| File name: | 1.exe |
| Full analysis: | https://app.any.run/tasks/2a80dbcd-3e29-4e02-b249-ecd2b278d3e2 |
| Verdict: | Malicious activity |
| Threats: | INC Ransomware is a ransomware-as-a-service (RaaS) spotted in mid-2023. It targets industries like retail, real estate, finance, healthcare, and education, primarily in the U.S. and UK. It encrypts and exfiltrates data demanding a ransom. It employs advanced evasion techniques, destroys backup, and abuses legitimate system tools at all the stages of the kill chain. |
| Analysis date: | December 14, 2024, 18:09:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | FB14AAE2ED93A7DDFA718F433F585735 |
| SHA1: | 34EFA21245F1424BE44346B2DC0698844DD30F3F |
| SHA256: | D1E0CAC795C8F8EF7080D0C96F0240EA18F15D56EE5A17BB6595AF01AA641E11 |
| SSDEEP: | 3072:BUViX88MYMorfeSEQvVYxVZ/cY+aci6V5SoksuJBrfuaOxlMEZsPeB2D4eEGzMWX:OiLCSEVcio5S0kByvQEgNX |
MALICIOUS
RANSOMWARE has been detected
- 1.exe (PID: 6312)
Renames files like ransomware
- 1.exe (PID: 6312)
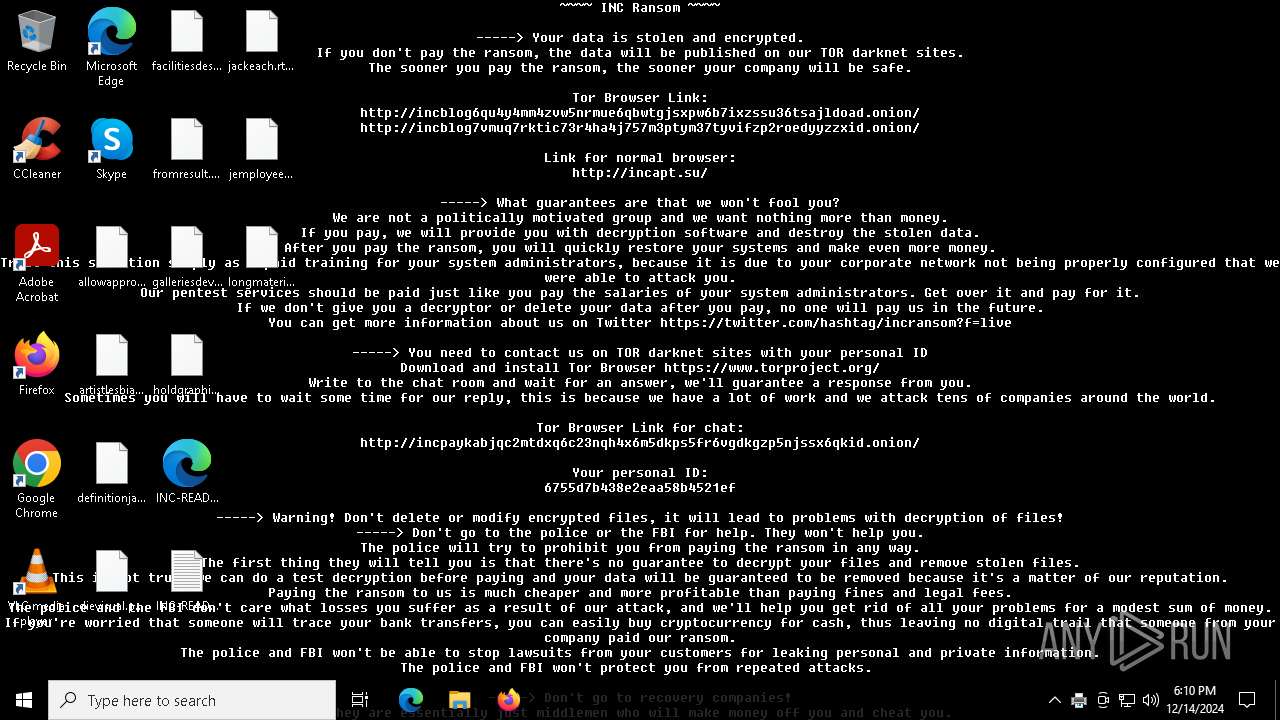
INC has been detected
- 1.exe (PID: 6312)
INC has been detected (YARA)
- 1.exe (PID: 6312)
INC note has been found
- 1.exe (PID: 6312)
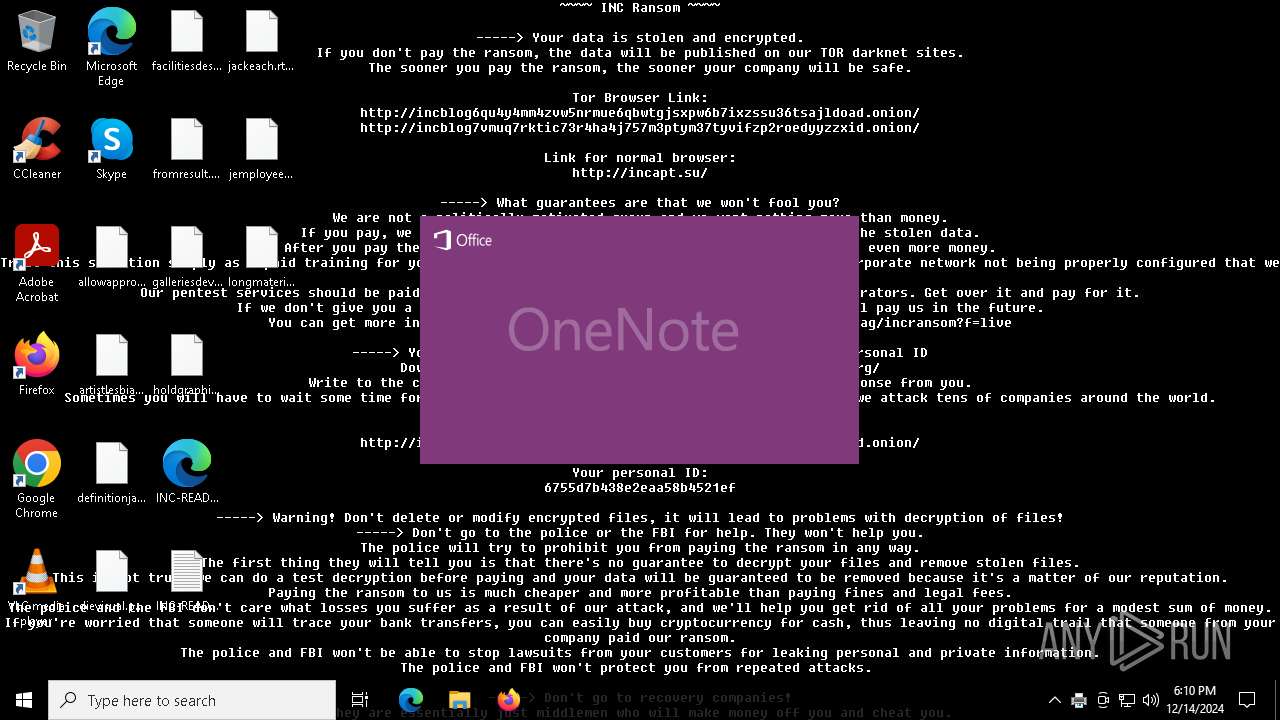
Scans artifacts that could help determine the target
- ONENOTE.EXE (PID: 6164)
SUSPICIOUS
Changes the desktop background image
- 1.exe (PID: 6312)
Executes as Windows Service
- FXSSVC.exe (PID: 6392)
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 6164)
Reads security settings of Internet Explorer
- ONENOTE.EXE (PID: 6164)
Reads the date of Windows installation
- ONENOTE.EXE (PID: 6164)
Checks Windows Trust Settings
- ONENOTE.EXE (PID: 6164)
INFO
Create files in a temporary directory
- 1.exe (PID: 6312)
- ONENOTE.EXE (PID: 6164)
Creates files or folders in the user directory
- 1.exe (PID: 6312)
- printfilterpipelinesvc.exe (PID: 9048)
- ONENOTE.EXE (PID: 6164)
Creates files in the program directory
- 1.exe (PID: 6312)
- FXSSVC.exe (PID: 6392)
Reads the machine GUID from the registry
- 1.exe (PID: 6312)
- ONENOTE.EXE (PID: 6164)
Reads the computer name
- 1.exe (PID: 6312)
- ONENOTE.EXE (PID: 6164)
Checks supported languages
- 1.exe (PID: 6312)
- ONENOTE.EXE (PID: 6164)
Reads security settings of Internet Explorer
- printfilterpipelinesvc.exe (PID: 9048)
Disables trace logs
- FXSSVC.exe (PID: 6392)
Reads Microsoft Office registry keys
- ONENOTE.EXE (PID: 6164)
Reads Environment values
- ONENOTE.EXE (PID: 6164)
Checks proxy server information
- ONENOTE.EXE (PID: 6164)
Reads product name
- ONENOTE.EXE (PID: 6164)
Sends debugging messages
- ONENOTE.EXE (PID: 6164)
Process checks computer location settings
- ONENOTE.EXE (PID: 6164)
Reads CPU info
- ONENOTE.EXE (PID: 6164)
Reads the software policy settings
- ONENOTE.EXE (PID: 6164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:04:09 08:25:18+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 105472 |
| InitializedDataSize: | 61952 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9a34 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows command line |
Total processes
138
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6164 | /insertdoc "C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\{EC03BED0-C788-477D-9AE5-55809D64A596}.xps" 133786734437930000 | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | printfilterpipelinesvc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6312 | "C:\Users\admin\AppData\Local\Temp\1.exe" | C:\Users\admin\AppData\Local\Temp\1.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6392 | C:\WINDOWS\system32\fxssvc.exe | C:\Windows\System32\FXSSVC.exe | — | services.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Fax Service Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 9048 | C:\WINDOWS\system32\printfilterpipelinesvc.exe -Embedding | C:\Windows\System32\printfilterpipelinesvc.exe | — | svchost.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Print Filter Pipeline Host Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 246
Read events
6 015
Write events
219
Delete events
12
Modification events
| (PID) Process: | (6312) 1.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | Wallpaper |
Value: C:\Users\admin\AppData\Local\Temp\\background-image.jpg | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | Server |
Value: | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | From |
Value: | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Receipts |
| Operation: | write | Name: | User |
Value: | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Groups\<All devices> |
| Operation: | write | Name: | Devices |
Value: | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Rules\0:0 |
| Operation: | write | Name: | CountryCode |
Value: 0 | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Rules\0:0 |
| Operation: | write | Name: | AreaCode |
Value: 0 | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Rules\0:0 |
| Operation: | write | Name: | UseGroup |
Value: 1 | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax\Outbound Routing\Rules\0:0 |
| Operation: | write | Name: | GroupName |
Value: <All devices> | |||
| (PID) Process: | (6392) FXSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Fax |
| Operation: | write | Name: | JobQueueTimeout |
Value: 600 | |||
Executable files
1
Suspicious files
528
Text files
534
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6312 | 1.exe | C:\ProgramData\Adobe\ARM\Acrobat_23.001.20093\AcroRdrDCx64Upd2300820470_MUI.msp | — | |
MD5:— | SHA256:— | |||
| 6312 | 1.exe | C:\ProgramData\INC-README.txt | text | |
MD5:FA10BAA9160DD6FEB78F89362088E804 | SHA256:779871CD60C04B16C6CB6F0702FC76A9EB70FE3885192A00A61A7A0DE575BA65 | |||
| 6312 | 1.exe | C:\ProgramData\INC-README.html | html | |
MD5:E9B887D02B9616003877786FA48A5CC8 | SHA256:FFBF4FFCD386A49C22D338403496661D32B2DA8C8B94162A7A0F575530330493 | |||
| 6312 | 1.exe | C:\Users\admin\AppData\Local\VirtualStore\INC-README.txt | text | |
MD5:FA10BAA9160DD6FEB78F89362088E804 | SHA256:779871CD60C04B16C6CB6F0702FC76A9EB70FE3885192A00A61A7A0DE575BA65 | |||
| 6312 | 1.exe | C:\Users\admin\AppData\Local\VirtualStore\INC-README.html | html | |
MD5:E9B887D02B9616003877786FA48A5CC8 | SHA256:FFBF4FFCD386A49C22D338403496661D32B2DA8C8B94162A7A0F575530330493 | |||
| 6312 | 1.exe | C:\ProgramData\Adobe\ARM\Acrobat_23.001.20093\INC-README.html | html | |
MD5:E9B887D02B9616003877786FA48A5CC8 | SHA256:FFBF4FFCD386A49C22D338403496661D32B2DA8C8B94162A7A0F575530330493 | |||
| 6312 | 1.exe | C:\ProgramData\Adobe\INC-README.html | html | |
MD5:E9B887D02B9616003877786FA48A5CC8 | SHA256:FFBF4FFCD386A49C22D338403496661D32B2DA8C8B94162A7A0F575530330493 | |||
| 6312 | 1.exe | C:\ProgramData\Adobe\ARM\INC-README.txt | text | |
MD5:FA10BAA9160DD6FEB78F89362088E804 | SHA256:779871CD60C04B16C6CB6F0702FC76A9EB70FE3885192A00A61A7A0DE575BA65 | |||
| 6312 | 1.exe | C:\ProgramData\Adobe\INC-README.txt | text | |
MD5:FA10BAA9160DD6FEB78F89362088E804 | SHA256:779871CD60C04B16C6CB6F0702FC76A9EB70FE3885192A00A61A7A0DE575BA65 | |||
| 6312 | 1.exe | C:\ProgramData\Adobe\ARM\INC-README.html | html | |
MD5:E9B887D02B9616003877786FA48A5CC8 | SHA256:FFBF4FFCD386A49C22D338403496661D32B2DA8C8B94162A7A0F575530330493 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
38
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4308 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6564 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
8996 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8996 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4308 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
6164 | ONENOTE.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 104.126.37.131:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
4308 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
Threats
Process | Message |
|---|---|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|