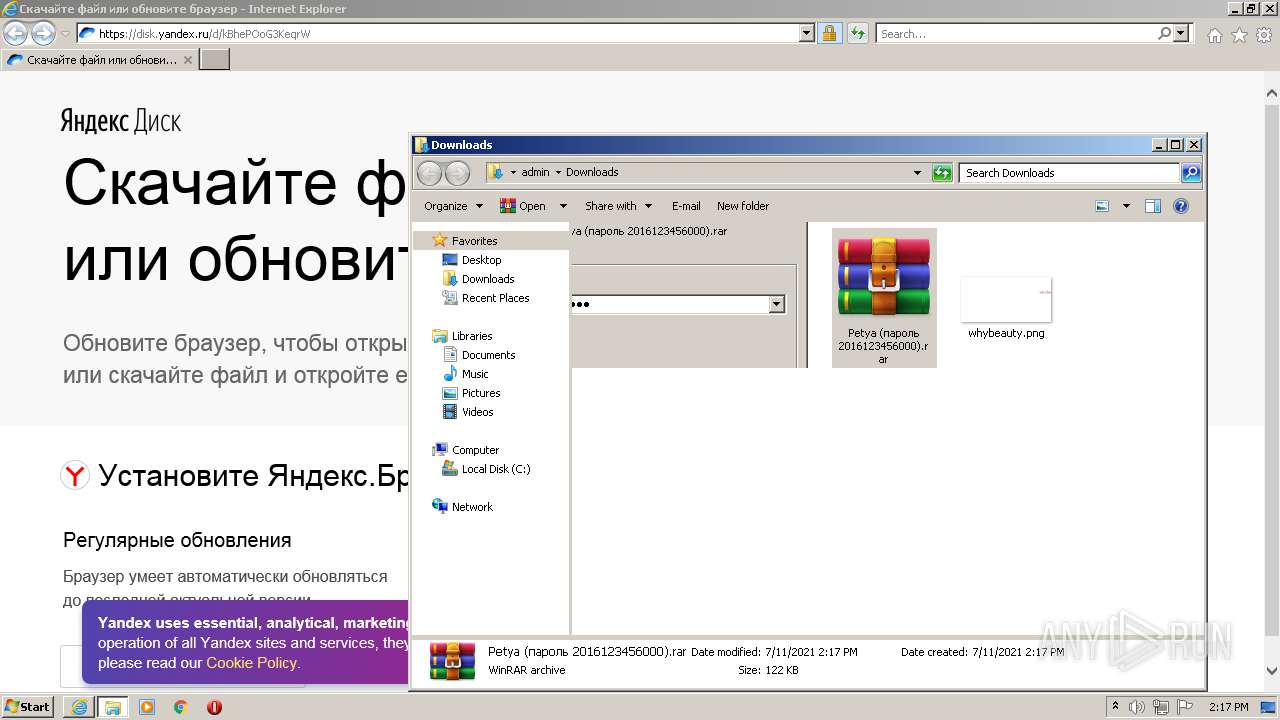
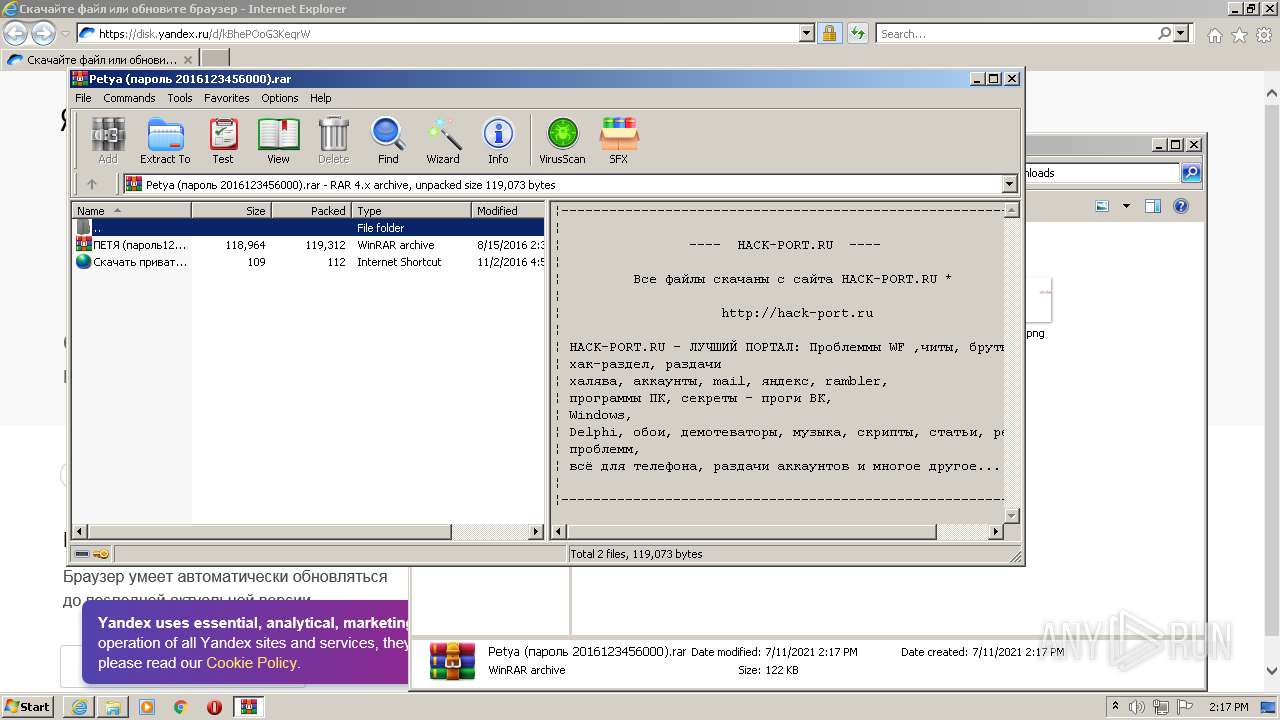
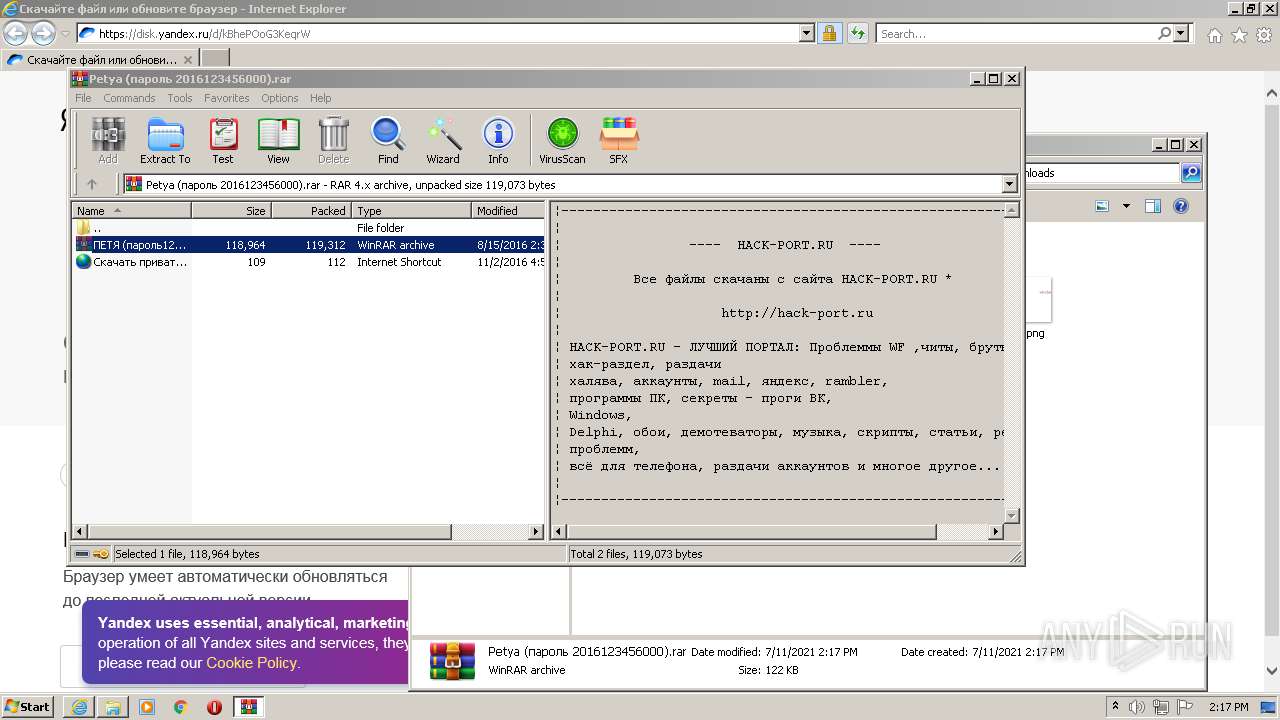
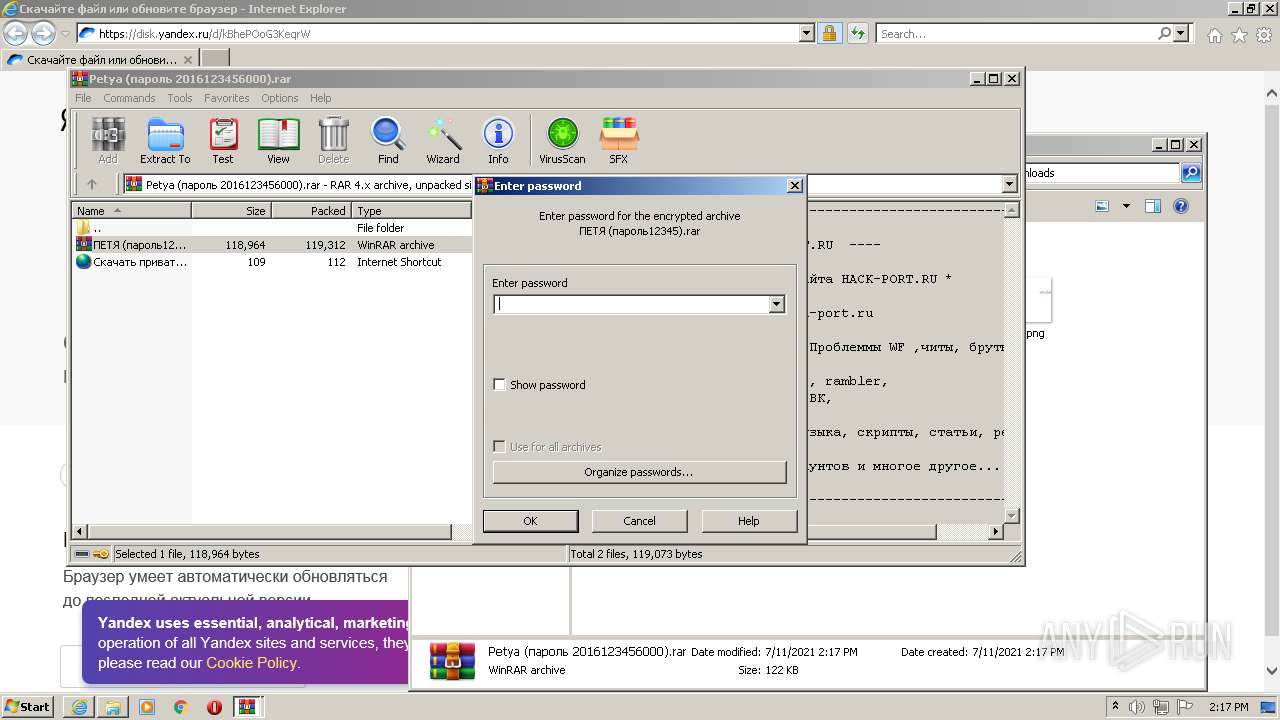
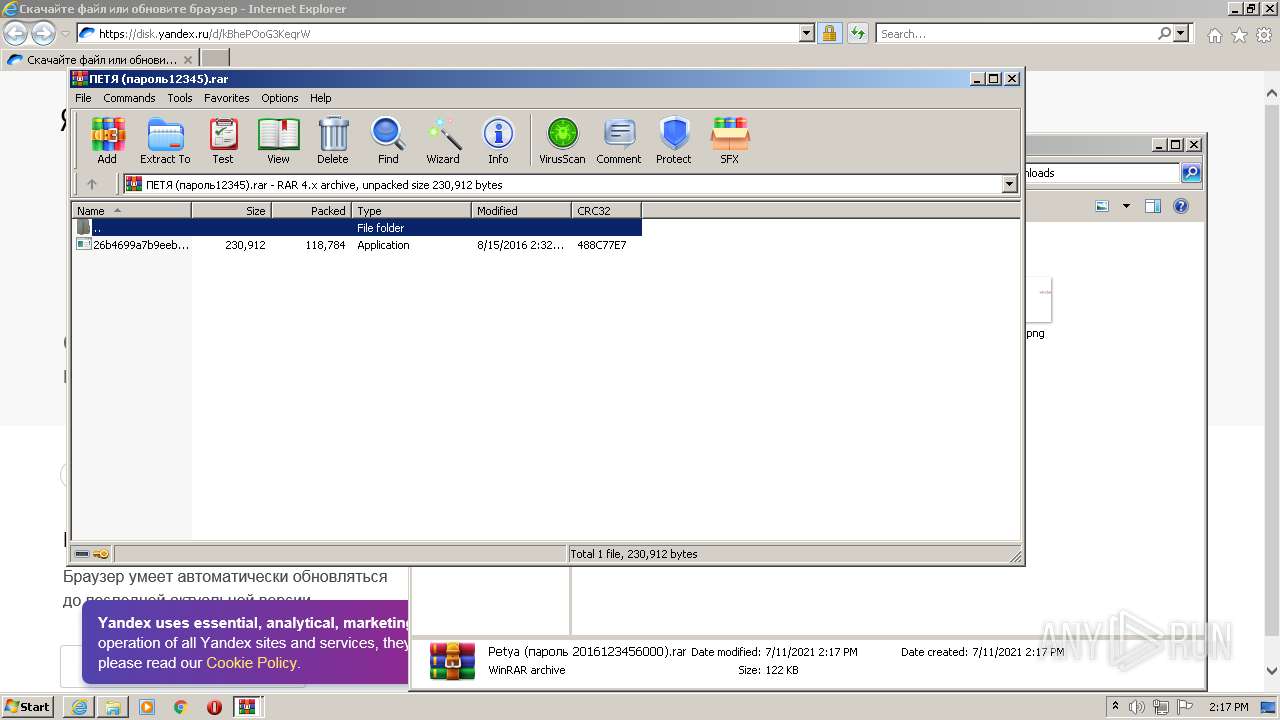
| URL: | https://disk.yandex.ru/d/kBhePOoG3KeqrW |
| Full analysis: | https://app.any.run/tasks/38522ee2-ebac-4c6c-8450-f6a7733ec143 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2021, 13:16:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | FA99C6E493A2E3EF2DD64948ECE88686 |
| SHA1: | 319F7A30511F6166D77C015B3A99C1974C098E6E |
| SHA256: | D27329EEB4CE78B05C3BD9C9CC70F3E464DF3EFF45D7A26EDA84D0163F089A00 |
| SSDEEP: | 3:N8U2fnePUin:2U2fGn |
MALICIOUS
Application was dropped or rewritten from another process
- 26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe (PID: 604)
- 26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe (PID: 3968)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1660)
- iexplore.exe (PID: 1832)
Reads the computer name
- WinRAR.exe (PID: 2396)
- WinRAR.exe (PID: 3540)
- 26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe (PID: 3968)
Checks supported languages
- WinRAR.exe (PID: 2396)
- WinRAR.exe (PID: 3540)
- 26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe (PID: 3968)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3540)
Application launched itself
- WinRAR.exe (PID: 2396)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3540)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1660)
Reads the computer name
- iexplore.exe (PID: 1660)
- iexplore.exe (PID: 1832)
Checks Windows Trust Settings
- iexplore.exe (PID: 1832)
- iexplore.exe (PID: 1660)
Application launched itself
- iexplore.exe (PID: 1660)
Checks supported languages
- iexplore.exe (PID: 1660)
- iexplore.exe (PID: 1832)
Reads settings of System Certificates
- iexplore.exe (PID: 1832)
- iexplore.exe (PID: 1660)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1660)
Creates files in the user directory
- iexplore.exe (PID: 1832)
Reads internet explorer settings
- iexplore.exe (PID: 1832)
Changes settings of System certificates
- iexplore.exe (PID: 1660)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1660)
Manual execution by user
- WinRAR.exe (PID: 2396)
- 26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe (PID: 604)
- 26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe (PID: 3968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 604 | "C:\Users\admin\Desktop\26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe" | C:\Users\admin\Desktop\26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1660 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://disk.yandex.ru/d/kBhePOoG3KeqrW" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1832 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1660 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2396 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\Petya (?????? 2016123456000).rar" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3540 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2396.25659\???? (??????12345).rar" | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3968 | "C:\Users\admin\Desktop\26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe" | C:\Users\admin\Desktop\26b4699a7b9eeb16e76305d843d4ab05e94d43f3201436927e13b3ebafa90739.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
15 679
Read events
15 505
Write events
170
Delete events
4
Modification events
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 12438704 | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30897751 | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 312440657 | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30897751 | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1660) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
18
Text files
16
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | binary | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\68FAF71AF355126BCA00CE2E73CC7374_77B682CF3AAC7B00161DFFF7DEA4CC8C | binary | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\I8OZ9IXI.txt | text | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\68FAF71AF355126BCA00CE2E73CC7374_77B682CF3AAC7B00161DFFF7DEA4CC8C | der | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E887E036775F4159E2816B7B9E527E5F_759E91EA549A31D17CF4D7FE309177F9 | binary | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E887E036775F4159E2816B7B9E527E5F_81A9EAEF491877F5AE96F9A03F4042E4 | der | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E887E036775F4159E2816B7B9E527E5F_759E91EA549A31D17CF4D7FE309177F9 | der | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1F4BA66CDBFEC85A20E11BF729AF23_AA85F8F9DAFF33153B5AEC2E983B94B6 | der | |
MD5:— | SHA256:— | |||
| 1832 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\DOTBATAV\disk.yandex[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
21
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1832 | iexplore.exe | GET | 200 | 2.16.186.232:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | unknown | der | 1.63 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEDbEISBuJVGq0KdX46enAhA%3D | RU | der | 1.48 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEFcAp3OG3HlvO0Q7Ft5KH%2F8%3D | RU | der | 1.48 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEFZmQLn1X2nsT8%2FuNzo5n6w%3D | RU | der | 1.48 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEFIn0TfHy7SBwk%2BiWUR4QnM%3D | RU | der | 1.48 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 5.45.205.244:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEFjVURl8vAlh6dEYrJMUMng%3D | RU | der | 1.48 Kb | whitelisted |
1660 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1832 | iexplore.exe | GET | 200 | 2.16.186.232:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | unknown | der | 1.58 Kb | whitelisted |
1832 | iexplore.exe | GET | 200 | 2.16.186.41:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a431d6cf719e59cf | unknown | compressed | 4.70 Kb | whitelisted |
1660 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1832 | iexplore.exe | 87.250.250.50:443 | disk.yandex.ru | YANDEX LLC | RU | whitelisted |
1832 | iexplore.exe | 2.16.186.41:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
1832 | iexplore.exe | 2.16.186.232:80 | subca.ocsp-certum.com | Akamai International B.V. | — | whitelisted |
1832 | iexplore.exe | 5.45.205.244:80 | yandex.ocsp-responder.com | YANDEX LLC | RU | whitelisted |
1832 | iexplore.exe | 77.88.21.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
— | — | 77.88.21.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
1832 | iexplore.exe | 178.154.131.216:443 | yastatic.net | YANDEX LLC | RU | whitelisted |
1832 | iexplore.exe | 77.88.21.127:443 | downloader.disk.yandex.ru | YANDEX LLC | RU | whitelisted |
1832 | iexplore.exe | 213.180.206.192:443 | s474sas.storage.yandex.net | YANDEX LLC | RU | whitelisted |
1660 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
disk.yandex.ru |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
subca.ocsp-certum.com |
| whitelisted |
yandex.ocsp-responder.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
yastatic.net |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
downloader.disk.yandex.ru |
| shared |
s474sas.storage.yandex.net |
| whitelisted |