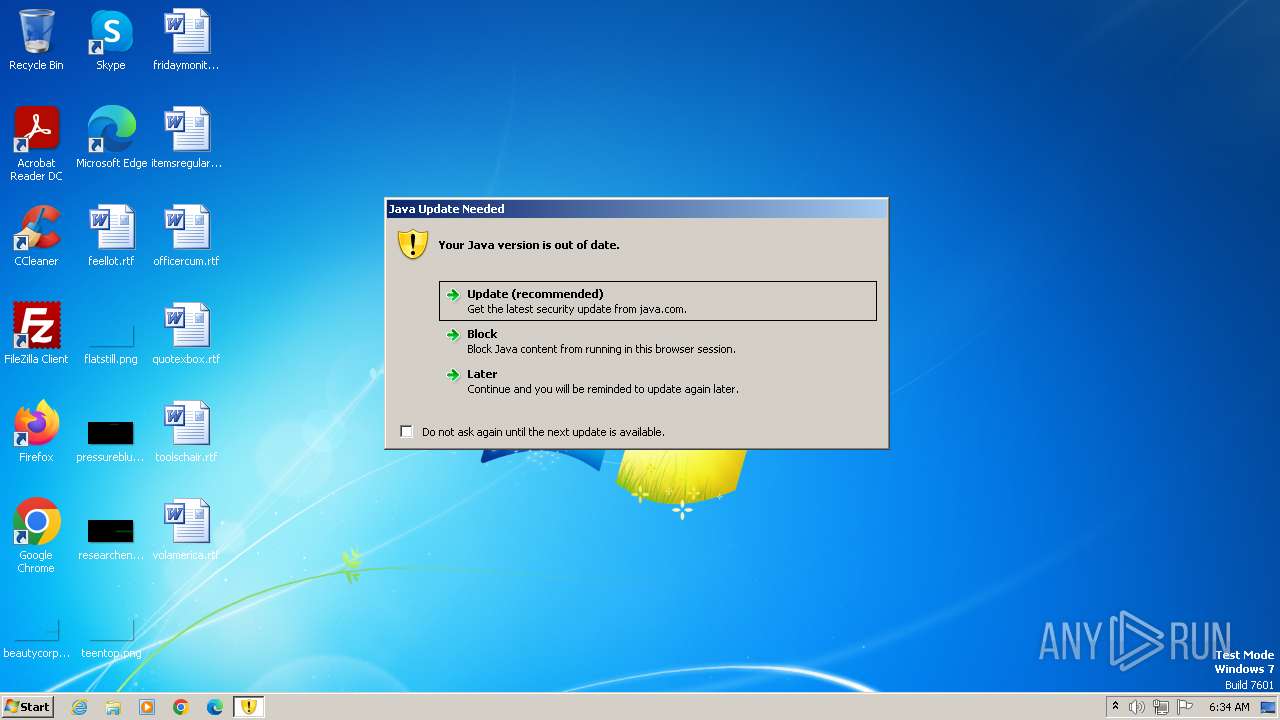
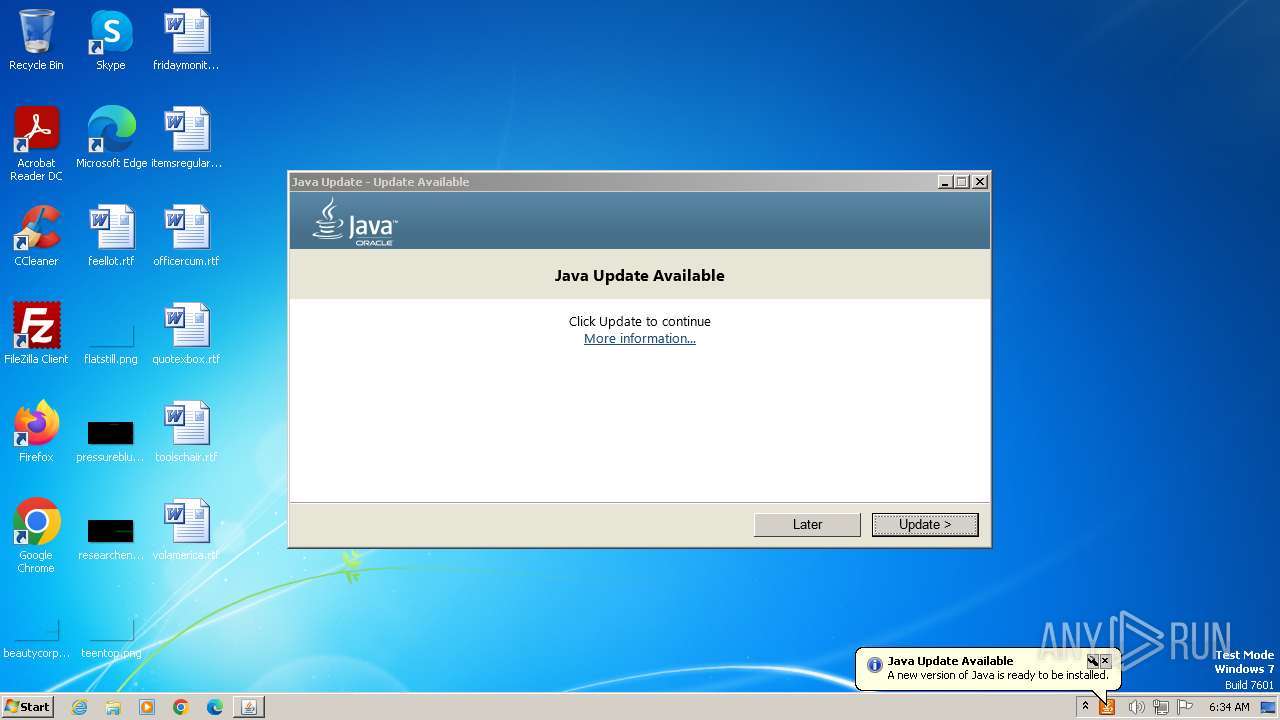
| URL: | http://download.jsglobalonline.com/TradeCast//TC.jnlp |
| Full analysis: | https://app.any.run/tasks/d7f9e0aa-910c-44df-ba5a-a41d455b28cf |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2023, 05:34:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | 68B8EE5B742EC97335F953D9C311070B386B6713 |
| SHA256: | D2136699DD46DF1E9A4630E55B7FB7A568AAF8D47EF88BC7FE3305B3870DE7EC |
| SSDEEP: | 3:N1KaKEluCEkE2KiJUbn:Ca5N8n |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks for Java to be installed
- javaws.exe (PID: 856)
- javaw.exe (PID: 372)
- javaw.exe (PID: 4000)
- javaw.exe (PID: 3320)
- jp2launcher.exe (PID: 3744)
- jucheck.exe (PID: 2876)
Reads the Internet Settings
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Reads security settings of Internet Explorer
- jucheck.exe (PID: 2876)
Checks Windows Trust Settings
- jucheck.exe (PID: 2876)
Reads settings of System Certificates
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Reads Microsoft Outlook installation path
- jucheck.exe (PID: 2876)
Reads Internet Explorer settings
- jucheck.exe (PID: 2876)
INFO
Application launched itself
- iexplore.exe (PID: 2472)
Checks supported languages
- javaws.exe (PID: 856)
- javaw.exe (PID: 372)
- javaw.exe (PID: 4000)
- javaw.exe (PID: 3320)
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
- javaws.exe (PID: 3328)
The process uses the downloaded file
- iexplore.exe (PID: 2472)
Create files in a temporary directory
- javaw.exe (PID: 372)
- javaw.exe (PID: 4000)
- javaw.exe (PID: 3320)
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Creates files in the program directory
- javaw.exe (PID: 372)
Reads the computer name
- javaw.exe (PID: 372)
- javaw.exe (PID: 4000)
- javaw.exe (PID: 3320)
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Reads the machine GUID from the registry
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Checks proxy server information
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Creates files or folders in the user directory
- jucheck.exe (PID: 2876)
- jp2launcher.exe (PID: 3744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
48
Monitored processes
10
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 372 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.11.271.2" "update" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 856 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TC.jnlp" | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | iexplore.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 1 Version: 11.271.2.09 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://download.jsglobalonline.com/TradeCast//TC.jnlp" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2512 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2472 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Common Files\Java\Java Update\jucheck.exe" | C:\Program Files\Common Files\Java\Java Update\jucheck.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Checker Exit code: 0 Version: 2.8.271.9 Modules
| |||||||||||||||
| 3320 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.suppression.11.271.2" "false" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
| 3328 | "C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe" -J-Djdk.disableLastUsageTracking=true -SSVBaselineUpdate | C:\Program Files\Java\jre1.8.0_271\bin\javaws.exe | — | jucheck.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Start Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 3464 | C:\Windows\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3744 | "C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe" -secure -javaws -jre "C:\Program Files\Java\jre1.8.0_271" -vma LWNsYXNzcGF0aABDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxkZXBsb3kuamFyAC1EamF2YS5zZWN1cml0eS5wb2xpY3k9ZmlsZTpDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxzZWN1cml0eVxqYXZhd3MucG9saWN5AC1EdHJ1c3RQcm94eT10cnVlAC1YdmVyaWZ5OnJlbW90ZQAtRGpubHB4LmhvbWU9QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxiaW4ALURqYXZhLnNlY3VyaXR5Lm1hbmFnZXIALURzdW4uYXd0Lndhcm11cD10cnVlAC1YYm9vdGNsYXNzcGF0aC9hOkM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcbGliXGphdmF3cy5qYXI7QzpcUHJvZ3JhbSBGaWxlc1xKYXZhXGpyZTEuOC4wXzI3MVxsaWJcZGVwbG95LmphcjtDOlxQcm9ncmFtIEZpbGVzXEphdmFcanJlMS44LjBfMjcxXGxpYlxwbHVnaW4uamFyAC1EamRrLmRpc2FibGVMYXN0VXNhZ2VUcmFja2luZz10cnVlAC1Eam5scHguanZtPUM6XFByb2dyYW0gRmlsZXNcSmF2YVxqcmUxLjguMF8yNzFcYmluXGphdmF3LmV4ZQAtRGpubHB4LnZtYXJncz1MVVJxWkdzdVpHbHpZV0pzWlV4aGMzUlZjMkZuWlZSeVlXTnJhVzVuUFhSeWRXVUE= -ma LVNTVkJhc2VsaW5lVXBkYXRlAC1ub3RXZWJKYXZh | C:\Program Files\Java\jre1.8.0_271\bin\jp2launcher.exe | javaws.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Web Launcher Exit code: 0 Version: 11.271.2.09 Modules
| |||||||||||||||
| 4000 | "C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe" -cp "C:\PROGRA~1\Java\JRE18~1.0_2\lib\deploy.jar" com.sun.deploy.panel.ControlPanel -userConfig "deployment.expiration.decision.timestamp.11.271.2" "1697780093" | C:\Program Files\Java\jre1.8.0_271\bin\javaw.exe | — | javaws.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.2710.9 Modules
| |||||||||||||||
Total events
20 343
Read events
20 221
Write events
113
Delete events
9
Modification events
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2472) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
12
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TC.jnlp | xml | |
MD5:6A53BD52629EA2165F4947548C04B865 | SHA256:5CF530BF78F89C2AAA635806D41F52A1E24FBAA3C8956E8D578AF58F9D85F2A3 | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TC.jnlp.d6lz0cr.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2512 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\TC.jnlp.d6lz0cr.partial | xml | |
MD5:6A53BD52629EA2165F4947548C04B865 | SHA256:5CF530BF78F89C2AAA635806D41F52A1E24FBAA3C8956E8D578AF58F9D85F2A3 | |||
| 2876 | jucheck.exe | C:\Users\admin\AppData\Local\Temp\au-descriptor-1.8.0_391-b13.xml | xml | |
MD5:FACFDF11AEA6324F7D155D58EFFA30FF | SHA256:6E02C6765766CB66DE2F01408E90B0E046CF331696EE9E244B34CFBD9D7AA60D | |||
| 2876 | jucheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:CACCBB6413C588394C0EBBF886417D08 | SHA256:16E8ED25272AB148F1F32977950E0B4F9E6000B53484D0473C2A892E24BB0FFC | |||
| 2876 | jucheck.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:655553511FFF8A912634ABDF7077C82A | SHA256:5168840A8BAD2BC99664A88137A5351E203AC2124656B9E7F8A344BFC82E0A6E | |||
| 372 | javaw.exe | C:\Users\admin\AppData\LocalLow\Sun\Java\Deployment\deployment.properties | text | |
MD5:6CBE9CBCD89CD31F1008F01DDB91DD1C | SHA256:47231A4746D305340A26B1B5F472D91667B451A8AD5B4C01C50015318C299D9B | |||
| 2472 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFE7726CF160B6C241.TMP | binary | |
MD5:2A2BDB6D6E28912FD52EFD04BF4CF6C2 | SHA256:00AA3A2CD9C20E3198203092A3709A95C604CCEA2F7252B9E60507AFE5BEF01A | |||
| 372 | javaw.exe | C:\Users\admin\AppData\Local\Temp\JavaDeployReg.log | text | |
MD5:8BC43C852803D06300FF249AE9DC2596 | SHA256:7552B5460FE425CB5317586F2FA079DCA5EB52B7ECC1F9E28BF6E7607E97D003 | |||
| 372 | javaw.exe | C:\ProgramData\Oracle\Java\.oracle_jre_usage\17dfc292991c8061.timestamp | text | |
MD5:2BBCEAB1E379649BCB4F0960F011C910 | SHA256:CC22CD24A5615072231AA87E0888D11663907AA28FE655635CF69E4A28A9E50A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
13
DNS requests
5
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2512 | iexplore.exe | GET | 200 | 175.107.196.23:80 | http://download.jsglobalonline.com/TradeCast//TC.jnlp | unknown | xml | 5.26 Kb | unknown |
2876 | jucheck.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?759210f56ceeef91 | unknown | compressed | 4.66 Kb | unknown |
2876 | jucheck.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3744 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3744 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 471 b | unknown |
3744 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 727 b | unknown |
3744 | jp2launcher.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | binary | 727 b | unknown |
2472 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2512 | iexplore.exe | 175.107.196.23:80 | — | Cyber Internet Services Pakistan | PK | malicious |
2876 | jucheck.exe | 23.212.218.110:443 | javadl-esd-secure.oracle.com | AKAMAI-AS | AU | unknown |
2876 | jucheck.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
2876 | jucheck.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3744 | jp2launcher.exe | 23.212.218.110:443 | javadl-esd-secure.oracle.com | AKAMAI-AS | AU | unknown |
3744 | jp2launcher.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2472 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | EDGECAST | US | whitelisted |
2472 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
javadl-esd-secure.oracle.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3744 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |
3744 | jp2launcher.exe | Potentially Bad Traffic | ET POLICY Vulnerable Java Version 1.8.x Detected |