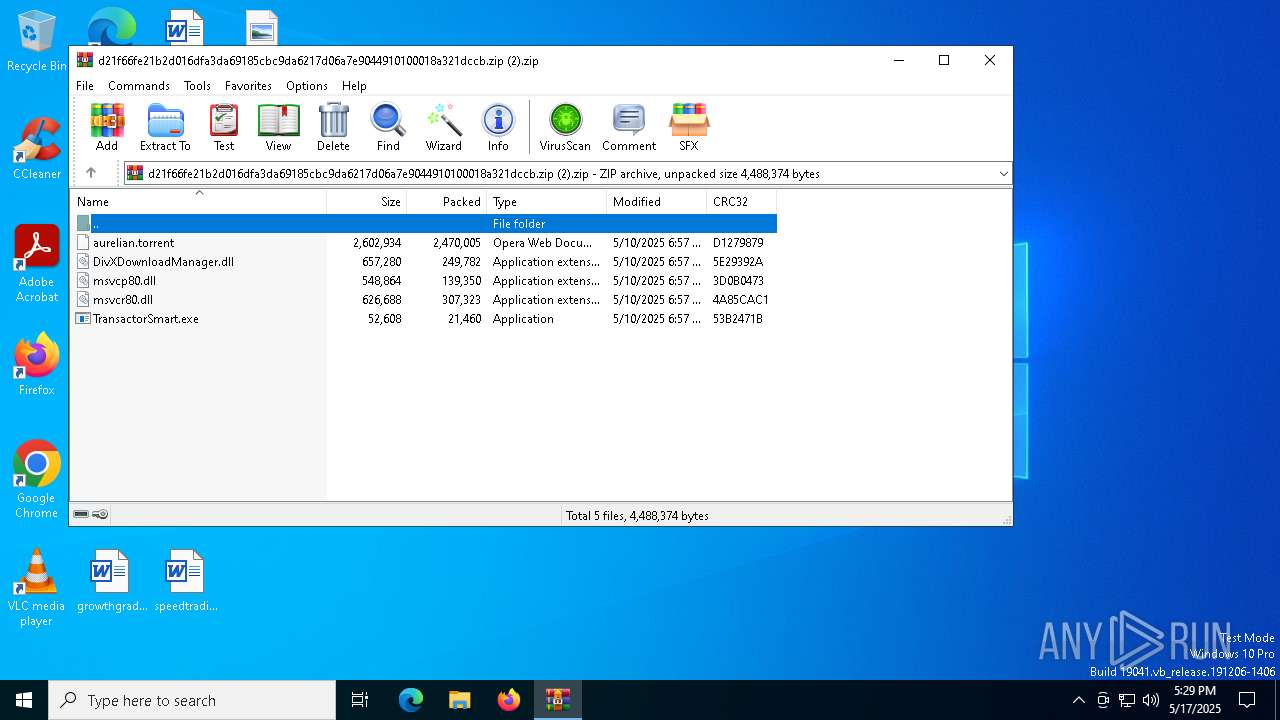
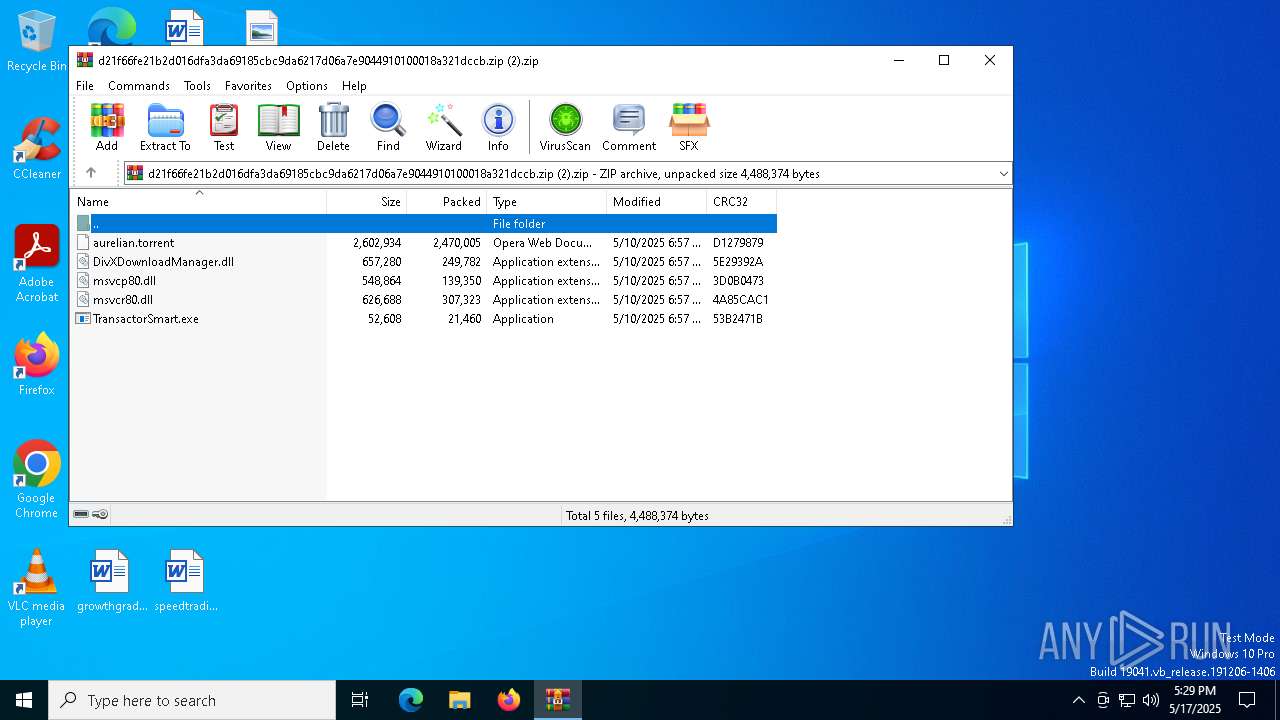
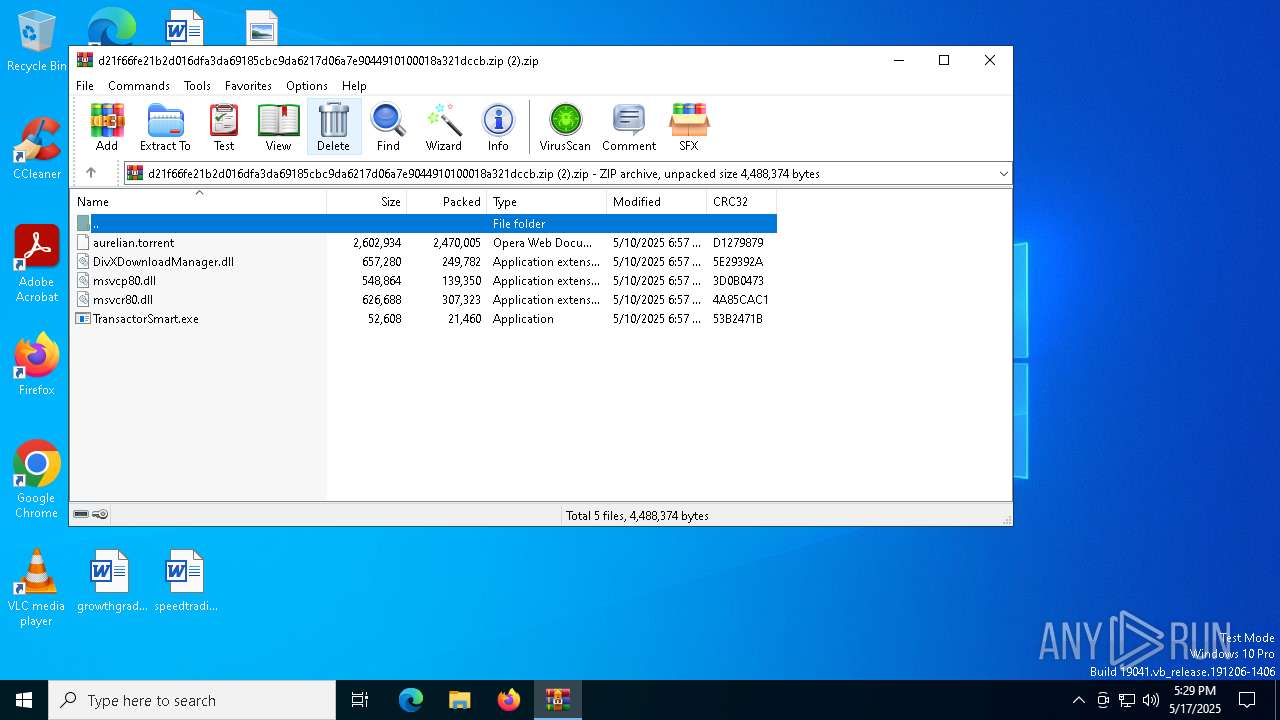
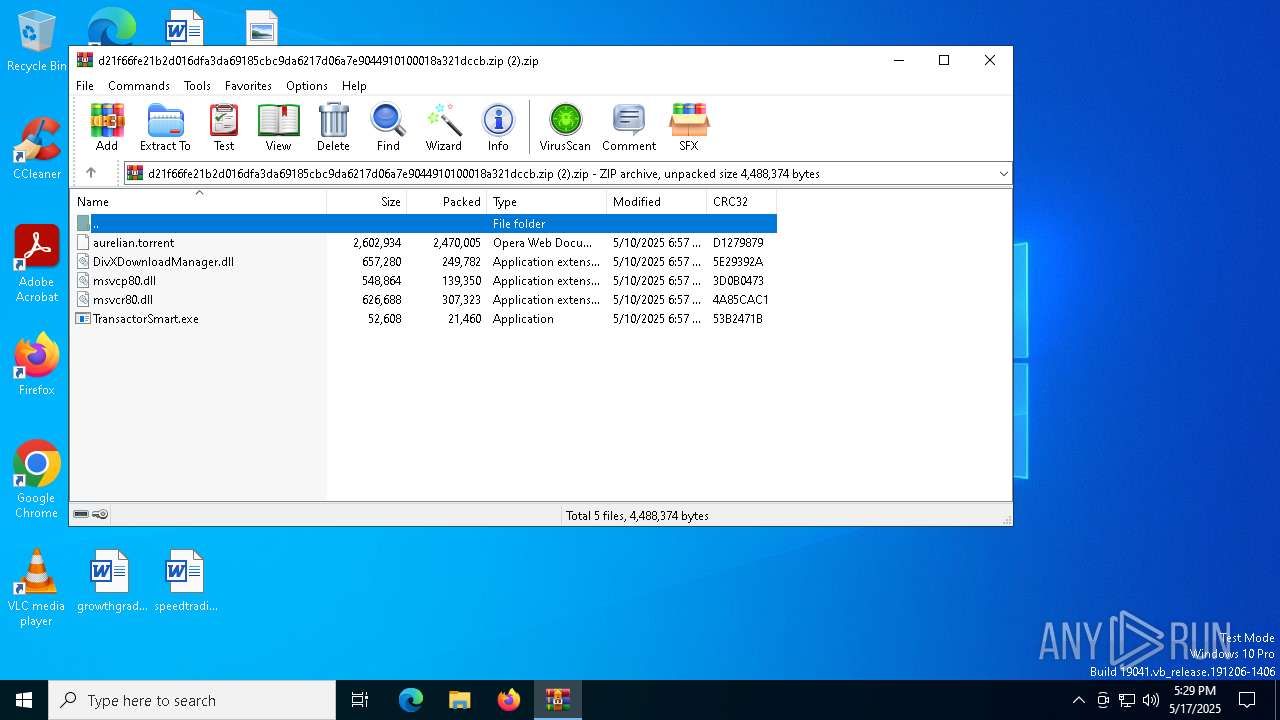
| File name: | d21f66fe21b2d016dfa3da69185cbc9da6217d06a7e9044910100018a321dccb.zip (2) |
| Full analysis: | https://app.any.run/tasks/7a81473c-3b65-4a49-a421-da72a71070cf |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 17:29:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0C3EDBEA834A8F5FC732A50E9D78D214 |
| SHA1: | 26B0295864A938CE536C9AD0FAC125043A7B2E12 |
| SHA256: | D21F66FE21B2D016DFA3DA69185CBC9DA6217D06A7E9044910100018A321DCCB |
| SSDEEP: | 98304:ChotiscCFoFMlRgTpoqlTJOlwxjU99sSDulODkbl9PEhSTvdOaLqgmCMXnBZPEv+:Wq5Q2jx7r |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 7376)
- TransactorSmart.exe (PID: 8184)
Executing a file with an untrusted certificate
- TransactorSmart.exe (PID: 8184)
- TransactorSmart.exe (PID: 7188)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 7376)
- TransactorSmart.exe (PID: 8184)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7376)
The process drops C-runtime libraries
- TransactorSmart.exe (PID: 8184)
Executable content was dropped or overwritten
- TransactorSmart.exe (PID: 8184)
- TransactorSmart.exe (PID: 7188)
Starts itself from another location
- TransactorSmart.exe (PID: 8184)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 7376)
- TransactorSmart.exe (PID: 8184)
- TransactorSmart.exe (PID: 7188)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7376)
Checks supported languages
- TransactorSmart.exe (PID: 8184)
- TransactorSmart.exe (PID: 7188)
Reads the computer name
- TransactorSmart.exe (PID: 8184)
- TransactorSmart.exe (PID: 7188)
Creates files or folders in the user directory
- TransactorSmart.exe (PID: 8184)
Creates files in the program directory
- TransactorSmart.exe (PID: 8184)
- TransactorSmart.exe (PID: 7188)
Create files in a temporary directory
- TransactorSmart.exe (PID: 7188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:10 19:57:04 |
| ZipCRC: | 0xd1279879 |
| ZipCompressedSize: | 2470005 |
| ZipUncompressedSize: | 2602934 |
| ZipFileName: | aurelian.torrent |
Total processes
131
Monitored processes
6
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7176 | "C:\ProgramData\asus\tcpvcon.exe" "C:\ProgramData\asus\tcpvcon.exe" /accepteula | C:\ProgramData\asus\tcpvcon.exe | — | TransactorSmart.exe | |||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Sysinternals TcpVcon Version: 4.18 | |||||||||||||||
| 7188 | C:\ProgramData\asus\TransactorSmart.exe | C:\ProgramData\asus\TransactorSmart.exe | TransactorSmart.exe | ||||||||||||
User: admin Company: DivX, LLC Integrity Level: MEDIUM Description: DivX Download Manager Service Version: 1.2.0.195 Modules
| |||||||||||||||
| 7376 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\d21f66fe21b2d016dfa3da69185cbc9da6217d06a7e9044910100018a321dccb.zip (2).zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7504 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7536 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8184 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa7376.34670\TransactorSmart.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa7376.34670\TransactorSmart.exe | WinRAR.exe | ||||||||||||
User: admin Company: DivX, LLC Integrity Level: MEDIUM Description: DivX Download Manager Service Exit code: 0 Version: 1.2.0.195 Modules
| |||||||||||||||
Total events
2 337
Read events
2 329
Write events
8
Delete events
0
Modification events
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\d21f66fe21b2d016dfa3da69185cbc9da6217d06a7e9044910100018a321dccb.zip (2).zip | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7376) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7376.34670\DivXDownloadManager.dll | executable | |
MD5:E1146619FC1DB71A1E3668371342E626 | SHA256:A39E5A8204F10AD32C0156569439624D744A4D504CBEF9925E94BCC7439FEC0E | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7376.34670\msvcr80.dll | executable | |
MD5:43143ABB001D4211FAB627C136124A44 | SHA256:CB8928FF2FAF2921B1EDDC267DCE1BB64E6FEE4D15B68CD32588E0F3BE116B03 | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7376.34670\msvcp80.dll | executable | |
MD5:272A9E637ADCAF30B34EA184F4852836 | SHA256:35B15B78C31111DB4FA11D9C9CAD3A6F22C92DAA5E6F069DC455E72073266CC4 | |||
| 8184 | TransactorSmart.exe | C:\ProgramData\asus\msvcr80.dll | executable | |
MD5:43143ABB001D4211FAB627C136124A44 | SHA256:CB8928FF2FAF2921B1EDDC267DCE1BB64E6FEE4D15B68CD32588E0F3BE116B03 | |||
| 8184 | TransactorSmart.exe | C:\ProgramData\asus\aurelian.torrent | binary | |
MD5:73051F1FED9D7F0B21D4CDC48224A32B | SHA256:C050D48792242351FD33A0375F262B8743EB61164D250D27758286C9083FE3FD | |||
| 8184 | TransactorSmart.exe | C:\ProgramData\asus\TransactorSmart.exe | executable | |
MD5:FF254C1778AEFE5AF06889F1F999DEE3 | SHA256:94BC0C01641801F258E207ECA8227845F3F1C686E7394CE3864A6B2538B8EADB | |||
| 7188 | TransactorSmart.exe | C:\ProgramData\asus\tcpvcon.exe | executable | |
MD5:1CF39530D557CE880D7F71984928384F | SHA256:198995FECC0E38A2749B7E48C54112A959B77878683B726EE36430C4BACEC196 | |||
| 7376 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa7376.34670\TransactorSmart.exe | executable | |
MD5:FF254C1778AEFE5AF06889F1F999DEE3 | SHA256:94BC0C01641801F258E207ECA8227845F3F1C686E7394CE3864A6B2538B8EADB | |||
| 8184 | TransactorSmart.exe | C:\ProgramData\asus\msvcp80.dll | executable | |
MD5:272A9E637ADCAF30B34EA184F4852836 | SHA256:35B15B78C31111DB4FA11D9C9CAD3A6F22C92DAA5E6F069DC455E72073266CC4 | |||
| 7188 | TransactorSmart.exe | C:\Users\admin\AppData\Local\Temp\F577E45.tmp | binary | |
MD5:0FA5AE659DB2DA06908FDBE3B1400149 | SHA256:06DE27C0D629F8FF5BEC3B0789128B2C13664E8FF521503CFB4078C5F1C6FB8D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.35:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8020 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8020 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.216.77.35:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8020 | SIHClient.exe | 172.202.163.200:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |