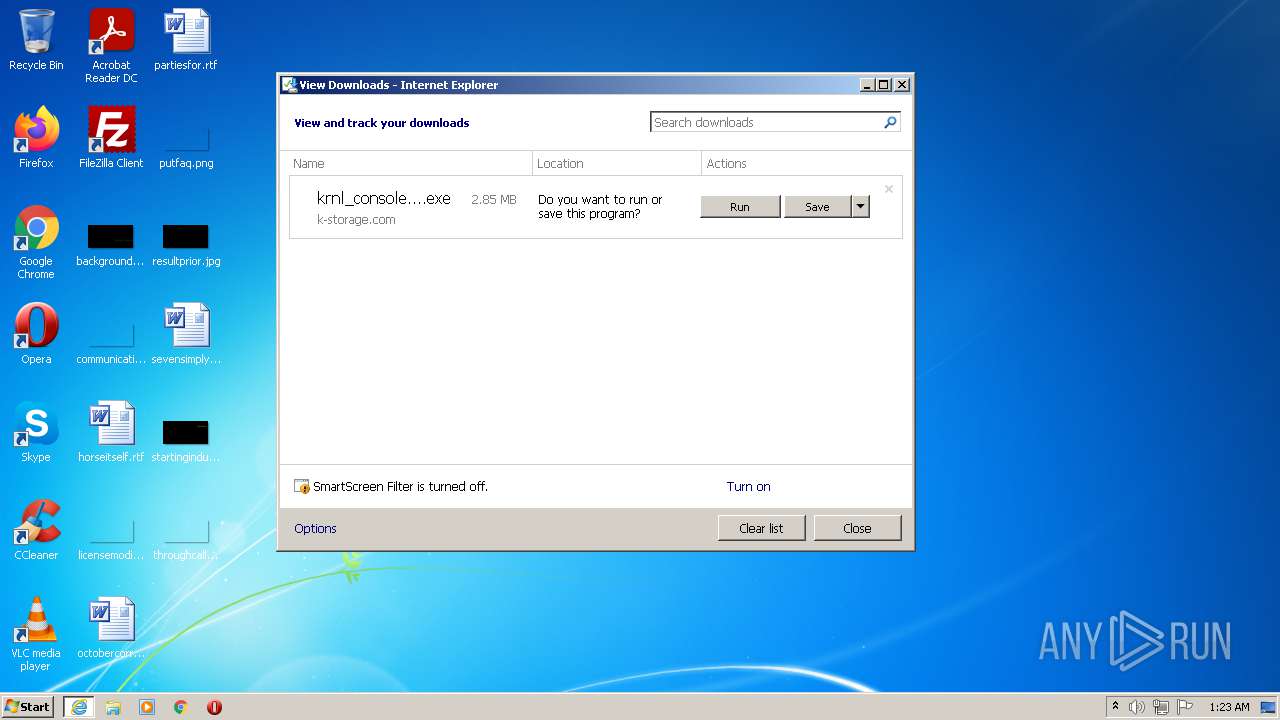
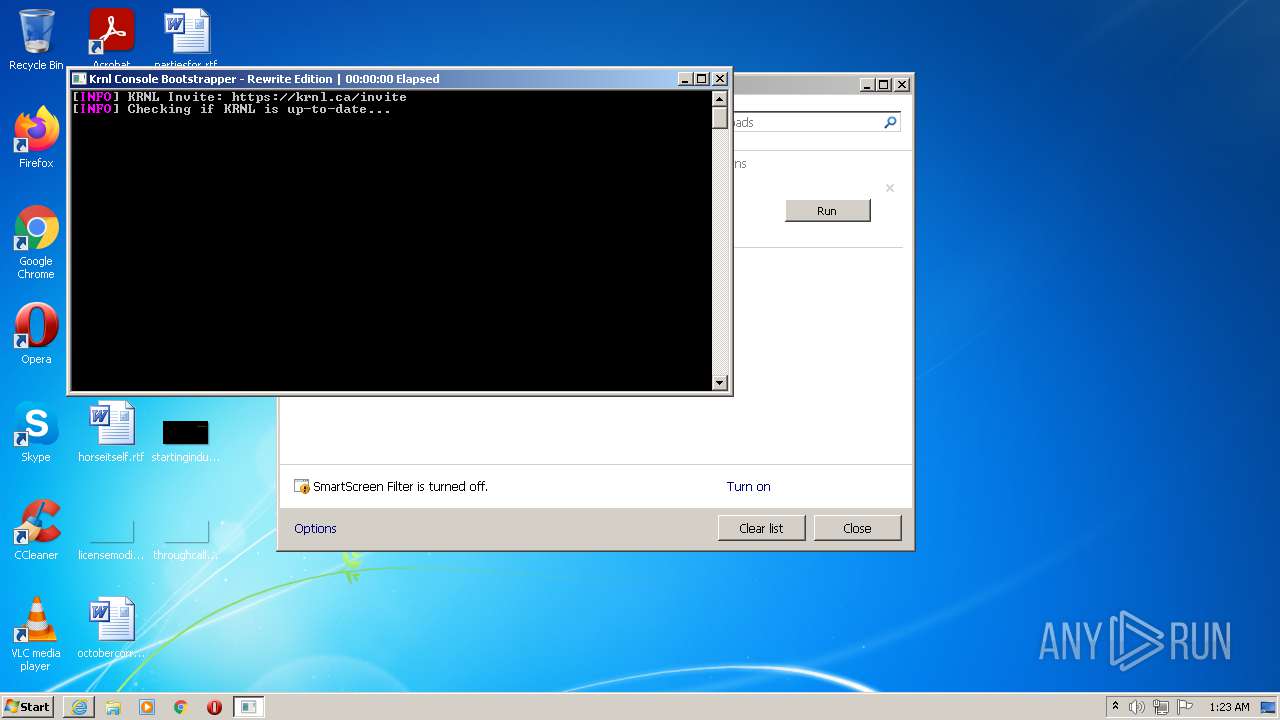
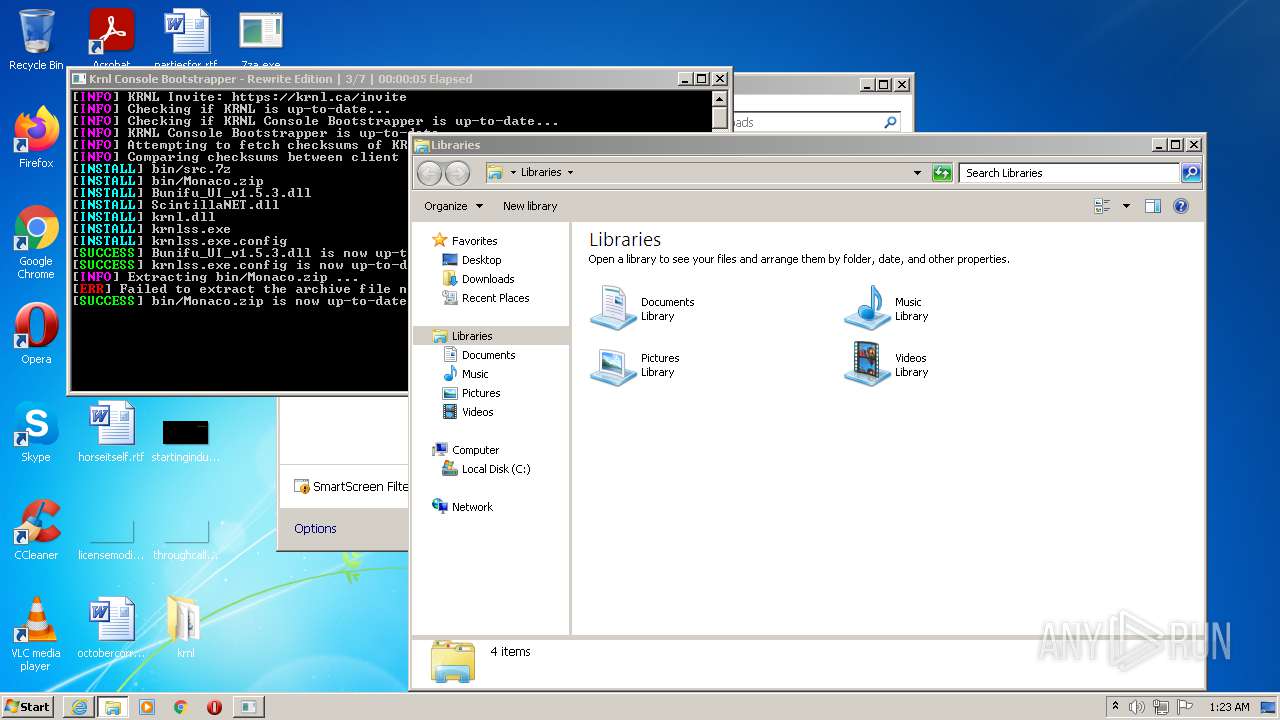
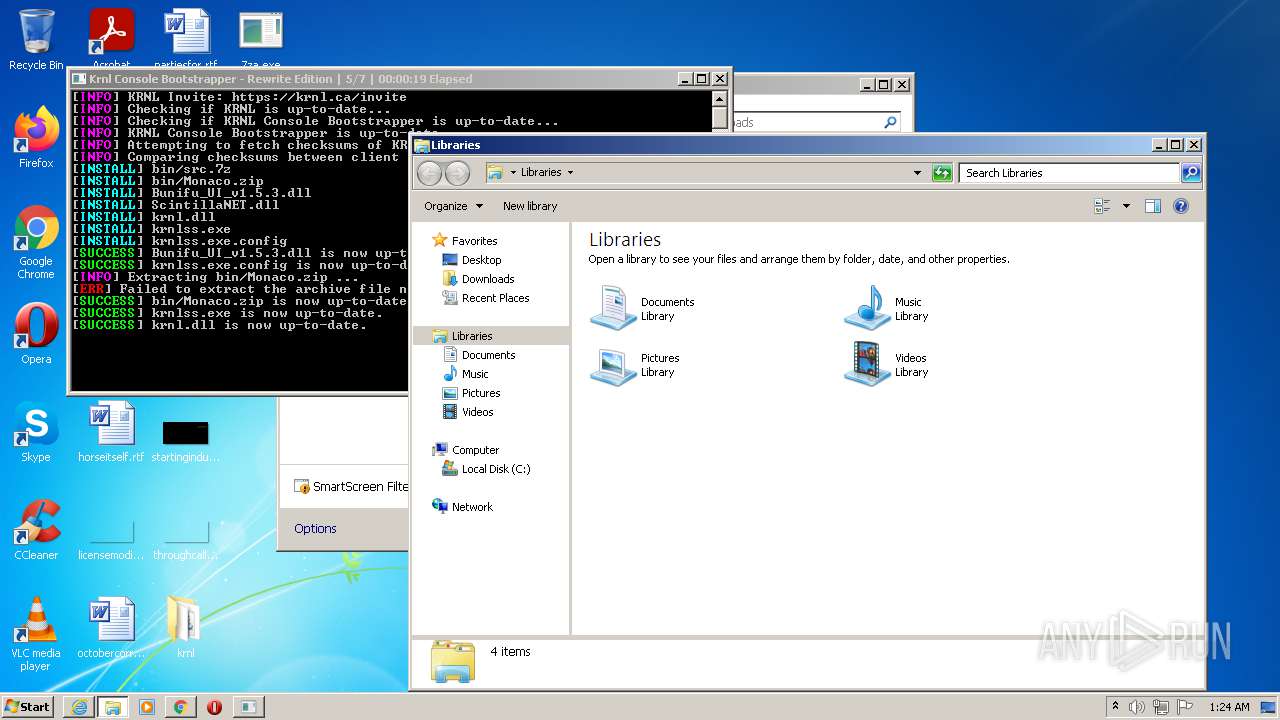
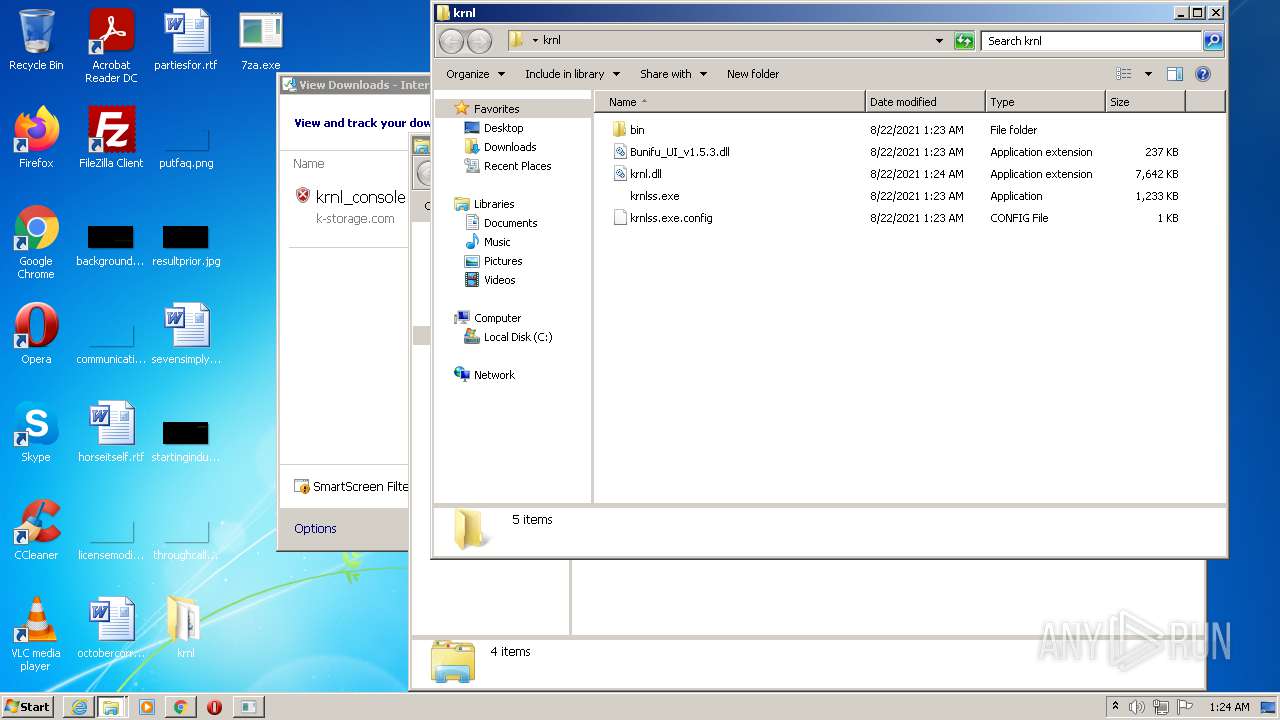
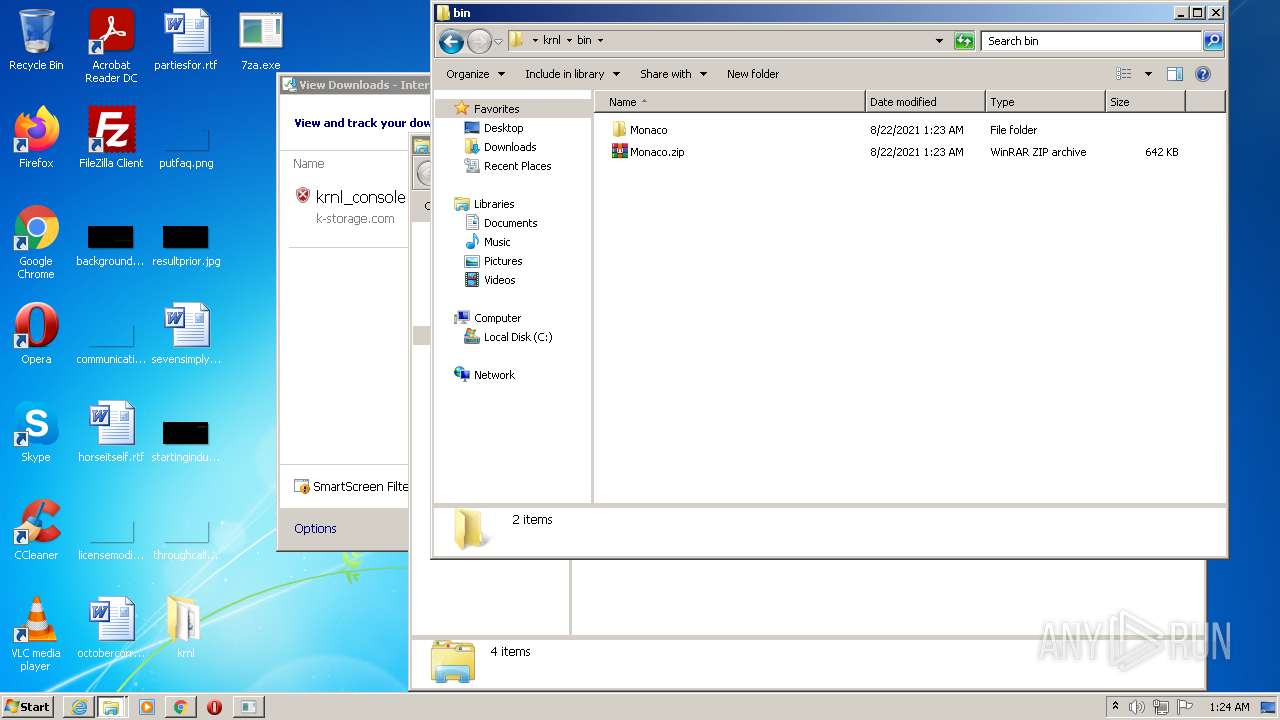
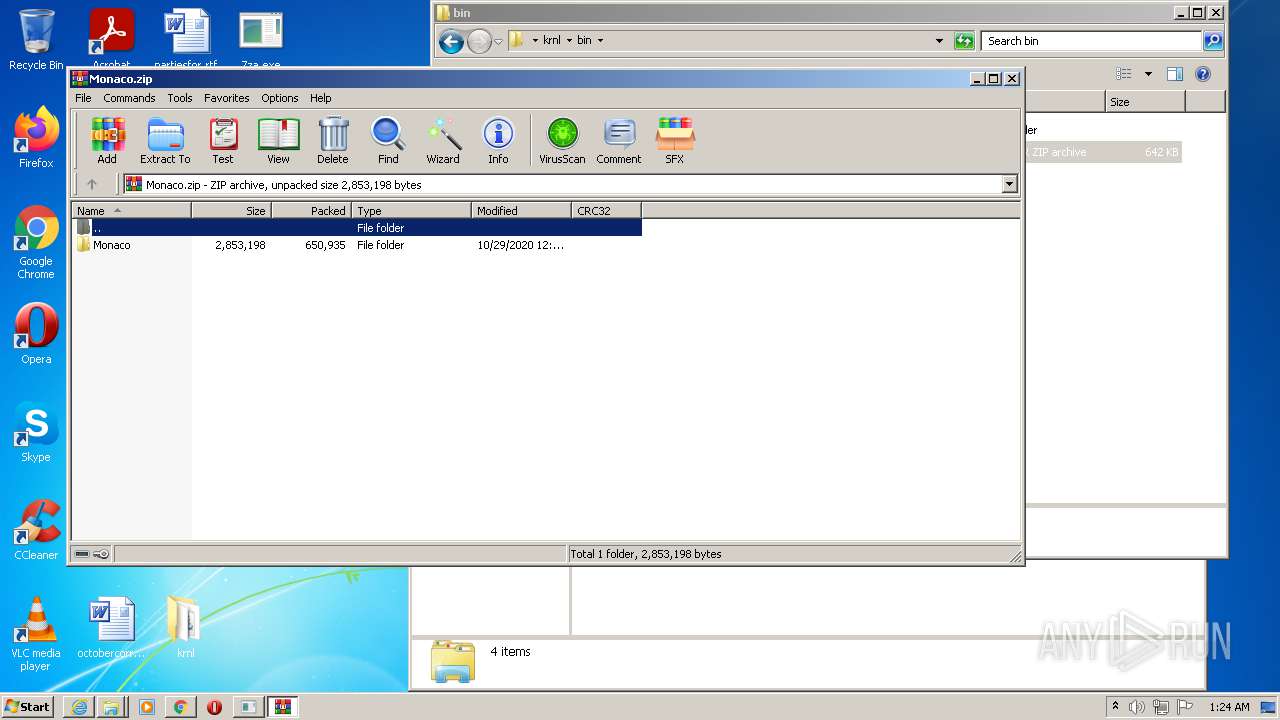
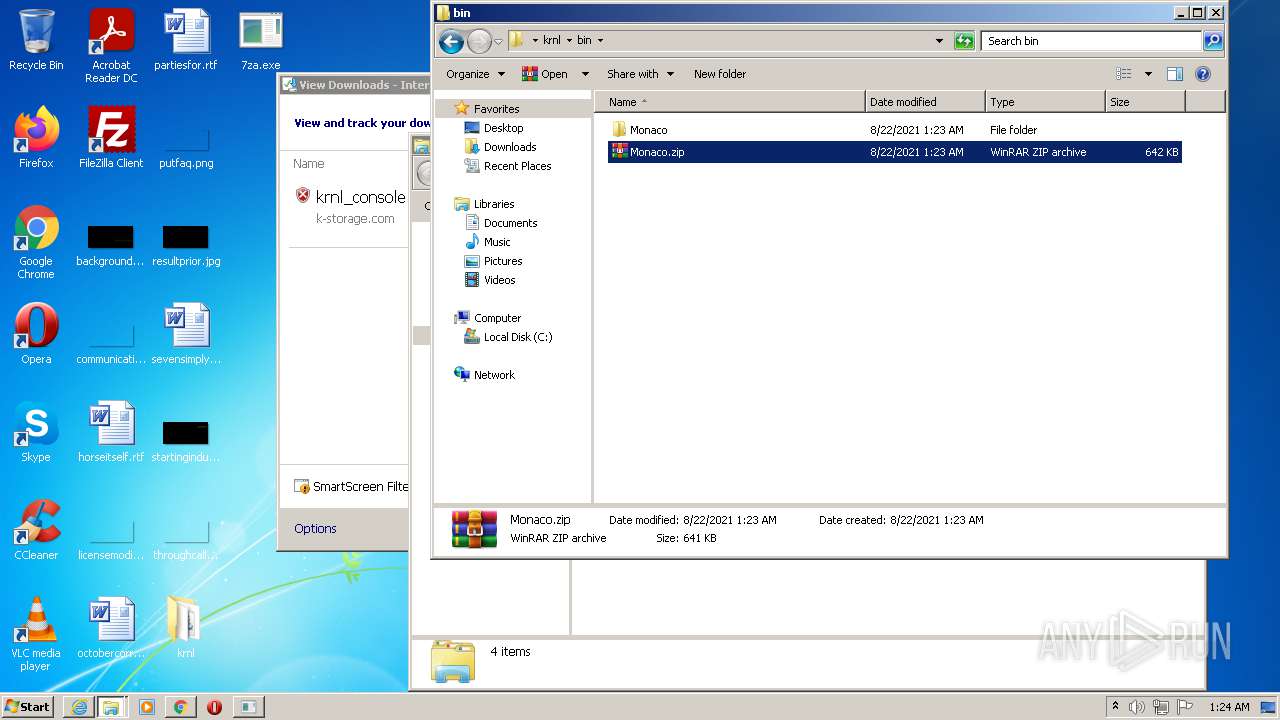
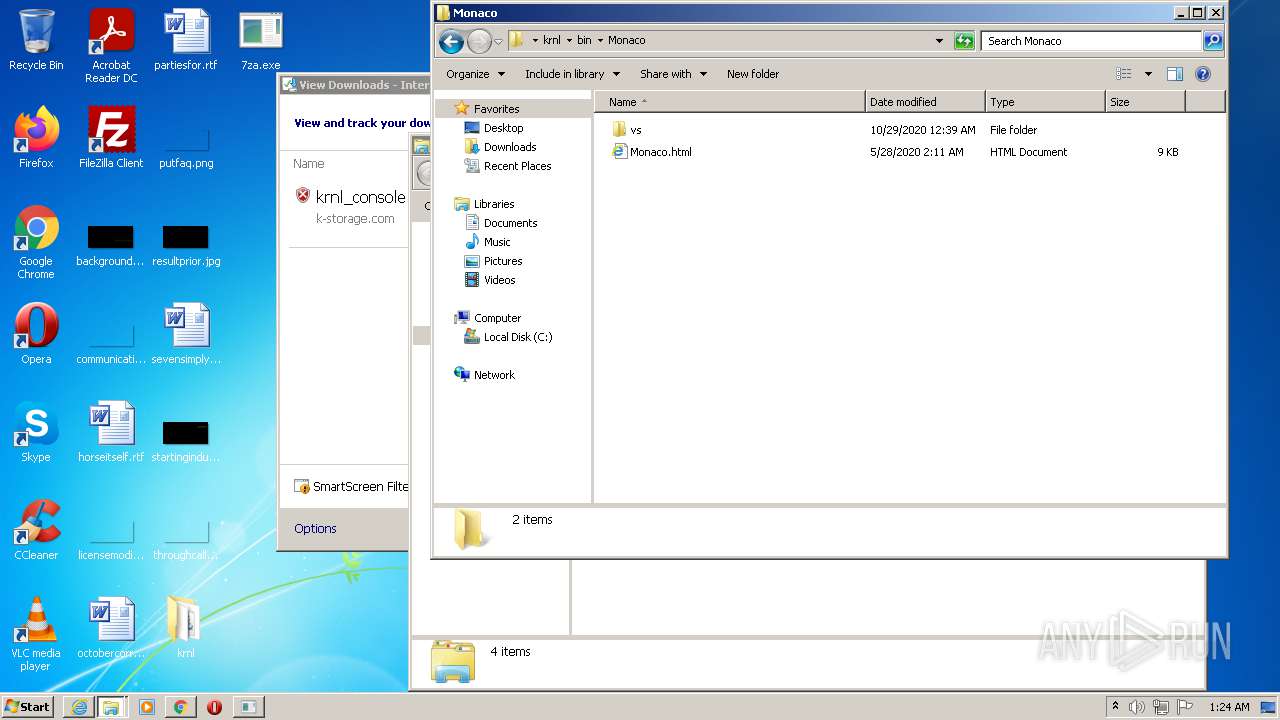
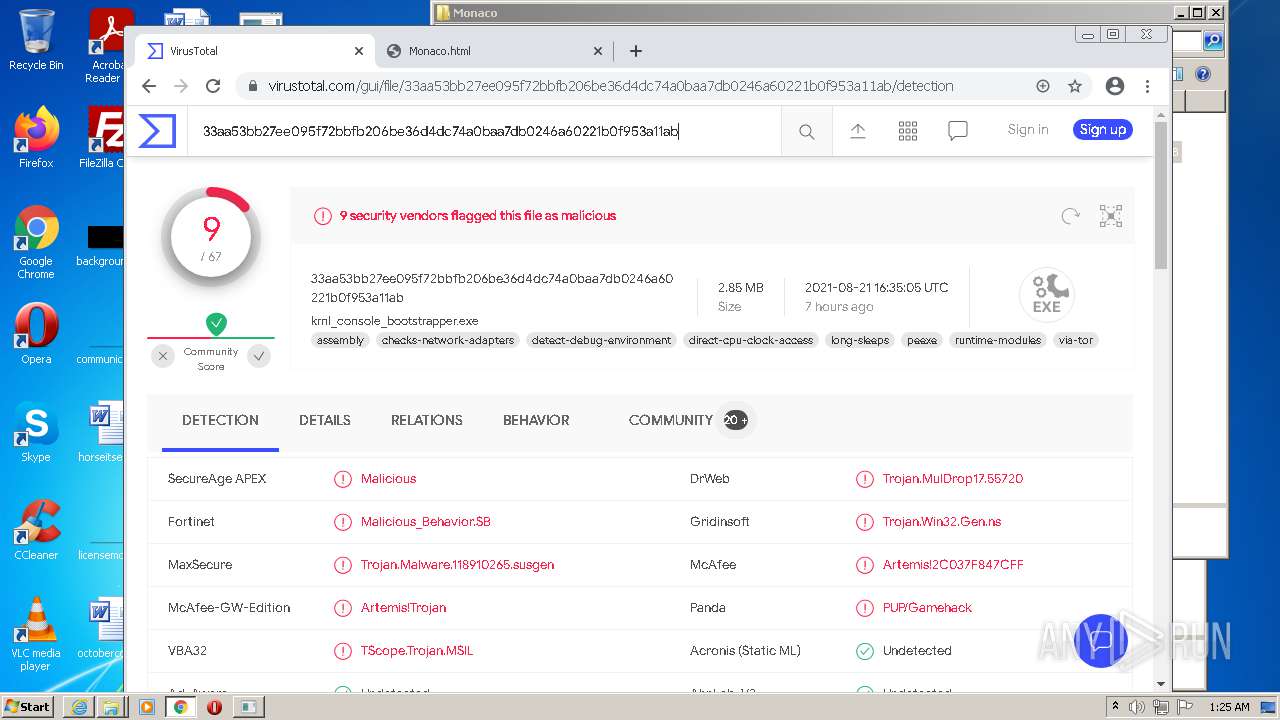
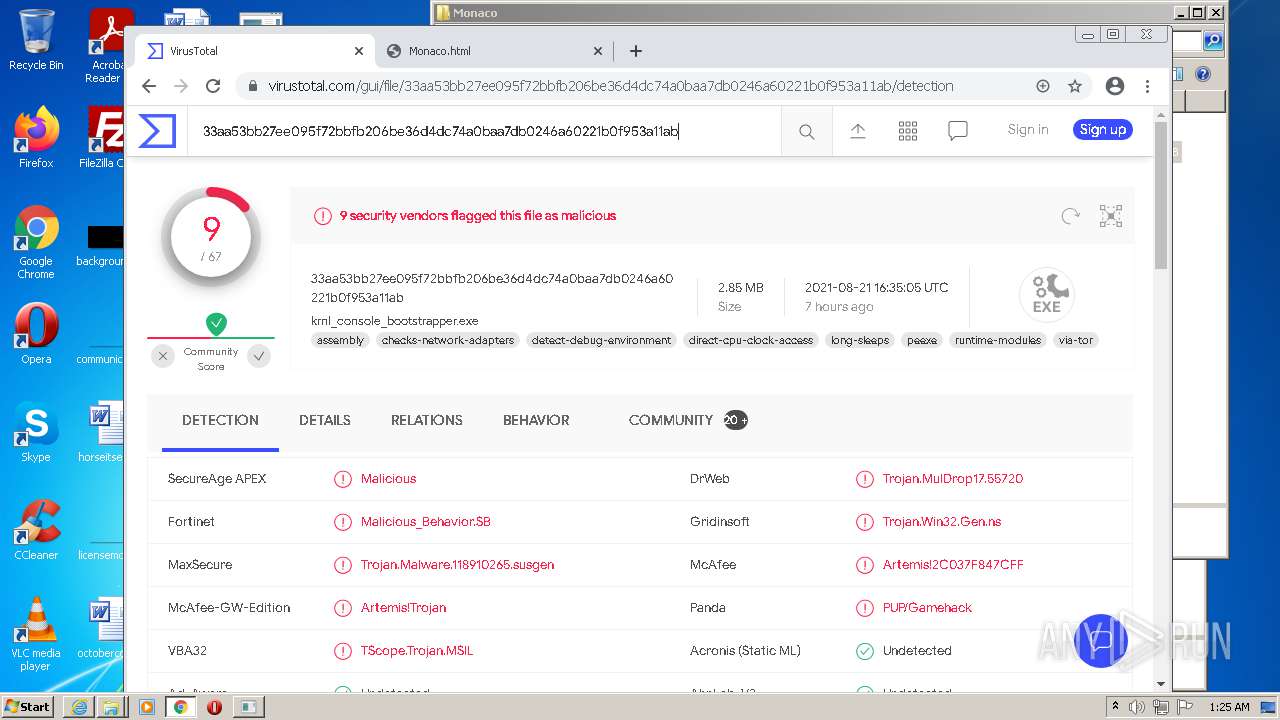
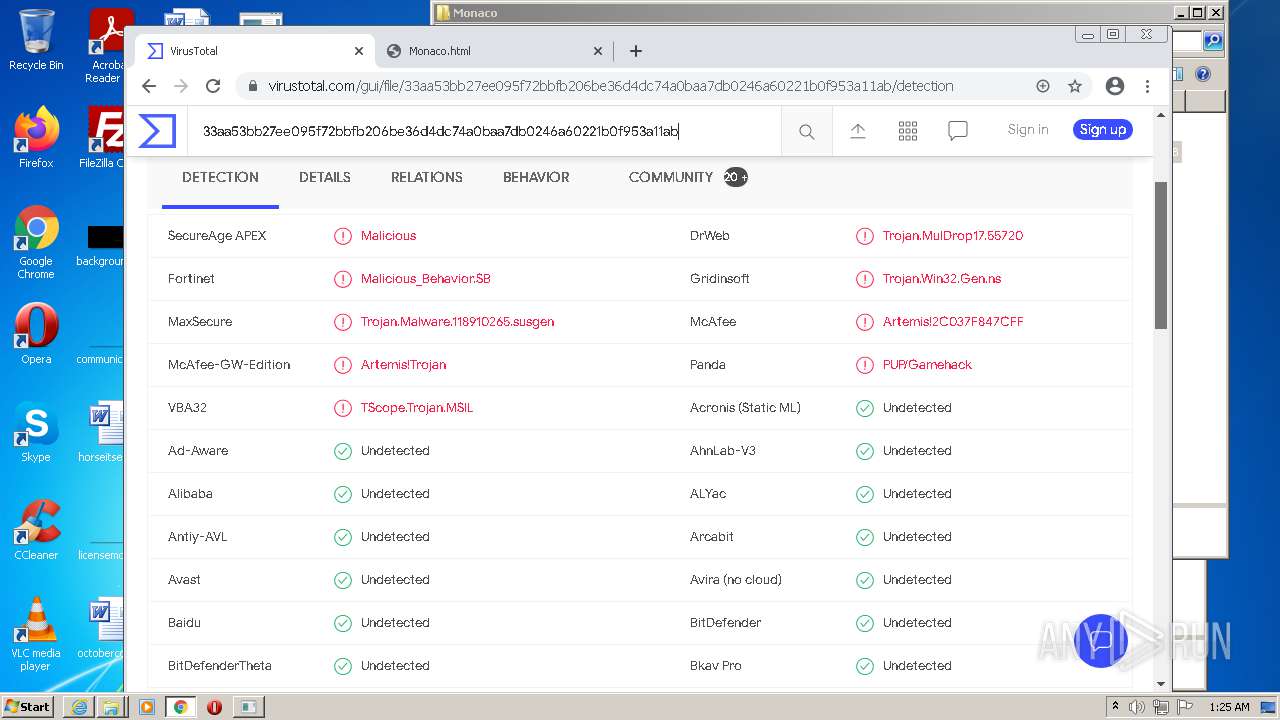
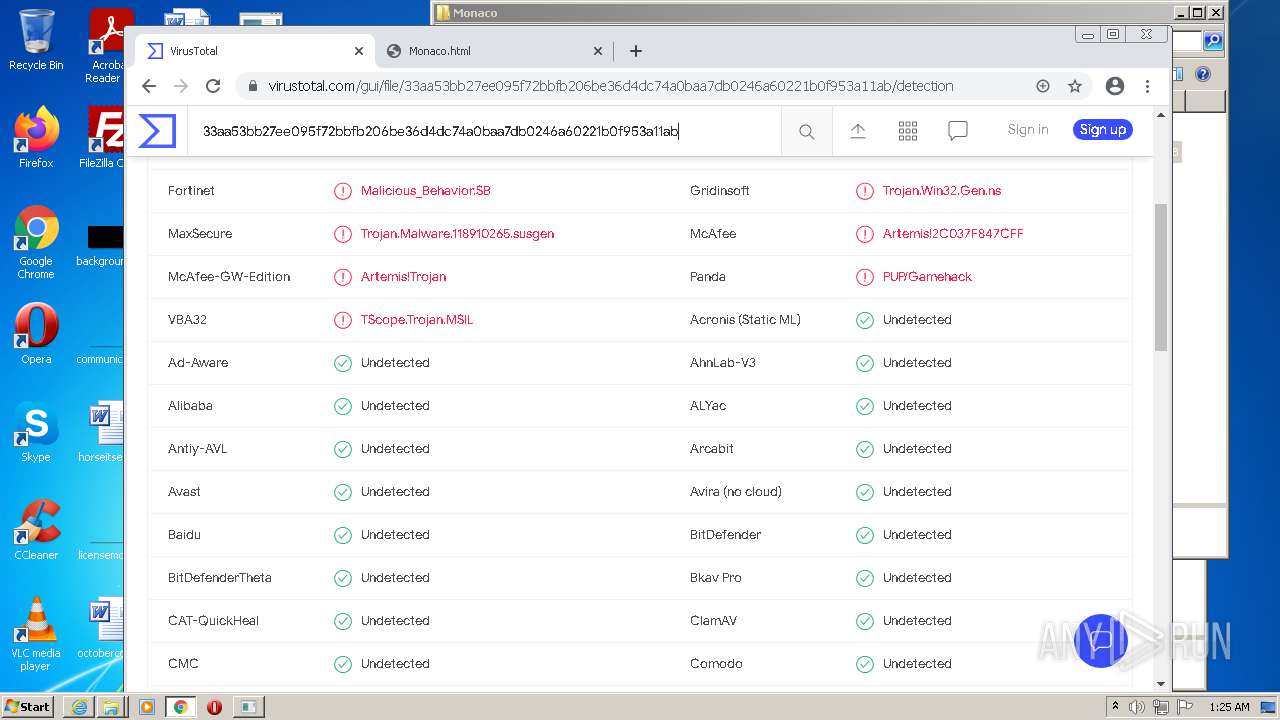
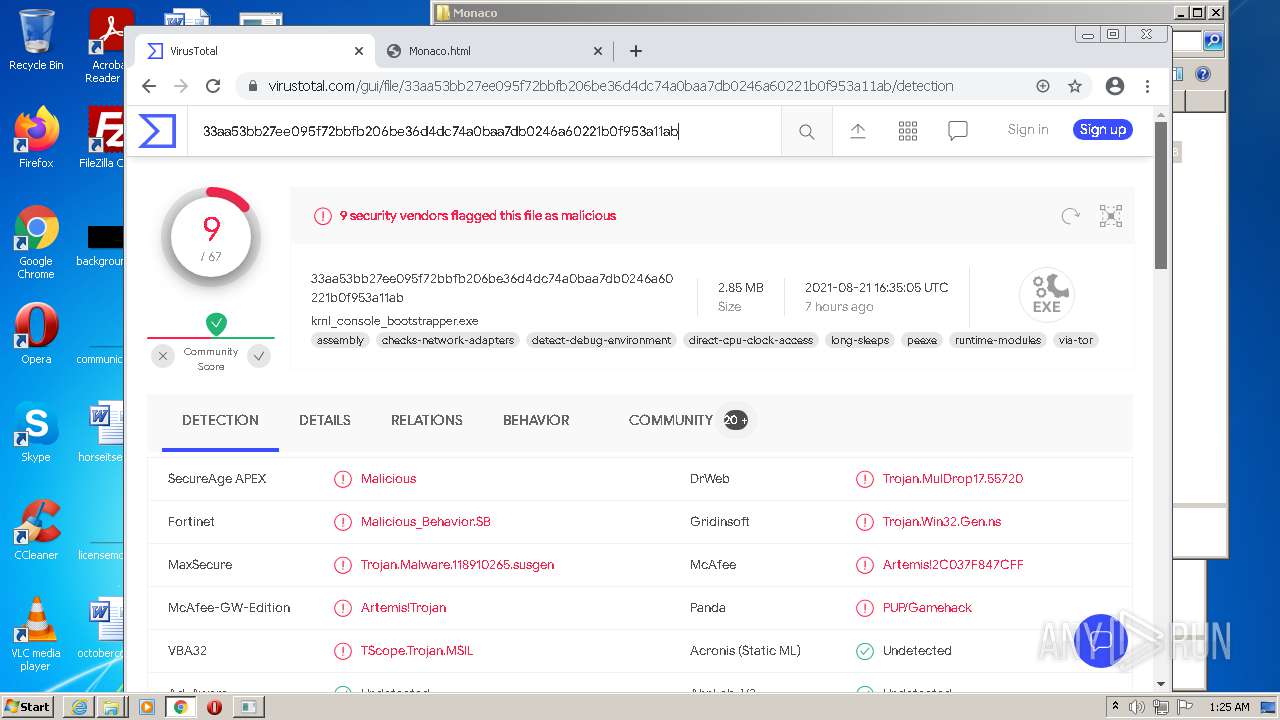
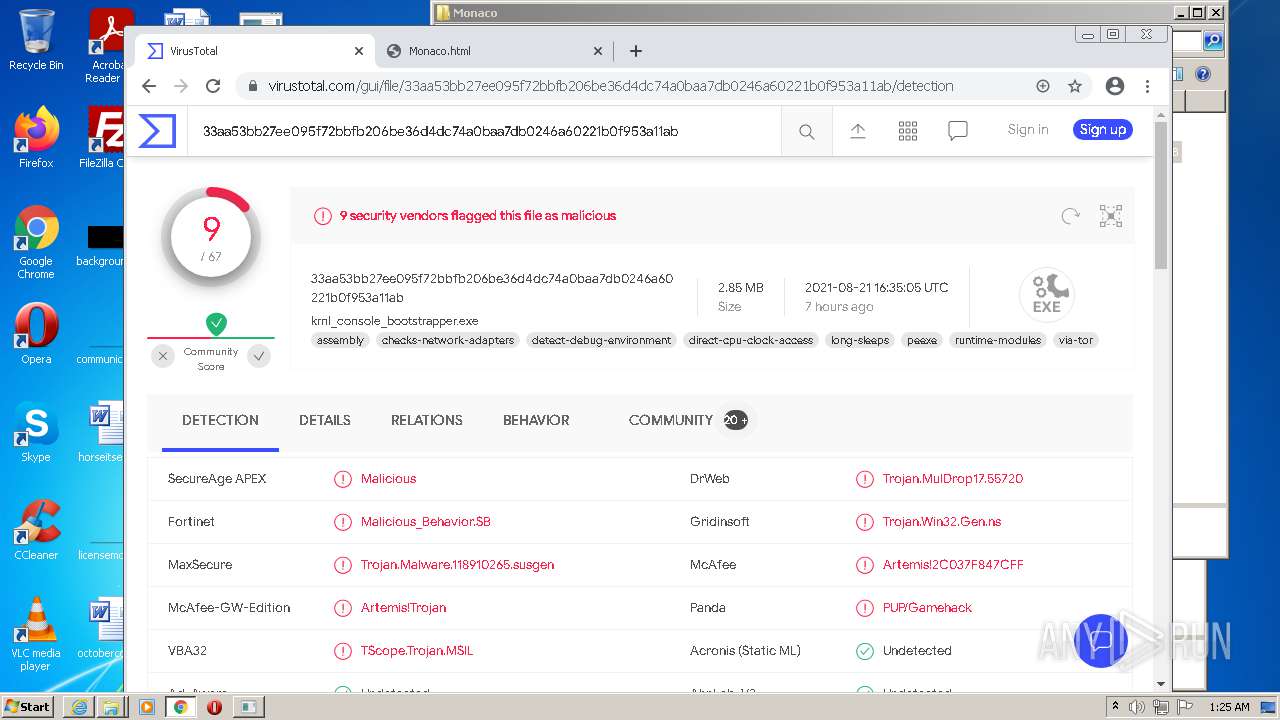
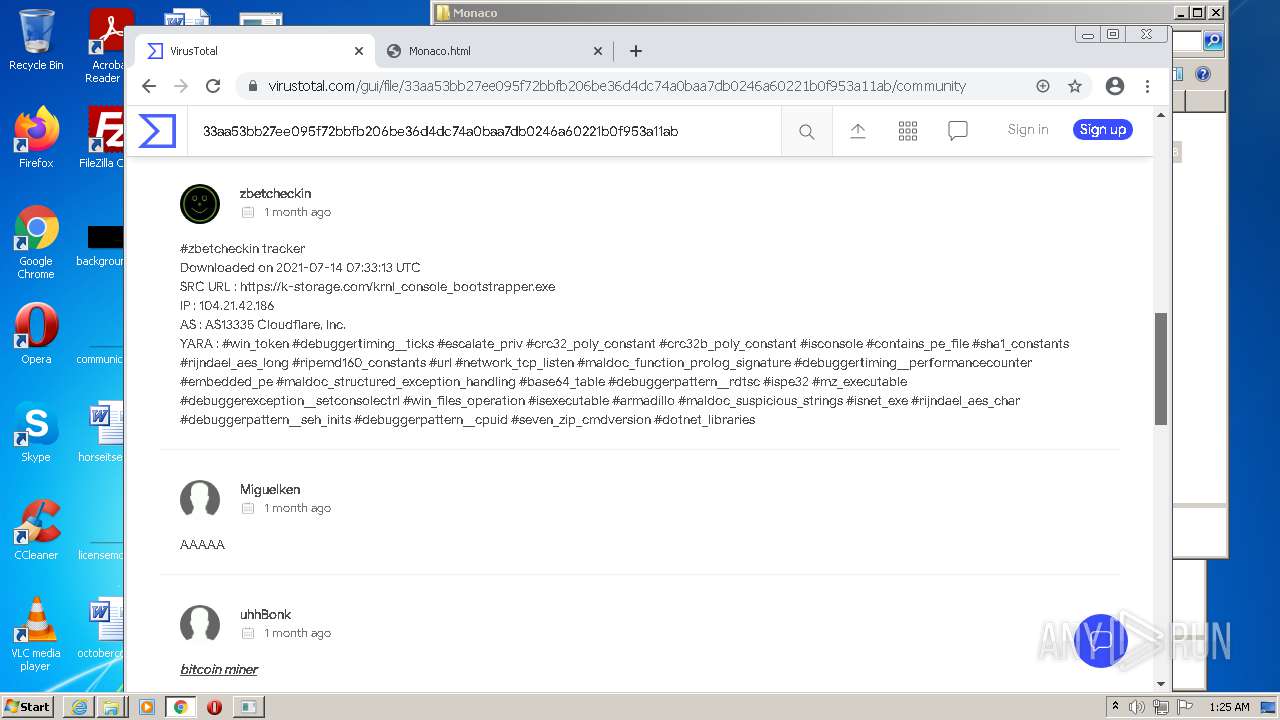
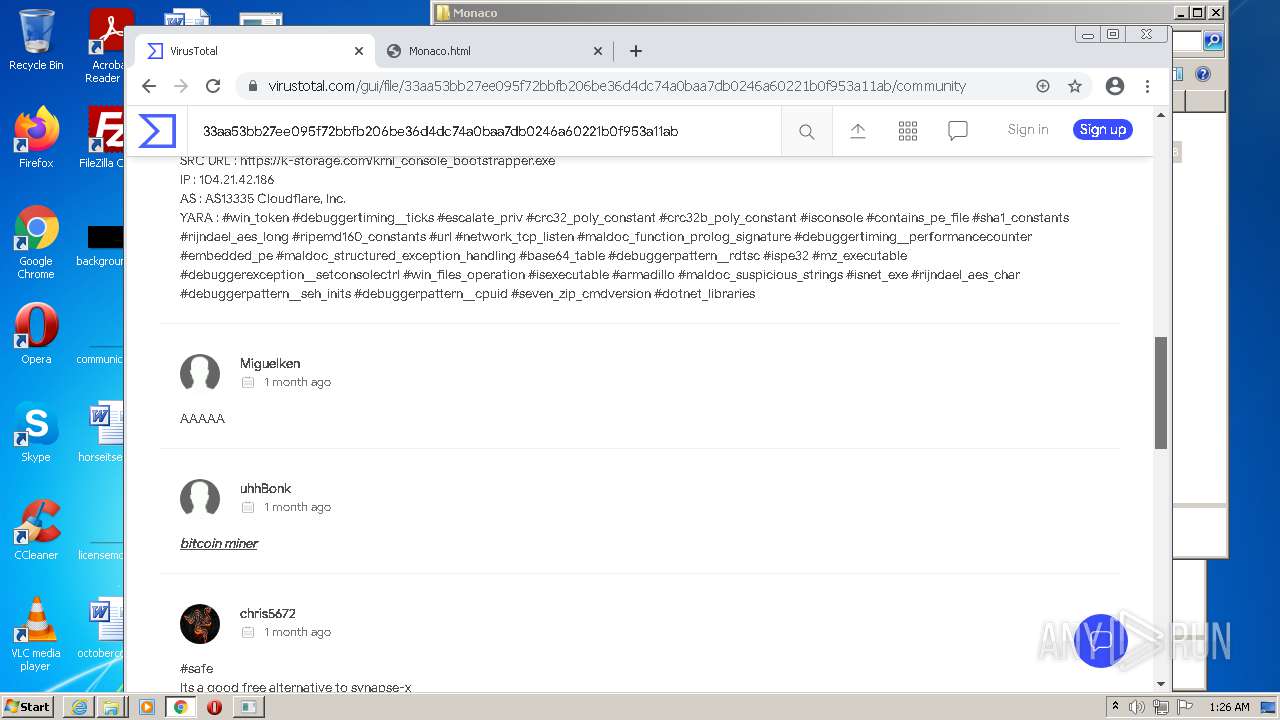
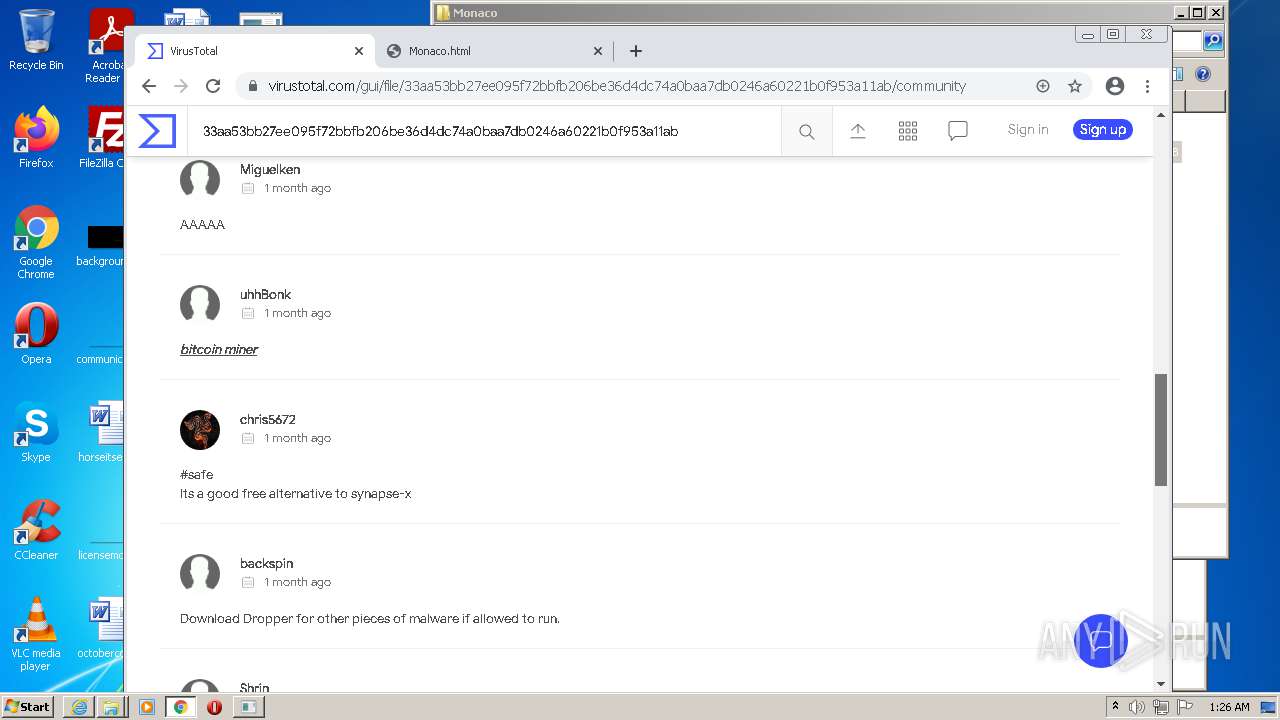
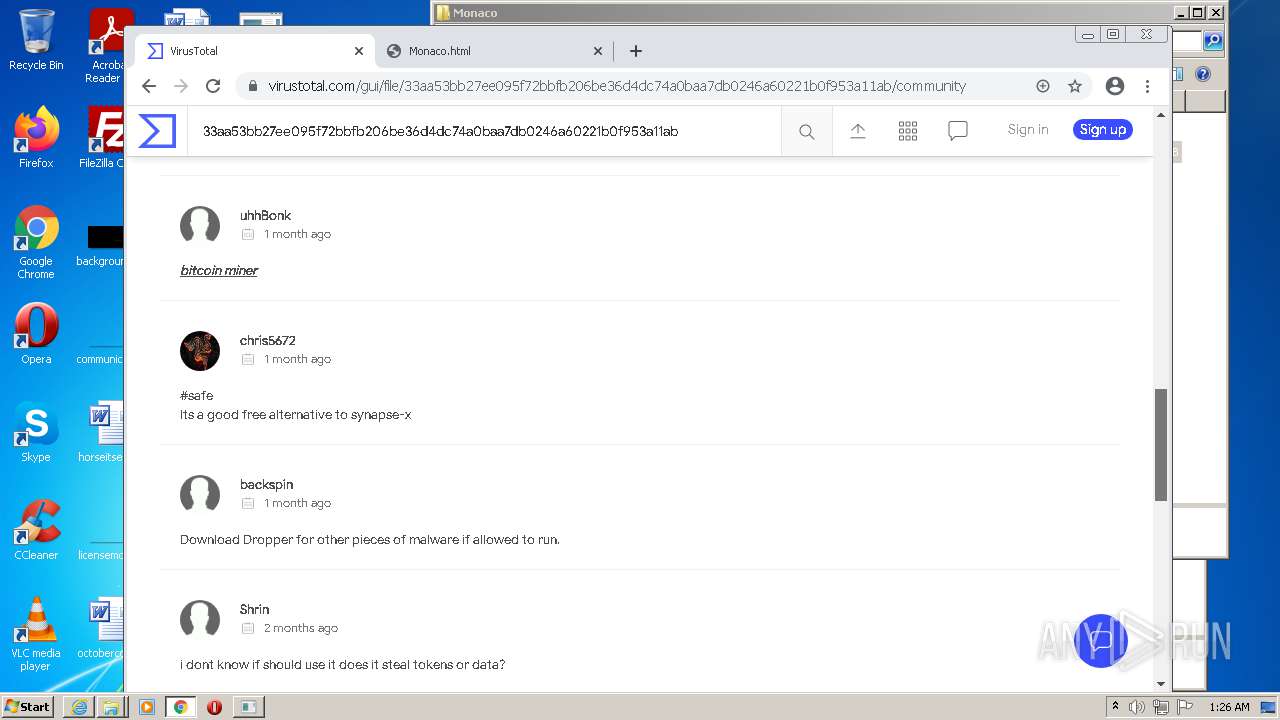
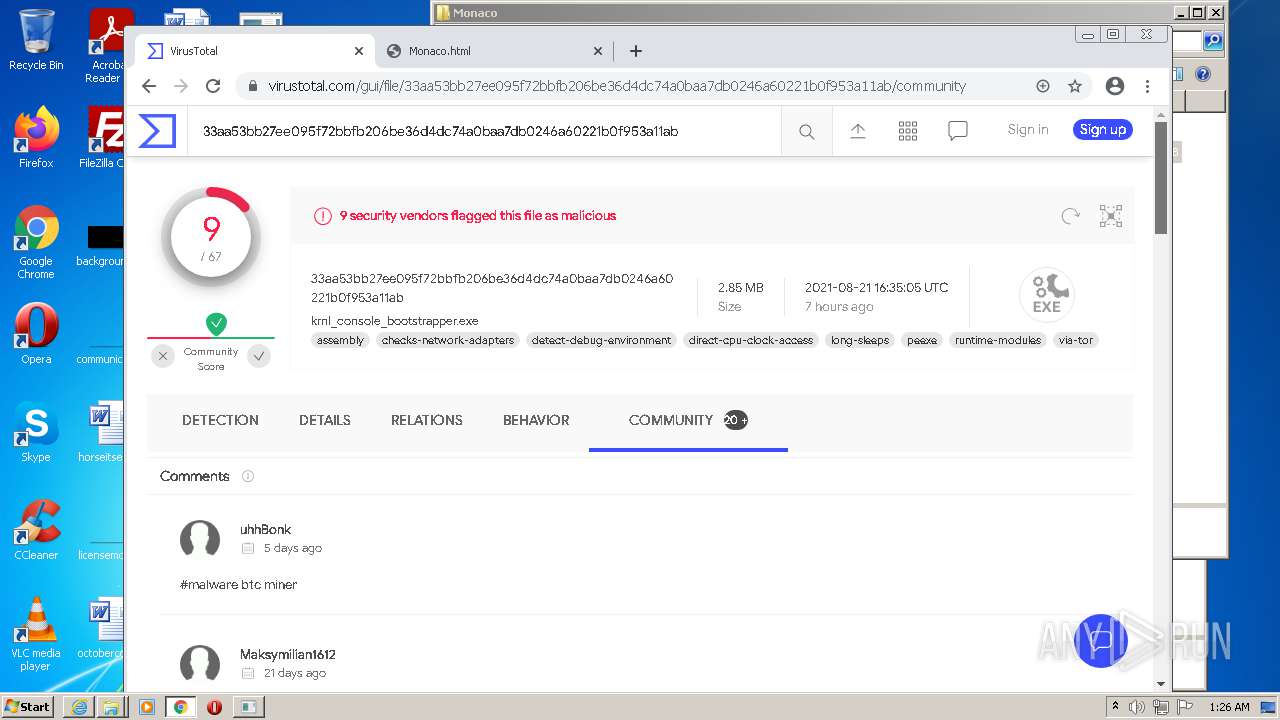
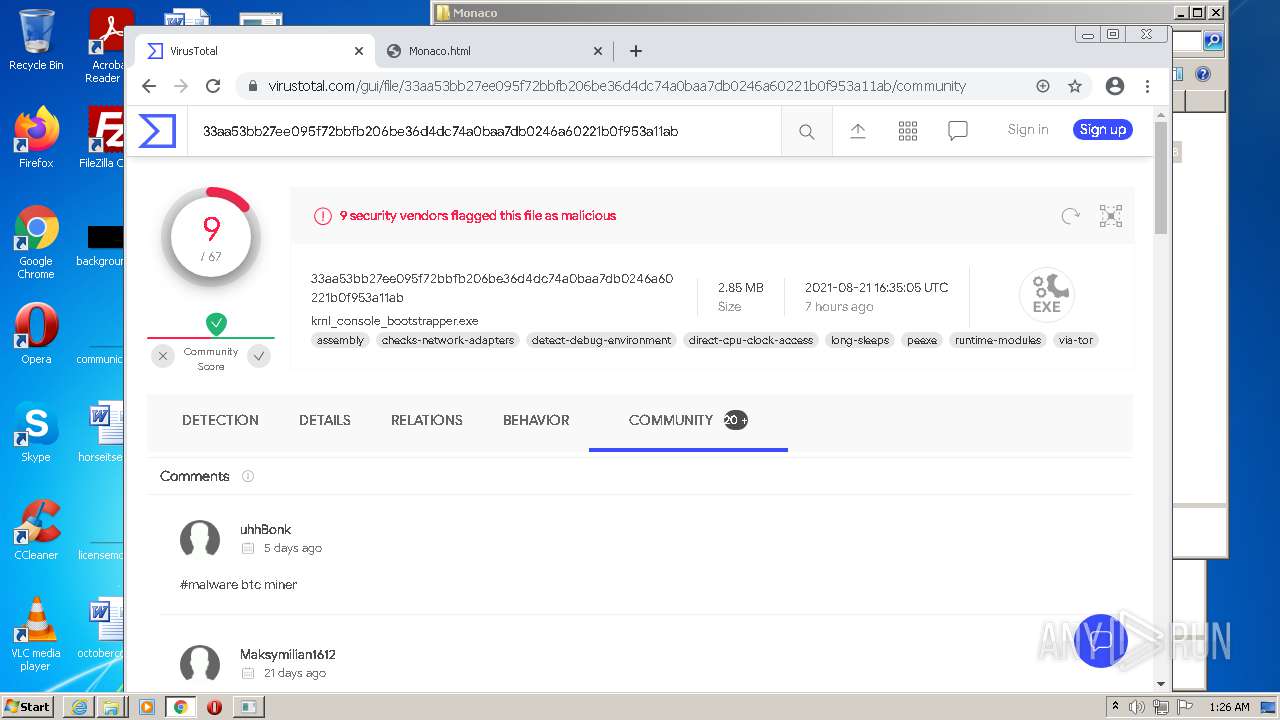
| URL: | https://k-storage.com/krnl_console_bootstrapper.exe |
| Full analysis: | https://app.any.run/tasks/310643ba-b40f-4f53-8550-0e3a693a4347 |
| Verdict: | Malicious activity |
| Analysis date: | August 22, 2021, 00:23:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | F7CEBB00B0CDE2288CBF2276F0E8F803 |
| SHA1: | CA6A985BD5620F87019C6C024FBC47C7C0D0072E |
| SHA256: | D1E54509F59C494355FCC5DB97C087C82D7AA6166BCC7A001D540D0B5FB1C1B2 |
| SSDEEP: | 3:N8EsXA3OXL0JNJPWXEw4A:2EsXDXbEw4A |
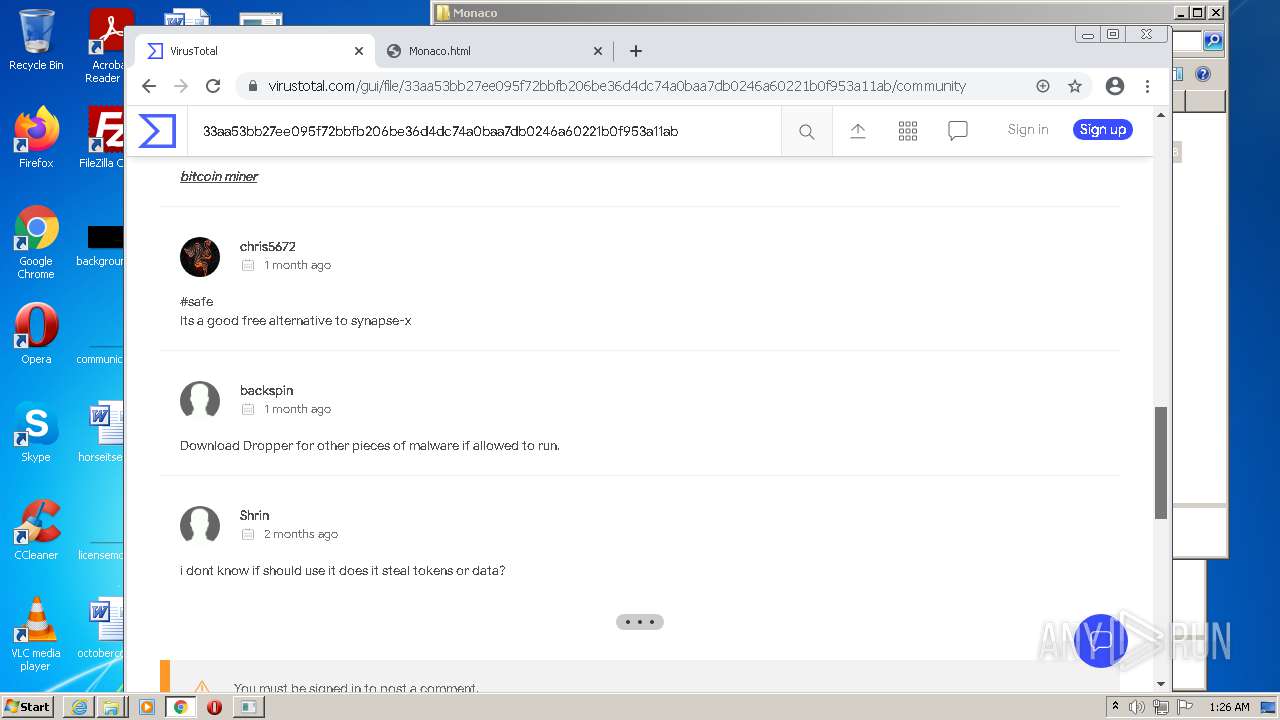
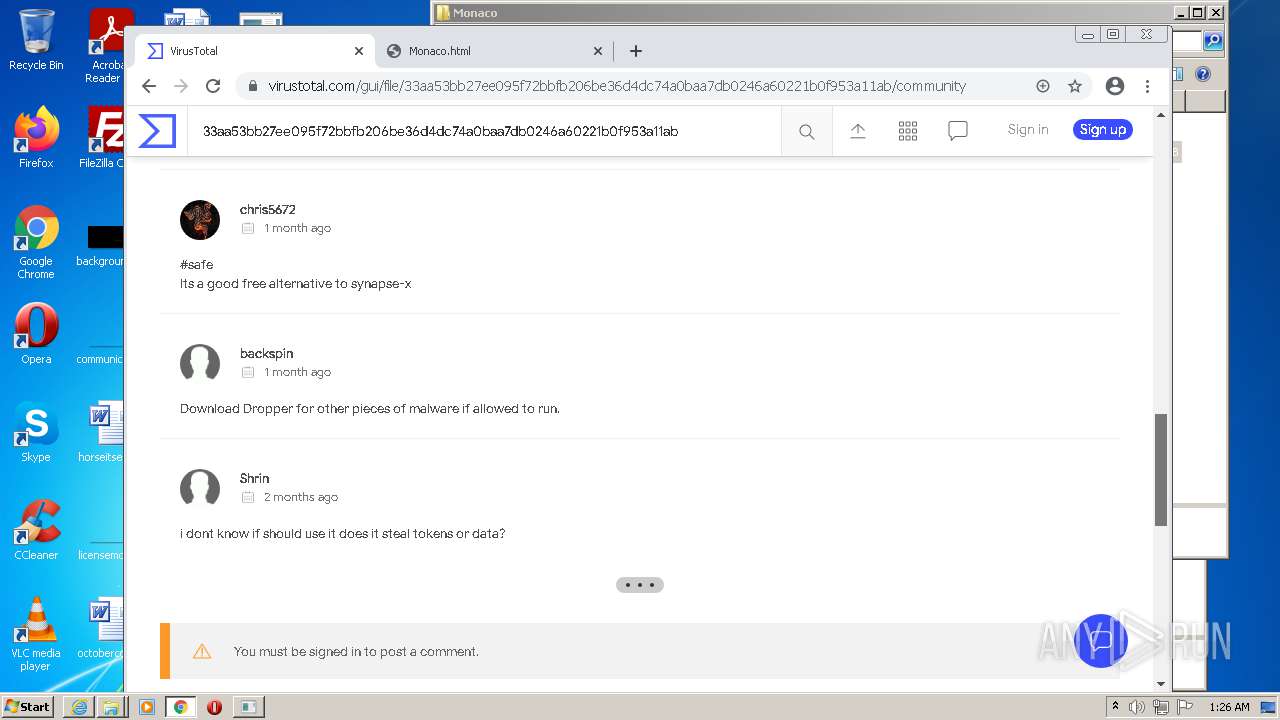
MALICIOUS
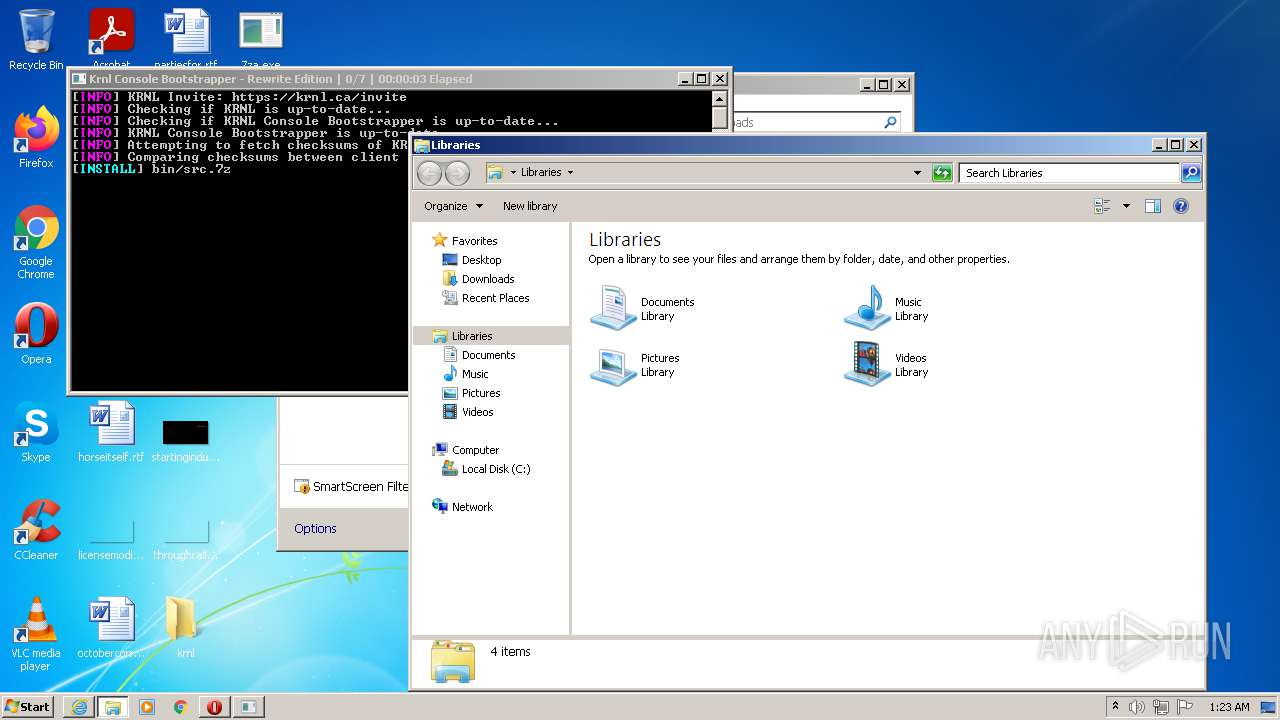
Drops executable file immediately after starts
- SearchProtocolHost.exe (PID: 2888)
Application was dropped or rewritten from another process
- krnl_console_bootstrapper.exe (PID: 2272)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2888)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1236)
- iexplore.exe (PID: 2692)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 1236)
- krnl_console_bootstrapper.exe (PID: 2272)
Reads the computer name
- krnl_console_bootstrapper.exe (PID: 2272)
- WinRAR.exe (PID: 2568)
- WinRAR.exe (PID: 3420)
Checks supported languages
- krnl_console_bootstrapper.exe (PID: 2272)
- WinRAR.exe (PID: 2568)
- WinRAR.exe (PID: 3420)
Reads Environment values
- krnl_console_bootstrapper.exe (PID: 2272)
Drops a file with a compile date too recent
- krnl_console_bootstrapper.exe (PID: 2272)
Modifies files in Chrome extension folder
- chrome.exe (PID: 1256)
Reads default file associations for system extensions
- chrome.exe (PID: 2408)
INFO
Reads the computer name
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 1236)
- explorer.exe (PID: 3392)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 2784)
- chrome.exe (PID: 976)
- chrome.exe (PID: 3288)
- iexplore.exe (PID: 3396)
- iexplore.exe (PID: 2692)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 1824)
- chrome.exe (PID: 2408)
- chrome.exe (PID: 3296)
Checks supported languages
- iexplore.exe (PID: 2684)
- iexplore.exe (PID: 1236)
- explorer.exe (PID: 3392)
- chrome.exe (PID: 1256)
- chrome.exe (PID: 2784)
- chrome.exe (PID: 3556)
- chrome.exe (PID: 2452)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 2808)
- chrome.exe (PID: 1344)
- chrome.exe (PID: 2632)
- chrome.exe (PID: 976)
- chrome.exe (PID: 3948)
- chrome.exe (PID: 3868)
- chrome.exe (PID: 3604)
- chrome.exe (PID: 1824)
- chrome.exe (PID: 508)
- chrome.exe (PID: 3288)
- chrome.exe (PID: 2560)
- chrome.exe (PID: 1736)
- chrome.exe (PID: 2860)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 2852)
- chrome.exe (PID: 568)
- chrome.exe (PID: 3172)
- chrome.exe (PID: 3156)
- chrome.exe (PID: 912)
- iexplore.exe (PID: 2692)
- iexplore.exe (PID: 3396)
- chrome.exe (PID: 3296)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 3532)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 1824)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 2408)
- chrome.exe (PID: 2840)
- chrome.exe (PID: 2772)
- chrome.exe (PID: 3296)
- chrome.exe (PID: 3004)
- chrome.exe (PID: 3992)
Application launched itself
- iexplore.exe (PID: 2684)
- chrome.exe (PID: 1256)
Changes internet zones settings
- iexplore.exe (PID: 2684)
Checks Windows Trust Settings
- iexplore.exe (PID: 1236)
- iexplore.exe (PID: 2684)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2684)
Reads the date of Windows installation
- iexplore.exe (PID: 2684)
- chrome.exe (PID: 2628)
Reads settings of System Certificates
- iexplore.exe (PID: 1236)
- krnl_console_bootstrapper.exe (PID: 2272)
- chrome.exe (PID: 2784)
- iexplore.exe (PID: 2684)
Manual execution by user
- explorer.exe (PID: 3392)
- chrome.exe (PID: 1256)
- WinRAR.exe (PID: 2568)
- WinRAR.exe (PID: 3420)
- iexplore.exe (PID: 3396)
Reads the hosts file
- chrome.exe (PID: 1256)
- chrome.exe (PID: 2784)
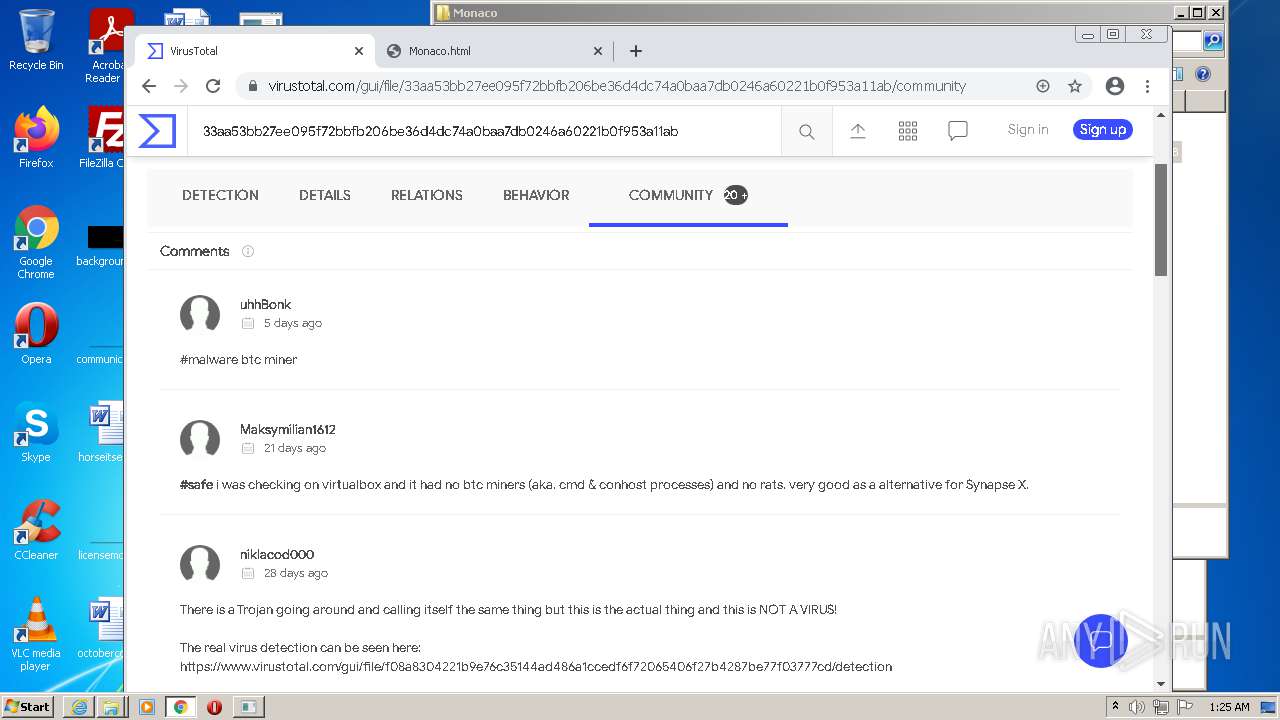
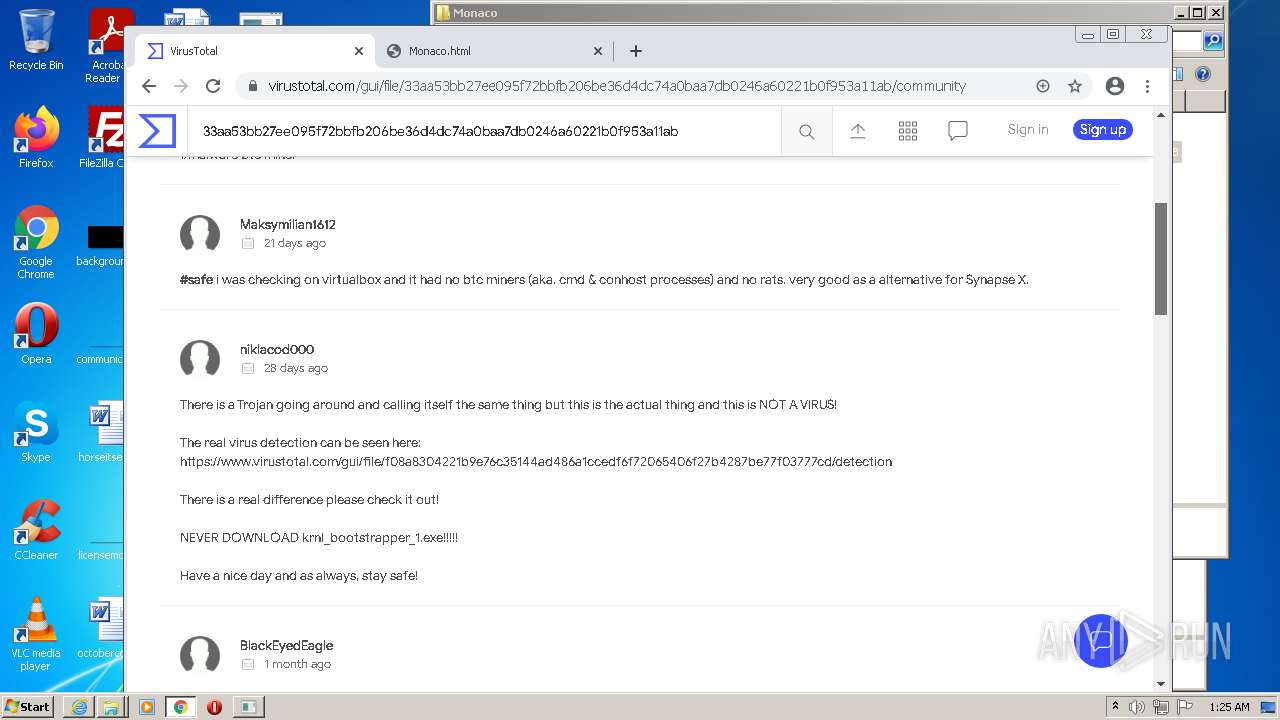
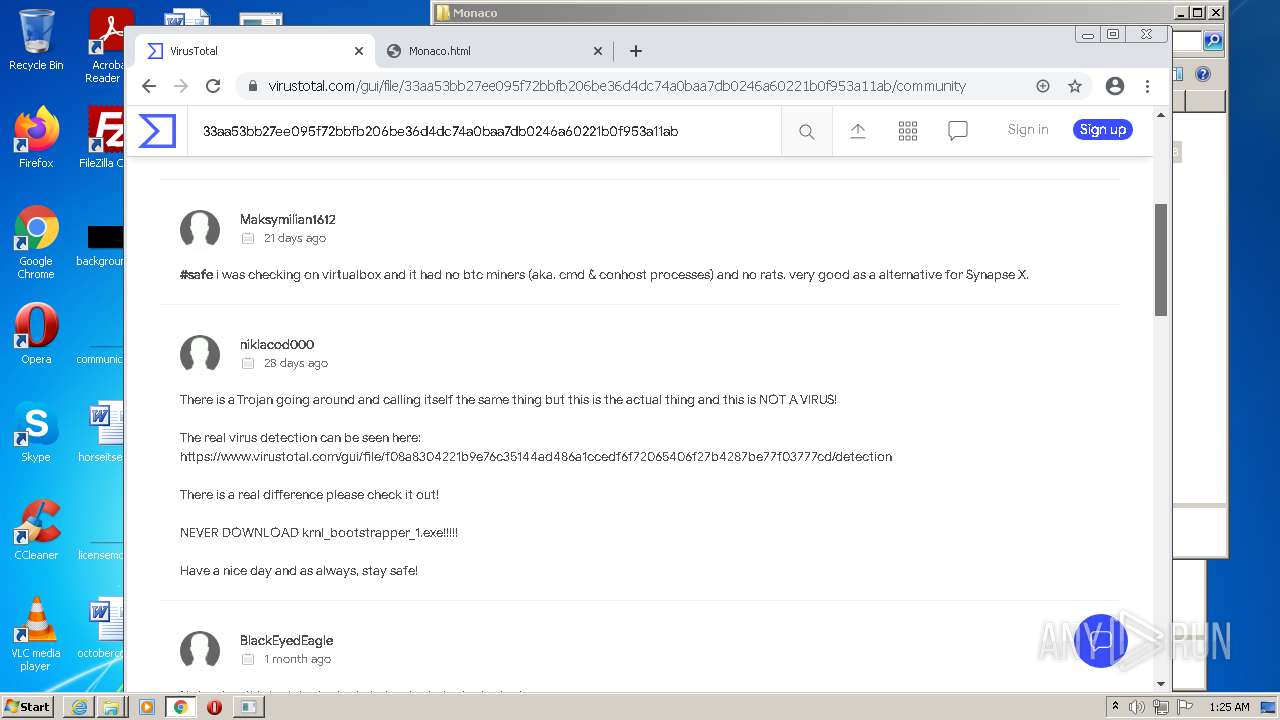
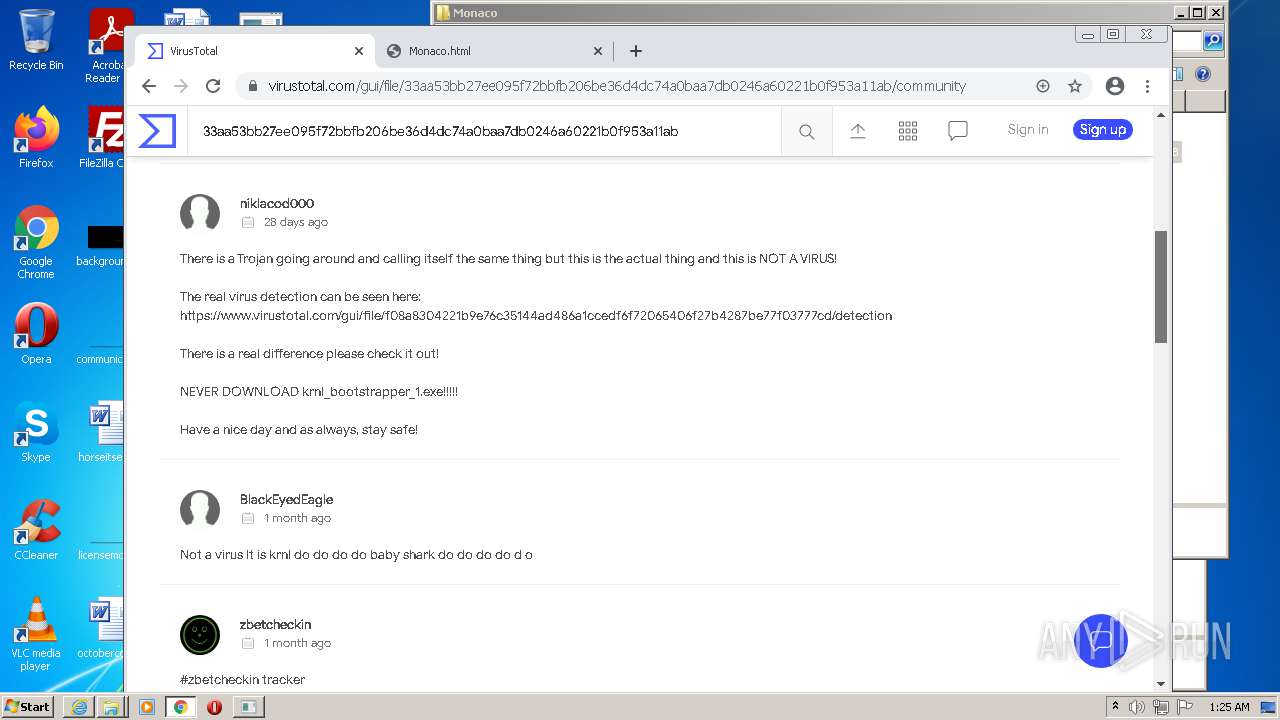
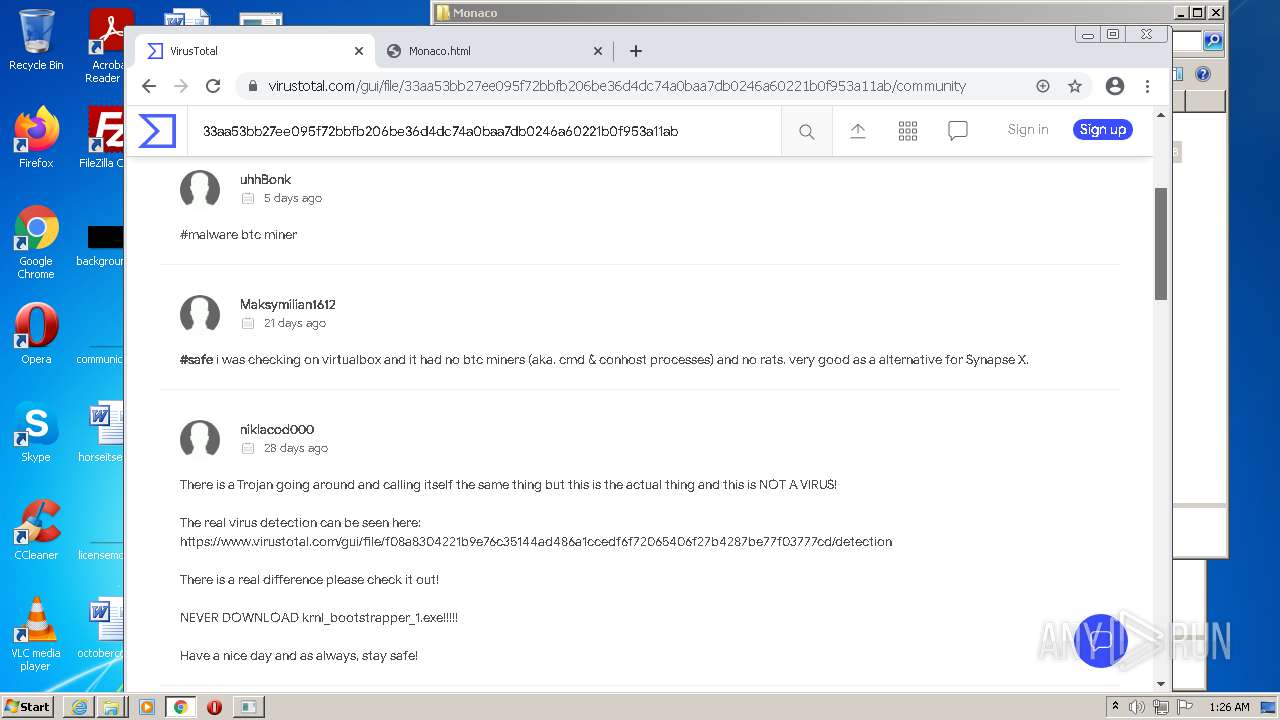
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 1256)
Reads internet explorer settings
- iexplore.exe (PID: 2692)
Creates files in the user directory
- iexplore.exe (PID: 2684)
Changes settings of System certificates
- iexplore.exe (PID: 2684)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
87
Monitored processes
45
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2900 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4124 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 912 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1972 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2932 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2684 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1256 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 3221225547 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1344 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2284 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2884 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3012 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1824 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=968,9736166410061900614,10245041739208014068,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3080 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
44 491
Read events
43 989
Write events
491
Delete events
11
Modification events
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30906091 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 64645971 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30906092 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2684) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
7
Suspicious files
142
Text files
289
Unknown types
44
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-61219917-4E8.pma | — | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC9AAD605AA6D1364.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:— | SHA256:— | |||
| 2888 | SearchProtocolHost.exe | C:\Users\admin\Downloads\krnl_console_bootstrapper.exe.fhzafub.partial | executable | |
MD5:— | SHA256:— | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\krnl_console_bootstrapper[1].exe | executable | |
MD5:— | SHA256:— | |||
| 2684 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{2F99686E-02DF-11EC-A146-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 1256 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | binary | |
MD5:— | SHA256:— | |||
| 1236 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
70
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2784 | chrome.exe | GET | 302 | 216.239.32.21:80 | http://virustotal.com/ | US | — | — | whitelisted |
1772 | svchost.exe | HEAD | 302 | 172.217.23.110:80 | http://redirector.gvt1.com/edgedl/release2/chrome_component/gpe7ohs3f5omwhxxpxvcdvkwva_1.3.36.101/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.101_win_adeodp7n5nw3wgk7xjdln2w2sgsq.crx3 | US | — | — | whitelisted |
1672 | svchost.exe | GET | 304 | 2.16.186.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?bddad4af5c095095 | unknown | — | — | whitelisted |
2684 | iexplore.exe | GET | 304 | 2.16.186.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4d77c15eeec9893d | unknown | — | — | whitelisted |
2784 | chrome.exe | GET | 302 | 172.217.23.110:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | html | 555 b | whitelisted |
2684 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2684 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2684 | iexplore.exe | GET | 304 | 2.16.186.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e8e0a7ca159c35f5 | unknown | — | — | whitelisted |
2684 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
2684 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1236 | iexplore.exe | 104.21.42.186:443 | k-storage.com | Cloudflare Inc | US | unknown |
1236 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2272 | krnl_console_bootstrapper.exe | 104.21.39.171:443 | cdn.krnl.ca | Cloudflare Inc | US | malicious |
2272 | krnl_console_bootstrapper.exe | 104.21.42.186:443 | k-storage.com | Cloudflare Inc | US | unknown |
— | — | 104.21.42.186:443 | k-storage.com | Cloudflare Inc | US | unknown |
2784 | chrome.exe | 142.250.185.196:443 | www.google.com | Google Inc. | US | whitelisted |
2784 | chrome.exe | 142.250.185.206:443 | clients2.google.com | Google Inc. | US | whitelisted |
2784 | chrome.exe | 142.250.186.35:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2784 | chrome.exe | 142.250.184.237:443 | accounts.google.com | Google Inc. | US | suspicious |
2784 | chrome.exe | 142.250.184.202:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
k-storage.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
cdn.krnl.ca |
| malicious |
clientservices.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |