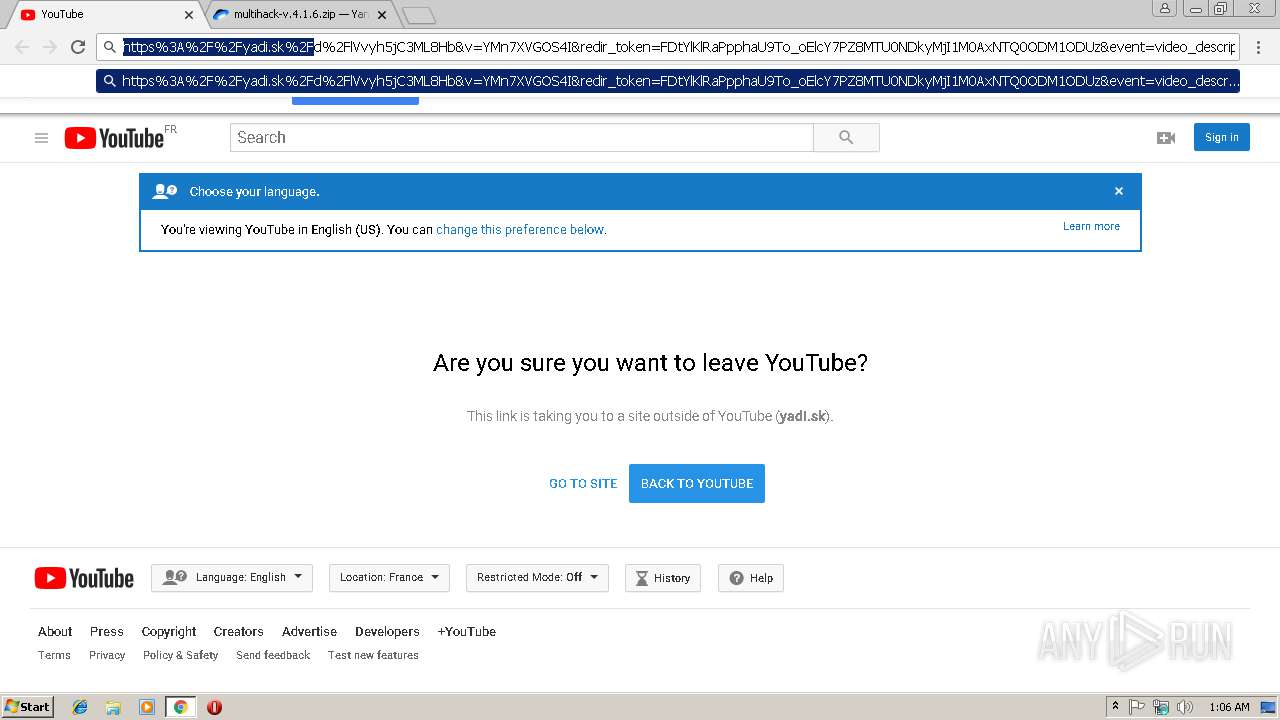
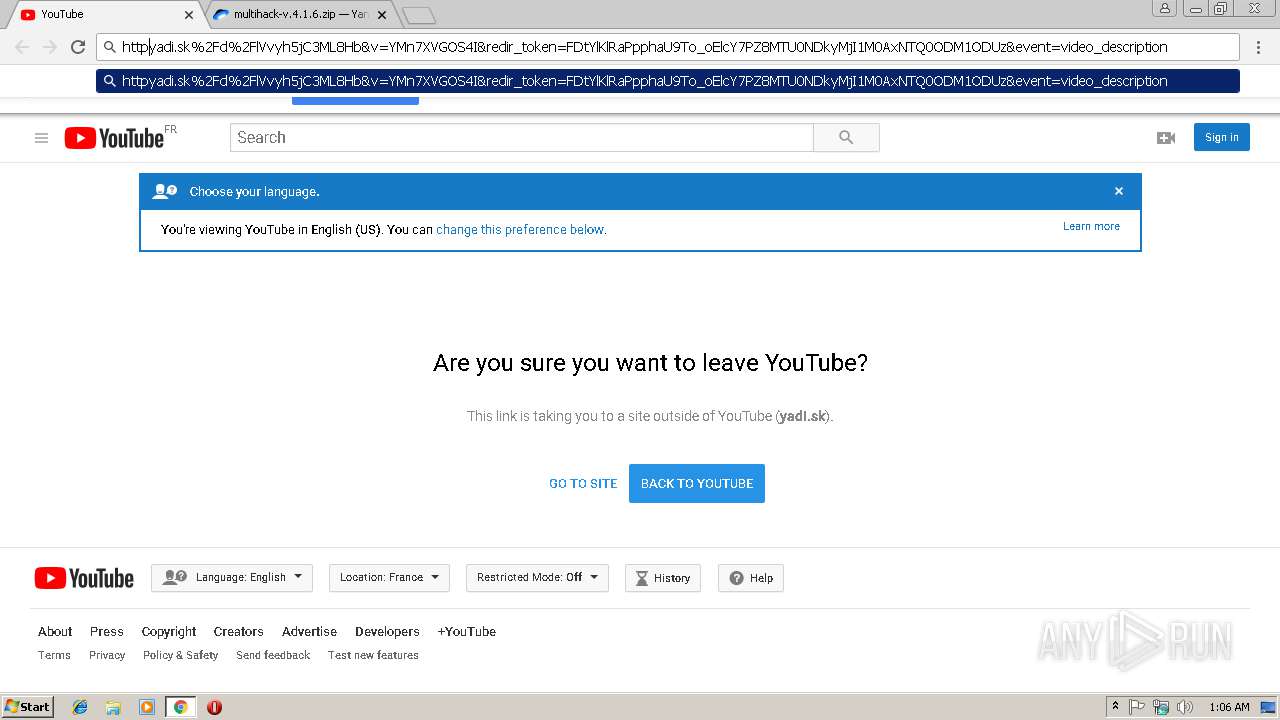
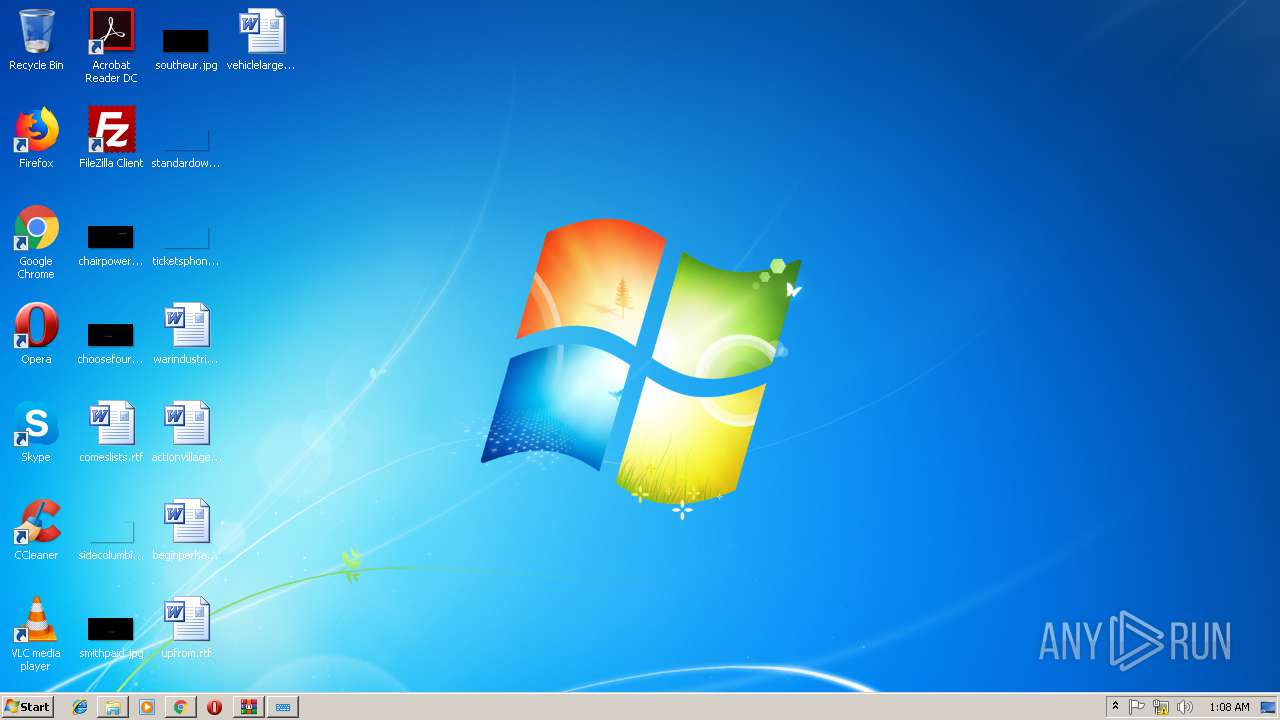
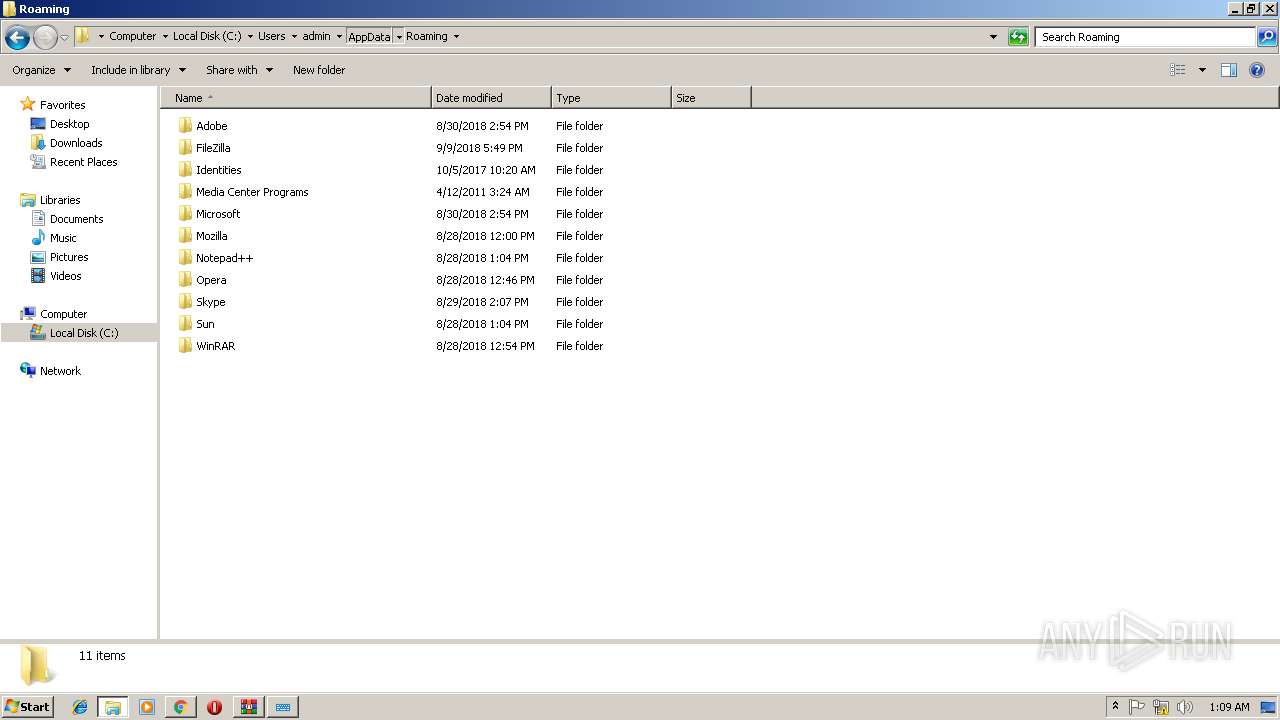
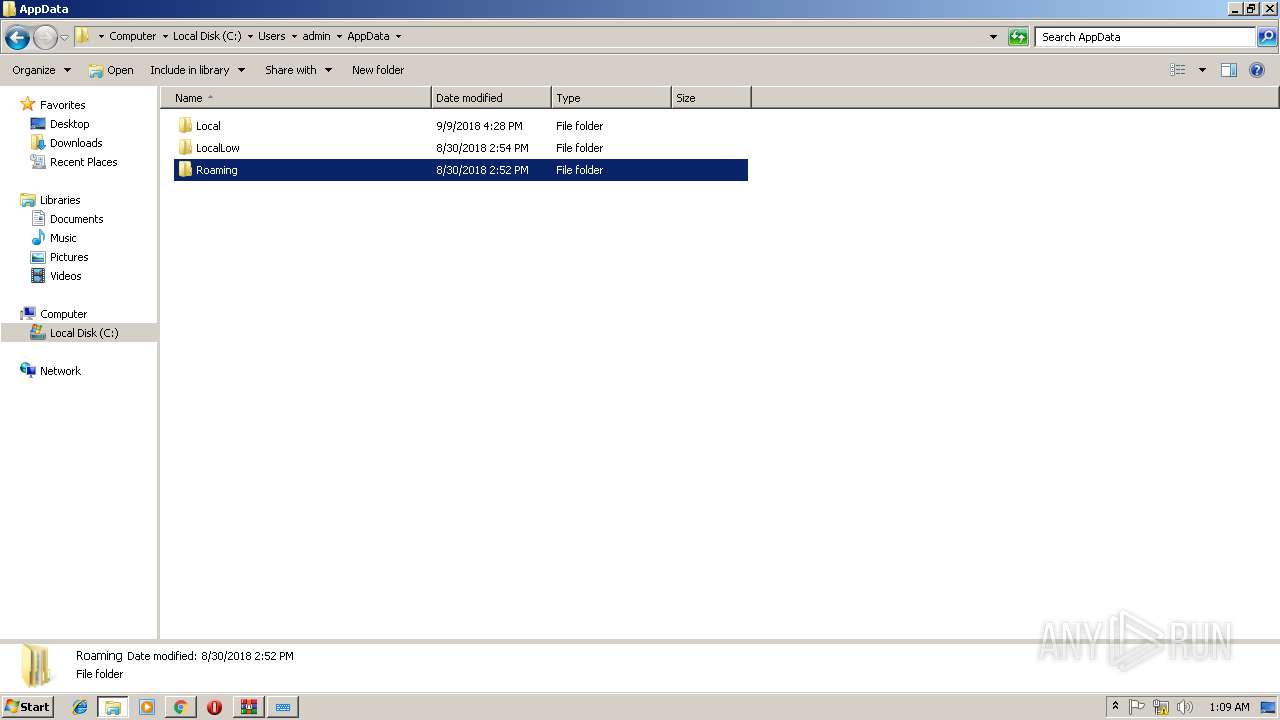
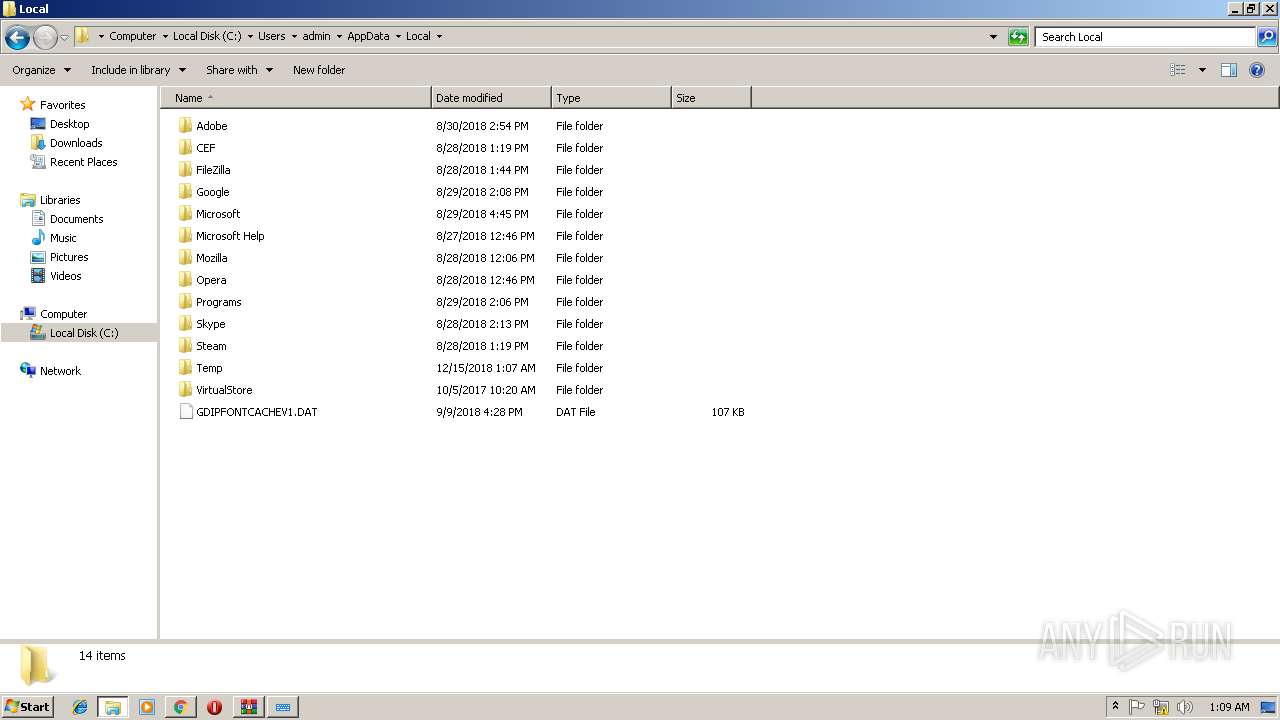
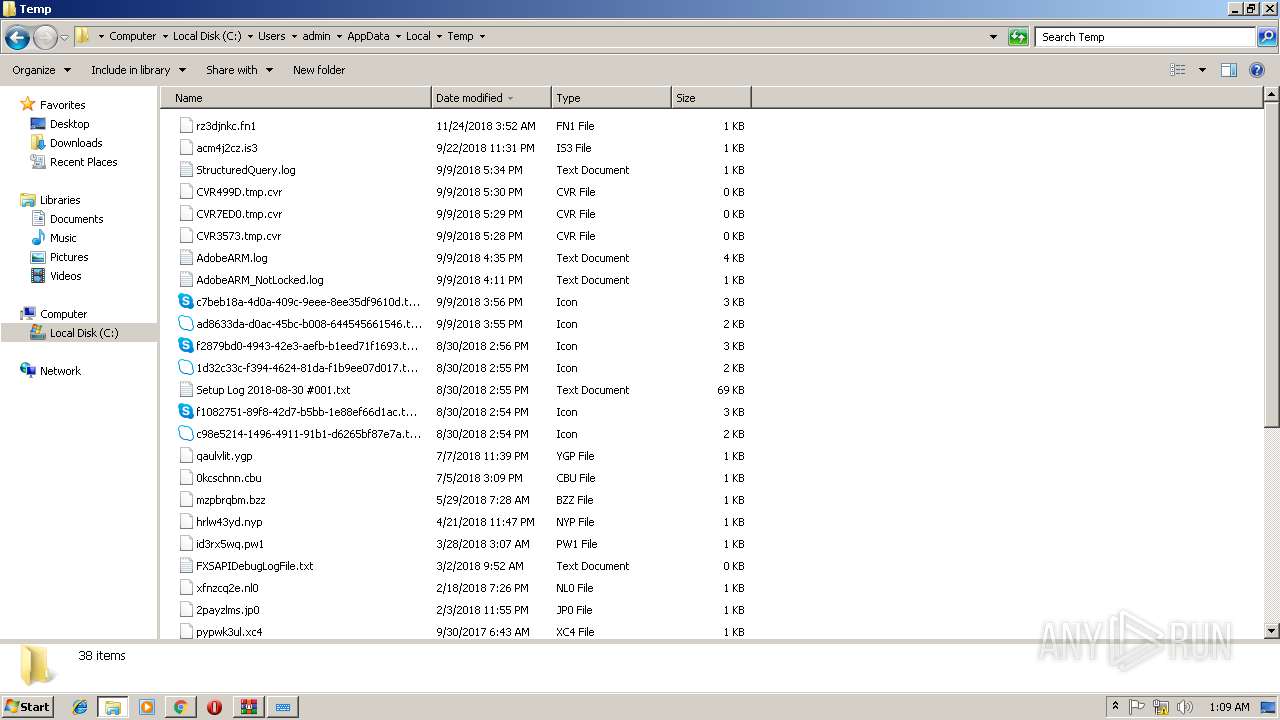
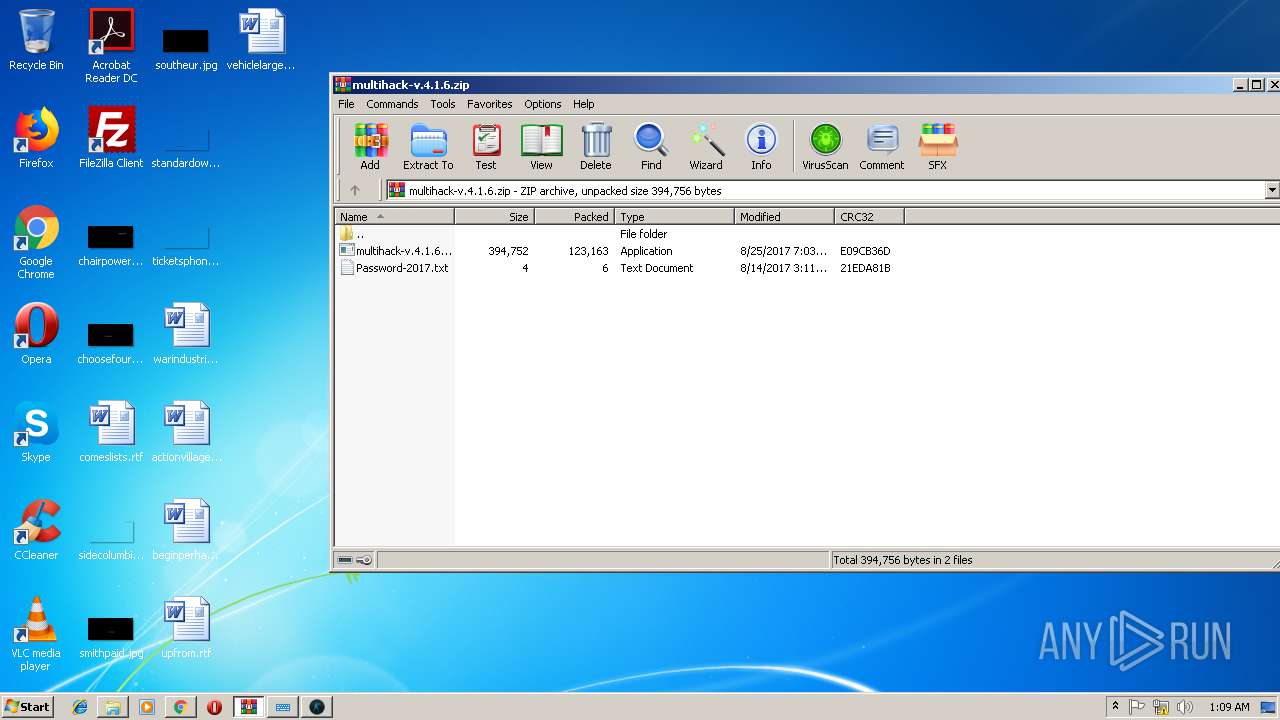
| URL: | https://www.youtube.com/redirect?q=https%3A%2F%2Fyadi.sk%2Fd%2FlVvyh5jC3ML8Hb&v=YMn7XVGOS4I&redir_token=FDtYlKlRaPpphaU9To_oElcY7PZ8MTU0NDkyMjI1M0AxNTQ0ODM1ODUz&event=video_description |
| Full analysis: | https://app.any.run/tasks/0660b800-fcf3-40c0-9c74-51a7d27a12e4 |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2018, 01:05:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
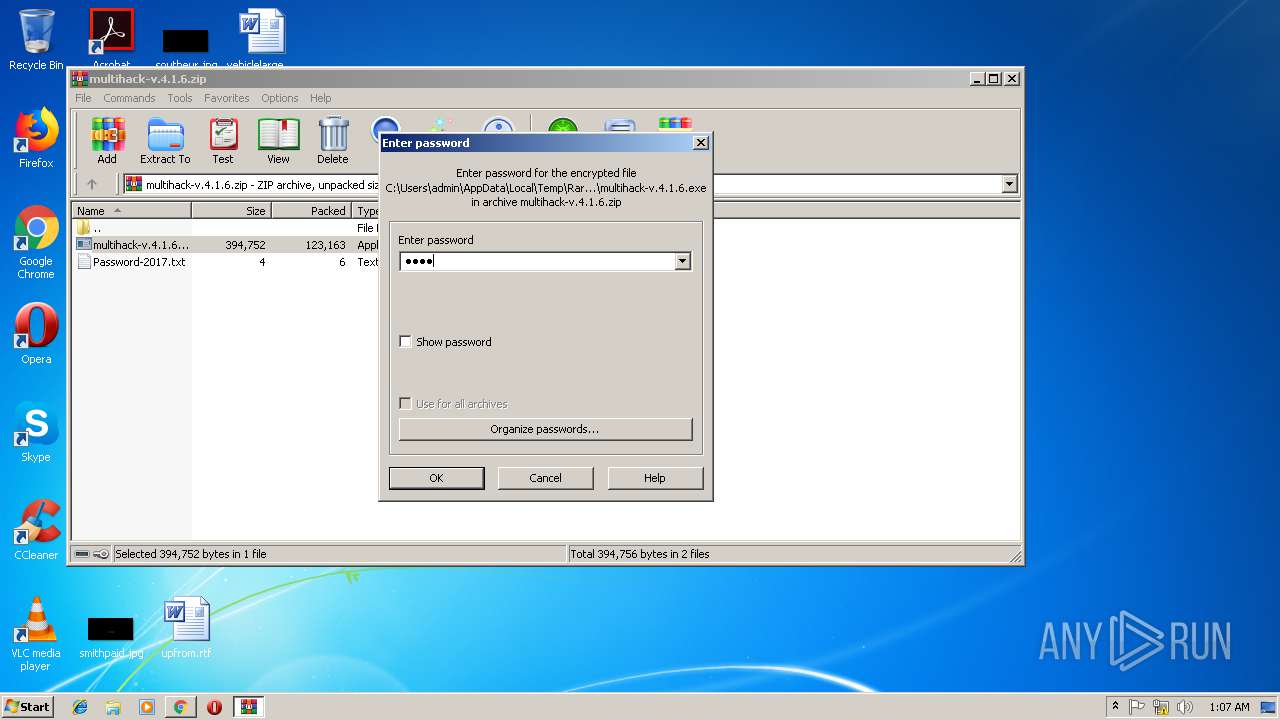
| Indicators: | |
| MD5: | 63DDF40FD0EC8B59D9F54EFDB3EF8FEC |
| SHA1: | 3621EC778AECE39050DD90E3C4EB8F118E10F9A5 |
| SHA256: | D1E45094C22C977058D8C5BA1357415BE9745CEFD6DEFCDAC6551A611905A380 |
| SSDEEP: | 3:N8DSLUxGTKXtWNRWCXjLK4j2Xj9UWOPb9zJ25B97mvEfK2BoqyOxCUqmv+ABv6Nn:2OLUxGKW5zFjfJRzWB97mFO0/RN |
MALICIOUS
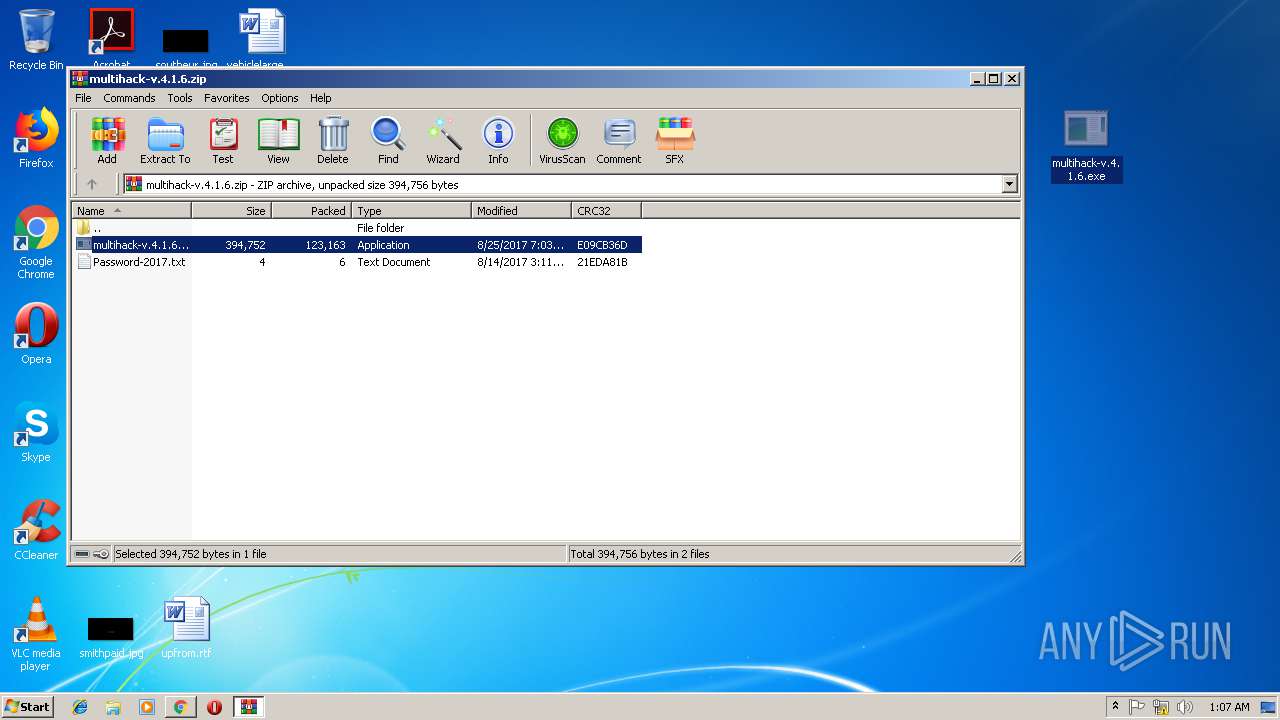
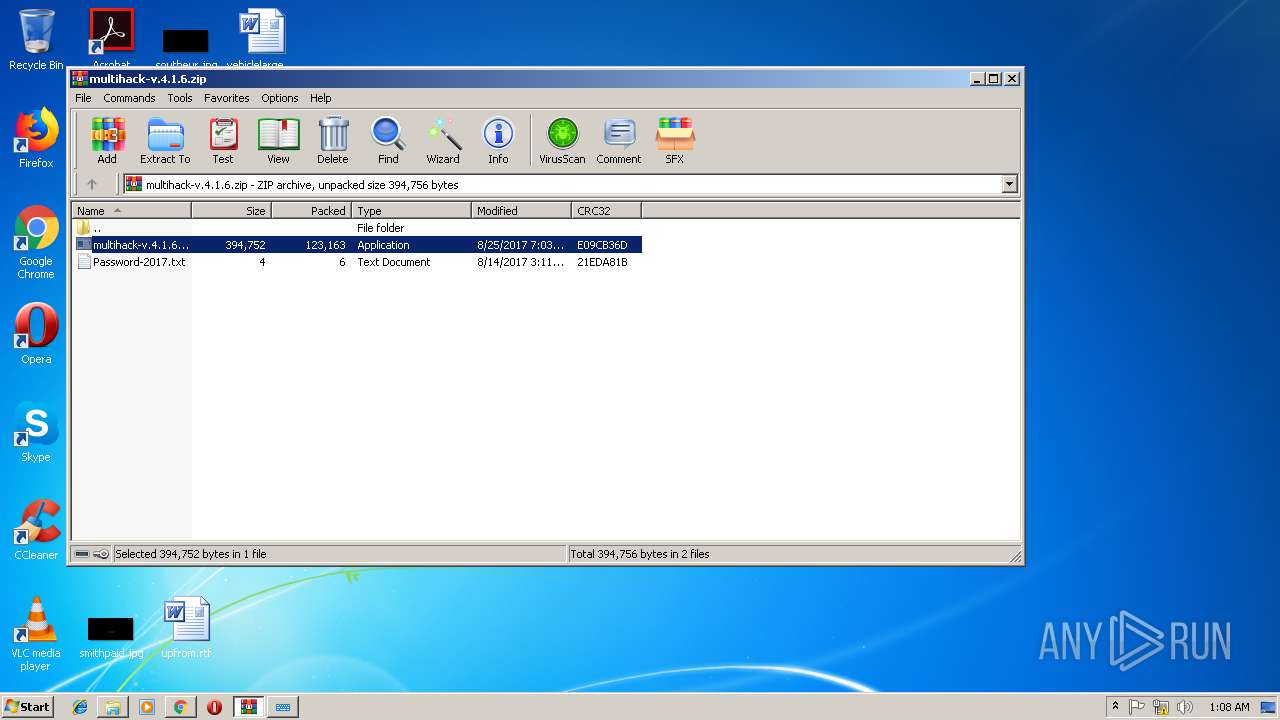
Application was dropped or rewritten from another process
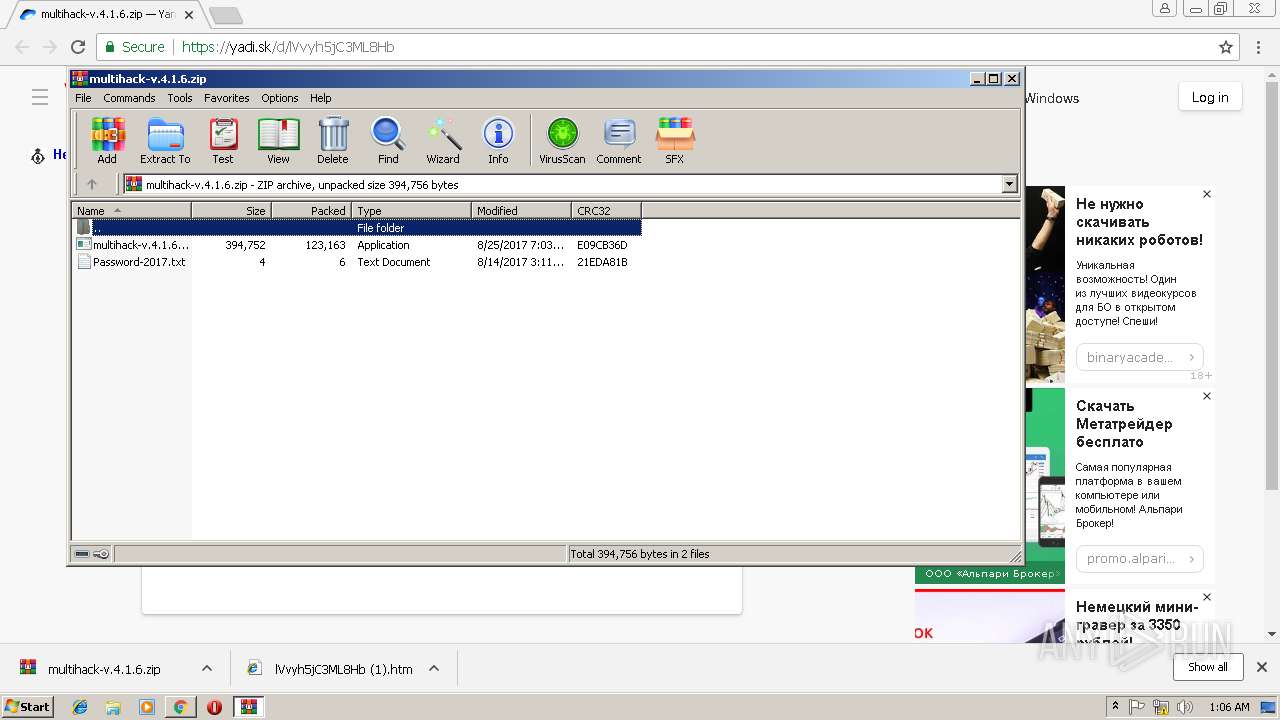
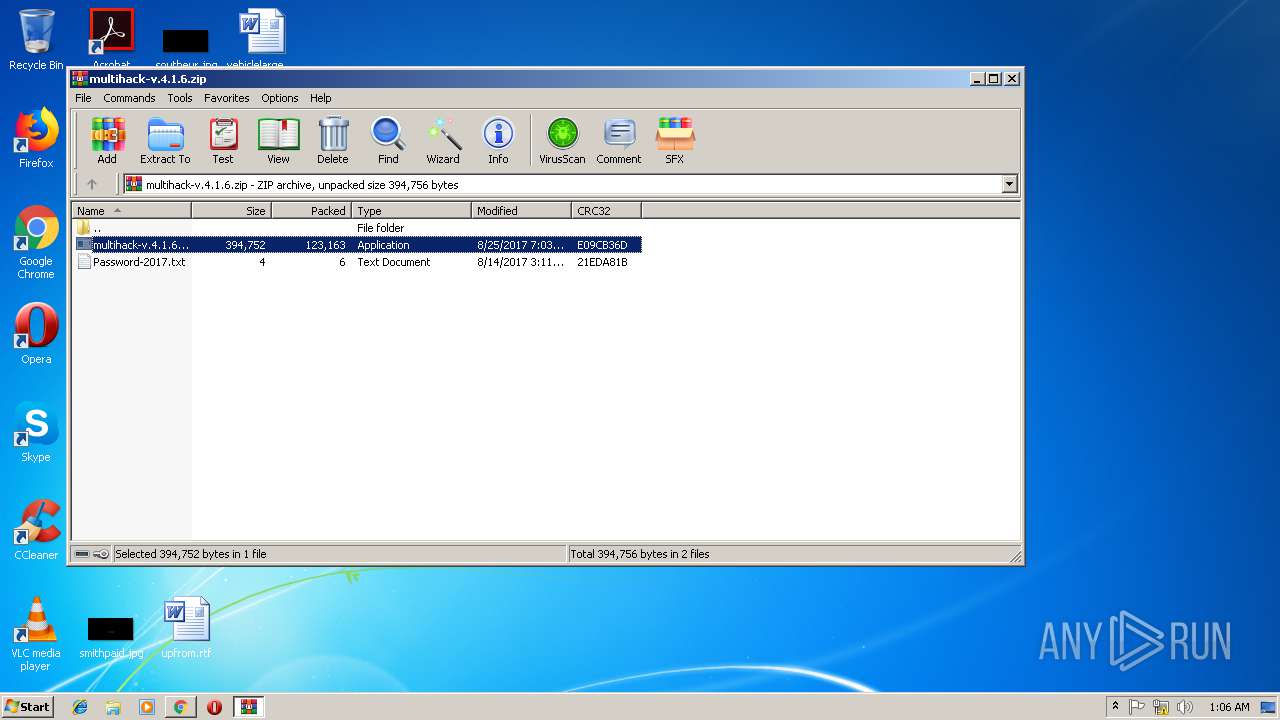
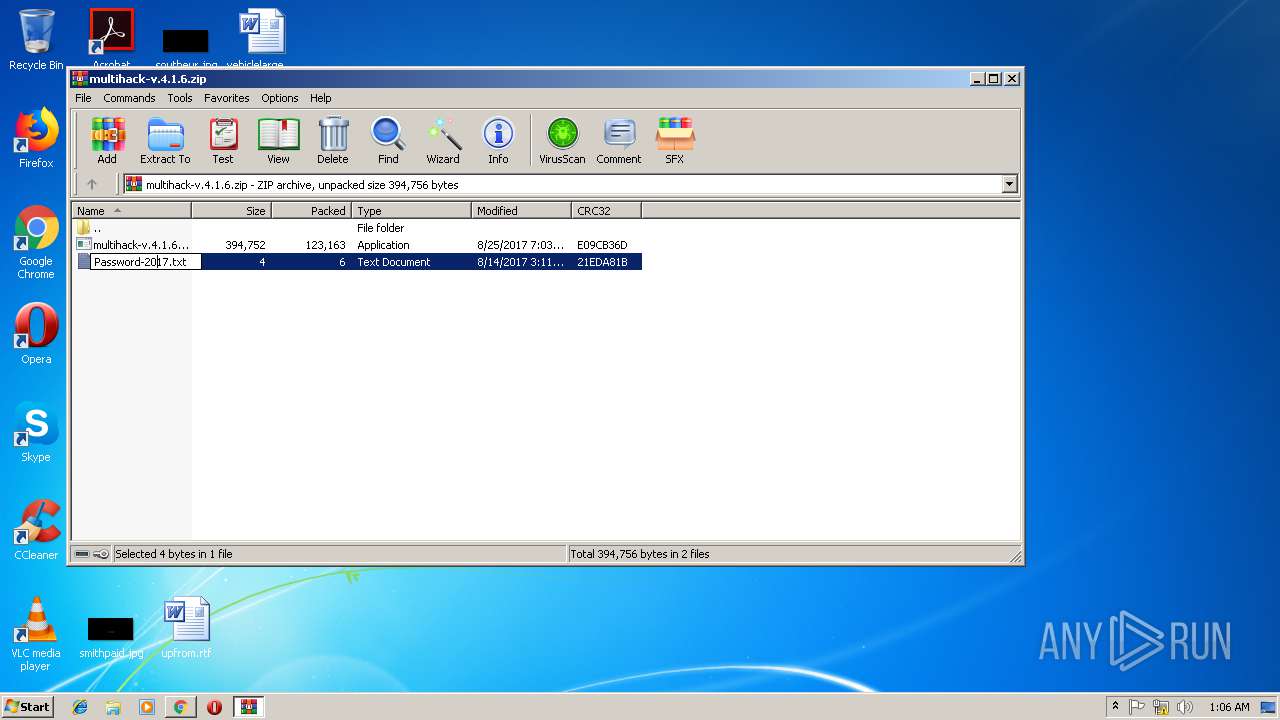
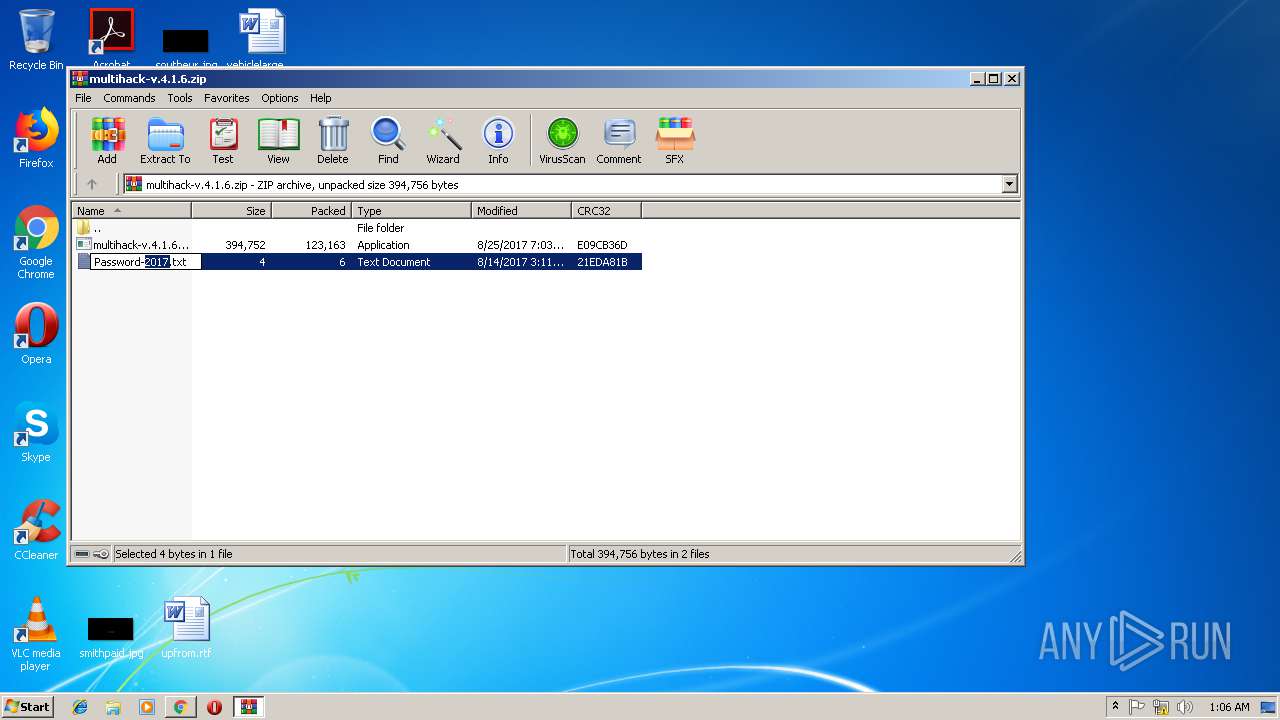
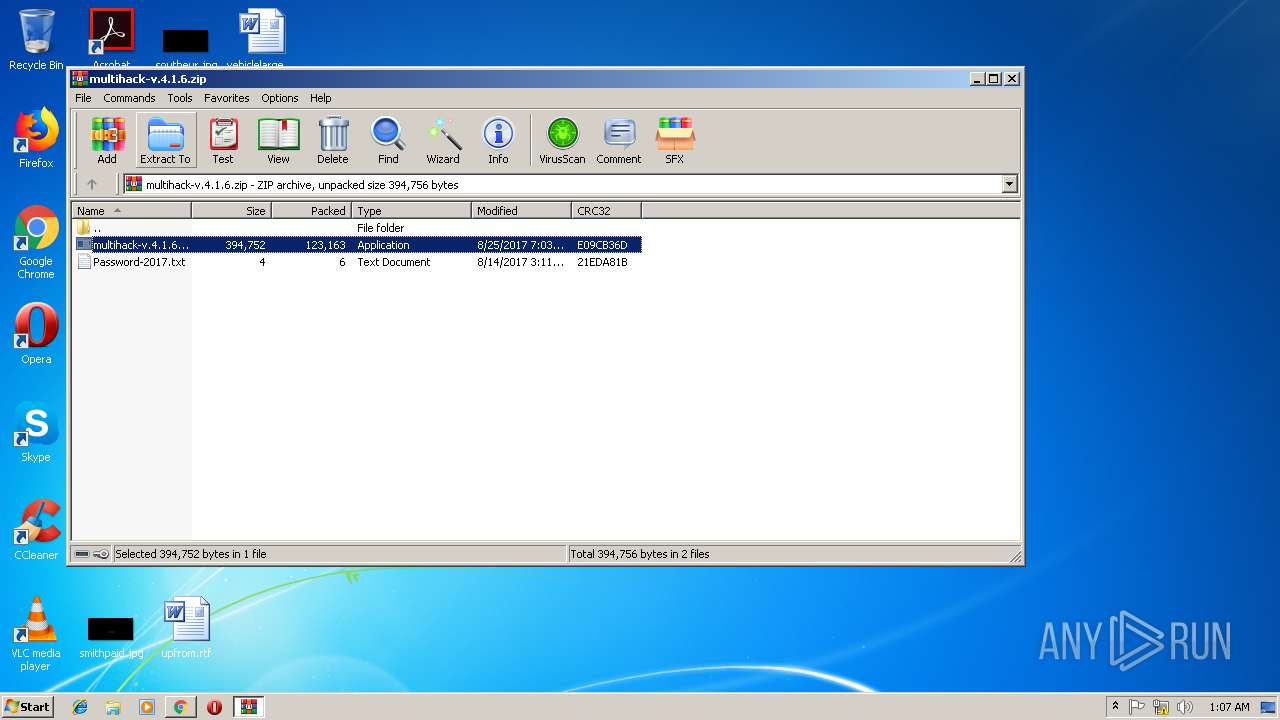
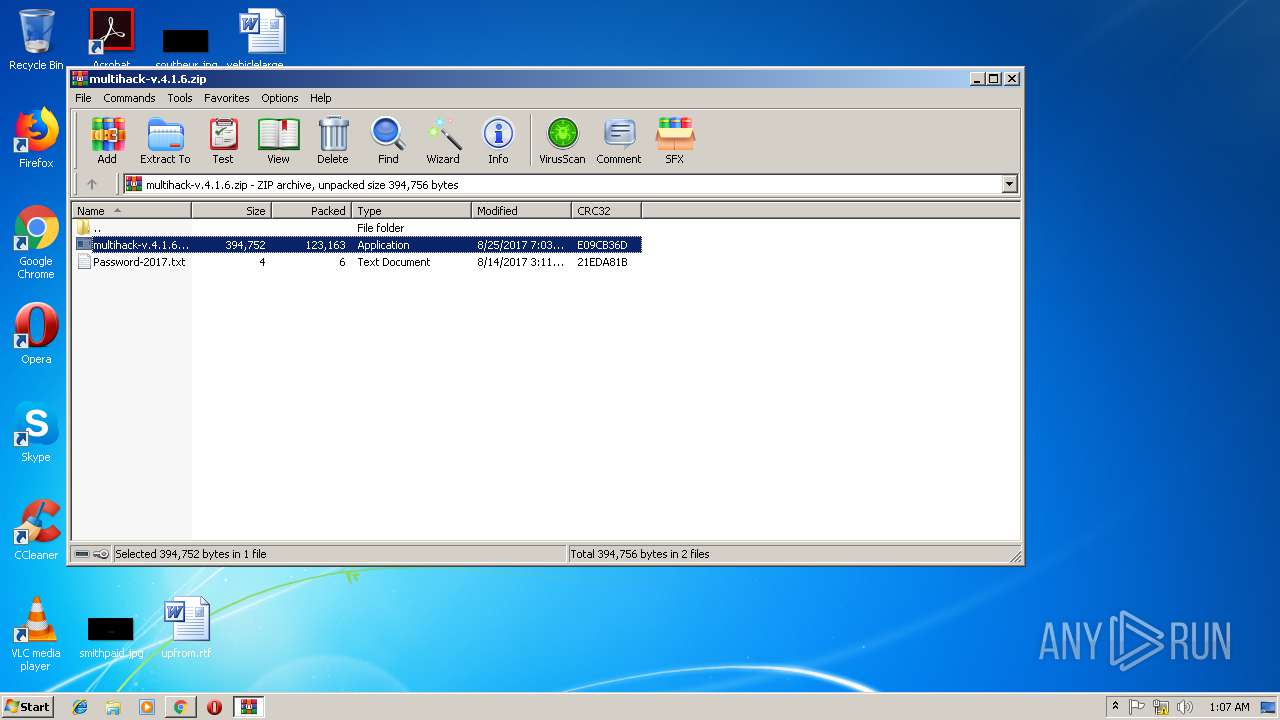
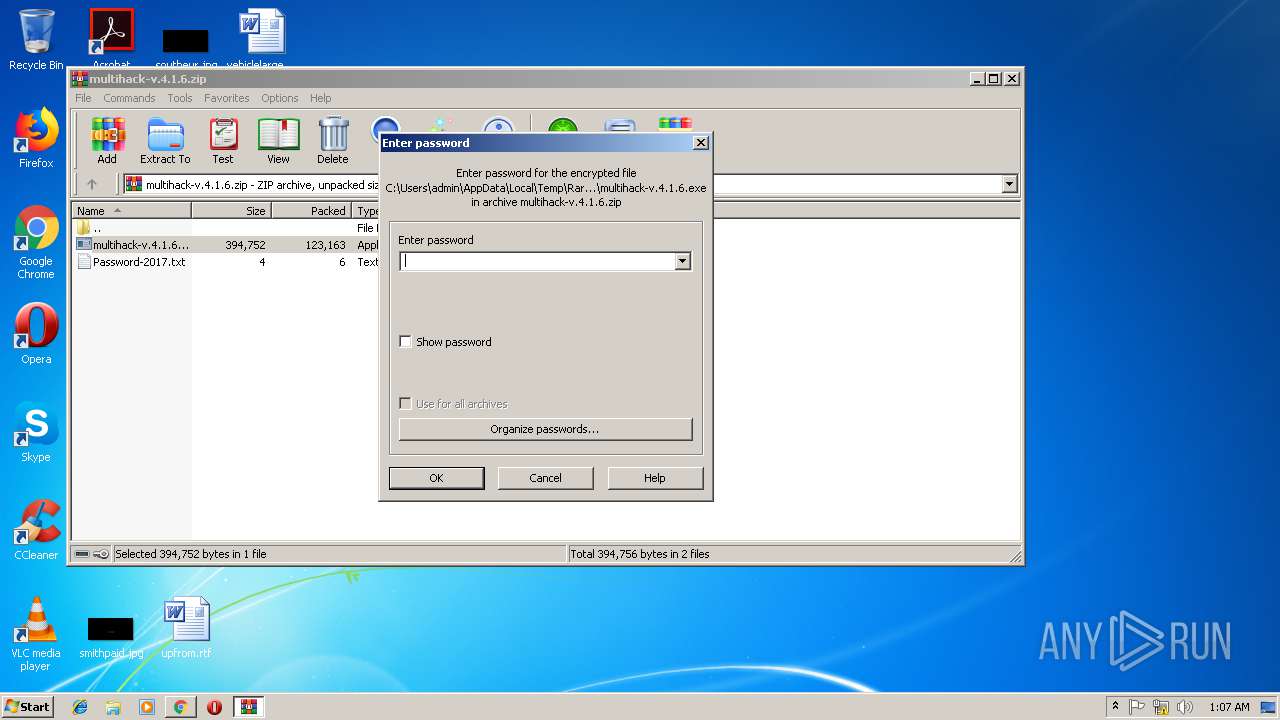
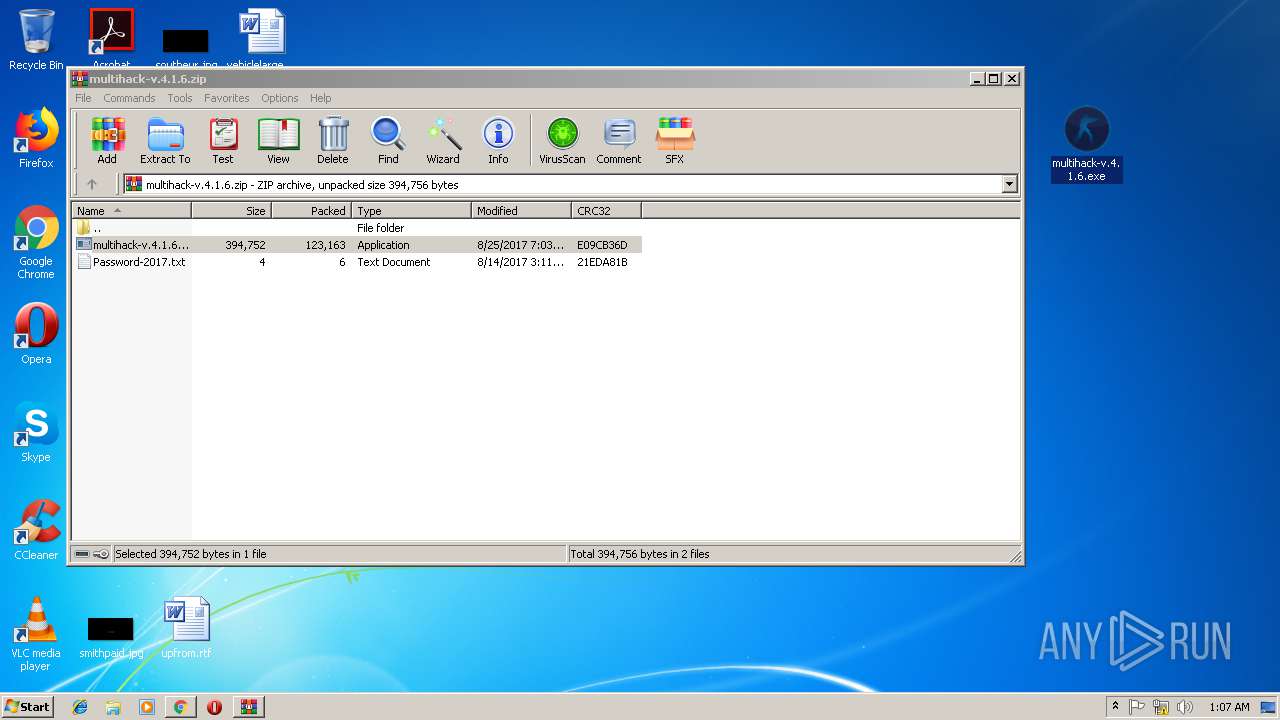
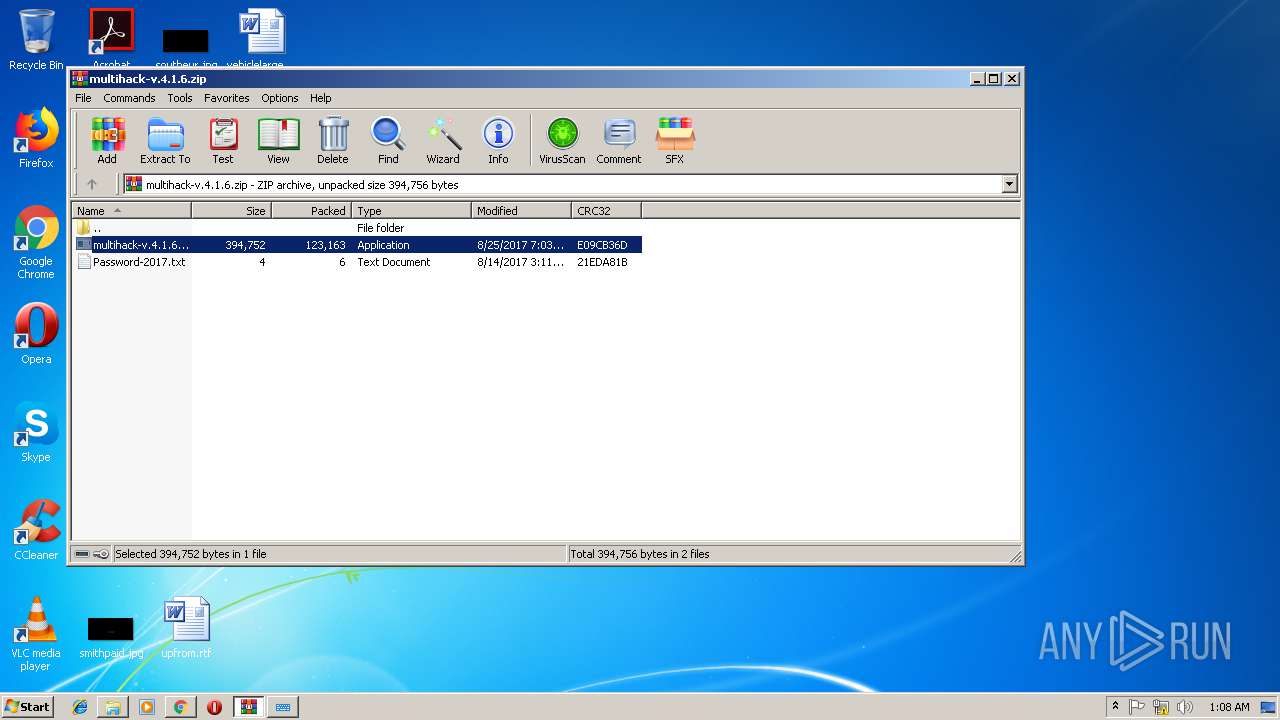
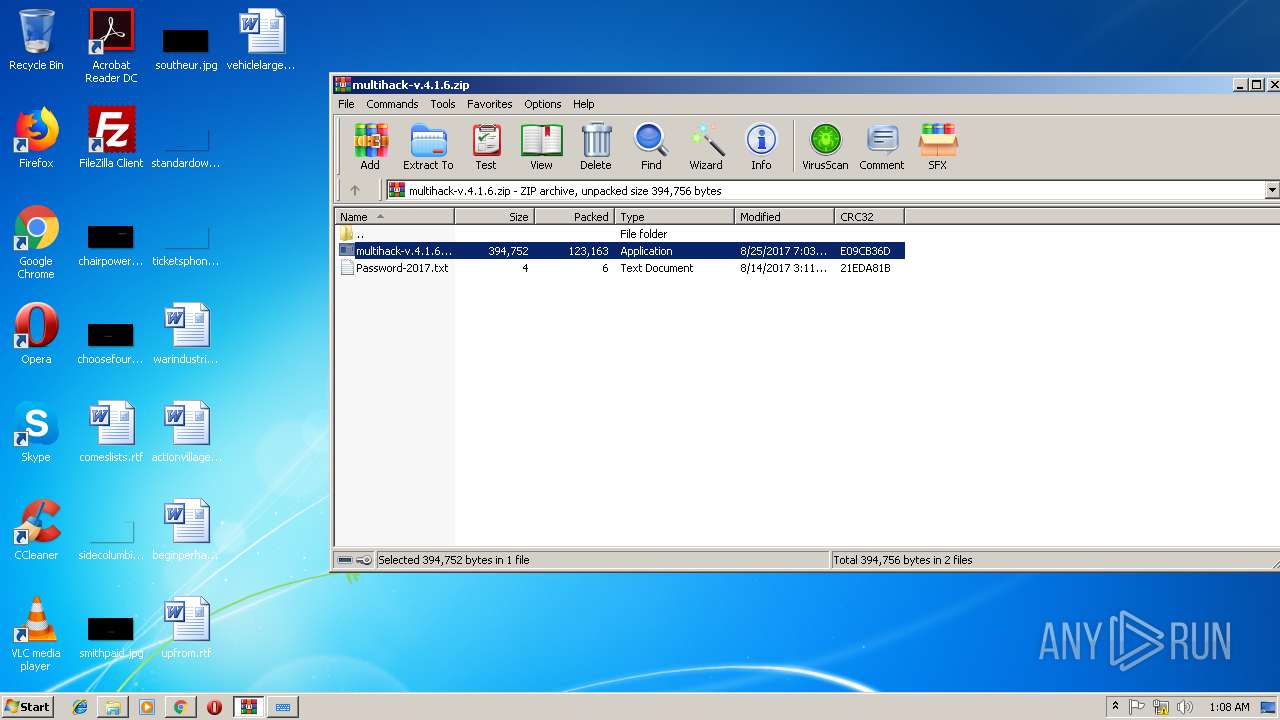
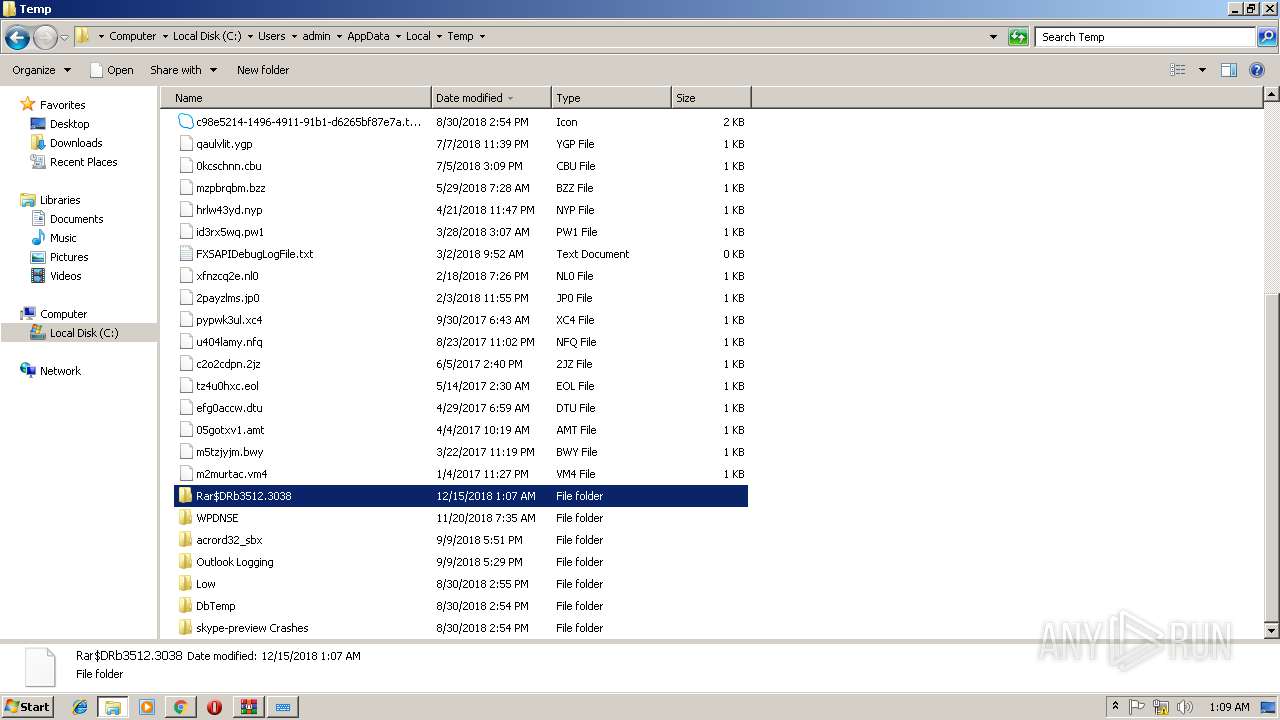
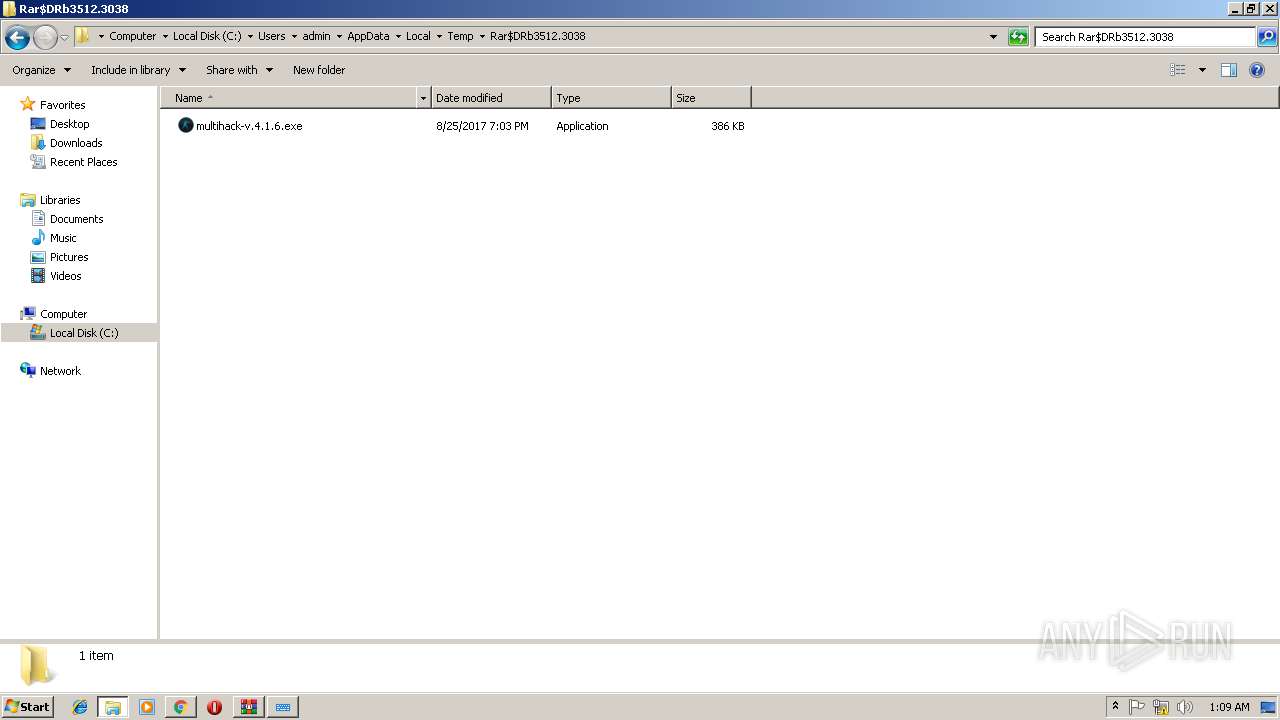
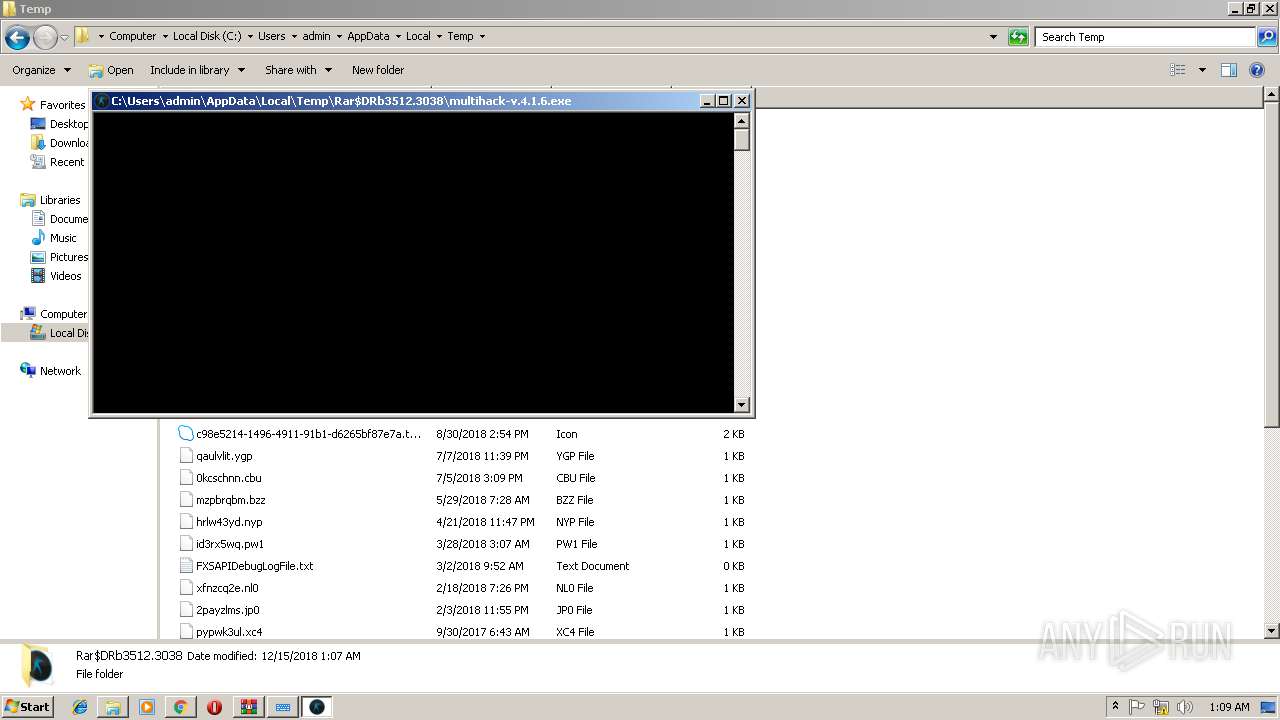
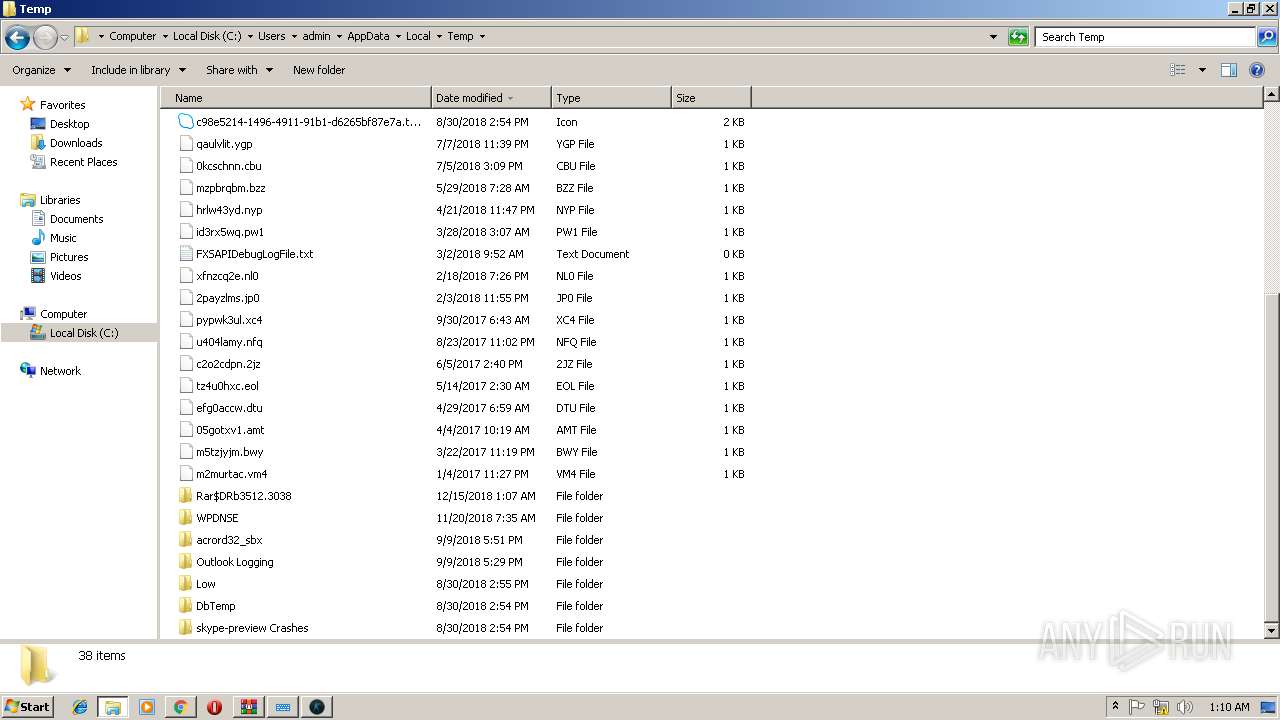
- multihack-v.4.1.6.exe (PID: 2912)
- multihack-v.4.1.6.exe (PID: 3756)
SUSPICIOUS
Connects to unusual port
- multihack-v.4.1.6.exe (PID: 2912)
- multihack-v.4.1.6.exe (PID: 3756)
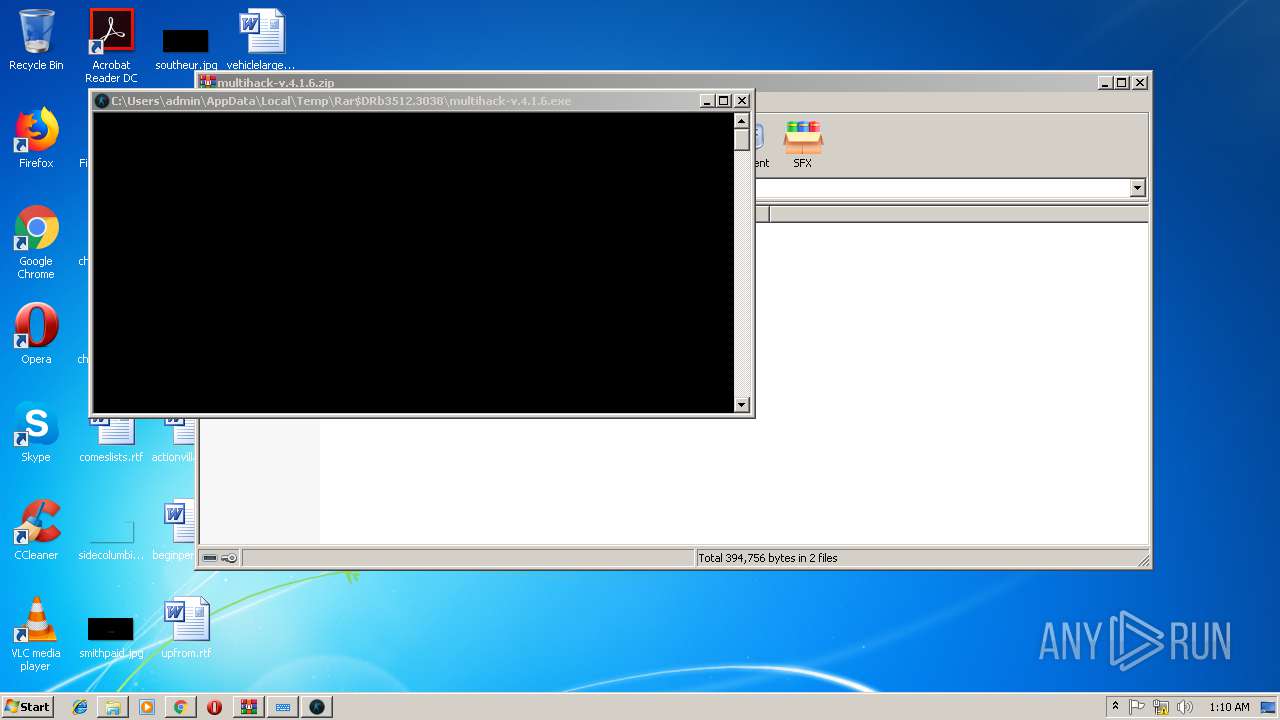
Executable content was dropped or overwritten
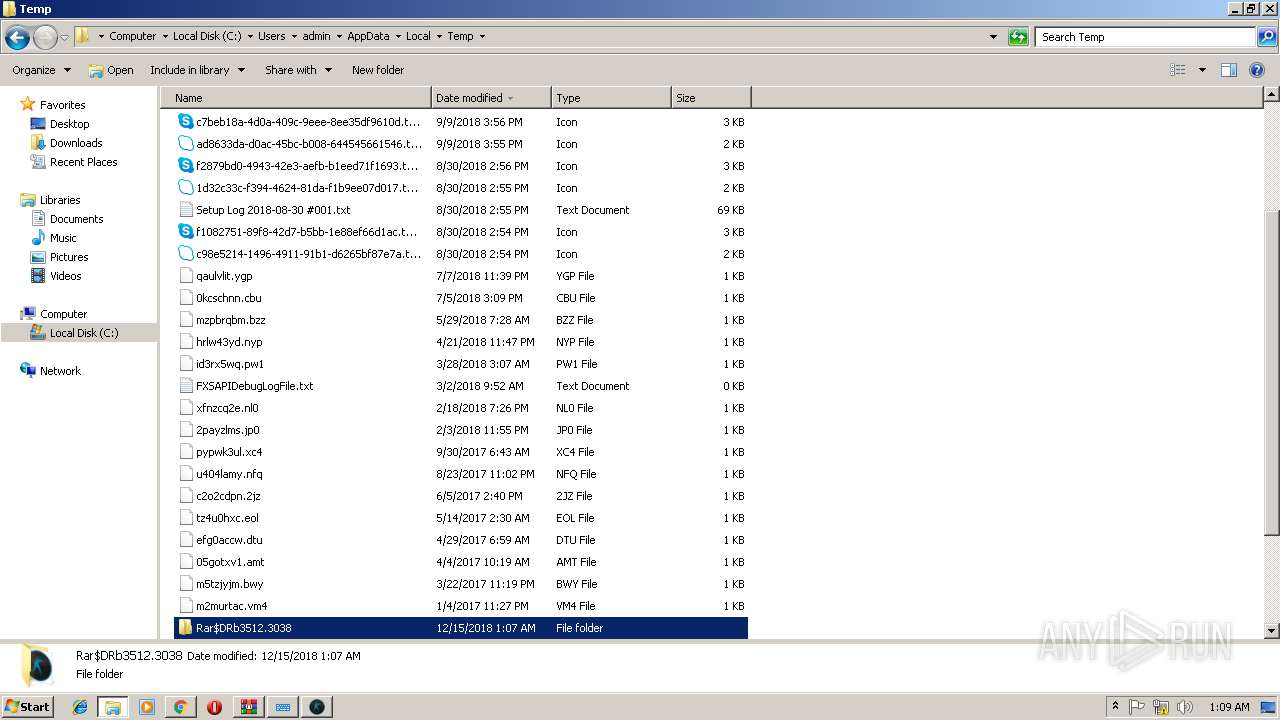
- WinRAR.exe (PID: 3512)
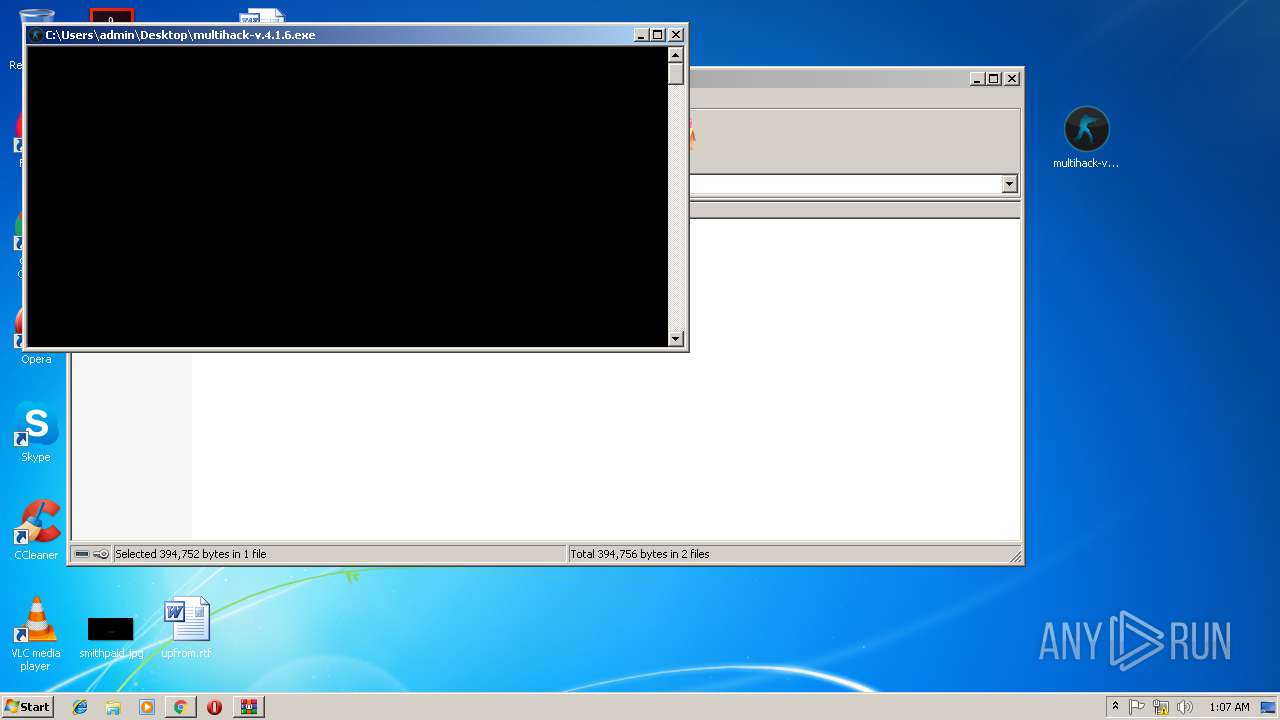
Starts CMD.EXE for commands execution
- multihack-v.4.1.6.exe (PID: 2912)
- multihack-v.4.1.6.exe (PID: 3756)
INFO
Application launched itself
- chrome.exe (PID: 2968)
Creates files in the user directory
- chrome.exe (PID: 2968)
Reads Microsoft Office registry keys
- chrome.exe (PID: 2968)
Reads Internet Cache Settings
- chrome.exe (PID: 2968)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
26
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1916 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,1271383365220138652,16944992696421106841,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=E4C7F16925935359B7620EBD097AD2A6 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=E4C7F16925935359B7620EBD097AD2A6 --renderer-client-id=8 --mojo-platform-channel-handle=2368 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2420 | "C:\Windows\system32\osk.exe" | C:\Windows\system32\osk.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Accessibility On-Screen Keyboard Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
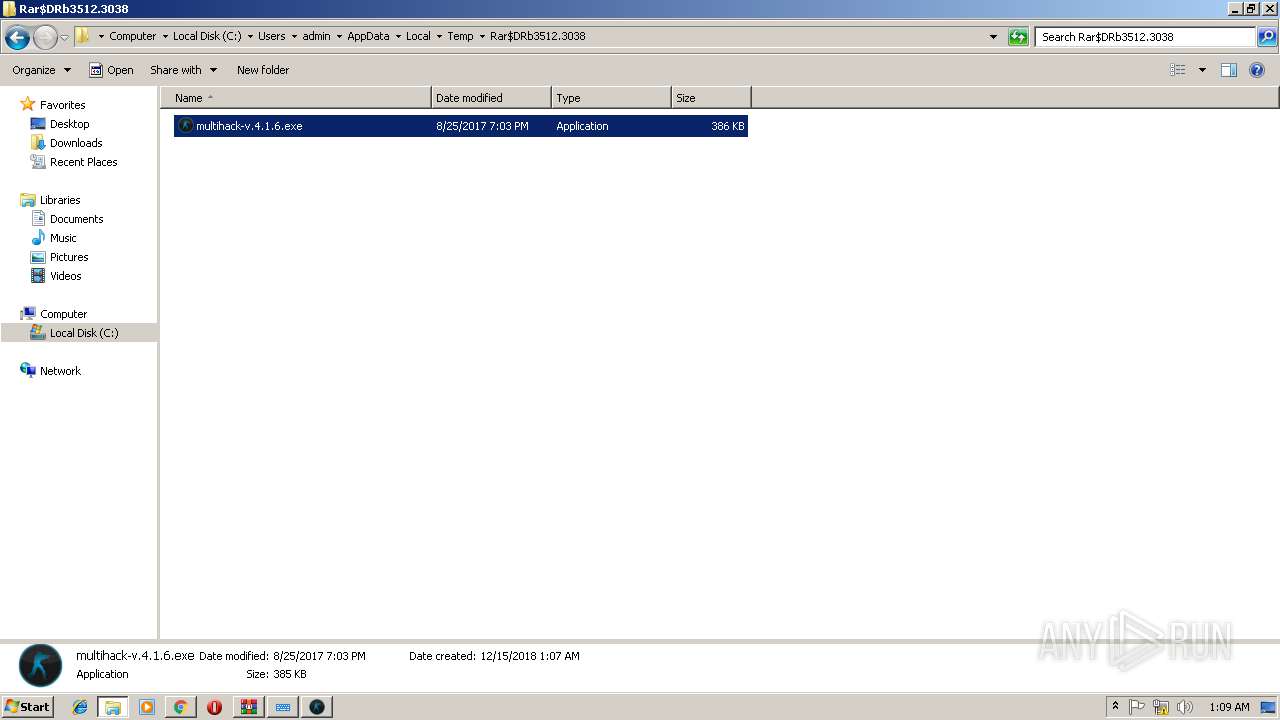
| 2444 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Rar$DRb3512.3038\update.bat" " | C:\Windows\system32\cmd.exe | — | multihack-v.4.1.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2444 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES1AF1.tmp" "c:\Users\admin\AppData\Local\Temp\CSC16125419C5C74D94BCFEE257B6CA2CD8.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 12.00.52512.0 built by: VSWINSERVICING Modules
| |||||||||||||||
| 2564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,1271383365220138652,16944992696421106841,131072 --enable-features=PasswordImport --service-pipe-token=6594FA022F0CF9BA49D6BA57F21202F0 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6594FA022F0CF9BA49D6BA57F21202F0 --renderer-client-id=4 --mojo-platform-channel-handle=1908 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2632 | "C:\Windows\system32\osk.exe" | C:\Windows\system32\osk.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Accessibility On-Screen Keyboard Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2644 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=988,1271383365220138652,16944992696421106841,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=F77E7C0AC9ACD4685A97D231FB9B6490 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=F77E7C0AC9ACD4685A97D231FB9B6490 --renderer-client-id=6 --mojo-platform-channel-handle=4120 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2812 | cmd /c ""C:\Users\admin\Desktop\update.bat" " | C:\Windows\system32\cmd.exe | — | multihack-v.4.1.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2820 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\do3r1iyw.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | multihack-v.4.1.6.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2972 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
Total events
2 246
Read events
1 899
Write events
343
Delete events
4
Modification events
| (PID) Process: | (2908) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2968-13189309528904375 |
Value: 259 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2968-13189309528904375 |
Value: 259 | |||
| (PID) Process: | (2968) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
1
Suspicious files
49
Text files
122
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\83f5afba-a556-4815-9882-34b2f247f92e.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\e7b7270c-7748-4e3f-be8e-b5e89dc1b0a8.tmp | — | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF246b1e.TMP | text | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF246b4d.TMP | text | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2968 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old~RF246f45.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
77
DNS requests
48
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2968 | chrome.exe | 87.250.250.90:443 | an.yandex.ru | YANDEX LLC | RU | whitelisted |
2968 | chrome.exe | 172.217.16.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
2968 | chrome.exe | 77.88.21.36:443 | favicon.yandex.net | YANDEX LLC | RU | whitelisted |
2968 | chrome.exe | 87.250.247.181:443 | avatars.mds.yandex.net | YANDEX LLC | RU | whitelisted |
2968 | chrome.exe | 87.250.250.114:443 | ysa-static.passport.yandex.ru | YANDEX LLC | RU | whitelisted |
2968 | chrome.exe | 87.240.182.224:443 | vk.com | VKontakte Ltd | RU | unknown |
2968 | chrome.exe | 64.233.184.198:443 | www.youtube.com | Google Inc. | US | whitelisted |
2968 | chrome.exe | 172.217.21.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
2968 | chrome.exe | 172.217.22.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2968 | chrome.exe | 216.58.207.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.gstatic.com |
| whitelisted |
www.youtube.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.gstatic.com |
| whitelisted |
s.ytimg.com |
| whitelisted |
yadi.sk |
| shared |
sb-ssl.google.com |
| whitelisted |
yastatic.net |
| whitelisted |
mc.yandex.ru |
| whitelisted |