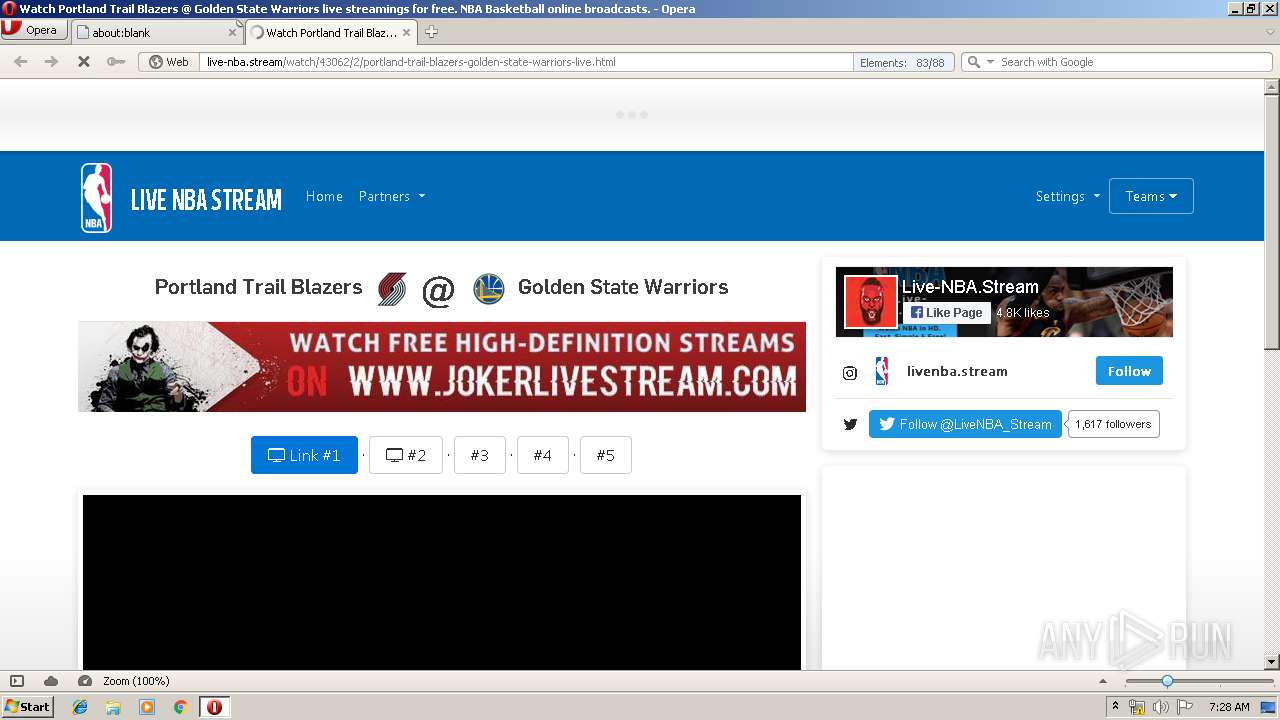
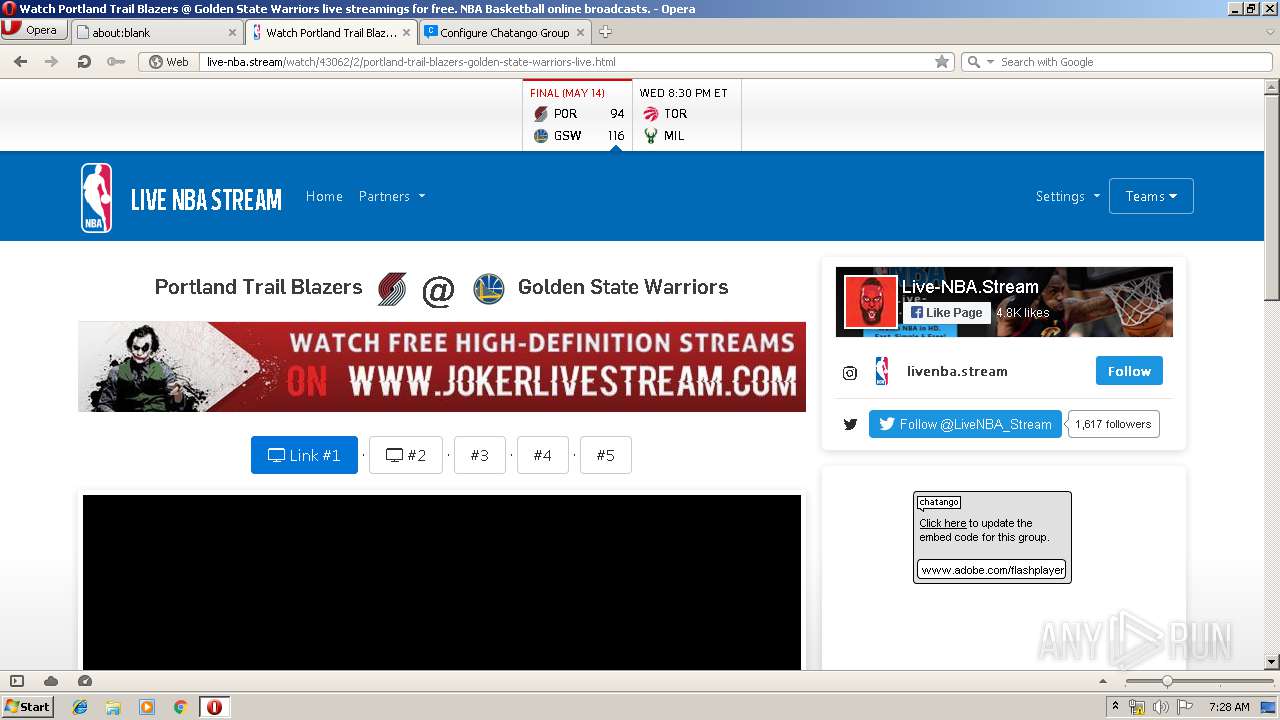
| URL: | https://live-nba.stream/watch/43062/2/portland-trail-blazers-golden-state-warriors-live.html |
| Full analysis: | https://app.any.run/tasks/1d32bde1-a317-409b-8b69-59d0d4b59f02 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 06:27:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0A9216A1AA760487AE1DC296C72BE3A2 |
| SHA1: | E41AB8063C36D1C24B9752E113523E830D0E7BBA |
| SHA256: | D22485A9A81D97F9D388625CF4469B95F8CEBFDBA6364285F6E1516600448025 |
| SSDEEP: | 3:N8MT6iG9zXKXViBwc2AxacrhMTAwJ:2Mm9Oq2yaPJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Creates files in the user directory
- opera.exe (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
35
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1684 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /o /eo /l /b /id 3660 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2856 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 3660 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | opera.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 3660 | "C:\Program Files\Opera\opera.exe" https://live-nba.stream/watch/43062/2/portland-trail-blazers-golden-state-warriors-live.html | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
265
Read events
204
Write events
61
Delete events
0
Modification events
| (PID) Process: | (3660) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe https://live-nba.stream/watch/43062/2/portland-trail-blazers-golden-state-warriors-live.html | |||
| (PID) Process: | (3660) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1684) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
Executable files
0
Suspicious files
87
Text files
46
Unknown types
58
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprFB07.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprFB27.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\oprFBC4.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\S4KD4BA1XE0HANVX6Z70.temp | — | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr1289.tmp | — | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\16ec093b8f51508f.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 3660 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
125
DNS requests
46
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3660 | opera.exe | GET | 200 | 151.139.128.14:80 | http://crl.usertrust.com/AddTrustExternalCARoot.crl | US | der | 673 b | whitelisted |
3660 | opera.exe | GET | 200 | 192.35.177.64:80 | http://crl.identrust.com/DSTROOTCAX3CRL.crl | US | der | 896 b | whitelisted |
3660 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3660 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertGlobalRootCA.crl | US | der | 581 b | whitelisted |
3660 | opera.exe | GET | 200 | 104.18.20.226:80 | http://crl.globalsign.net/root.crl | US | der | 782 b | whitelisted |
3660 | opera.exe | GET | 200 | 151.139.128.14:80 | http://crl.comodoca.com/COMODORSACertificationAuthority.crl | US | der | 812 b | whitelisted |
3660 | opera.exe | GET | 200 | 172.217.22.35:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEGP04nWBbUL75ThIZuPamrU%3D | US | der | 471 b | whitelisted |
3660 | opera.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEAwlX%2BWwe0xUZK7sA79up6Y%3D | US | der | 471 b | whitelisted |
3660 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQQX6Z6gAidtSefNc6DC0OInqPHDQQUD4BhHIIxYdUvKOeNRji0LOHG2eICEAJvJGeK%2FtwlV70AH1C0Bso%3D | US | der | 471 b | whitelisted |
3660 | opera.exe | GET | 304 | 208.93.230.18:80 | http://st.chatango.com/flash/flashgroup.swf | US | swf | 127 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3660 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3660 | opera.exe | 185.125.230.221:443 | live-nba.stream | MAROSNET Telecommunication Company LLC | RU | unknown |
3660 | opera.exe | 185.26.182.112:443 | sitecheck2.opera.com | Opera Software AS | — | malicious |
3660 | opera.exe | 185.26.182.93:443 | sitecheck2.opera.com | Opera Software AS | — | whitelisted |
3660 | opera.exe | 192.35.177.64:80 | crl.identrust.com | IdenTrust | US | malicious |
3660 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
3660 | opera.exe | 104.19.195.151:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | shared |
3660 | opera.exe | 195.181.170.18:443 | 1079020916.rsc.cdn77.org | Datacamp Limited | DE | suspicious |
3660 | opera.exe | 31.13.90.36:443 | www.facebook.com | Facebook, Inc. | IE | whitelisted |
3660 | opera.exe | 172.217.22.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
live-nba.stream |
| suspicious |
sitecheck2.opera.com |
| whitelisted |
certs.opera.com |
| whitelisted |
crl.identrust.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
1079020916.rsc.cdn77.org |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
www.facebook.com |
| whitelisted |
platform.twitter.com |
| whitelisted |
st.chatango.com |
| whitelisted |