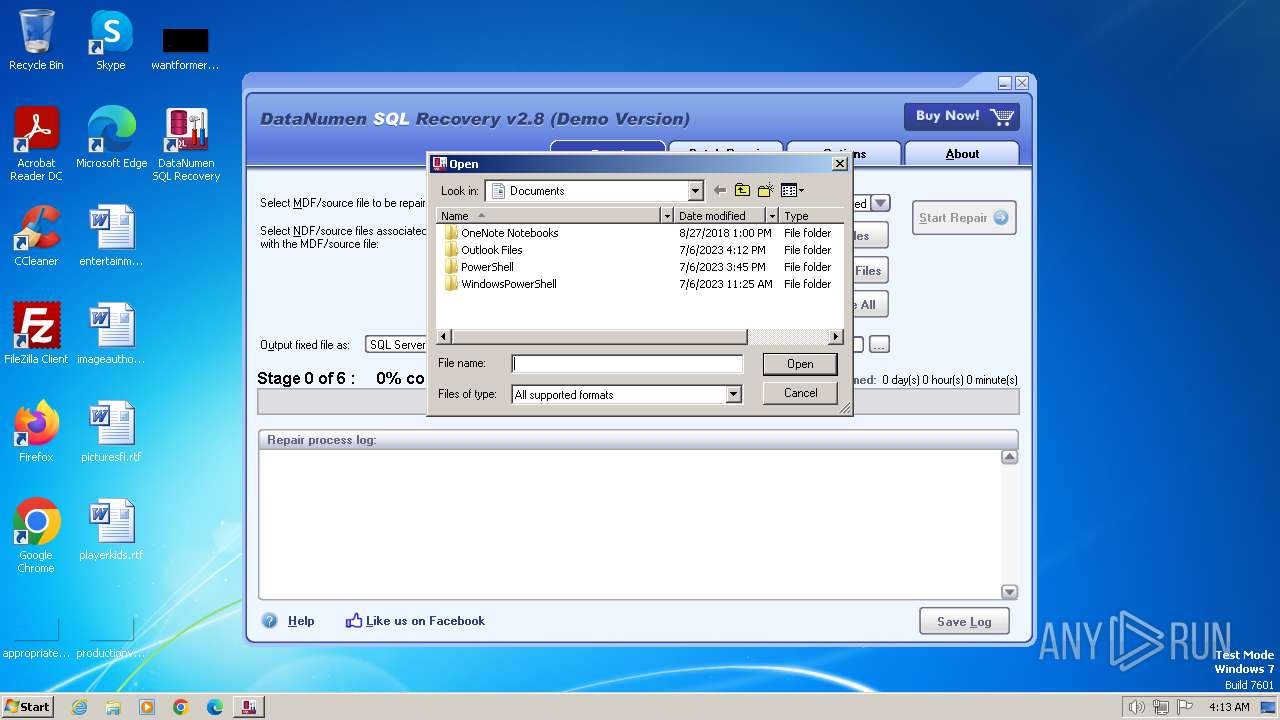
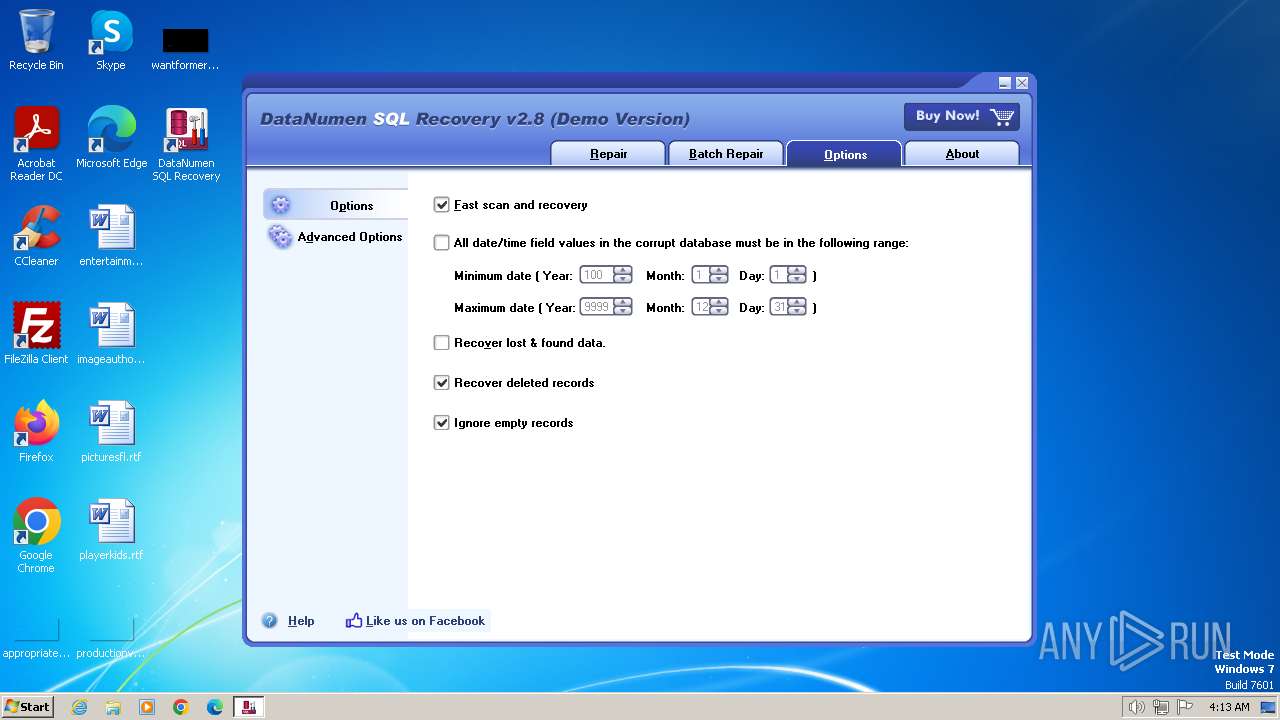
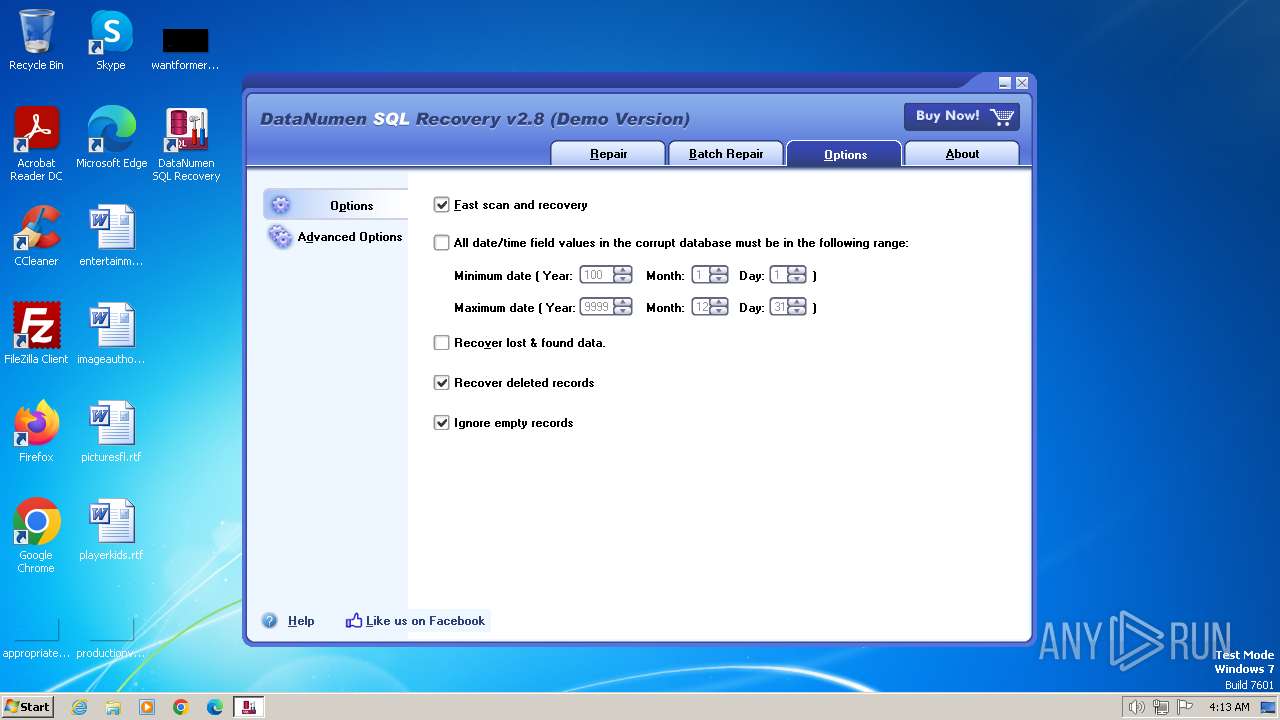
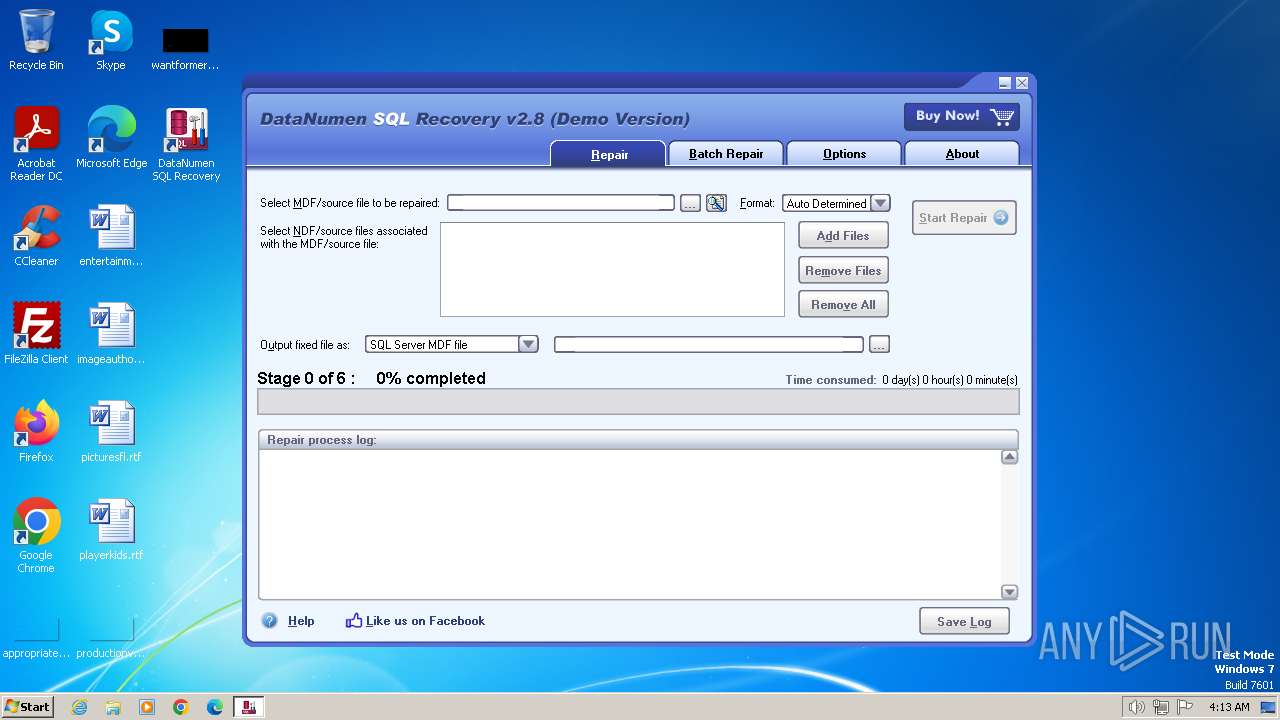
| File name: | dsr.exe |
| Full analysis: | https://app.any.run/tasks/079b4af5-4a6b-4118-b83c-6458a56a673d |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2024, 04:12:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | DE7760E35B6B6F6FDCF4BA02FF10B6F3 |
| SHA1: | 3AC8FD54607990645A8224E84EF347140C76531E |
| SHA256: | D205F48DD98C98B5BF714B6B0F2576B356482C53C8A4BEB4078635333E5D9B68 |
| SSDEEP: | 98304:kETd3DmrLmCpCQOoHyQon1K4oYx0PiUg88ztooWAud85PXdMiBCL7heTKrHtcuhw:j1SA |
MALICIOUS
Drops the executable file immediately after the start
- dsr.exe (PID: 2420)
- GLBFAFA.tmp (PID: 2016)
Creates a writable file in the system directory
- GLBFAFA.tmp (PID: 2016)
SUSPICIOUS
Starts application with an unusual extension
- dsr.exe (PID: 2420)
- GLBFAFA.tmp (PID: 2016)
Executable content was dropped or overwritten
- GLBFAFA.tmp (PID: 2016)
- dsr.exe (PID: 2420)
Reads the Internet Settings
- GLBFAFA.tmp (PID: 2016)
INFO
Checks supported languages
- GLBFAFA.tmp (PID: 2016)
- dsr.exe (PID: 2420)
- GLJFBE6.tmp (PID: 480)
- DSR.exe (PID: 1652)
Create files in a temporary directory
- dsr.exe (PID: 2420)
- GLBFAFA.tmp (PID: 2016)
Reads the computer name
- GLBFAFA.tmp (PID: 2016)
- DSR.exe (PID: 1652)
Creates files in the program directory
- GLBFAFA.tmp (PID: 2016)
Creates files or folders in the user directory
- GLBFAFA.tmp (PID: 2016)
Reads the machine GUID from the registry
- DSR.exe (PID: 1652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:08:16 20:13:16+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 7.1 |
| CodeSize: | 1024 |
| InitializedDataSize: | 2171904 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.8.0.0 |
| ProductVersionNumber: | 1032.4455.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
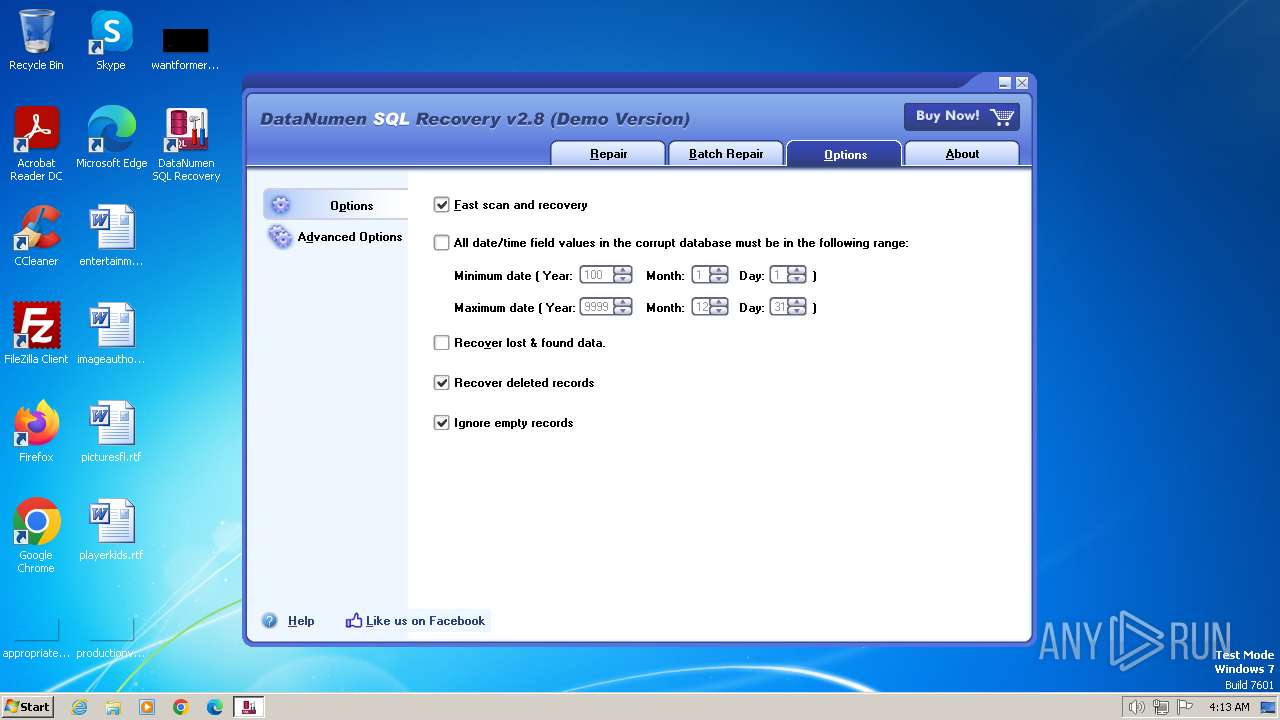
| CompanyName: | DataNumen, Inc. |
| FileDescription: | DataNumen SQL Recovery Installer |
| FileVersion: | 2.8 |
| LegalCopyright: | Copyright(C) 2001 - 2018 DataNumen, Inc. |
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\dsr.exe" | C:\Users\admin\AppData\Local\Temp\dsr.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 480 | "C:\Users\admin\AppData\Local\Temp\GLJFBE6.tmp" C:\Program Files\DSR\DSRSHL.dll | C:\Users\admin\AppData\Local\Temp\GLJFBE6.tmp | — | GLBFAFA.tmp | |||||||||||
User: admin Company: Altiris Integrity Level: HIGH Description: WiseScript COM Registration Tool Exit code: 0 Version: 10.03.0.250 Modules
| |||||||||||||||
| 1652 | "C:\PROGRA~1\DSR\DSR.exe" | C:\Program Files\DSR\DSR.exe | — | GLBFAFA.tmp | |||||||||||
User: admin Company: DataNumen, Inc. Integrity Level: HIGH Exit code: 0 Version: 2.8.0.2 Modules
| |||||||||||||||
| 2016 | C:\Users\admin\AppData\Local\Temp\GLBFAFA.tmp 6656 C:\Users\admin\AppData\Local\Temp\dsr.exe | C:\Users\admin\AppData\Local\Temp\GLBFAFA.tmp | dsr.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Local\Temp\dsr.exe" | C:\Users\admin\AppData\Local\Temp\dsr.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
1 676
Read events
1 647
Write events
28
Delete events
1
Modification events
| (PID) Process: | (2016) GLBFAFA.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2016) GLBFAFA.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2016) GLBFAFA.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2016) GLBFAFA.tmp | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1652) DSR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (1652) DSR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 06000000000000000B0000000100000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (1652) DSR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000006000000000000000B00000001000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (1652) DSR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (1652) DSR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (1652) DSR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlgLegacy |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
Executable files
22
Suspicious files
8
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\~GLH0005.TMP | text | |
MD5:B553B8BA8B29F1FF08B1728E23D5B575 | SHA256:E223063DC2342EB6562F249C4590322F638A9AC818584BA1308569131068AC42 | |||
| 2016 | GLBFAFA.tmp | C:\Users\admin\AppData\Local\Temp\GLCFBD5.tmp | executable | |
MD5:46F6AE8FC1D9D46739B8A0672D0F6314 | SHA256:0551132BEBED0A5FF030CD7B5E5E19DA307EDFD2CAEE46F7CF408925ED51458B | |||
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\SQLPreview.dll | executable | |
MD5:9DE0F2896CD20A48658C9F6EEA798BBE | SHA256:CA00BD0874B27C99F9089AED27F709DD2CAAB8505353DAA0F4ABC869E6FB343A | |||
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\~GLH0001.TMP | executable | |
MD5:483C9E7E370B301A8AEC02480E343618 | SHA256:F0042B2321C7CF73ABD333B6DDA322E5DF21482305298C208EF68CED8866E0EA | |||
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\~GLH0003.TMP | executable | |
MD5:23BB1729D2903F6CD6746592B27469E2 | SHA256:539023D669EFA03D34424C9A6AE890E243B91D866327F7551E4C4539BD45CECE | |||
| 2016 | GLBFAFA.tmp | C:\PROGRA~1\DSR\temp.000 | executable | |
MD5:23BB1729D2903F6CD6746592B27469E2 | SHA256:539023D669EFA03D34424C9A6AE890E243B91D866327F7551E4C4539BD45CECE | |||
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\~GLH0004.TMP | executable | |
MD5:23BB1729D2903F6CD6746592B27469E2 | SHA256:539023D669EFA03D34424C9A6AE890E243B91D866327F7551E4C4539BD45CECE | |||
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\Survey.exe | executable | |
MD5:23BB1729D2903F6CD6746592B27469E2 | SHA256:539023D669EFA03D34424C9A6AE890E243B91D866327F7551E4C4539BD45CECE | |||
| 2016 | GLBFAFA.tmp | C:\Users\admin\AppData\Local\Temp\GLJFBE6.tmp | executable | |
MD5:EF6ABA90B8A30869CF0CC9978BE6BF63 | SHA256:8D172BC2473F04DAC1AE0ED3F6BEC87B7FE1E0CD05DF2B2ADD528C7175E31185 | |||
| 2016 | GLBFAFA.tmp | C:\Program Files\DSR\DSR.ini | text | |
MD5:B553B8BA8B29F1FF08B1728E23D5B575 | SHA256:E223063DC2342EB6562F249C4590322F638A9AC818584BA1308569131068AC42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |