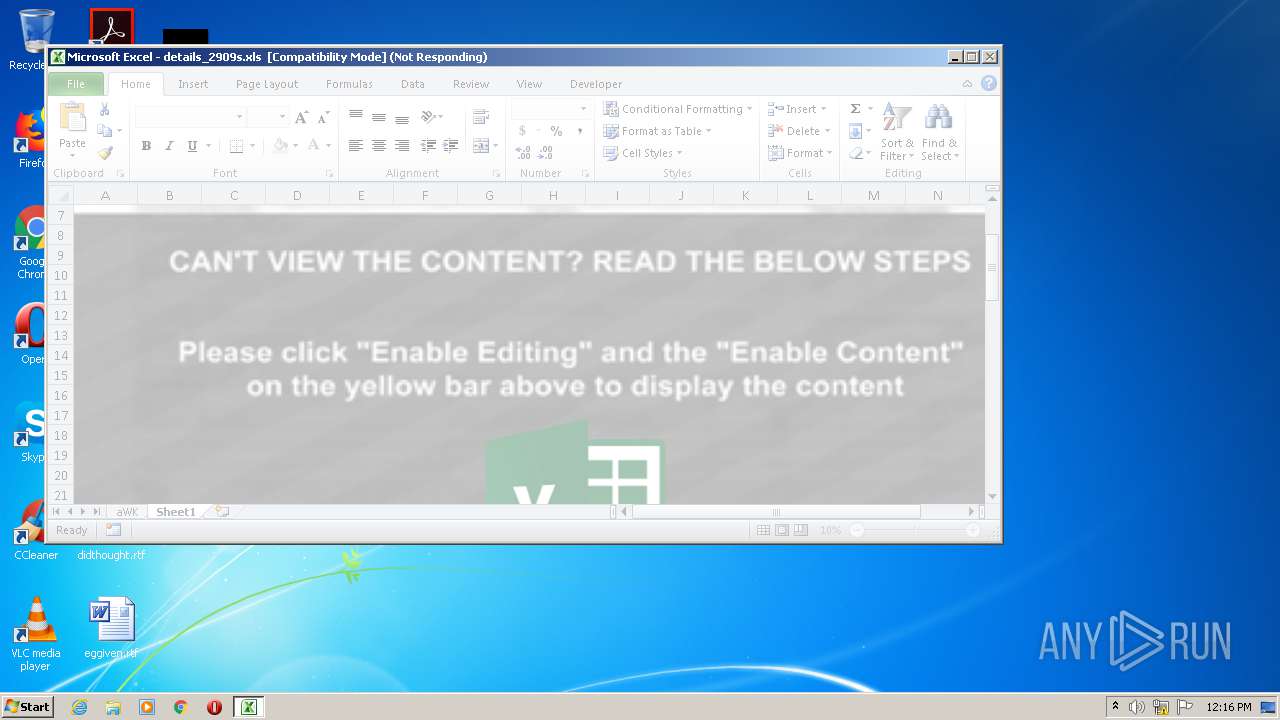
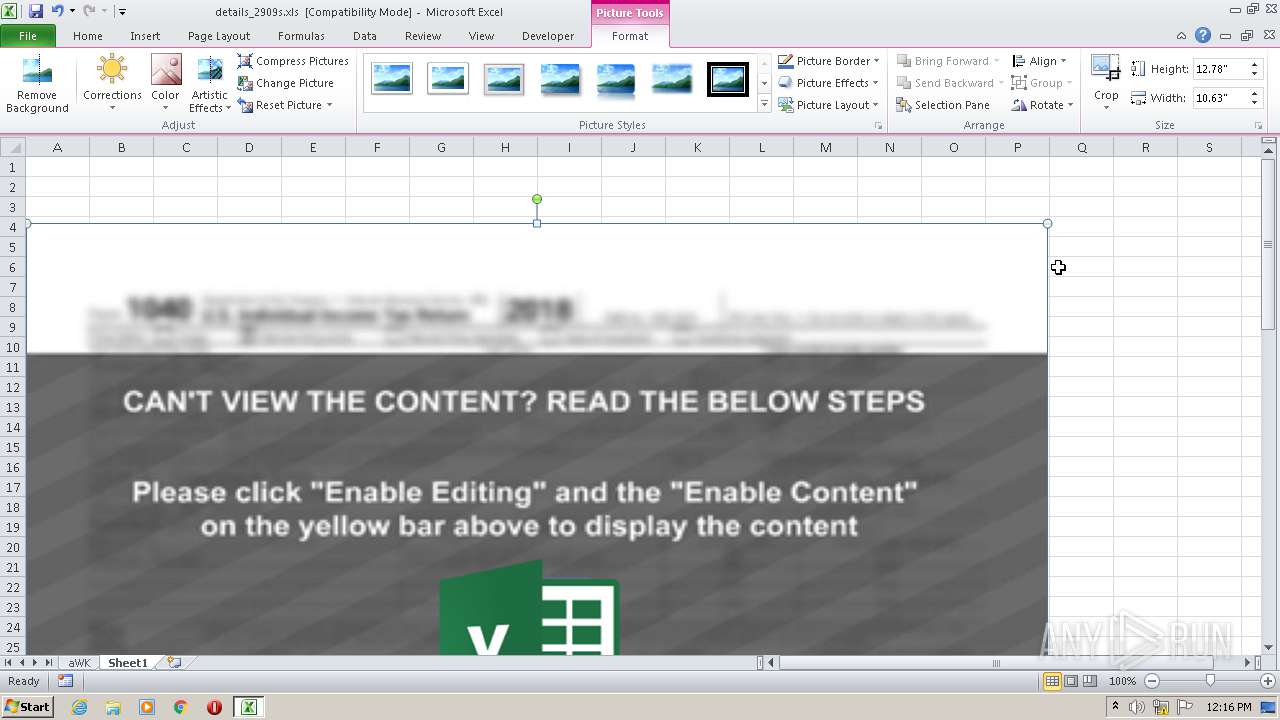
| File name: | details_2909s.xls |
| Full analysis: | https://app.any.run/tasks/ab342a76-8838-4a64-b826-28c1401ec270 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 11:15:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-excel |
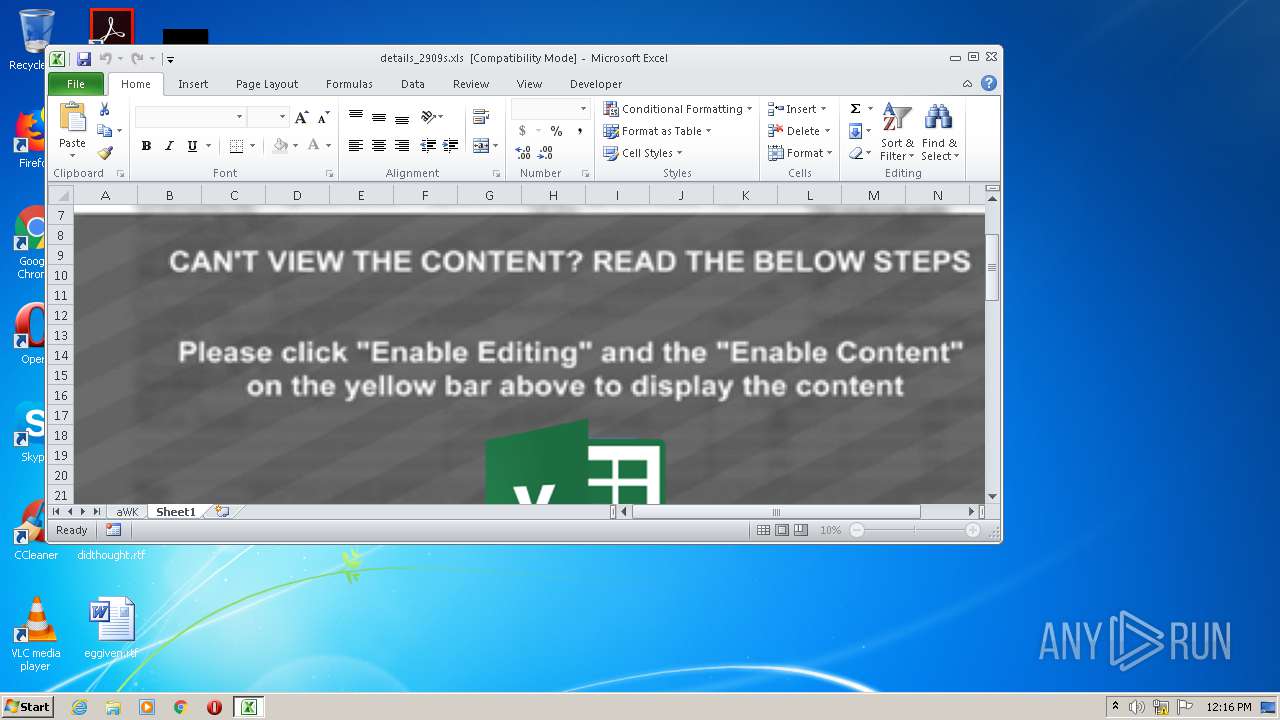
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: fVMakTTGsTpDRxQCGfU, Last Saved By: fckav, Name of Creating Application: Microsoft Excel, Create Time/Date: Mon Sep 14 22:28:14 2020, Last Saved Time/Date: Tue Sep 29 19:07:39 2020, Security: 1 |
| MD5: | EC8FCB4756BC4C0AB2B9484991D5F94B |
| SHA1: | 1204EEDA224C9E301A8F260EE4D9619FC61A54E2 |
| SHA256: | D1FB5680D011C22DDADB72A81E6177708F0A21FC53A5FFE77CE760233E2C4006 |
| SSDEEP: | 6144:P1H8RmO81u+O+J2MT79Sa866Zqcr7pn0vMrHENH/pEaWo:t4mZ1/OQ2ha86grd0vaHEN5 |
MALICIOUS
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 2132)
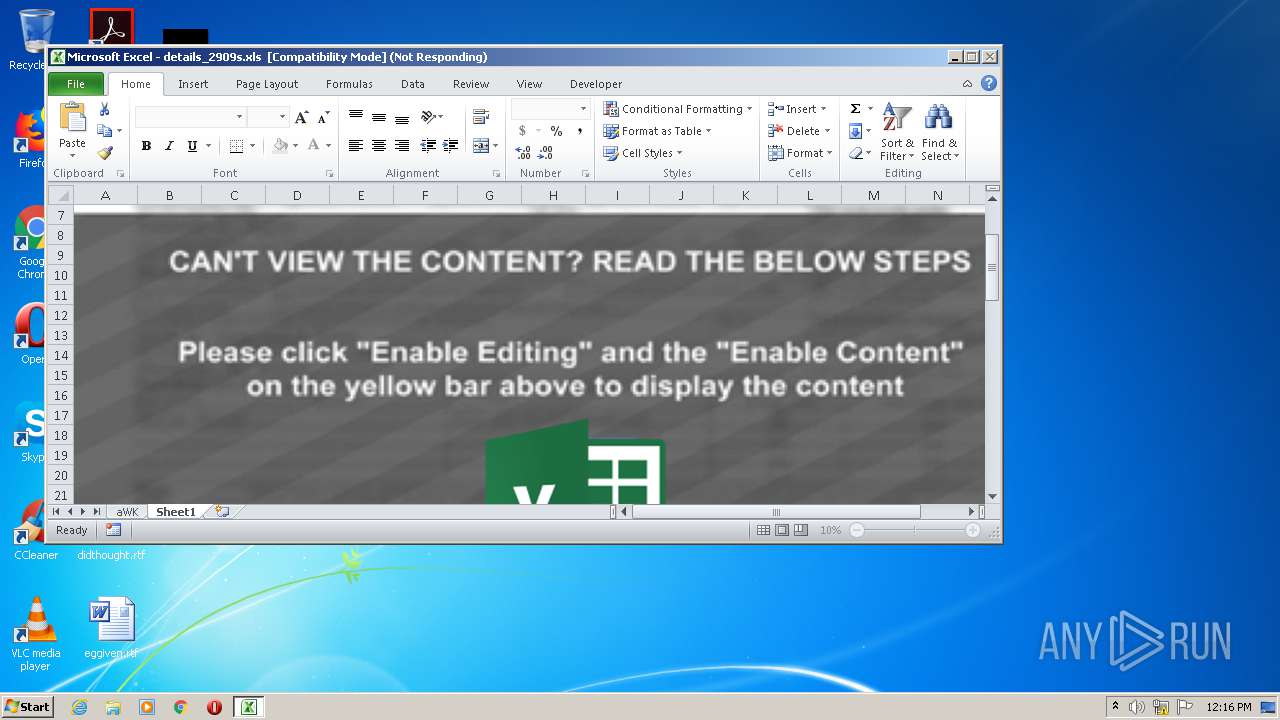
Executable content was dropped or overwritten
- EXCEL.EXE (PID: 2132)
Loads dropped or rewritten executable
- rundll32.exe (PID: 252)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- EXCEL.EXE (PID: 2132)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 2132)
Reads Internet Cache Settings
- EXCEL.EXE (PID: 2132)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xls | | | Microsoft Excel sheet (78.9) |
|---|
EXIF
FlashPix
| Author: | fVMakTTGsTpDRxQCGfU |
|---|---|
| LastModifiedBy: | fckav |
| Software: | Microsoft Excel |
| CreateDate: | 2020:09:14 21:28:14 |
| ModifyDate: | 2020:09:29 18:07:39 |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: |
|
| HeadingPairs: |
|
Total processes
37
Monitored processes
2
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Windows\System32\rundll32.exe" C:\joZSZER\QgkmeET\sMHvbkl.dll,DllRegisterServer | C:\Windows\System32\rundll32.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
635
Read events
572
Write events
52
Delete events
11
Modification events
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | 8? |
Value: 20383F0054080000010000000000000000000000 | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2132) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
2
Suspicious files
4
Text files
0
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVRAC00.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CabF167.tmp | — | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\TarF168.tmp | — | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\FC7F75C304F4CF0B7BB86860AECC9154 | binary | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FC7F75C304F4CF0B7BB86860AECC9154 | der | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | der | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E49827401028F7A0F97B5576C77A26CB_7CE95D8DCA26FE957E7BD7D76F353B08 | binary | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\xls_s_2909.exe1[1].c1 | executable | |
MD5:— | SHA256:— | |||
| 2132 | EXCEL.EXE | C:\joZSZER\QgkmeET\sMHvbkl.dll | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
4
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1052 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
2132 | EXCEL.EXE | GET | 200 | 2.16.186.11:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
1052 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA7yTSbUNi7CXXtef0luXqk%3D | US | der | 279 b | whitelisted |
— | — | GET | 200 | 2.16.186.27:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgMUCa%2Fbr4RVVQqyuCwvRqJ7cg%3D%3D | unknown | der | 527 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2132 | EXCEL.EXE | 2.16.186.11:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2132 | EXCEL.EXE | 47.254.26.204:443 | winsetup220.com | Alibaba (China) Technology Co., Ltd. | US | suspicious |
— | — | 2.16.186.27:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | whitelisted |
1052 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
winsetup220.com |
| suspicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |