| File name: | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe |
| Full analysis: | https://app.any.run/tasks/82747625-fb07-4693-971a-d2674f3c23f5 |
| Verdict: | Malicious activity |
| Analysis date: | July 26, 2025, 07:57:28 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | 0799756F104A70CB6CE0CFC422DE25DB |
| SHA1: | CCEC79B6300F8E86C3BEFF86BAC01362F71E7715 |
| SHA256: | D2049157980B7EE0A54948D4DEF4AB62303CA51CADAADA06FB51C583ECBCE1A2 |
| SSDEEP: | 98304:f0S48XA1HN4rI1yz6ywKhnp8TsDFwccqVdUor0yR53IMxcBmC6S4Srw0TjcKrtJP:zsY2ubEKZE2p73+nSJ+ |
MALICIOUS
GENERIC has been found (auto)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
Bypass execution policy to execute commands
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2704)
Run PowerShell with an invisible window
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
SUSPICIOUS
Executable content was dropped or overwritten
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- powershell.exe (PID: 1980)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
- powershell.exe (PID: 828)
Malware-specific behavior (creating "System.dll" in Temp)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
The process executes Powershell scripts
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2704)
Starts CMD.EXE for commands execution
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Executes as Windows Service
- tor.exe (PID: 5460)
Connects to unusual port
- tor.exe (PID: 5460)
There is functionality for taking screenshot (YARA)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 5368)
- DismHost.exe (PID: 5348)
Process drops legitimate windows executable
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
The process creates files with name similar to system file names
- powershell.exe (PID: 1980)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
- powershell.exe (PID: 828)
Process drops python dynamic module
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2980)
- cmd.exe (PID: 2704)
Creates a software uninstall entry
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
INFO
Checks supported languages
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- tor.exe (PID: 3572)
- tor.exe (PID: 5460)
- ssh-keygen.exe (PID: 4884)
- DismHost.exe (PID: 5368)
- ArmyPlus.exe (PID: 3148)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
- tor.exe (PID: 5476)
- ssh-keygen.exe (PID: 6892)
- DismHost.exe (PID: 5348)
- ArmyPlus.exe (PID: 3288)
The sample compiled with english language support
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Creates files in the program directory
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- powershell.exe (PID: 1980)
- tor.exe (PID: 5460)
- ssh-keygen.exe (PID: 4884)
- powershell.exe (PID: 828)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Reads the machine GUID from the registry
- tor.exe (PID: 5460)
- ssh-keygen.exe (PID: 4884)
- tor.exe (PID: 3572)
- ArmyPlus.exe (PID: 3148)
- tor.exe (PID: 5476)
- ssh-keygen.exe (PID: 6892)
- ArmyPlus.exe (PID: 3288)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
Reads the computer name
- tor.exe (PID: 3572)
- ssh-keygen.exe (PID: 4884)
- DismHost.exe (PID: 5368)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
- tor.exe (PID: 5476)
- tor.exe (PID: 5460)
- DismHost.exe (PID: 5348)
- ArmyPlus.exe (PID: 3288)
- ArmyPlus.exe (PID: 3148)
- ssh-keygen.exe (PID: 6892)
Gets data length (POWERSHELL)
- powershell.exe (PID: 1980)
- powershell.exe (PID: 828)
The executable file from the user directory is run by the Powershell process
- DismHost.exe (PID: 5368)
- DismHost.exe (PID: 5348)
Reads Environment values
- DismHost.exe (PID: 5368)
- DismHost.exe (PID: 5348)
Creates files or folders in the user directory
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
Manual execution by a user
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 3836)
Create files in a temporary directory
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6656)
- d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe (PID: 6688)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 21:57:46+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 27136 |
| InitializedDataSize: | 186880 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x352d |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
160
Monitored processes
22
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | powershell -windowstyle hidden -ExecutionPolicy Bypass .\init.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1980 | powershell -windowstyle hidden -ExecutionPolicy Bypass .\init.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2096 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2704 | cmd /c start /min powershell -windowstyle hidden -ExecutionPolicy Bypass .\init.ps1 | C:\Windows\System32\cmd.exe | — | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2980 | cmd /c start /min powershell -windowstyle hidden -ExecutionPolicy Bypass .\init.ps1 | C:\Windows\System32\cmd.exe | — | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
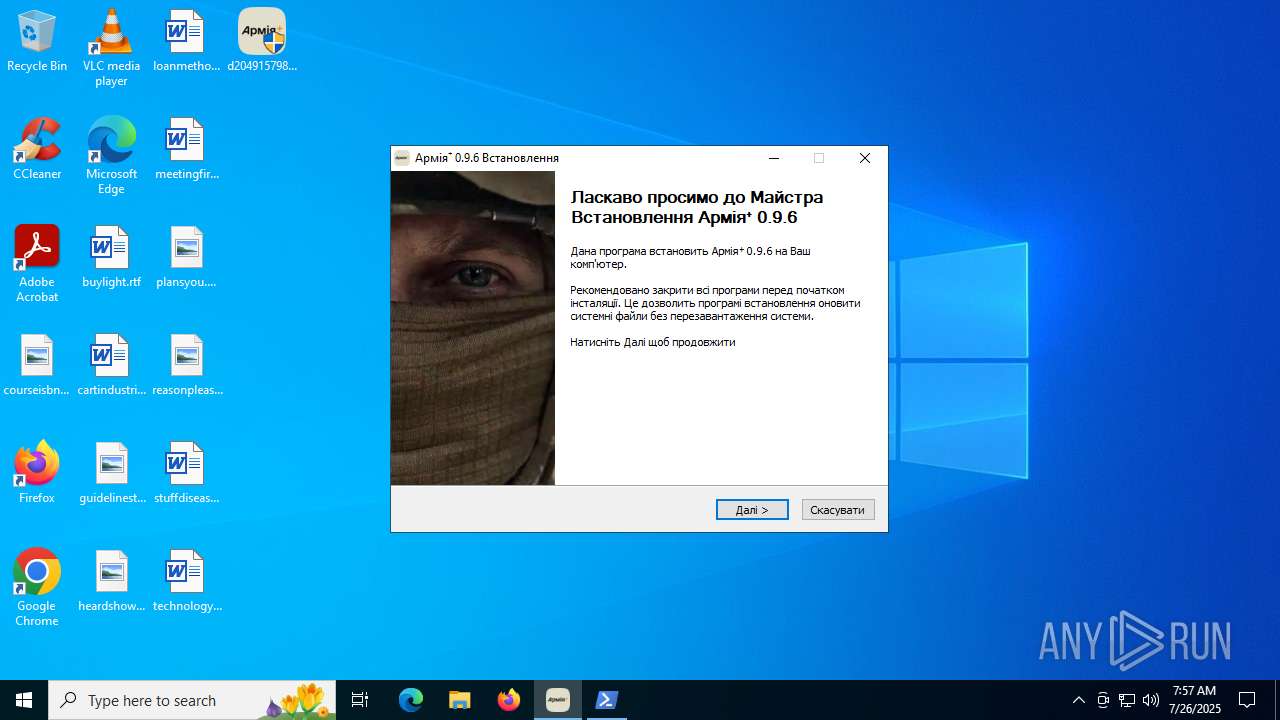
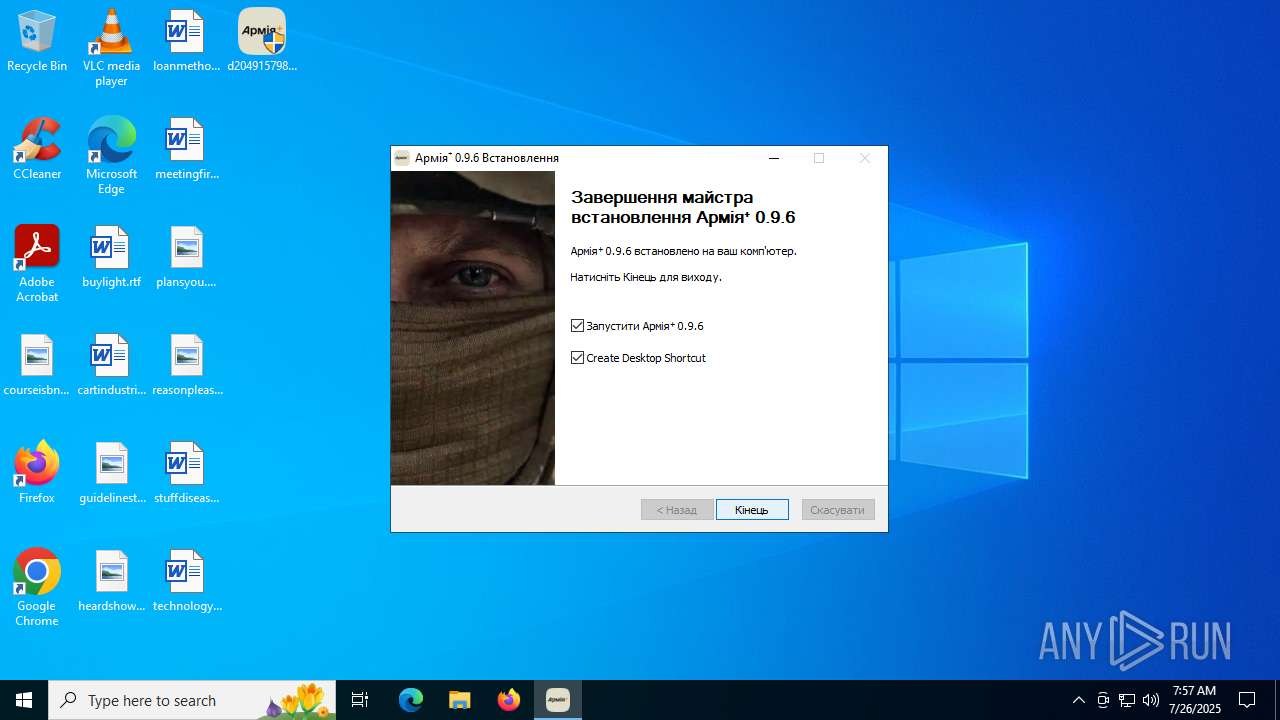
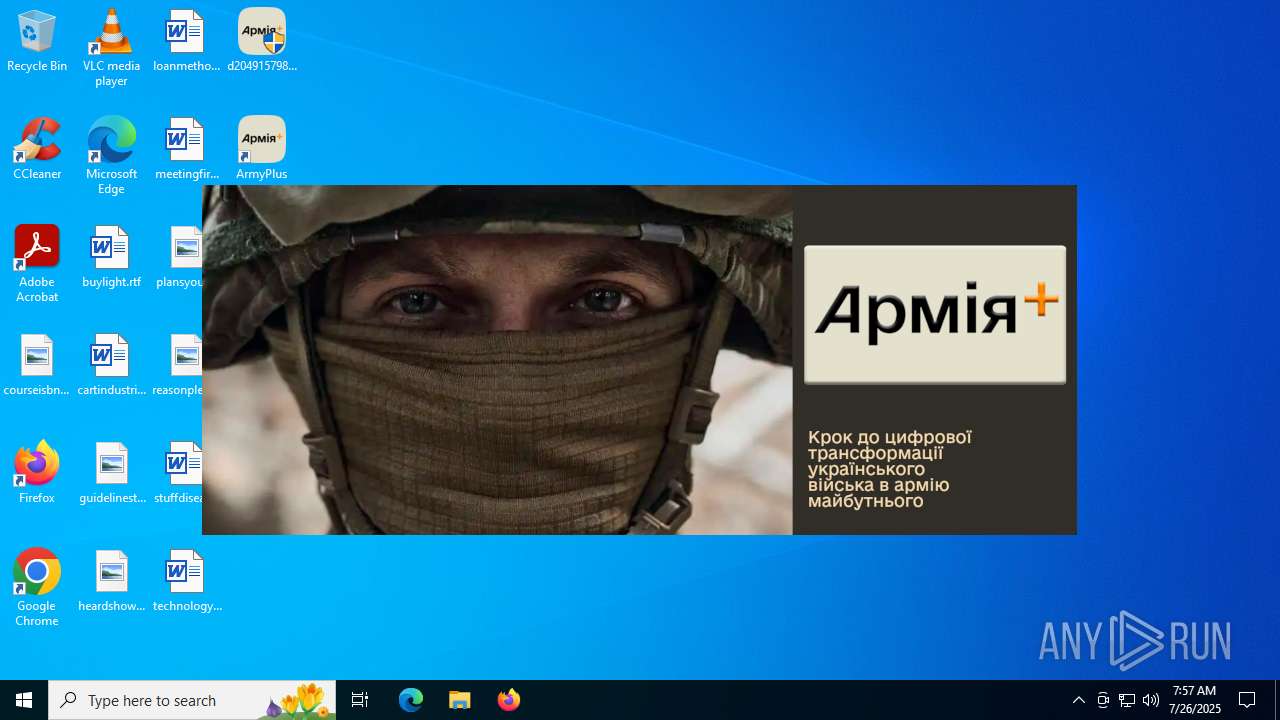
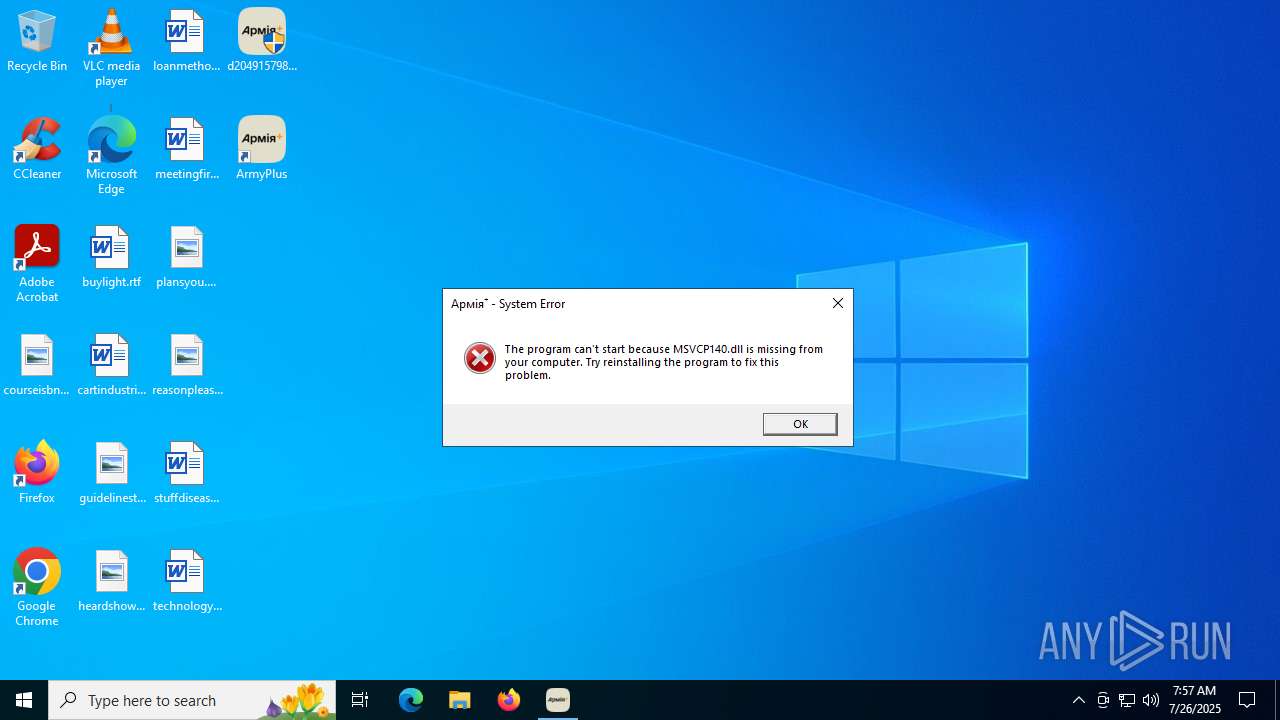
| 3148 | "C:\Program Files (x86)\ArmyPlus\ArmyPlus.exe" | C:\Program Files (x86)\ArmyPlus\ArmyPlus.exe | — | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: ArmyPlus Exit code: 0 Version: 0.9.6.0 Modules
| |||||||||||||||
| 3288 | "C:\Program Files (x86)\ArmyPlus\ArmyPlus.exe" | C:\Program Files (x86)\ArmyPlus\ArmyPlus.exe | — | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | |||||||||||
User: admin Integrity Level: HIGH Description: ArmyPlus Version: 0.9.6.0 Modules
| |||||||||||||||
| 3572 | "C:\ProgramData\OneDriveData\Tor\tor.exe" --service install -options -f C:\ProgramData\OneDriveData\Data\Tor\conf | C:\ProgramData\OneDriveData\Tor\tor.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
16 733
Read events
16 687
Write events
41
Delete events
5
Modification events
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqTime |
Value: 0 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqCount |
Value: 0 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | PoqTime |
Value: 0 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | PoqCount |
Value: 0 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | RptTime |
Value: 0 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | RptCount |
Value: 0 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31194626 | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2025/7/26:7:57:46.631 10.0.19041.3989 (WinBuild.160101.0800) | |||
| (PID) Process: | (1508) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingRequired |
Value: | |||
Executable files
156
Suspicious files
18
Text files
40
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1980 | powershell.exe | C:\ProgramData\OneDriveData\Data\Tor\geoip6 | — | |
MD5:— | SHA256:— | |||
| 6656 | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | C:\Users\admin\AppData\Local\Temp\nsvCD10.tmp\InstallOptions.dll | executable | |
MD5:ECE25721125D55AA26CDFE019C871476 | SHA256:C7FEF6457989D97FECC0616A69947927DA9D8C493F7905DC8475C748F044F3CF | |||
| 6656 | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | C:\Program Files (x86)\ArmyPlus\init.ps1 | text | |
MD5:52853B39922251A4166A5B032E577E7A | SHA256:86039BC8B1A6BB823F5CBF27D1A4A3B319B83D242F09FFCD96F38BBDBBAAA78F | |||
| 6656 | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | C:\Program Files (x86)\ArmyPlus\guid.txt | text | |
MD5:ED0C7C1925AC23BD8B4D09E77AABB0EE | SHA256:8BA4C3EDE1ED05A3AD7075FEE503215648EC078A13523492E2E91A59FA40C8DA | |||
| 1980 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF18cf32.TMP | binary | |
MD5:00A03B286E6E0EBFF8D9C492365D5EC2 | SHA256:4DBFC417D053BA6867308671F1C61F4DCAFC61F058D4044DB532DA6D3BDE3615 | |||
| 1980 | powershell.exe | C:\ProgramData\OneDriveData\Tor\libevent_core-2-1-7.dll | executable | |
MD5:F1BCC8BD3200845993211EB807F33E56 | SHA256:7CD199BBF3BFE19182C5ECA3A080A7E93CEC0D30CBD872A305C92BC9282A7399 | |||
| 1980 | powershell.exe | C:\ProgramData\OneDriveData\Tor\libevent_extra-2-1-7.dll | executable | |
MD5:F963552B851FDE3834405BB98BAE0C36 | SHA256:36C66CFC6E9663BDD2CDC54A1253A8C26C837CA0BD8C52769B5820641C18D4C3 | |||
| 6656 | d2049157980b7ee0a54948d4def4ab62303ca51cadaada06fb51c583ecbce1a2.exe | C:\Program Files (x86)\ArmyPlus\tor-win32-0.4.7.11.zip | compressed | |
MD5:53E566693EDAD254C72EBDE361F0E6B0 | SHA256:C9494749F02493BF3D53C849F9672FDA5426F90B1C34D81237A0BC24C0C6993A | |||
| 1980 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QSCULSLNMWFH7G0MWQ64.temp | binary | |
MD5:3F1418519E3C693843E2A141F87884C8 | SHA256:BFECF83293AE0621E3182395E6481D3164C65143AA0FA2040620B5D572CEF749 | |||
| 1980 | powershell.exe | C:\ProgramData\OneDriveData\Tor\libssl-1_1.dll | executable | |
MD5:EEFDECBAAD203610A047F59E3B434557 | SHA256:E84F4EEF9CF94E2B261F037B64234EA0D4CE1E6CF5873E20A210A9FD191304C6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
31
DNS requests
13
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6540 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.13:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4460 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5460 | tor.exe | 167.71.33.11:9001 | — | DIGITALOCEAN-ASN | DE | unknown |
6540 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6540 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5460 | tor.exe | 202.165.228.225:9001 | — | Multinet Broadband | PK | malicious |
5460 | tor.exe | 95.211.184.218:443 | — | LeaseWeb Netherlands B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5460 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 153 |
5460 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 277 |
5460 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 413 |
Process | Message |
|---|---|
powershell.exe | PID=1980 TID=6788 Enter DismInitializeInternal - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 Input parameters: LogLevel: 2, LogFilePath: C:\WINDOWS\Logs\DISM\dism.log, ScratchDirectory: (null) - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 DismApi.dll: Parent process command line: powershell -windowstyle hidden -ExecutionPolicy Bypass .\init.ps1 - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 DismApi.dll: <----- Starting DismApi.dll session -----> - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 DismApi.dll: Host machine information: OS Version=10.0.19045, Running architecture=amd64, Number of processors=4 - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 DismApi.dll: API Version 10.0.19041.3758 - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 DismApi.dll: - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 DismApi.dll: - DismInitializeInternal
|
powershell.exe | PID=1980 TID=6788 Lookup in table by path failed for: DummyPath-2BA51B78-C7F7-4910-B99D-BB7345357CDC - CTransactionalImageTable::LookupImagePath
|
powershell.exe | PID=1980 TID=6788 Initialized GlobalConfig - DismInitializeInternal
|