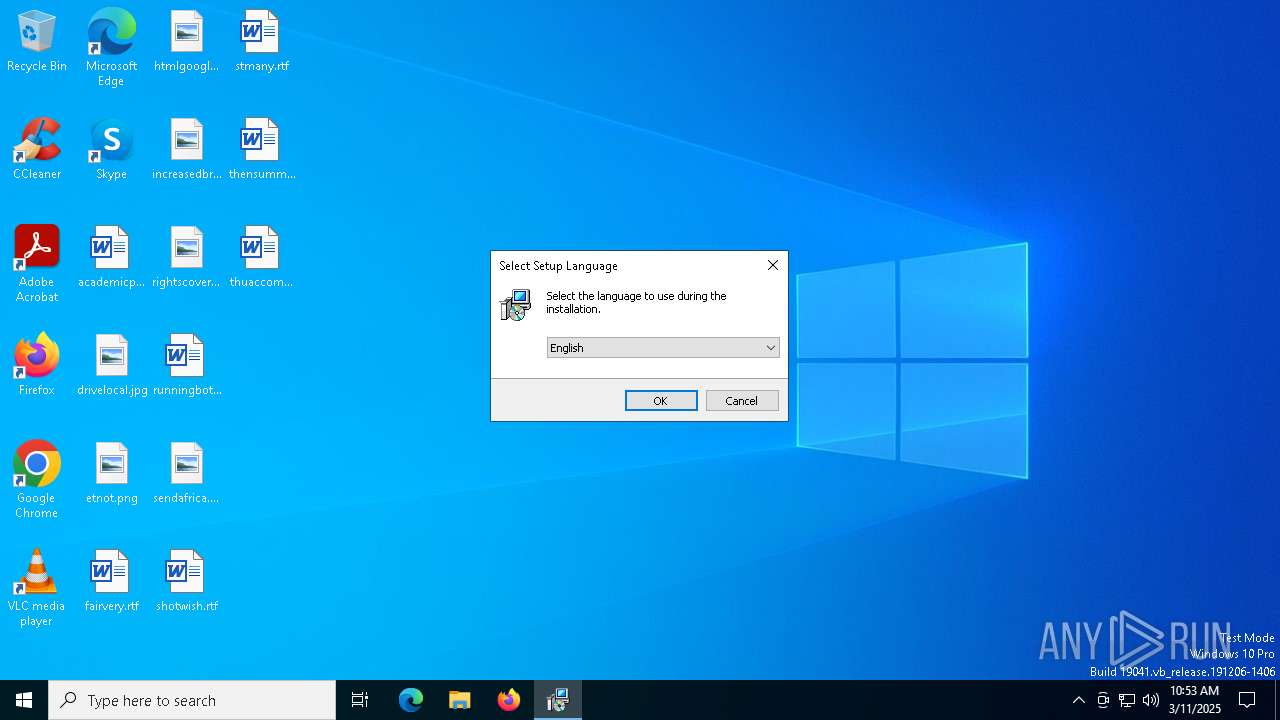
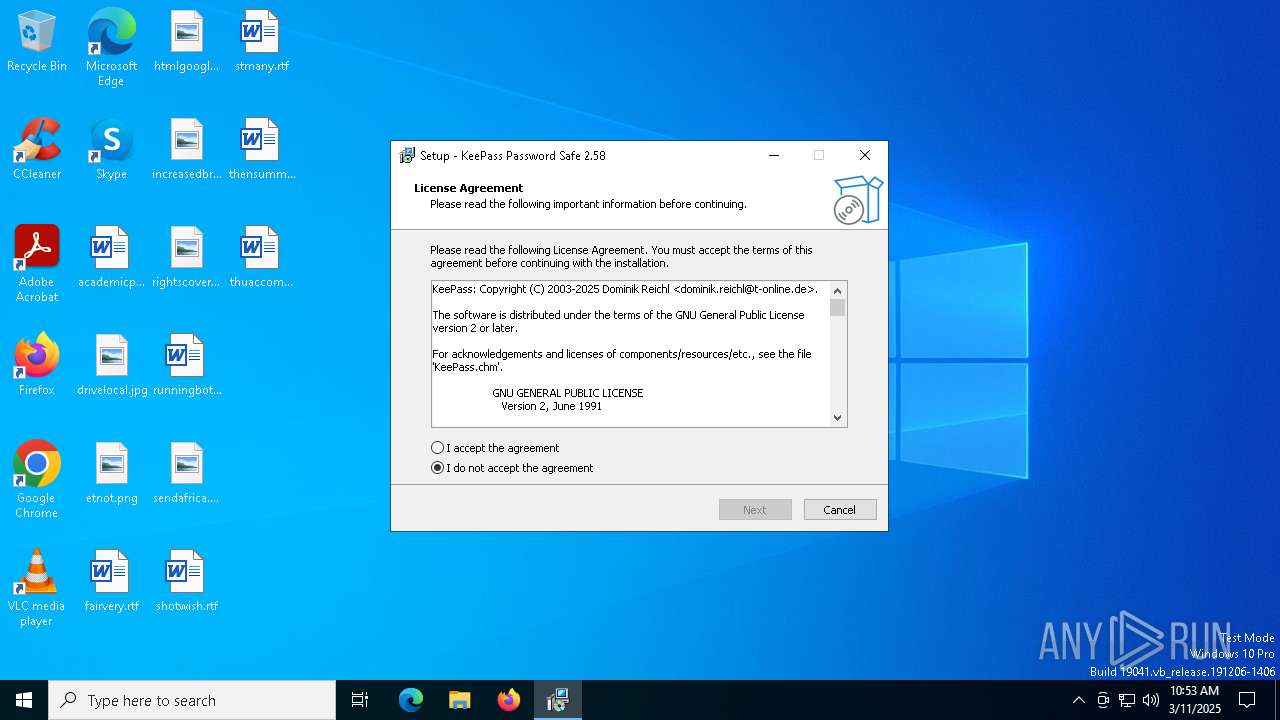
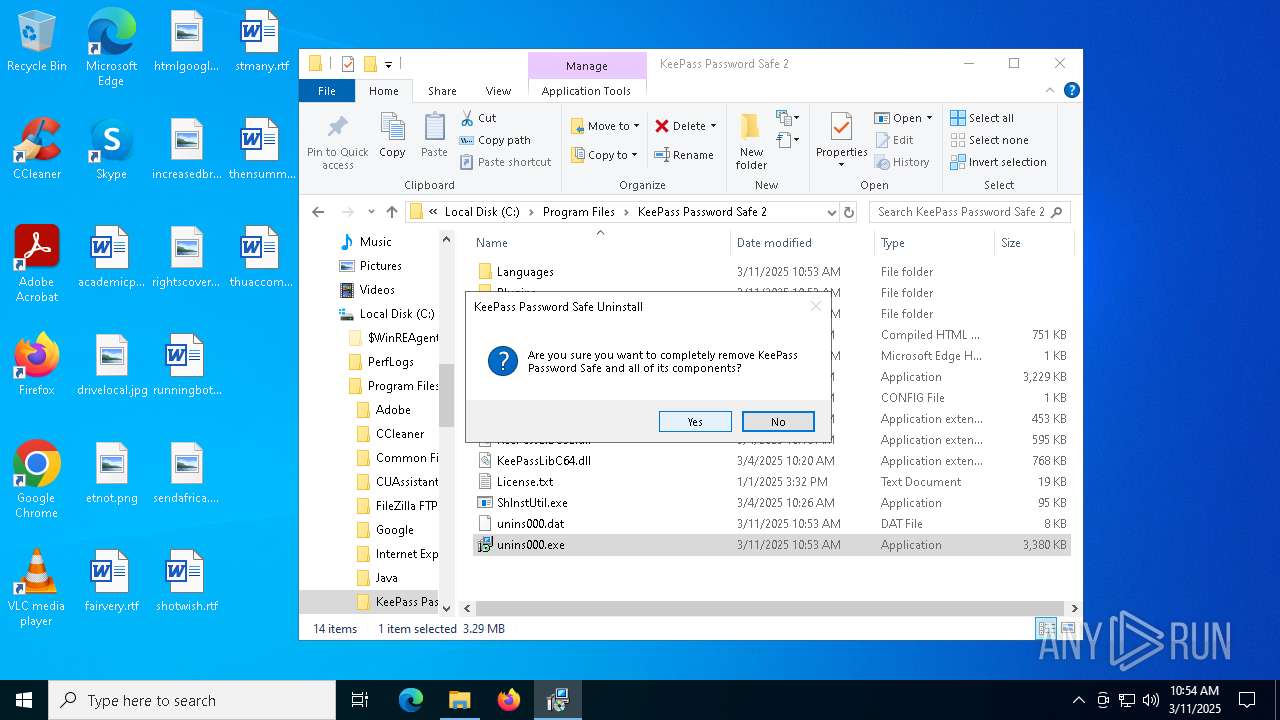
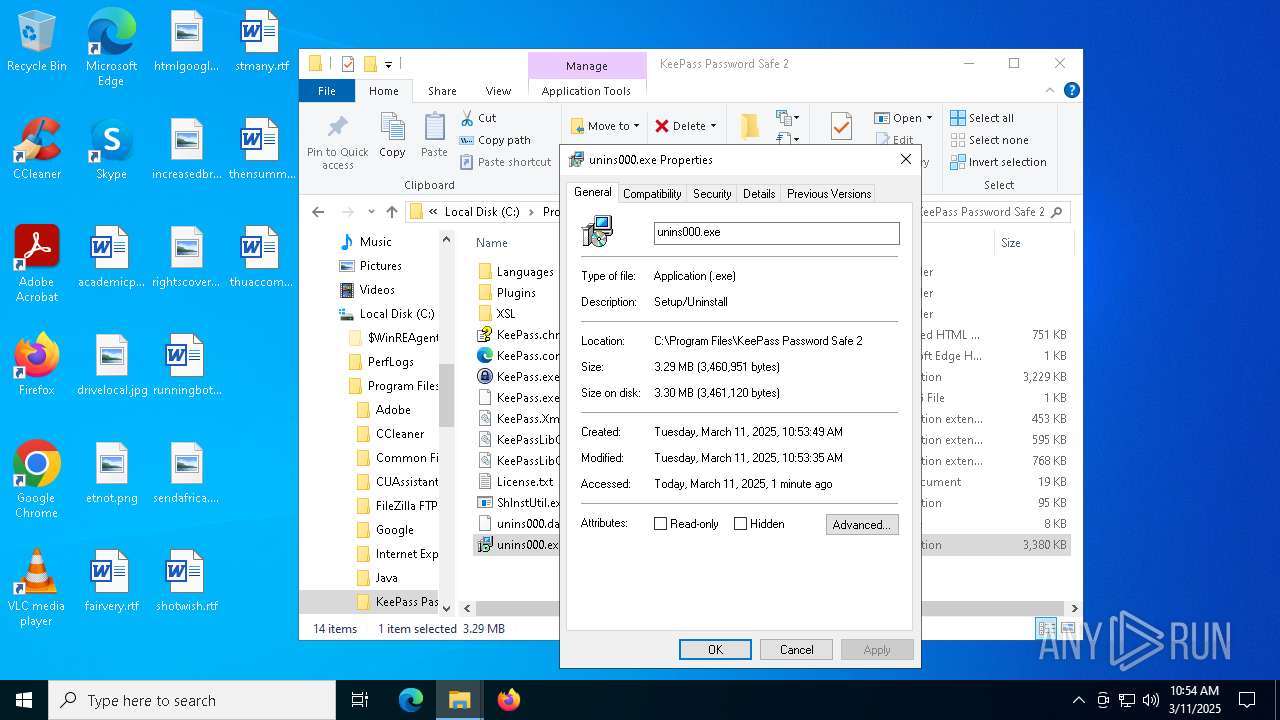
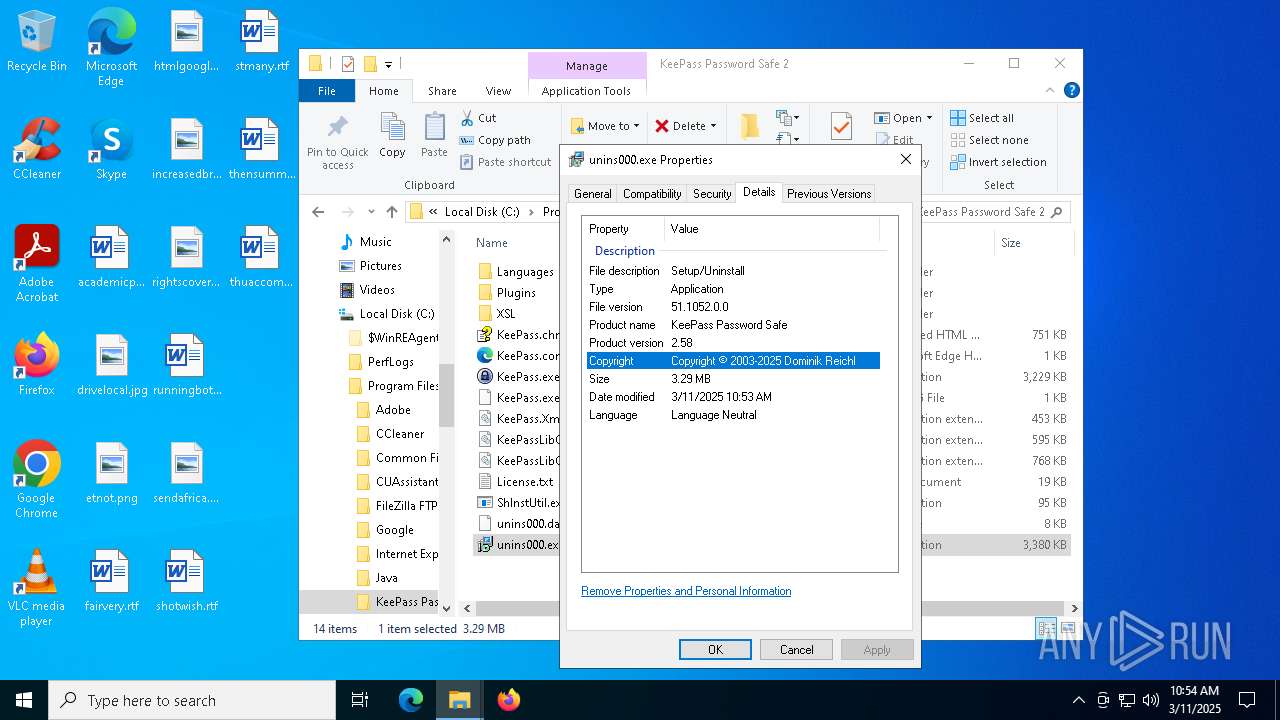
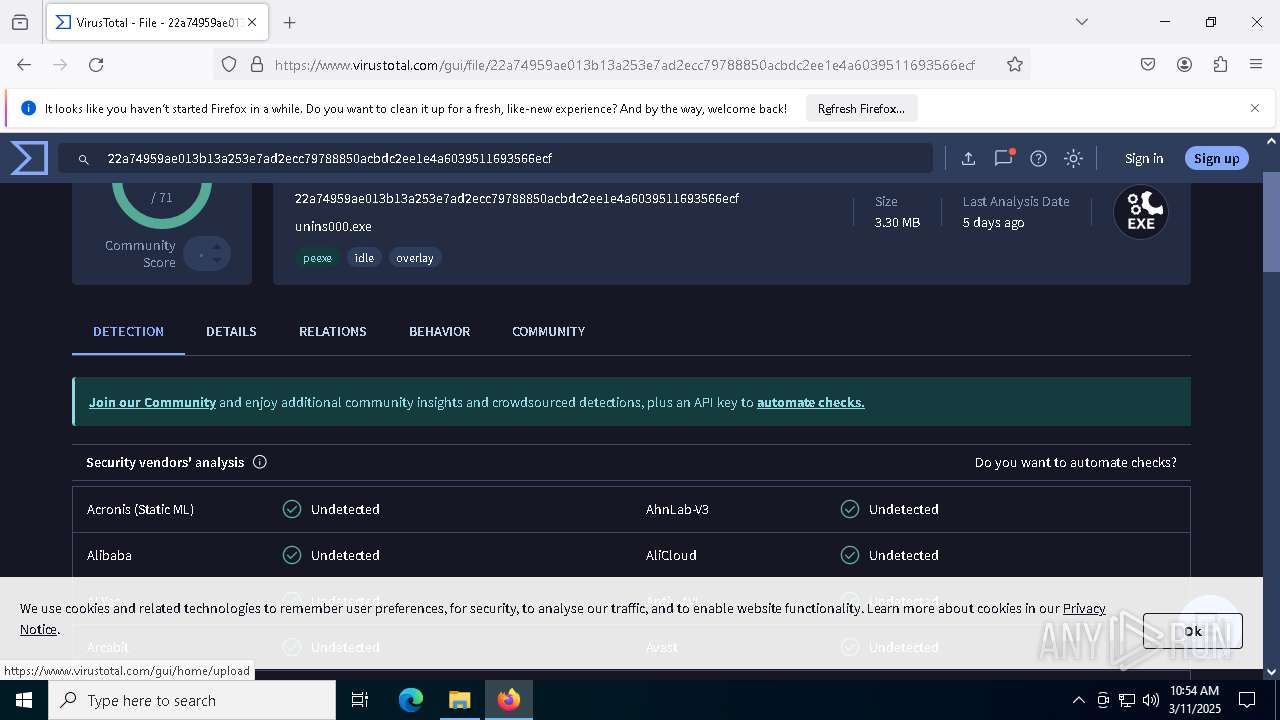
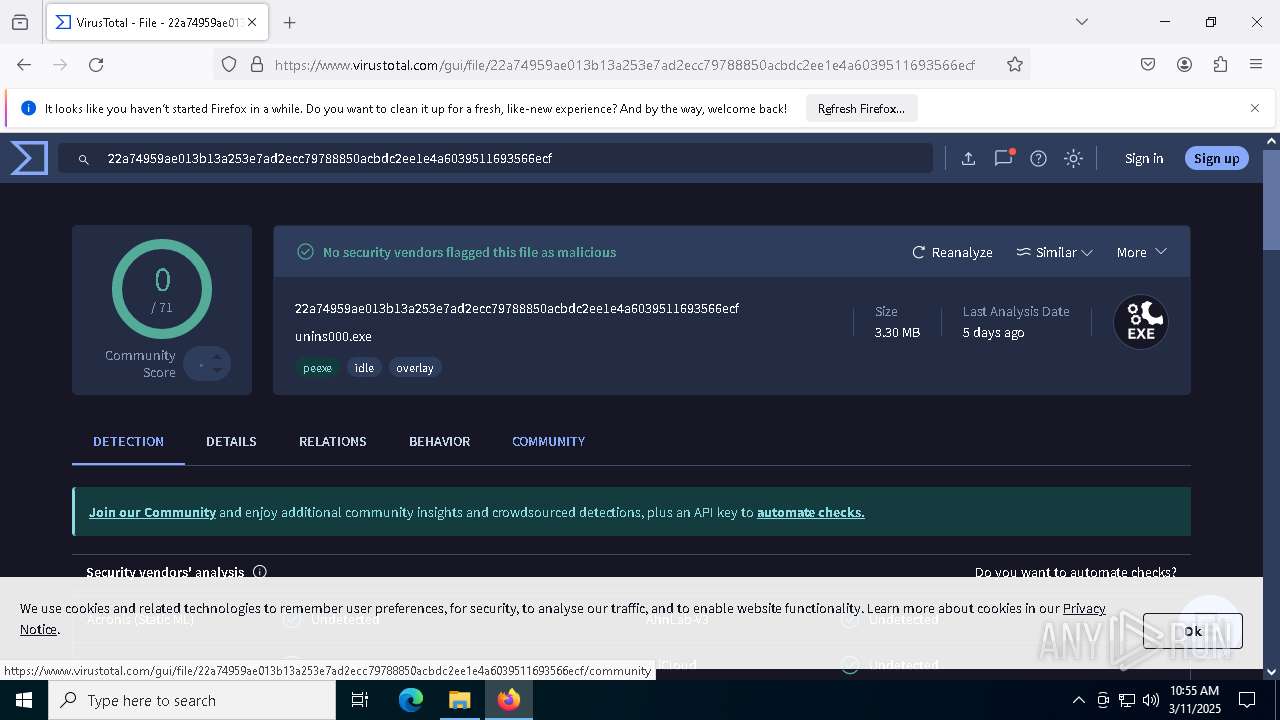
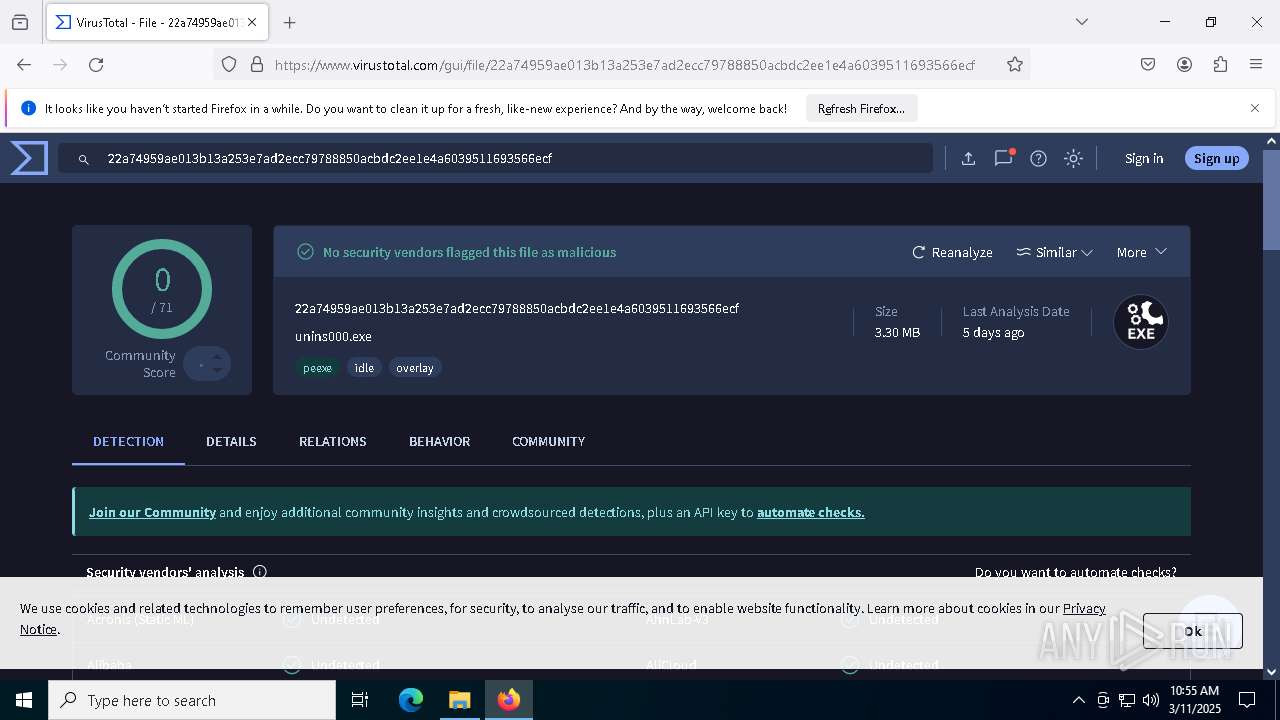
| File name: | KeePass-2.58-Setup.exe |
| Full analysis: | https://app.any.run/tasks/91595944-6e23-4fc4-b49c-fbfadc5160af |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2025, 10:53:28 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | 9D2EA8123352CD9549DD9872037DAAF8 |
| SHA1: | 4FFA6357002272262076C77E39CABFF04227721F |
| SHA256: | D1FB8A8E9837FD91033F930B52FA2F2B0A83CD2A49FBC00BA98153911B0A7715 |
| SSDEEP: | 98304:a6GavikObQjvpGGr13cA26yGM8S8ndKcx1qN/RbmAwc4NtPROOZartjRwAampj6x:7YJVg |
MALICIOUS
Changes the autorun value in the registry
- ShInstUtil.exe (PID: 7356)
SUSPICIOUS
Executable content was dropped or overwritten
- KeePass-2.58-Setup.exe (PID: 7424)
- KeePass-2.58-Setup.exe (PID: 7580)
- KeePass-2.58-Setup.tmp (PID: 7604)
- mscorsvw.exe (PID: 672)
- mscorsvw.exe (PID: 5008)
- mscorsvw.exe (PID: 8112)
- mscorsvw.exe (PID: 4620)
- mscorsvw.exe (PID: 680)
- mscorsvw.exe (PID: 7392)
- _unins.tmp (PID: 5216)
- unins000.exe (PID: 6476)
- _unins.tmp (PID: 6268)
- unins000.exe (PID: 7840)
Reads security settings of Internet Explorer
- KeePass-2.58-Setup.tmp (PID: 7448)
- ShInstUtil.exe (PID: 900)
- unins000.exe (PID: 2284)
- ShInstUtil.exe (PID: 3016)
Reads the Windows owner or organization settings
- KeePass-2.58-Setup.tmp (PID: 7604)
Process drops legitimate windows executable
- mscorsvw.exe (PID: 672)
- mscorsvw.exe (PID: 4620)
- mscorsvw.exe (PID: 7392)
- mscorsvw.exe (PID: 8112)
Starts itself from another location
- unins000.exe (PID: 6476)
- unins000.exe (PID: 7840)
Starts application with an unusual extension
- unins000.exe (PID: 6476)
- unins000.exe (PID: 7840)
Application launched itself
- unins000.exe (PID: 2284)
- unins000.exe (PID: 8188)
INFO
Checks supported languages
- KeePass-2.58-Setup.exe (PID: 7424)
- KeePass-2.58-Setup.tmp (PID: 7448)
- KeePass-2.58-Setup.exe (PID: 7580)
- KeePass-2.58-Setup.tmp (PID: 7604)
- ShInstUtil.exe (PID: 6036)
- ShInstUtil.exe (PID: 900)
- ngen.exe (PID: 6564)
- ngen.exe (PID: 4164)
- mscorsvw.exe (PID: 4408)
- mscorsvw.exe (PID: 680)
- ShInstUtil.exe (PID: 7356)
- mscorsvw.exe (PID: 4620)
- mscorsvw.exe (PID: 672)
- mscorsvw.exe (PID: 5008)
- mscorsvw.exe (PID: 7392)
- KeePass.exe (PID: 5360)
- mscorsvw.exe (PID: 8112)
- unins000.exe (PID: 2284)
- unins000.exe (PID: 7840)
- unins000.exe (PID: 8188)
- _unins.tmp (PID: 6268)
- ShInstUtil.exe (PID: 3016)
- mscorsvw.exe (PID: 1764)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 7980)
- ngen.exe (PID: 3028)
Create files in a temporary directory
- KeePass-2.58-Setup.exe (PID: 7424)
- KeePass-2.58-Setup.exe (PID: 7580)
- KeePass-2.58-Setup.tmp (PID: 7604)
- _unins.tmp (PID: 5216)
- unins000.exe (PID: 6476)
- unins000.exe (PID: 7840)
- _unins.tmp (PID: 6268)
Reads the computer name
- KeePass-2.58-Setup.tmp (PID: 7448)
- KeePass-2.58-Setup.exe (PID: 7580)
- KeePass-2.58-Setup.tmp (PID: 7604)
- ShInstUtil.exe (PID: 900)
- ngen.exe (PID: 4164)
- ngen.exe (PID: 6564)
- mscorsvw.exe (PID: 4408)
- mscorsvw.exe (PID: 680)
- mscorsvw.exe (PID: 4620)
- mscorsvw.exe (PID: 7392)
- mscorsvw.exe (PID: 5008)
- mscorsvw.exe (PID: 672)
- KeePass.exe (PID: 5360)
- mscorsvw.exe (PID: 8112)
- unins000.exe (PID: 2284)
- mscorsvw.exe (PID: 2088)
- mscorsvw.exe (PID: 1764)
- ngen.exe (PID: 3028)
- mscorsvw.exe (PID: 7980)
Process checks computer location settings
- KeePass-2.58-Setup.tmp (PID: 7448)
- ShInstUtil.exe (PID: 900)
- _unins.tmp (PID: 6268)
- ShInstUtil.exe (PID: 3016)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 516)
- KeePass.exe (PID: 5360)
Compiled with Borland Delphi (YARA)
- KeePass-2.58-Setup.tmp (PID: 7448)
- KeePass-2.58-Setup.exe (PID: 7424)
- KeePass-2.58-Setup.exe (PID: 7580)
- KeePass-2.58-Setup.tmp (PID: 7604)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 6964)
- BackgroundTransferHost.exe (PID: 7952)
- BackgroundTransferHost.exe (PID: 5592)
- BackgroundTransferHost.exe (PID: 516)
- BackgroundTransferHost.exe (PID: 3096)
Detects InnoSetup installer (YARA)
- KeePass-2.58-Setup.exe (PID: 7424)
- KeePass-2.58-Setup.tmp (PID: 7448)
- KeePass-2.58-Setup.exe (PID: 7580)
- KeePass-2.58-Setup.tmp (PID: 7604)
The sample compiled with english language support
- KeePass-2.58-Setup.tmp (PID: 7604)
- mscorsvw.exe (PID: 672)
- mscorsvw.exe (PID: 8112)
- mscorsvw.exe (PID: 4620)
- mscorsvw.exe (PID: 7392)
Creates files in the program directory
- KeePass-2.58-Setup.tmp (PID: 7604)
The sample compiled with german language support
- KeePass-2.58-Setup.tmp (PID: 7604)
Creates a software uninstall entry
- KeePass-2.58-Setup.tmp (PID: 7604)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 516)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 516)
NGen native .NET image generation
- ngen.exe (PID: 4164)
- ngen.exe (PID: 6564)
- ngen.exe (PID: 3028)
Reads the machine GUID from the registry
- mscorsvw.exe (PID: 4408)
- mscorsvw.exe (PID: 680)
- mscorsvw.exe (PID: 4620)
- mscorsvw.exe (PID: 672)
- mscorsvw.exe (PID: 5008)
- KeePass.exe (PID: 5360)
Manual execution by a user
- unins000.exe (PID: 2284)
- firefox.exe (PID: 7824)
- unins000.exe (PID: 8188)
Application launched itself
- firefox.exe (PID: 7388)
- firefox.exe (PID: 7824)
Executable content was dropped or overwritten
- firefox.exe (PID: 7388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:12 05:53:16+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 684032 |
| InitializedDataSize: | 108544 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa7f98 |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.58.0.0 |
| ProductVersionNumber: | 2.58.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Dominik Reichl |
| FileDescription: | KeePass Password Safe 2.58 Setup |
| FileVersion: | 2.58.0.0 |
| LegalCopyright: | Copyright © 2003-2025 Dominik Reichl |
| OriginalFileName: | |
| ProductName: | KeePass Password Safe |
| ProductVersion: | 2.58 |
Total processes
202
Monitored processes
58
Malicious processes
2
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 516 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 2b0 -InterruptEvent 0 -NGENProcess 27c -Pipe 2a4 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | ngen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.9093.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 680 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 284 -InterruptEvent 0 -NGENProcess 1f4 -Pipe 2a8 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | ngen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.9093.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 744 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1904 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {87175be6-8755-4e6e-95c2-2baab37d2ef3} 7388 "\\.\pipe\gecko-crash-server-pipe.7388" 23c78dec310 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 900 | "C:\Program Files\KeePass Password Safe 2\ShInstUtil.exe" ngen_install | C:\Program Files\KeePass Password Safe 2\ShInstUtil.exe | — | KeePass-2.58-Setup.tmp | |||||||||||
User: admin Company: Dominik Reichl Integrity Level: HIGH Description: ShInstUtil - KeePass Helper Utility Exit code: 0 Version: 2.58.0.0 Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4364 -childID 2 -isForBrowser -prefsHandle 4356 -prefMapHandle 4352 -prefsLen 36588 -prefMapSize 244583 -jsInitHandle 1512 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {93b0cc4d-5483-4974-80d9-d7193f663b7f} 7388 "\\.\pipe\gecko-crash-server-pipe.7388" 23c7ff64850 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 1764 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 274 -InterruptEvent 0 -NGENProcess 1ec -Pipe 294 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.9093.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 2088 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe -StartupEvent 1ec -InterruptEvent 0 -NGENProcess 1f4 -Pipe 274 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.8.9093.0 built by: NET481REL1LAST_C Modules
| |||||||||||||||
| 2104 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 766
Read events
29 686
Write events
67
Delete events
13
Modification events
| (PID) Process: | (5592) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5592) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5592) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (516) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (516) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (516) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3096) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3096) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3096) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6964) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
33
Suspicious files
219
Text files
63
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\ed476ddb-017c-460c-83f9-59a4308a3edd.down_data | — | |
MD5:— | SHA256:— | |||
| 516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:AFF8BC4EF467C5F51808C28370F9C59A | SHA256:5D6E51CC5AC70D7ED298C2559DF8F583E491644FB562566281DB657FBB1D5E98 | |||
| 7580 | KeePass-2.58-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-N5H5K.tmp\KeePass-2.58-Setup.tmp | executable | |
MD5:01BB812F5DF4484A91643DC6AE0C3FD9 | SHA256:0F006ED48944006F810FFE3704D832C70B6B25BAFFB316DDCBC07F57E43C017E | |||
| 7424 | KeePass-2.58-Setup.exe | C:\Users\admin\AppData\Local\Temp\is-1IE9D.tmp\KeePass-2.58-Setup.tmp | executable | |
MD5:01BB812F5DF4484A91643DC6AE0C3FD9 | SHA256:0F006ED48944006F810FFE3704D832C70B6B25BAFFB316DDCBC07F57E43C017E | |||
| 7604 | KeePass-2.58-Setup.tmp | C:\Program Files\KeePass Password Safe 2\is-5HGAU.tmp | executable | |
MD5:32DB4B7FF735194A4776B07309CF4201 | SHA256:DC5DC13556902811E83CC9A677056CF43FF4E0D6EE1B319CC9EE07925E068A32 | |||
| 7604 | KeePass-2.58-Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-SNU87.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\475ea34f-add3-4423-9e97-4a83aa442dfc.up_meta_secure | binary | |
MD5:F2DB59EE4BD2EBB9CFB680FFB272FDC1 | SHA256:C18861530DF01773F2E9505F1153E1EDF788F596AC71BF9E31349368CBD9F8D8 | |||
| 7604 | KeePass-2.58-Setup.tmp | C:\Program Files\KeePass Password Safe 2\is-8GDKQ.tmp | executable | |
MD5:CE747E44482A1E95543E94E893318293 | SHA256:22A74959AE013B13A253E7AD2ECC79788850ACBDC2EE1E4A6039511693566ECF | |||
| 516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:5E16E74D50899C2ACB576669F07DEE54 | SHA256:9B0954B5A8009228D7253B74A69B0E909169BB741F574934537E32A66517A322 | |||
| 516 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\475ea34f-add3-4423-9e97-4a83aa442dfc.520558a8-4c77-4579-801a-3d7b1420f22c.down_meta | binary | |
MD5:F7F1A40B8DB3990A0938D3D25C7060FC | SHA256:D62F9F749002572A6807A93EC375D414BD3FB81B84AC3623961F789CC2A8678B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
112
DNS requests
153
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
516 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7720 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8024 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7388 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
7388 | firefox.exe | POST | 200 | 184.24.77.62:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7388 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
7388 | firefox.exe | POST | — | 184.24.77.62:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
7388 | firefox.exe | POST | 200 | 172.217.16.131:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 40.126.31.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
7720 | backgroundTaskHost.exe | 20.74.47.205:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7720 | backgroundTaskHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
516 | BackgroundTransferHost.exe | 2.19.122.61:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
516 | BackgroundTransferHost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |