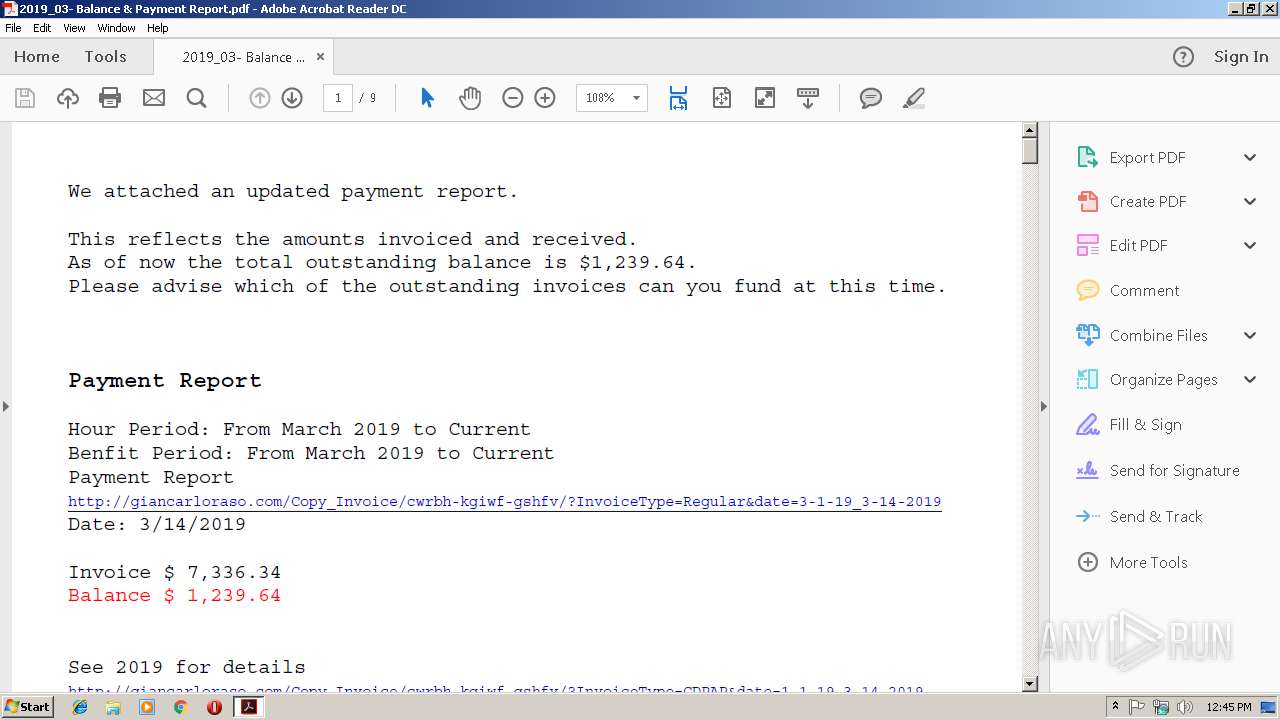
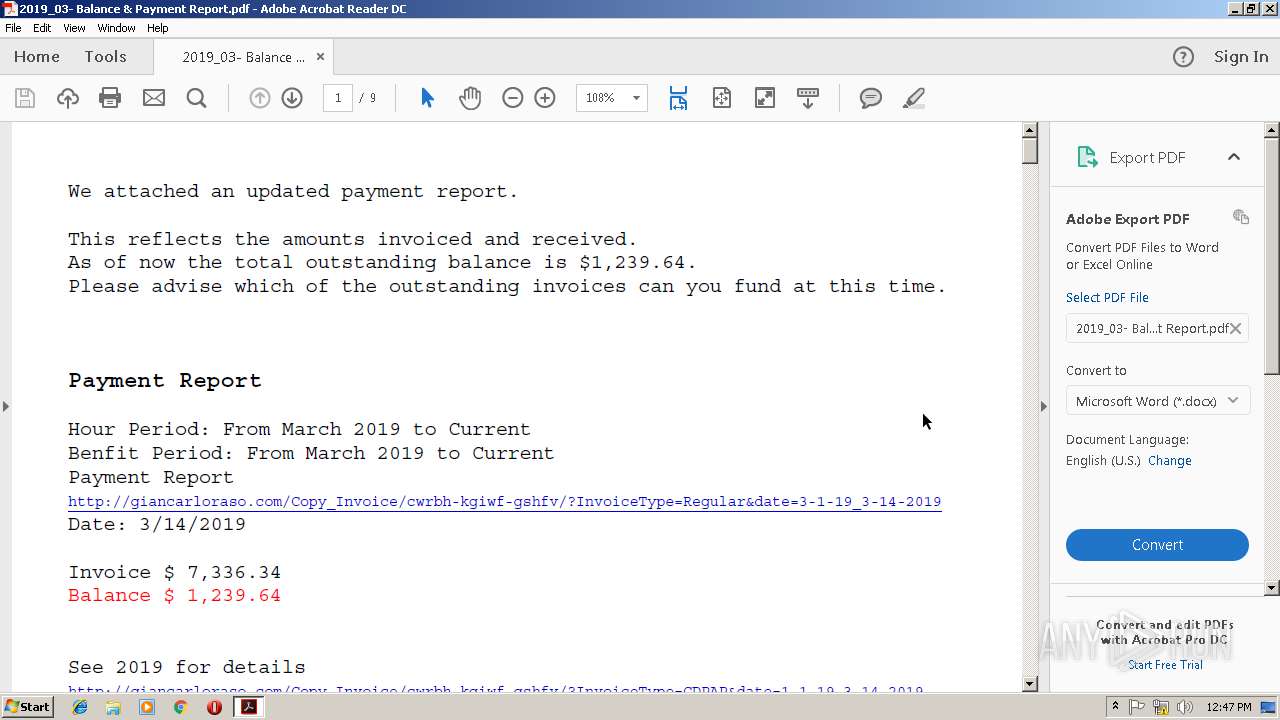
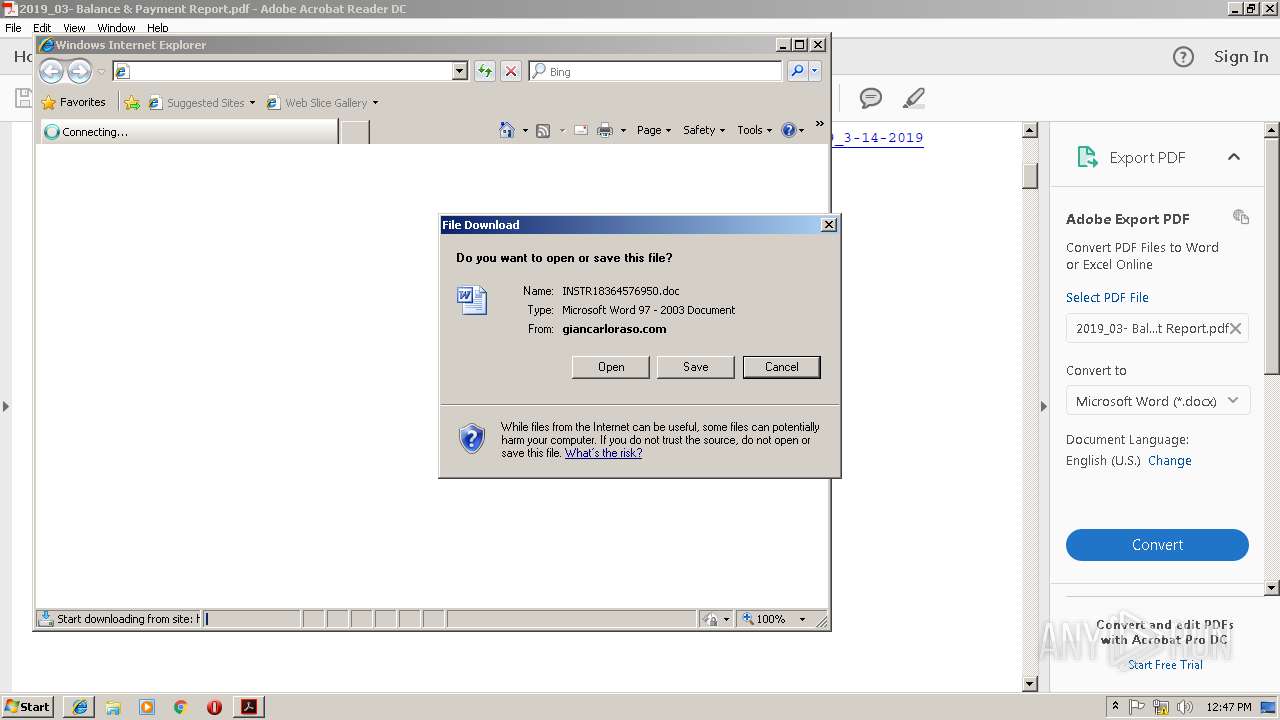
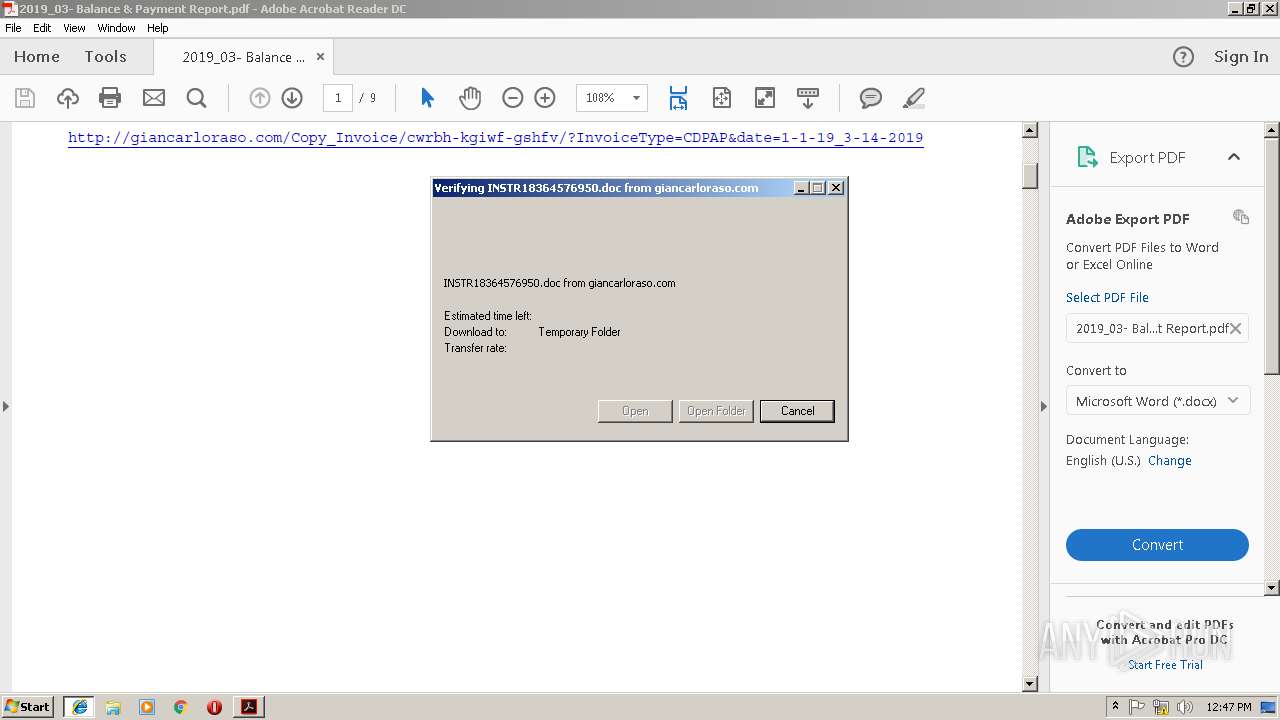
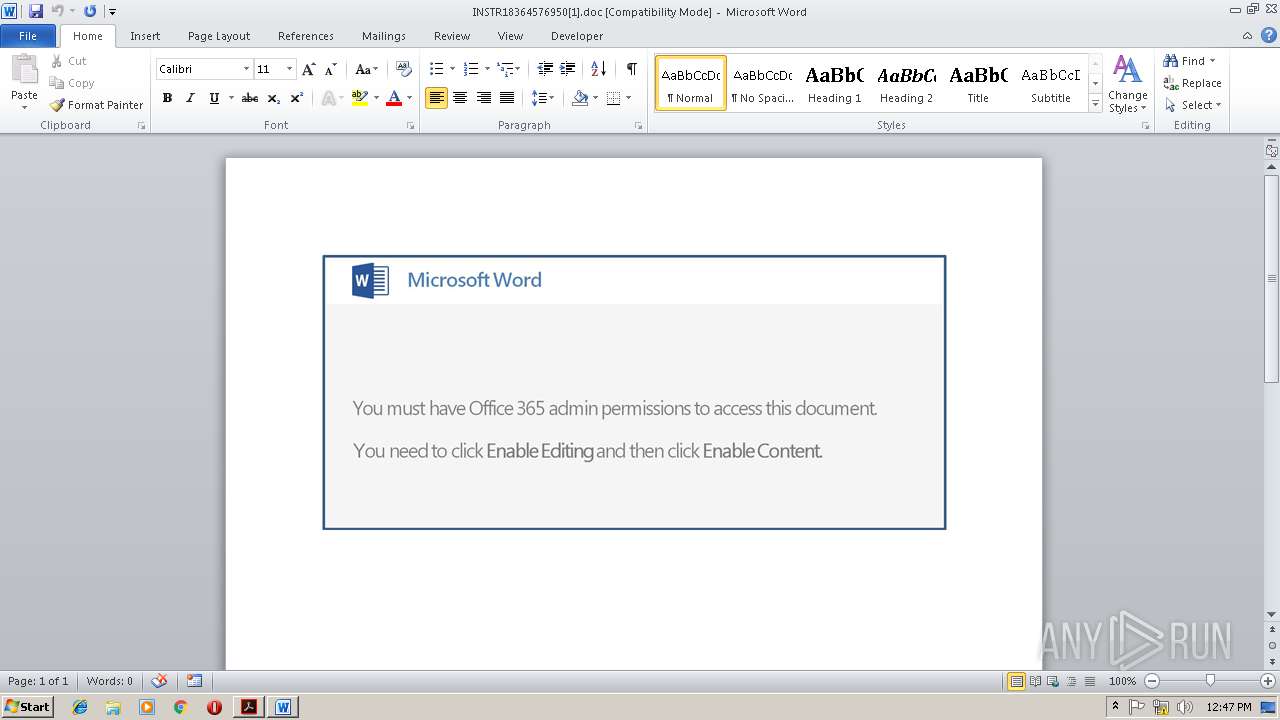
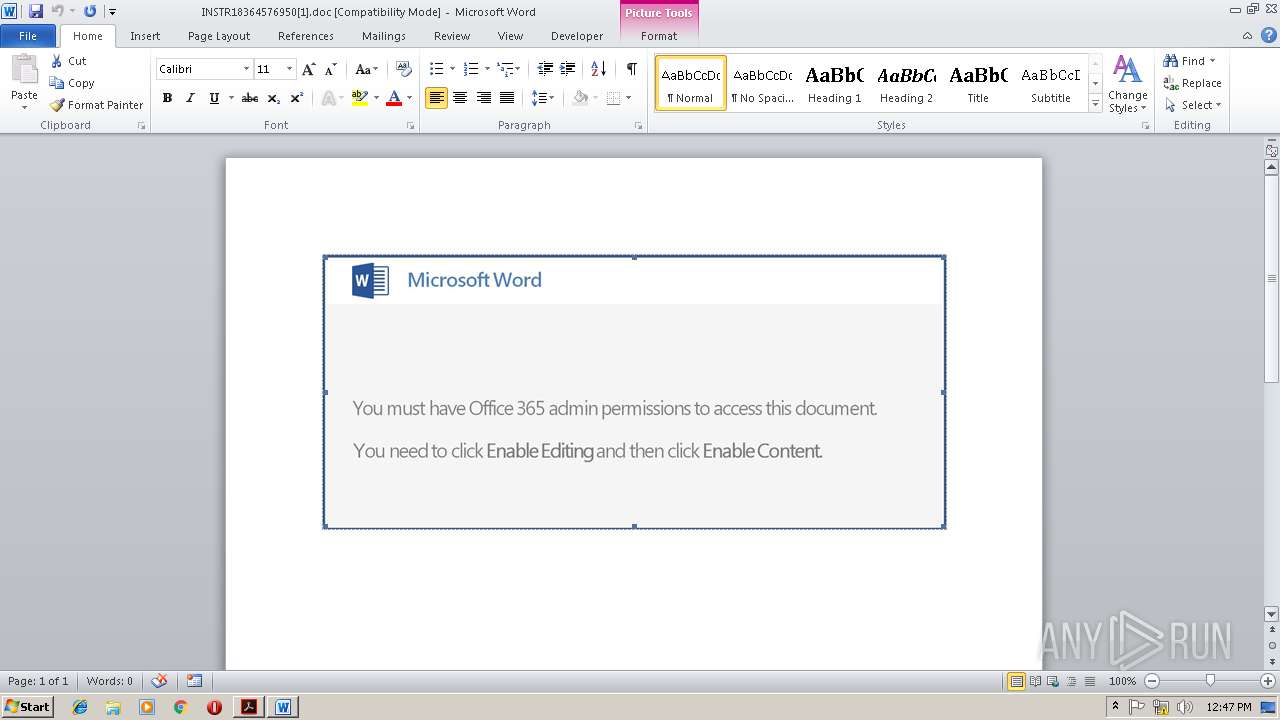
| File name: | 2019_03- Balance & Payment Report.pdf |
| Full analysis: | https://app.any.run/tasks/f31c0d68-65cb-4951-9bc8-66b6f4a96ce7 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 14, 2019, 12:45:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.3 |
| MD5: | 86A1DDA1CAB82B6FB6DC0C0DAB4C13DB |
| SHA1: | AA5C87A9BD3506D48941156E25E22F35EACC2658 |
| SHA256: | D24AE44E608B105B88293D760B1707E286825EAFB216C2D6BEFE1B946C21FAAA |
| SSDEEP: | 12288:1jSYW5WMlxgbOMCCYvrR2HGo7PD12v0WBjS2QRFHT:UWFbLeR2HvJ29kZLT |
MALICIOUS
Application was dropped or rewritten from another process
- 746.exe (PID: 3892)
- 746.exe (PID: 3784)
- wabmetagen.exe (PID: 3084)
- wabmetagen.exe (PID: 4056)
Downloads executable files from the Internet
- powershell.exe (PID: 3344)
Emotet process was detected
- wabmetagen.exe (PID: 3084)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 4056)
Connects to CnC server
- wabmetagen.exe (PID: 4056)
EMOTET was detected
- wabmetagen.exe (PID: 4056)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 3344)
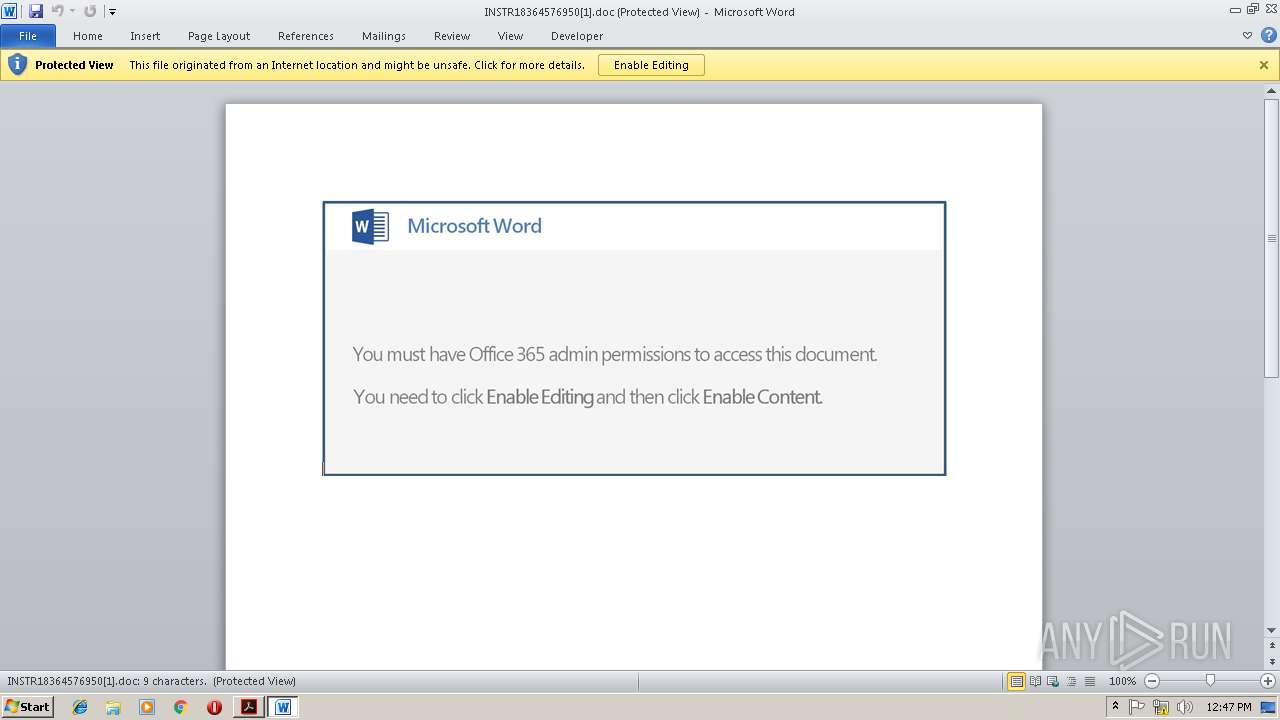
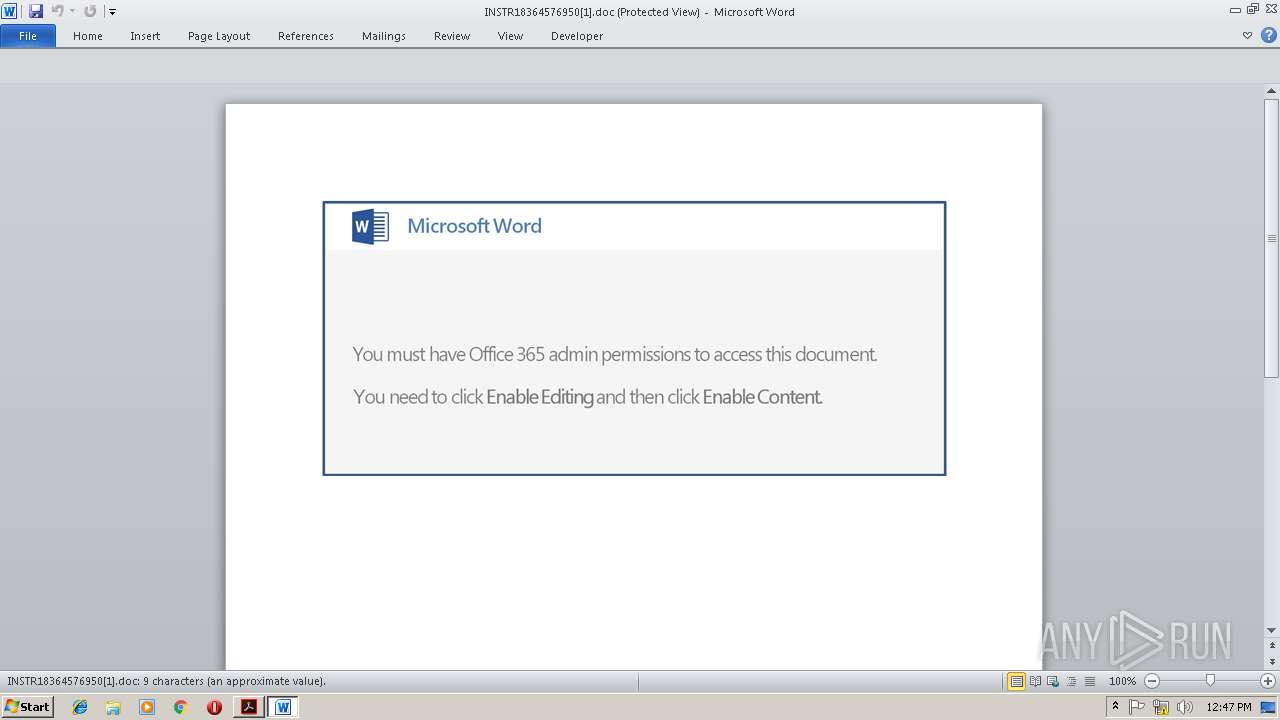
Starts Microsoft Office Application
- WINWORD.EXE (PID: 2064)
- iexplore.exe (PID: 2448)
Executable content was dropped or overwritten
- powershell.exe (PID: 3344)
- 746.exe (PID: 3784)
Application launched itself
- 746.exe (PID: 3892)
- wabmetagen.exe (PID: 3084)
- WINWORD.EXE (PID: 2064)
Starts Internet Explorer
- AcroRd32.exe (PID: 2848)
Creates files in the program directory
- AdobeARM.exe (PID: 3560)
Starts itself from another location
- 746.exe (PID: 3784)
INFO
Application launched itself
- RdrCEF.exe (PID: 4004)
- AcroRd32.exe (PID: 2848)
Creates files in the user directory
- WINWORD.EXE (PID: 2064)
- iexplore.exe (PID: 2740)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2064)
- WINWORD.EXE (PID: 1712)
Reads Internet Cache Settings
- iexplore.exe (PID: 2740)
Changes internet zones settings
- iexplore.exe (PID: 2448)
Reads internet explorer settings
- iexplore.exe (PID: 2740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.3 |
|---|---|
| Linearized: | No |
| PageCount: | 9 |
| Producer: | dompdf + CPDF |
| CreateDate: | 2019:03:14 01:19:04+03:00 |
| ModifyDate: | 2019:03:14 01:19:04+03:00 |
Total processes
49
Monitored processes
16
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1712 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /Embedding | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\INSTR18364576950[1].doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2200 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\2019_03- Balance & Payment Report.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2448 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2448 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2848 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\2019_03- Balance & Payment Report.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2984 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3024 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="4004.1.1368322876\1124427651" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3084 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 746.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Sticky Notes Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3320 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="4004.0.1985366828\64233931" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
2 984
Read events
2 465
Write events
509
Delete events
10
Modification events
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (2848) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2848) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2848) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2848) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2848) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3560) AdobeARM.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Adobe ARM\1.0\ARM |
| Operation: | write | Name: | iSpeedLauncherLogonTime |
Value: 761E6369B680D401 | |||
| (PID) Process: | (3560) AdobeARM.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
6
Text files
27
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rl7r08f_11s3slk_1p4.tmp | — | |
MD5:— | SHA256:— | |||
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R9ly9vi_11s3slj_1p4.tmp | — | |
MD5:— | SHA256:— | |||
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rc0tlie_11s3sli_1p4.tmp | — | |
MD5:— | SHA256:— | |||
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R4j0aea_11s3slh_1p4.tmp | — | |
MD5:— | SHA256:— | |||
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1uuqiwx_11s3slg_1p4.tmp | — | |
MD5:— | SHA256:— | |||
| 3560 | AdobeARM.exe | C:\Users\admin\AppData\Local\Temp\Tmp3809.tmp | — | |
MD5:— | SHA256:— | |||
| 3560 | AdobeARM.exe | C:\Users\admin\AppData\Local\Temp\Tmp3829.tmp | — | |
MD5:— | SHA256:— | |||
| 2448 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2448 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
15
DNS requests
11
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2848 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2848 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
2848 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
2848 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
3344 | powershell.exe | GET | 200 | 173.230.251.210:80 | http://shefdomi.com/ihrbuild.com/niL/ | US | executable | 354 Kb | suspicious |
2740 | iexplore.exe | GET | 200 | 192.198.90.198:80 | http://giancarloraso.com/Copy_Invoice/cwrbh-kgiwf-gshfv/ | US | document | 141 Kb | malicious |
4056 | wabmetagen.exe | GET | 200 | 187.233.152.78:443 | http://187.233.152.78:443/ | MX | binary | 132 b | malicious |
2848 | AcroRd32.exe | GET | 304 | 2.16.186.32:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
2448 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2848 | AcroRd32.exe | 2.16.186.32:80 | acroipm2.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 2.18.68.206:443 | ardownload2.adobe.com | Akamai International B.V. | — | whitelisted |
2740 | iexplore.exe | 192.198.90.198:80 | giancarloraso.com | Centrilogic, Inc. | US | suspicious |
2448 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3560 | AdobeARM.exe | 2.18.68.206:443 | ardownload2.adobe.com | Akamai International B.V. | — | whitelisted |
3344 | powershell.exe | 38.123.253.66:443 | smesmedia.com | Cogent Communications | US | unknown |
3344 | powershell.exe | 103.31.250.67:443 | tribuana-aerospace.com | Argon Data Communication | ID | suspicious |
3344 | powershell.exe | 190.210.176.190:443 | pasioncontinental.com | NSS S.A. | AR | suspicious |
2848 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ardownload2.adobe.com |
| whitelisted |
www.bing.com |
| whitelisted |
giancarloraso.com |
| malicious |
smesmedia.com |
| unknown |
tribuana-aerospace.com |
| suspicious |
pasioncontinental.com |
| suspicious |
shefdomi.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2740 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
3344 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3344 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3344 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3344 | powershell.exe | Misc activity | ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging) |
4056 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report